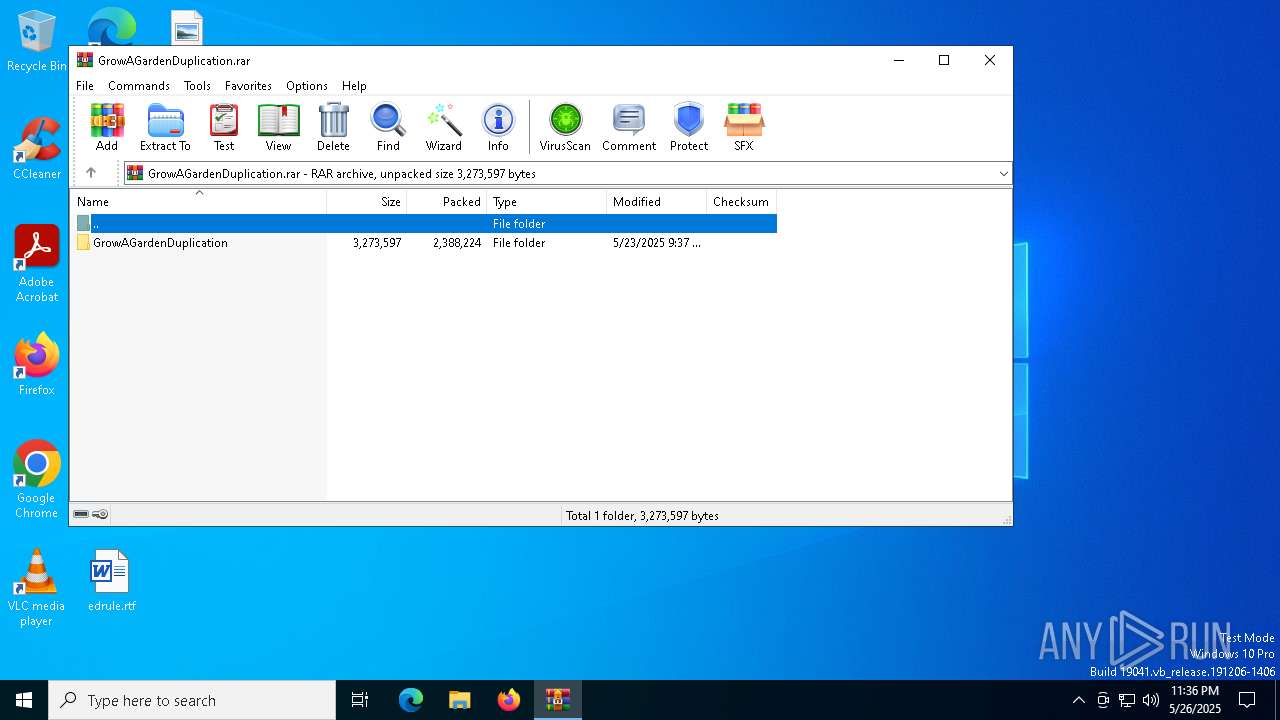
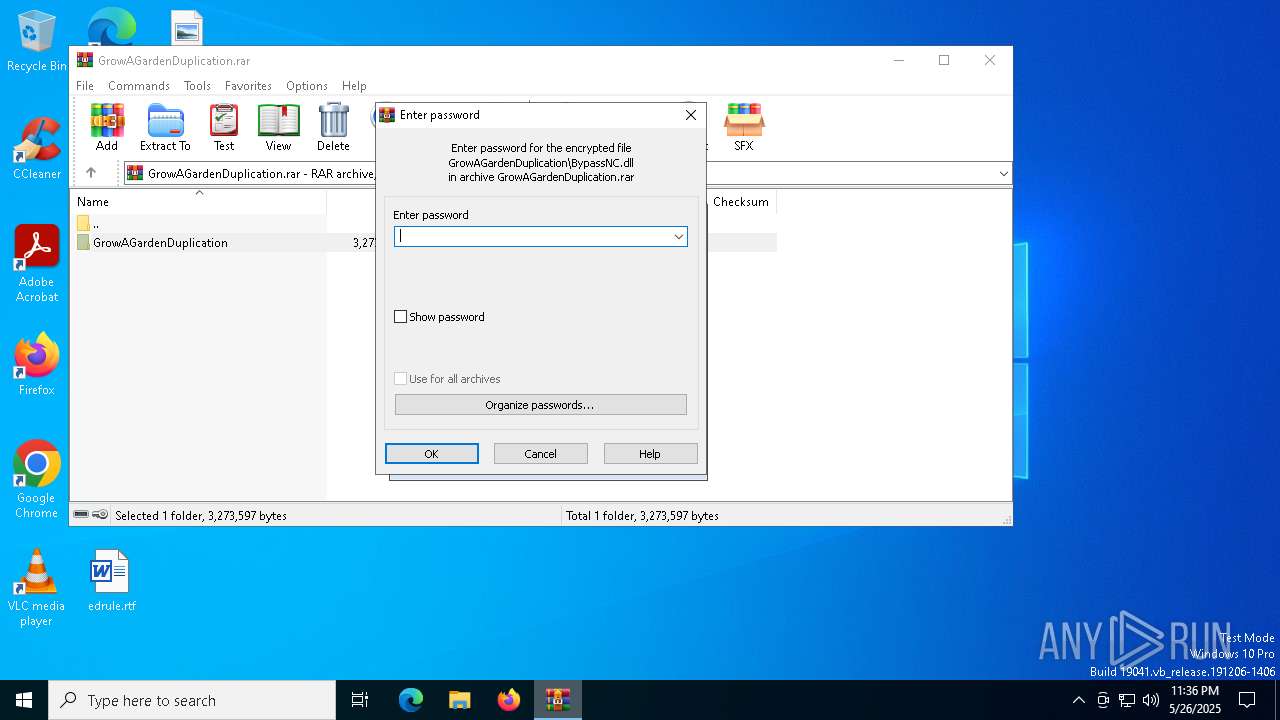
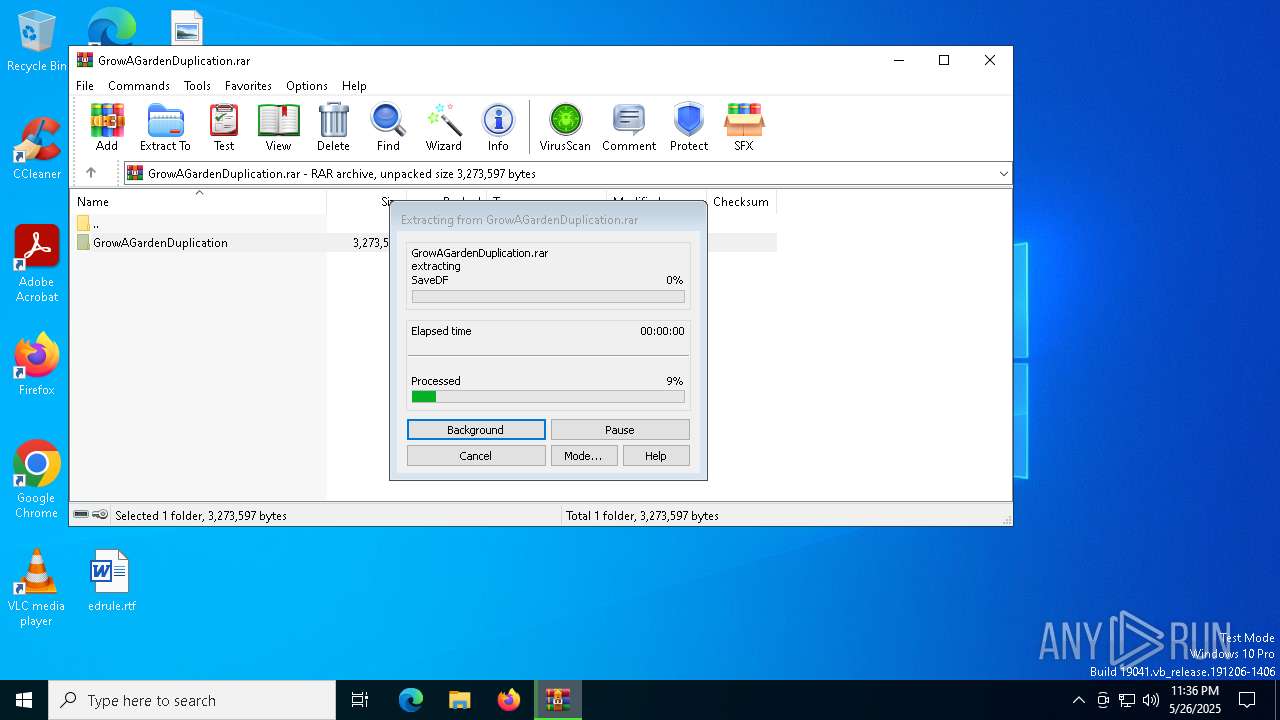
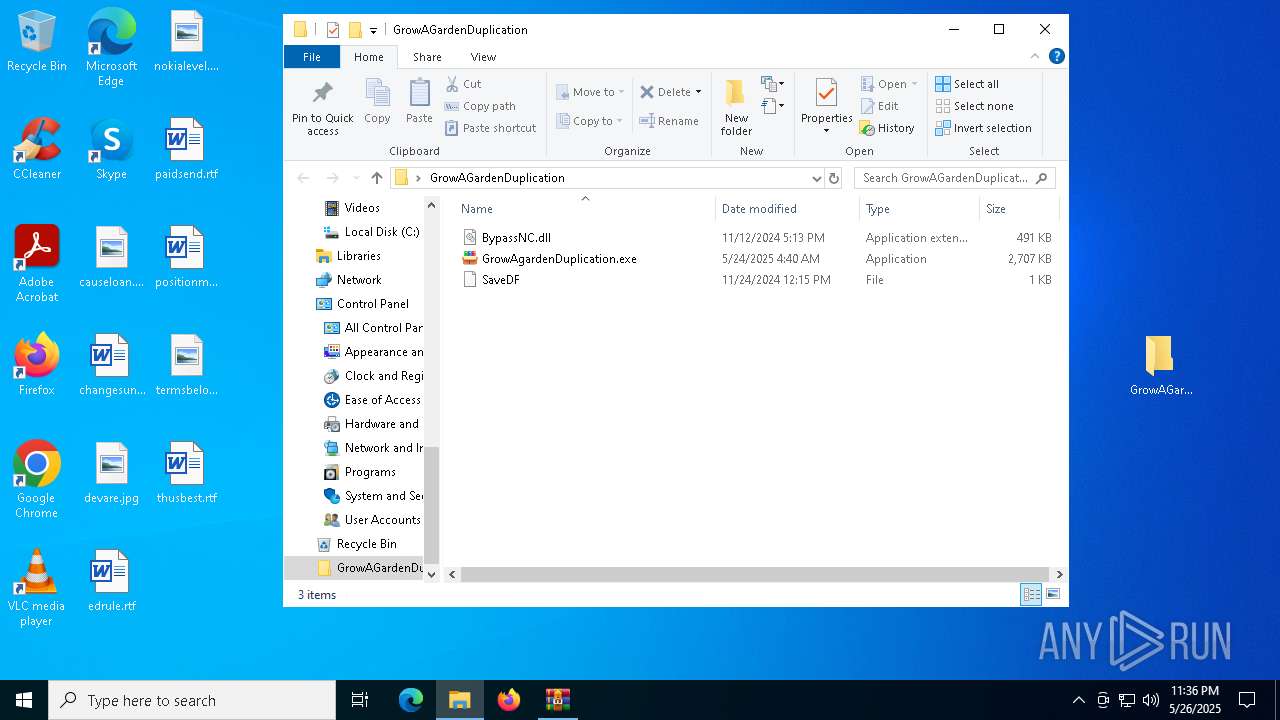
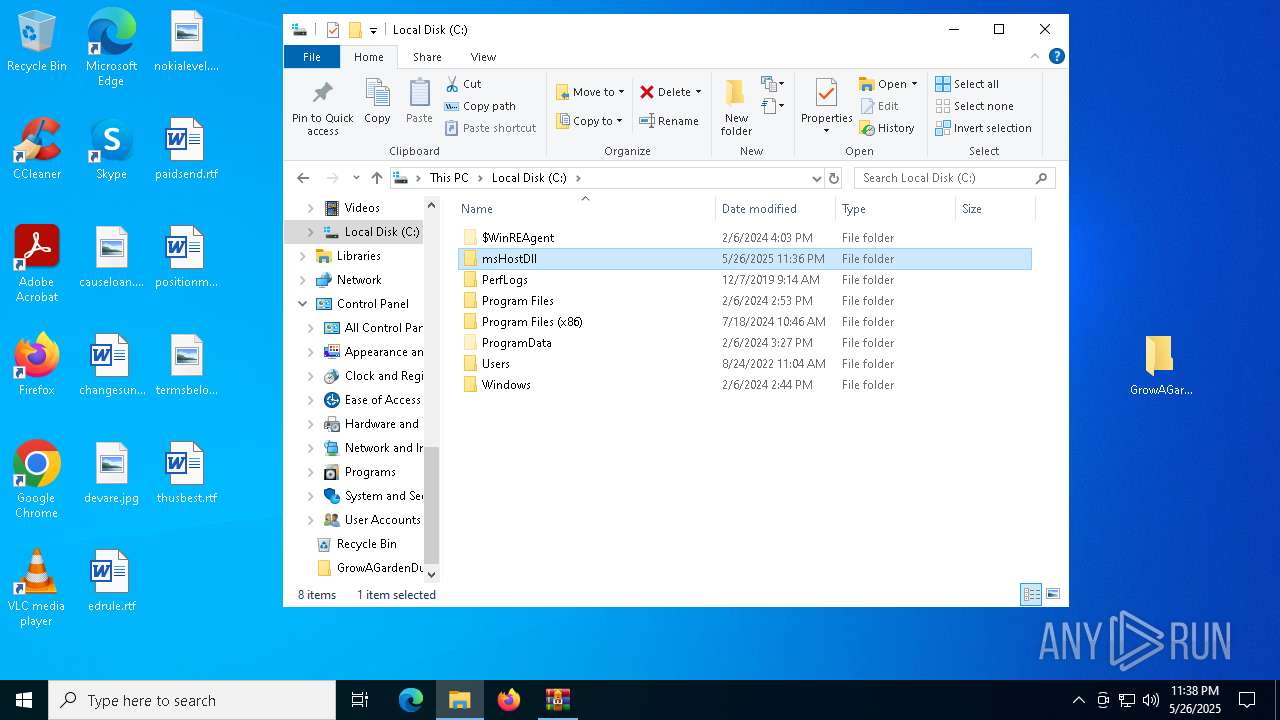
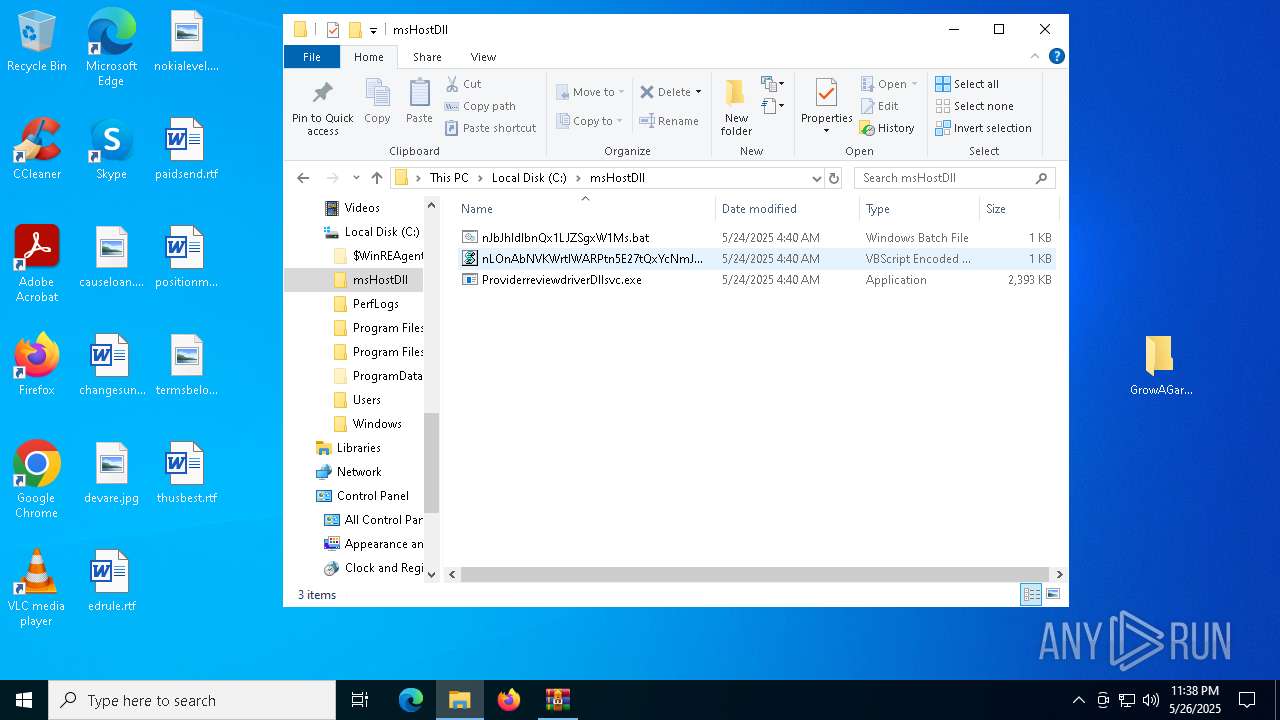
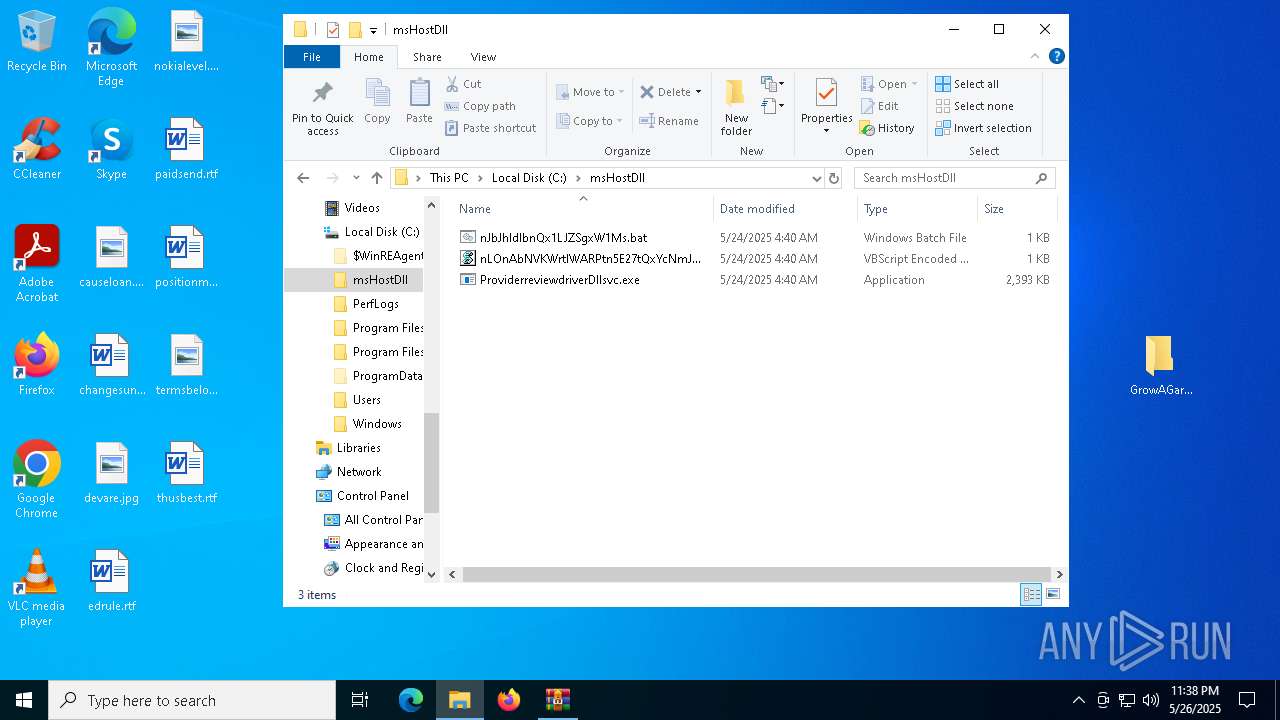
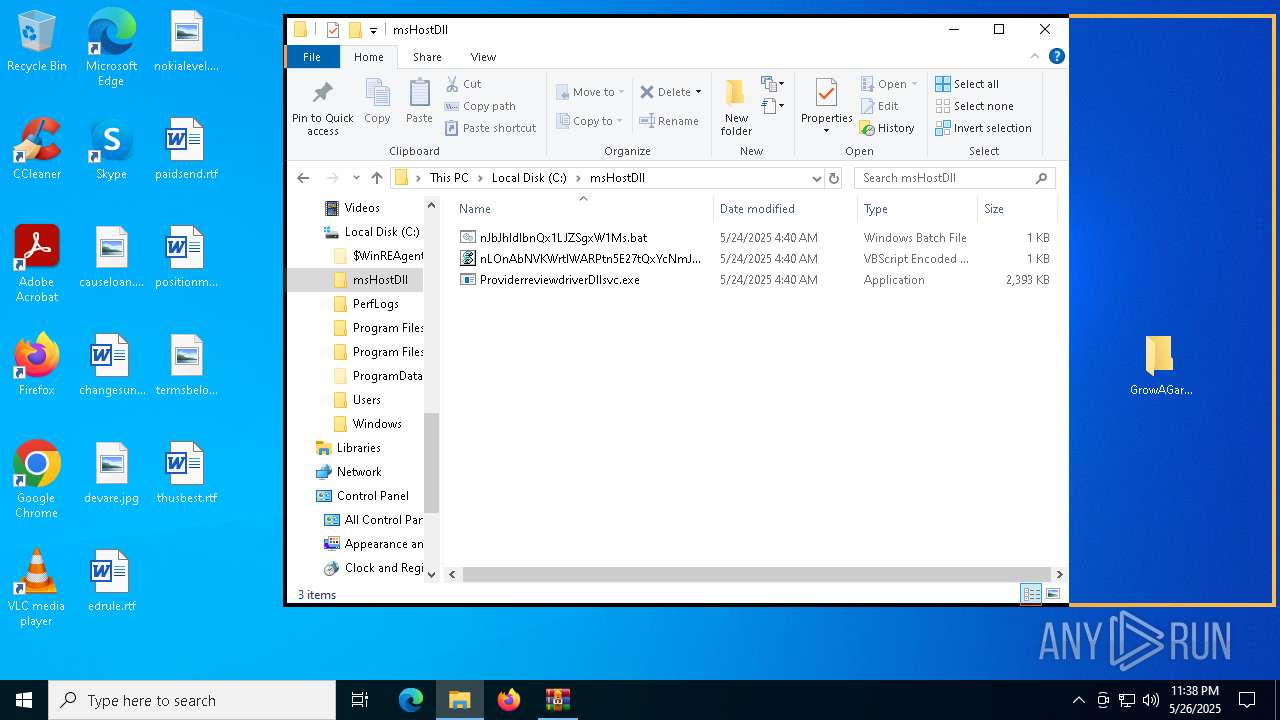
| File name: | GrowAGardenDuplication.rar |
| Full analysis: | https://app.any.run/tasks/63a3eb7f-e895-44d9-9429-0a24ec594374 |
| Verdict: | Malicious activity |
| Threats: | DCrat, also known as Dark Crystal RAT, is a remote access trojan (RAT), which was first introduced in 2018. It is a modular malware that can be customized to perform different tasks. For instance, it can steal passwords, crypto wallet information, hijack Telegram and Steam accounts, and more. Attackers may use a variety of methods to distribute DCrat, but phishing email campaigns are the most common. |
| Analysis date: | May 26, 2025, 23:36:34 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 0AAEA411ACD61ECA3CCA5533F1F27102 |
| SHA1: | 5139828871966E8B1D4BCA72ECBBEC2D7E5A3DDF |
| SHA256: | 8A68F0AAC1F981E8AC13498B41A68D6C56DBCEF8B3191845B11BB40D788C24EB |
| SSDEEP: | 98304:UfIwiCcsSFDS0B4zZ2xPIVCH1/S1w+4Tb2hhDcqGZ3e7uJaaS0Yk3j+WBK5U/7KS:P9qrh4/7h |
MALICIOUS
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 7324)
SUSPICIOUS
Executable content was dropped or overwritten
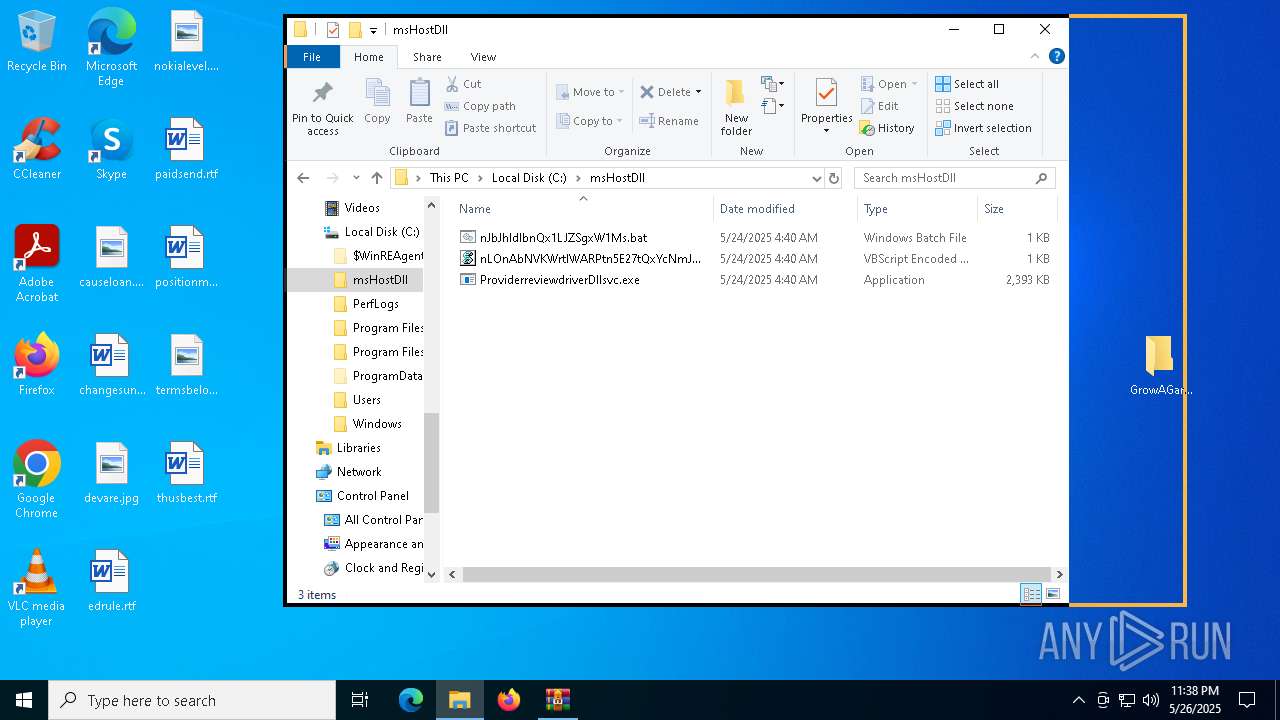
- GrowAgardenDuplication.exe (PID: 8160)
- ProviderreviewdriverDllsvc.exe (PID: 7456)
- ProviderreviewdriverDllsvc.exe (PID: 7652)
- ProviderreviewdriverDllsvc.exe (PID: 7960)
Reads security settings of Internet Explorer
- GrowAgardenDuplication.exe (PID: 8160)
Runs shell command (SCRIPT)
- wscript.exe (PID: 7324)
Executing commands from a ".bat" file
- wscript.exe (PID: 7324)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 7324)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7504)
Drops encrypted VBS script (Microsoft Script Encoder)
- GrowAgardenDuplication.exe (PID: 8160)
Manual execution by a user
- GrowAgardenDuplication.exe (PID: 8160)
- ProviderreviewdriverDllsvc.exe (PID: 7652)
- cmd.exe (PID: 7760)
Reads the computer name
- GrowAgardenDuplication.exe (PID: 8160)
- ProviderreviewdriverDllsvc.exe (PID: 7456)
- ProviderreviewdriverDllsvc.exe (PID: 7652)
- ProviderreviewdriverDllsvc.exe (PID: 7960)
Checks supported languages
- GrowAgardenDuplication.exe (PID: 8160)
- ProviderreviewdriverDllsvc.exe (PID: 7456)
- ProviderreviewdriverDllsvc.exe (PID: 7652)
- ProviderreviewdriverDllsvc.exe (PID: 7960)
Process checks computer location settings
- GrowAgardenDuplication.exe (PID: 8160)
Reads the machine GUID from the registry
- ProviderreviewdriverDllsvc.exe (PID: 7456)
- ProviderreviewdriverDllsvc.exe (PID: 7652)
- ProviderreviewdriverDllsvc.exe (PID: 7960)
Reads Environment values
- ProviderreviewdriverDllsvc.exe (PID: 7456)
- ProviderreviewdriverDllsvc.exe (PID: 7652)
- ProviderreviewdriverDllsvc.exe (PID: 7960)
Reads the software policy settings
- slui.exe (PID: 7704)
- slui.exe (PID: 4560)
Checks proxy server information
- slui.exe (PID: 4560)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 223360 |
| UncompressedSize: | 501856 |
| OperatingSystem: | Win32 |
| ArchivedFileName: | GrowAGardenDuplication/BypassNC.dll |
Total processes
144
Monitored processes
14
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 4180 | C:\WINDOWS\system32\cmd.exe /c ""C:\msHostDll\nJbJhldlbnQx1LJZSgxW1Ms.bat" " | C:\Windows\SysWOW64\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4560 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7324 | "C:\WINDOWS\System32\WScript.exe" "C:\msHostDll\nLOnAbNVKWrtIWARPtn5E27tQxYcNmJpWGcFjWmihOAc.vbe" | C:\Windows\SysWOW64\wscript.exe | — | GrowAgardenDuplication.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 7408 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7456 | "C:\msHostDll/ProviderreviewdriverDllsvc.exe" | C:\msHostDll\ProviderreviewdriverDllsvc.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 16.10.31418.88 Modules
| |||||||||||||||
| 7504 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\GrowAGardenDuplication.rar | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 7652 | "C:\msHostDll\ProviderreviewdriverDllsvc.exe" | C:\msHostDll\ProviderreviewdriverDllsvc.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 16.10.31418.88 Modules
| |||||||||||||||
| 7672 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7704 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7744 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
4 685
Read events
4 674
Write events
11
Delete events
0
Modification events
| (PID) Process: | (7504) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7504) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7504) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7504) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\GrowAGardenDuplication.rar | |||
| (PID) Process: | (7504) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7504) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7504) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7504) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7504) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (8160) GrowAgardenDuplication.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.vbe\OpenWithProgids |
| Operation: | write | Name: | VBEFile |
Value: | |||
Executable files
30
Suspicious files
1
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
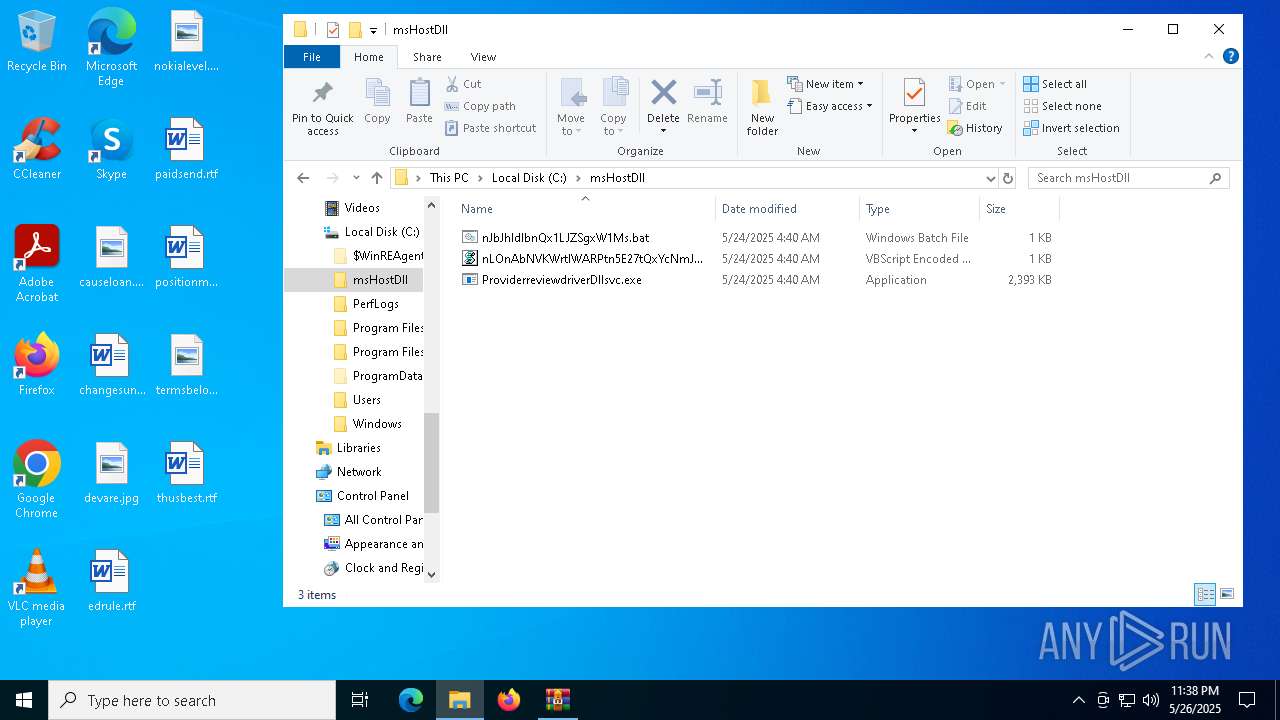
| 8160 | GrowAgardenDuplication.exe | C:\msHostDll\nJbJhldlbnQx1LJZSgxW1Ms.bat | text | |
MD5:FBB69E23CBB5FD2CD7FA8753924CF6CF | SHA256:8ABB64C1AB11E86F9D385FA5E77E004AAE8E54E406DE962AE06C468350C04926 | |||
| 7504 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb7504.41356\GrowAGardenDuplication\BypassNC.dll | executable | |
MD5:318B6CBAB2CD399E2CDC4456EF55747B | SHA256:BC0EF657AC2D07926A5A79E2E142DE0470B79F9D521D59739478F0D15463FBE7 | |||
| 7456 | ProviderreviewdriverDllsvc.exe | C:\Users\admin\Desktop\FTUdhzah.log | executable | |
MD5:00574FB20124EAFD40DC945EC86CA59C | SHA256:3A0C38E5DC41A8D668EBDD9368CEE89F4991350E6967A9715CAE8F36E0D032BB | |||
| 7456 | ProviderreviewdriverDllsvc.exe | C:\Users\admin\Desktop\YlHJBElx.log | executable | |
MD5:1DCDE09C6A8CE8F5179FB24D0C5A740D | SHA256:1F02230A8536ADB1D6F8DADFD7CA8CA66B5528EC98B15693E3E2F118A29D49D8 | |||
| 7456 | ProviderreviewdriverDllsvc.exe | C:\Users\admin\Desktop\ZqSkBnax.log | executable | |
MD5:BBDE7073BAAC996447F749992D65FFBA | SHA256:1FAE639DF1C497A54C9F42A8366EDAE3C0A6FEB4EB917ECAD9323EF8D87393E8 | |||
| 7456 | ProviderreviewdriverDllsvc.exe | C:\Users\admin\Desktop\iTaZkgqe.log | executable | |
MD5:F4B38D0F95B7E844DD288B441EBC9AAF | SHA256:AAB95596475CA74CEDE5BA50F642D92FA029F6F74F6FAEAE82A9A07285A5FB97 | |||
| 7456 | ProviderreviewdriverDllsvc.exe | C:\Users\admin\Desktop\PCntRbfP.log | executable | |
MD5:2D6975FD1CC3774916D8FF75C449EE7B | SHA256:75CE6EB6CDDD67D47FB7C5782F45FDC497232F87A883650BA98679F92708A986 | |||
| 7652 | ProviderreviewdriverDllsvc.exe | C:\Users\admin\Desktop\wgvsmhXX.log | executable | |
MD5:91FB2078C1DD5D8307149D9EA288FFF9 | SHA256:80E1A5E95A2412691095F76C4E812CF623C3C63AE5A79545C99745F27E023050 | |||
| 7652 | ProviderreviewdriverDllsvc.exe | C:\Users\admin\Desktop\nCnCCoHp.log | executable | |
MD5:F4B38D0F95B7E844DD288B441EBC9AAF | SHA256:AAB95596475CA74CEDE5BA50F642D92FA029F6F74F6FAEAE82A9A07285A5FB97 | |||
| 7652 | ProviderreviewdriverDllsvc.exe | C:\Users\admin\Desktop\mxccCESp.log | executable | |
MD5:BBDE7073BAAC996447F749992D65FFBA | SHA256:1FAE639DF1C497A54C9F42A8366EDAE3C0A6FEB4EB917ECAD9323EF8D87393E8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
22
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7052 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7052 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6544 | svchost.exe | 40.126.31.131:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
5796 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
7052 | SIHClient.exe | 52.149.20.212:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |