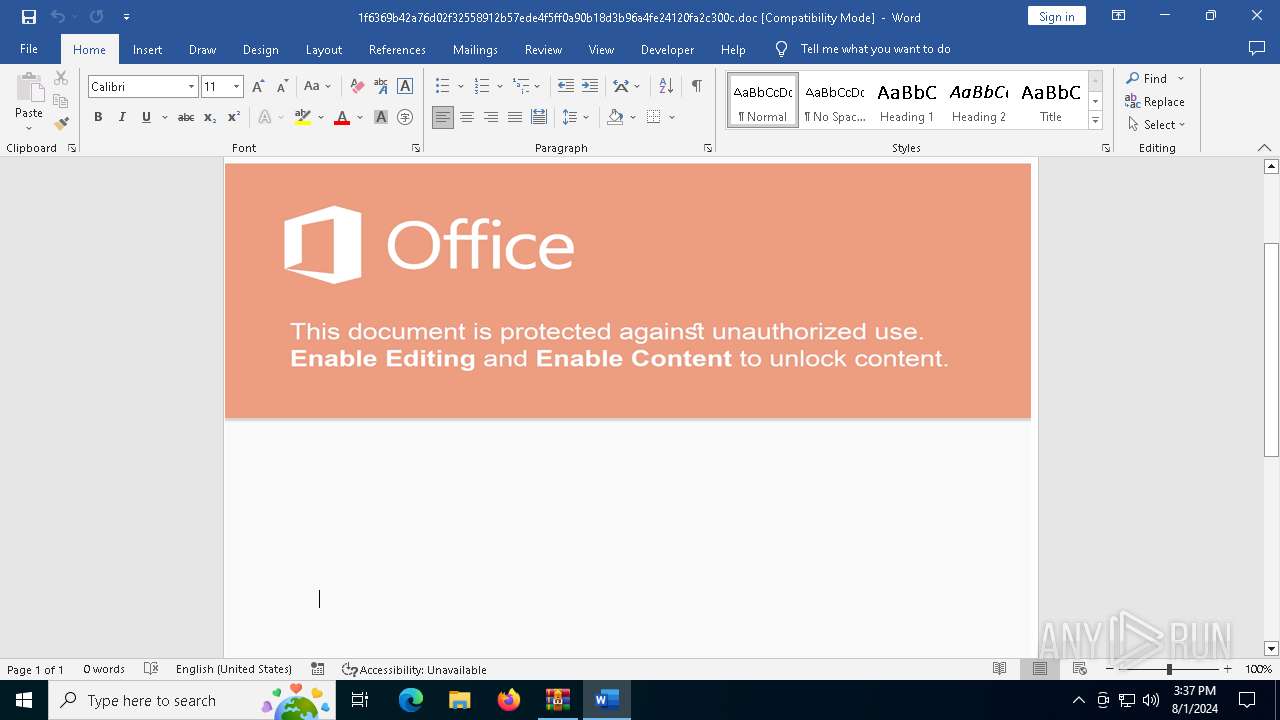
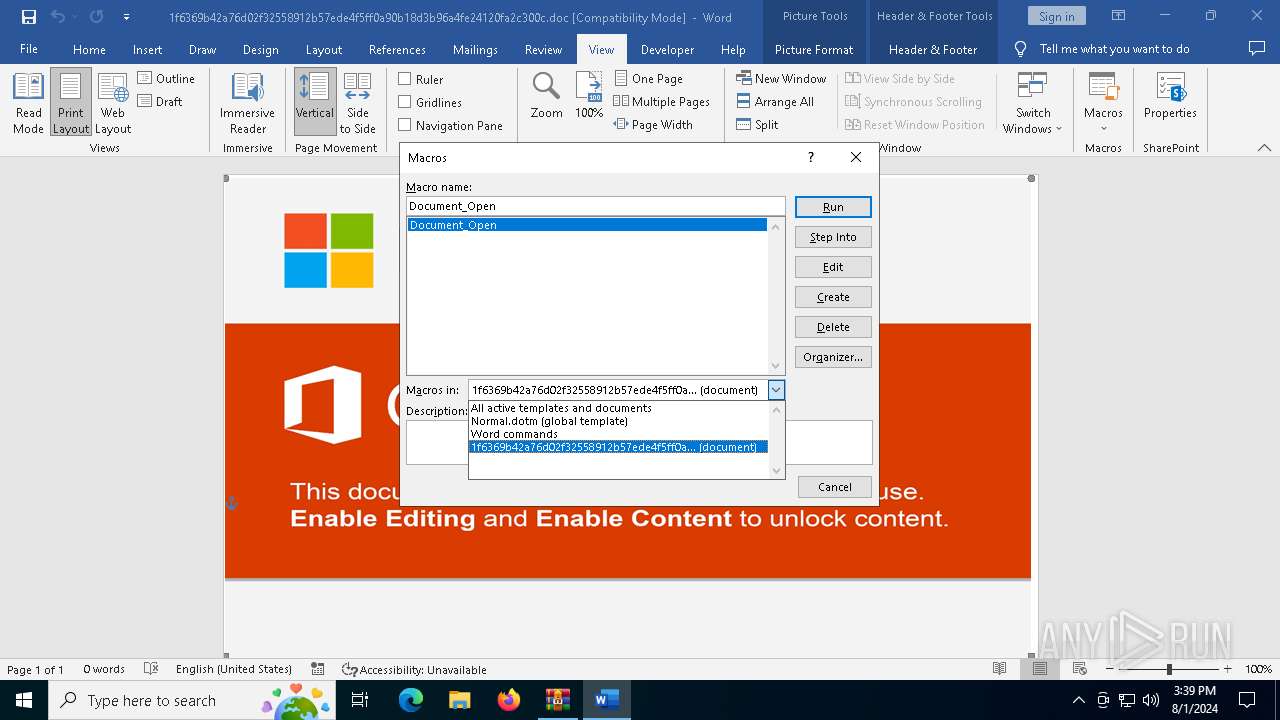
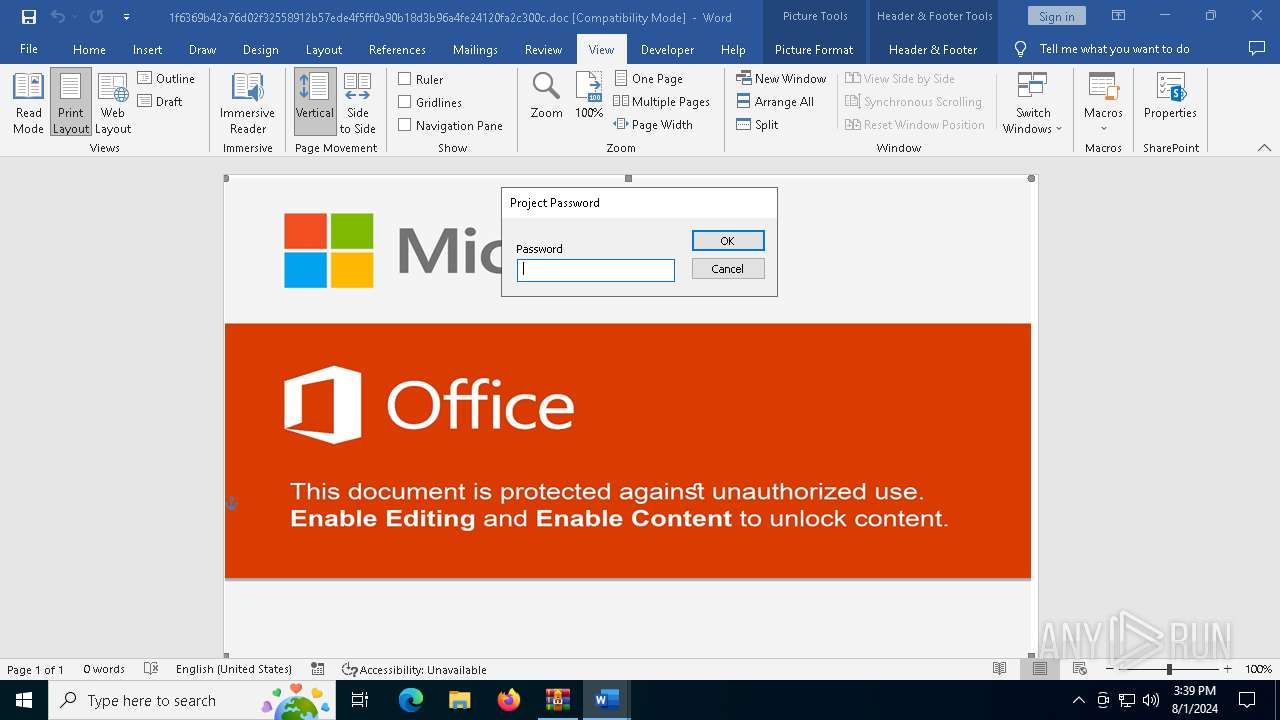
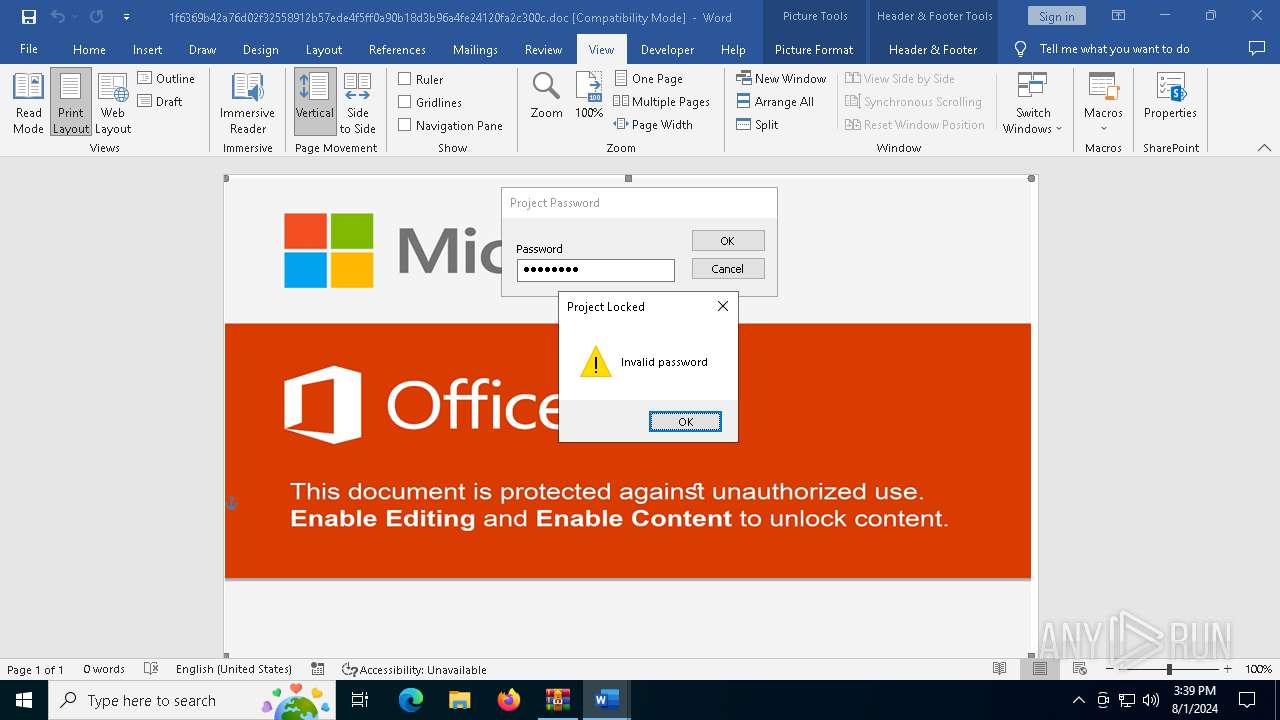
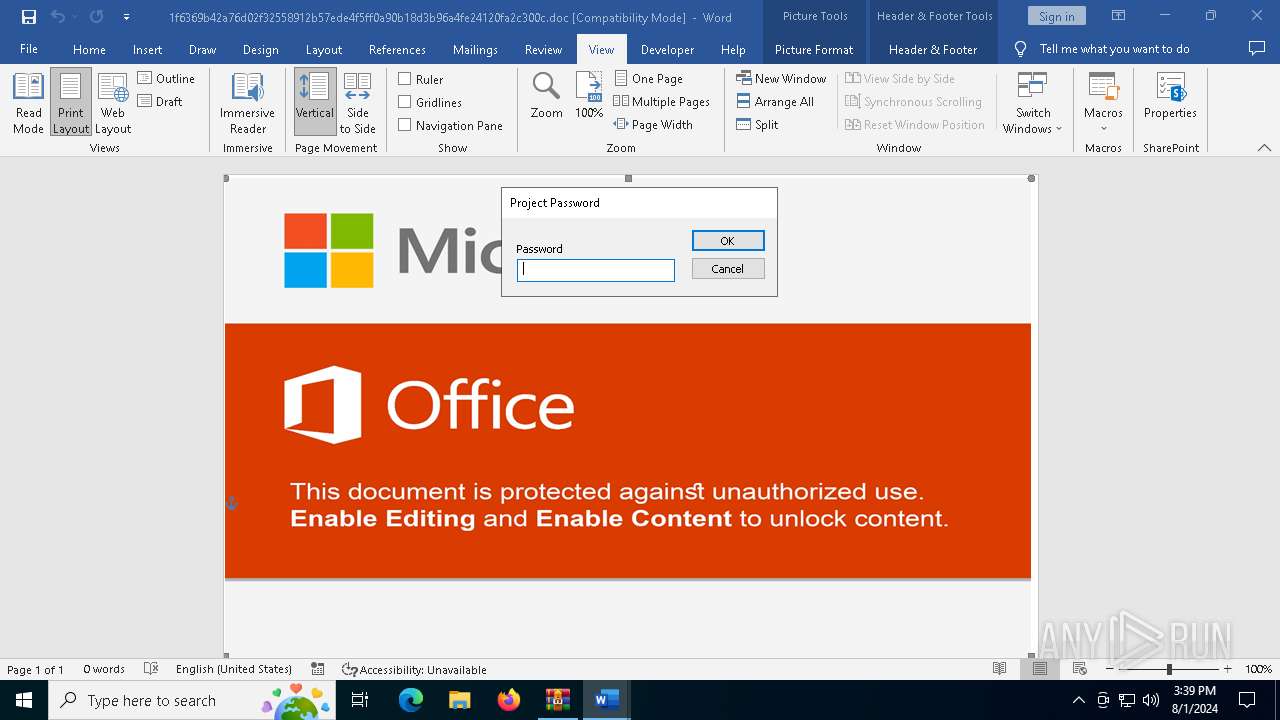
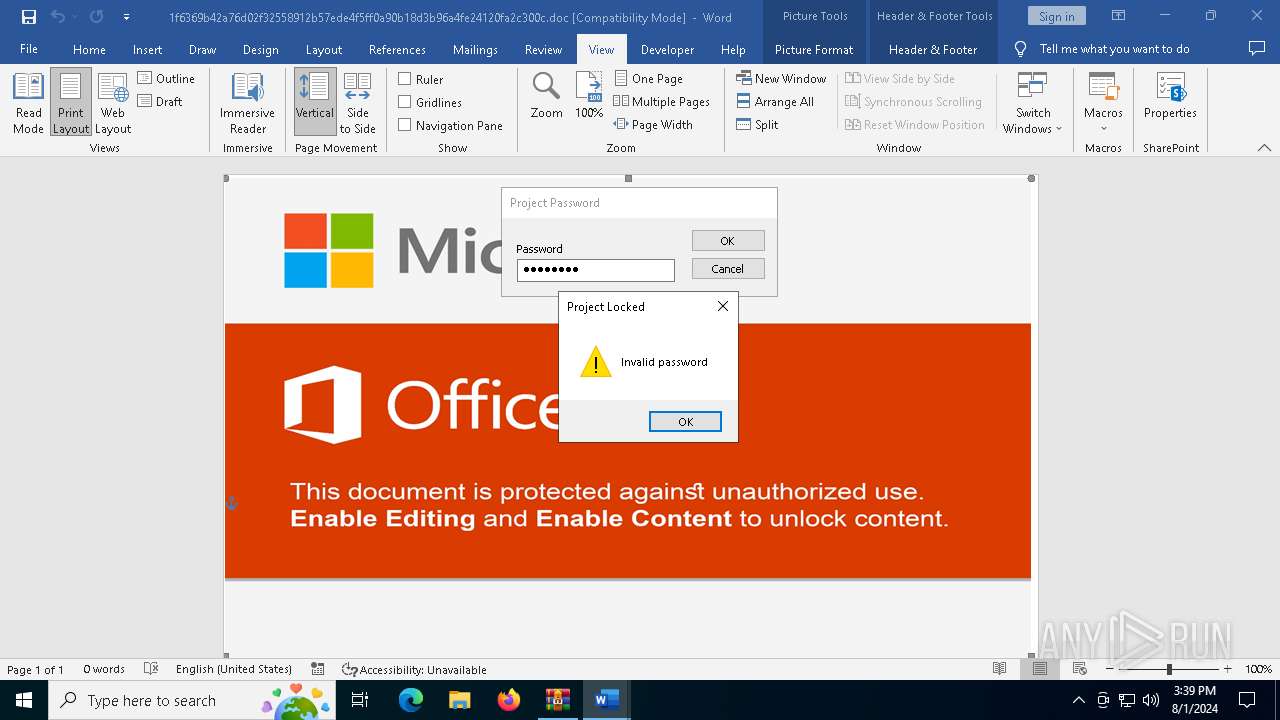
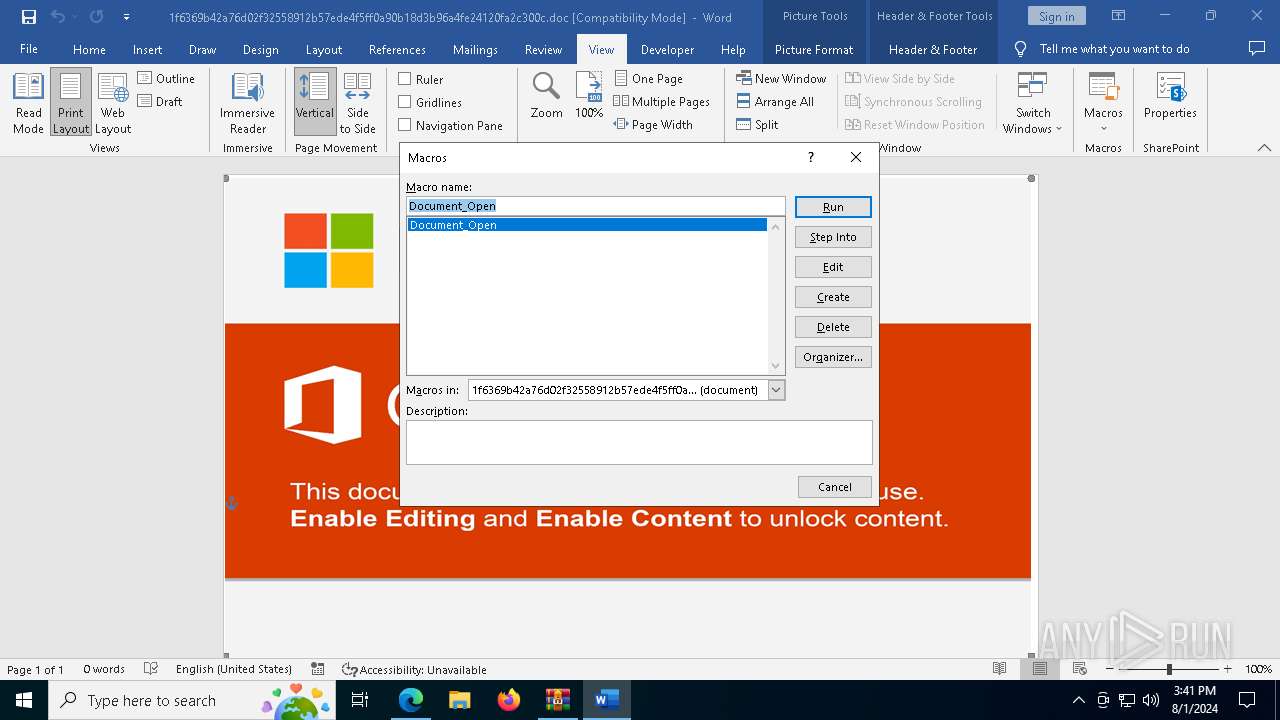
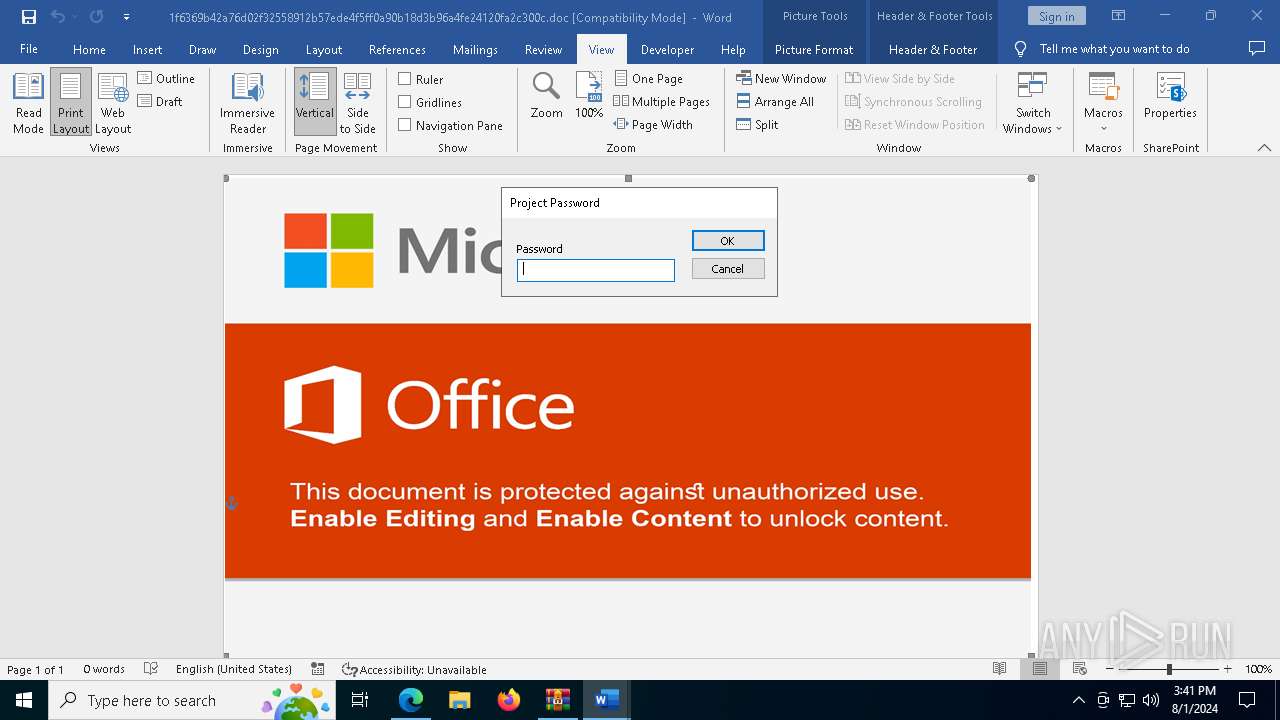
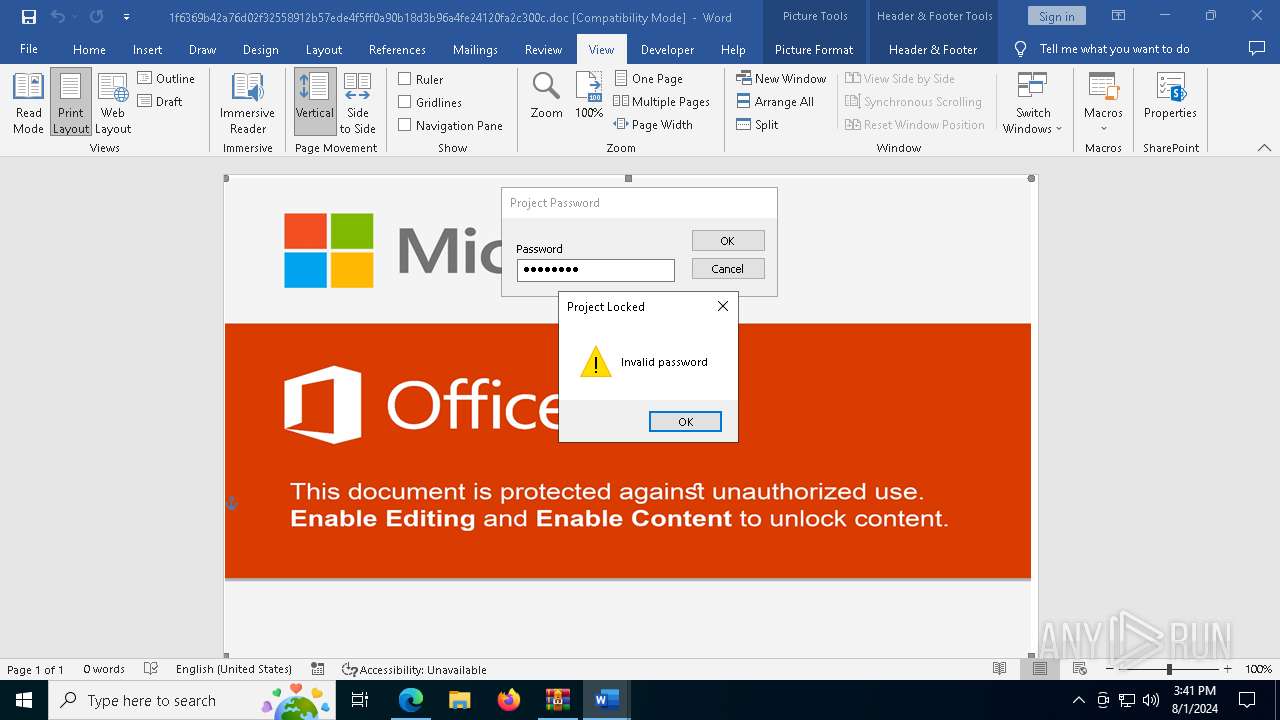
| File name: | VirusShare_486bdf835a453c6ffb5f56647e697871.zip |
| Full analysis: | https://app.any.run/tasks/c29c3c3a-da84-4f75-abd8-0ec088410cdb |
| Verdict: | Malicious activity |
| Analysis date: | August 01, 2024, 15:36:57 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | B8B09FC0B813AB41174DF6ABEA91276D |
| SHA1: | DCCBCD46D90B98CEA5B69AF5B582F8B51A4A0557 |
| SHA256: | 8A595F06C8AB01C29015CF26114DBF26B66BE01E59ED0ADF5413C23ECD8F23C5 |
| SSDEEP: | 6144:ZHv9gSLB4nl9NdvgMQtDm/E6fksPppefL1/DgPMGxHBbdfrJ:ZP9gQ4nl5eDm/NfksPjefhazxHBD |
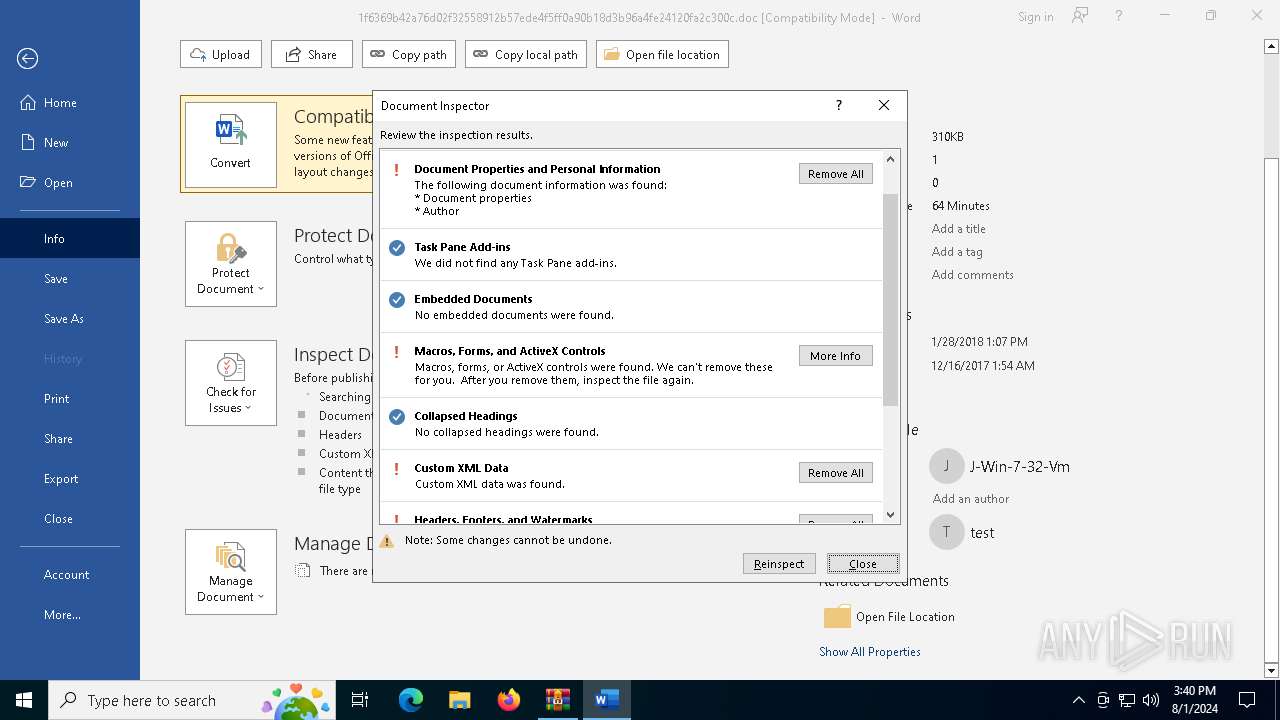
MALICIOUS
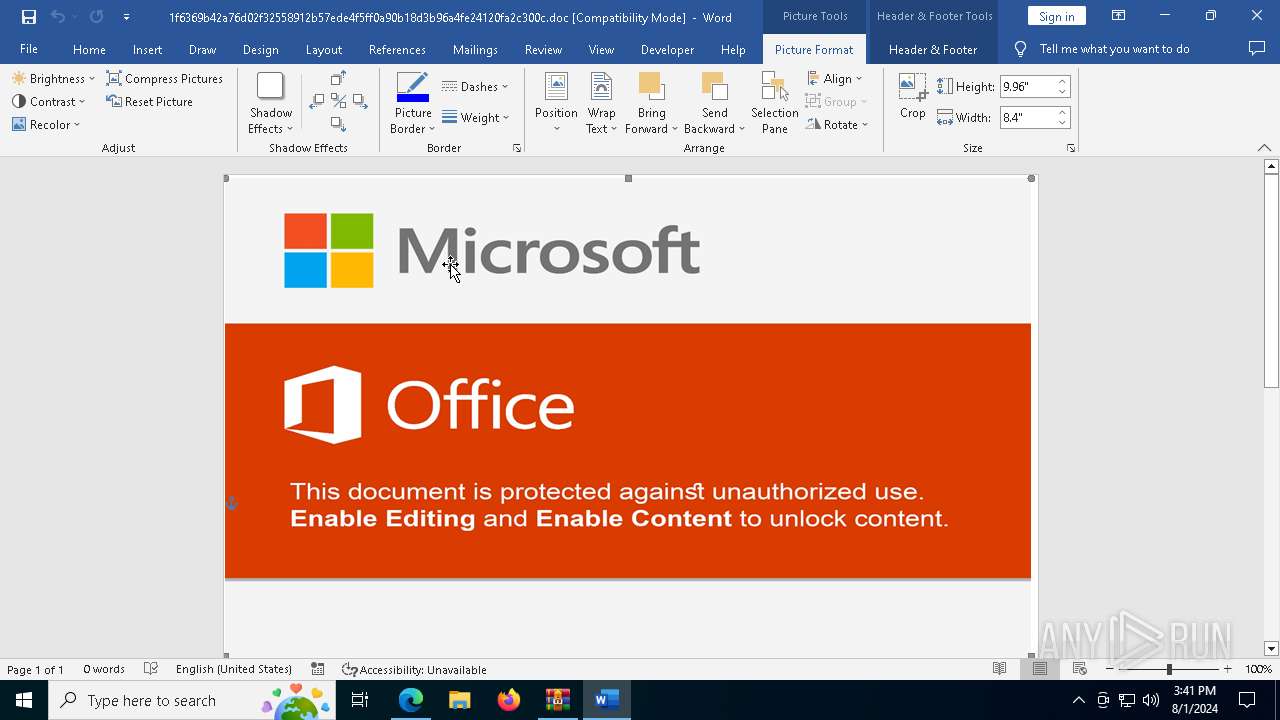
Opens a text file (SCRIPT)
- WINWORD.EXE (PID: 6124)
Microsoft Office executes commands via PowerShell or Cmd
- WINWORD.EXE (PID: 6124)
Unusual execution from MS Office
- WINWORD.EXE (PID: 6124)
Starts CMD.EXE for commands execution
- WINWORD.EXE (PID: 6124)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 232)
- cmd.exe (PID: 4644)
- cmd.exe (PID: 1076)
- cmd.exe (PID: 1140)
Bypass execution policy to execute commands
- powershell.exe (PID: 6440)
- powershell.exe (PID: 2456)
Run PowerShell with an invisible window
- powershell.exe (PID: 6440)
- powershell.exe (PID: 2456)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 1964)
- cmd.exe (PID: 6292)
SUSPICIOUS
Creates FileSystem object to access computer's file system (SCRIPT)
- WINWORD.EXE (PID: 6124)
Access the System.Security .NET namespace (SCRIPT)
- WINWORD.EXE (PID: 6124)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6704)
Writes binary data to a Stream object (SCRIPT)
- WINWORD.EXE (PID: 6124)
Runs shell command (SCRIPT)
- WINWORD.EXE (PID: 6124)
- wscript.exe (PID: 1132)
- wscript.exe (PID: 6260)
The process executes via Task Scheduler
- wscript.exe (PID: 1132)
- wscript.exe (PID: 6260)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 1132)
- powershell.exe (PID: 6440)
- wscript.exe (PID: 6260)
- powershell.exe (PID: 2456)
The process executes Powershell scripts
- cmd.exe (PID: 1964)
- cmd.exe (PID: 6292)
Deletes scheduled task without confirmation
- schtasks.exe (PID: 6272)
- schtasks.exe (PID: 3136)
Writes data into a file (POWERSHELL)
- powershell.exe (PID: 6440)
Lists all scheduled tasks in specific format
- schtasks.exe (PID: 3036)
- schtasks.exe (PID: 5760)
Using 'findstr.exe' to search for text patterns in files and output
- powershell.exe (PID: 6440)
- powershell.exe (PID: 2456)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 6440)
- powershell.exe (PID: 2456)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 6292)
- cmd.exe (PID: 1964)
INFO
Reads the computer name
- TextInputHost.exe (PID: 7052)
- identity_helper.exe (PID: 7356)
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 6704)
- msedge.exe (PID: 4296)
Checks supported languages
- TextInputHost.exe (PID: 7052)
- identity_helper.exe (PID: 7356)
Disables trace logs
- powershell.exe (PID: 6440)
- powershell.exe (PID: 2456)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 6440)
- powershell.exe (PID: 2456)
Checks proxy server information
- powershell.exe (PID: 6440)
- powershell.exe (PID: 2456)
Gets data length (POWERSHELL)
- powershell.exe (PID: 6440)
- powershell.exe (PID: 2456)
Reads Environment values
- identity_helper.exe (PID: 7356)
Application launched itself
- msedge.exe (PID: 4296)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2018:01:30 04:42:38 |
| ZipCRC: | 0xe4b58566 |
| ZipCompressedSize: | 256200 |
| ZipUncompressedSize: | 317952 |
| ZipFileName: | 1f6369b42a76d02f32558912b57ede4f5ff0a90b18d3b96a4fe24120fa2c300c |
Total processes
206
Monitored processes
77
Malicious processes
7
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 232 | C:\WINDOWS\system32\cmd.exe /c SchTasks /Create /SC MINUTE /MO 1 /TN "Conhost" /TR "wscript C:\Users\admin\AppData\Roaming\AdobeAcrobatLicenseVerify.vbs" | C:\Windows\System32\cmd.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 304 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 888 | schtasks /create /sc minute /mo 5 /tn AdobeAcrobatLicenseVerify /tr "wscript.exe "C:\Users\admin\AppData\Local\Temp\AdobeAcrobatLicenseVerify.vbs" \"powershell.exe -ExecutionPolicy bypass -WindowStyle hidden -NoProfile 'C:\Users\admin\AppData\Roaming\AdobeAcrobatLicenseVerify.ps1' \"" | C:\Windows\System32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 964 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "809800FB-4033-4C1F-9ED8-227FFC3AB6BD" "FF7F0B92-4F89-46CD-8855-53DFBB9F53AC" "6124" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
| 1076 | C:\WINDOWS\system32\cmd.exe /c SchTasks /Create /SC MINUTE /MO 1 /TN "Conhost" /TR "wscript C:\Users\admin\AppData\Roaming\AdobeAcrobatLicenseVerify.vbs" | C:\Windows\System32\cmd.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1132 | "C:\WINDOWS\system32\wscript.EXE" C:\Users\admin\AppData\Roaming\AdobeAcrobatLicenseVerify.vbs | C:\Windows\System32\wscript.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 1140 | C:\WINDOWS\system32\cmd.exe /c SchTasks /Create /SC MINUTE /MO 1 /TN "Conhost" /TR "wscript C:\Users\admin\AppData\Roaming\AdobeAcrobatLicenseVerify.vbs" | C:\Windows\System32\cmd.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1452 | C:\WINDOWS\system32\cmd.exe /c echo Set oShell = WScript.CreateObject ("WScript.Shell") : oShell.run "cmd.exe /c Powershell -exec bypass -Windowstyle hidden -File C:\Users\admin\AppData\Roaming\AdobeAcrobatLicenseVerify.ps1 ",0,0 > "C:\Users\admin\AppData\Roaming\AdobeAcrobatLicenseVerify.vbs" | C:\Windows\System32\cmd.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1492 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1556 | "C:\WINDOWS\system32\findstr.exe" AdobeAcrobatLicenseVerify | C:\Windows\System32\findstr.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
52 361
Read events
51 703
Write events
587
Delete events
71
Modification events
| (PID) Process: | (6704) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6704) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6704) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6704) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\VirusShare_486bdf835a453c6ffb5f56647e697871.zip | |||
| (PID) Process: | (6704) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6704) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6704) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6704) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6704) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (6704) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
0
Suspicious files
318
Text files
120
Unknown types
34
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6124 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:6FCFB8F15BF86A78B9B7B77C063DC27F | SHA256:— | |||
| 6124 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\Rar$DIb6704.45569\~$6369b42a76d02f32558912b57ede4f5ff0a90b18d3b96a4fe24120fa2c300c.doc | abr | |
MD5:318BC1F3E495729BFF96325F4DFA6057 | SHA256:— | |||
| 4232 | cmd.exe | C:\Users\admin\AppData\Roaming\AdobeAcrobatLicenseVerify.vbs | text | |
MD5:BA2B36EC76F13B0B6CC3B263EF9D3026 | SHA256:B7DFDBC89FABF327F9A6AAEB233030B04A7AF202CC72559BD9BEE39A98ADFD4C | |||
| 6704 | WinRAR.exe | C:\Users\admin\Downloads\__rzi_6704.45355 | compressed | |
MD5:74EA960DD56B8782D91B1613D629C9B8 | SHA256:6943B298FC7F03B95514D26014F4186C248EB0A9295A47EFF56DFCADFBB0646E | |||
| 6124 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\8EB474DB-725D-40DD-8739-C05A03BFE320 | xml | |
MD5:29BE722147447CBB2F4EF5F9343DAEFB | SHA256:— | |||
| 6704 | WinRAR.exe | C:\Users\admin\Downloads\VirusShare_486bdf835a453c6ffb5f56647e697871.zip | compressed | |
MD5:74EA960DD56B8782D91B1613D629C9B8 | SHA256:6943B298FC7F03B95514D26014F4186C248EB0A9295A47EFF56DFCADFBB0646E | |||
| 6124 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | abr | |
MD5:4F9AEA3F51868F4B5966D14C6DD0FDD5 | SHA256:— | |||
| 6124 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\fb3b0dbfee58fac8.customDestinations-ms | binary | |
MD5:E4A1661C2C886EBB688DEC494532431C | SHA256:B76875C50EF704DBBF7F02C982445971D1BBD61AEBE2E4B28DDC58A1D66317D5 | |||
| 6124 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntitiesUpdated.bin | text | |
MD5:7AFCA3C1F9F4CEEFB65CFA56EEA061B9 | SHA256:— | |||
| 6124 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\AdobeAcrobatLicenseVerify.ps1 | text | |
MD5:93B79FEA62A774DD781E3278CDDAE898 | SHA256:322C502CBE74FA99FA1F162CC6AC6CE1D9594945E68584DC326D39298589B328 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
20
TCP/UDP connections
190
DNS requests
252
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6124 | WINWORD.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6124 | WINWORD.EXE | GET | 200 | 104.85.249.160:80 | http://crl.microsoft.com/pki/crl/products/microsoftrootcert.crl | unknown | — | — | whitelisted |
6124 | WINWORD.EXE | GET | 200 | 104.85.249.160:80 | http://crl.microsoft.com/pki/crl/products/MicCodSigPCA_08-31-2010.crl | unknown | — | — | whitelisted |
6124 | WINWORD.EXE | GET | 200 | 104.85.249.160:80 | http://crl.microsoft.com/pki/crl/products/MicrosoftTimeStampPCA.crl | unknown | — | — | whitelisted |
6124 | WINWORD.EXE | GET | 200 | 23.200.161.157:80 | http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl | unknown | — | — | whitelisted |
6124 | WINWORD.EXE | GET | 200 | 104.85.249.160:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
7108 | msedge.exe | GET | 304 | 95.100.111.187:80 | http://apps.identrust.com/roots/dstrootcax3.p7c | unknown | — | — | whitelisted |
6124 | WINWORD.EXE | GET | 200 | 104.85.249.160:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
7108 | msedge.exe | GET | 304 | 2.20.33.52:80 | http://x1.i.lencr.org/ | unknown | — | — | whitelisted |
7108 | msedge.exe | GET | 304 | 2.20.33.52:80 | http://r3.i.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | unknown |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | unknown |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:137 | — | — | — | unknown |
6124 | WINWORD.EXE | 52.109.32.97:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | unknown |
6124 | WINWORD.EXE | 52.113.194.132:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
6124 | WINWORD.EXE | 104.85.249.128:443 | omex.cdn.office.net | Akamai International B.V. | PL | unknown |
6124 | WINWORD.EXE | 52.111.232.11:443 | messaging.lifecycle.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | JP | unknown |
6124 | WINWORD.EXE | 20.189.173.9:443 | self.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| unknown |
google.com |
| unknown |
officeclient.microsoft.com |
| unknown |
omex.cdn.office.net |
| unknown |
ecs.office.com |
| unknown |
messaging.lifecycle.office.com |
| unknown |
self.events.data.microsoft.com |
| unknown |
ocsp.digicert.com |
| unknown |
metadata.templates.cdn.office.net |
| unknown |
binaries.templates.cdn.office.net |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7108 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Request to Azure content delivery network (aadcdn .ms__auth .net) |
7108 | msedge.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
7108 | msedge.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
7108 | msedge.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
Process | Message |
|---|---|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|