| URL: | videocallgirl.top/alb |
| Full analysis: | https://app.any.run/tasks/518c4b24-d35c-4b45-8a07-ccc2f75aef07 |
| Verdict: | Malicious activity |
| Analysis date: | December 10, 2023, 15:49:45 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 696EDEBF7DB13522A210567474F49342 |
| SHA1: | 6299C6227A1B3F72669C512946C6DC60429DB7AD |
| SHA256: | 8A53F34265FEE2D691EB3307C3F73A1C5F537678B9BFF4AFE78210E19FB9B111 |
| SSDEEP: | 3:keEJReJ:k3eJ |
MALICIOUS
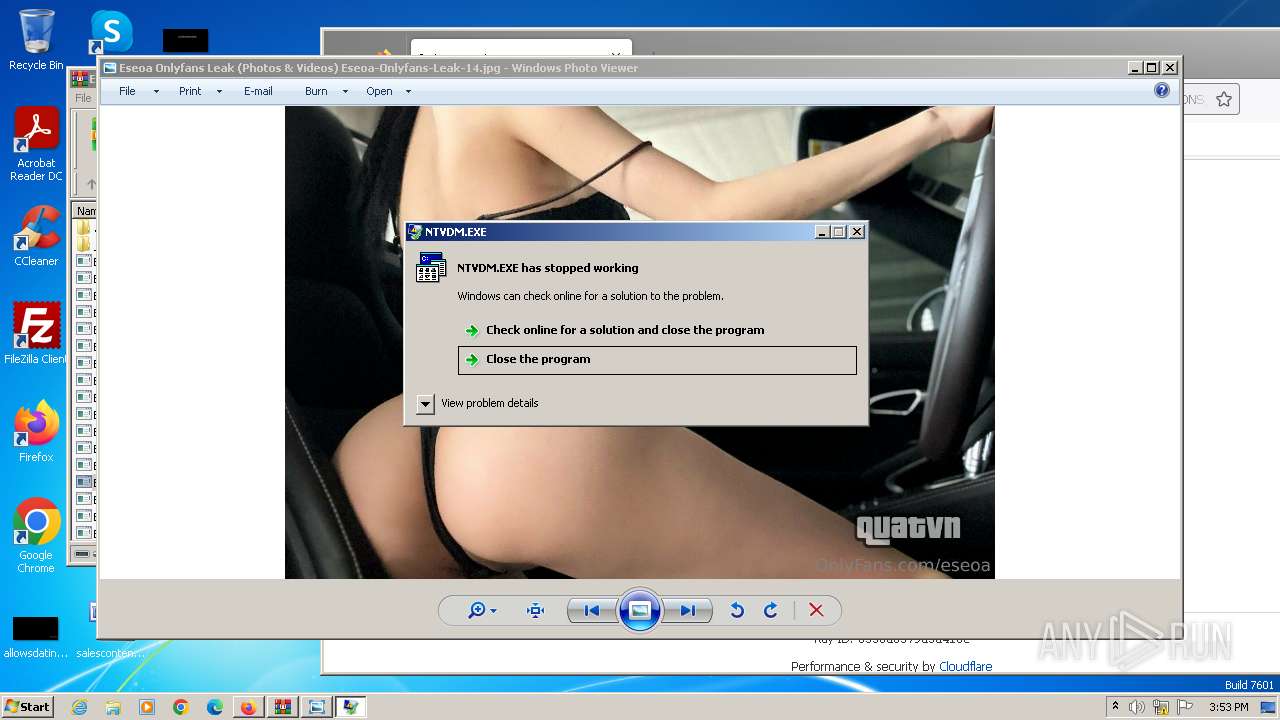
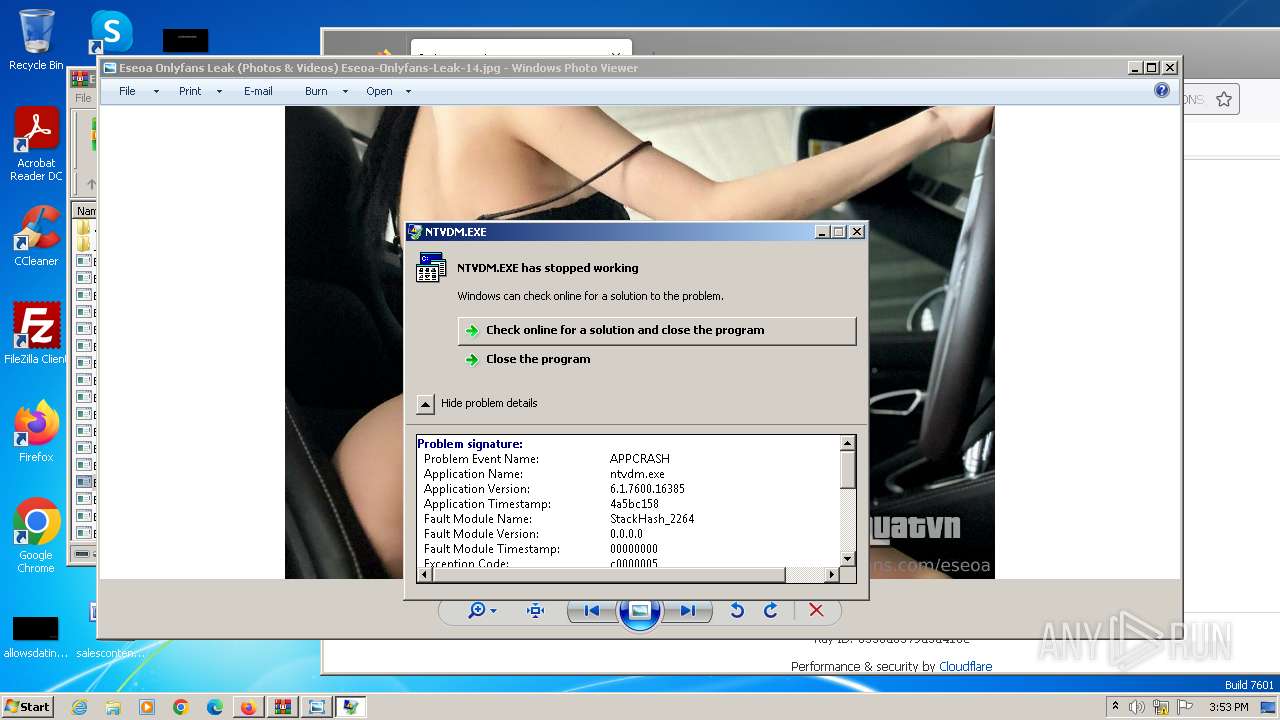
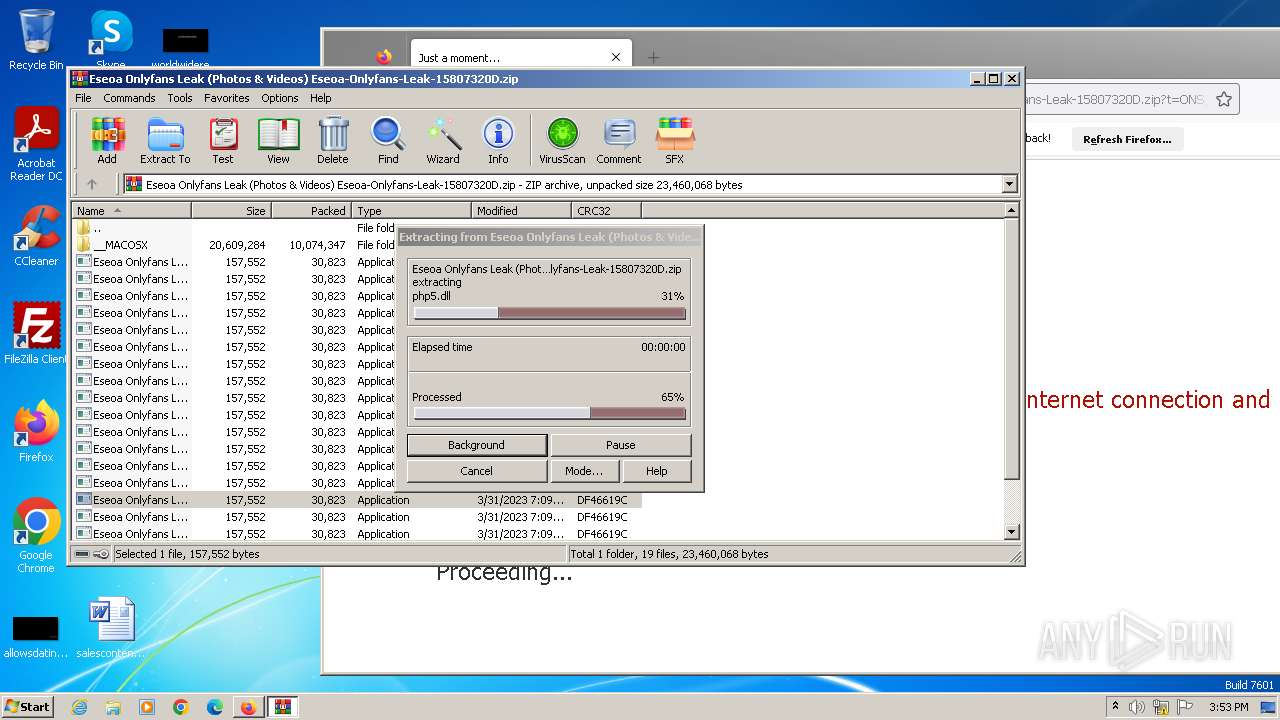
Drops the executable file immediately after the start
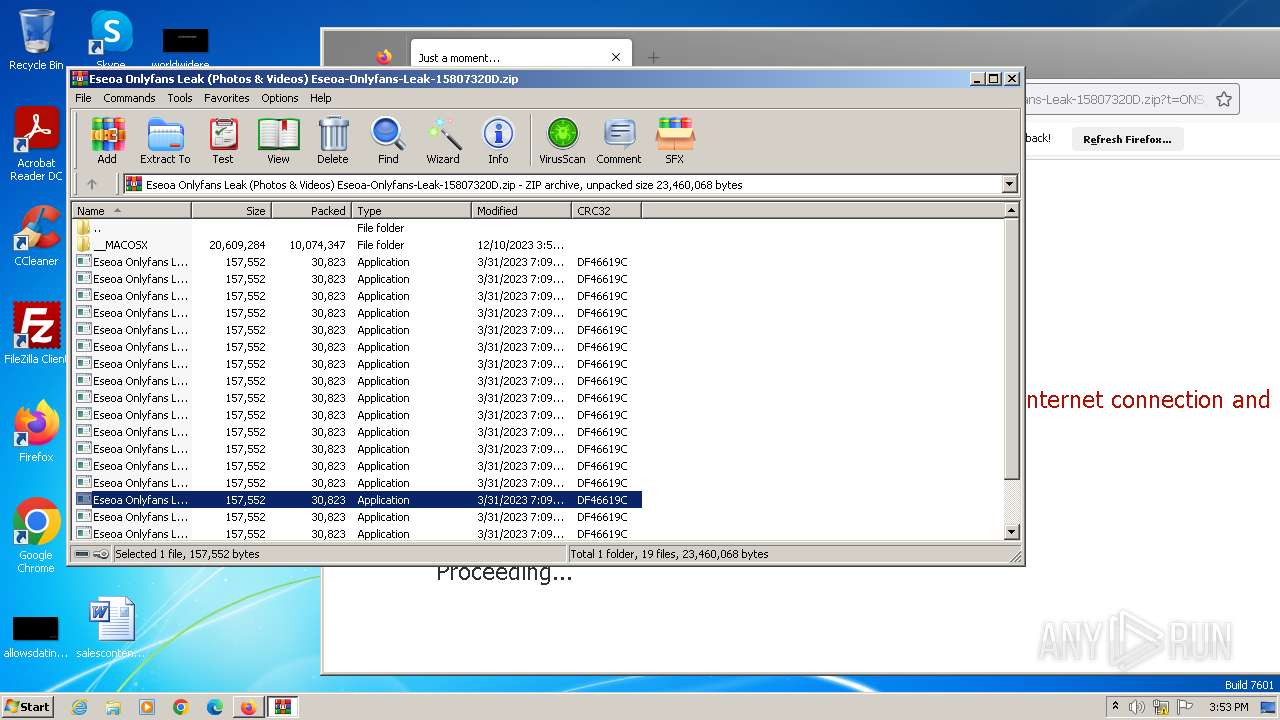
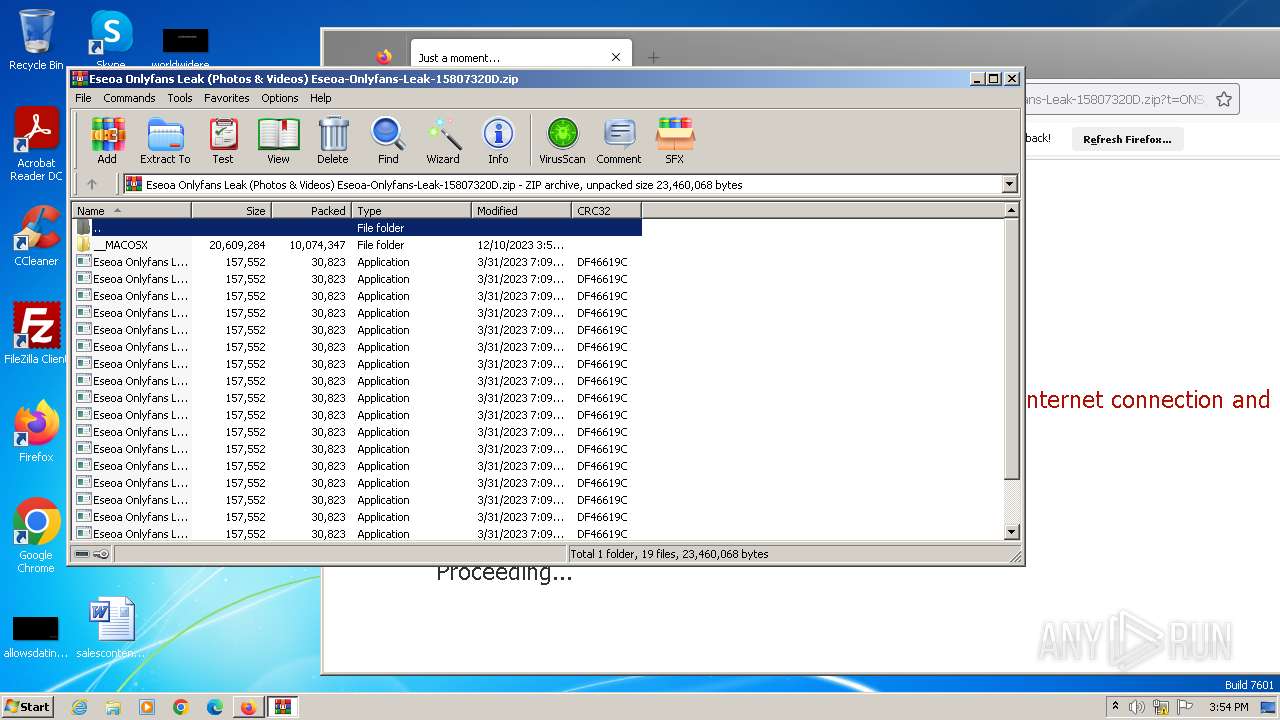
- Eseoa Onlyfans Leak (Photos & Videos) Eseoa-Onlyfans-Leak-1.exe (PID: 3292)
- php.exe (PID: 3444)
- Eseoa Onlyfans Leak (Photos & Videos) Eseoa-Onlyfans-Leak-6.exe (PID: 2092)
- Eseoa Onlyfans Leak (Photos & Videos) Eseoa-Onlyfans-Leak-10.exe (PID: 3368)
- Eseoa Onlyfans Leak (Photos & Videos) Eseoa-Onlyfans-Leak-14.exe (PID: 2392)
- Eseoa Onlyfans Leak (Photos & Videos) Eseoa-Onlyfans-Leak-15.exe (PID: 292)
Run PowerShell with an invisible window
- powershell.exe (PID: 3416)
- powershell.exe (PID: 3888)
- powershell.exe (PID: 2436)
- powershell.exe (PID: 2940)
- powershell.exe (PID: 3484)
SUSPICIOUS
Process drops legitimate windows executable
- php.exe (PID: 3444)
- WinRAR.exe (PID: 3472)
- Eseoa Onlyfans Leak (Photos & Videos) Eseoa-Onlyfans-Leak-1.exe (PID: 3292)
- Eseoa Onlyfans Leak (Photos & Videos) Eseoa-Onlyfans-Leak-6.exe (PID: 2092)
- Eseoa Onlyfans Leak (Photos & Videos) Eseoa-Onlyfans-Leak-10.exe (PID: 3368)
- Eseoa Onlyfans Leak (Photos & Videos) Eseoa-Onlyfans-Leak-14.exe (PID: 2392)
- Eseoa Onlyfans Leak (Photos & Videos) Eseoa-Onlyfans-Leak-15.exe (PID: 292)
The process drops C-runtime libraries
- Eseoa Onlyfans Leak (Photos & Videos) Eseoa-Onlyfans-Leak-1.exe (PID: 3292)
- Eseoa Onlyfans Leak (Photos & Videos) Eseoa-Onlyfans-Leak-6.exe (PID: 2092)
- php.exe (PID: 3444)
- Eseoa Onlyfans Leak (Photos & Videos) Eseoa-Onlyfans-Leak-10.exe (PID: 3368)
- Eseoa Onlyfans Leak (Photos & Videos) Eseoa-Onlyfans-Leak-14.exe (PID: 2392)
- Eseoa Onlyfans Leak (Photos & Videos) Eseoa-Onlyfans-Leak-15.exe (PID: 292)
Starts CMD.EXE for commands execution
- php.exe (PID: 3444)
- cmd.exe (PID: 2504)
- rhc.exe (PID: 2028)
- php.exe (PID: 1604)
- php.exe (PID: 3652)
- rhc.exe (PID: 2980)
- cmd.exe (PID: 2056)
- php.exe (PID: 4064)
- php.exe (PID: 2184)
- rhc.exe (PID: 3356)
- cmd.exe (PID: 3884)
- php.exe (PID: 2240)
- rhc.exe (PID: 1028)
- php.exe (PID: 3484)
- php.exe (PID: 4088)
- cmd.exe (PID: 3684)
- php.exe (PID: 1016)
- php.exe (PID: 3928)
- rhc.exe (PID: 3292)
- cmd.exe (PID: 476)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 4076)
- cmd.exe (PID: 2400)
- cmd.exe (PID: 2932)
- cmd.exe (PID: 2324)
- cmd.exe (PID: 528)
Executing commands from a ".bat" file
- php.exe (PID: 3444)
- rhc.exe (PID: 2028)
- cmd.exe (PID: 2504)
- php.exe (PID: 3652)
- cmd.exe (PID: 2056)
- rhc.exe (PID: 2980)
- rhc.exe (PID: 3356)
- php.exe (PID: 2184)
- cmd.exe (PID: 3884)
- php.exe (PID: 3484)
- cmd.exe (PID: 3684)
- rhc.exe (PID: 1028)
- php.exe (PID: 1016)
- cmd.exe (PID: 476)
- rhc.exe (PID: 3292)
Powershell version downgrade attack
- powershell.exe (PID: 3416)
- powershell.exe (PID: 3872)
- powershell.exe (PID: 1616)
- powershell.exe (PID: 3888)
- powershell.exe (PID: 2436)
- powershell.exe (PID: 1364)
- powershell.exe (PID: 3072)
- powershell.exe (PID: 2940)
- powershell.exe (PID: 3076)
- powershell.exe (PID: 3484)
Application launched itself
- cmd.exe (PID: 2504)
- cmd.exe (PID: 2056)
- cmd.exe (PID: 3884)
- cmd.exe (PID: 3684)
- cmd.exe (PID: 476)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 4076)
- cmd.exe (PID: 2612)
- cmd.exe (PID: 3704)
- cmd.exe (PID: 2400)
- cmd.exe (PID: 2932)
- cmd.exe (PID: 3320)
- cmd.exe (PID: 1628)
- cmd.exe (PID: 2324)
- cmd.exe (PID: 528)
- cmd.exe (PID: 3764)
The process executes via Task Scheduler
- rhc.exe (PID: 2260)
- rhc.exe (PID: 3788)
- rhc.exe (PID: 2092)
- rhc.exe (PID: 2408)
- rhc.exe (PID: 1448)
- rhc.exe (PID: 3796)
Process requests binary or script from the Internet
- php.exe (PID: 1604)
Start notepad (likely ransomware note)
- WinRAR.exe (PID: 3472)
INFO
Application launched itself
- firefox.exe (PID: 2524)
- firefox.exe (PID: 2956)
Checks supported languages
- Eseoa Onlyfans Leak (Photos & Videos) Eseoa-Onlyfans-Leak-1.exe (PID: 3292)
- php.exe (PID: 1604)
- rhc.exe (PID: 2368)
- rhc.exe (PID: 2028)
- php.exe (PID: 916)
- rhc.exe (PID: 2260)
- Eseoa Onlyfans Leak (Photos & Videos) Eseoa-Onlyfans-Leak-6.exe (PID: 2092)
- php.exe (PID: 3652)
- rhc.exe (PID: 860)
- rhc.exe (PID: 2980)
- php.exe (PID: 4064)
- rhc.exe (PID: 3788)
- php.exe (PID: 1816)
- php.exe (PID: 3444)
- Eseoa Onlyfans Leak (Photos & Videos) Eseoa-Onlyfans-Leak-10.exe (PID: 3368)
- php.exe (PID: 2184)
- rhc.exe (PID: 3356)
- rhc.exe (PID: 1904)
- php.exe (PID: 2240)
- rhc.exe (PID: 2092)
- php.exe (PID: 3652)
- Eseoa Onlyfans Leak (Photos & Videos) Eseoa-Onlyfans-Leak-14.exe (PID: 2392)
- php.exe (PID: 3484)
- rhc.exe (PID: 1528)
- rhc.exe (PID: 1028)
- php.exe (PID: 4088)
- rhc.exe (PID: 2408)
- php.exe (PID: 1016)
- php.exe (PID: 3928)
- rhc.exe (PID: 3176)
- rhc.exe (PID: 3292)
- php.exe (PID: 2924)
- Eseoa Onlyfans Leak (Photos & Videos) Eseoa-Onlyfans-Leak-15.exe (PID: 292)
- rhc.exe (PID: 1448)
- rhc.exe (PID: 3796)
- php.exe (PID: 3064)
- php.exe (PID: 1928)
The process uses the downloaded file
- firefox.exe (PID: 2956)
- WinRAR.exe (PID: 3472)
Reads the computer name
- Eseoa Onlyfans Leak (Photos & Videos) Eseoa-Onlyfans-Leak-1.exe (PID: 3292)
- php.exe (PID: 3444)
- php.exe (PID: 1604)
- Eseoa Onlyfans Leak (Photos & Videos) Eseoa-Onlyfans-Leak-6.exe (PID: 2092)
- php.exe (PID: 916)
- php.exe (PID: 3652)
- php.exe (PID: 4064)
- php.exe (PID: 1816)
- Eseoa Onlyfans Leak (Photos & Videos) Eseoa-Onlyfans-Leak-10.exe (PID: 3368)
- php.exe (PID: 2184)
- php.exe (PID: 2240)
- php.exe (PID: 3652)
- Eseoa Onlyfans Leak (Photos & Videos) Eseoa-Onlyfans-Leak-14.exe (PID: 2392)
- php.exe (PID: 3484)
- php.exe (PID: 4088)
- Eseoa Onlyfans Leak (Photos & Videos) Eseoa-Onlyfans-Leak-15.exe (PID: 292)
- php.exe (PID: 1016)
- php.exe (PID: 2924)
- php.exe (PID: 3928)
- php.exe (PID: 3064)
- php.exe (PID: 1928)
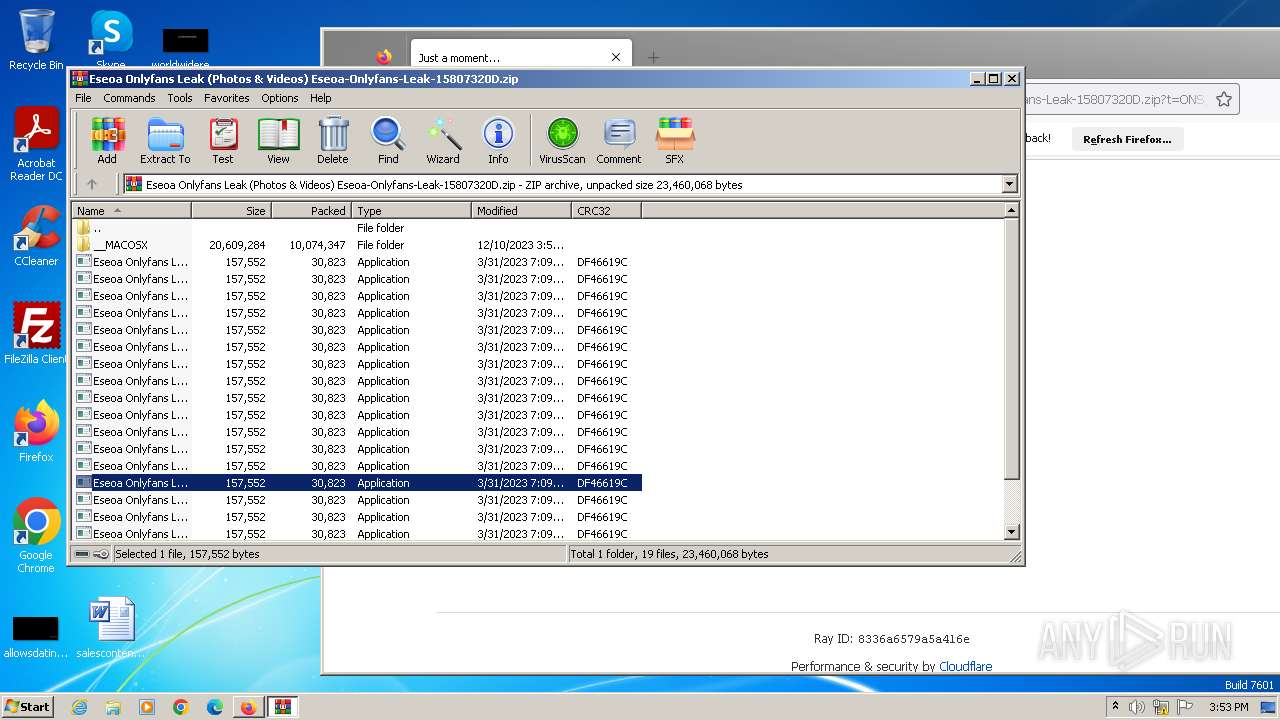
Manual execution by a user
- WinRAR.exe (PID: 3472)
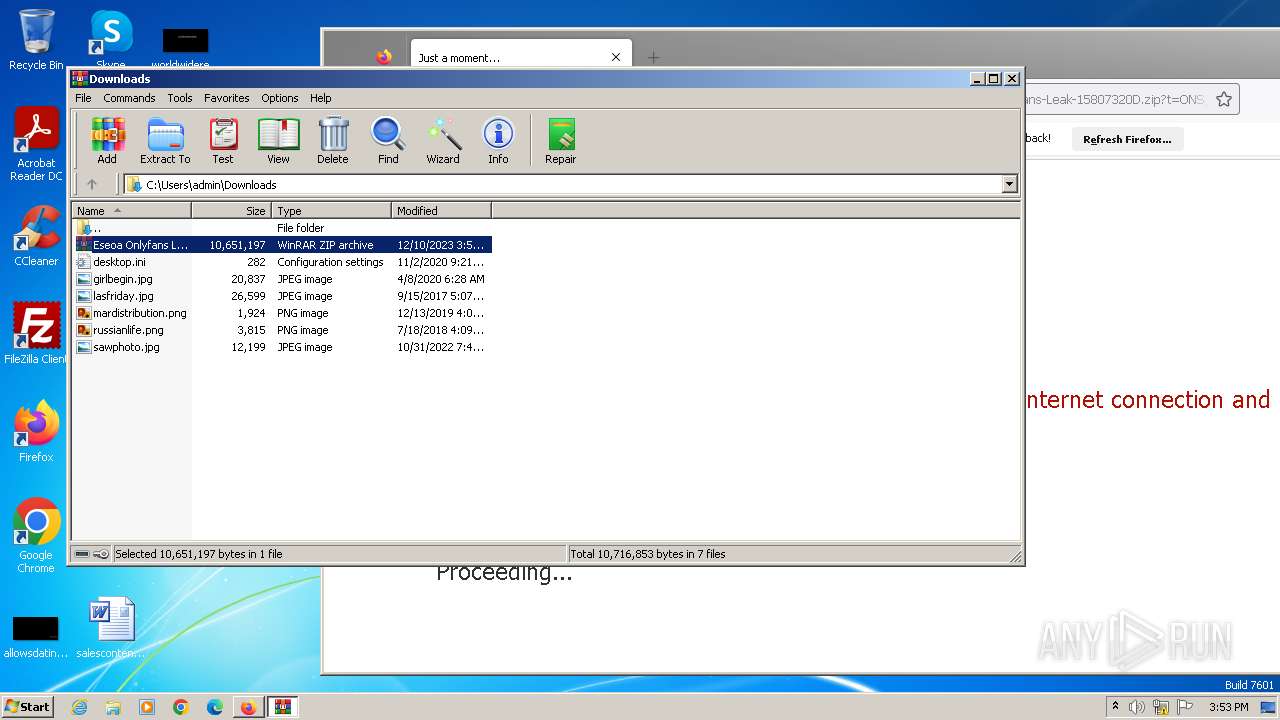
Creates files in the program directory
- Eseoa Onlyfans Leak (Photos & Videos) Eseoa-Onlyfans-Leak-1.exe (PID: 3292)
- php.exe (PID: 1604)
- Eseoa Onlyfans Leak (Photos & Videos) Eseoa-Onlyfans-Leak-6.exe (PID: 2092)
- php.exe (PID: 3444)
- Eseoa Onlyfans Leak (Photos & Videos) Eseoa-Onlyfans-Leak-10.exe (PID: 3368)
- Eseoa Onlyfans Leak (Photos & Videos) Eseoa-Onlyfans-Leak-14.exe (PID: 2392)
- Eseoa Onlyfans Leak (Photos & Videos) Eseoa-Onlyfans-Leak-15.exe (PID: 292)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3472)
- firefox.exe (PID: 2956)
Reads the machine GUID from the registry
- php.exe (PID: 916)
- php.exe (PID: 3652)
- php.exe (PID: 2924)
- php.exe (PID: 3064)
- php.exe (PID: 1816)
- php.exe (PID: 1928)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
183
Monitored processes
111
Malicious processes
54
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
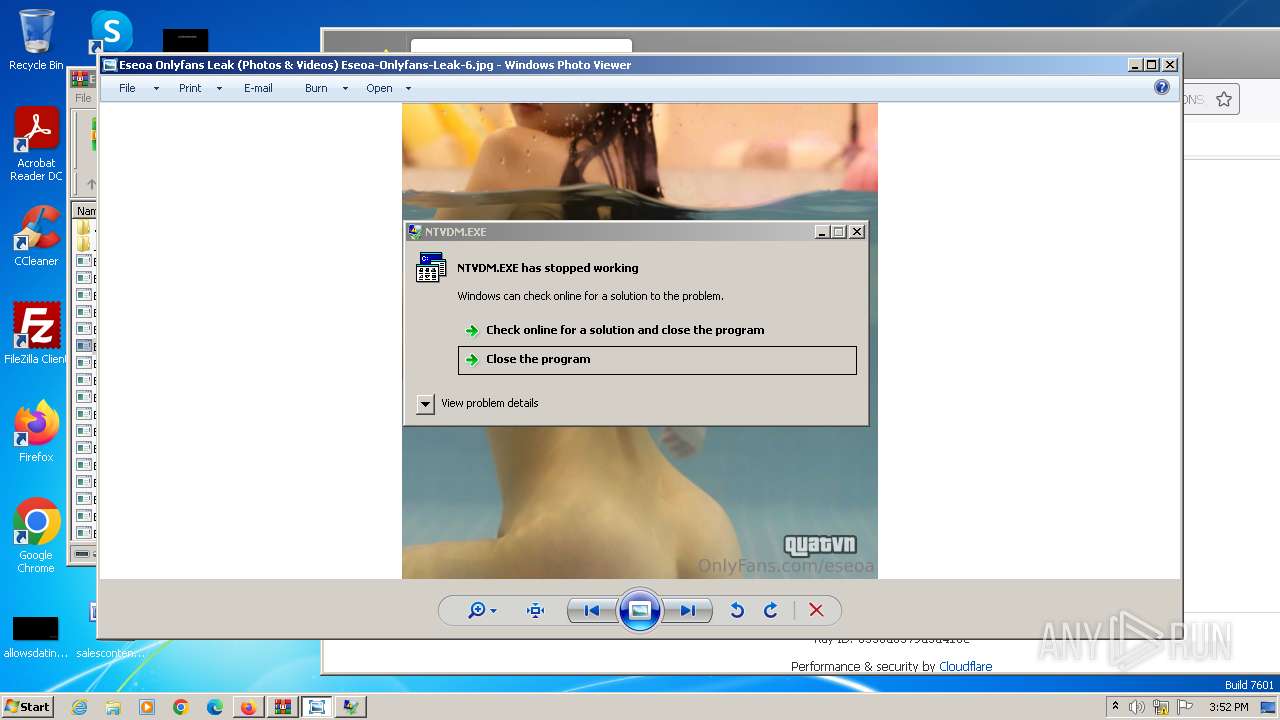
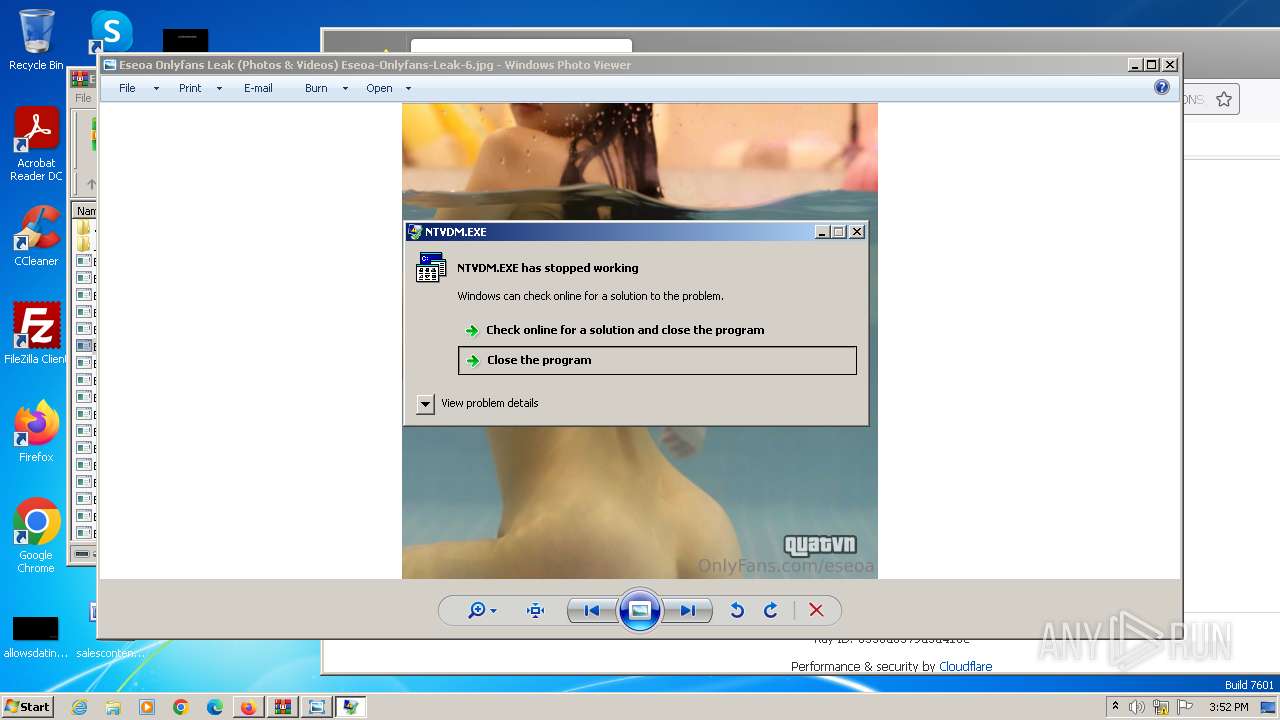
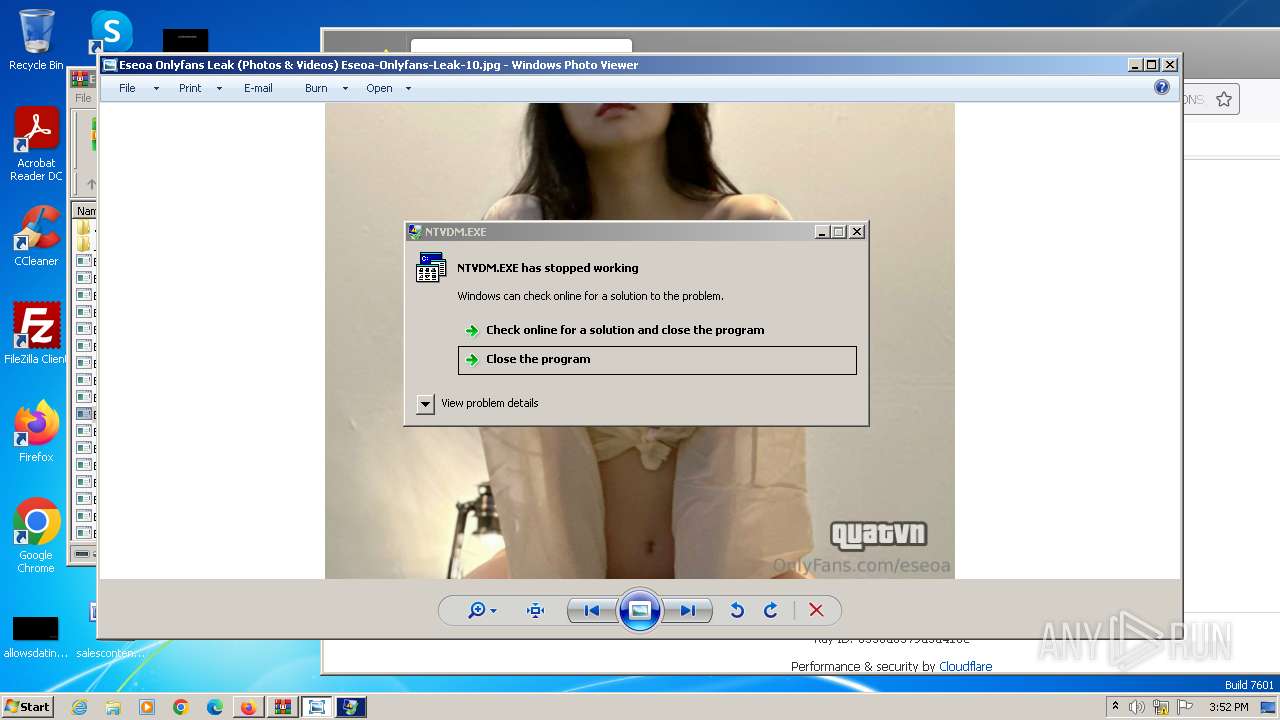
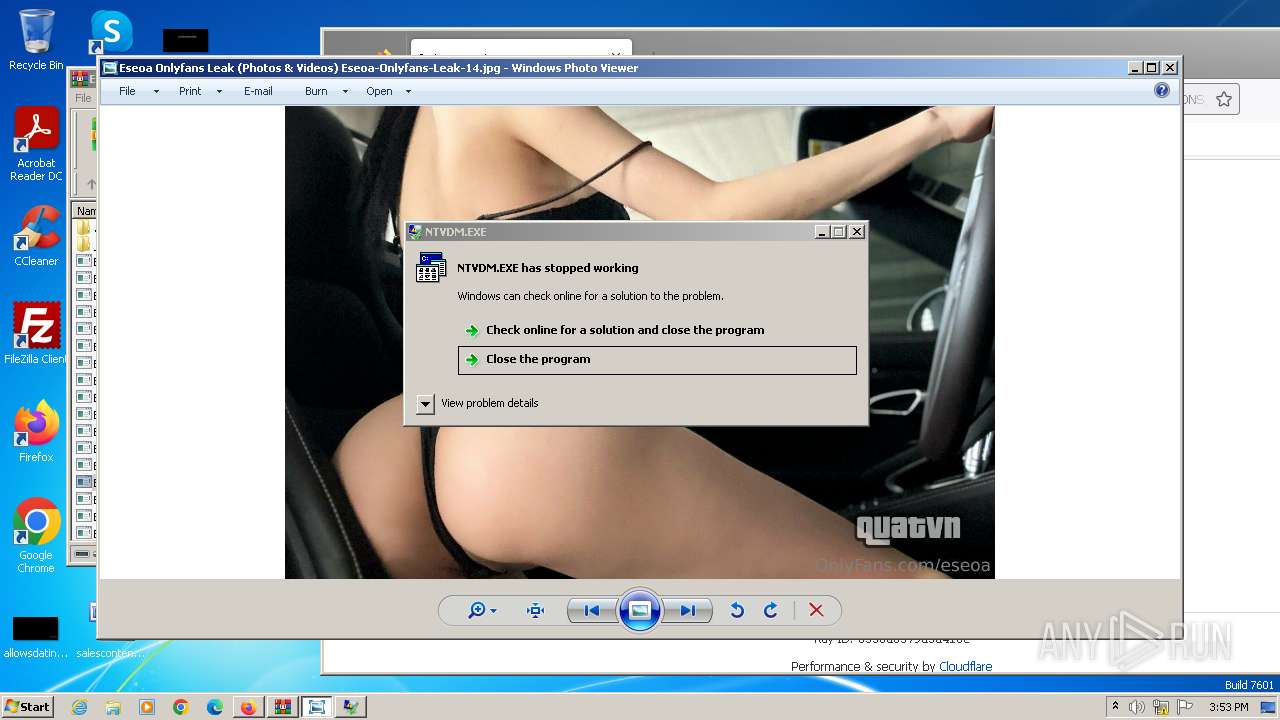
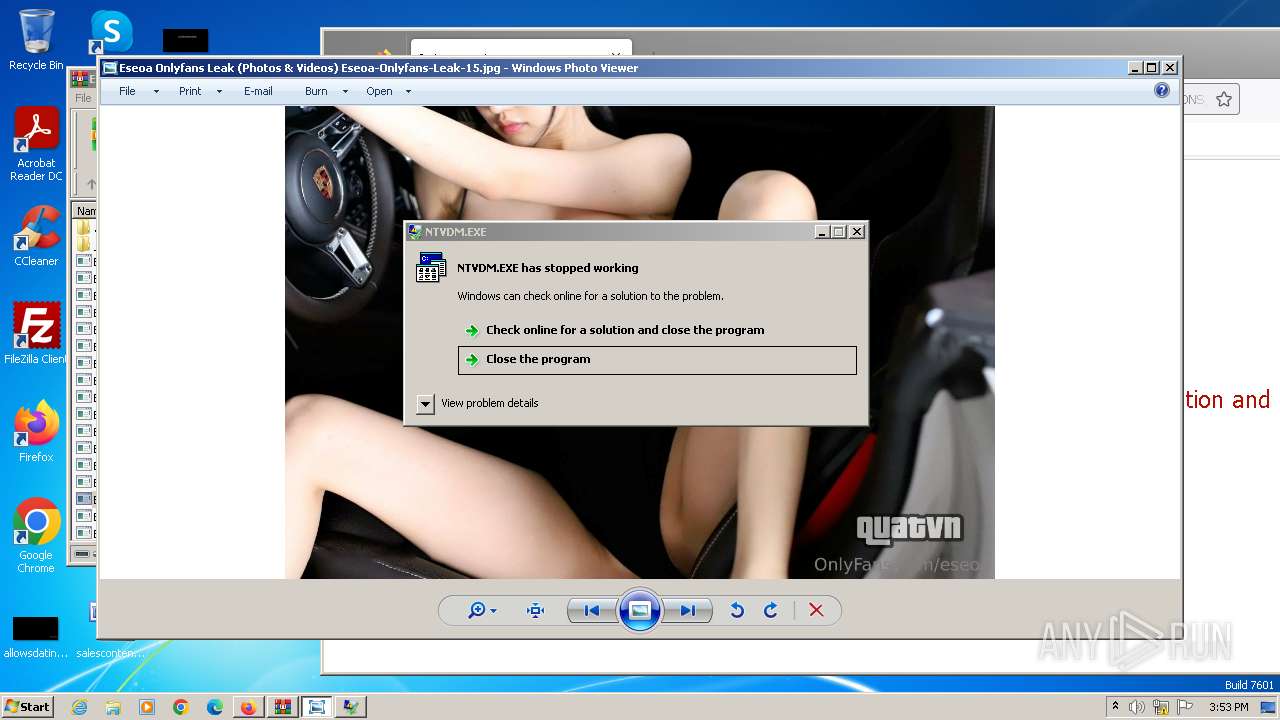
| 276 | "C:\Windows\system32\ntvdm.exe" | C:\Windows\System32\ntvdm.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: NTVDM.EXE Exit code: 3221225477 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 292 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="2956.8.1726965377\1081090428" -childID 7 -isForBrowser -prefsHandle 4584 -prefMapHandle 3384 -prefsLen 29313 -prefMapSize 244195 -jsInitHandle 920 -jsInitLen 240908 -parentBuildID 20230710165010 -appDir "C:\Program Files\Mozilla Firefox\browser" - {b593bb7e-bced-4041-b890-ce9191ae2dbf} 2956 "\\.\pipe\gecko-crash-server-pipe.2956" 4596 229d6110 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 115.0.2 Modules
| |||||||||||||||
| 292 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3472.9886\Eseoa Onlyfans Leak (Photos & Videos) Eseoa-Onlyfans-Leak-15.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3472.9886\Eseoa Onlyfans Leak (Photos & Videos) Eseoa-Onlyfans-Leak-15.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Western Digital Technologies, Inc. Integrity Level: MEDIUM Description: WD Sync Service Exit code: 0 Version: 1.0.6698.8728 Modules
| |||||||||||||||
| 476 | cmd.exe /c ""C:\ProgramData\CloudContent\rhc.exe" "C:\ProgramData\CloudContent\php.exe" "C:\ProgramData\CloudContent\include.php"" | C:\Windows\System32\cmd.exe | — | php.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 476 | C:\Windows\system32\cmd.exe /c ""C:\ProgramData\install.bat"" | C:\Windows\System32\cmd.exe | — | rhc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 528 | C:\Windows\system32\cmd.exe /K "C:\ProgramData\install.bat" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 588 | cmd.exe /c ""C:\ProgramData\CloudContent\rhc.exe" "C:\ProgramData\install.bat"" | C:\Windows\System32\cmd.exe | — | php.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 756 | cmd.exe /c start "" "C:\ProgramData\ContentData\img\Eseoa Onlyfans Leak (Photos & Videos) Eseoa-Onlyfans-Leak-6.jpg" | C:\Windows\System32\cmd.exe | — | php.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 860 | "C:\ProgramData\CloudContent\rhc.exe" "C:\ProgramData\CloudContent\php.exe" "C:\ProgramData\CloudContent\include.php" | C:\ProgramData\CloudContent\rhc.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 916 | php.exe index.php | C:\ProgramData\CloudContent\php.exe | rhc.exe | ||||||||||||
User: admin Company: The PHP Group Integrity Level: MEDIUM Description: CLI Exit code: 0 Version: 5.6.9 Modules
| |||||||||||||||
Total events
37 830
Read events
37 129
Write events
695
Delete events
6
Modification events
| (PID) Process: | (2524) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Launcher |
Value: 2166C0A101000000 | |||
| (PID) Process: | (2956) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Browser |
Value: 044CC1A101000000 | |||
| (PID) Process: | (2956) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Telemetry |
Value: 0 | |||
| (PID) Process: | (2956) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (2956) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\PreXULSkeletonUISettings |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Theme |
Value: 1 | |||
| (PID) Process: | (2956) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\PreXULSkeletonUISettings |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Enabled |
Value: 1 | |||
| (PID) Process: | (2956) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|DisableTelemetry |
Value: 1 | |||
| (PID) Process: | (2956) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|DisableDefaultBrowserAgent |
Value: 0 | |||
| (PID) Process: | (2956) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|SetDefaultBrowserUserChoice |
Value: 1 | |||
| (PID) Process: | (2956) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|AppLastRunTime |
Value: D14E5F3C23B0D901 | |||
Executable files
303
Suspicious files
191
Text files
424
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2956 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\sessionCheckpoints.json | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 2956 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\urlCache-current.bin | binary | |
MD5:B7A3C61D0C144CC5E166B1E769CA8F8C | SHA256:7FADCB77FFACA6B9E9F15C6F1CD3AAD4C20DCD90FA92429A627A3A7110CA2644 | |||
| 2956 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\1657114595AmcateirvtiSty.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 2956 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\prefs-1.js | text | |
MD5:B1873D3D2D6060F048F98150DEFF0F4D | SHA256:A2AFCEB1BFA47504A2091E92D9784F74F7176F8F7B82E76FBEA14F55B284E448 | |||
| 2956 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\prefs.js | text | |
MD5:B1873D3D2D6060F048F98150DEFF0F4D | SHA256:A2AFCEB1BFA47504A2091E92D9784F74F7176F8F7B82E76FBEA14F55B284E448 | |||
| 2956 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\1451318868ntouromlalnodry--epcr.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 2956 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\1657114595AmcateirvtiSty.sqlite-wal | — | |
MD5:— | SHA256:— | |||
| 2956 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\2918063365piupsah.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 2956 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 2956 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\scriptCache-new.bin | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
52
TCP/UDP connections
110
DNS requests
250
Threats
19
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2956 | firefox.exe | POST | 200 | 18.238.30.218:80 | http://ocsp.r2m02.amazontrust.com/ | unknown | binary | 471 b | unknown |
2956 | firefox.exe | POST | 200 | 23.55.161.194:80 | http://r3.o.lencr.org/ | unknown | binary | 503 b | unknown |
2956 | firefox.exe | POST | 200 | 23.55.161.194:80 | http://r3.o.lencr.org/ | unknown | binary | 503 b | unknown |
2956 | firefox.exe | GET | 200 | 188.114.97.3:80 | http://videocallgirl.top/cdn-cgi/styles/challenges.css | unknown | text | 2.56 Kb | unknown |
2956 | firefox.exe | POST | 200 | 23.55.161.194:80 | http://r3.o.lencr.org/ | unknown | binary | 503 b | unknown |
2956 | firefox.exe | GET | 404 | 188.114.97.3:80 | http://videocallgirl.top/favicon.ico | unknown | html | 1.00 Kb | unknown |
2956 | firefox.exe | POST | 200 | 142.250.203.195:80 | http://ocsp.pki.goog/gts1c3 | unknown | binary | 471 b | unknown |
2956 | firefox.exe | GET | 200 | 188.114.97.3:80 | http://videocallgirl.top/cdn-cgi/challenge-platform/h/b/orchestrate/chl_page/v1?ray=8336a3f759d37273 | unknown | text | 54.3 Kb | unknown |
2956 | firefox.exe | GET | 404 | 188.114.97.3:80 | http://videocallgirl.top/favicon.ico | unknown | html | 1.00 Kb | unknown |
2956 | firefox.exe | POST | 200 | 23.55.161.194:80 | http://r3.o.lencr.org/ | unknown | binary | 503 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2956 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2956 | firefox.exe | 188.114.97.3:80 | videocallgirl.top | CLOUDFLARENET | NL | unknown |
2956 | firefox.exe | 23.23.117.73:443 | spocs.getpocket.com | AMAZON-AES | US | unknown |
2956 | firefox.exe | 34.117.237.239:443 | contile.services.mozilla.com | GOOGLE-CLOUD-PLATFORM | US | unknown |
2956 | firefox.exe | 34.149.100.209:443 | firefox.settings.services.mozilla.com | GOOGLE | US | unknown |
2956 | firefox.exe | 142.251.36.170:443 | safebrowsing.googleapis.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
videocallgirl.top |
| unknown |
detectportal.firefox.com |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
spocs.getpocket.com |
| shared |
firefox.settings.services.mozilla.com |
| whitelisted |
safebrowsing.googleapis.com |
| whitelisted |
push.services.mozilla.com |
| whitelisted |
example.org |
| whitelisted |
ipv4only.arpa |
| whitelisted |
r3.o.lencr.org |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
2956 | firefox.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |
2956 | firefox.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
2956 | firefox.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
1080 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
2956 | firefox.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |
1080 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
2956 | firefox.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |
2956 | firefox.exe | Generic Protocol Command Decode | SURICATA HTTP gzip decompression failed |
2956 | firefox.exe | Generic Protocol Command Decode | SURICATA HTTP invalid response chunk len |