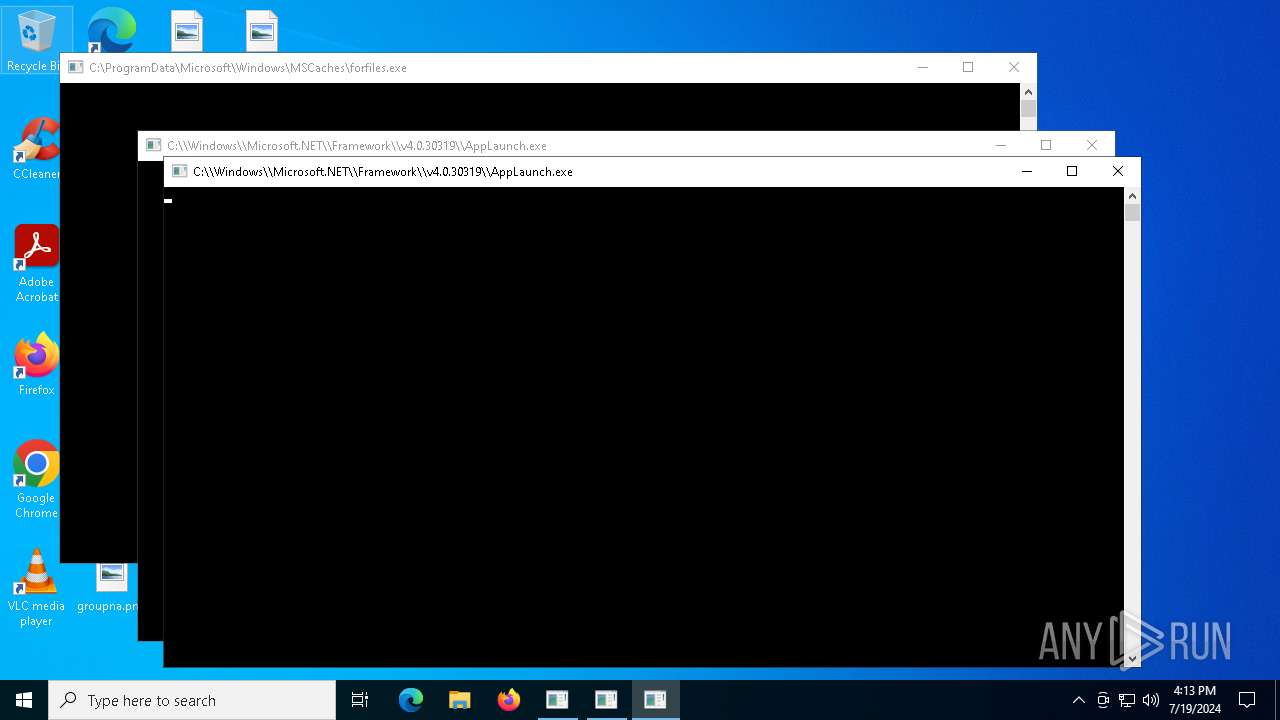
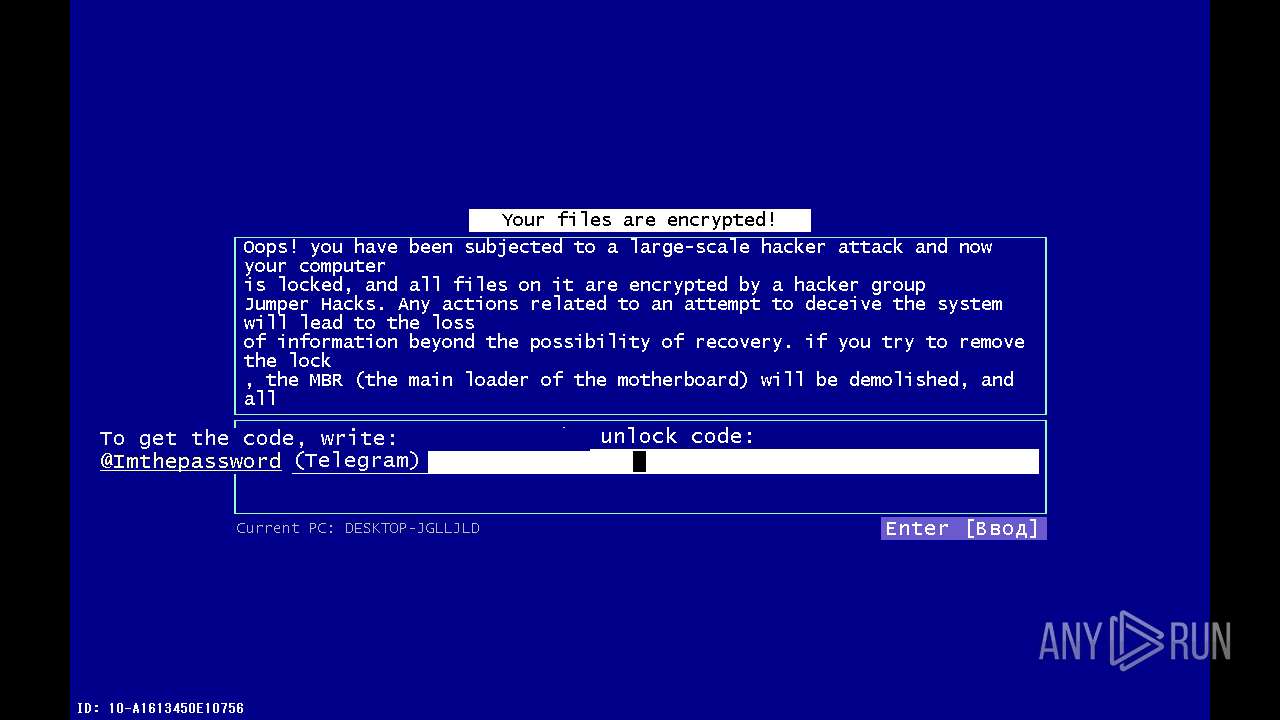
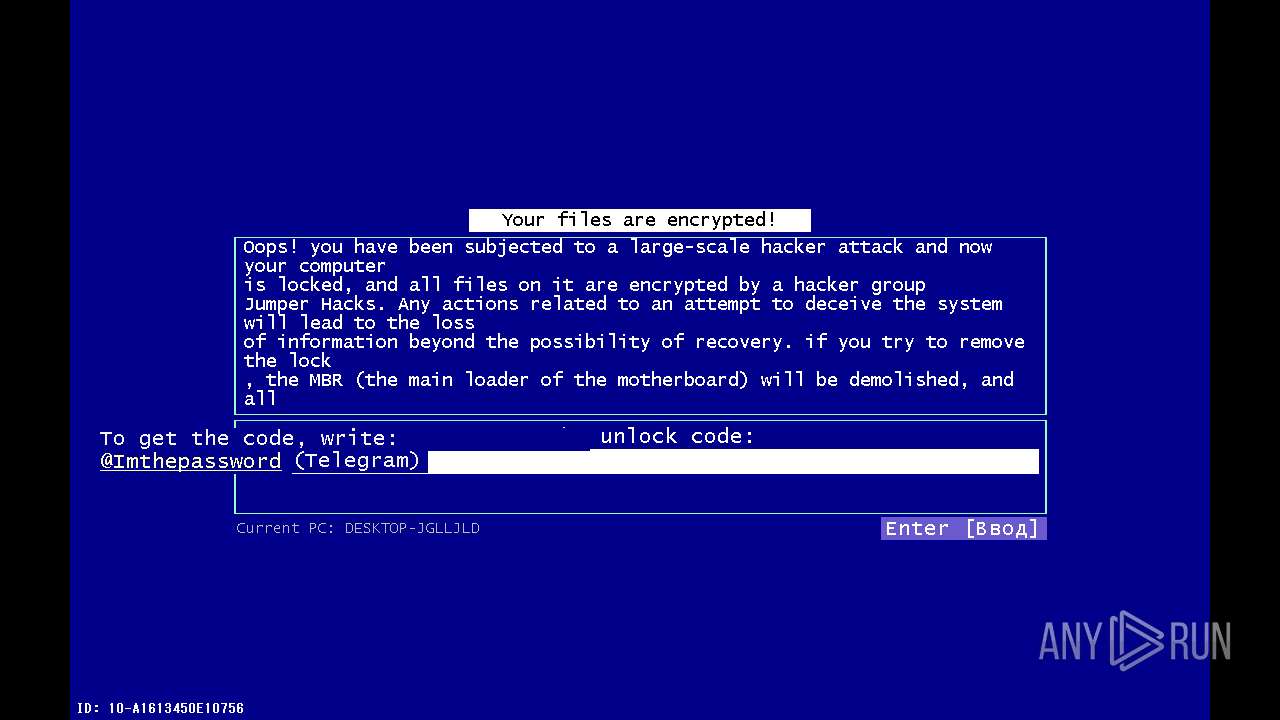
| File name: | 89ffb715e0a02eb089269f055f3104aecf648cd88366bf3ed49fb318ee257588.exe |
| Full analysis: | https://app.any.run/tasks/9235e593-226a-45a4-8b74-da5a779b3823 |
| Verdict: | Malicious activity |
| Analysis date: | July 19, 2024, 16:13:22 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (GUI) x86-64 (stripped to external PDB), for MS Windows |
| MD5: | 177DBA5455E57AFE9DA6CFA0DDA3D61D |
| SHA1: | 96A4C6B60F58313FB18B6546871006A174D207FF |
| SHA256: | 89FFB715E0A02EB089269F055F3104AECF648CD88366BF3ED49FB318EE257588 |
| SSDEEP: | 98304:nerFpgFMcnWWGME6XVgjsaXBaIyKmw3bVA/cAkrqYjGnE2EOOBqdLIikYtLvfFBQ:nlEVH |
MALICIOUS
Drops the executable file immediately after the start
- 89ffb715e0a02eb089269f055f3104aecf648cd88366bf3ed49fb318ee257588.exe (PID: 4496)
Changes the autorun value in the registry
- AppLaunch.exe (PID: 3020)
Changes the login/logoff helper path in the registry
- AppLaunch.exe (PID: 3020)
SUSPICIOUS
Executable content was dropped or overwritten
- 89ffb715e0a02eb089269f055f3104aecf648cd88366bf3ed49fb318ee257588.exe (PID: 4496)
Process drops legitimate windows executable
- 89ffb715e0a02eb089269f055f3104aecf648cd88366bf3ed49fb318ee257588.exe (PID: 4496)
Reads security settings of Internet Explorer
- 89ffb715e0a02eb089269f055f3104aecf648cd88366bf3ed49fb318ee257588.exe (PID: 4496)
The process checks if it is being run in the virtual environment
- 89ffb715e0a02eb089269f055f3104aecf648cd88366bf3ed49fb318ee257588.exe (PID: 4496)
The process creates files with name similar to system file names
- 89ffb715e0a02eb089269f055f3104aecf648cd88366bf3ed49fb318ee257588.exe (PID: 4496)
There is functionality for VM detection (VMWare)
- 89ffb715e0a02eb089269f055f3104aecf648cd88366bf3ed49fb318ee257588.exe (PID: 4496)
Application launched itself
- AppLaunch.exe (PID: 7852)
- AppLaunch.exe (PID: 2252)
- AppLaunch.exe (PID: 6668)
- AppLaunch.exe (PID: 1832)
- AppLaunch.exe (PID: 8028)
- AppLaunch.exe (PID: 1300)
- AppLaunch.exe (PID: 1580)
- AppLaunch.exe (PID: 5612)
- AppLaunch.exe (PID: 6948)
- AppLaunch.exe (PID: 6324)
- AppLaunch.exe (PID: 3724)
- AppLaunch.exe (PID: 7588)
- AppLaunch.exe (PID: 6616)
Executes application which crashes
- cmd.exe (PID: 7384)
- AppLaunch.exe (PID: 7852)
- cmd.exe (PID: 7028)
- AppLaunch.exe (PID: 2252)
- cmd.exe (PID: 7364)
- AppLaunch.exe (PID: 6668)
- cmd.exe (PID: 7588)
- AppLaunch.exe (PID: 1832)
- cmd.exe (PID: 7236)
- AppLaunch.exe (PID: 1300)
- AppLaunch.exe (PID: 1580)
- cmd.exe (PID: 6288)
- cmd.exe (PID: 972)
- AppLaunch.exe (PID: 8028)
- cmd.exe (PID: 5920)
- AppLaunch.exe (PID: 5612)
- cmd.exe (PID: 6608)
- AppLaunch.exe (PID: 6948)
- cmd.exe (PID: 3556)
- AppLaunch.exe (PID: 6324)
- cmd.exe (PID: 1068)
- AppLaunch.exe (PID: 7588)
- cmd.exe (PID: 3328)
- AppLaunch.exe (PID: 3724)
- cmd.exe (PID: 1580)
- AppLaunch.exe (PID: 6616)
Uses TASKKILL.EXE to kill process
- AppLaunch.exe (PID: 3020)
Starts CMD.EXE for commands execution
- AppLaunch.exe (PID: 3020)
Likely accesses (executes) a file from the Public directory
- cmd.exe (PID: 4568)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 6916)
- cmd.exe (PID: 3868)
- cmd.exe (PID: 4568)
- cmd.exe (PID: 4612)
- cmd.exe (PID: 7796)
INFO
Checks supported languages
- forfiles.exe (PID: 7228)
- 89ffb715e0a02eb089269f055f3104aecf648cd88366bf3ed49fb318ee257588.exe (PID: 4496)
- AppLaunch.exe (PID: 7852)
- AppLaunch.exe (PID: 7160)
- cmd.exe (PID: 7028)
- AppLaunch.exe (PID: 2252)
- AppLaunch.exe (PID: 3020)
- cmd.exe (PID: 7384)
- AppLaunch.exe (PID: 2788)
- AppLaunch.exe (PID: 6668)
- cmd.exe (PID: 7364)
- cmd.exe (PID: 7588)
- cmd.exe (PID: 7236)
- AppLaunch.exe (PID: 1832)
- AppLaunch.exe (PID: 6404)
- AppLaunch.exe (PID: 7132)
- cmd.exe (PID: 972)
- AppLaunch.exe (PID: 8028)
- AppLaunch.exe (PID: 6404)
- AppLaunch.exe (PID: 1300)
- cmd.exe (PID: 6288)
- AppLaunch.exe (PID: 1580)
- AppLaunch.exe (PID: 8140)
- cmd.exe (PID: 5920)
- AppLaunch.exe (PID: 5612)
- AppLaunch.exe (PID: 508)
- cmd.exe (PID: 3556)
- AppLaunch.exe (PID: 8176)
- AppLaunch.exe (PID: 6948)
- AppLaunch.exe (PID: 6324)
- AppLaunch.exe (PID: 1940)
- cmd.exe (PID: 1068)
- cmd.exe (PID: 6608)
- AppLaunch.exe (PID: 3724)
- cmd.exe (PID: 3328)
- AppLaunch.exe (PID: 7792)
- AppLaunch.exe (PID: 7588)
- AppLaunch.exe (PID: 5444)
- AppLaunch.exe (PID: 6616)
- AppLaunch.exe (PID: 4968)
- cmd.exe (PID: 1580)
Reads the computer name
- 89ffb715e0a02eb089269f055f3104aecf648cd88366bf3ed49fb318ee257588.exe (PID: 4496)
- AppLaunch.exe (PID: 3020)
- AppLaunch.exe (PID: 7160)
- AppLaunch.exe (PID: 2788)
- AppLaunch.exe (PID: 6404)
- AppLaunch.exe (PID: 7132)
- AppLaunch.exe (PID: 6404)
- AppLaunch.exe (PID: 8140)
- AppLaunch.exe (PID: 508)
- AppLaunch.exe (PID: 8176)
- AppLaunch.exe (PID: 1940)
- AppLaunch.exe (PID: 5444)
- AppLaunch.exe (PID: 7792)
- AppLaunch.exe (PID: 4968)
Creates files in the program directory
- 89ffb715e0a02eb089269f055f3104aecf648cd88366bf3ed49fb318ee257588.exe (PID: 4496)
Reads the machine GUID from the registry
- AppLaunch.exe (PID: 3020)
- AppLaunch.exe (PID: 7160)
- AppLaunch.exe (PID: 2788)
- AppLaunch.exe (PID: 6404)
- AppLaunch.exe (PID: 7132)
- AppLaunch.exe (PID: 8140)
- AppLaunch.exe (PID: 6404)
- AppLaunch.exe (PID: 508)
- AppLaunch.exe (PID: 8176)
- AppLaunch.exe (PID: 1940)
- AppLaunch.exe (PID: 5444)
- AppLaunch.exe (PID: 7792)
- AppLaunch.exe (PID: 4968)
Creates files or folders in the user directory
- WerFault.exe (PID: 5896)
- WerFault.exe (PID: 7480)
- WerFault.exe (PID: 7380)
- WerFault.exe (PID: 2140)
- WerFault.exe (PID: 5468)
- WerFault.exe (PID: 5116)
- WerFault.exe (PID: 5820)
- WerFault.exe (PID: 8152)
- WerFault.exe (PID: 5408)
- WerFault.exe (PID: 6512)
- WerFault.exe (PID: 7616)
- WerFault.exe (PID: 568)
- WerFault.exe (PID: 1340)
- WerFault.exe (PID: 6292)
- WerFault.exe (PID: 7588)
- WerFault.exe (PID: 1652)
- WerFault.exe (PID: 4092)
- WerFault.exe (PID: 7400)
- WerFault.exe (PID: 6264)
- WerFault.exe (PID: 4804)
- WerFault.exe (PID: 2788)
- WerFault.exe (PID: 2028)
- WerFault.exe (PID: 5004)
- WerFault.exe (PID: 5112)
- WerFault.exe (PID: 2060)
- WerFault.exe (PID: 6204)
- WerFault.exe (PID: 6356)
- WerFault.exe (PID: 3688)
- WerFault.exe (PID: 7180)
- WerFault.exe (PID: 5400)
- WerFault.exe (PID: 5420)
- WerFault.exe (PID: 6972)
- WerFault.exe (PID: 5732)
- WerFault.exe (PID: 6880)
- WerFault.exe (PID: 4328)
Create files in a temporary directory
- AppLaunch.exe (PID: 3020)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.2) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:07:18 15:15:41+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Large address aware, No debug |
| PEType: | PE32+ |
| LinkerVersion: | 2.3 |
| CodeSize: | 3346432 |
| InitializedDataSize: | 106496 |
| UninitializedDataSize: | 4251648 |
| EntryPoint: | 0x73f9c0 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Unknown (0) |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | English (British) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | NoStopMedia |
| FileVersion: | 1.0.0.0 |
| FileDescription: | Launcher |
| InternalName: | trenininmiba |
| LegalCopyright: | Copyright © NoStopMedia. All rights reserved. |
| LegalTrademarks: | - |
| OriginalFileName: | trenininmiba.exe |
| ProductName: | Launcher |
| ProductVersion: | 1.0.0.0 |
Total processes
294
Monitored processes
119
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 508 | "C:\\Windows\\Microsoft.NET\\Framework\\v4.0.30319\\AppLaunch.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\AppLaunch.exe | — | AppLaunch.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft .NET ClickOnce Launch Utility Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 568 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 1832 -s 632 | C:\Windows\SysWOW64\WerFault.exe | — | AppLaunch.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 972 | /c echo "groupna.png" | C:\ProgramData\Microsoft\Windows\MSCaches\cmd.exe | forfiles.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 3221225477 Modules
| |||||||||||||||
| 1068 | /c echo "strongfamilies.rtf" | C:\ProgramData\Microsoft\Windows\MSCaches\cmd.exe | forfiles.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 3221225477 Modules
| |||||||||||||||
| 1164 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | AppLaunch.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1300 | "C:\\Windows\\Microsoft.NET\\Framework\\v4.0.30319\\AppLaunch.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\AppLaunch.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft .NET ClickOnce Launch Utility Exit code: 3221225477 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 1340 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 7236 -s 524 | C:\Windows\SysWOW64\WerFault.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1348 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | AppLaunch.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1540 | "C:\Users\admin\Desktop\89ffb715e0a02eb089269f055f3104aecf648cd88366bf3ed49fb318ee257588.exe" | C:\Users\admin\Desktop\89ffb715e0a02eb089269f055f3104aecf648cd88366bf3ed49fb318ee257588.exe | — | explorer.exe | |||||||||||
User: admin Company: NoStopMedia Integrity Level: MEDIUM Description: Launcher Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1580 | "C:\\Windows\\Microsoft.NET\\Framework\\v4.0.30319\\AppLaunch.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\AppLaunch.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft .NET ClickOnce Launch Utility Exit code: 3221225477 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
Total events
91 879
Read events
91 577
Write events
185
Delete events
117
Modification events
| (PID) Process: | (7380) WerFault.exe | Key: | \REGISTRY\A\{19f6146b-f670-b4e1-4693-11b37f5b5c5c}\Root\InventoryApplicationFile |
| Operation: | write | Name: | WritePermissionsCheck |
Value: 1 | |||
| (PID) Process: | (7380) WerFault.exe | Key: | \REGISTRY\A\{19f6146b-f670-b4e1-4693-11b37f5b5c5c}\Root\InventoryApplicationFile\PermissionsCheckTestKey |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (7480) WerFault.exe | Key: | \REGISTRY\A\{19f6146b-f670-b4e1-4693-11b37f5b5c5c}\Root\InventoryApplicationFile |
| Operation: | write | Name: | WritePermissionsCheck |
Value: 1 | |||
| (PID) Process: | (7480) WerFault.exe | Key: | \REGISTRY\A\{19f6146b-f670-b4e1-4693-11b37f5b5c5c}\Root\InventoryApplicationFile\PermissionsCheckTestKey |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (7380) WerFault.exe | Key: | \REGISTRY\A\{19f6146b-f670-b4e1-4693-11b37f5b5c5c}\Root\InventoryApplicationFile\applaunch.exe|7127527a8f617d48 |
| Operation: | write | Name: | ProgramId |
Value: 0000f519feec486de87ed73cb92d3cac802400000000 | |||
| (PID) Process: | (7380) WerFault.exe | Key: | \REGISTRY\A\{19f6146b-f670-b4e1-4693-11b37f5b5c5c}\Root\InventoryApplicationFile\applaunch.exe|7127527a8f617d48 |
| Operation: | write | Name: | FileId |
Value: 0000fd08e9a06fe2897850095ed293f90c77489a08f7 | |||
| (PID) Process: | (7380) WerFault.exe | Key: | \REGISTRY\A\{19f6146b-f670-b4e1-4693-11b37f5b5c5c}\Root\InventoryApplicationFile\applaunch.exe|7127527a8f617d48 |
| Operation: | write | Name: | LowerCaseLongPath |
Value: c:\windows\microsoft.net\framework\v4.0.30319\applaunch.exe | |||
| (PID) Process: | (7380) WerFault.exe | Key: | \REGISTRY\A\{19f6146b-f670-b4e1-4693-11b37f5b5c5c}\Root\InventoryApplicationFile\applaunch.exe|7127527a8f617d48 |
| Operation: | write | Name: | LongPathHash |
Value: applaunch.exe|7127527a8f617d48 | |||
| (PID) Process: | (7380) WerFault.exe | Key: | \REGISTRY\A\{19f6146b-f670-b4e1-4693-11b37f5b5c5c}\Root\InventoryApplicationFile\applaunch.exe|7127527a8f617d48 |
| Operation: | write | Name: | Name |
Value: AppLaunch.exe | |||
| (PID) Process: | (7380) WerFault.exe | Key: | \REGISTRY\A\{19f6146b-f670-b4e1-4693-11b37f5b5c5c}\Root\InventoryApplicationFile\applaunch.exe|7127527a8f617d48 |
| Operation: | write | Name: | OriginalFileName |
Value: applaunch.exe | |||
Executable files
4
Suspicious files
69
Text files
82
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7480 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_cmd.exe_a62847f525d85c16db81bd0e7ef97a412ff56b_2076538d_f3c885e5-edef-426a-9d36-5528b25aff64\Report.wer | — | |
MD5:— | SHA256:— | |||
| 7380 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_AppLaunch.exe_e7da30cf5d9744fbce7b9206b9c58a4383a2cb8_e872a7f5_a60ffbab-63a4-485a-af00-b8a7ef15ff8b\Report.wer | — | |
MD5:— | SHA256:— | |||
| 5896 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_AppLaunch.exe_e53256f71dfa44eaf6293a32c34cec881a4cbc_e872a7f5_498e470e-b39f-48ae-b226-40518f397086\Report.wer | — | |
MD5:— | SHA256:— | |||
| 2140 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_cmd.exe_a62847f525d85c16db81bd0e7ef97a412ff56b_2076538d_49927bf0-0345-4c56-9408-c4416e30b1c6\Report.wer | — | |
MD5:— | SHA256:— | |||
| 7480 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERD36C.tmp.dmp | binary | |
MD5:5A1774530CDE80EA3357F3C7489AE6A3 | SHA256:A6C03202FF2414BD27C540EBCEF7E914F47CAF5EEE1606ECCC7DD8C4751C45CD | |||
| 7480 | WerFault.exe | C:\WINDOWS\AppCompat\Programs\Amcache.hve | binary | |
MD5:43B0559E2A66564938E701D168DF7D37 | SHA256:5FFFE181CAE312503BF078418E10AF549D995CE199BEC969E3143E244643513C | |||
| 7380 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERD505.tmp.xml | xml | |
MD5:DC1E1AD6B0DBB5F3378EDFC23C25B426 | SHA256:C896F75E299666F2EF596C887859B0C418260C740DA659B54A39C51CB7DDC2EA | |||
| 5468 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_AppLaunch.exe_e7da30cf5d9744fbce7b9206b9c58a4383a2cb8_e872a7f5_cccb6e4c-95b5-4570-b865-c597f4361e46\Report.wer | — | |
MD5:— | SHA256:— | |||
| 7480 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERD467.tmp.WERInternalMetadata.xml | xml | |
MD5:DDBD7A9258526C675EA62DAE0C0CB30A | SHA256:48D1834359C31EE0DA77257C4B655F23804AF47239C9FF946CAB6AF69154FEAB | |||
| 4496 | 89ffb715e0a02eb089269f055f3104aecf648cd88366bf3ed49fb318ee257588.exe | C:\ProgramData\Microsoft\Windows\MSCaches\forfiles.exe | executable | |
MD5:9BB67AEA5E26CB136F23F29CC48D6B9E | SHA256:9B4886F187489A190BB2C412772C1998539F086C63A4CFD72FF3B107CBC21907 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
52
DNS requests
25
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 302 | 118.139.162.14:443 | https://excelautomationsolutions.in/222/xex.php | unknown | — | — | unknown |
— | — | GET | 200 | 20.242.39.171:443 | https://fe3cr.delivery.mp.microsoft.com/clientwebservice/ping | unknown | — | — | unknown |
4496 | 89ffb715e0a02eb089269f055f3104aecf648cd88366bf3ed49fb318ee257588.exe | GET | — | 3.233.207.248:80 | http://blockpg-dock.safezone.mcafee.com/blockpage/redirect/?ctxt=Kzd5WVBCL0JWS0lTS0c0YXhxNWdKMjlLbi9rQjN6UlMzVE01NGxYMnMyaEVDeFpXYzgvYlVCcS9LUzkyVnpkNUE0NkNITVh4ZGNZbzFnbTNXWWZEMS8zT1hIa3kySzBCaTNkRFFTMVhielJxMk5vU2x4dGJydz09&ts=1721405636 | unknown | — | — | unknown |
— | — | GET | 200 | 40.68.123.157:443 | https://slscr.update.microsoft.com/sls/ping | unknown | — | — | unknown |
— | — | POST | — | 20.190.160.20:443 | https://login.live.com/RST2.srf | unknown | — | — | unknown |
— | — | POST | — | 40.126.32.72:443 | https://login.live.com/RST2.srf | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4716 | svchost.exe | 40.126.32.133:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
5620 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.209.33.156:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
— | — | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
— | — | 40.126.32.133:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
— | — | 239.255.255.250:1900 | — | — | — | whitelisted |
2760 | svchost.exe | 40.113.103.199:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3196 | svchost.exe | 20.189.173.21:443 | watson.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
6068 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
login.live.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
watson.events.data.microsoft.com |
| whitelisted |
excelautomationsolutions.in |
| unknown |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
blockpg-dock.safezone.mcafee.com |
| unknown |
slscr.update.microsoft.com |
| whitelisted |