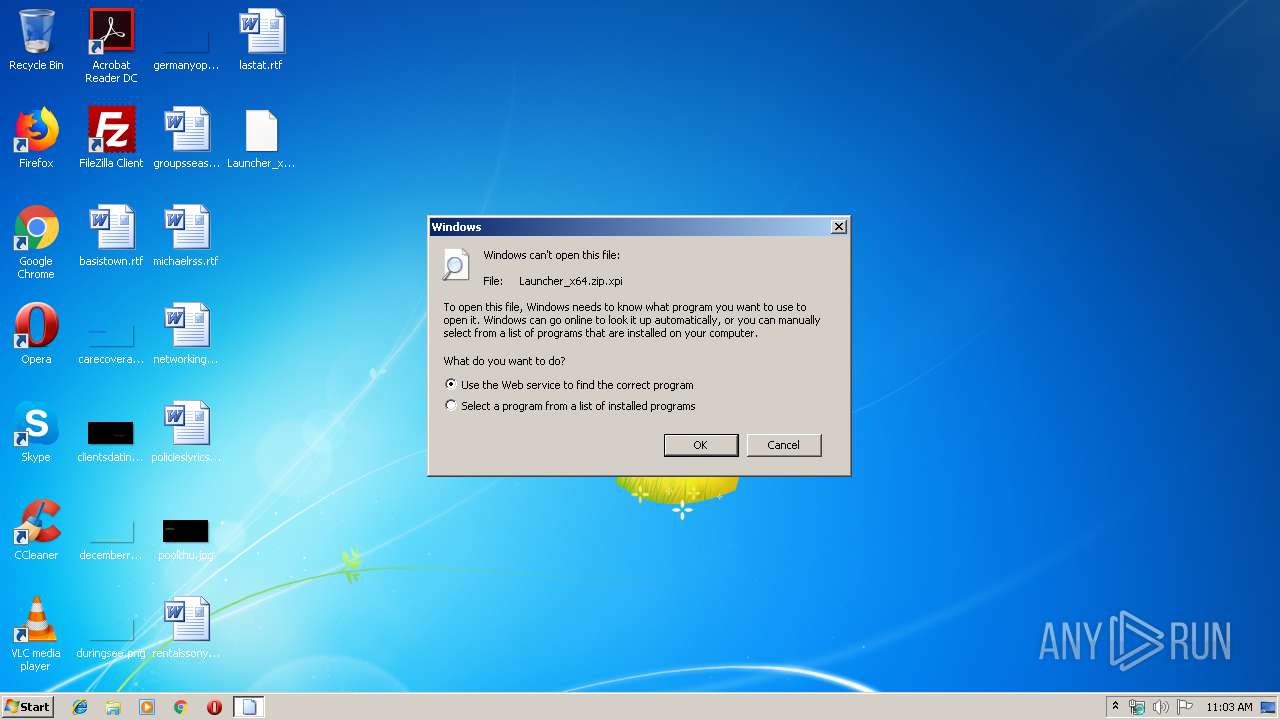
| download: | Launcher_x64.zip |
| Full analysis: | https://app.any.run/tasks/85e606b0-4c66-41bf-9fdd-bd214839e792 |
| Verdict: | Malicious activity |
| Analysis date: | January 18, 2020, 11:03:34 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | DCF05FD51D73E24501938EB0DB3DD1D2 |
| SHA1: | 8CE7A76C9CCDD4D4D2D8BF9EBDFC2719C09F122B |
| SHA256: | 89F169FB5B5C48B159267BAFCD99A305F1893D33E63E683BA5F7A3A38E14F0DF |
| SSDEEP: | 98304:vq72XgABrSzxYkvEFKOV/vgvpsQrEEY8mrYZLuaPwzN9WFSfwXM2NV8:vJXAzxFvrORmsCG8WyLuaPwzLfvUV8 |
MALICIOUS
Application was dropped or rewritten from another process
- Install.exe (PID: 1024)
- Install.exe (PID: 3840)
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3420)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2112)
Creates files in the user directory
- Install.exe (PID: 3840)
Application launched itself
- Install.exe (PID: 1024)
INFO
Manual execution by user
- WinRAR.exe (PID: 2112)
- Install.exe (PID: 1024)
- chrome.exe (PID: 3020)
Application launched itself
- chrome.exe (PID: 3020)
Reads the hosts file
- chrome.exe (PID: 3020)
- chrome.exe (PID: 3140)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xpi | | | Mozilla Firefox browser extension (66.6) |
|---|---|---|
| .zip | | | ZIP compressed archive (33.3) |
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2019:11:09 21:47:21 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | en-US/ |
Total processes
54
Monitored processes
17
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 292 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=75.0.3770.100 --initial-client-data=0x7c,0x80,0x84,0x78,0x88,0x6fc1a9d0,0x6fc1a9e0,0x6fc1a9ec | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 600 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1012,9963599843819386336,16336257095877305939,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=12352522707040593992 --mojo-platform-channel-handle=3364 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 716 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=1756 --on-initialized-event-handle=312 --parent-handle=316 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1024 | "C:\Users\admin\Desktop\Launcher_x64\Install.exe" | C:\Users\admin\Desktop\Launcher_x64\Install.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1400 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1012,9963599843819386336,16336257095877305939,131072 --enable-features=PasswordImport --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=10400890566117535834 --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2244 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1932 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1012,9963599843819386336,16336257095877305939,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=18235206092927119984 --mojo-platform-channel-handle=3508 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2064 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1012,9963599843819386336,16336257095877305939,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=11559146289453994751 --mojo-platform-channel-handle=3628 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2112 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\Launcher_x64.zip" C:\Users\admin\Desktop\Launcher_x64\ | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2644 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1012,9963599843819386336,16336257095877305939,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAADgAAAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=6237635804463987228 --mojo-platform-channel-handle=1020 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 3020 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 3221225547 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
640
Read events
551
Write events
86
Delete events
3
Modification events
| (PID) Process: | (2112) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2112) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2112) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2112) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2112) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2112) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3840) Install.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Install_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3840) Install.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Install_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (3840) Install.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Install_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (3840) Install.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Install_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: 4294901760 | |||
Executable files
4
Suspicious files
28
Text files
58
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3020 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\6db041c9-81a1-4c21-b7b5-28aad9fb325d.tmp | — | |
MD5:— | SHA256:— | |||
| 2112 | WinRAR.exe | C:\Users\admin\Desktop\Launcher_x64\en-US\lan-eng.lg | executable | |
MD5:— | SHA256:— | |||
| 3020 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000020.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2112 | WinRAR.exe | C:\Users\admin\Desktop\Launcher_x64\inc\bin.dll | executable | |
MD5:— | SHA256:— | |||
| 3840 | Install.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\admin@mywps[1].txt | text | |
MD5:— | SHA256:— | |||
| 3020 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:— | SHA256:— | |||
| 3020 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:— | SHA256:— | |||
| 3020 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Feature Engagement Tracker\EventDB\LOG.old~RF3aef18.TMP | text | |
MD5:— | SHA256:— | |||
| 3020 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF3aeeab.TMP | text | |
MD5:— | SHA256:— | |||
| 3020 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RF3aeeab.TMP | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
13
DNS requests
11
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3840 | Install.exe | 104.18.57.40:443 | fiasyfssa.mywps.me | Cloudflare Inc | US | unknown |
3140 | chrome.exe | 172.217.16.131:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
3140 | chrome.exe | 172.217.18.163:443 | www.google.com.ua | Google Inc. | US | whitelisted |
3140 | chrome.exe | 172.217.18.106:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
3140 | chrome.exe | 172.217.23.131:443 | www.gstatic.com | Google Inc. | US | whitelisted |
3140 | chrome.exe | 216.58.210.3:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
3140 | chrome.exe | 216.58.207.46:443 | apis.google.com | Google Inc. | US | whitelisted |
3140 | chrome.exe | 172.217.22.46:443 | ogs.google.com | Google Inc. | US | whitelisted |
3140 | chrome.exe | 216.58.208.35:443 | www.google.co.uk | Google Inc. | US | whitelisted |
3140 | chrome.exe | 172.217.21.228:443 | www.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
fiasyfssa.mywps.me |
| suspicious |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com.ua |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
ogs.google.com |
| whitelisted |
www.google.com |
| malicious |