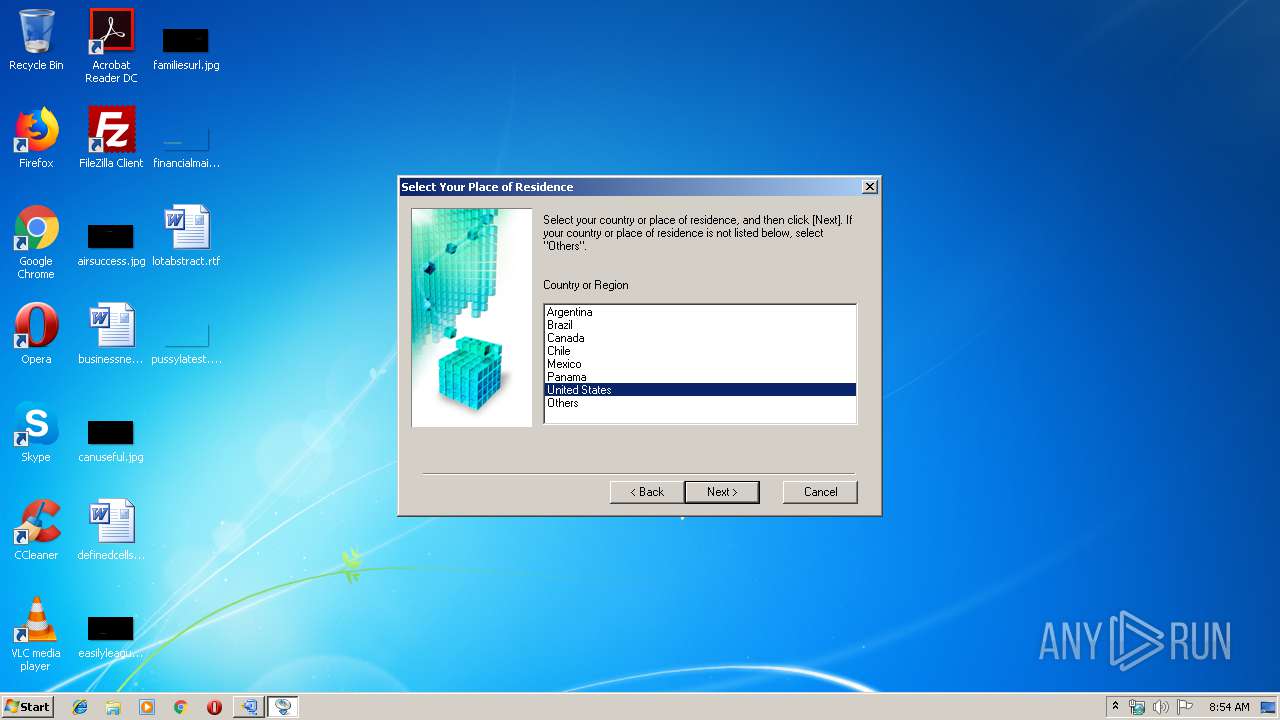
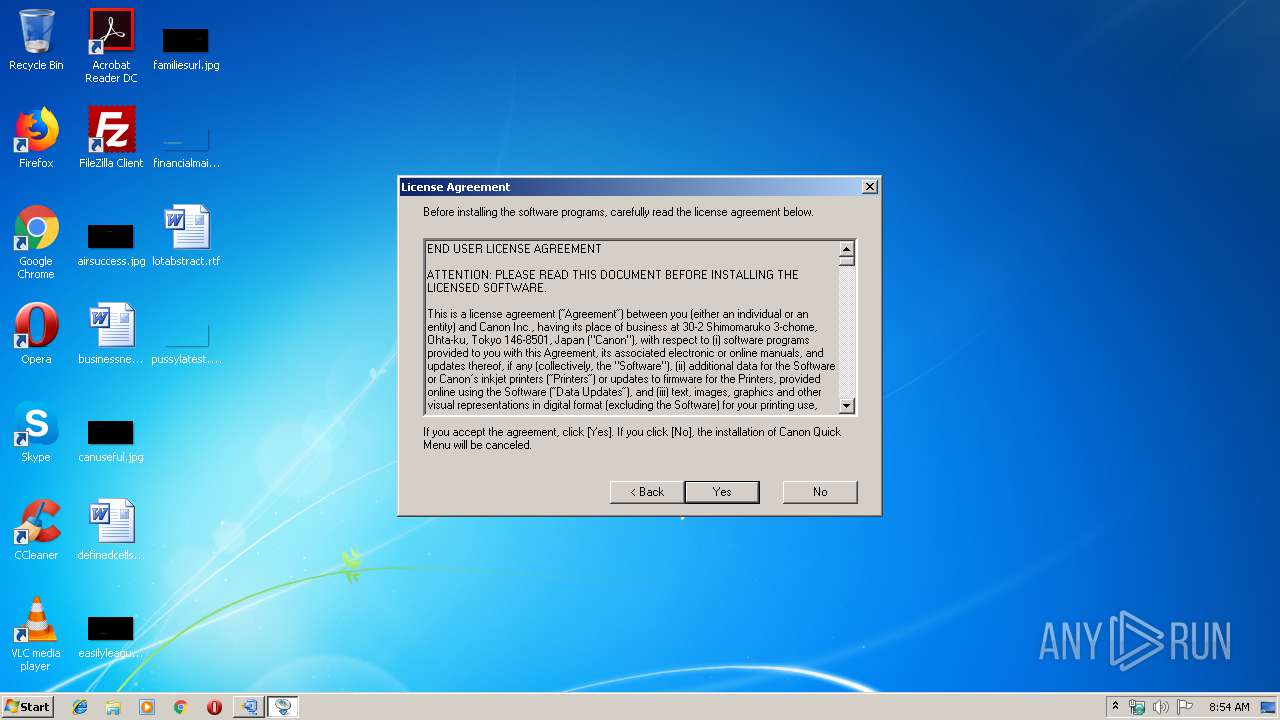
| download: | qm__-win-2_8_5-ea31_2.exe |
| Full analysis: | https://app.any.run/tasks/e0d16785-96a3-43e5-956a-ea5c4ad2d9a9 |
| Verdict: | Malicious activity |
| Analysis date: | December 04, 2019, 08:53:57 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | E2CB2820DF559DC07E1294EFAF9C8428 |
| SHA1: | F50467B067E0DC00BB8DC42B45534CA45FBF3724 |
| SHA256: | 89AF6F1A9BC6167361ED49B9FA8D838562E3741956B7952D1FA1963808546D4C |
| SSDEEP: | 196608:CDSb0Y9loTC2bkPcBQWkpI0YGmgLVMKCwXqLPPEckLwY6+8NQfDyCxb:CDlY9loNIPZIvSqKCwqby/6fNADBV |
MALICIOUS
Loads dropped or rewritten executable
- CNQMMAIN.EXE (PID: 3748)
- Setup.exe (PID: 952)
Application was dropped or rewritten from another process
- CNQMMAIN.EXE (PID: 3748)
- Setup.exe (PID: 952)
Changes the autorun value in the registry
- Setup.exe (PID: 952)
SUSPICIOUS
Creates files in the user directory
- CNQMMAIN.EXE (PID: 3748)
Reads Internet Cache Settings
- CNQMMAIN.EXE (PID: 3748)
Executable content was dropped or overwritten
- qm__-win-2_8_5-ea31_2.exe (PID: 2188)
- Setup.exe (PID: 952)
Reads Environment values
- CNQMMAIN.EXE (PID: 3748)
Creates a software uninstall entry
- Setup.exe (PID: 952)
Creates files in the program directory
- Setup.exe (PID: 952)
INFO
Dropped object may contain Bitcoin addresses
- qm__-win-2_8_5-ea31_2.exe (PID: 2188)
Manual execution by user
- CNQMMAIN.EXE (PID: 3748)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (32.1) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (28.5) |
| .exe | | | Winzip Win32 self-extracting archive (generic) (23.7) |
| .dll | | | Win32 Dynamic Link Library (generic) (6.7) |
| .exe | | | Win32 Executable (generic) (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2009:11:02 21:24:15+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 8 |
| CodeSize: | 77824 |
| InitializedDataSize: | 65536 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xaf1e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 02-Nov-2009 20:24:15 |
| Detected languages: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000F0 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 02-Nov-2009 20:24:15 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00012775 | 0x00013000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.50172 |
.rdata | 0x00014000 | 0x00003822 | 0x00004000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.98675 |
.data | 0x00018000 | 0x0000E6E4 | 0x00002000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 1.97345 |
.rsrc | 0x00027000 | 0x00009B6C | 0x0000A000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.56412 |
_winzip_ | 0x00031000 | 0x008EB000 | 0x008EB000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 7.9991 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.04402 | 1503 | Latin 1 / Western European | English - United States | RT_MANIFEST |
2 | 4.03621 | 744 | Latin 1 / Western European | English - United States | RT_ICON |
3 | 3.14459 | 296 | Latin 1 / Western European | English - United States | RT_ICON |
4 | 5.56342 | 3752 | Latin 1 / Western European | English - United States | RT_ICON |
5 | 5.99214 | 2216 | Latin 1 / Western European | English - United States | RT_ICON |
6 | 3.69605 | 1384 | Latin 1 / Western European | English - United States | RT_ICON |
7 | 5.83382 | 9640 | Latin 1 / Western European | English - United States | RT_ICON |
8 | 6.01045 | 4264 | Latin 1 / Western European | English - United States | RT_ICON |
9 | 4.68735 | 1128 | Latin 1 / Western European | English - United States | RT_ICON |
63 | 3.18826 | 764 | Latin 1 / Western European | English - United States | RT_STRING |
Imports
COMCTL32.dll |
GDI32.dll |
KERNEL32.dll |
SHELL32.dll |
USER32.dll |
Total processes
43
Monitored processes
4
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 952 | ".\qm__-win-2_8_5-ea31_2\Setup.exe" | C:\Users\admin\AppData\Local\Temp\WZSE0.TMP\qm__-win-2_8_5-ea31_2\Setup.exe | qm__-win-2_8_5-ea31_2.exe | ||||||||||||
User: admin Company: CANON INC. Integrity Level: HIGH Description: SETUP Exit code: 0 Version: 4.3.5.0 Modules
| |||||||||||||||
| 2188 | "C:\Users\admin\AppData\Local\Temp\qm__-win-2_8_5-ea31_2.exe" | C:\Users\admin\AppData\Local\Temp\qm__-win-2_8_5-ea31_2.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3220 | "C:\Users\admin\AppData\Local\Temp\qm__-win-2_8_5-ea31_2.exe" | C:\Users\admin\AppData\Local\Temp\qm__-win-2_8_5-ea31_2.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 3748 | "C:\Program Files\Canon\Quick Menu\CNQMMAIN.EXE" | C:\Program Files\Canon\Quick Menu\CNQMMAIN.EXE | explorer.exe | ||||||||||||
User: admin Company: CANON INC. Integrity Level: MEDIUM Description: Canon Quick Menu Exit code: 0 Version: 2.8.5.0 Modules
| |||||||||||||||
Total events
332
Read events
247
Write events
70
Delete events
15
Modification events
| (PID) Process: | (952) Setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | CanonQuickMenu |
Value: C:\Program Files\Canon\Quick Menu\CNQMMAIN.EXE /logon | |||
| (PID) Process: | (952) Setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Canon\MyPrinter\Canon Utilities\Quick Menu |
| Operation: | write | Name: | AppPath |
Value: C:\Program Files\Canon\Quick Menu\CNQMMAIN.EXE | |||
| (PID) Process: | (952) Setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Canon\MyPrinter\Canon Utilities\Quick Menu |
| Operation: | write | Name: | AppName |
Value: Quick Menu | |||
| (PID) Process: | (952) Setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Canon\Solution Menu EX |
| Operation: | write | Name: | AppPath |
Value: C:\Program Files\Canon\Quick Menu\CNSEMAIN.EXE | |||
| (PID) Process: | (952) Setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Canon\Solution Menu EX |
| Operation: | write | Name: | LanguageCode |
Value: EN | |||
| (PID) Process: | (952) Setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Canon\Quick Menu |
| Operation: | write | Name: | AppPath |
Value: C:\Program Files\Canon\Quick Menu\CNQMMAIN.EXE | |||
| (PID) Process: | (952) Setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Canon\Quick Menu |
| Operation: | write | Name: | LanguageCode |
Value: EN | |||
| (PID) Process: | (952) Setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Canon\Quick Menu |
| Operation: | write | Name: | Version |
Value: 2.8.5.0 | |||
| (PID) Process: | (952) Setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Canon\WRes |
| Operation: | write | Name: | Path |
Value: C:\ProgramData\CanonIJWSpt\WResList | |||
| (PID) Process: | (952) Setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Canon\WRes |
| Operation: | write | Name: | RESIDENCE |
Value: america | |||
Executable files
187
Suspicious files
5
Text files
290
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2188 | qm__-win-2_8_5-ea31_2.exe | C:\Users\admin\AppData\Local\Temp\WZSE0.TMP\qm__-win-2_8_5-ea31_2\Data2.cab | — | |
MD5:— | SHA256:— | |||
| 2188 | qm__-win-2_8_5-ea31_2.exe | C:\Users\admin\AppData\Local\Temp\WZSE0.TMP\qm__-win-2_8_5-ea31_2\CHECKSUM | text | |
MD5:— | SHA256:— | |||
| 2188 | qm__-win-2_8_5-ea31_2.exe | C:\Users\admin\AppData\Local\Temp\WZSE0.TMP\qm__-win-2_8_5-ea31_2\Data1.cab | compressed | |
MD5:A207C5D7252252A4CBF88275A8C6F107 | SHA256:055A695CB0AB29A80619AE29C560091DC758D0F57B710A8FA5BF81386A41F678 | |||
| 2188 | qm__-win-2_8_5-ea31_2.exe | C:\Users\admin\AppData\Local\Temp\WZSE0.TMP\qm__-win-2_8_5-ea31_2\Res\EULA\EC_Bulgarian.txt | text | |
MD5:39FB1833720217D474777EA514862D4E | SHA256:0DE60F7904942ABCBAB3762F2989D92C34BC34A980A908307C3F4DCFEF750D71 | |||
| 2188 | qm__-win-2_8_5-ea31_2.exe | C:\Users\admin\AppData\Local\Temp\WZSE0.TMP\qm__-win-2_8_5-ea31_2\NDP452-KB2901954-Web.exe | executable | |
MD5:CA41DBA55A727F01104871B160CD5B1D | SHA256:BD173D14A371E6786C4AE90BE1F2C560458D672BA4CBEB3CF55BEBFEF2E2778A | |||
| 2188 | qm__-win-2_8_5-ea31_2.exe | C:\Users\admin\AppData\Local\Temp\WZSE0.TMP\qm__-win-2_8_5-ea31_2\Res\EULA\AS_English.txt | text | |
MD5:E486A1CCE9783669E6D134F5B7079B79 | SHA256:FDE061163306A308B2FBC406F75B8FBA8902C90C52B810ABB11B51FEEEEB2290 | |||
| 2188 | qm__-win-2_8_5-ea31_2.exe | C:\Users\admin\AppData\Local\Temp\WZSE0.TMP\qm__-win-2_8_5-ea31_2\Res\EULA\AS_SimplifiedChinese.txt | text | |
MD5:815CB446819BF939DA9CEA24387FFBA8 | SHA256:6866C75342B85DB8B02FC5DF0BFADDC1B913654726F977CFD223710DCBEA336D | |||
| 2188 | qm__-win-2_8_5-ea31_2.exe | C:\Users\admin\AppData\Local\Temp\WZSE0.TMP\qm__-win-2_8_5-ea31_2\Res\EULA\EC_Czech.txt | text | |
MD5:F39ACA9FBF7B4790E7FD9AD7DF6E5D4A | SHA256:531A4CD24075BF623D7A0FDB9494CDB96B54F63BB0A21585CC17D73F445FD3DA | |||
| 2188 | qm__-win-2_8_5-ea31_2.exe | C:\Users\admin\AppData\Local\Temp\WZSE0.TMP\qm__-win-2_8_5-ea31_2\Res\EULA\EC_Danish.txt | text | |
MD5:C0CB96D4EE53B7057AEE6BD649FB0441 | SHA256:5D2C357AAB859295804FC61F29F832A2BCBD30E3E823707169ADE9682CEF82EA | |||
| 2188 | qm__-win-2_8_5-ea31_2.exe | C:\Users\admin\AppData\Local\Temp\WZSE0.TMP\qm__-win-2_8_5-ea31_2\Res\EULA\AS_TraditionalChinese.txt | text | |
MD5:BD804E7D84E9EDBAF49ABEE5E4252CCC | SHA256:540DF7BE98067789EB145C873604A24EB24537E8BB6131742C7589D38C0D19EC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
1
DNS requests
1
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3748 | CNQMMAIN.EXE | GET | 200 | 23.32.242.48:80 | http://gdlp01.c-wss.com/rmds/ij/ijs/print_order/updatedate.xml | NL | xml | 174 b | whitelisted |
3748 | CNQMMAIN.EXE | GET | 200 | 23.32.242.48:80 | http://gdlp01.c-wss.com/rmds/ij/ijs/print_order/wrtllist | NL | xml | 425 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3748 | CNQMMAIN.EXE | 23.32.242.48:80 | gdlp01.c-wss.com | Akamai International B.V. | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
gdlp01.c-wss.com |
| whitelisted |