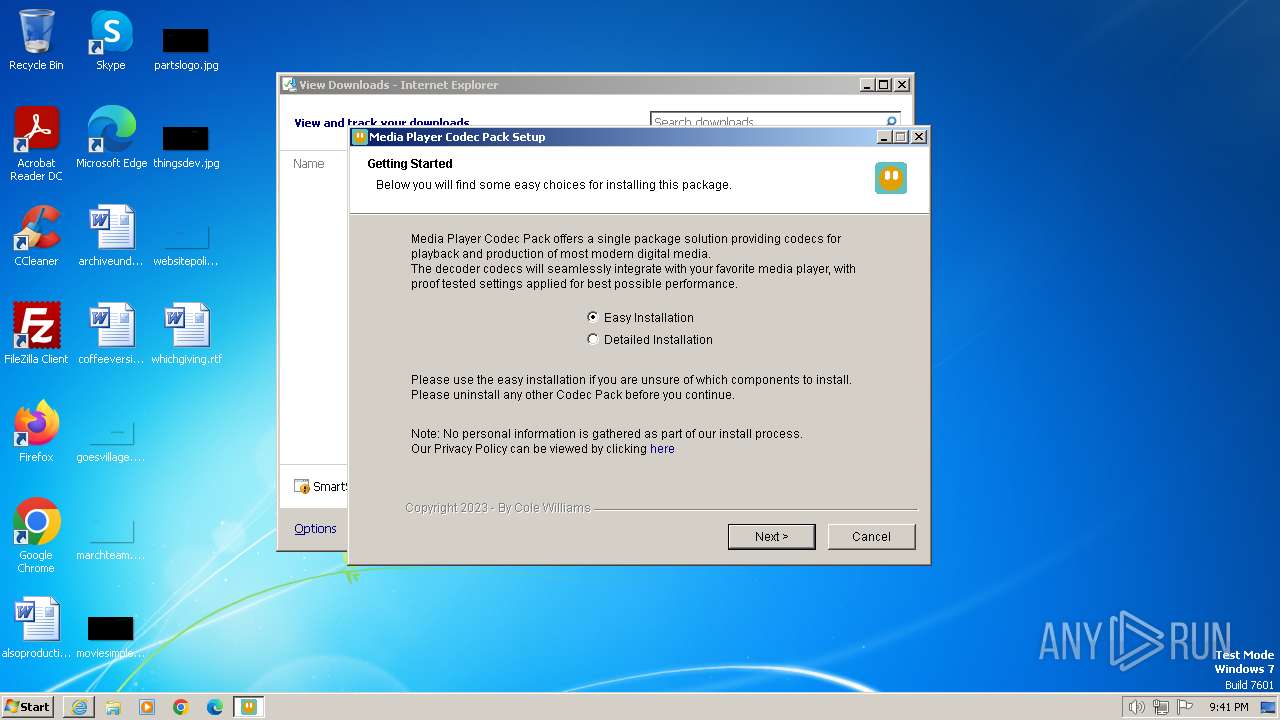
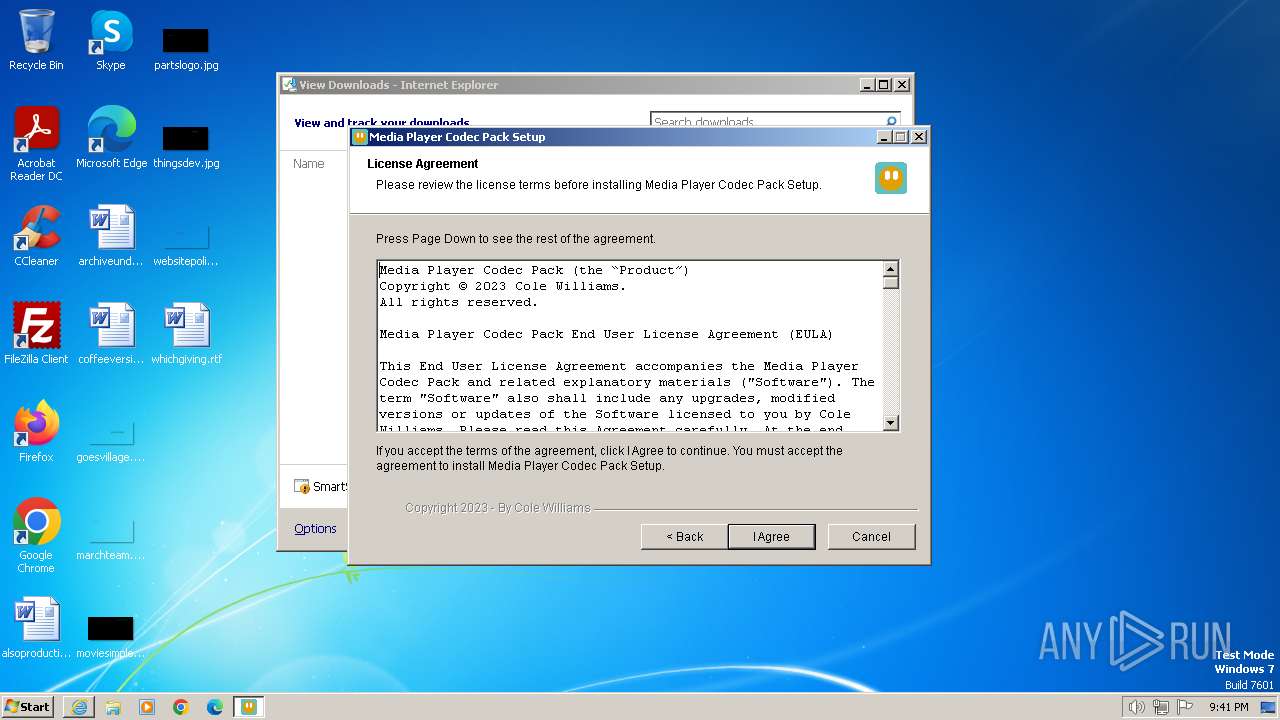
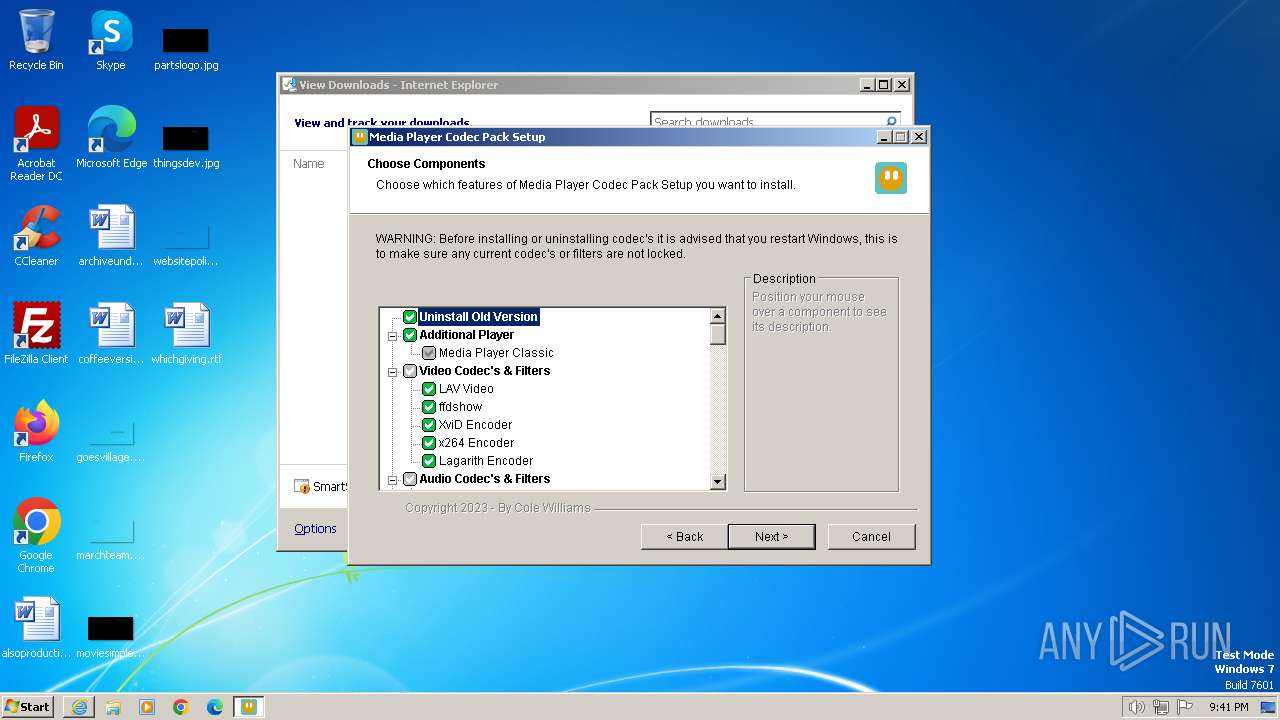
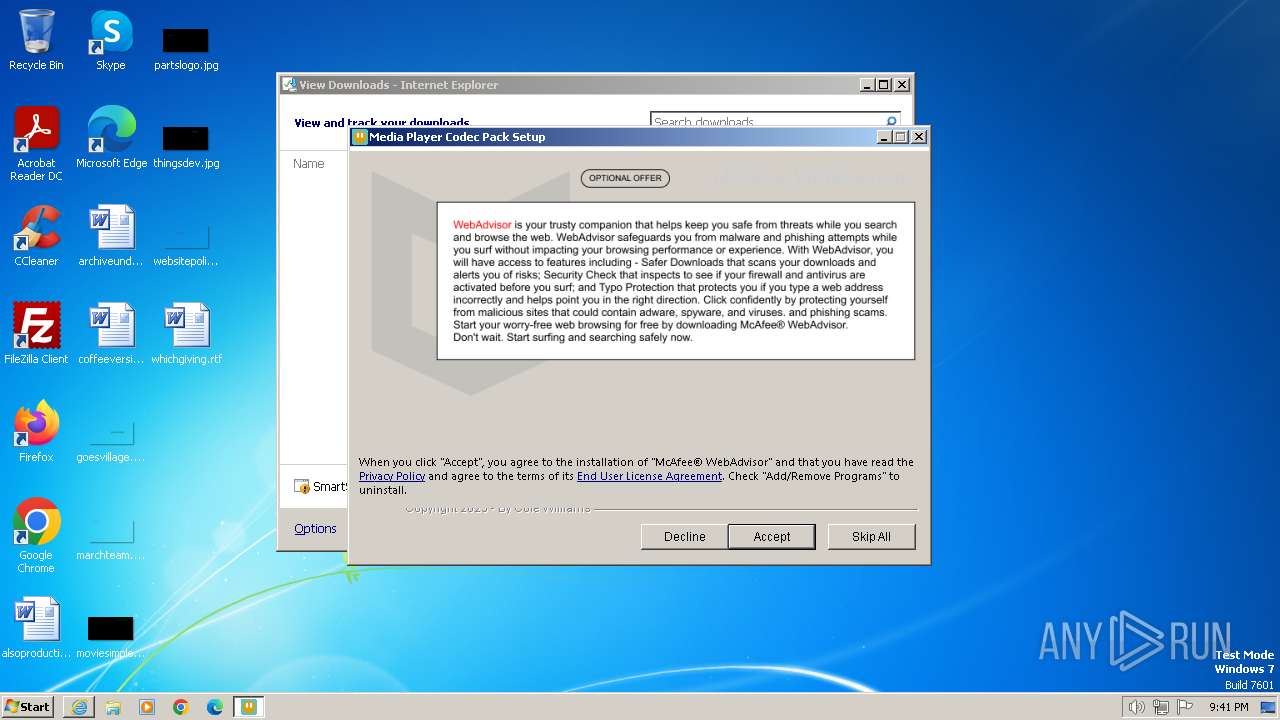
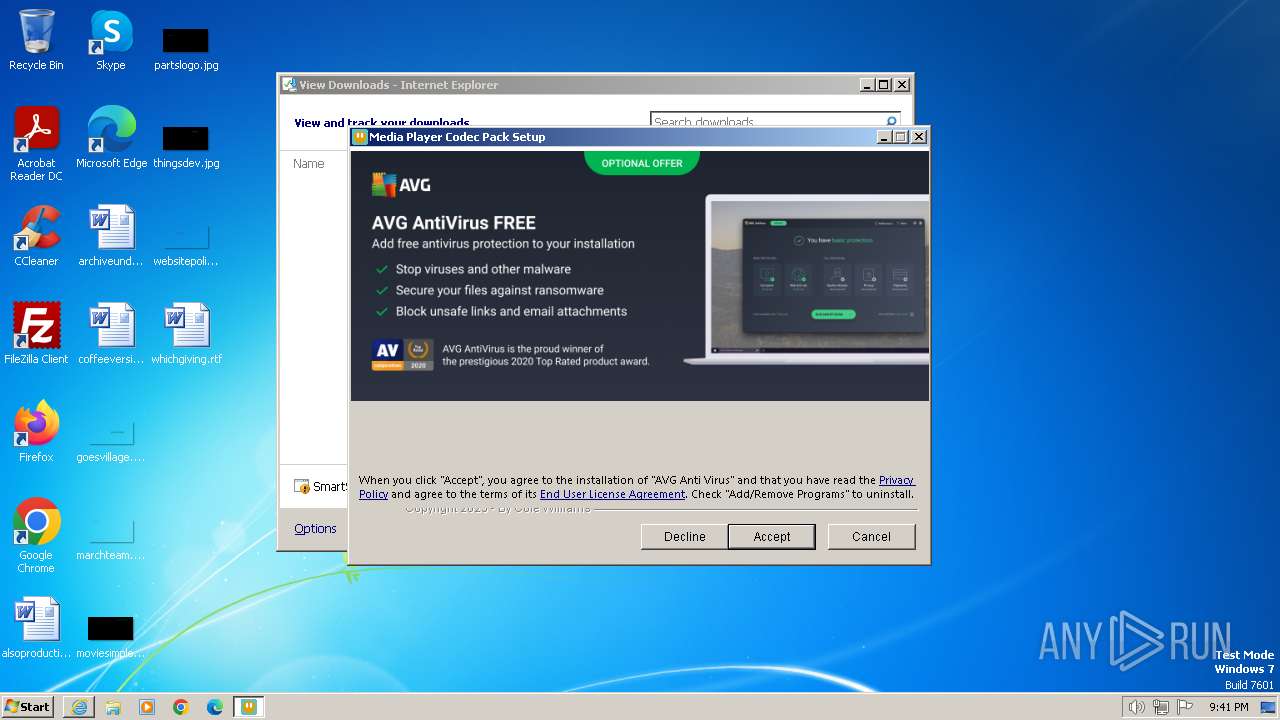
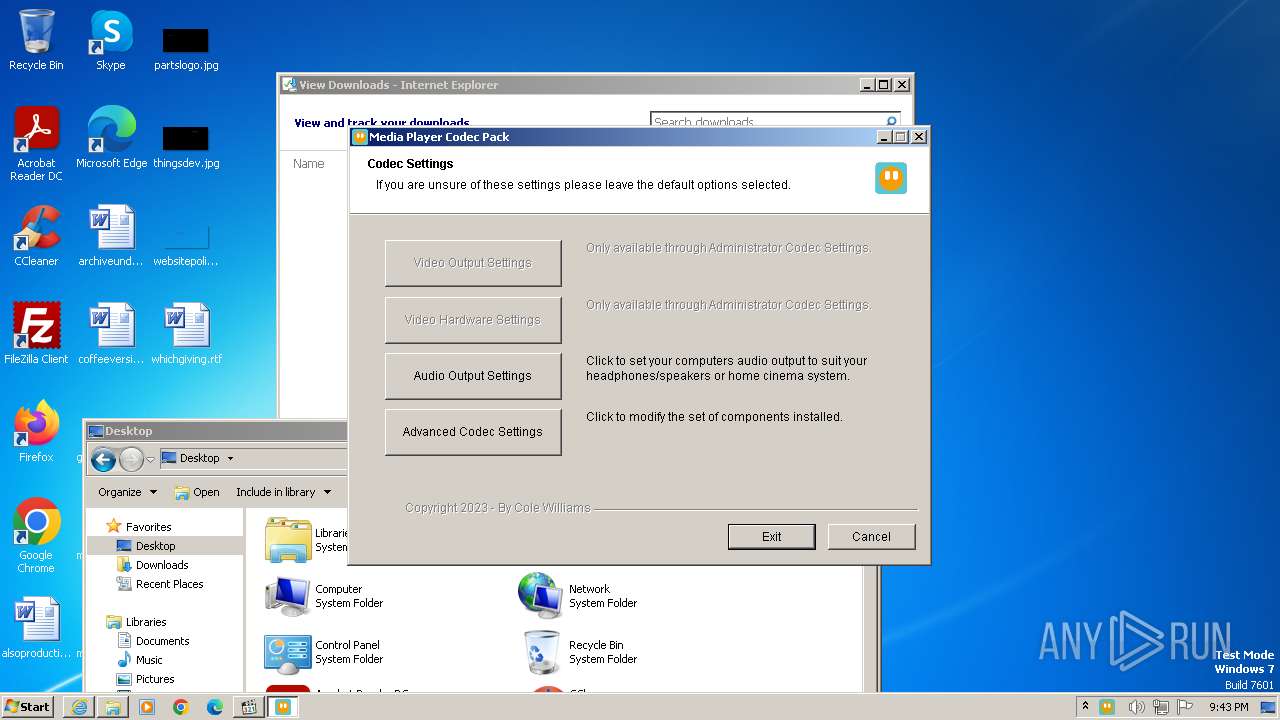
| URL: | https://www.mediaplayercodecpack.com/files/media.player.codec.pack.v4.5.9.setup.exe |
| Full analysis: | https://app.any.run/tasks/9997e2d7-78b7-4196-8109-7768e61fe944 |
| Verdict: | Malicious activity |
| Analysis date: | January 06, 2024, 21:40:18 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 1300B9474528F0542E1ECBFF0FDE451C |
| SHA1: | 3A028920A0EA4879B37915D598B3CE985B258FC7 |
| SHA256: | 897AA07CE91D6064FE1E02923F12357E57839E050A12A9C1D721732A17521134 |
| SSDEEP: | 3:N8DSLwvpW2LK96ELV43hvkUcjRQaA:2OLwk2w6h31BctQaA |
MALICIOUS
Creates a writable file in the system directory
- media.player.codec.pack.v4.5.9.setup.exe (PID: 3748)
Create files in the Startup directory
- media.player.codec.pack.v4.5.9.setup.exe (PID: 3748)
SUSPICIOUS
The process creates files with name similar to system file names
- media.player.codec.pack.v4.5.9.setup.exe (PID: 1536)
- media.player.codec.pack.v4.5.9.setup.exe (PID: 3748)
- CodecSettings.exe (PID: 2532)
Reads settings of System Certificates
- media.player.codec.pack.v4.5.9.setup.exe (PID: 1536)
- media.player.codec.pack.v4.5.9.setup.exe (PID: 3748)
Reads the Internet Settings
- media.player.codec.pack.v4.5.9.setup.exe (PID: 3748)
- RegAsm.exe (PID: 3368)
- mpc-hc.exe (PID: 3072)
- media.player.codec.pack.v4.5.9.setup.exe (PID: 1536)
Starts application with an unusual extension
- media.player.codec.pack.v4.5.9.setup.exe (PID: 3748)
Creates a software uninstall entry
- media.player.codec.pack.v4.5.9.setup.exe (PID: 3748)
Changes default file association
- media.player.codec.pack.v4.5.9.setup.exe (PID: 3748)
Searches for installed software
- media.player.codec.pack.v4.5.9.setup.exe (PID: 3748)
INFO
Reads the computer name
- media.player.codec.pack.v4.5.9.setup.exe (PID: 1536)
- media.player.codec.pack.v4.5.9.setup.exe (PID: 3748)
- SetACL.exe (PID: 2112)
- SetACL.exe (PID: 3232)
- SetACL.exe (PID: 3328)
- SetACL.exe (PID: 2452)
- SetACL.exe (PID: 3500)
- SetACL.exe (PID: 3380)
- SetACL.exe (PID: 3860)
- SetACL.exe (PID: 3136)
- RegAsm.exe (PID: 3368)
- SetACL.exe (PID: 2620)
- SetACL.exe (PID: 1820)
- SetACL.exe (PID: 3920)
- SetACL.exe (PID: 3824)
- SetACL.exe (PID: 3944)
- SetACL.exe (PID: 4036)
- SetACL.exe (PID: 3568)
- SetACL.exe (PID: 2952)
- SetACL.exe (PID: 2480)
- SetACL.exe (PID: 560)
- SetACL.exe (PID: 844)
- SetACL.exe (PID: 1936)
- SetACL.exe (PID: 3148)
- SetACL.exe (PID: 3084)
- SetACL.exe (PID: 1384)
- SetACL.exe (PID: 3284)
- SetACL.exe (PID: 996)
- SetACL.exe (PID: 2368)
- SetACL.exe (PID: 3076)
- SetACL.exe (PID: 2972)
- SetACL.exe (PID: 1812)
- SetACL.exe (PID: 2888)
- SetACL.exe (PID: 2404)
- SetACL.exe (PID: 2428)
- SetACL.exe (PID: 2788)
- SetACL.exe (PID: 2572)
- SetACL.exe (PID: 3808)
- SetACL.exe (PID: 1628)
- SetACL.exe (PID: 2032)
- SetACL.exe (PID: 2204)
- SetACL.exe (PID: 3696)
- SetACL.exe (PID: 3828)
- SetACL.exe (PID: 332)
- SetACL.exe (PID: 840)
- SetACL.exe (PID: 3036)
- SetACL.exe (PID: 4044)
- SetACL.exe (PID: 3700)
- SetACL.exe (PID: 2692)
- SetACL.exe (PID: 4060)
- SetACL.exe (PID: 4000)
- SetACL.exe (PID: 3344)
- SetACL.exe (PID: 3936)
- SetACL.exe (PID: 1792)
- SetACL.exe (PID: 3008)
- SetACL.exe (PID: 3352)
- SetACL.exe (PID: 1732)
- SetACL.exe (PID: 3004)
- SetACL.exe (PID: 3032)
- SetACL.exe (PID: 3108)
- SetACL.exe (PID: 2764)
- mpc-hc.exe (PID: 3072)
- SetACL.exe (PID: 2296)
- CodecSettings.exe (PID: 2532)
Application launched itself
- iexplore.exe (PID: 2044)
- msedge.exe (PID: 2672)
Drops the executable file immediately after the start
- iexplore.exe (PID: 296)
- media.player.codec.pack.v4.5.9.setup.exe (PID: 1536)
- msedge.exe (PID: 2672)
- media.player.codec.pack.v4.5.9.setup.exe (PID: 3748)
- CodecSettings.exe (PID: 2532)
Checks supported languages
- media.player.codec.pack.v4.5.9.setup.exe (PID: 1536)
- media.player.codec.pack.v4.5.9.setup.exe (PID: 3748)
- nsC059.tmp (PID: 2052)
- nsBFDB.tmp (PID: 876)
- SetACL.exe (PID: 2112)
- nsC145.tmp (PID: 568)
- SetACL.exe (PID: 3232)
- nsC1B4.tmp (PID: 1556)
- nsC222.tmp (PID: 3188)
- nsC2A0.tmp (PID: 3292)
- nsC30F.tmp (PID: 2076)
- SetACL.exe (PID: 3328)
- nsC37D.tmp (PID: 3452)
- SetACL.exe (PID: 2452)
- nsC0D7.tmp (PID: 2804)
- nsC45A.tmp (PID: 3672)
- nsC4D8.tmp (PID: 3644)
- SetACL.exe (PID: 3380)
- SetACL.exe (PID: 3136)
- nsC546.tmp (PID: 2108)
- SetACL.exe (PID: 3860)
- nsC632.tmp (PID: 3816)
- nsC6B0.tmp (PID: 3844)
- nsC3EB.tmp (PID: 3440)
- SetACL.exe (PID: 3500)
- nsC5B4.tmp (PID: 840)
- RegAsm.exe (PID: 3368)
- nsDF3B.tmp (PID: 1932)
- TrayMenu.exe (PID: 2528)
- SetACL.exe (PID: 2620)
- nsDFB9.tmp (PID: 2664)
- nsE027.tmp (PID: 1824)
- nsE0A5.tmp (PID: 3872)
- SetACL.exe (PID: 3568)
- nsE113.tmp (PID: 2868)
- nsE182.tmp (PID: 3968)
- SetACL.exe (PID: 3920)
- SetACL.exe (PID: 3944)
- nsE1F0.tmp (PID: 3572)
- SetACL.exe (PID: 3824)
- SetACL.exe (PID: 4036)
- SetACL.exe (PID: 1820)
- SetACL.exe (PID: 2952)
- nsE2DD.tmp (PID: 1608)
- nsE26E.tmp (PID: 956)
- nsE35B.tmp (PID: 1588)
- SetACL.exe (PID: 560)
- SetACL.exe (PID: 844)
- nsE3C9.tmp (PID: 1848)
- SetACL.exe (PID: 2480)
- nsE437.tmp (PID: 2448)
- SetACL.exe (PID: 1936)
- SetACL.exe (PID: 3148)
- nsE4B5.tmp (PID: 2152)
- SetACL.exe (PID: 3084)
- nsE533.tmp (PID: 1408)
- nsE620.tmp (PID: 900)
- SetACL.exe (PID: 2972)
- nsE76B.tmp (PID: 452)
- nsE68E.tmp (PID: 3052)
- SetACL.exe (PID: 1384)
- nsE6FC.tmp (PID: 3252)
- SetACL.exe (PID: 3284)
- SetACL.exe (PID: 996)
- nsE7E9.tmp (PID: 2912)
- SetACL.exe (PID: 2368)
- nsE5B1.tmp (PID: 3312)
- SetACL.exe (PID: 3076)
- nsE857.tmp (PID: 2852)
- SetACL.exe (PID: 2572)
- nsE8C6.tmp (PID: 2520)
- SetACL.exe (PID: 1812)
- nsE9A2.tmp (PID: 2592)
- nsE934.tmp (PID: 2644)
- SetACL.exe (PID: 2888)
- SetACL.exe (PID: 2404)
- nsEA11.tmp (PID: 1860)
- SetACL.exe (PID: 2428)
- nsEA8F.tmp (PID: 2688)
- SetACL.exe (PID: 2788)
- nsEB6B.tmp (PID: 1556)
- SetACL.exe (PID: 3808)
- SetACL.exe (PID: 1628)
- nsEBDA.tmp (PID: 3232)
- SetACL.exe (PID: 2032)
- nsEC48.tmp (PID: 3540)
- SetACL.exe (PID: 2204)
- nsECB7.tmp (PID: 3648)
- SetACL.exe (PID: 3696)
- nsED35.tmp (PID: 3708)
- SetACL.exe (PID: 3700)
- nsEAFD.tmp (PID: 680)
- nsEE11.tmp (PID: 3896)
- SetACL.exe (PID: 3828)
- SetACL.exe (PID: 332)
- SetACL.exe (PID: 840)
- nsEE80.tmp (PID: 3864)
- nsEEFE.tmp (PID: 1976)
- SetACL.exe (PID: 4044)
- SetACL.exe (PID: 3036)
- nsEF6C.tmp (PID: 3980)
- nsEFDA.tmp (PID: 3368)
- nsEDA3.tmp (PID: 1168)
- SetACL.exe (PID: 4060)
- nsF058.tmp (PID: 2544)
- nsF0C7.tmp (PID: 2944)
- SetACL.exe (PID: 1792)
- SetACL.exe (PID: 3936)
- nsF1B3.tmp (PID: 948)
- nsF222.tmp (PID: 3932)
- SetACL.exe (PID: 4000)
- SetACL.exe (PID: 2692)
- nsF135.tmp (PID: 1784)
- SetACL.exe (PID: 3344)
- nsF31E.tmp (PID: 3624)
- SetACL.exe (PID: 3352)
- SetACL.exe (PID: 3004)
- nsF38C.tmp (PID: 696)
- nsF3FA.tmp (PID: 1504)
- SetACL.exe (PID: 1732)
- nsF469.tmp (PID: 1596)
- SetACL.exe (PID: 3032)
- nsF2A0.tmp (PID: 1548)
- SetACL.exe (PID: 3008)
- SetACL.exe (PID: 2764)
- nsF5C3.tmp (PID: 2164)
- mpc-hc.exe (PID: 3072)
- CodecSettings.exe (PID: 2532)
- nsF4E7.tmp (PID: 2128)
- SetACL.exe (PID: 2296)
- nsF555.tmp (PID: 4012)
- SetACL.exe (PID: 3108)
Malware-specific behavior (creating "System.dll" in Temp)
- media.player.codec.pack.v4.5.9.setup.exe (PID: 1536)
- media.player.codec.pack.v4.5.9.setup.exe (PID: 3748)
- CodecSettings.exe (PID: 2532)
Reads the machine GUID from the registry
- media.player.codec.pack.v4.5.9.setup.exe (PID: 1536)
- media.player.codec.pack.v4.5.9.setup.exe (PID: 3748)
- RegAsm.exe (PID: 3368)
- mpc-hc.exe (PID: 3072)
Create files in a temporary directory
- media.player.codec.pack.v4.5.9.setup.exe (PID: 1536)
- media.player.codec.pack.v4.5.9.setup.exe (PID: 3748)
- CodecSettings.exe (PID: 2532)
Reads Environment values
- media.player.codec.pack.v4.5.9.setup.exe (PID: 1536)
- media.player.codec.pack.v4.5.9.setup.exe (PID: 3748)
The process uses the downloaded file
- iexplore.exe (PID: 2044)
- msedge.exe (PID: 2672)
- msedge.exe (PID: 2348)
Manual execution by a user
- explorer.exe (PID: 2592)
- msedge.exe (PID: 2672)
- mpc-hc.exe (PID: 3072)
- CodecSettings.exe (PID: 2532)
Reads CPU info
- media.player.codec.pack.v4.5.9.setup.exe (PID: 3748)
Process drops legitimate windows executable
- media.player.codec.pack.v4.5.9.setup.exe (PID: 3748)
Creates files in the program directory
- media.player.codec.pack.v4.5.9.setup.exe (PID: 3748)
The process drops C-runtime libraries
- media.player.codec.pack.v4.5.9.setup.exe (PID: 3748)
Checks proxy server information
- mpc-hc.exe (PID: 3072)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
273
Monitored processes
159
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 296 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2044 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 332 | C:\Windows\system32\Codecs\SetACL.exe -on HKEY_LOCAL_MACHINE\SOFTWARE\Classes\MediaFoundation\MediaSources\DoNotUse -ot reg -actn setowner -ownr n:S-1-5-80-956008885-3418522649-1831038044-1853292631-2271478464;s:y -silent | C:\Windows\System32\Codecs\SetACL.exe | — | nsEE11.tmp | |||||||||||
User: admin Company: Helge Klein Integrity Level: HIGH Description: SetACL 3 Exit code: 0 Version: 3.0.6.0 Modules
| |||||||||||||||
| 452 | "C:\Users\admin\AppData\Local\Temp\nsa76DA.tmp\nsE76B.tmp" C:\Windows\system32\Codecs\SetACL.exe -on HKEY_LOCAL_MACHINE\SOFTWARE\Classes\MediaFoundation\MediaSources\DoNotUse -ot reg -actn ace -ace n:S-1-5-32-544;s:y;p:full -silent | C:\Users\admin\AppData\Local\Temp\nsa76DA.tmp\nsE76B.tmp | — | media.player.codec.pack.v4.5.9.setup.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 560 | C:\Windows\system32\Codecs\SetACL.exe -on HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\DirectShow\Preferred -ot reg -actn ace -ace n:S-1-5-32-544;s:y;p:read -silent | C:\Windows\System32\Codecs\SetACL.exe | — | nsE2DD.tmp | |||||||||||
User: admin Company: Helge Klein Integrity Level: HIGH Description: SetACL 3 Exit code: 0 Version: 3.0.6.0 Modules
| |||||||||||||||
| 568 | "C:\Users\admin\AppData\Local\Temp\nsa76DA.tmp\nsC145.tmp" "C:\Windows\system32\Codecs\SetACL.exe" MACHINE\SOFTWARE\Classes\MediaFoundation\MediaSources\Preferred /registry /grant S-1-5-32-544 /full /r:cont_obj /sid /silent | C:\Users\admin\AppData\Local\Temp\nsa76DA.tmp\nsC145.tmp | — | media.player.codec.pack.v4.5.9.setup.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 3 Modules
| |||||||||||||||
| 680 | "C:\Users\admin\AppData\Local\Temp\nsa76DA.tmp\nsEAFD.tmp" C:\Windows\system32\Codecs\SetACL.exe -on HKEY_LOCAL_MACHINE\SOFTWARE\Classes\MediaFoundation\MediaSources\DoNotUse -ot reg -actn ace -ace n:S-1-5-32-544;s:y;p:read -silent | C:\Users\admin\AppData\Local\Temp\nsa76DA.tmp\nsEAFD.tmp | — | media.player.codec.pack.v4.5.9.setup.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 696 | "C:\Users\admin\AppData\Local\Temp\nsa76DA.tmp\nsF38C.tmp" C:\Windows\system32\Codecs\SetACL.exe -on "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Foundation\ByteStreamHandlers\.mp4" -ot reg -actn setowner -ownr n:S-1-5-80-956008885-3418522649-1831038044-1853292631-2271478464;s:y -silent | C:\Users\admin\AppData\Local\Temp\nsa76DA.tmp\nsF38C.tmp | — | media.player.codec.pack.v4.5.9.setup.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 840 | "C:\Users\admin\AppData\Local\Temp\nsa76DA.tmp\nsC5B4.tmp" "C:\Windows\system32\Codecs\SetACL.exe" "MACHINE\SOFTWARE\Microsoft\Windows Media Foundation\ByteStreamHandlers\.mp4" /registry /grant S-1-5-32-544 /full /r:cont_obj /sid /silent | C:\Users\admin\AppData\Local\Temp\nsa76DA.tmp\nsC5B4.tmp | — | media.player.codec.pack.v4.5.9.setup.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 3 Modules
| |||||||||||||||
| 840 | C:\Windows\system32\Codecs\SetACL.exe -on HKEY_LOCAL_MACHINE\SOFTWARE\Classes\MediaFoundation\MediaSources\DoNotUse -ot reg -actn ace -ace n:S-1-5-80-956008885-3418522649-1831038044-1853292631-2271478464;s:y;p:full -silent | C:\Windows\System32\Codecs\SetACL.exe | — | nsEE80.tmp | |||||||||||
User: admin Company: Helge Klein Integrity Level: HIGH Description: SetACL 3 Exit code: 25 Version: 3.0.6.0 Modules
| |||||||||||||||
| 844 | C:\Windows\system32\Codecs\SetACL.exe -on HKEY_LOCAL_MACHINE\SOFTWARE\Classes\MediaFoundation\MediaSources\DoNotUse -ot reg -actn setowner -ownr n:S-1-5-80-956008885-3418522649-1831038044-1853292631-2271478464;s:y -silent | C:\Windows\System32\Codecs\SetACL.exe | — | nsE35B.tmp | |||||||||||
User: admin Company: Helge Klein Integrity Level: HIGH Description: SetACL 3 Exit code: 0 Version: 3.0.6.0 Modules
| |||||||||||||||
Total events
33 938
Read events
33 612
Write events
314
Delete events
12
Modification events
| (PID) Process: | (2044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (2044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (2044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (2044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
375
Suspicious files
1 097
Text files
139
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 296 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\media.player.codec.pack.v4.5.9.setup.exe.5fuvru2.partial | — | |
MD5:— | SHA256:— | |||
| 2044 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\media.player.codec.pack.v4.5.9.setup.exe | — | |
MD5:— | SHA256:— | |||
| 296 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B2FAF7692FD9FFBD64EDE317E42334BA_D7393C8F62BDE4D4CB606228BC7A711E | binary | |
MD5:C6E7A3EF2CA48B5F3D632715CC7331AE | SHA256:2DB0AFD67885E0E9D677A7E8C092C3A24EF2E2876874CDD44A8855CA6A8E5E58 | |||
| 296 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 2044 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | binary | |
MD5:E33545AB02AE0223FDE67194BC0BB4BB | SHA256:E86088975AAD16B82AD2B627A334D10614E456C790D24D49C021E5C1D6058591 | |||
| 296 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B2FAF7692FD9FFBD64EDE317E42334BA_D7393C8F62BDE4D4CB606228BC7A711E | binary | |
MD5:47724CBA3F4CF0FA3BDEB2B01671F214 | SHA256:5DAB82A60289704C34FFCA0A777BA27E0A0A82ED0EF22AF31297ADD946C8F1F0 | |||
| 296 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\07CEF2F654E3ED6050FFC9B6EB844250_3431D4C539FB2CFCB781821E9902850D | binary | |
MD5:E6AC57E8AACFC97C04C86D0AEE61B4CC | SHA256:D612754CC8550C6F59652C7AAA9CEDF5B29FA6E87020DB1DC20EB74DEBB66E9D | |||
| 1536 | media.player.codec.pack.v4.5.9.setup.exe | C:\Users\admin\AppData\Local\Temp\nsc80D5.tmp | — | |
MD5:— | SHA256:— | |||
| 2044 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{333C72ED-ACDC-11EE-AE0A-12A9866C77DE}.dat | binary | |
MD5:ECDA378B49794B2ED336C7239D4EF98A | SHA256:9CBEA6209F6897CD79870504B03EA6AC92A8B28AFD21241C4156AC4C674105AA | |||
| 2044 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\urlblockindex[1].bin | binary | |
MD5:FA518E3DFAE8CA3A0E495460FD60C791 | SHA256:775853600060162C4B4E5F883F9FD5A278E61C471B3EE1826396B6D129499AA7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
67
DNS requests
99
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1080 | svchost.exe | GET | 304 | 72.247.153.162:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?a414549a770d7263 | unknown | — | — | unknown |
296 | iexplore.exe | GET | 200 | 184.24.77.199:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?608cb4ab6d3f68d3 | unknown | compressed | 4.66 Kb | unknown |
296 | iexplore.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | unknown | binary | 1.42 Kb | unknown |
296 | iexplore.exe | GET | 200 | 184.24.77.199:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?f6bf34dbb61e71d7 | unknown | compressed | 4.66 Kb | unknown |
296 | iexplore.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | unknown | binary | 2.18 Kb | unknown |
2044 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
2044 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA177el9ggmWelJjG4vdGL0%3D | unknown | binary | 471 b | unknown |
2044 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | binary | 471 b | unknown |
2044 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAqvpsXKY8RRQeo74ffHUxc%3D | unknown | binary | 471 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
296 | iexplore.exe | 51.195.149.65:443 | www.mediaplayercodecpack.com | OVH SAS | FR | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
296 | iexplore.exe | 184.24.77.199:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
296 | iexplore.exe | 104.18.38.233:80 | ocsp.comodoca.com | CLOUDFLARENET | — | shared |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1080 | svchost.exe | 72.247.153.162:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
2044 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | EDGECAST | US | whitelisted |
2044 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1536 | media.player.codec.pack.v4.5.9.setup.exe | 13.32.23.230:443 | d3j6hg32mwjrha.cloudfront.net | AMAZON-02 | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.mediaplayercodecpack.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
d3j6hg32mwjrha.cloudfront.net |
| whitelisted |
d1ej3nsy6n25r4.cloudfront.net |
| unknown |
ieonline.microsoft.com |
| whitelisted |