| File name: | encrypt.bat |
| Full analysis: | https://app.any.run/tasks/73990e9d-1c6c-41d8-adad-3d495252d5a4 |
| Verdict: | Malicious activity |
| Analysis date: | November 24, 2024, 03:37:34 |
| OS: | Windows 11 Professional (build: 22000, 64 bit) |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, ASCII text, with CRLF line terminators |
| MD5: | 0FD637A29F1EF50673C6CFF872BFAC8F |
| SHA1: | 16F3168AD9CD2EA2B45AAEF3DB5827983E0CCD83 |
| SHA256: | 897260817994EB0F999F77C653DFF92901F3844C871D6AB35E39F5531C87A525 |
| SSDEEP: | 48:53PbrUMUUAbak+ck1jFBjaZCNCMGXKoBgglf+fWXfq6d6z3lKZhlfeY/HC7:52UAboc6PgCFGaigglmOXyJ4vlc |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads the Internet Settings
- powershell.exe (PID: 3352)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 1192)
Creates file in the systems drive root
- cmd.exe (PID: 1192)
INFO
Disables trace logs
- powershell.exe (PID: 3352)
Checks proxy server information
- powershell.exe (PID: 3352)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
113
Monitored processes
3
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1192 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\Desktop\encrypt.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1848 | \??\C:\Windows\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
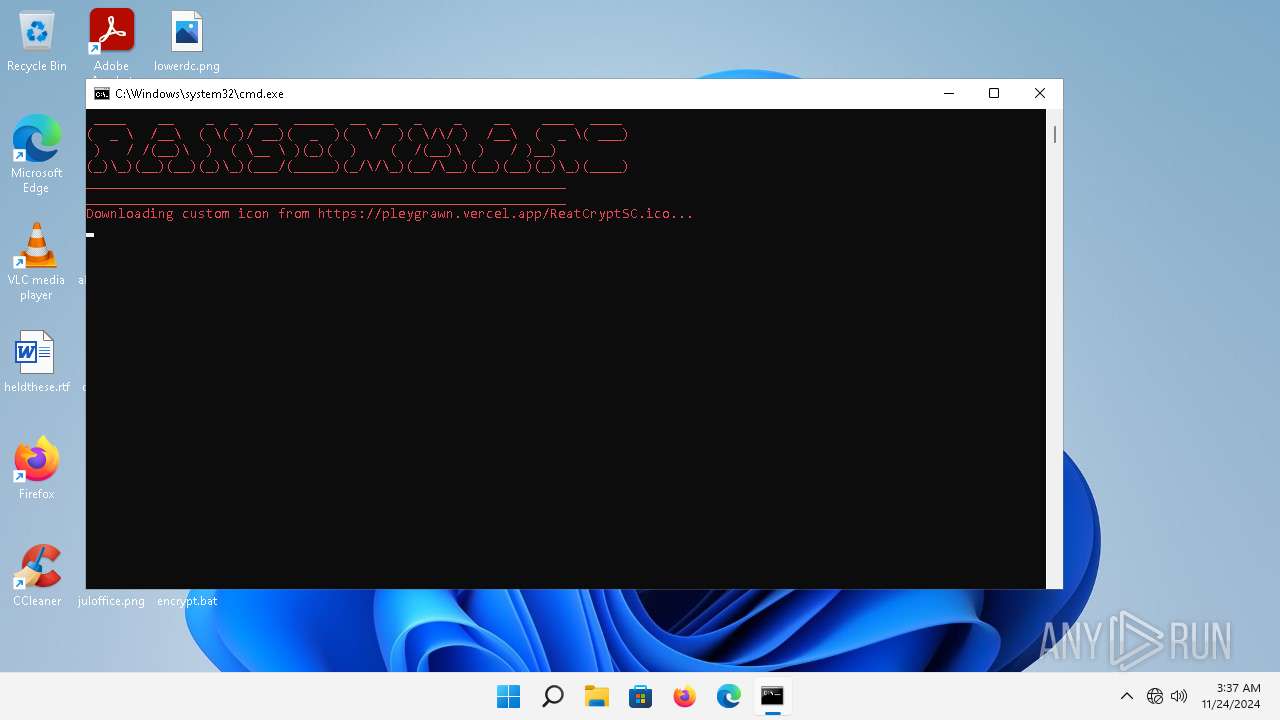
| 3352 | powershell -Command "Invoke-WebRequest 'https://pleygrawn.vercel.app/ReatCryptSC.ico' -OutFile 'C:\Users\admin\AppData\Local\Temp\ReatCryptSC.ico'" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
4 647
Read events
4 647
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
1
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3352 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_rq2m11qu.n5e.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3352 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_e2pvh5tb.apj.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3352 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\CLR_v4.0\UsageLogs\powershell.exe.log | text | |
MD5:8F41D8D3644D29DDFBF23B0502DB02A7 | SHA256:910C507F8C246ADCDAD74256EBF677F73DA4357126C4A170BCD86A56D84212C9 | |||
| 3352 | powershell.exe | C:\Users\admin\AppData\Local\Temp\ReatCryptSC.ico | image | |
MD5:EDDA8A67EE83E6E837AED229A66C2C7A | SHA256:7FE8C7B41960041D59C2DDACE5DF2A5A9024A2ABEADC682A9D0294519B871792 | |||
| 3352 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:DD0DB2BB02B7908C5E52638E28F8E861 | SHA256:32EE214B64563C0ED0B596301B78D13559732EB252ADF41D38FB0430ECEAB048 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
27
DNS requests
17
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1296 | svchost.exe | GET | 200 | 88.221.110.147:80 | http://www.msftconnecttest.com/connecttest.txt | unknown | — | — | whitelisted |
2648 | MoUsoCoreWorker.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?68e3da0bf5243979 | unknown | — | — | whitelisted |
2860 | svchost.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/pinrulesstl.cab?6a9a8dc8f99a4184 | unknown | — | — | whitelisted |
— | — | GET | 200 | 76.76.21.61:443 | https://pleygrawn.vercel.app/ReatCryptSC.ico | unknown | image | 165 Kb | unknown |
— | — | GET | 200 | 23.213.164.137:443 | https://fs.microsoft.com/fs/windows/config.json | unknown | binary | 55 b | whitelisted |
— | — | GET | 200 | 52.113.194.132:443 | https://ecs.office.com/config/v2/Office/officeclicktorun/16.0.16626.20134/Production/CC?&Clientid=%7b80C2A92B-EDEE-479E-8470-DBC6C547F2FB%7d&Application=officeclicktorun&Platform=win32&Version=16.0.16626.20134&MsoVersion=16.0.16626.20134&ProcessName=officec2rclient.exe&Audience=Production&Build=ship&Architecture=x64&OsVersion=10.0&OsBuild=22000&Channel=CC&InstallType=C2R&SessionId=%7b260DF157-5AD4-4FEA-9571-2A5ABE2A8008%7d&LabMachine=false | unknown | binary | 79.0 Kb | whitelisted |
— | — | GET | 200 | 13.107.6.156:443 | https://mrodevicemgr.officeapps.live.com/mrodevicemgrsvc/api/v1/C2RTargetAudienceData?omid=97560490bafb0d49bca6f8f0df91025d&susid=c408ee57-2103-4c34-9e6f-30bdf6c87e50&audienceFFN=492350f6-3a01-4f97-b9c0-c7c6ddf67d60&tid=&osver=Client%7C10.0.22000&offver=16.0.16626.20134&ring=Production&aud=Production&ch=CC&osarch=x64&manstate=6 | unknown | binary | 190 b | whitelisted |
2860 | svchost.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?fd5a1b7975a5d4dc | unknown | — | — | whitelisted |
2860 | svchost.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/pinrulesstl.cab?7b06b985bb73d1f0 | unknown | — | — | whitelisted |
2860 | svchost.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?bff1da83beece417 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3420 | rundll32.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 52.109.32.97:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
5052 | OfficeC2RClient.exe | 52.109.32.97:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
— | — | 34.149.100.209:443 | firefox.settings.services.mozilla.com | GOOGLE | US | whitelisted |
— | — | 34.120.208.123:443 | incoming.telemetry.mozilla.org | GOOGLE-CLOUD-PLATFORM | US | whitelisted |
5552 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1296 | svchost.exe | 88.221.110.147:80 | — | Akamai International B.V. | DE | unknown |
2648 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2648 | MoUsoCoreWorker.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
firefox.settings.services.mozilla.com |
| whitelisted |
incoming.telemetry.mozilla.org |
| whitelisted |
prod.remote-settings.prod.webservices.mozgcp.net |
| whitelisted |
telemetry-incoming.r53-2.services.mozilla.com |
| whitelisted |
google.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
pleygrawn.vercel.app |
| unknown |
ecs.office.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1296 | svchost.exe | Misc activity | ET INFO Microsoft Connection Test |
1656 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloud infrastructure to build app (vercel .app) |