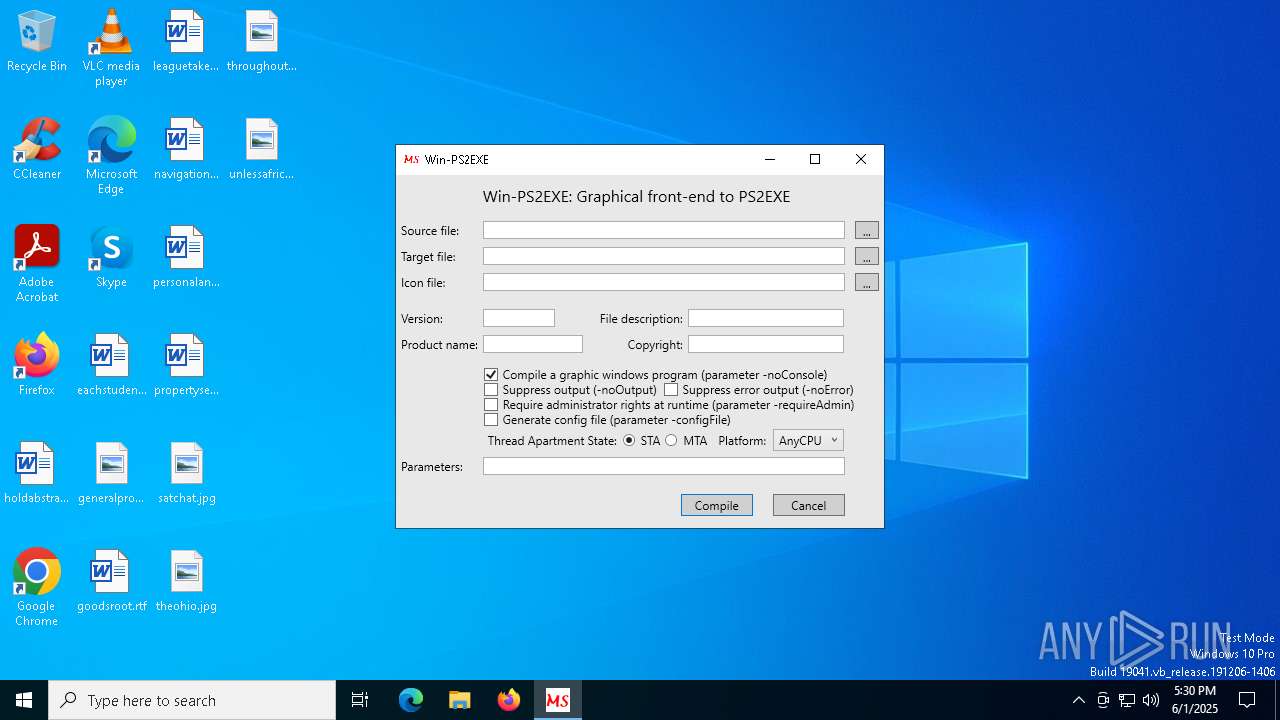
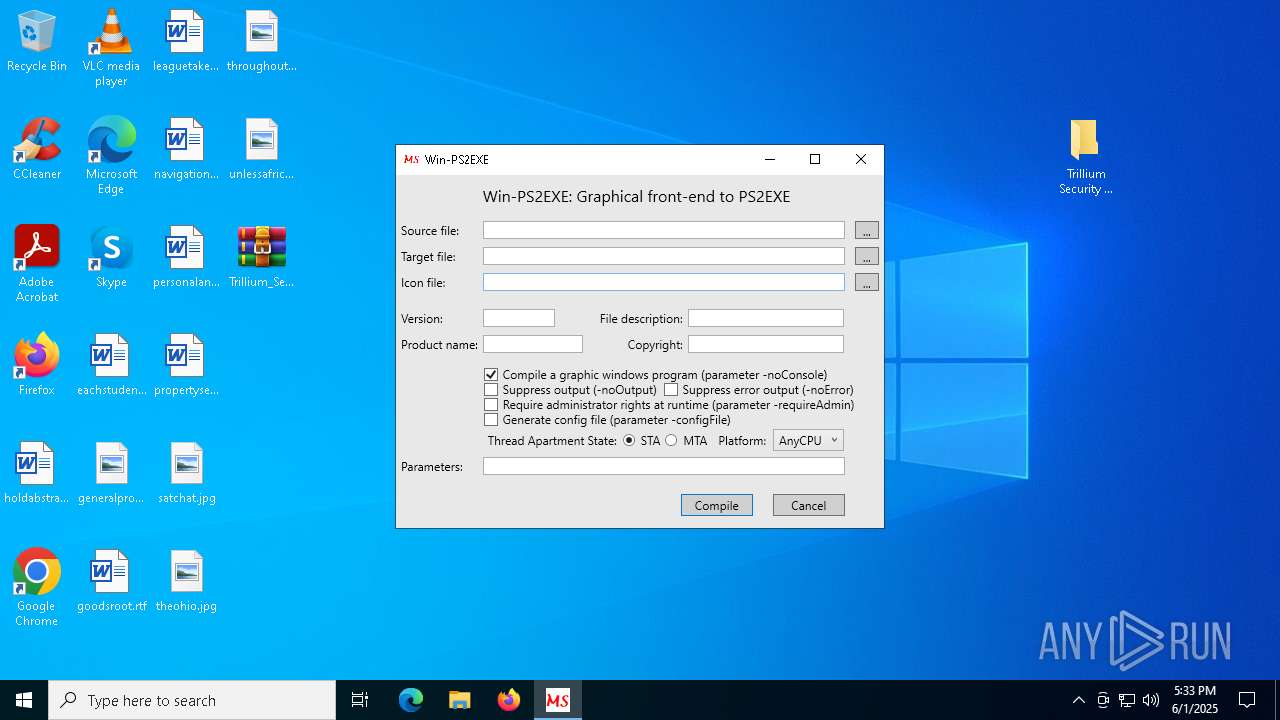
| File name: | Win-PS2EXE.exe |
| Full analysis: | https://app.any.run/tasks/d7e7e3e0-54da-4373-8f6c-9fdba9be0c4c |
| Verdict: | Malicious activity |
| Analysis date: | June 01, 2025, 17:30:28 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | A14CD9701168DC0FD0EDC5D4550330F4 |
| SHA1: | 032EBF36E0B57F0A622A6390B000D56E39C5C332 |
| SHA256: | 8965FEB0301C9970FA3C867882B51883F72109199703950D9F9F57F0DA3AA261 |
| SSDEEP: | 768:4Y7dPDOZdWGazzzLwnmmmmmmmmmmmmrNgOuKY3o3tGkduqVC+Obac9q/fLuU:4Y9GgOuKY3o3tGkduqVC+ObzifLuU |
MALICIOUS
No malicious indicators.SUSPICIOUS
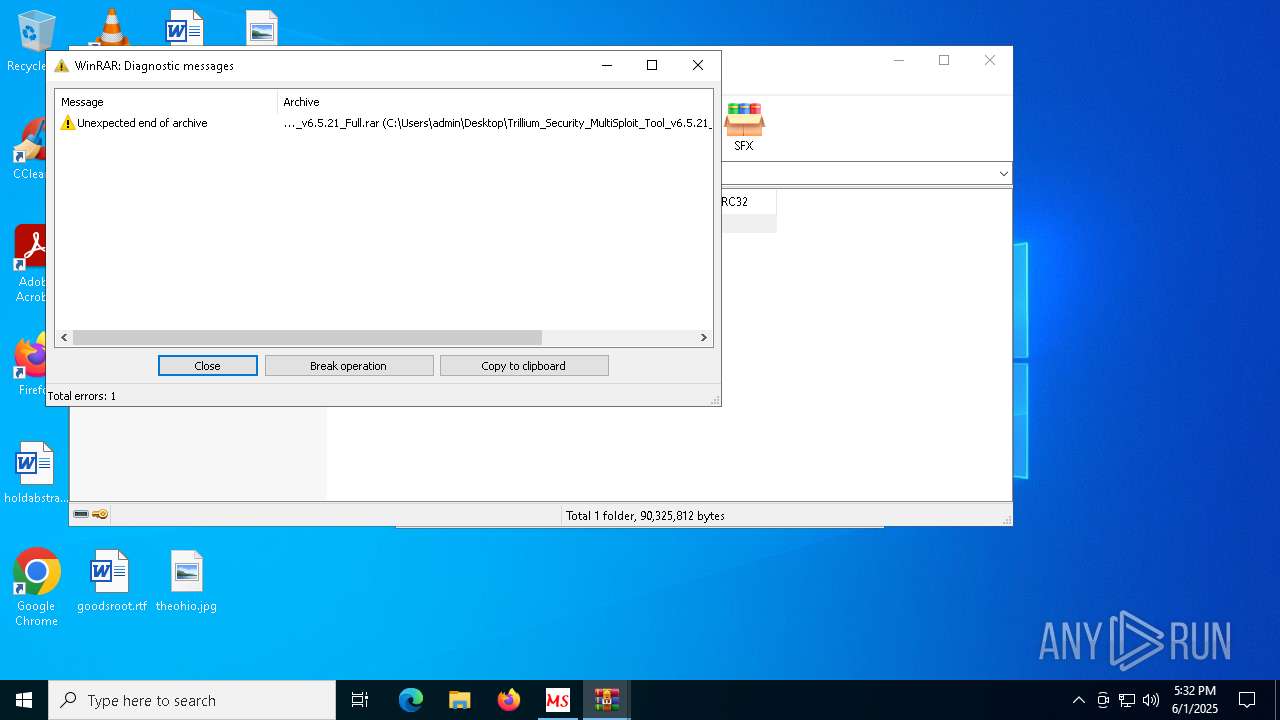
The process creates files with name similar to system file names
- WinRAR.exe (PID: 8028)
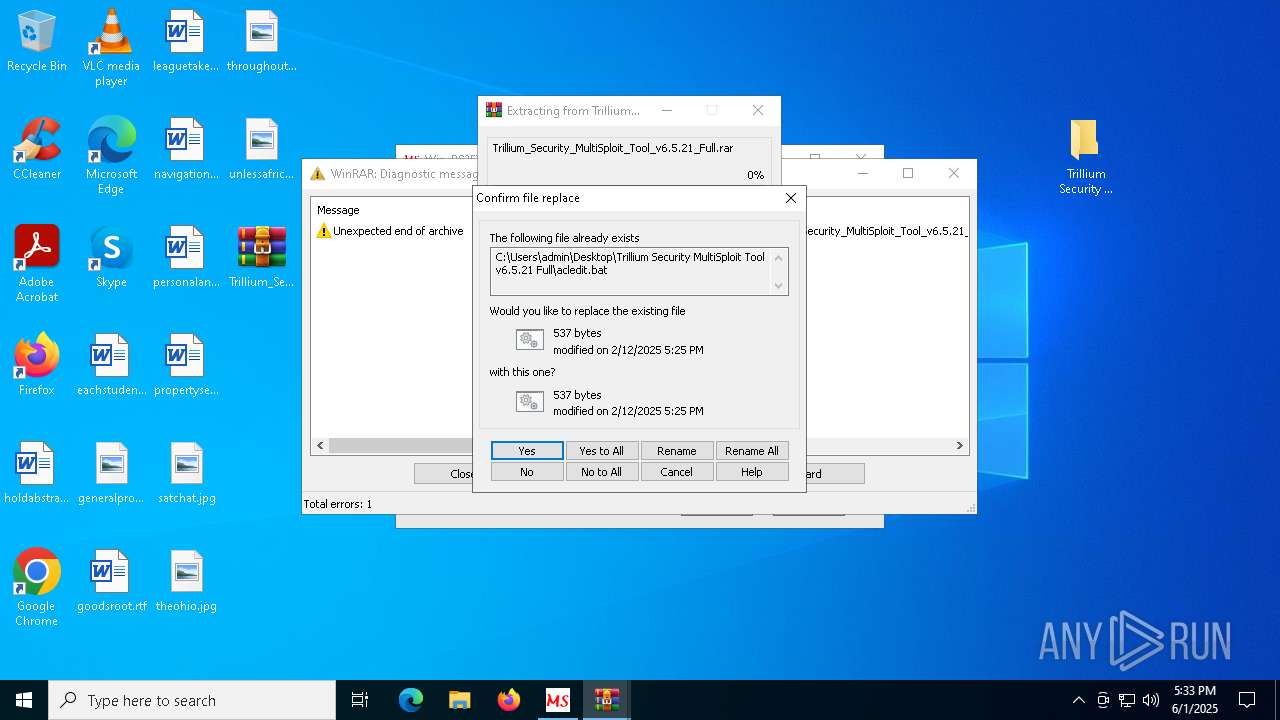
Process drops legitimate windows executable
- WinRAR.exe (PID: 8028)
Process drops python dynamic module
- WinRAR.exe (PID: 8028)
INFO
Reads the machine GUID from the registry
- Win-PS2EXE.exe (PID: 1176)
Manual execution by a user
- WinRAR.exe (PID: 6132)
- WinRAR.exe (PID: 8028)
- WinRAR.exe (PID: 2092)
Checks supported languages
- Win-PS2EXE.exe (PID: 1176)
Reads the software policy settings
- slui.exe (PID: 4008)
- slui.exe (PID: 6584)
Checks proxy server information
- slui.exe (PID: 4008)
Reads the computer name
- Win-PS2EXE.exe (PID: 1176)
The sample compiled with english language support
- WinRAR.exe (PID: 8028)
The sample compiled with german language support
- WinRAR.exe (PID: 8028)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 8028)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (82.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (7.4) |
| .exe | | | Win32 Executable (generic) (5.1) |
| .exe | | | Generic Win/DOS Executable (2.2) |
| .exe | | | DOS Executable Generic (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:09:26 14:30:36+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 26112 |
| InitializedDataSize: | 4608 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x846e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.1.2 |
| ProductVersionNumber: | 1.0.1.2 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | Graphical front end to Invoke-PS2EXE |
| CompanyName: | MS |
| FileDescription: | Graphical front end to Invoke-PS2EXE |
| FileVersion: | 1.0.1.2 |
| InternalName: | Win-PS2EXE.exe |
| LegalCopyright: | © Markus Scholtes 2023 |
| OriginalFileName: | Win-PS2EXE.exe |
| ProductName: | Win-PS2EXE |
| ProductVersion: | 1.0.1.2 |
| AssemblyVersion: | 1.0.1.2 |
Total processes
136
Monitored processes
8
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1176 | "C:\Users\admin\AppData\Local\Temp\Win-PS2EXE.exe" | C:\Users\admin\AppData\Local\Temp\Win-PS2EXE.exe | — | explorer.exe | |||||||||||
User: admin Company: MS Integrity Level: MEDIUM Description: Graphical front end to Invoke-PS2EXE Version: 1.0.1.2 Modules
| |||||||||||||||
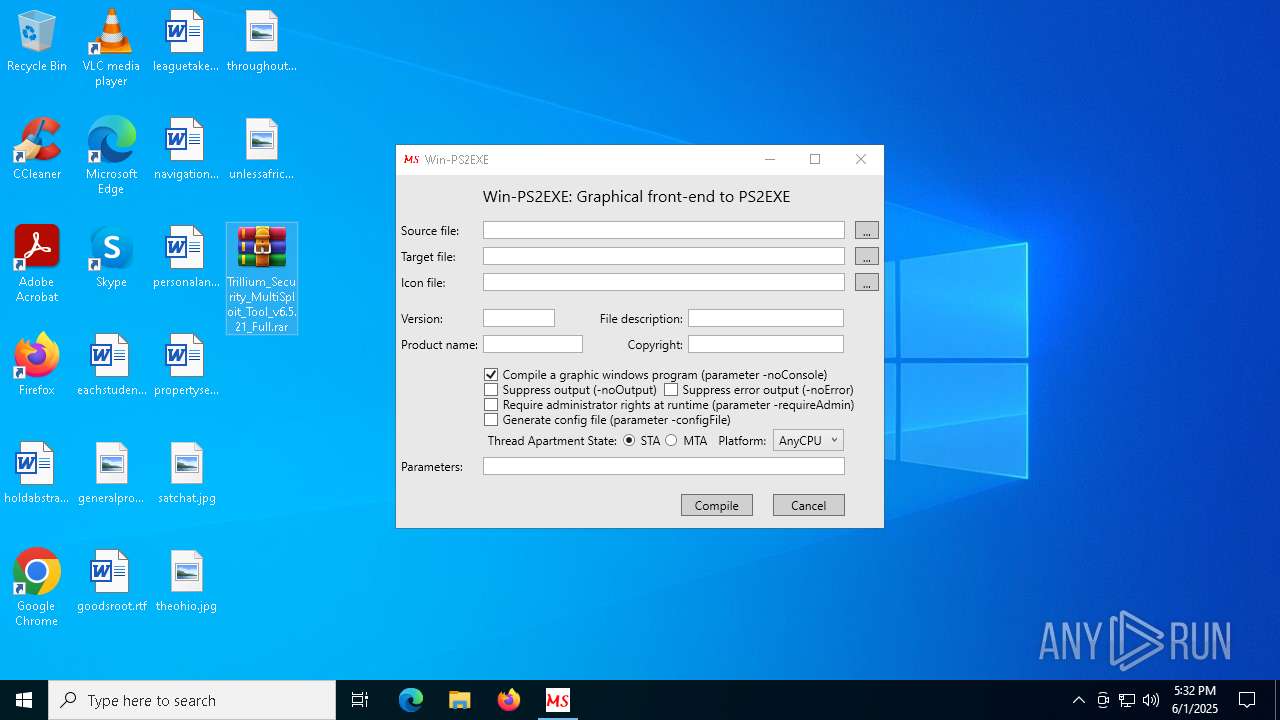
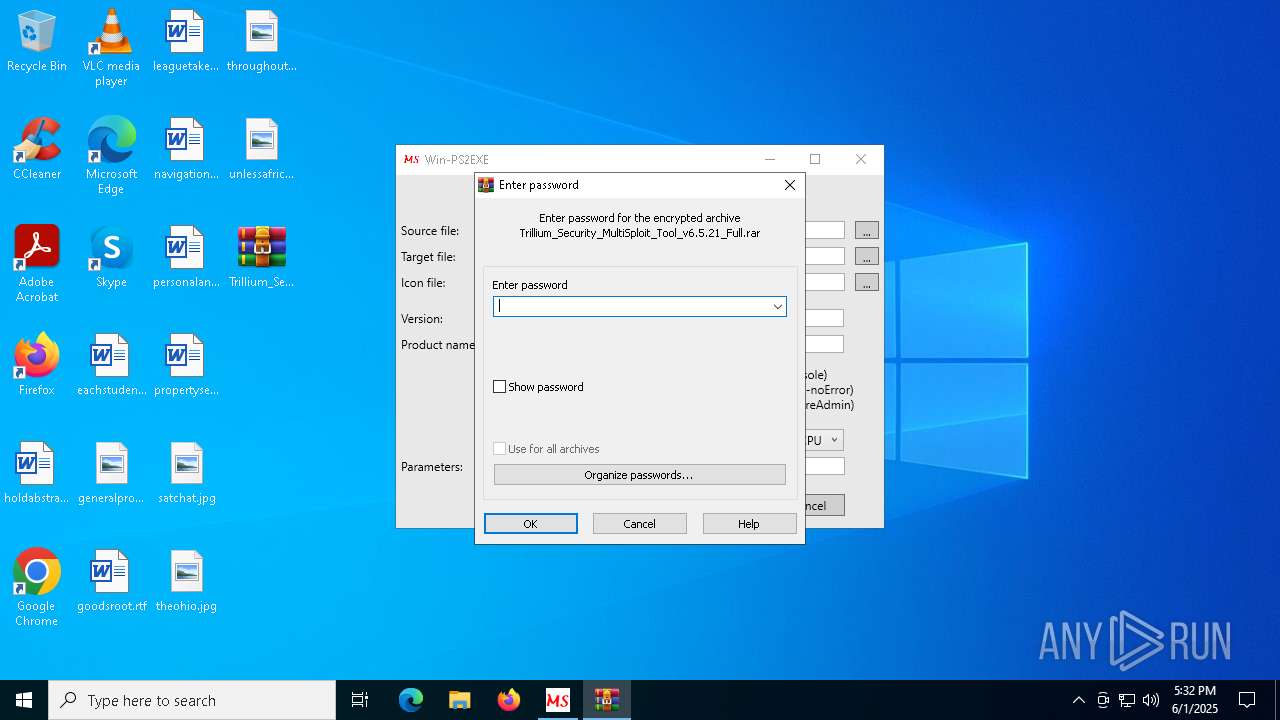
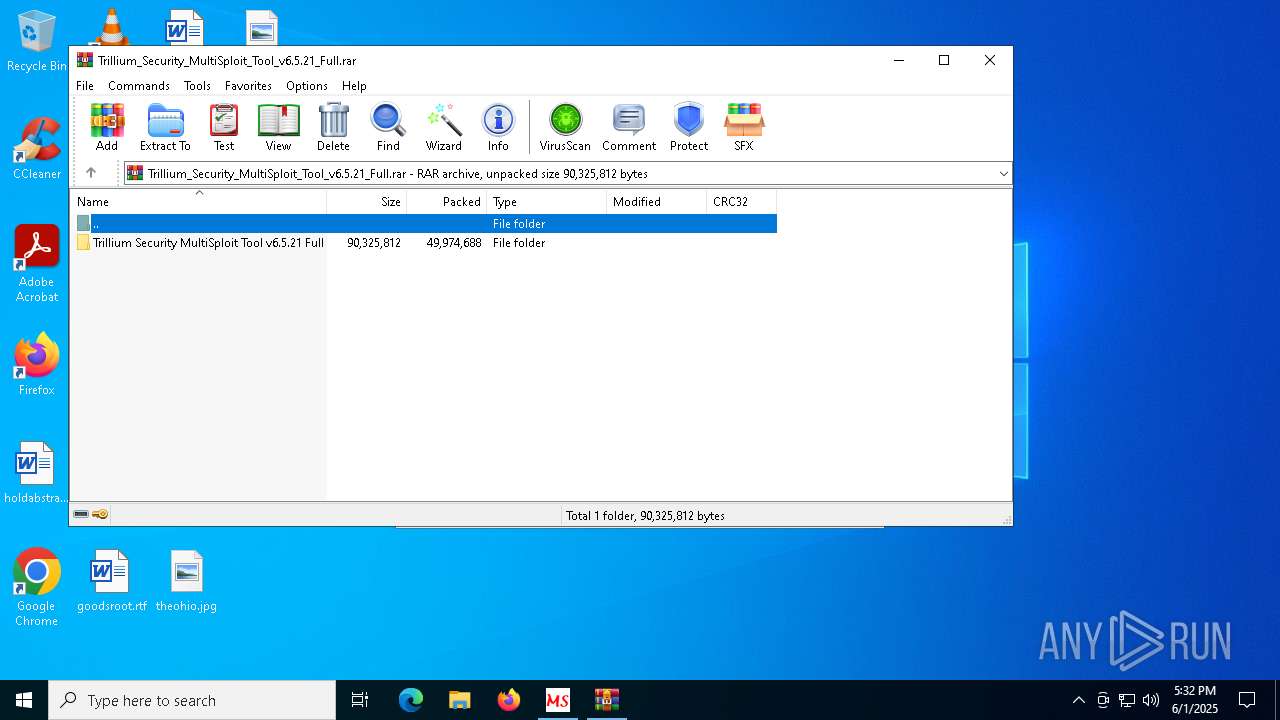
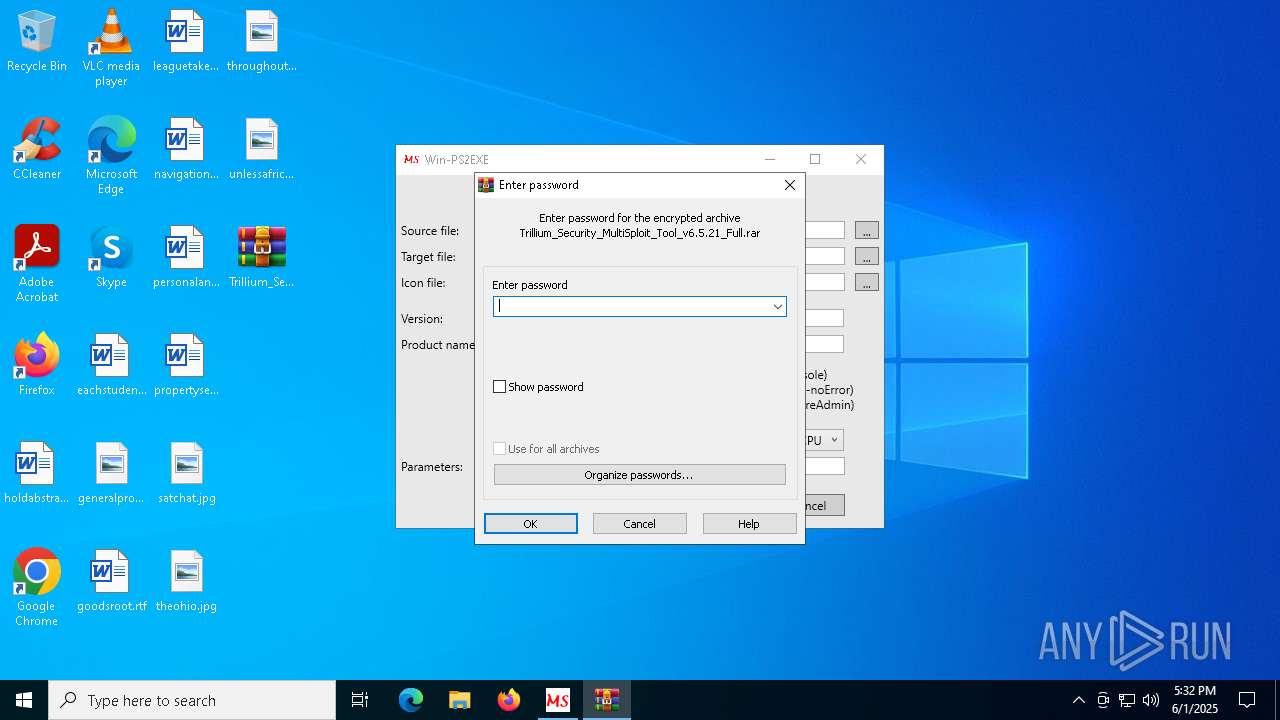
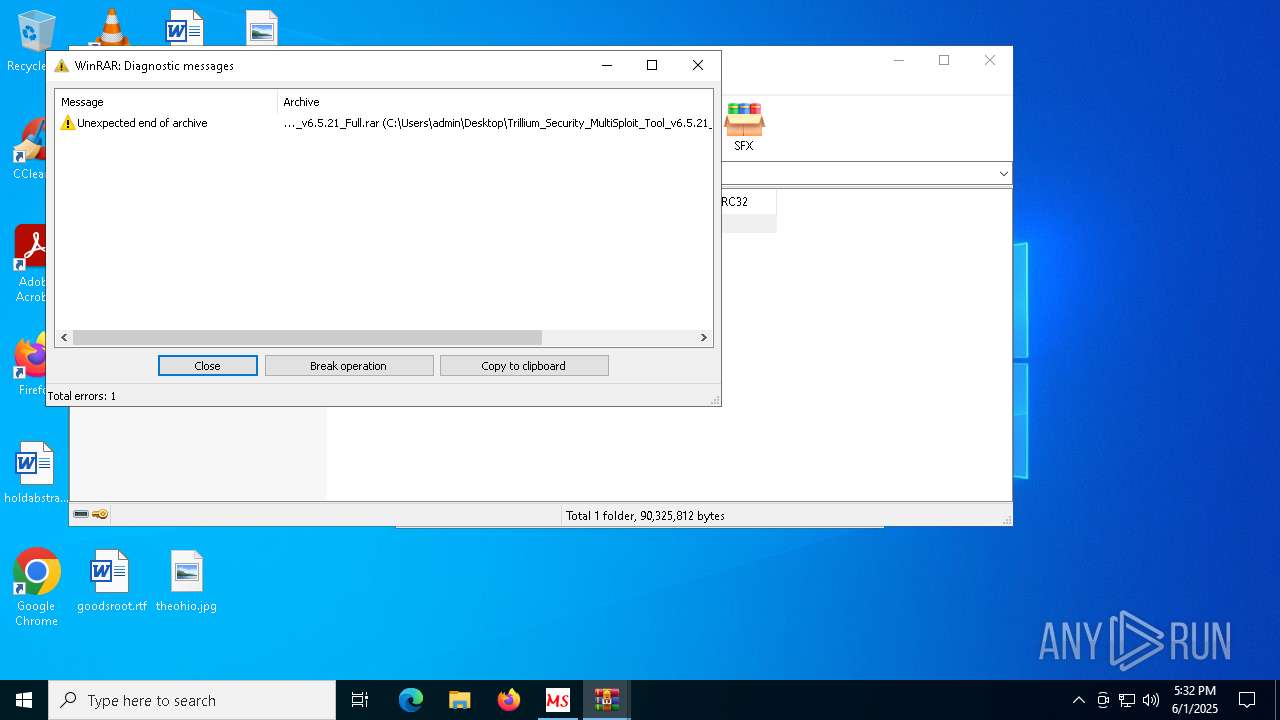
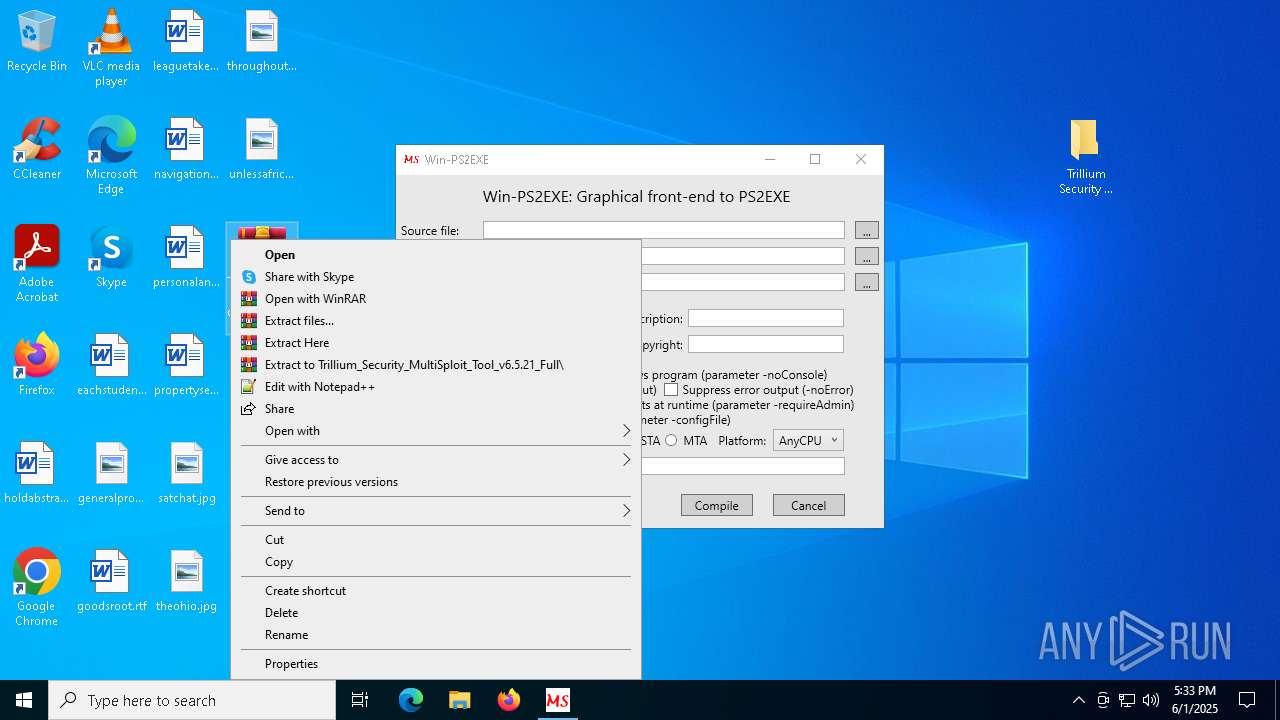
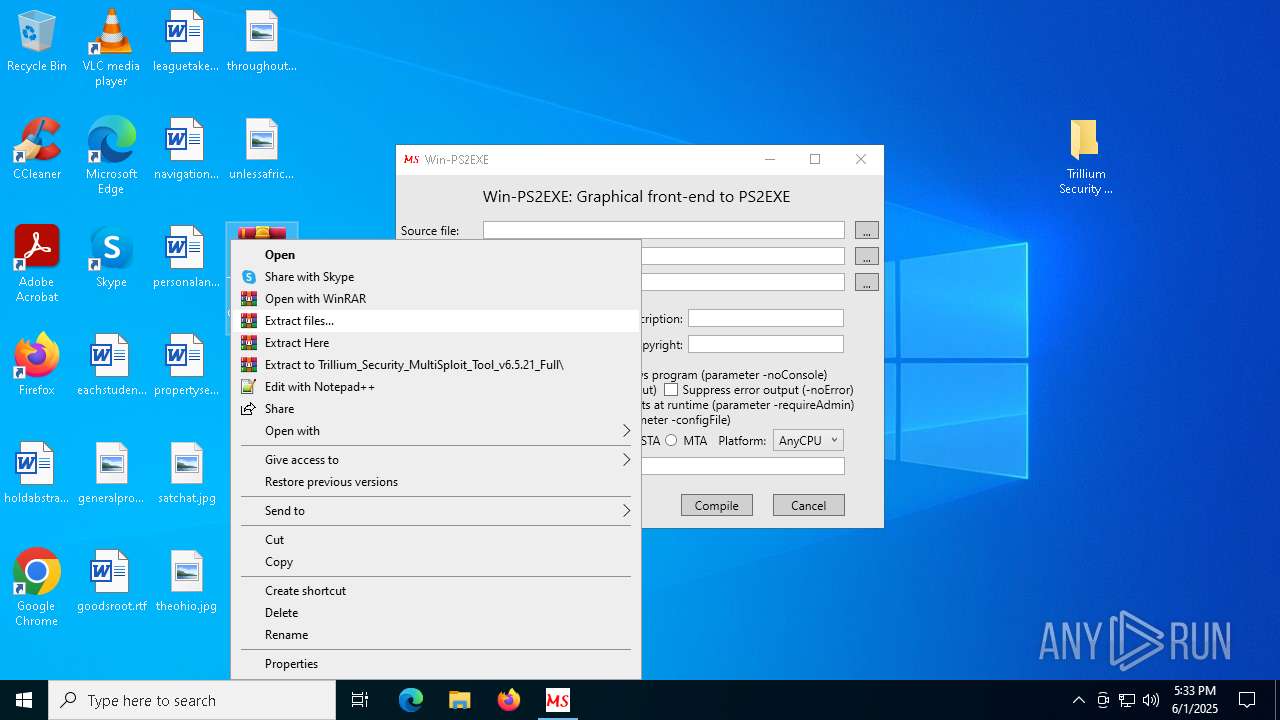
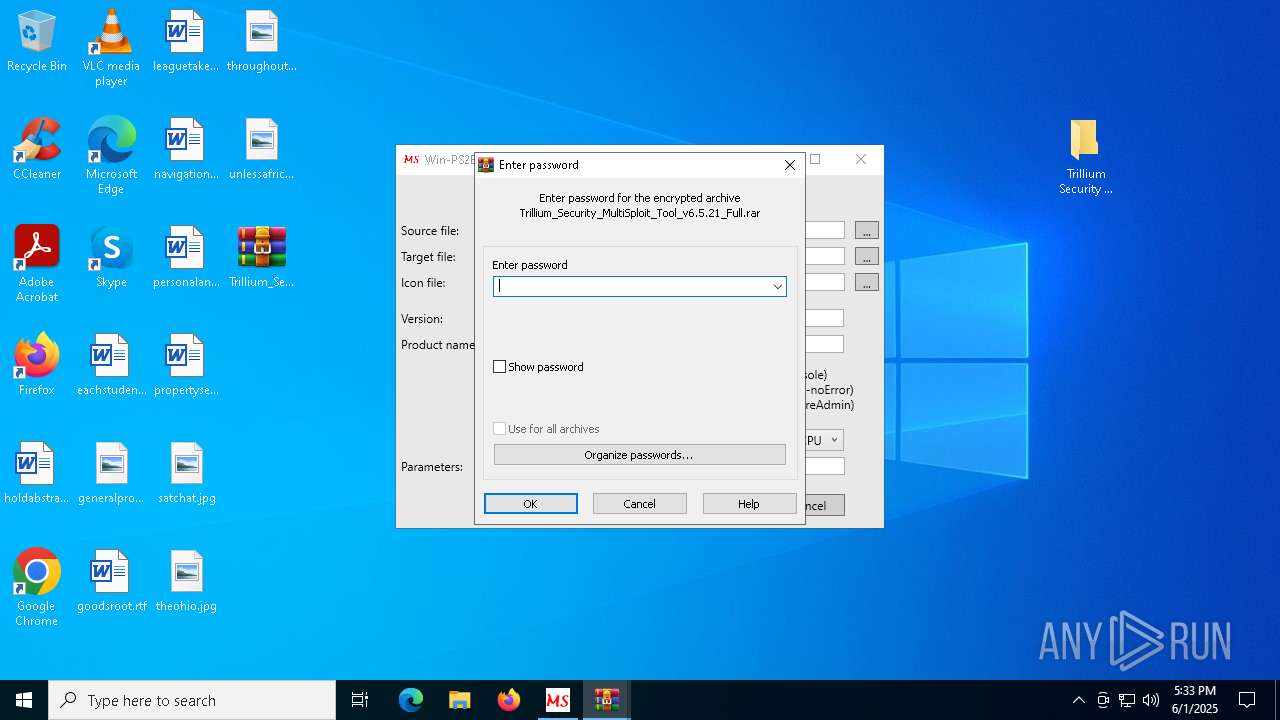
| 2092 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\Trillium_Security_MultiSploit_Tool_v6.5.21_Full.rar" C:\Users\admin\Desktop\ | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 4008 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6072 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) | |||||||||||||||
| 6132 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\Trillium_Security_MultiSploit_Tool_v6.5.21_Full.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 6584 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7572 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 8028 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\Trillium_Security_MultiSploit_Tool_v6.5.21_Full.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
4 114
Read events
4 078
Write events
36
Delete events
0
Modification events
| (PID) Process: | (6132) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6132) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6132) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6132) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Trillium_Security_MultiSploit_Tool_v6.5.21_Full.rar | |||
| (PID) Process: | (6132) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6132) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6132) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6132) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6132) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (6132) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
Executable files
36
Suspicious files
92
Text files
391
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
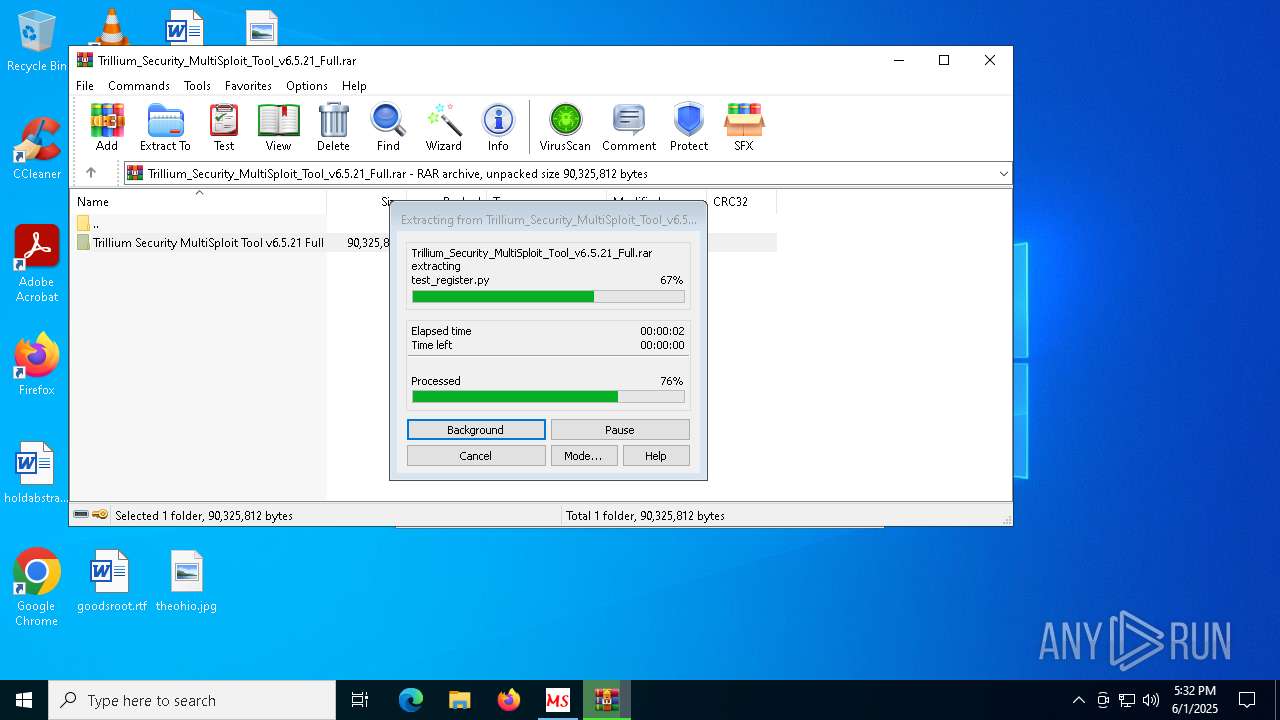
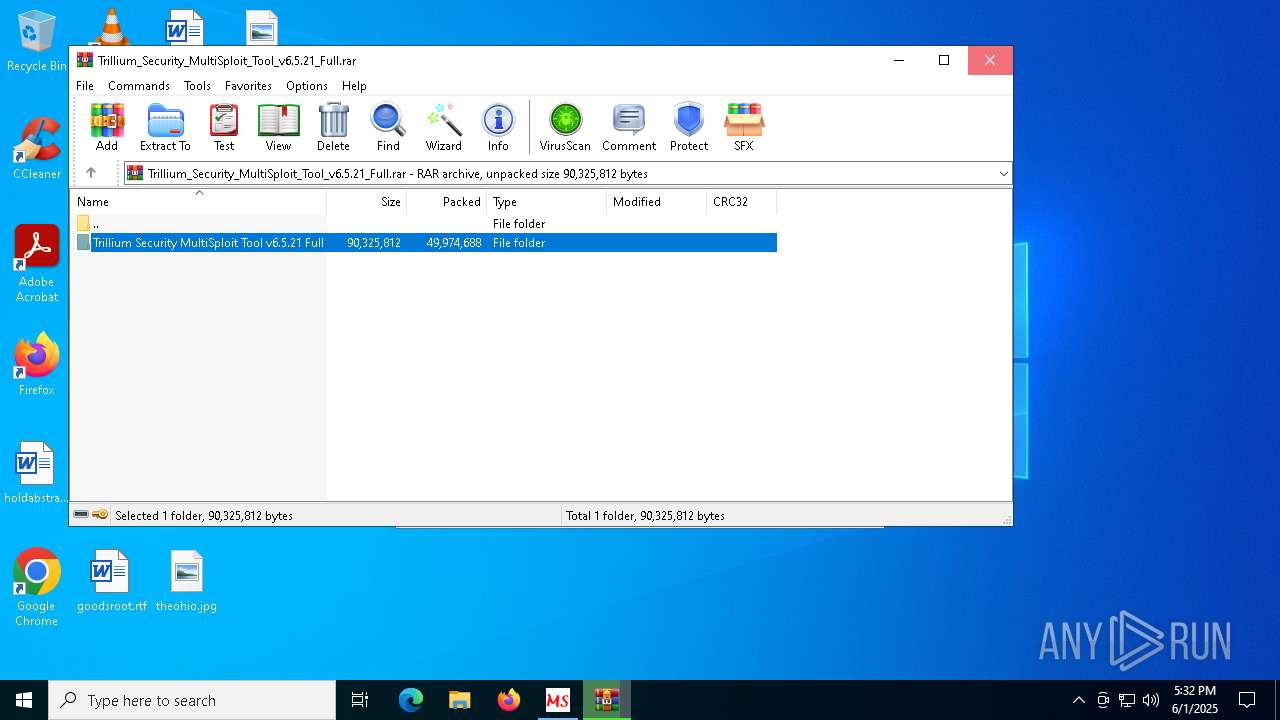
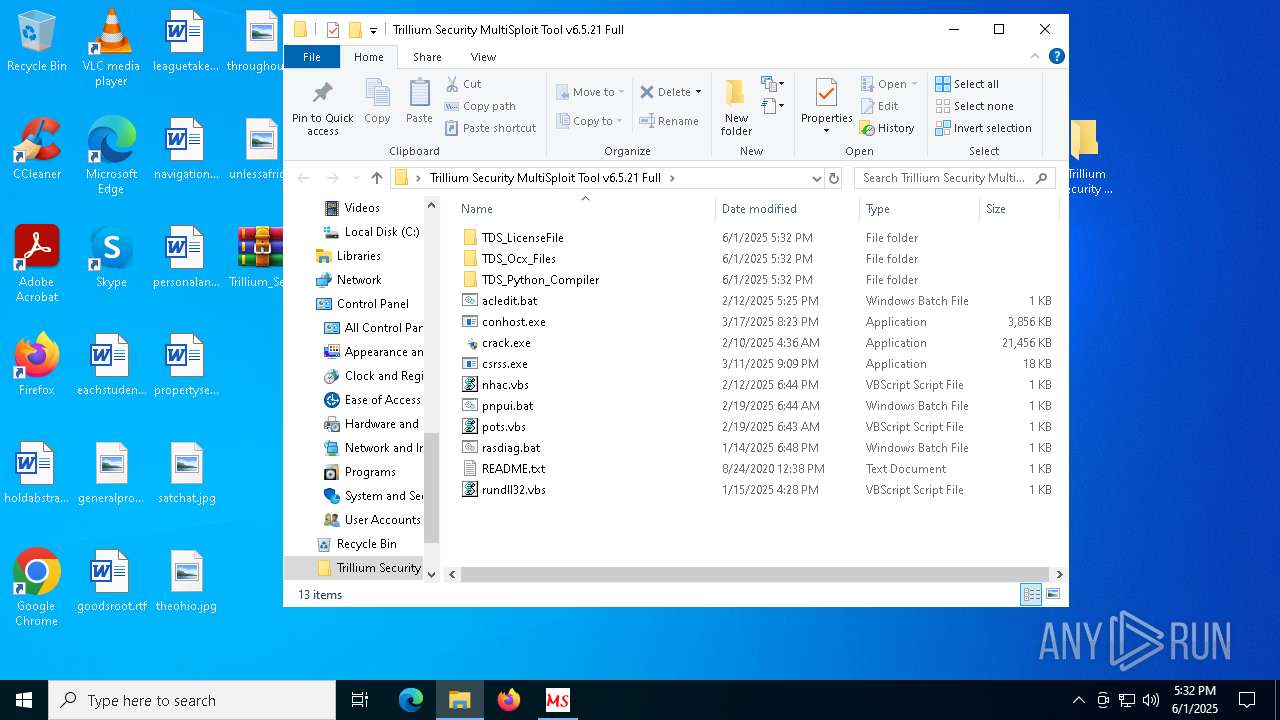
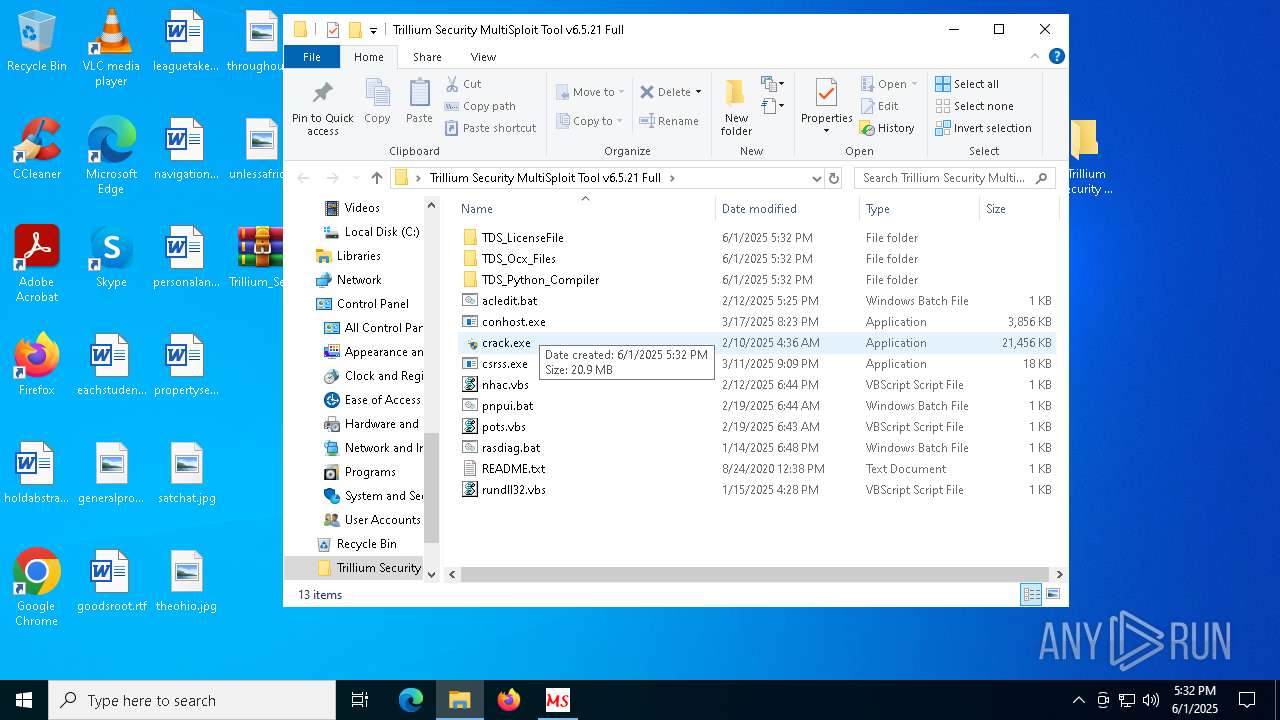
| 8028 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb8028.47508\Trillium Security MultiSploit Tool v6.5.21 Full\crack.exe | executable | |
MD5:0F60E7958CBD9F8BEAC3D89A141D112D | SHA256:BF4788424F6290A3023407D97BDB7CCE3B262B615ABE9D012C1A47FE42EC49B6 | |||
| 8028 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb8028.47508\Trillium Security MultiSploit Tool v6.5.21 Full\csrss.exe | executable | |
MD5:0E14E70C14597160AAAEABA06536191D | SHA256:269DD8A318E57E8445D23E76DB7C692B4C670840064168BBD1A221B363B9EE6F | |||
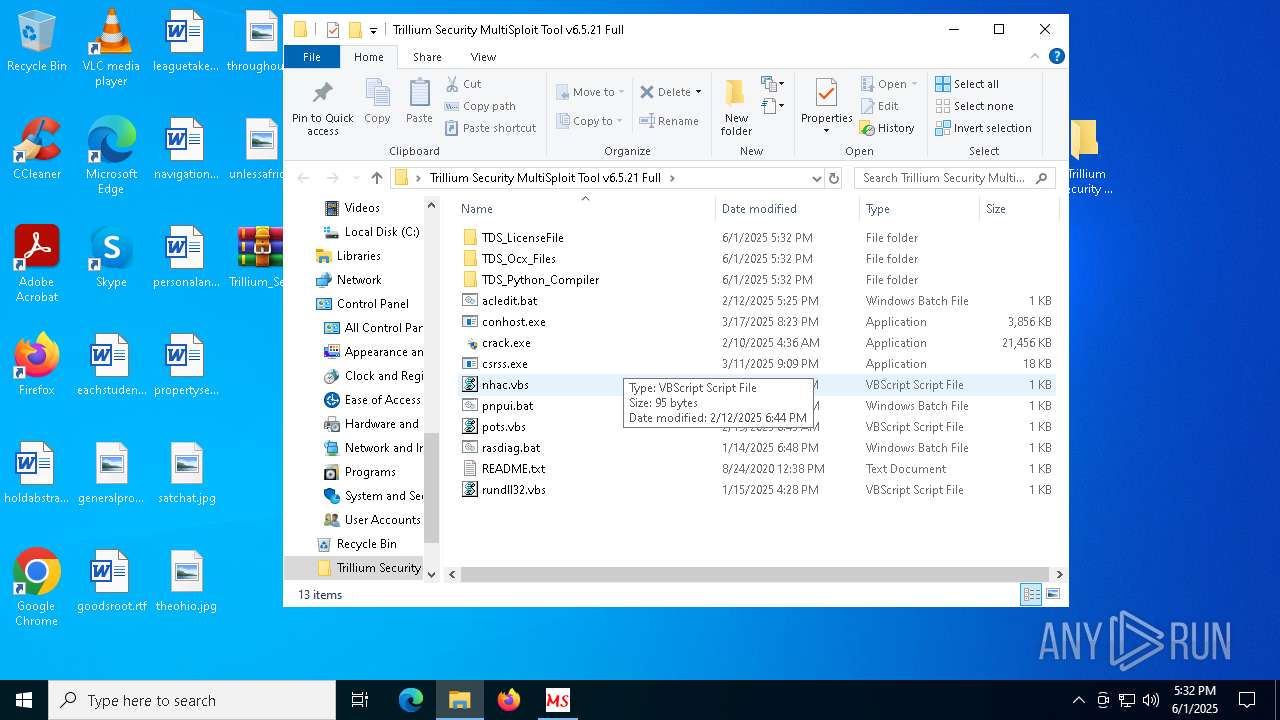
| 8028 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb8028.47508\Trillium Security MultiSploit Tool v6.5.21 Full\nhac.vbs | text | |
MD5:5929A32F53268FB5DA65837D95390F05 | SHA256:AE1E366C62776646980F0DBA9AE6107A0842827E3FF26A3486F685646BF1A523 | |||
| 8028 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb8028.47508\Trillium Security MultiSploit Tool v6.5.21 Full\rundll32.vbs | text | |
MD5:6A18E846C6BE9B68DA2448EC4D6F9CC4 | SHA256:CFB13E7F03514BC8C1558A8D7819037185C530F2DA645897ADBE22CD30D56C2A | |||
| 8028 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb8028.47508\Trillium Security MultiSploit Tool v6.5.21 Full\TDS_Ocx_Files\Trillium_Security_OCX_Registrator.exe | executable | |
MD5:0732C318475AD1197E9B4191B912A514 | SHA256:B2E7D11309C60AEF82B52F3244C14BBC999905B6A25EE3E127D55F463C4C2482 | |||
| 8028 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb8028.47508\Trillium Security MultiSploit Tool v6.5.21 Full\pnpui.bat | text | |
MD5:9EA1BB4FF775243C97272F9FC14F7658 | SHA256:FC711EC126E0A47BCF178AFFD6A72A0A65785A608D7EDB85A682150583FC7273 | |||
| 8028 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb8028.47508\Trillium Security MultiSploit Tool v6.5.21 Full\TDS_Ocx_Files\Codejock.CommandBars.Unicode.v15.2.1.ocx | executable | |
MD5:B4379ADDC623DE30530471F91072921D | SHA256:0EB80EC5D996FB90B93FE8306CED53EE4CA67CA8A767C1693205296775C4E2A7 | |||
| 8028 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb8028.47508\Trillium Security MultiSploit Tool v6.5.21 Full\rasdiag.bat | text | |
MD5:B791442311C4FFBE2471DF0EB834BAC1 | SHA256:62FA167C45C5535D931711A3572716FC029534F5CDF90D77A23947C6A534A499 | |||
| 8028 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb8028.47508\Trillium Security MultiSploit Tool v6.5.21 Full\README.txt | text | |
MD5:7F9417CCB22A0DD79C477ED8AD9F8422 | SHA256:AAD6B1EC76D47FDD6914A7AFCA3CE2C557EF5ACA0E5E015976759BCA019A016F | |||
| 8028 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb8028.47508\Trillium Security MultiSploit Tool v6.5.21 Full\TDS_LicenseFile\user_license.bin | binary | |
MD5:60873A125FB0D8EE23BFCDFAEED1D12E | SHA256:74A9F507D1A840BB02FF040A2D36F722F1CC9CACEBA47BF66812B2A4C6238962 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
35
DNS requests
19
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7512 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
3096 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
3096 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
7548 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 40.126.31.0:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
5496 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6544 | svchost.exe | 20.190.159.75:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |