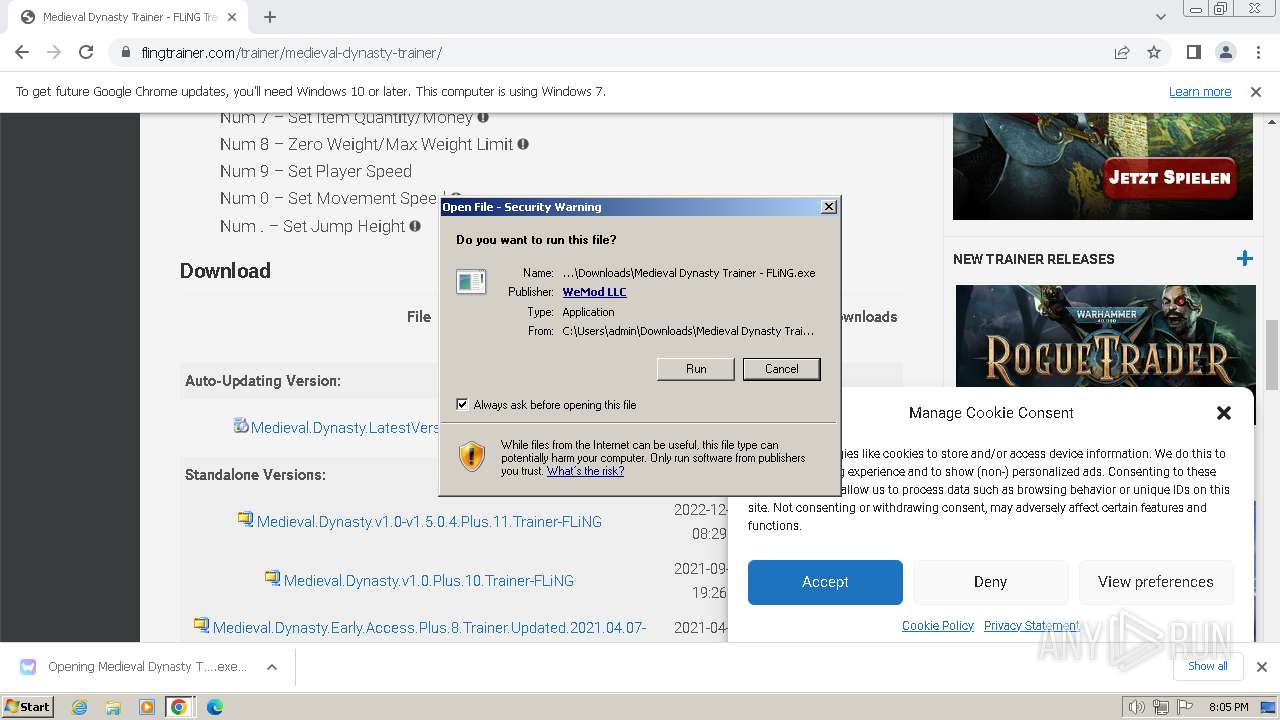
| URL: | https://flingtrainer.com/trainer/medieval-dynasty-trainer/ |
| Full analysis: | https://app.any.run/tasks/ac4f7f78-dbea-4abd-8a97-f2ef48eae0d9 |
| Verdict: | Malicious activity |
| Analysis date: | January 02, 2024, 20:04:44 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 477387A655DBCD75592E82386EF0CCBD |
| SHA1: | B39B8C1AF5EBE2476C056BF6AEA68F81C1A1B246 |
| SHA256: | 8935BBF9EDBFFBD1FB8D002132B021E860C602E4805D734C20A060C2BCE3FB71 |
| SSDEEP: | 3:N8ILSZAEMLBlT0RXEm:2VhMN50t |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads Microsoft Outlook installation path
- Medieval Dynasty Trainer - FLiNG.exe (PID: 3640)
Reads the Internet Settings
- Medieval Dynasty Trainer - FLiNG.exe (PID: 3640)
Reads security settings of Internet Explorer
- Medieval Dynasty Trainer - FLiNG.exe (PID: 3640)
Checks Windows Trust Settings
- Medieval Dynasty Trainer - FLiNG.exe (PID: 3640)
Reads settings of System Certificates
- Medieval Dynasty Trainer - FLiNG.exe (PID: 3640)
Reads Internet Explorer settings
- Medieval Dynasty Trainer - FLiNG.exe (PID: 3640)
INFO
Application launched itself
- iexplore.exe (PID: 120)
- chrome.exe (PID: 1784)
Reads the computer name
- Medieval Dynasty Trainer - FLiNG.exe (PID: 3640)
Checks supported languages
- Medieval Dynasty Trainer - FLiNG.exe (PID: 3640)
The process uses the downloaded file
- chrome.exe (PID: 292)
- chrome.exe (PID: 1784)
Drops the executable file immediately after the start
- chrome.exe (PID: 2332)
- chrome.exe (PID: 1784)
Manual execution by a user
- chrome.exe (PID: 1784)
Checks proxy server information
- Medieval Dynasty Trainer - FLiNG.exe (PID: 3640)
Reads the machine GUID from the registry
- Medieval Dynasty Trainer - FLiNG.exe (PID: 3640)
Creates files or folders in the user directory
- Medieval Dynasty Trainer - FLiNG.exe (PID: 3640)
Reads Environment values
- Medieval Dynasty Trainer - FLiNG.exe (PID: 3640)
Create files in a temporary directory
- Medieval Dynasty Trainer - FLiNG.exe (PID: 3640)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
58
Monitored processes
24
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 120 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://flingtrainer.com/trainer/medieval-dynasty-trainer/" | C:\Program Files\Internet Explorer\iexplore.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 292 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=4868 --field-trial-handle=1204,i,1652333663597689371,628985636997329199,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 392 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:120 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 664 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2244 --field-trial-handle=1204,i,1652333663597689371,628985636997329199,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 908 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=3452 --field-trial-handle=1204,i,1652333663597689371,628985636997329199,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 952 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=12 --mojo-platform-channel-handle=3420 --field-trial-handle=1204,i,1652333663597689371,628985636997329199,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1768 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --first-renderer-process --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=2104 --field-trial-handle=1204,i,1652333663597689371,628985636997329199,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1784 | "C:\Program Files\Google\Chrome\Application\chrome.exe" "--disable-features=OptimizationGuideModelDownloading,OptimizationHintsFetching,OptimizationTargetPrediction,OptimizationHints" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1928 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=109.0.5414.120 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd4,0x6e4d8b38,0x6e4d8b48,0x6e4d8b54 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 2332 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=1372 --field-trial-handle=1204,i,1652333663597689371,628985636997329199,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
Total events
22 577
Read events
22 437
Write events
139
Delete events
1
Modification events
| (PID) Process: | (120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (120) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
4
Suspicious files
156
Text files
94
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 392 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\103621DE9CD5414CC2538780B4B75751 | der | |
MD5:60FE01DF86BE2E5331B0CDBE86165686 | SHA256:C08CCBC876CD5A7CDFA9670F9637DA57F6A1282198A9BC71FC7D7247A6E5B7A8 | |||
| 392 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\wpautoterms[1].css | text | |
MD5:58BE32B1DE9286357161BD2936231A4F | SHA256:2721CB3BE7704BE75A403489D609671FAB74269A881CA8B62F1B47F118C02A76 | |||
| 392 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:60642349EEFAEBAA9A82542643B5407B | SHA256:1937BB73F9FE4532C5E173725ED58B1D4E00D7D78F04602DD8EE9C6264C45342 | |||
| 392 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:AC05D27423A85ADC1622C714F2CB6184 | SHA256:C6456E12E5E53287A547AF4103E0397CB9697E466CF75844312DC296D43D144D | |||
| 392 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\1B1495DD322A24490E2BF2FAABAE1C61 | binary | |
MD5:DEC6BBE308EB44937F77160A25EE32DB | SHA256:68A71DE28F488586C2B169F4652347E0A1FD632D48A6D6725393607BFA18BC7E | |||
| 392 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:F934A880FAE8075BB1976973B4AE810A | SHA256:339F70A7C37FEB5012B9FDDAF031EE9E551E04F283F2D8CB4FFB4CDEDD03486E | |||
| 392 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:5A49C67713EB33F89F04E7F19DC5401B | SHA256:B5D6C9F1ED61C8B8D53F983D8BFD267C6824CC236CB13410A84731B49C497951 | |||
| 392 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\QQDHICYI.txt | text | |
MD5:A6D72017A86B42B9F278A378AA0C58BD | SHA256:526DE1502A6F2783EA2A80A7F7319EA811AD6166C21EF651B72A1DECFAA9F80F | |||
| 392 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar185.tmp | binary | |
MD5:9C0C641C06238516F27941AA1166D427 | SHA256:4276AF3669A141A59388BC56A87F6614D9A9BDDDF560636C264219A7EB11256F | |||
| 392 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar183.tmp | binary | |
MD5:9C0C641C06238516F27941AA1166D427 | SHA256:4276AF3669A141A59388BC56A87F6614D9A9BDDDF560636C264219A7EB11256F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
17
TCP/UDP connections
77
DNS requests
76
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
392 | iexplore.exe | GET | 200 | 23.50.131.196:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?53bfb7cf8a6cf97e | unknown | compressed | 4.66 Kb | unknown |
392 | iexplore.exe | GET | 200 | 23.50.131.196:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?129d20c84d8c4223 | unknown | compressed | 4.66 Kb | unknown |
392 | iexplore.exe | GET | 200 | 23.50.131.196:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?6b21170b0e7a1648 | unknown | compressed | 65.2 Kb | unknown |
392 | iexplore.exe | GET | 200 | 23.50.131.196:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?947fb26d7412b1b7 | unknown | compressed | 65.2 Kb | unknown |
392 | iexplore.exe | GET | 200 | 69.192.161.44:80 | http://x1.c.lencr.org/ | unknown | binary | 717 b | unknown |
392 | iexplore.exe | GET | 200 | 69.192.161.44:80 | http://x2.c.lencr.org/ | unknown | binary | 300 b | unknown |
392 | iexplore.exe | GET | 200 | 216.58.212.131:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | unknown | binary | 724 b | unknown |
392 | iexplore.exe | GET | 200 | 216.58.212.131:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
392 | iexplore.exe | GET | 200 | 216.58.212.131:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEDEixfO34qnbCeE6N8VMp00%3D | unknown | binary | 471 b | unknown |
392 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | unknown | binary | 1.47 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
392 | iexplore.exe | 188.114.97.3:443 | flingtrainer.com | CLOUDFLARENET | NL | unknown |
392 | iexplore.exe | 23.50.131.196:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
392 | iexplore.exe | 69.192.161.44:80 | x1.c.lencr.org | AKAMAI-AS | DE | unknown |
392 | iexplore.exe | 142.250.184.202:443 | fonts.googleapis.com | GOOGLE | US | whitelisted |
392 | iexplore.exe | 192.0.80.242:443 | gravatar.com | AUTOMATTIC | US | unknown |
392 | iexplore.exe | 216.58.206.34:443 | pagead2.googlesyndication.com | GOOGLE | US | unknown |
392 | iexplore.exe | 172.217.16.132:443 | www.google.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
flingtrainer.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
x2.c.lencr.org |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
gravatar.com |
| whitelisted |
pagead2.googlesyndication.com |
| whitelisted |
api.wemod.com |
| unknown |
www.google.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |