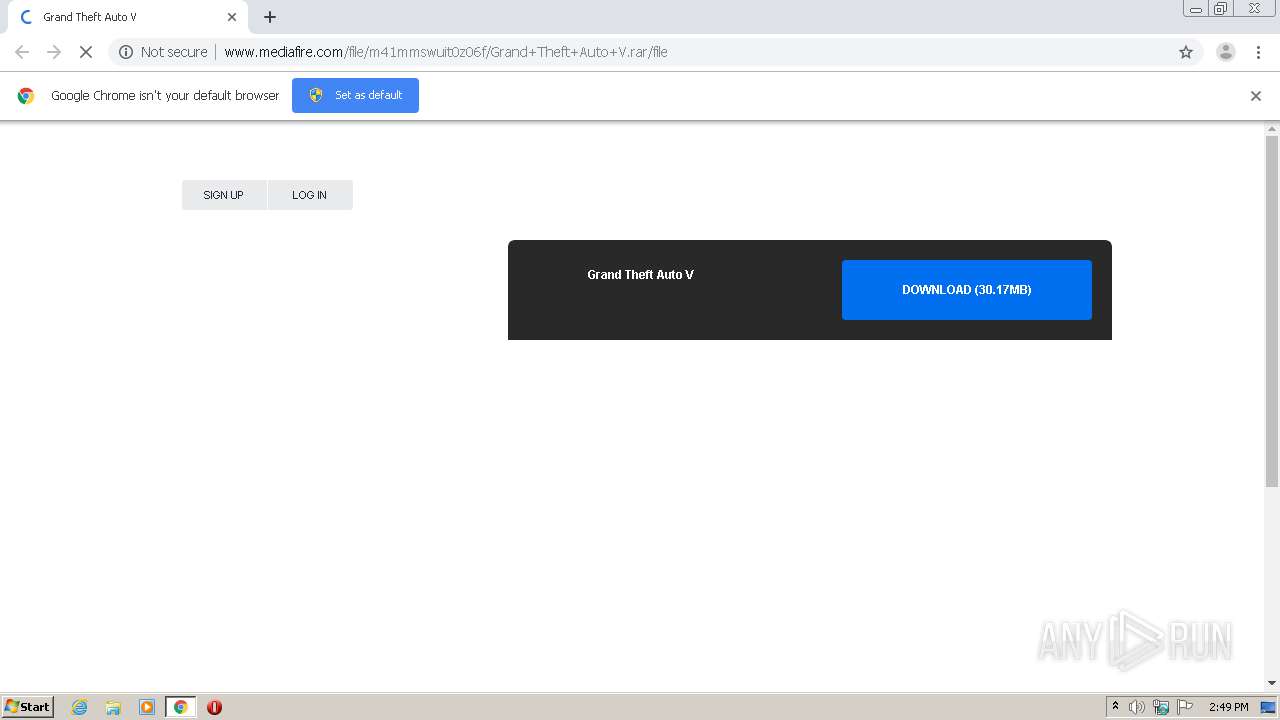
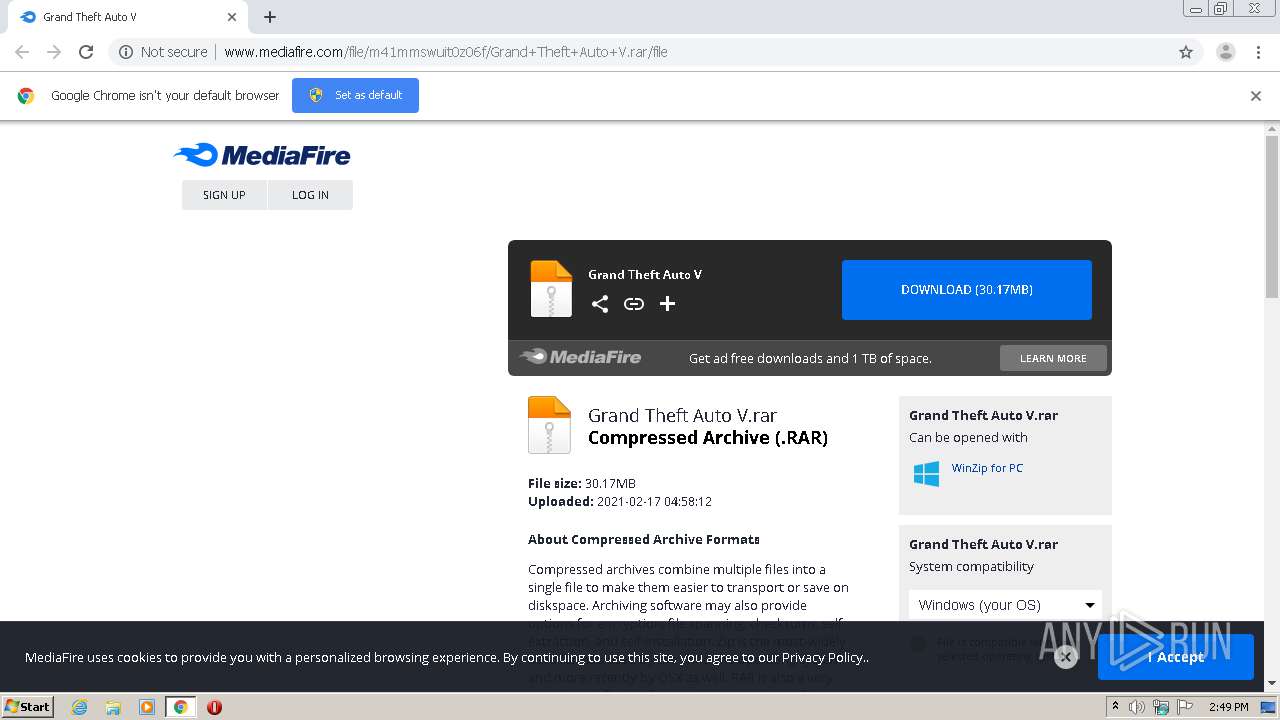
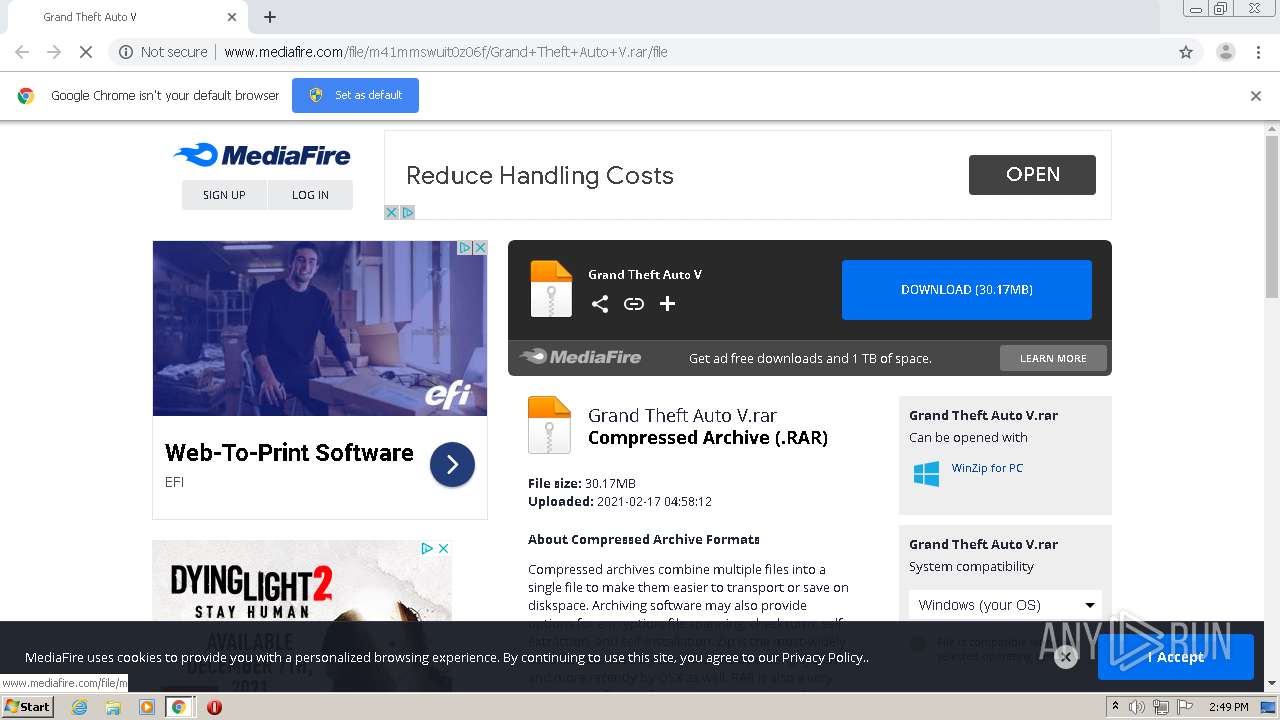
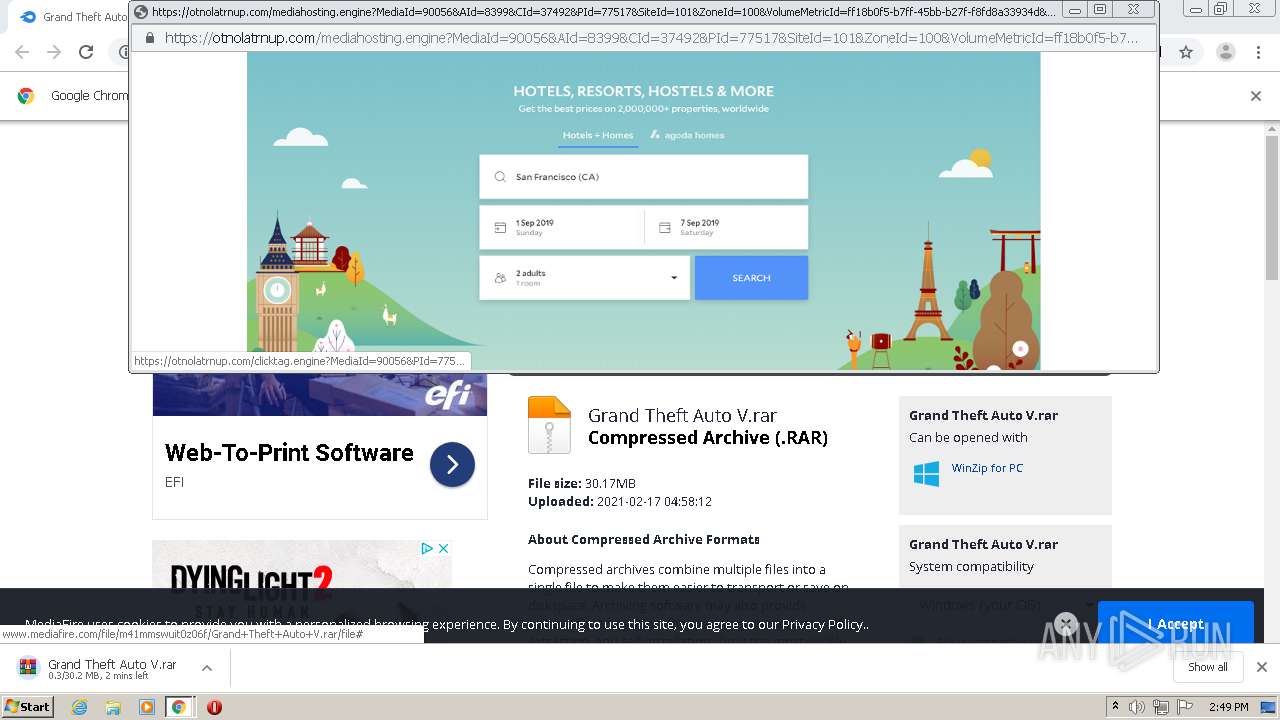
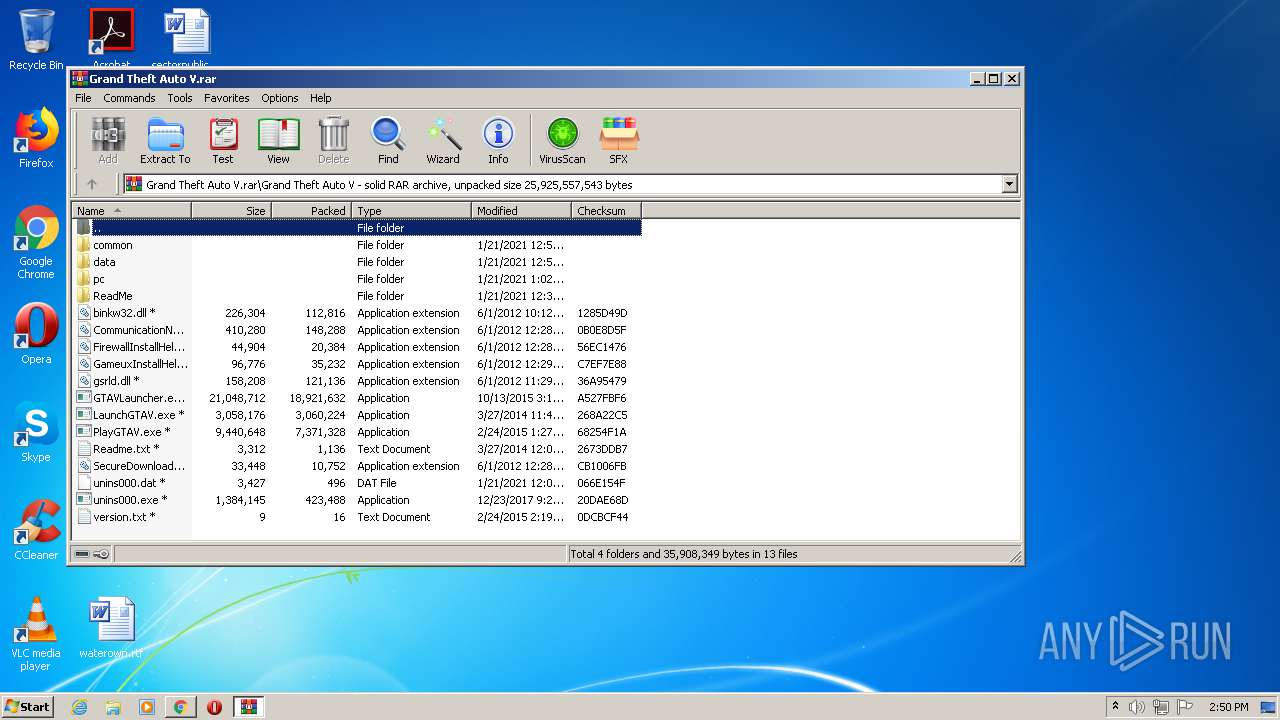
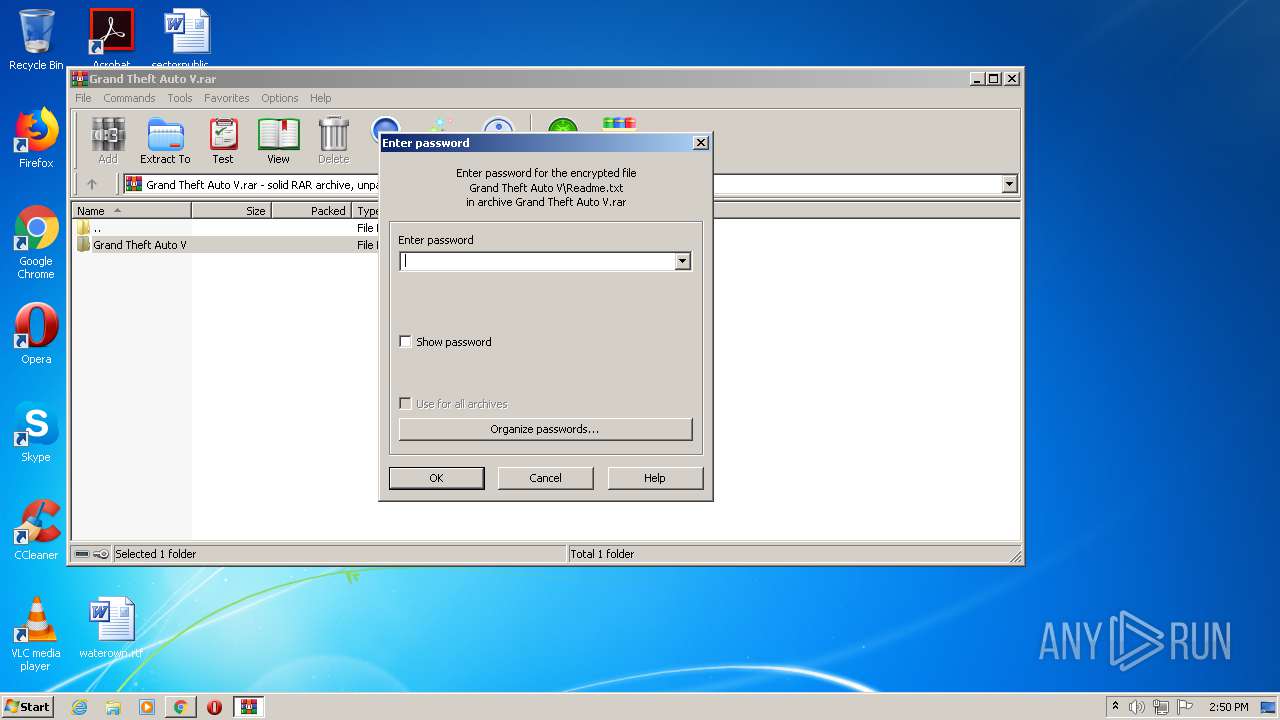
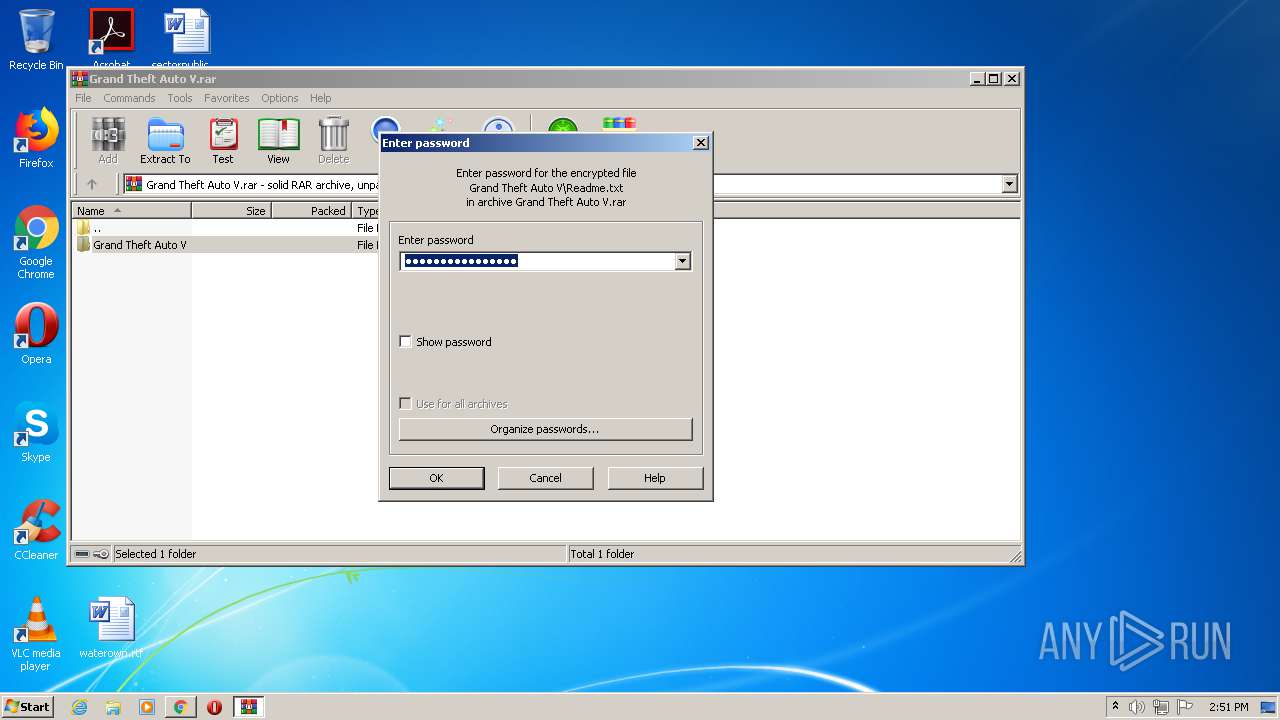
| URL: | http://www.mediafire.com/file/m41mmswuit0z06f/Grand+Theft+Auto+V.rar/file |
| Full analysis: | https://app.any.run/tasks/724b1fe7-34cb-475e-b6aa-8cb676ce122d |
| Verdict: | Malicious activity |
| Analysis date: | June 12, 2021, 13:49:05 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | FFA2DE1950CB8995A2C1EEA128D007E4 |
| SHA1: | 8B1A1A9900D6148F5EC1DC0A95F55750EAC00046 |
| SHA256: | 892BD3E76DD7C8CCFA1E6F2367831E21B2D56F48079BDB30A579F71A6014B823 |
| SSDEEP: | 3:N1KJS4w3eGUosUcSNgOS6OYIA:Cc4w3eGwsyFA |
MALICIOUS
No malicious indicators.SUSPICIOUS
Drops a file with a compile date too recent
- WinRAR.exe (PID: 3220)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3220)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 3220)
Drops a file with too old compile date
- WinRAR.exe (PID: 3220)
INFO
Application launched itself
- chrome.exe (PID: 2504)
Reads the hosts file
- chrome.exe (PID: 2504)
- chrome.exe (PID: 2376)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
78
Monitored processes
40
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 352 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=972,3058781329655364157,10011870262999515417,131072 --enable-features=PasswordImport --disable-gpu-sandbox --use-gl=disabled --gpu-preferences=KAAAAAAAAADgACAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=5018854332753575371 --mojo-platform-channel-handle=5044 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 920 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=972,3058781329655364157,10011870262999515417,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=3445370618491512799 --renderer-client-id=35 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4796 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 928 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=972,3058781329655364157,10011870262999515417,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=8286561231854823330 --renderer-client-id=26 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3860 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1328 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=75.0.3770.100 --initial-client-data=0x7c,0x80,0x84,0x78,0x88,0x6c55a9d0,0x6c55a9e0,0x6c55a9ec | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1428 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=972,3058781329655364157,10011870262999515417,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=17318600635675298671 --renderer-client-id=28 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4760 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1704 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=972,3058781329655364157,10011870262999515417,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=16345535723891248025 --renderer-client-id=13 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3956 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1724 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=972,3058781329655364157,10011870262999515417,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=328599884091009658 --renderer-client-id=16 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4292 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1748 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=972,3058781329655364157,10011870262999515417,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAADgACAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=16835407459362337680 --mojo-platform-channel-handle=1044 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1788 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=972,3058781329655364157,10011870262999515417,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=15244641929083080556 --renderer-client-id=8 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2332 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1992 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=972,3058781329655364157,10011870262999515417,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=14782442190136497186 --mojo-platform-channel-handle=4880 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
1 450
Read events
1 342
Write events
105
Delete events
3
Modification events
| (PID) Process: | (2504) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2504) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2504) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (2504) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (2504) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2676) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 2504-13267979362802875 |
Value: 259 | |||
| (PID) Process: | (2504) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (2504) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (2504) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3252-13245750958665039 |
Value: 0 | |||
| (PID) Process: | (2504) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
Executable files
10
Suspicious files
66
Text files
113
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2504 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-60C4BB63-9C8.pma | — | |
MD5:— | SHA256:— | |||
| 2504 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\da249647-74b2-4073-b66f-878b4db46bbb.tmp | — | |
MD5:— | SHA256:— | |||
| 2504 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000048.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2504 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2504 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Platform Notifications\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2504 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF141ba4.TMP | text | |
MD5:— | SHA256:— | |||
| 2504 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Feature Engagement Tracker\AvailabilityDB\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2504 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Feature Engagement Tracker\AvailabilityDB\LOG.old~RF141c9e.TMP | text | |
MD5:— | SHA256:— | |||
| 2504 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2504 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old~RF141e83.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
28
TCP/UDP connections
157
DNS requests
129
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2376 | chrome.exe | GET | 200 | 104.17.166.186:80 | http://6.adsco.re/ | US | — | — | whitelisted |
2376 | chrome.exe | GET | 200 | 104.17.166.186:80 | http://6.adsco.re/ | US | — | — | whitelisted |
2376 | chrome.exe | GET | 200 | 104.16.202.237:80 | http://www.mediafire.com/file/m41mmswuit0z06f/Grand+Theft+Auto+V.rar/file | US | html | 81.1 Kb | shared |
2376 | chrome.exe | GET | 200 | 142.250.186.46:80 | http://translate.google.com/translate_a/element.js?cb=googFooterTranslate | US | text | 3.68 Kb | whitelisted |
2376 | chrome.exe | GET | 200 | 104.16.202.237:80 | http://www.mediafire.com/js/prebid2.44.1.js | US | text | 52.9 Kb | shared |
2376 | chrome.exe | POST | 200 | 185.33.221.53:80 | http://ib.adnxs.com/ut/v3/prebid | unknown | text | 239 b | whitelisted |
2376 | chrome.exe | GET | 200 | 104.16.203.237:80 | http://static.mediafire.com/images/backgrounds/download/apps_list_sprite-v4.png | US | image | 6.78 Kb | shared |
2376 | chrome.exe | POST | 200 | 185.33.221.53:80 | http://ib.adnxs.com/ut/v3/prebid | unknown | text | 253 b | whitelisted |
2376 | chrome.exe | GET | 200 | 162.252.214.5:80 | http://4.adsco.re/ | US | text | 63 b | whitelisted |
2376 | chrome.exe | GET | 200 | 104.17.166.186:80 | http://c.adsco.re/ | US | html | 13.5 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2376 | chrome.exe | 142.250.185.200:443 | www.googletagmanager.com | Google Inc. | US | suspicious |
2376 | chrome.exe | 142.250.186.174:443 | fundingchoicesmessages.google.com | Google Inc. | US | whitelisted |
2376 | chrome.exe | 142.250.185.162:443 | securepubads.g.doubleclick.net | Google Inc. | US | whitelisted |
2376 | chrome.exe | 142.250.186.46:80 | translate.google.com | Google Inc. | US | whitelisted |
2376 | chrome.exe | 185.33.221.53:80 | ib.adnxs.com | AppNexus, Inc | — | unknown |
2376 | chrome.exe | 104.16.94.65:443 | static.cloudflareinsights.com | Cloudflare Inc | US | shared |
2376 | chrome.exe | 35.244.159.8:443 | mediafire-d.openx.net | — | US | whitelisted |
2376 | chrome.exe | 104.16.68.69:443 | dmx.districtm.io | Cloudflare Inc | US | shared |
2376 | chrome.exe | 104.16.203.237:80 | www.mediafire.com | Cloudflare Inc | US | unknown |
2376 | chrome.exe | 142.250.186.78:443 | clients1.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.mediafire.com |
| shared |
accounts.google.com |
| shared |
safebrowsing.googleapis.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
fundingchoicesmessages.google.com |
| whitelisted |
securepubads.g.doubleclick.net |
| whitelisted |
c.aaxads.com |
| whitelisted |
translate.google.com |
| whitelisted |
static.mediafire.com |
| shared |
static.cloudflareinsights.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2376 | chrome.exe | Attempted User Privilege Gain | ET INFO Session Traversal Utilities for NAT (STUN Binding Request) |
— | — | Attempted User Privilege Gain | ET INFO Session Traversal Utilities for NAT (STUN Binding Request) |
— | — | Attempted User Privilege Gain | ET INFO Session Traversal Utilities for NAT (STUN Binding Request) |
— | — | Attempted User Privilege Gain | ET INFO Session Traversal Utilities for NAT (STUN Binding Response) |
2376 | chrome.exe | Attempted User Privilege Gain | ET INFO Session Traversal Utilities for NAT (STUN Binding Response) |
— | — | Attempted User Privilege Gain | ET INFO Session Traversal Utilities for NAT (STUN Binding Response) |
2376 | chrome.exe | Generic Protocol Command Decode | SURICATA HTTP unable to match response to request |