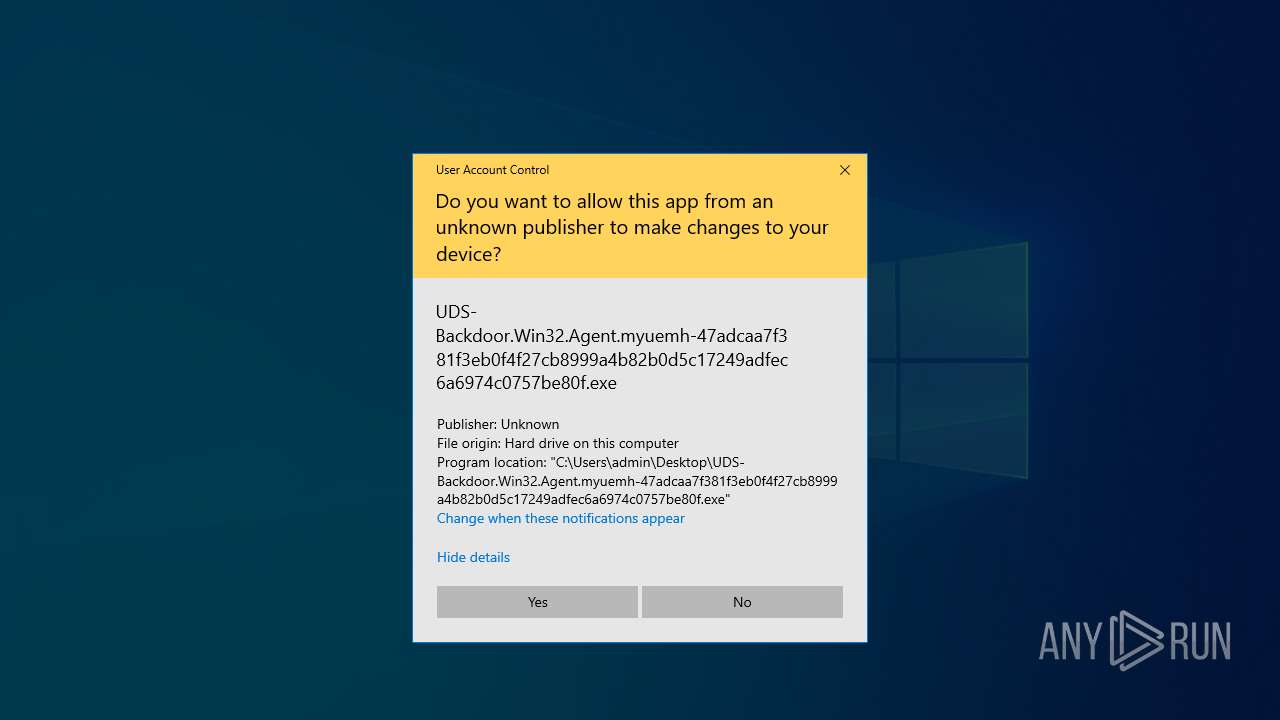
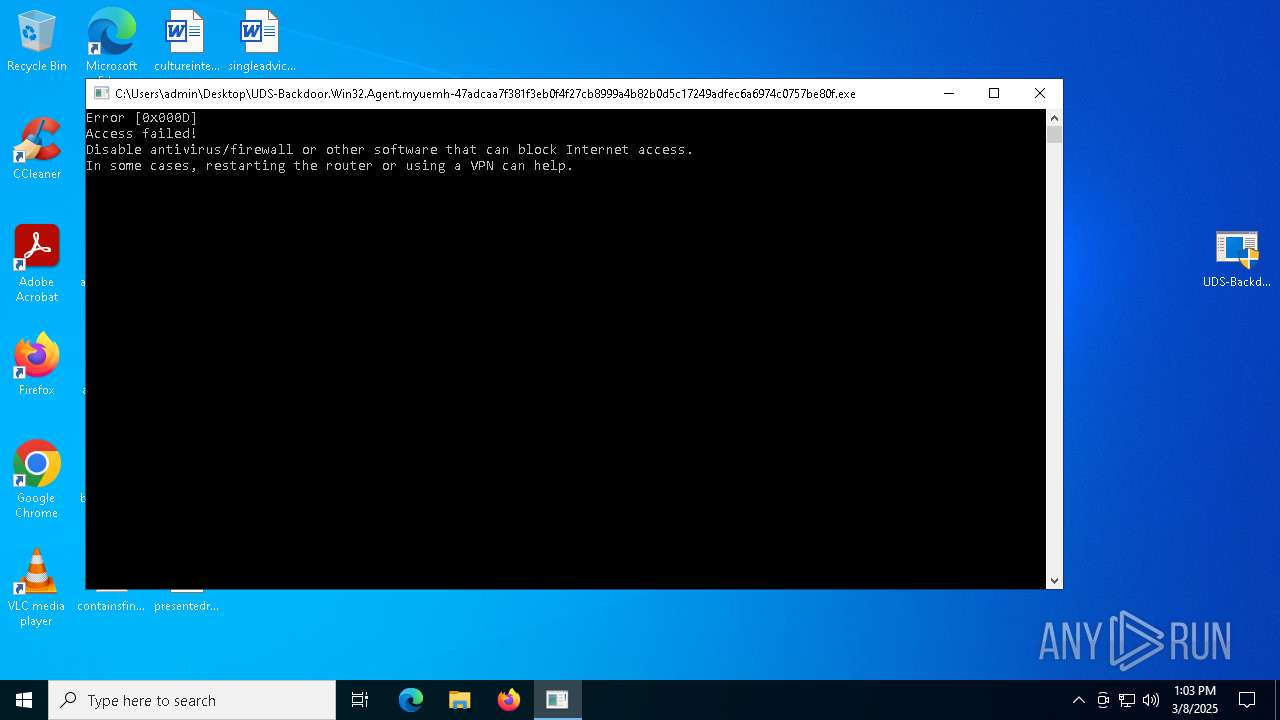
| File name: | UDS-Backdoor.Win32.Agent.myuemh-47adcaa7f381f3eb0f4f27cb8999a4b82b0d5c17249adfec6a6974c0757be80f.7z |
| Full analysis: | https://app.any.run/tasks/1e711aa4-ece2-49da-b5b8-6ec5ebb7df1b |
| Verdict: | Malicious activity |
| Analysis date: | March 08, 2025, 13:03:30 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | F3EBB1BB0F17AE3F143BFEB7D406C74F |
| SHA1: | F8A94A28C256A3C52C25BB173B539274EA804E98 |
| SHA256: | 892729652C05E580C834464D5E96E3D448F089B3CCFE0DDFE2373C1EDBD4659D |
| SSDEEP: | 98304:u/3p3QeHlXiUjO70qNRThDsXJoxJV8F6T860YB9gQyp6cgD/KswV9tWEyS1Jx1tx:VGsWS2SlSKi7Yw/cTp8j |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 7356)
SUSPICIOUS
Reads the BIOS version
- UDS-Backdoor.Win32.Agent.myuemh-47adcaa7f381f3eb0f4f27cb8999a4b82b0d5c17249adfec6a6974c0757be80f.exe (PID: 8180)
Reads security settings of Internet Explorer
- UDS-Backdoor.Win32.Agent.myuemh-47adcaa7f381f3eb0f4f27cb8999a4b82b0d5c17249adfec6a6974c0757be80f.exe (PID: 8180)
INFO
Creates files or folders in the user directory
- BackgroundTransferHost.exe (PID: 864)
- UDS-Backdoor.Win32.Agent.myuemh-47adcaa7f381f3eb0f4f27cb8999a4b82b0d5c17249adfec6a6974c0757be80f.exe (PID: 8180)
Reads the software policy settings
- BackgroundTransferHost.exe (PID: 864)
- UDS-Backdoor.Win32.Agent.myuemh-47adcaa7f381f3eb0f4f27cb8999a4b82b0d5c17249adfec6a6974c0757be80f.exe (PID: 8180)
Reads security settings of Internet Explorer
- BackgroundTransferHost.exe (PID: 864)
- BackgroundTransferHost.exe (PID: 1196)
- BackgroundTransferHost.exe (PID: 2236)
- BackgroundTransferHost.exe (PID: 5988)
- BackgroundTransferHost.exe (PID: 7884)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7356)
Checks proxy server information
- BackgroundTransferHost.exe (PID: 864)
- UDS-Backdoor.Win32.Agent.myuemh-47adcaa7f381f3eb0f4f27cb8999a4b82b0d5c17249adfec6a6974c0757be80f.exe (PID: 8180)
Manual execution by a user
- UDS-Backdoor.Win32.Agent.myuemh-47adcaa7f381f3eb0f4f27cb8999a4b82b0d5c17249adfec6a6974c0757be80f.exe (PID: 8180)
Process checks whether UAC notifications are on
- UDS-Backdoor.Win32.Agent.myuemh-47adcaa7f381f3eb0f4f27cb8999a4b82b0d5c17249adfec6a6974c0757be80f.exe (PID: 8180)
Reads the computer name
- UDS-Backdoor.Win32.Agent.myuemh-47adcaa7f381f3eb0f4f27cb8999a4b82b0d5c17249adfec6a6974c0757be80f.exe (PID: 8180)
Checks supported languages
- UDS-Backdoor.Win32.Agent.myuemh-47adcaa7f381f3eb0f4f27cb8999a4b82b0d5c17249adfec6a6974c0757be80f.exe (PID: 8180)
Reads the machine GUID from the registry
- UDS-Backdoor.Win32.Agent.myuemh-47adcaa7f381f3eb0f4f27cb8999a4b82b0d5c17249adfec6a6974c0757be80f.exe (PID: 8180)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|---|
| ModifyDate: | 2021:10:26 12:22:14+00:00 |
| ArchivedFileName: | UDS-Backdoor.Win32.Agent.myuemh-47adcaa7f381f3eb0f4f27cb8999a4b82b0d5c17249adfec6a6974c0757be80f.exe |
Total processes
142
Monitored processes
10
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 864 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1196 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2236 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5988 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7356 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\UDS-Backdoor.Win32.Agent.myuemh-47adcaa7f381f3eb0f4f27cb8999a4b82b0d5c17249adfec6a6974c0757be80f.7z | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 7484 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7520 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7800 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | UDS-Backdoor.Win32.Agent.myuemh-47adcaa7f381f3eb0f4f27cb8999a4b82b0d5c17249adfec6a6974c0757be80f.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7884 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 8180 | "C:\Users\admin\Desktop\UDS-Backdoor.Win32.Agent.myuemh-47adcaa7f381f3eb0f4f27cb8999a4b82b0d5c17249adfec6a6974c0757be80f.exe" | C:\Users\admin\Desktop\UDS-Backdoor.Win32.Agent.myuemh-47adcaa7f381f3eb0f4f27cb8999a4b82b0d5c17249adfec6a6974c0757be80f.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
3 642
Read events
3 605
Write events
37
Delete events
0
Modification events
| (PID) Process: | (7356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\UDS-Backdoor.Win32.Agent.myuemh-47adcaa7f381f3eb0f4f27cb8999a4b82b0d5c17249adfec6a6974c0757be80f.7z | |||
| (PID) Process: | (7356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7356) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (1196) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
Executable files
1
Suspicious files
9
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 864 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\3cd818c8-b34a-4c77-af25-d01580869a21.down_data | — | |
MD5:— | SHA256:— | |||
| 864 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\MetaData\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:B028385A98234773796C11E117B24974 | SHA256:35AB9DCC9A80FD875DA2AA3683D41CFBA1137D24FE1DE445D1CDBFF8799B02A3 | |||
| 864 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\4000f839-cdb8-420a-9bf8-dbddd6285f24.up_meta_secure | binary | |
MD5:3CDB462A4490A58C3262A853FBE0614D | SHA256:4696C87115A5C3309B1BC62E7FAA23C9D218D4F06BD434C79C17A701F1A4C2E2 | |||
| 8180 | UDS-Backdoor.Win32.Agent.myuemh-47adcaa7f381f3eb0f4f27cb8999a4b82b0d5c17249adfec6a6974c0757be80f.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\8B2B9A00839EED1DFDCCC3BFC2F5DF12 | binary | |
MD5:C9BE626E9715952E9B70F92F912B9787 | SHA256:C13E8D22800C200915F87F71C31185053E4E60CA25DE2E41E160E09CD2D815D4 | |||
| 8180 | UDS-Backdoor.Win32.Agent.myuemh-47adcaa7f381f3eb0f4f27cb8999a4b82b0d5c17249adfec6a6974c0757be80f.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\8B2B9A00839EED1DFDCCC3BFC2F5DF12 | binary | |
MD5:F5B2D1F9B3C217A5D64A65B009473B5D | SHA256:A58B6A07F7B52EA6AFF235E7D28F72A789AB3EEAA0ADDE8CB9B60988F587543B | |||
| 8180 | UDS-Backdoor.Win32.Agent.myuemh-47adcaa7f381f3eb0f4f27cb8999a4b82b0d5c17249adfec6a6974c0757be80f.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B46811C17859FFB409CF0E904A4AA8F8 | binary | |
MD5:BE4154BC8A1EAF886FCDBA8F8FA51D60 | SHA256:4E4D30427D7F06A492E19B4D427F8A2E0D23E6FF3805D6E0D1057CB48AFEDBCB | |||
| 864 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\Content\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:AD7A7F2CD8F6B61032EE00693F5E9D43 | SHA256:A4E66657A4625D0CF6407A5655E107A3DC9020F083CF764B184526C09442854F | |||
| 864 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\4000f839-cdb8-420a-9bf8-dbddd6285f24.f8045509-3f02-452e-a146-a9beb9f00cf1.down_meta | binary | |
MD5:5031E4E83938BDDB2DAEB726F4C9CED6 | SHA256:38610584AEFD50ACC28AB51082907857DD9F96A0E671D4B0B0091BC7982EAB06 | |||
| 864 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\3cd818c8-b34a-4c77-af25-d01580869a21.f8045509-3f02-452e-a146-a9beb9f00cf1.down_meta | binary | |
MD5:5031E4E83938BDDB2DAEB726F4C9CED6 | SHA256:38610584AEFD50ACC28AB51082907857DD9F96A0E671D4B0B0091BC7982EAB06 | |||
| 8180 | UDS-Backdoor.Win32.Agent.myuemh-47adcaa7f381f3eb0f4f27cb8999a4b82b0d5c17249adfec6a6974c0757be80f.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B46811C17859FFB409CF0E904A4AA8F8 | binary | |
MD5:971C514F84BBA0785F80AA1C23EDFD79 | SHA256:F157ED17FCAF8837FA82F8B69973848C9B10A02636848F995698212A08F31895 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
31
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7876 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
864 | BackgroundTransferHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
8180 | UDS-Backdoor.Win32.Agent.myuemh-47adcaa7f381f3eb0f4f27cb8999a4b82b0d5c17249adfec6a6974c0757be80f.exe | GET | 200 | 142.250.186.67:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
5868 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
8180 | UDS-Backdoor.Win32.Agent.myuemh-47adcaa7f381f3eb0f4f27cb8999a4b82b0d5c17249adfec6a6974c0757be80f.exe | GET | 200 | 142.250.186.67:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
5868 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 20.190.159.128:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7876 | backgroundTaskHost.exe | 20.223.36.55:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7876 | backgroundTaskHost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
864 | BackgroundTransferHost.exe | 2.23.227.215:443 | www.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
www.bing.com |
| whitelisted |
windse.ru |
| unknown |
c.pki.goog |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |