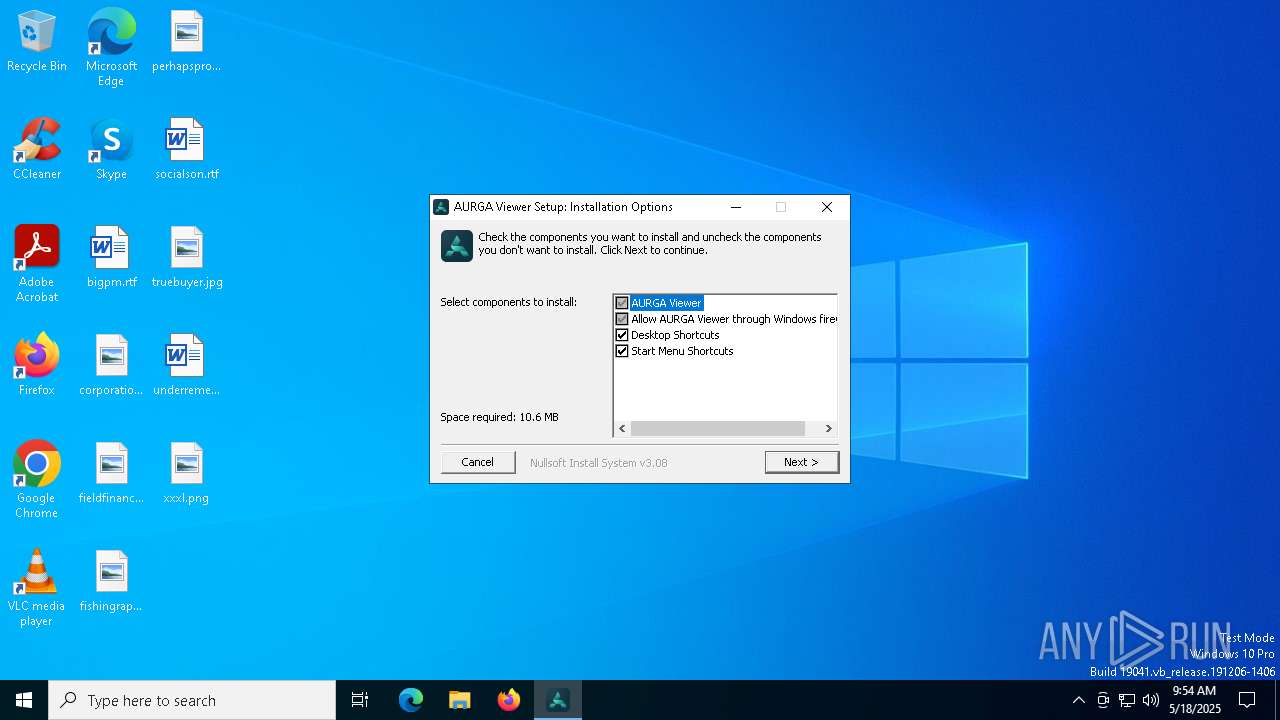
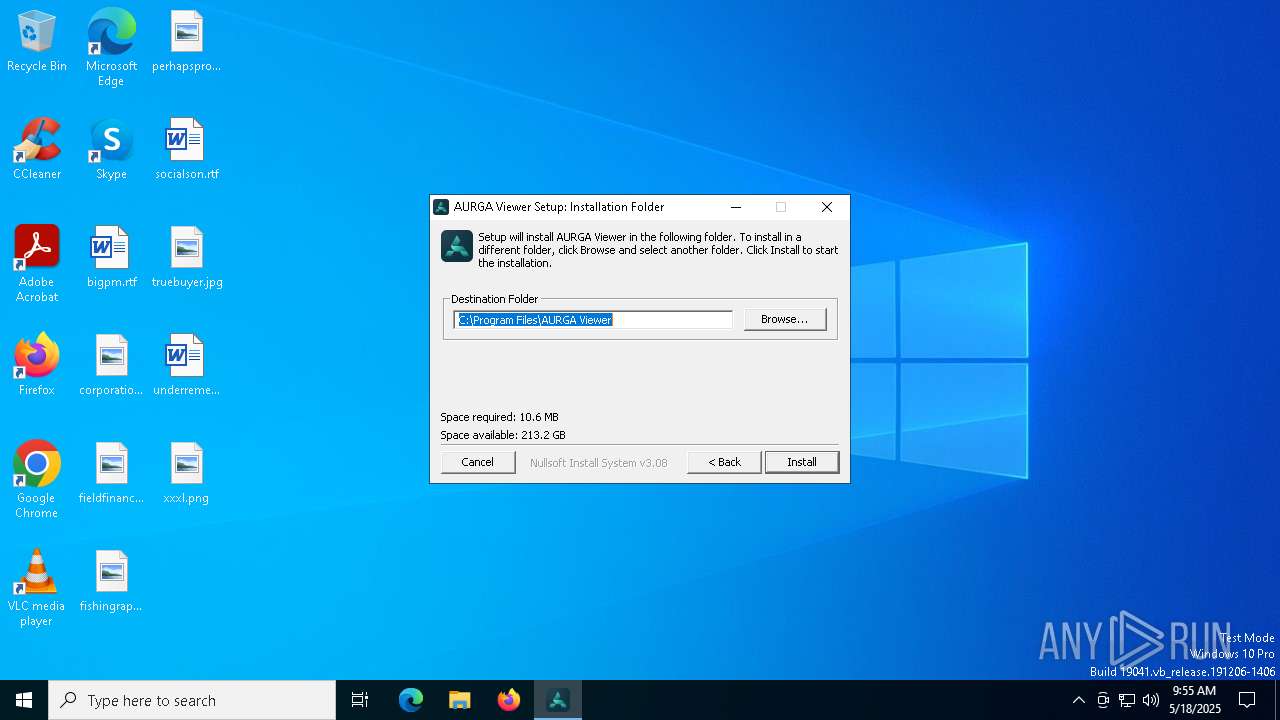
| File name: | AURGAViewer_Installer_x64_v1.1.0.2.exe |
| Full analysis: | https://app.any.run/tasks/5c498a4e-375c-407a-b8ef-7b268a56b608 |
| Verdict: | Malicious activity |
| Analysis date: | May 18, 2025, 09:54:48 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | 455E479134F35FF9999BB2AFE546B438 |
| SHA1: | E7AD41FE40943AFA26A5023A8D15084C8B954B32 |
| SHA256: | 891BA0B0603F3D47845C69FEAC08D7963AB984B31F2DD985E74C22A65858C436 |
| SSDEEP: | 98304:Pbbbn7bb6dQ1IfKlKdMsN6Pyw4zJR9uhZNfIAU4HQVjhIeO51iMdEida+KvbUQ0g:8zl7qxr9pW |
MALICIOUS
No malicious indicators.SUSPICIOUS
The process creates files with name similar to system file names
- AURGAViewer_Installer_x64_v1.1.0.2.exe (PID: 7020)
Malware-specific behavior (creating "System.dll" in Temp)
- AURGAViewer_Installer_x64_v1.1.0.2.exe (PID: 7020)
Creates a software uninstall entry
- AURGAViewer_Installer_x64_v1.1.0.2.exe (PID: 7020)
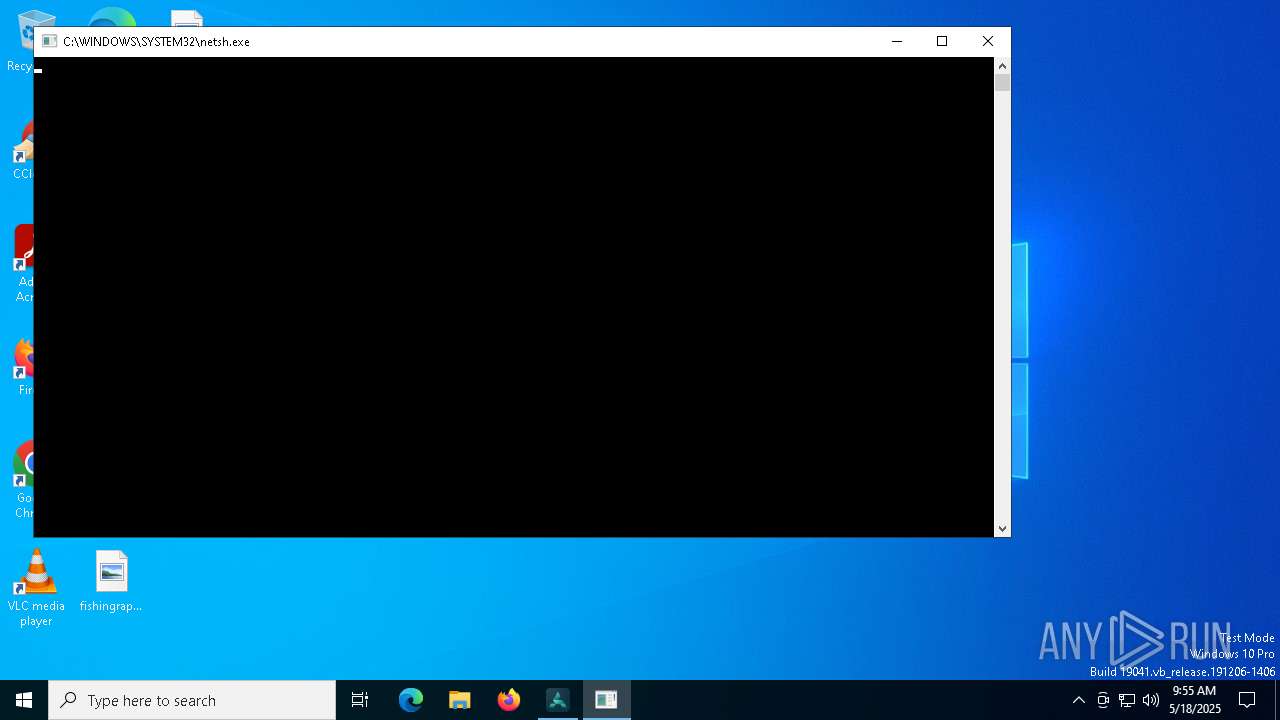
Uses NETSH.EXE to add a firewall rule or allowed programs
- AURGAViewer_Installer_x64_v1.1.0.2.exe (PID: 7020)
Executable content was dropped or overwritten
- AURGAViewer_Installer_x64_v1.1.0.2.exe (PID: 7020)
Executes application which crashes
- AURGAViewer.exe (PID: 6972)
- AURGAViewer.exe (PID: 1096)
INFO
Checks supported languages
- AURGAViewer_Installer_x64_v1.1.0.2.exe (PID: 7020)
- AURGAViewer.exe (PID: 6972)
- AURGAViewer.exe (PID: 1096)
Creates files in the program directory
- AURGAViewer_Installer_x64_v1.1.0.2.exe (PID: 7020)
The sample compiled with english language support
- AURGAViewer_Installer_x64_v1.1.0.2.exe (PID: 7020)
The sample compiled with chinese language support
- AURGAViewer_Installer_x64_v1.1.0.2.exe (PID: 7020)
Reads the computer name
- AURGAViewer_Installer_x64_v1.1.0.2.exe (PID: 7020)
- AURGAViewer.exe (PID: 6972)
- AURGAViewer.exe (PID: 1096)
Create files in a temporary directory
- AURGAViewer_Installer_x64_v1.1.0.2.exe (PID: 7020)
Creates files or folders in the user directory
- AURGAViewer_Installer_x64_v1.1.0.2.exe (PID: 7020)
- WerFault.exe (PID: 1568)
Manual execution by a user
- AURGAViewer.exe (PID: 6972)
- AURGAViewer.exe (PID: 1096)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2021:09:25 21:57:46+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 27136 |
| InitializedDataSize: | 186880 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x352d |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
147
Monitored processes
12
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1096 | "C:\Program Files\AURGA Viewer\AURGAViewer.exe" | C:\Program Files\AURGA Viewer\AURGAViewer.exe | explorer.exe | ||||||||||||
User: admin Company: AURGA CO., LIMITED Integrity Level: HIGH Description: AURGA Viewer Exit code: 3221225477 Version: 1.1.0.2 Modules
| |||||||||||||||
| 1180 | C:\WINDOWS\system32\WerFault.exe -u -p 1096 -s 1120 | C:\Windows\System32\WerFault.exe | — | AURGAViewer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1568 | C:\WINDOWS\system32\WerFault.exe -u -p 6972 -s 1256 | C:\Windows\System32\WerFault.exe | — | AURGAViewer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4844 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | netsh.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4976 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | netsh.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5048 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5344 | netsh advfirewall firewall add rule name="AURGA Viewer" dir=in action=allow program="C:\Program Files\AURGA Viewer\AURGAViewer.exe" enable=yes profile=public,private | C:\Windows\SysWOW64\netsh.exe | — | AURGAViewer_Installer_x64_v1.1.0.2.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5528 | "C:\Users\admin\AppData\Local\Temp\AURGAViewer_Installer_x64_v1.1.0.2.exe" | C:\Users\admin\AppData\Local\Temp\AURGAViewer_Installer_x64_v1.1.0.2.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 5528 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6044 | netsh advfirewall firewall add rule name="AURGA Viewer" dir=out action=allow program="C:\Program Files\AURGA Viewer\AURGAViewer.exe" enable=yes profile=public,private | C:\Windows\SysWOW64\netsh.exe | — | AURGAViewer_Installer_x64_v1.1.0.2.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
4 824
Read events
4 801
Write events
20
Delete events
3
Modification events
| (PID) Process: | (7020) AURGAViewer_Installer_x64_v1.1.0.2.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\AURGAViewer |
| Operation: | write | Name: | Install_Dir |
Value: C:\Program Files\AURGA Viewer | |||
| (PID) Process: | (7020) AURGAViewer_Installer_x64_v1.1.0.2.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\AURGAViewer |
| Operation: | write | Name: | DisplayName |
Value: AURGA Viewer | |||
| (PID) Process: | (7020) AURGAViewer_Installer_x64_v1.1.0.2.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\AURGAViewer |
| Operation: | write | Name: | UninstallString |
Value: "C:\Program Files\AURGA Viewer\uninstall.exe" | |||
| (PID) Process: | (7020) AURGAViewer_Installer_x64_v1.1.0.2.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\AURGAViewer |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Program Files\AURGA Viewer\AURGAViewer.exe | |||
| (PID) Process: | (7020) AURGAViewer_Installer_x64_v1.1.0.2.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\AURGAViewer |
| Operation: | write | Name: | NoModify |
Value: 1 | |||
| (PID) Process: | (7020) AURGAViewer_Installer_x64_v1.1.0.2.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\AURGAViewer |
| Operation: | write | Name: | NoRepair |
Value: 1 | |||
| (PID) Process: | (6972) AURGAViewer.exe | Key: | HKEY_CURRENT_USER\System\CurrentControlSet\Control\MediaProperties\PrivateProperties\DirectInput\VID_0627&PID_0001\Calibration\0 |
| Operation: | write | Name: | GUID |
Value: 10043E32CE33F0118001444553540000 | |||
| (PID) Process: | (6972) AURGAViewer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\DirectInput\AURGAVIEWER.EXE6635AA870033AE00 |
| Operation: | write | Name: | Name |
Value: AURGAVIEWER.EXE | |||
| (PID) Process: | (6972) AURGAViewer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\DirectInput\AURGAVIEWER.EXE6635AA870033AE00 |
| Operation: | write | Name: | UsesMapper |
Value: 00000000 | |||
| (PID) Process: | (6972) AURGAViewer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\DirectInput\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: AURGAVIEWER.EXE | |||
Executable files
6
Suspicious files
9
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1568 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_AURGAViewer.exe_6c80b110e2af583947e53ec5cc29f8ae61e8bfb5_535063cf_d0783f9f-cc30-44cc-8943-971872a227a6\Report.wer | — | |
MD5:— | SHA256:— | |||
| 1180 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_AURGAViewer.exe_6c80b110e2af583947e53ec5cc29f8ae61e8bfb5_535063cf_536bd63f-3072-4285-9e6c-b67b1c281dde\Report.wer | — | |
MD5:— | SHA256:— | |||
| 7020 | AURGAViewer_Installer_x64_v1.1.0.2.exe | C:\Users\admin\AppData\Local\Temp\nseC065.tmp\System.dll | executable | |
MD5:CFF85C549D536F651D4FB8387F1976F2 | SHA256:8DC562CDA7217A3A52DB898243DE3E2ED68B80E62DDCB8619545ED0B4E7F65A8 | |||
| 7020 | AURGAViewer_Installer_x64_v1.1.0.2.exe | C:\Program Files\AURGA Viewer\swscale-7.dll | executable | |
MD5:9852BABE72F9B5711EF68840C2689902 | SHA256:E043E1C4F44602BAFC6C54FA5B01A5B290B31C3C8BB1E3F64730E86F08C0B99C | |||
| 7020 | AURGAViewer_Installer_x64_v1.1.0.2.exe | C:\Program Files\AURGA Viewer\avformat-60.dll | executable | |
MD5:3ACF7498F01D2A01817FC9EC511E1233 | SHA256:C2EA1771A9E1B9DD85D00B59FD4CC5DCFF0110B061A491CF1EFBAEAB5809227A | |||
| 7020 | AURGAViewer_Installer_x64_v1.1.0.2.exe | C:\Program Files\AURGA Viewer\avutil-58.dll | executable | |
MD5:213BF9337E94B5066262373FEFBE95A3 | SHA256:A223CFAF2AC7C552762778C07D43413489D0D6FB70F19B922F489645CCAB2F0D | |||
| 7020 | AURGAViewer_Installer_x64_v1.1.0.2.exe | C:\Users\admin\Desktop\AURGA Viewer.lnk | binary | |
MD5:282BE8935101EC1FE8D9C8F090FFD0FC | SHA256:AD4AE323EE14A6A9F4214B47C440546E5379327CB74FB1E74E5C54E865D19F13 | |||
| 7020 | AURGAViewer_Installer_x64_v1.1.0.2.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\AURGA Viewer.lnk | binary | |
MD5:6C05F9BBB0325C53BFAFA3EF2C28DC32 | SHA256:1B821580256C573D6A6CB5B075BD9216A3FFAE3E95BCBA8F90D614F8E5991E71 | |||
| 1568 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER102C.tmp.xml | xml | |
MD5:2EC52C9C76DD8216029E52BF634C5B18 | SHA256:CD596EE6ECD460D98B194491B3F85357CE1CC1212807FDFEA968F5A546C64B2C | |||
| 1568 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERDC8.tmp.dmp | binary | |
MD5:AFE036D09030E182AE869935AE471B68 | SHA256:69205E845D1817141977D363AC5E6EDB03BC4F8BA0591F5E11D12BB289A2D268 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
30
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.15:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2100 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2100 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.216.77.15:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.159.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |