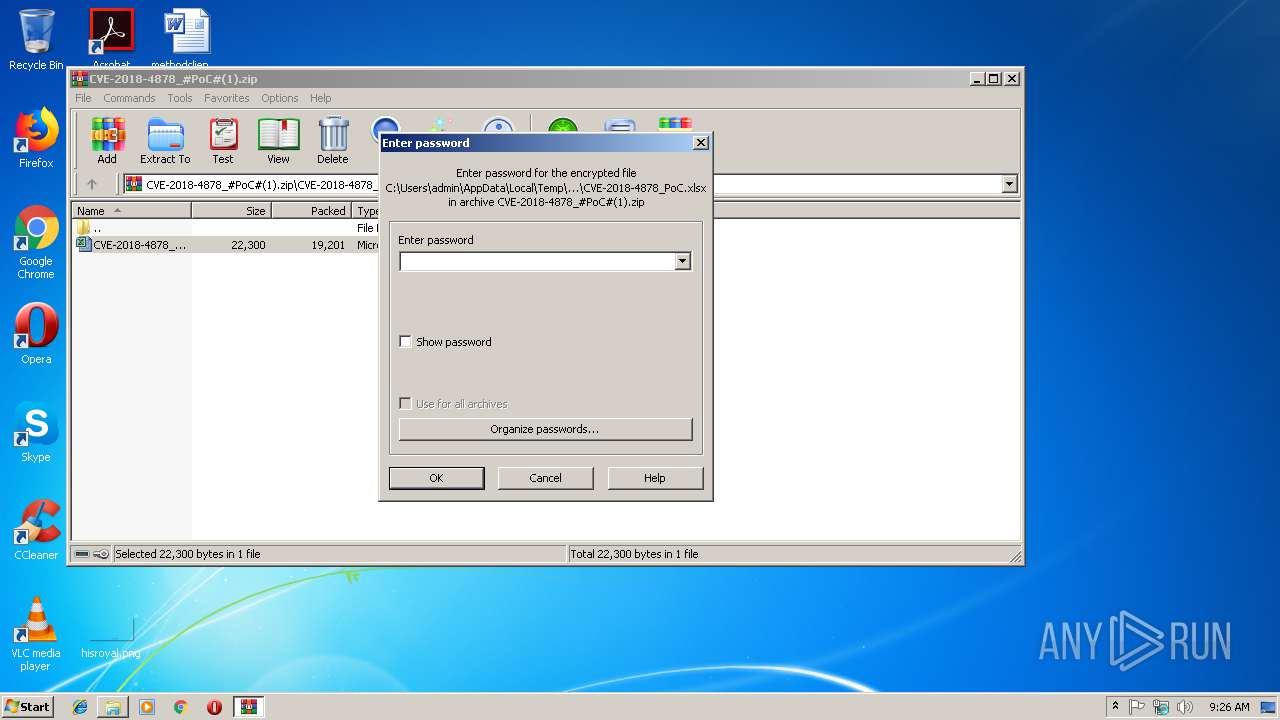
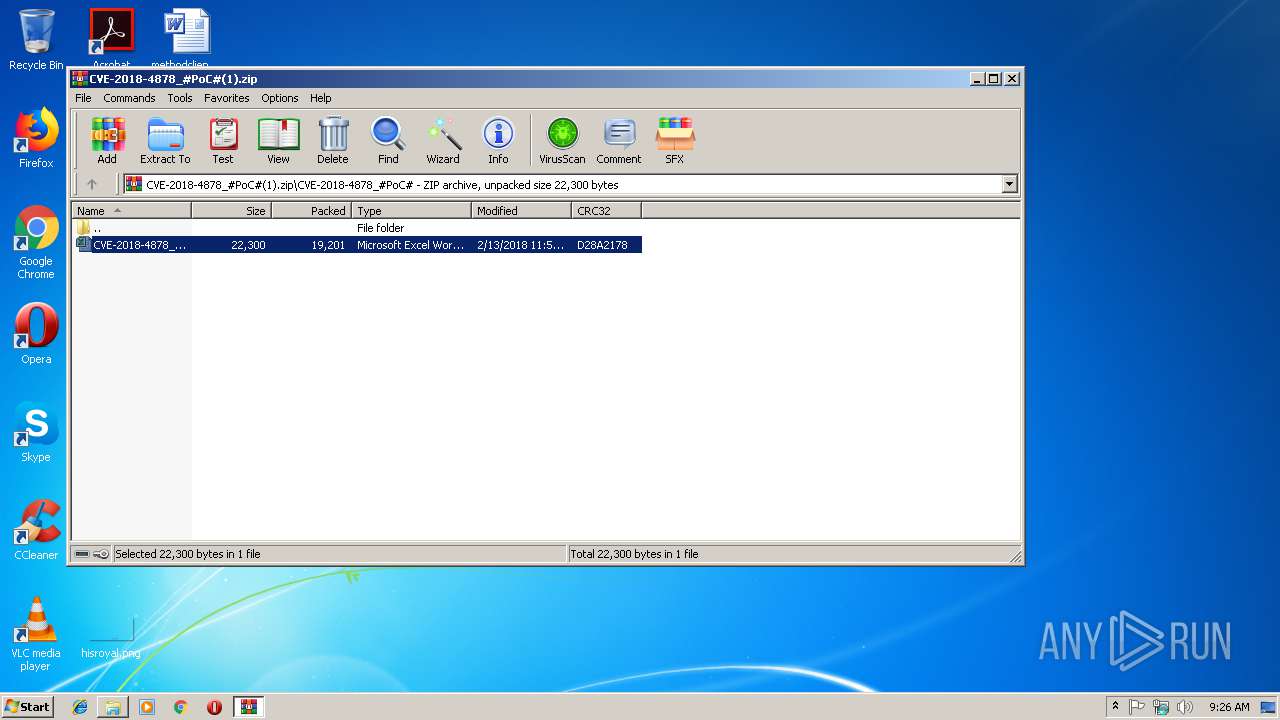
| File name: | CVE-2018-4878_#PoC#(1).zip |
| Full analysis: | https://app.any.run/tasks/2fc4c7b8-7e75-4204-a87f-174e61ee55da |
| Verdict: | Malicious activity |
| Analysis date: | December 06, 2018, 09:26:13 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 1D169B52BF39D8D11485A6A101464143 |
| SHA1: | 0CCF143889A3E52B03BE3596E6C054C95D0BF81B |
| SHA256: | 89019BFC86E39D91C685782280DFDDD0C9647B7EF97666B938ACE65ABC48AC19 |
| SSDEEP: | 384:M4sxpoIGuEsmzUv96hcA6Yv5GTm3Q19f1Lyouii7KDJ:M4sboIVNV6qAVsZuii7aJ |
MALICIOUS
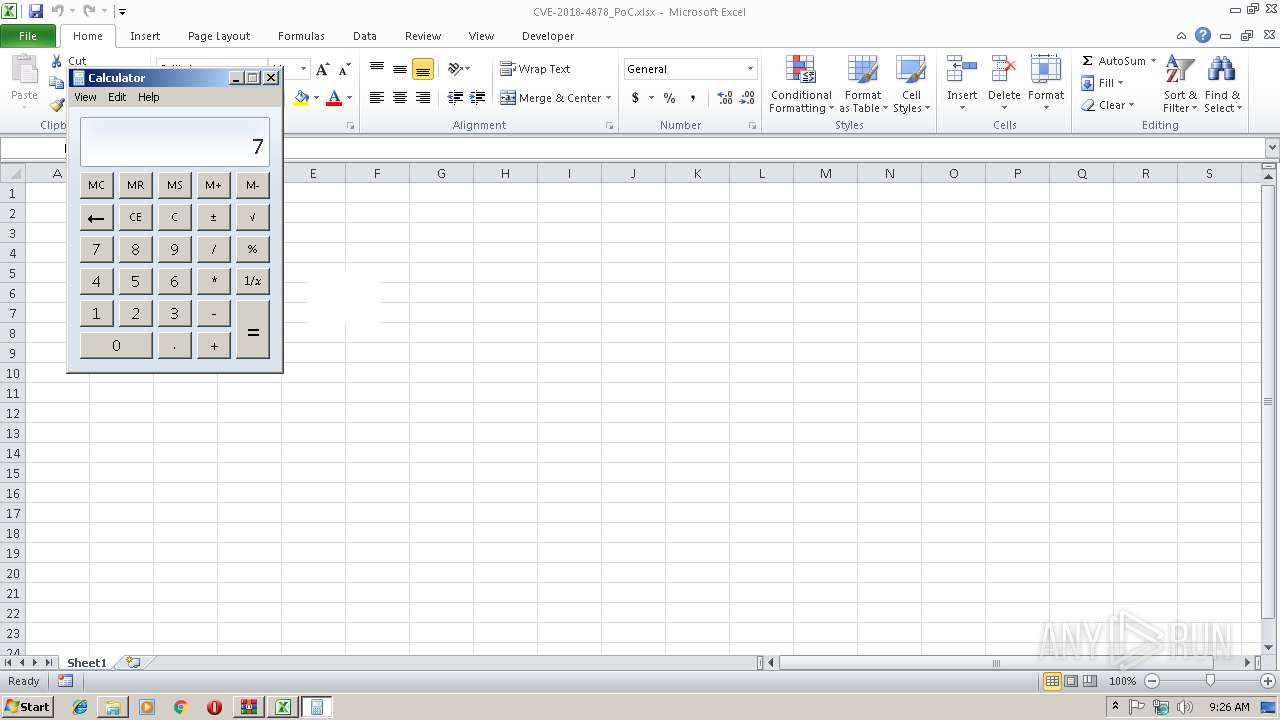
Starts CMD.EXE for commands execution
- EXCEL.EXE (PID: 2892)
Unusual execution from Microsoft Office
- EXCEL.EXE (PID: 2892)
Runs app for hidden code execution
- EXCEL.EXE (PID: 2892)
SUSPICIOUS
Starts Microsoft Office Application
- WinRAR.exe (PID: 2956)
Reads Internet Cache Settings
- EXCEL.EXE (PID: 2892)
Unusual connect from Microsoft Office
- EXCEL.EXE (PID: 2892)
INFO
Creates files in the user directory
- EXCEL.EXE (PID: 2892)
Reads Microsoft Office registry keys
- EXCEL.EXE (PID: 2892)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2018:02:13 14:02:16 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | CVE-2018-4878_#PoC#/ |
Total processes
38
Monitored processes
5
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2892 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2956 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\CVE-2018-4878_#PoC#(1).zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3036 | C:\Windows\System32\cmd.exe | C:\Windows\System32\cmd.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1278912021 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3556 | calc | C:\Windows\System32\calc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Calculator Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 4016 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 095
Read events
1 045
Write events
43
Delete events
7
Modification events
| (PID) Process: | (2956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2956) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\CVE-2018-4878_#PoC#(1).zip | |||
| (PID) Process: | (2956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (2892) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | write | Name: | }u* |
Value: 7D752A004C0B0000010000000000000000000000 | |||
Executable files
0
Suspicious files
1
Text files
1
Unknown types
38
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2892 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVRA9DD.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2892 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Macromedia\Flash Player\macromedia.com\support\flashplayer\sys\settings.sxx | — | |
MD5:— | SHA256:— | |||
| 2892 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\Excel8.0\ShockwaveFlashObjects.exd | tlb | |
MD5:— | SHA256:— | |||
| 2892 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Macromedia\Flash Player\macromedia.com\support\flashplayer\sys\settings.sol | sol | |
MD5:— | SHA256:— | |||
| 2892 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Adobe\Flash Player\APSPrivateData2\0\drm-ax-win-x86\CertStore.dat | cat | |
MD5:— | SHA256:— | |||
| 2892 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\R9ZEWH8D\crossdomain[1].xml | xml | |
MD5:— | SHA256:— | |||
| 2892 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0UU90R59\v5[1] | cat | |
MD5:— | SHA256:— | |||
| 2892 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Adobe\Flash Player\APSPrivateData2\0\drm-ax-win-x86\MiscGlobalDataStore.mgd.lkg | der | |
MD5:— | SHA256:— | |||
| 2892 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Adobe\Flash Player\APSPrivateData2\0\drm-ax-win-x86\GlobalStateStore.gs | der | |
MD5:— | SHA256:— | |||
| 2892 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Adobe\Flash Player\APSPrivateData2\0\drm-ax-win-x86\GlobalStateStore.gs.lkg | der | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
1
DNS requests
1
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2892 | EXCEL.EXE | GET | 200 | 52.4.148.166:80 | http://individualization.adobe.com/crossdomain.xml | US | xml | 286 b | whitelisted |
2892 | EXCEL.EXE | POST | 200 | 52.4.148.166:80 | http://individualization.adobe.com/flashaccess/i15n/v5 | US | cat | 9.54 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2892 | EXCEL.EXE | 52.4.148.166:80 | individualization.adobe.com | Amazon.com, Inc. | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
individualization.adobe.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2892 | EXCEL.EXE | Potential Corporate Privacy Violation | ET POLICY Outdated Flash Version M1 |