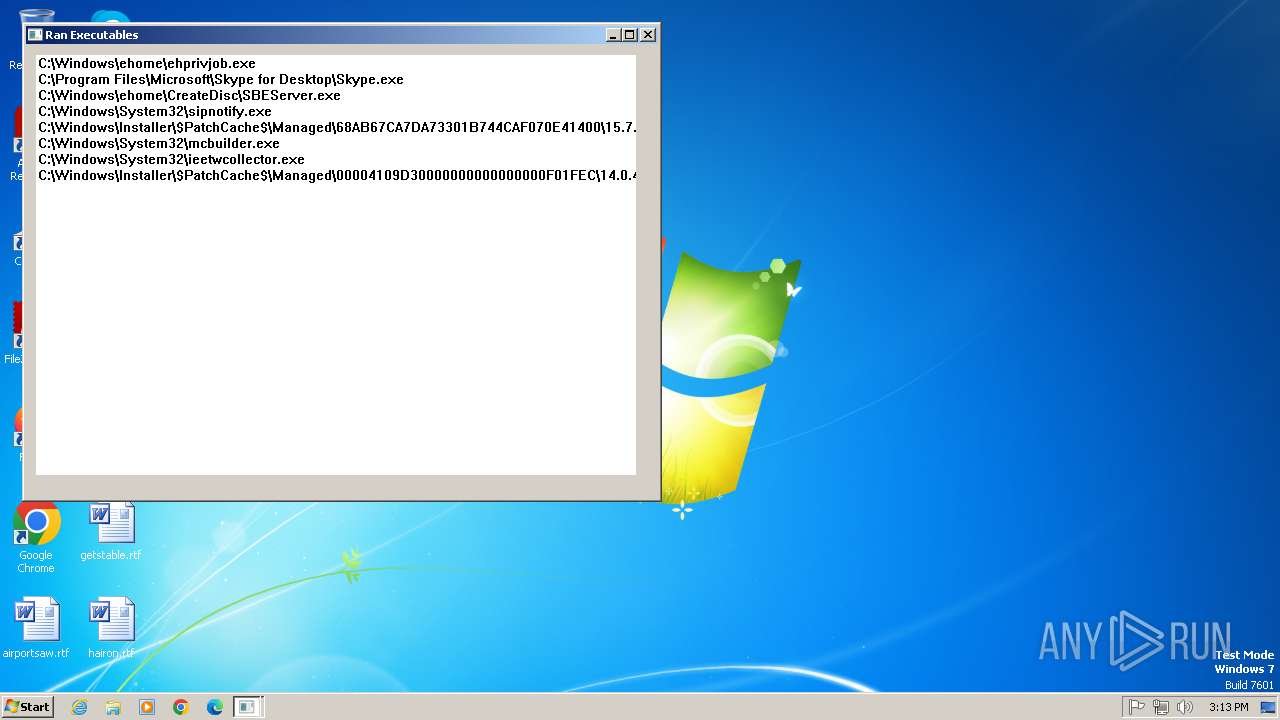
| File name: | lawn.exe |
| Full analysis: | https://app.any.run/tasks/a60b74c8-db6b-40a0-9b32-ad5cd027e68c |
| Verdict: | Malicious activity |
| Analysis date: | April 26, 2025, 14:13:05 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (console) Intel 80386, for MS Windows, 4 sections |
| MD5: | E1B7D32B92F0F6D983B465E46C14F3CD |
| SHA1: | B7F367A2E2D912170488B2678B5613247CB019C2 |
| SHA256: | 88D8C3E9143A5DEB47EEA2FBF37E39672CEBCA6A96391E1C92F2660758F17B26 |
| SSDEEP: | 768:TG/aLb2UYZLHQuYeckRkwVnEx5mwVvA1:TG/u+/HcWXnExxe1 |
MALICIOUS
Antivirus name has been found in the command line (generic signature)
- reset.exe (PID: 5568)
- sfc.exe (PID: 5428)
Starts Visual C# compiler
- lawn.exe (PID: 2848)
SUSPICIOUS
Reads security settings of Internet Explorer
- lawn.exe (PID: 2848)
- ServiceModelReg.exe (PID: 3056)
- ComSvcConfig.exe (PID: 3764)
Reads the Internet Settings
- lawn.exe (PID: 2848)
- sipnotify.exe (PID: 1032)
- Skype.exe (PID: 1336)
Process drops legitimate windows executable
- vcredist_x86.exe (PID: 2868)
- Skype-Setup.tmp (PID: 4280)
- vcredist_x86.exe (PID: 5176)
- setup.exe (PID: 2828)
Reads Microsoft Outlook installation path
- lawn.exe (PID: 2848)
Executable content was dropped or overwritten
- vcredist_x86.exe (PID: 2868)
- maintenanceservice_installer.exe (PID: 2656)
- RTLCPL.EXE (PID: 1892)
- GoogleUpdateSetup.exe (PID: 3972)
- Skype-Setup.exe (PID: 4164)
- Skype-Setup.tmp (PID: 4280)
- setup.exe (PID: 2828)
- vcredist_x86.exe (PID: 5176)
- Skype-Setup.exe (PID: 1496)
Application launched itself
- Skype.exe (PID: 1336)
- MRT-KB890830.exe (PID: 3008)
- CompatTelRunner.exe (PID: 5544)
Reads settings of System Certificates
- ServiceModelReg.exe (PID: 3056)
- ComSvcConfig.exe (PID: 3764)
- TsWpfWrp.exe (PID: 1828)
Searches for installed software
- vcredist_x86.exe (PID: 2868)
Loads DLL from Mozilla Firefox
- crashreporter.exe (PID: 604)
Malware-specific behavior (creating "System.dll" in Temp)
- maintenanceservice_installer.exe (PID: 2656)
Uses QWINSTA.EXE to read information about user sessions on remote desktops
- lawn.exe (PID: 2848)
Starts SC.EXE for service management
- lawn.exe (PID: 2848)
Uses SYSTEMINFO.EXE to read the environment
- lawn.exe (PID: 2848)
Uses RUNDLL32.EXE to load library
- SOUNDMAN.EXE (PID: 628)
Windows service management via SC.EXE
- sc.exe (PID: 4136)
Uses WEVTUTIL.EXE to event management in Windows
- lawn.exe (PID: 2848)
Uses TASKKILL.EXE to kill process
- Skype-Setup.tmp (PID: 4280)
Starts CMD.EXE for commands execution
- lawn.exe (PID: 2848)
Uses ICACLS.EXE to modify access control lists
- lawn.exe (PID: 2848)
Uses QUSER.EXE to read information about current user sessions
- lawn.exe (PID: 2848)
Uses powercfg.exe to modify the power settings
- lawn.exe (PID: 2848)
Checks for external IP
- CCUpdate.exe (PID: 5240)
Suspicious use of NETSH.EXE
- lawn.exe (PID: 2848)
Starts another process probably with elevated privileges via RUNAS.EXE
- runas.exe (PID: 4020)
Searches and executes a command on selected files
- forfiles.exe (PID: 5376)
The process drops C-runtime libraries
- Skype-Setup.tmp (PID: 4280)
Process uses IPCONFIG to get network configuration information
- lawn.exe (PID: 2848)
INFO
Checks supported languages
- lawn.exe (PID: 2848)
- Skype.exe (PID: 1336)
- ehprivjob.exe (PID: 1484)
- SBEServer.exe (PID: 312)
- MSTORDB.EXE (PID: 3064)
- ose.exe (PID: 984)
- AcroRd32Info.exe (PID: 676)
- ditrace.exe (PID: 2204)
- Skype.exe (PID: 3244)
- ONELEV.EXE (PID: 3632)
- vcredist_x86.exe (PID: 2868)
- Skype.exe (PID: 3196)
- ServiceModelReg.exe (PID: 3056)
- ose.exe (PID: 2984)
- Skype.exe (PID: 4012)
- ComSvcConfig.exe (PID: 3764)
- ehsched.exe (PID: 3084)
- FlickLearningWizard.exe (PID: 3284)
- DataSvcUtil.exe (PID: 3292)
- unpack200.exe (PID: 4068)
- crashreporter.exe (PID: 604)
- DW20.EXE (PID: 3984)
- ose.exe (PID: 1772)
- GoogleUpdateCore.exe (PID: 2984)
- Wkconv.exe (PID: 2204)
- RTLCPL.EXE (PID: 1892)
- tzupd.exe (PID: 3904)
- wmpenc.exe (PID: 3412)
Reads the machine GUID from the registry
- ehprivjob.exe (PID: 1484)
- SBEServer.exe (PID: 312)
- MSTORDB.EXE (PID: 3064)
- ONELEV.EXE (PID: 3632)
- ServiceModelReg.exe (PID: 3056)
- ComSvcConfig.exe (PID: 3764)
- DataSvcUtil.exe (PID: 3292)
- wmpenc.exe (PID: 3412)
Reads the computer name
- lawn.exe (PID: 2848)
- SBEServer.exe (PID: 312)
- MSTORDB.EXE (PID: 3064)
- Skype.exe (PID: 1336)
- ONELEV.EXE (PID: 3632)
- vcredist_x86.exe (PID: 2868)
- Skype.exe (PID: 3196)
- ServiceModelReg.exe (PID: 3056)
- Skype.exe (PID: 4012)
- ehsched.exe (PID: 3084)
- ComSvcConfig.exe (PID: 3764)
- DataSvcUtil.exe (PID: 3292)
- GoogleUpdateCore.exe (PID: 2984)
- wmpenc.exe (PID: 3412)
- tzupd.exe (PID: 3904)
- RTLCPL.EXE (PID: 1892)
Reads Environment values
- MSTORDB.EXE (PID: 3064)
- Skype.exe (PID: 1336)
Reads Microsoft Office registry keys
- MSTORDB.EXE (PID: 3064)
Reads product name
- Skype.exe (PID: 1336)
Reads CPU info
- Skype.exe (PID: 1336)
Create files in a temporary directory
- vcredist_x86.exe (PID: 2868)
The sample compiled with english language support
- vcredist_x86.exe (PID: 2868)
- RTLCPL.EXE (PID: 1892)
- maintenanceservice_installer.exe (PID: 2656)
- GoogleUpdateSetup.exe (PID: 3972)
- Skype-Setup.tmp (PID: 4280)
- vcredist_x86.exe (PID: 5176)
- setup.exe (PID: 2828)
Creates files or folders in the user directory
- Skype.exe (PID: 1336)
- IMJPDCT.EXE (PID: 1076)
- Wkconv.exe (PID: 2204)
Reads the software policy settings
- ServiceModelReg.exe (PID: 3056)
- ComSvcConfig.exe (PID: 3764)
- TsWpfWrp.exe (PID: 1828)
Application launched itself
- chrome.exe (PID: 3268)
- msedge.exe (PID: 2368)
Checks transactions between databases Windows and Oracle
- ComSvcConfig.exe (PID: 3764)
Reads Internet Explorer settings
- OUTLOOK.EXE (PID: 3144)
Node.js compiler has been detected
- Skype.exe (PID: 1336)
The sample compiled with arabic language support
- GoogleUpdateSetup.exe (PID: 3972)
The sample compiled with bulgarian language support
- GoogleUpdateSetup.exe (PID: 3972)
Reads security settings of Internet Explorer
- TsWpfWrp.exe (PID: 1828)
The sample compiled with german language support
- GoogleUpdateSetup.exe (PID: 3972)
The sample compiled with french language support
- GoogleUpdateSetup.exe (PID: 3972)
The sample compiled with japanese language support
- GoogleUpdateSetup.exe (PID: 3972)
The sample compiled with Indonesian language support
- GoogleUpdateSetup.exe (PID: 3972)
The sample compiled with Italian language support
- GoogleUpdateSetup.exe (PID: 3972)
The sample compiled with czech language support
- GoogleUpdateSetup.exe (PID: 3972)
The sample compiled with slovak language support
- GoogleUpdateSetup.exe (PID: 3972)
The sample compiled with chinese language support
- GoogleUpdateSetup.exe (PID: 3972)
The sample compiled with swedish language support
- GoogleUpdateSetup.exe (PID: 3972)
The sample compiled with portuguese language support
- GoogleUpdateSetup.exe (PID: 3972)
The sample compiled with polish language support
- GoogleUpdateSetup.exe (PID: 3972)
The sample compiled with russian language support
- GoogleUpdateSetup.exe (PID: 3972)
The sample compiled with korean language support
- GoogleUpdateSetup.exe (PID: 3972)
The sample compiled with turkish language support
- GoogleUpdateSetup.exe (PID: 3972)
Compiled with Borland Delphi (YARA)
- RTLCPL.EXE (PID: 1892)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win16/32 Executable Delphi generic (34.1) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (32.9) |
| .exe | | | DOS Executable Generic (32.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:04:24 19:52:04+00:00 |
| ImageFileCharacteristics: | Executable, Bytes reversed lo, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 2.18 |
| CodeSize: | 23040 |
| InitializedDataSize: | 3072 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1834 |
| OSVersion: | 1.11 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows command line |
Total processes
642
Monitored processes
412
Malicious processes
6
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 124 | "C:\Windows\System32\lpremove.exe" | C:\Windows\System32\lpremove.exe | — | lawn.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: MUI Language pack cleanup Exit code: 3221225794 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 128 | "C:\Windows\System32\bthudtask.exe" | C:\Windows\System32\bthudtask.exe | — | lawn.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Bluetooth Uninstall Device Task Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
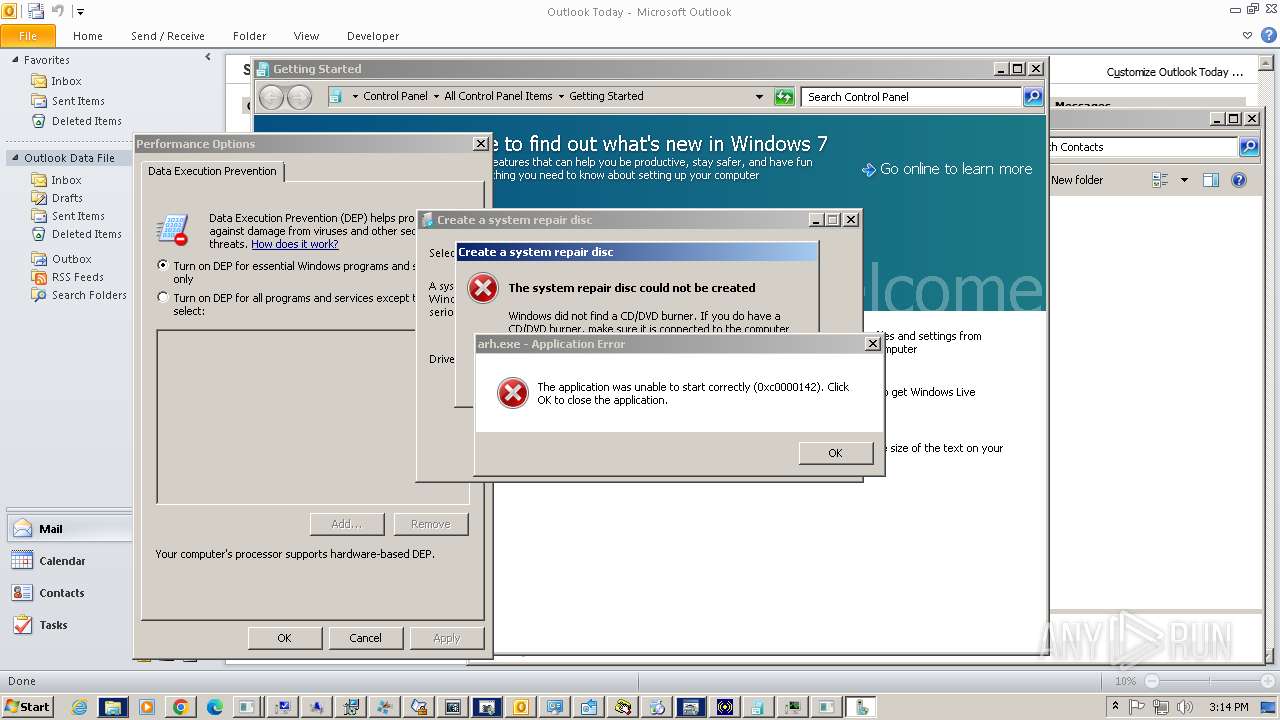
| 148 | "C:\Windows\System32\SystemPropertiesDataExecutionPrevention.exe" | C:\Windows\System32\SystemPropertiesDataExecutionPrevention.exe | — | lawn.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Change Data Execution Prevention Settings Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 312 | "C:\Windows\ehome\CreateDisc\SBEServer.exe" | C:\Windows\ehome\CreateDisc\SBEServer.exe | — | lawn.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: SBEServer Version: 0.9.0.0 Modules
| |||||||||||||||
| 580 | "C:\Program Files\Common Files\Steam\SteamServiceTmp.exe" | C:\Program Files\Common Files\Steam\SteamServiceTmp.exe | — | lawn.exe | |||||||||||
User: admin Company: Valve Corporation Integrity Level: MEDIUM Description: Steam Client Service Exit code: 3221226540 Version: 04.69.34.61 Modules
| |||||||||||||||
| 604 | "C:\Program Files\Mozilla Firefox\crashreporter.exe" | C:\Program Files\Mozilla Firefox\crashreporter.exe | — | lawn.exe | |||||||||||
User: admin Company: Mozilla Foundation Integrity Level: MEDIUM Exit code: 1073807364 Version: 115.0.2 Modules
| |||||||||||||||
| 628 | "C:\Windows\SOUNDMAN.EXE" | C:\Windows\SOUNDMAN.EXE | — | lawn.exe | |||||||||||
User: admin Company: Realtek Semiconductor Corp. Integrity Level: MEDIUM Description: Realtek Sound Manager Exit code: 1073807364 Version: 6, 0, 0, 5 Modules
| |||||||||||||||
| 676 | "C:\Windows\Installer\$PatchCache$\Managed\68AB67CA7DA73301B744CAF070E41400\15.7.20033\AcroRd32Info.exe" | C:\Windows\Installer\$PatchCache$\Managed\68AB67CA7DA73301B744CAF070E41400\15.7.20033\AcroRd32Info.exe | — | lawn.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat Reader DC Exit code: 255 Version: 15.7.20033.133275 Modules
| |||||||||||||||
| 872 | "C:\Windows\System32\fixmapi.exe" | C:\Windows\System32\fixmapi.exe | — | lawn.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: FIXMAPI 1.0 MAPI Repair Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 872 | "C:\Windows\System32\SystemPropertiesHardware.exe" | C:\Windows\System32\SystemPropertiesHardware.exe | lawn.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Hardware Settings Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
69 653
Read events
68 941
Write events
658
Delete events
54
Modification events
| (PID) Process: | (2848) lawn.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2848) lawn.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2848) lawn.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2848) lawn.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3064) MSTORDB.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Clip OrganizerDB\Resiliency\StartupItems |
| Operation: | write | Name: | $% |
Value: 24252000F80B0000010000000000000000000000 | |||
| (PID) Process: | (3064) MSTORDB.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3064) MSTORDB.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (3064) MSTORDB.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (3064) MSTORDB.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (3064) MSTORDB.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
Executable files
203
Suspicious files
173
Text files
122
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3144 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR489D.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3268 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF185147.TMP | — | |
MD5:— | SHA256:— | |||
| 3268 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1032 | sipnotify.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\SipNotify\default.cab | compressed | |
MD5:340674F6A3D1562E28A011EC11E40D83 | SHA256:259880E2346D986ABEED46AA9C2917C53E969AAE6927F2CA0A2AD0967736DF98 | |||
| 2868 | vcredist_x86.exe | C:\Users\admin\AppData\Local\Temp\{f65db027-aff3-4070-886a-0d87064aabb1}\.ba1\thm.xml | xml | |
MD5:0056F10A42638EA8B4BEFC614741DDD6 | SHA256:6B1BA0DEA830E556A58C883290FAA5D49C064E546CBFCD0451596A10CC693F87 | |||
| 1032 | sipnotify.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\SipNotify\eoscontent\en-us.html | html | |
MD5:5001C5247AF7E35AC35ACE61B87E8040 | SHA256:2920ED0DDFE475884703A5AE7B835F40398E509AA26B52A8DDD7F25DCD4B3D2E | |||
| 2868 | vcredist_x86.exe | C:\Users\admin\AppData\Local\Temp\{f65db027-aff3-4070-886a-0d87064aabb1}\.ba1\license.rtf | text | |
MD5:1E47EE7B71B22488068343DF4CE30534 | SHA256:8518F0420972C1DBE8A323FFC6F57863AF0B80C6A3B27FD0C6FC9BDABB7E2D13 | |||
| 1032 | sipnotify.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\SipNotify\eoscontent\metadata.json | binary | |
MD5:253EDC8EC7674BD78293FF3B21866074 | SHA256:51C3A033F0160A30C1773F1E5A9CD01AB018B151EDA1BB64D0226B2437106A56 | |||
| 1032 | sipnotify.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\SipNotify\eoscontent\styles.css | text | |
MD5:3383EEF350240253D7C2C2564381B3CB | SHA256:85443493D86D6D7FB0E07BC9705DFC9C858086FBA1B0E508092AB328D5F145E8 | |||
| 1336 | Skype.exe | C:\Users\admin\AppData\Roaming\Microsoft\Skype for Desktop\Crashpad\settings.dat | binary | |
MD5:3B2AEFD32F61DB8110091B81A16A9AD1 | SHA256:27A6D2020F45CD9D3F4DFCF837EC661A1D997B08D23E3CB41B94186C21A50B37 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
28
DNS requests
42
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1032 | sipnotify.exe | HEAD | 503 | 23.38.21.95:80 | http://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RE2JgkA?v=133901539988270000 | unknown | — | — | whitelisted |
3144 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | unknown | — | — | whitelisted |
5240 | CCUpdate.exe | HEAD | 200 | 96.16.53.156:80 | http://emupdate.avcdn.net/files/emupdate/pong.txt | unknown | — | — | whitelisted |
5240 | CCUpdate.exe | GET | 200 | 96.16.53.152:80 | http://ccleaner.tools.avcdn.net/tools/ccleaner/update/patches.ini | unknown | — | — | whitelisted |
5240 | CCUpdate.exe | GET | 200 | 96.16.53.152:80 | http://ccleaner.tools.avcdn.net/tools/ccleaner/update/ccupdate061_mv.cab | unknown | — | — | whitelisted |
— | — | HEAD | 503 | 23.38.21.95:80 | http://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RE2JgkA?v=133901540722920000 | unknown | — | — | whitelisted |
5240 | CCUpdate.exe | GET | 200 | 96.16.53.152:80 | http://ccleaner.tools.avcdn.net/tools/ccleaner/update/updates.xml | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1032 | sipnotify.exe | 23.38.21.95:80 | query.prod.cms.rt.microsoft.com | AKAMAI-AS | NL | whitelisted |
3268 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3780 | chrome.exe | 142.251.36.3:443 | clientservices.googleapis.com | GOOGLE | US | whitelisted |
3780 | chrome.exe | 74.125.133.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
3780 | chrome.exe | 142.251.36.4:443 | www.google.com | GOOGLE | US | whitelisted |
3780 | chrome.exe | 142.250.179.163:443 | www.gstatic.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
query.prod.cms.rt.microsoft.com |
| whitelisted |
get.skype.com |
| whitelisted |
a.config.skype.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| whitelisted |
www.google.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
ogads-pa.clients6.google.com |
| whitelisted |
apis.google.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Misc activity | ET INFO External IP Lookup Service in DNS Query (ip-info .ff .avast .com) |
1080 | svchost.exe | Misc activity | ET INFO External IP Lookup Service in DNS Query (ip-info .ff .avast .com) |
5240 | CCUpdate.exe | Misc activity | ET INFO Observed External IP Lookup Domain (ip-info .ff .avast .com) in TLS SNI |
1080 | svchost.exe | Misc activity | ET INFO External IP Lookup Service in DNS Query (ip-info .ff .avast .com) |
— | — | Misc activity | ET INFO External IP Lookup Service in DNS Query (ip-info .ff .avast .com) |
— | — | Misc activity | ET INFO Observed External IP Lookup Domain (ip-info .ff .avast .com) in TLS SNI |
— | — | Misc activity | ET INFO External IP Lookup Service in DNS Query (ip-info .ff .avast .com) |
Process | Message |
|---|---|
Skype.exe | [0426/151321.155:ERROR:filesystem_win.cc(130)] GetFileAttributes C:\Users\admin\AppData\Roaming\Microsoft\Skype for Desktop\Crashpad\attachments\3a0ee62b-79ac-4cc3-bbd5-f65252e7a91f: The system cannot find the file specified. (0x2)
|
elevation_service.exe | [0426/151332.308:ERROR:service_main.cc(154)] Failed to connect to the service control manager: The service process could not connect to the service controller. (0x427)
|
SteamService.exe | Failed to find Steam.exe |
mmc.exe | ViewerViewsFolderPath = 'C:\ProgramData\Microsoft\Event Viewer\Views': Microsoft.Windows.ManagementUI.CombinedControls.EventsNode
|
mmc.exe | ViewerConfigPath = 'C:\ProgramData\Microsoft\Event Viewer': Microsoft.Windows.ManagementUI.CombinedControls.EventsNode
|
mmc.exe | ViewerAdminViewsPath = 'C:\ProgramData\Microsoft\Event Viewer\Views\ApplicationViewsRootNode': Microsoft.Windows.ManagementUI.CombinedControls.EventsNode
|
mmc.exe | ViewerExternalLogsPath = 'C:\ProgramData\Microsoft\Event Viewer\ExternalLogs': Microsoft.Windows.ManagementUI.CombinedControls.EventsNode
|
mmc.exe | Failed to get ChannelConfigOwningPublisher -122-The data area passed to a system call is too small
|
mmc.exe | Getting next publisher from enum failed-259-No more data is available
|
mmc.exe | Failed to get ChannelConfigOwningPublisher -122-The data area passed to a system call is too small
|