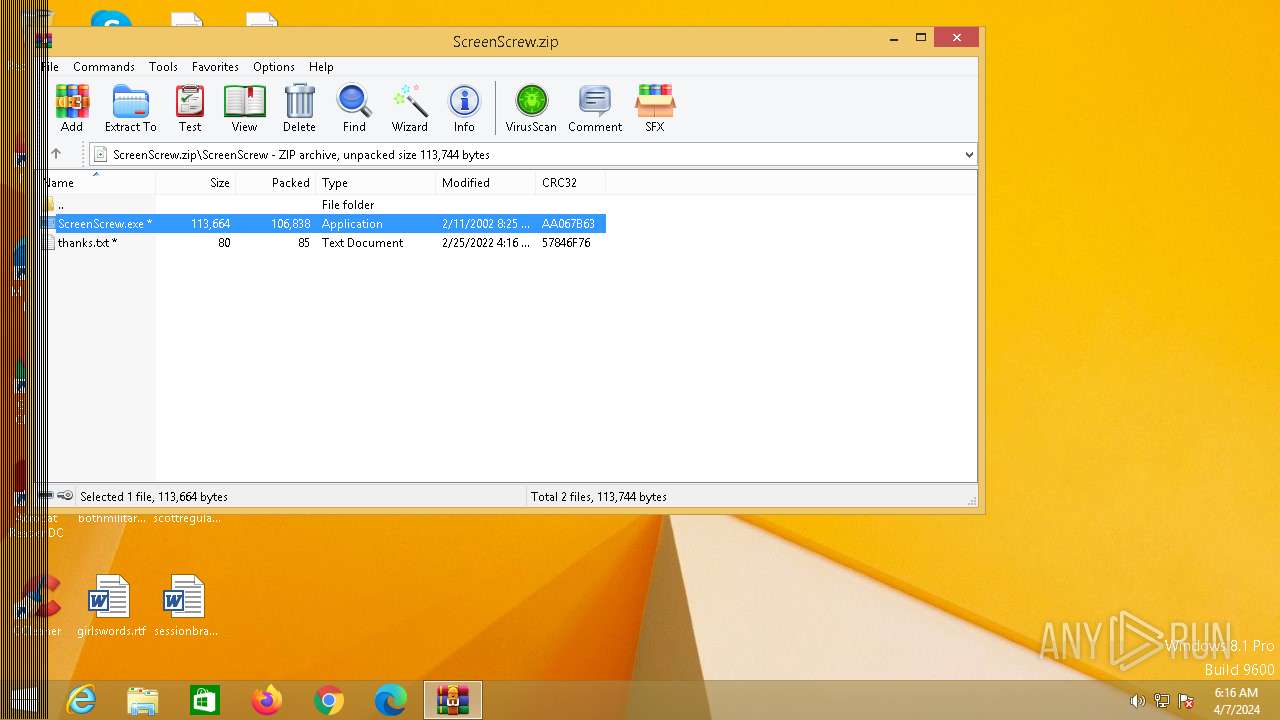
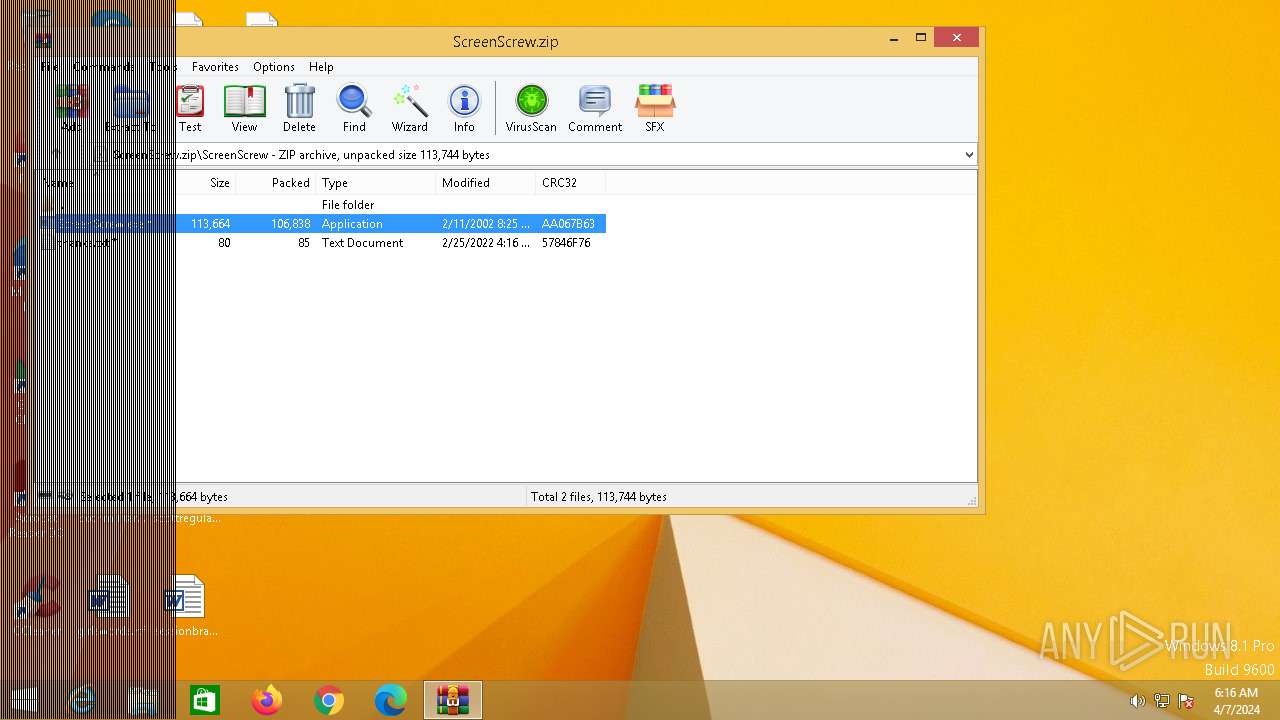
| File name: | ScreenScrew.zip |
| Full analysis: | https://app.any.run/tasks/2bd5d3a8-d42a-416c-ac80-86c8a16d80f6 |
| Verdict: | Malicious activity |
| Analysis date: | April 07, 2024, 13:15:21 |
| OS: | Windows 8.1 Professional (build: 9600, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | 7D7216940ED3873B9A43C88BBFF08B05 |
| SHA1: | 43DD4F3E9264BAC57B1AF80251CD9366743DD90D |
| SHA256: | 88CB7D8959E68CA748C477CE26DF0AE4F75CE243776261DE79951F6AEF75B618 |
| SSDEEP: | 3072:xcRCnp369rFhwRkS2W+8lN8/1VXloPqZYoWgLs2udbtLnalnjJy:xcRCnl69hhwCo+IQ1VXloPmWZdptLnaO |
MALICIOUS
The DLL Hijacking
- integratedoffice.exe (PID: 904)
SUSPICIOUS
Reads the Internet Settings
- slui.exe (PID: 2372)
Non-standard symbols in registry
- winword.exe (PID: 2200)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 1284)
Executes as Windows Service
- integratedoffice.exe (PID: 904)
INFO
Reads the software policy settings
- slui.exe (PID: 2372)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 1284)
Reads Microsoft Office registry keys
- integratedoffice.exe (PID: 904)
Reads the machine GUID from the registry
- integratedoffice.exe (PID: 904)
Checks supported languages
- integratedoffice.exe (PID: 904)
- ScreenScrew.exe (PID: 3040)
Manual execution by a user
- winword.exe (PID: 2200)
Reads the computer name
- integratedoffice.exe (PID: 904)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2022:08:01 11:25:10 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | ScreenScrew/ |
Total processes
56
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 904 | "C:\Program Files\Microsoft Office 15\ClientX64\integratedoffice.exe" | C:\Program Files\Microsoft Office 15\ClientX64\integratedoffice.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Office Click-to-Run Version: 15.0.4433.1508 Modules
| |||||||||||||||
| 1284 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\ScreenScrew.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 1073807364 Version: 5.91.0 Modules
| |||||||||||||||
| 2200 | "C:\Program Files\Microsoft Office 15\Root\Office15\WINWORD.EXE" /n "C:\Users\admin\Desktop\visitorsapply.rtf" /o "" | C:\Program Files\Microsoft Office 15\root\office15\winword.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 15.0.4433.1506 Modules
| |||||||||||||||
| 2372 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 6.3.9600.16384 (winblue_rtm.130821-1623) Modules
| |||||||||||||||
| 3040 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb1284.22960\ScreenScrew\ScreenScrew.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb1284.22960\ScreenScrew\ScreenScrew.exe | WinRAR.exe | ||||||||||||
User: admin Company: RJL Software, Inc. Integrity Level: MEDIUM Description: Screws with your screen :) Exit code: 1073807364 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
17 694
Read events
17 431
Write events
150
Delete events
113
Modification events
| (PID) Process: | (1284) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1284) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1284) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\125\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1284) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\EfiGuard-v1.1.1.zip | |||
| (PID) Process: | (1284) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (1284) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\EfiGuard-v1.1.1-silent.zip | |||
| (PID) Process: | (1284) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\ScreenScrew.zip | |||
| (PID) Process: | (1284) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1284) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1284) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
1
Suspicious files
5
Text files
2
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1284 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb1284.22960\ScreenScrew\ScreenScrew.exe | executable | |
MD5:— | SHA256:— | |||
| 1284 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb1284.22960\ScreenScrew\thanks.txt | text | |
MD5:— | SHA256:— | |||
| 2200 | winword.exe | C:\Users\admin\AppData\Local\Temp\CVR1D87.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2200 | winword.exe | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | binary | |
MD5:— | SHA256:— | |||
| 2200 | winword.exe | C:\Users\admin\Desktop\~$sitorsapply.rtf | binary | |
MD5:— | SHA256:— | |||
| 2200 | winword.exe | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\visitorsapply.rtf.LNK | binary | |
MD5:— | SHA256:— | |||
| 2200 | winword.exe | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:— | SHA256:— | |||
| 2200 | winword.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Word\~WRS{157DB5DD-586D-4F09-9828-38C3B7C9C986}.tmp | binary | |
MD5:— | SHA256:— | |||
| 2200 | winword.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Word\~WRS{531AFE78-3F71-433C-8358-546133488262}.tmp | binary | |
MD5:— | SHA256:— | |||
| 2200 | winword.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Word\~WRF{03B35E45-8285-42FF-B0BD-7CF47BF92DCA}.tmp | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
16
DNS requests
9
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
784 | svchost.exe | GET | 200 | 13.107.246.67:80 | http://clientconfig.passport.net/ppcrlcheck.xml | unknown | — | — | unknown |
784 | svchost.exe | GET | 200 | 23.53.40.10:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?24e8a31ae61b97ed | unknown | — | — | unknown |
784 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.251:5353 | — | — | — | unknown |
976 | slui.exe | 40.91.76.224:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2440 | slui.exe | 40.91.76.224:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
372 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2372 | slui.exe | 40.91.76.224:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1008 | msedge.exe | 13.107.21.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
1008 | msedge.exe | 52.168.117.175:443 | self.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
784 | svchost.exe | 40.126.32.76:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
edge.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
clientconfig.passport.net |
| whitelisted |
login.live.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
WinRAR.exe | SHIMVIEW: ShimInfo(Complete)
|
ScreenScrew.exe | SHIMVIEW: ShimInfo(Complete)
|
winword.exe | SHIMVIEW: ShimInfo(Complete)
|