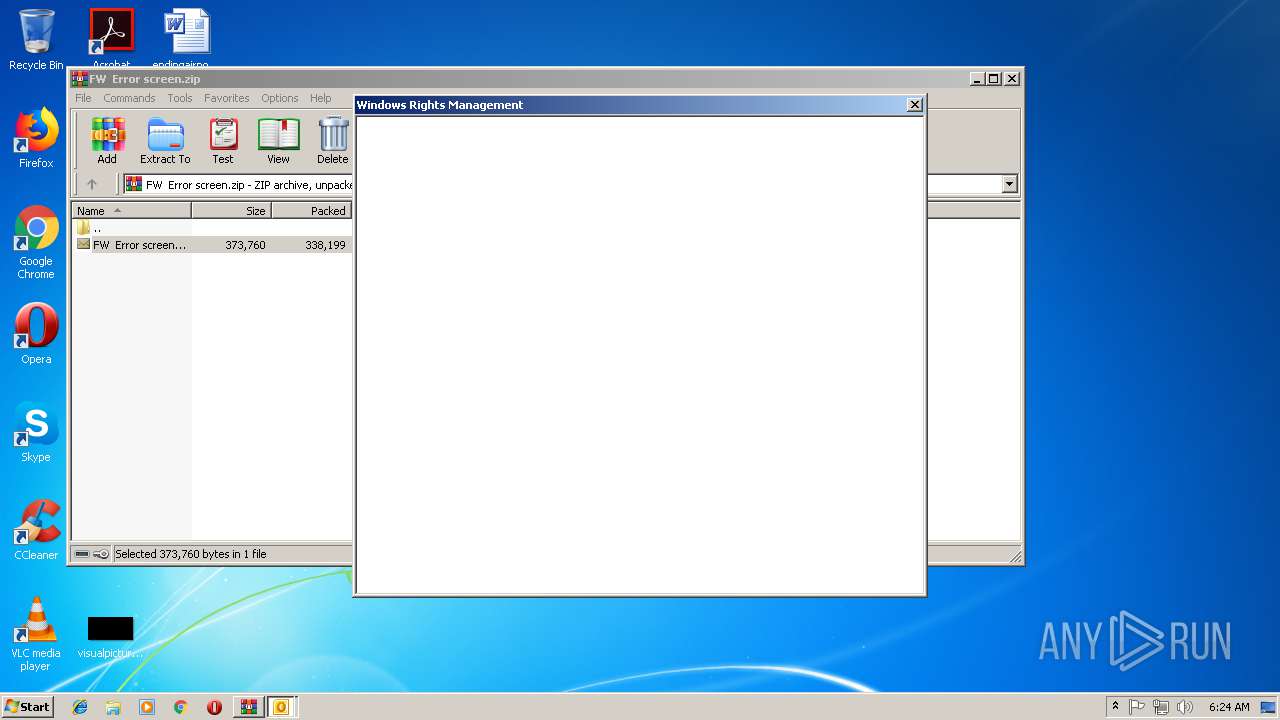
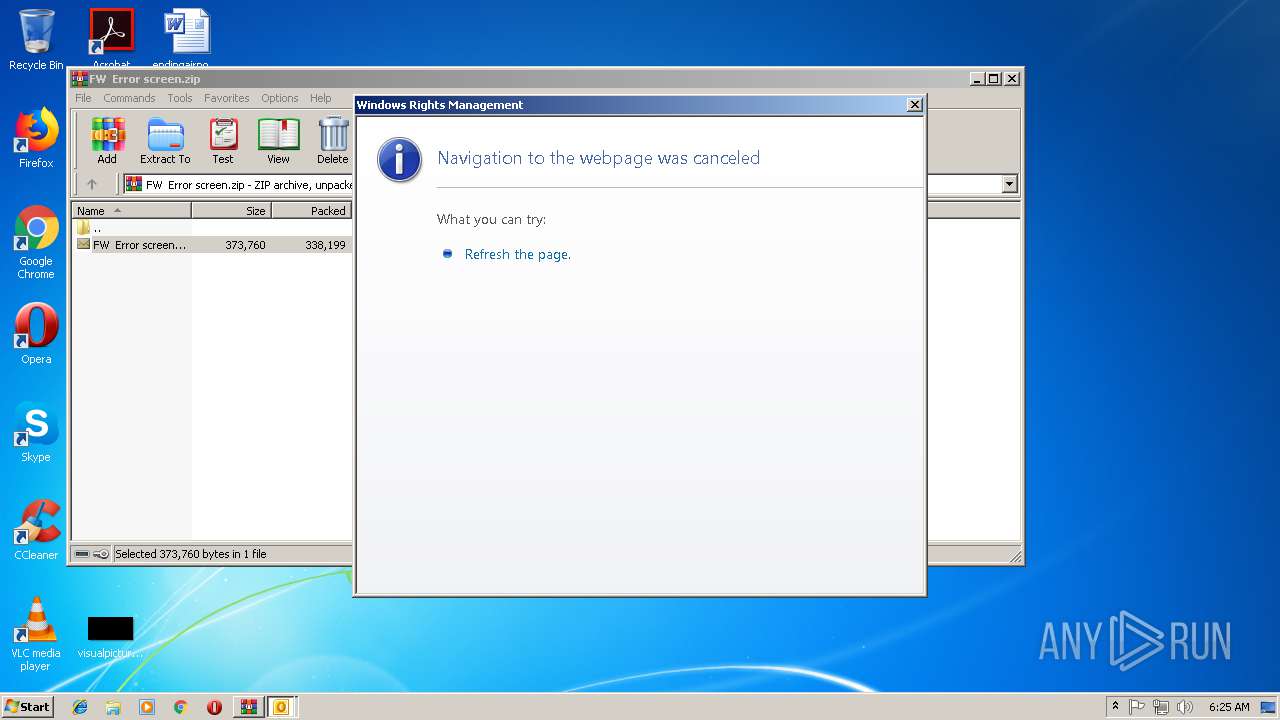
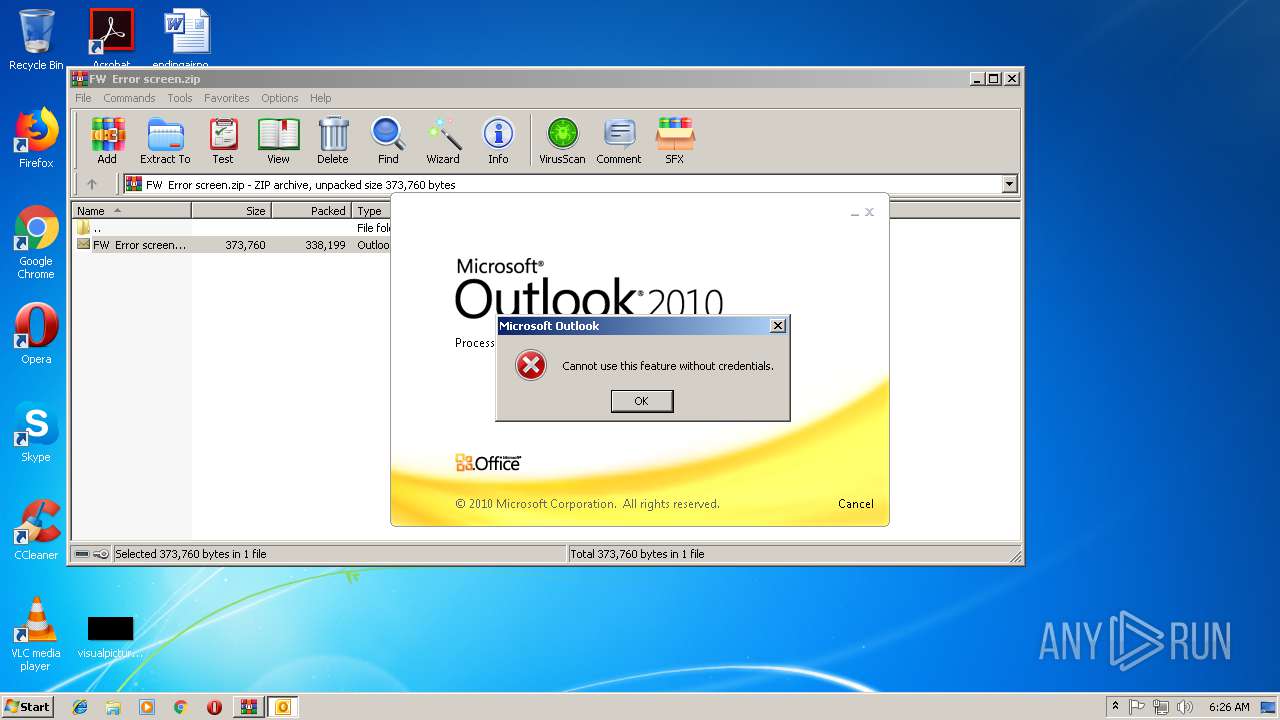
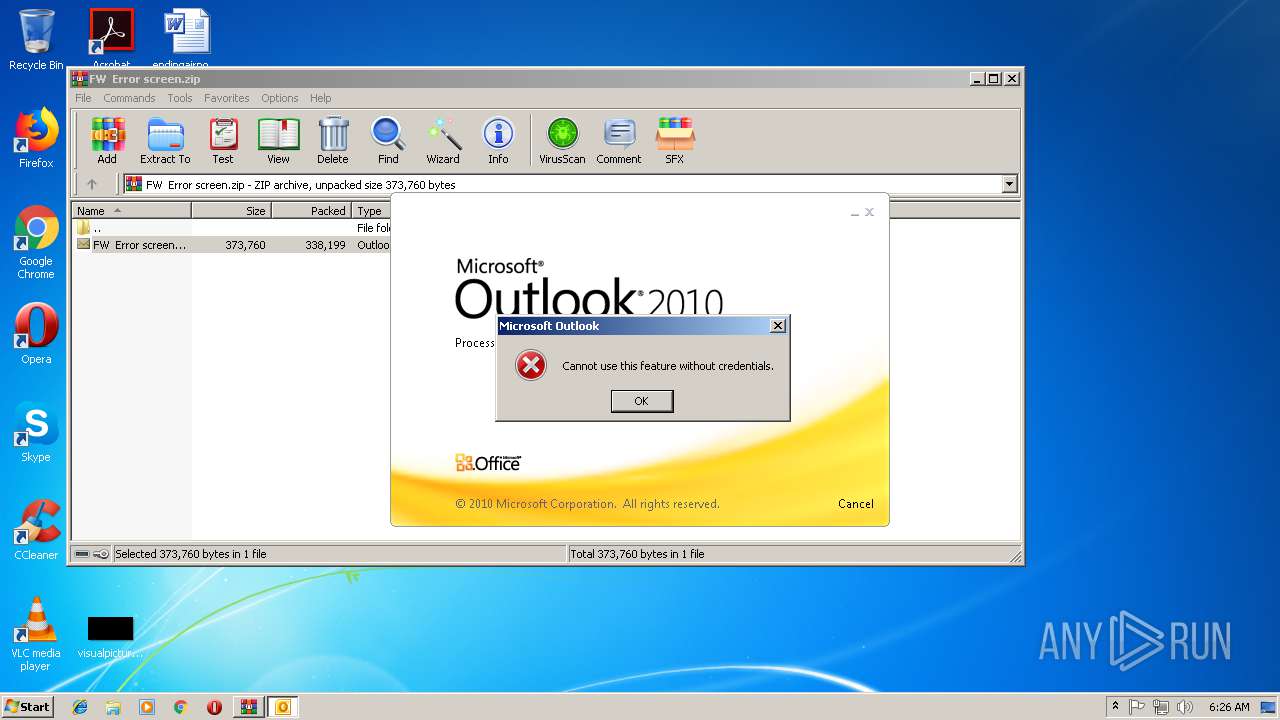
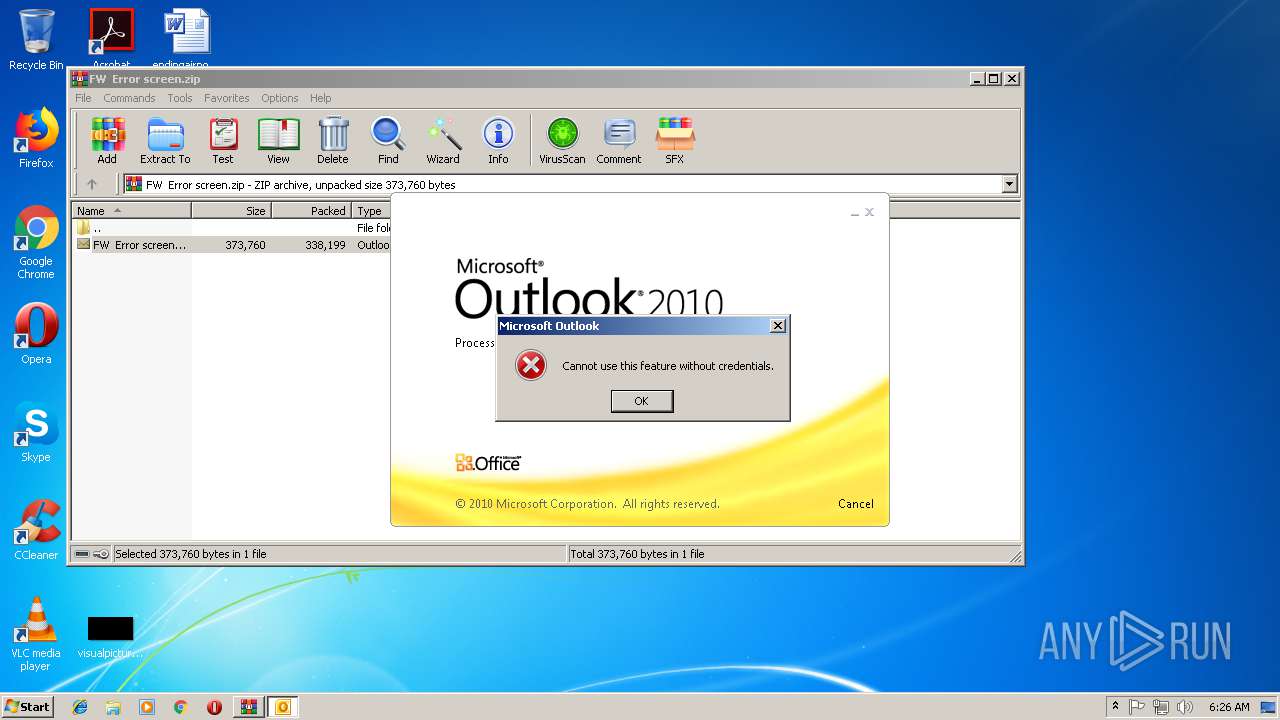
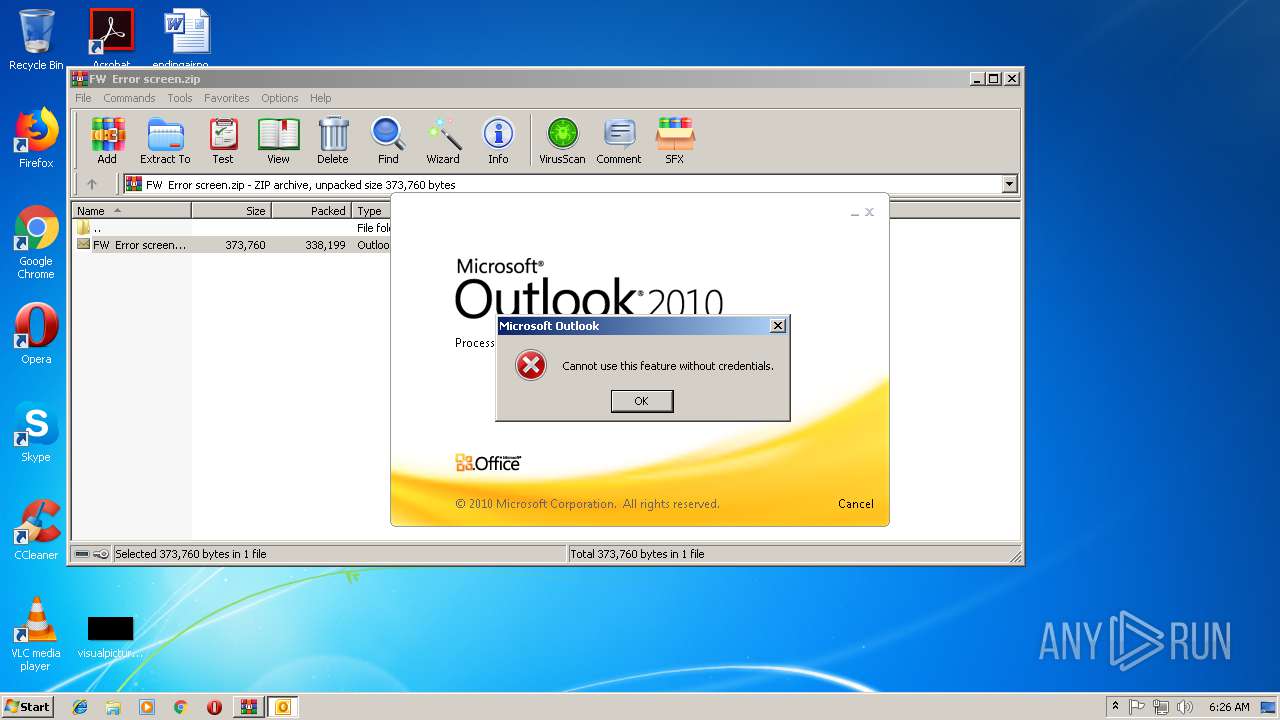
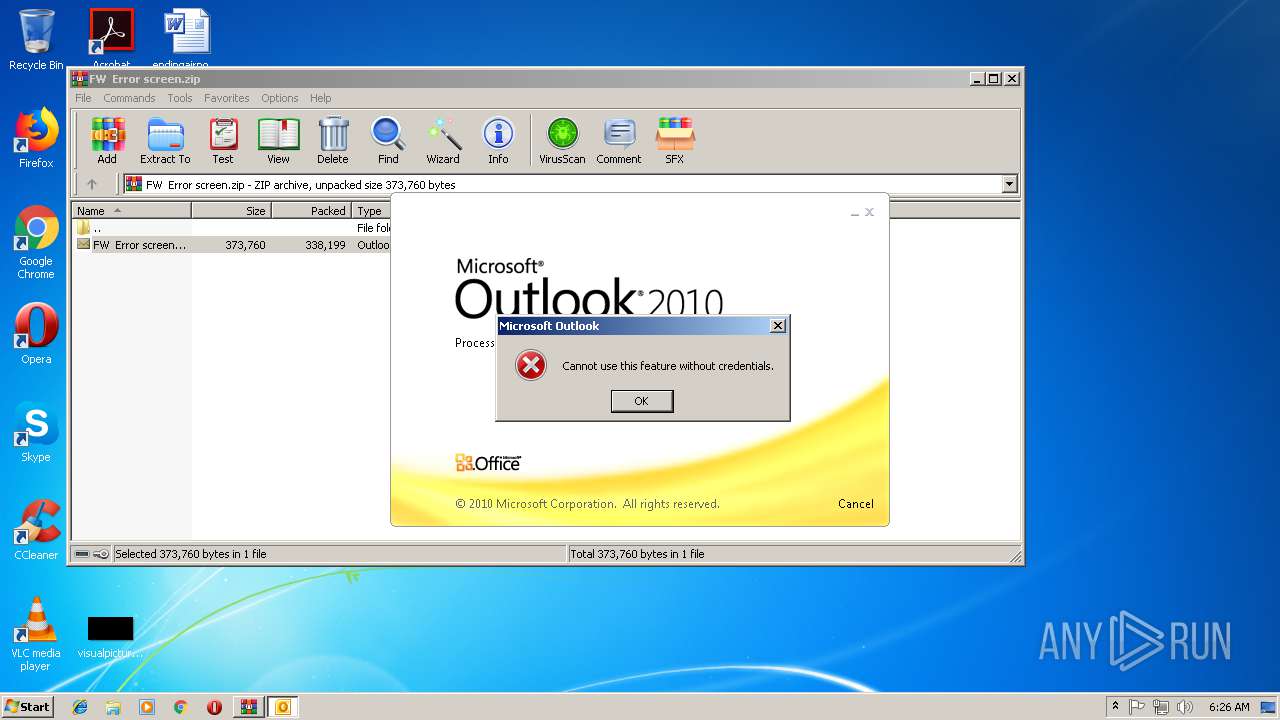
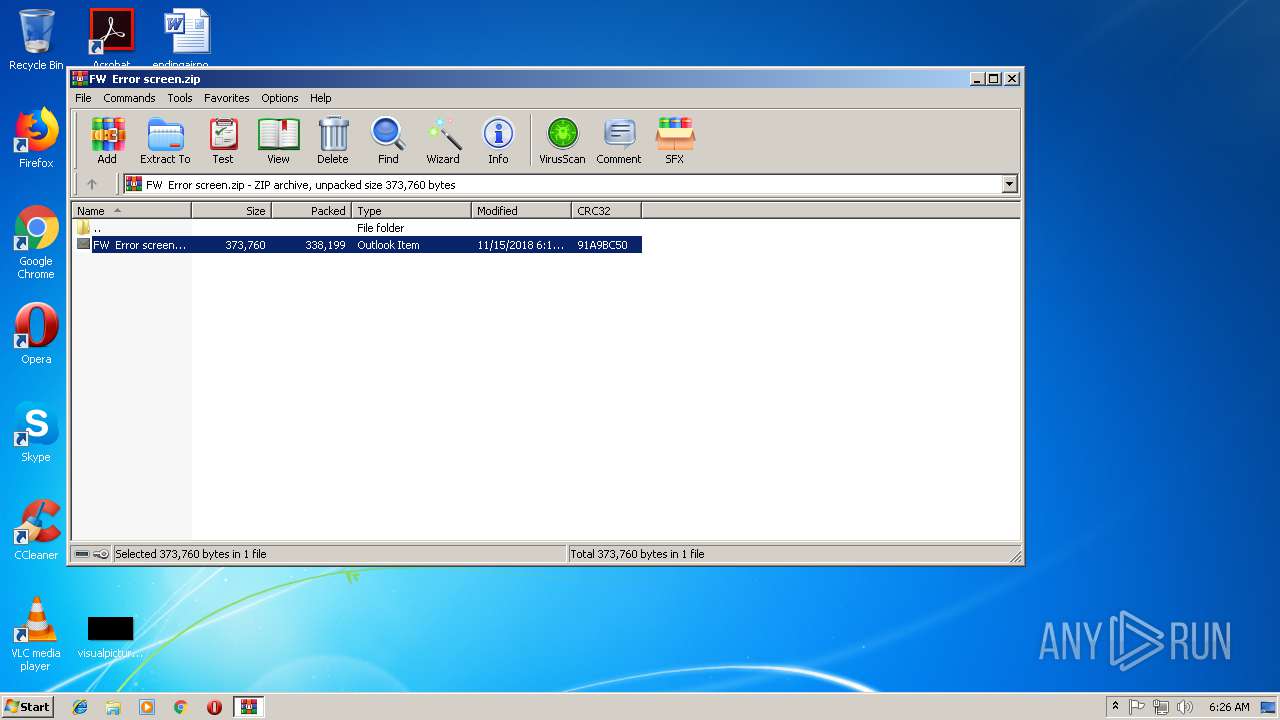
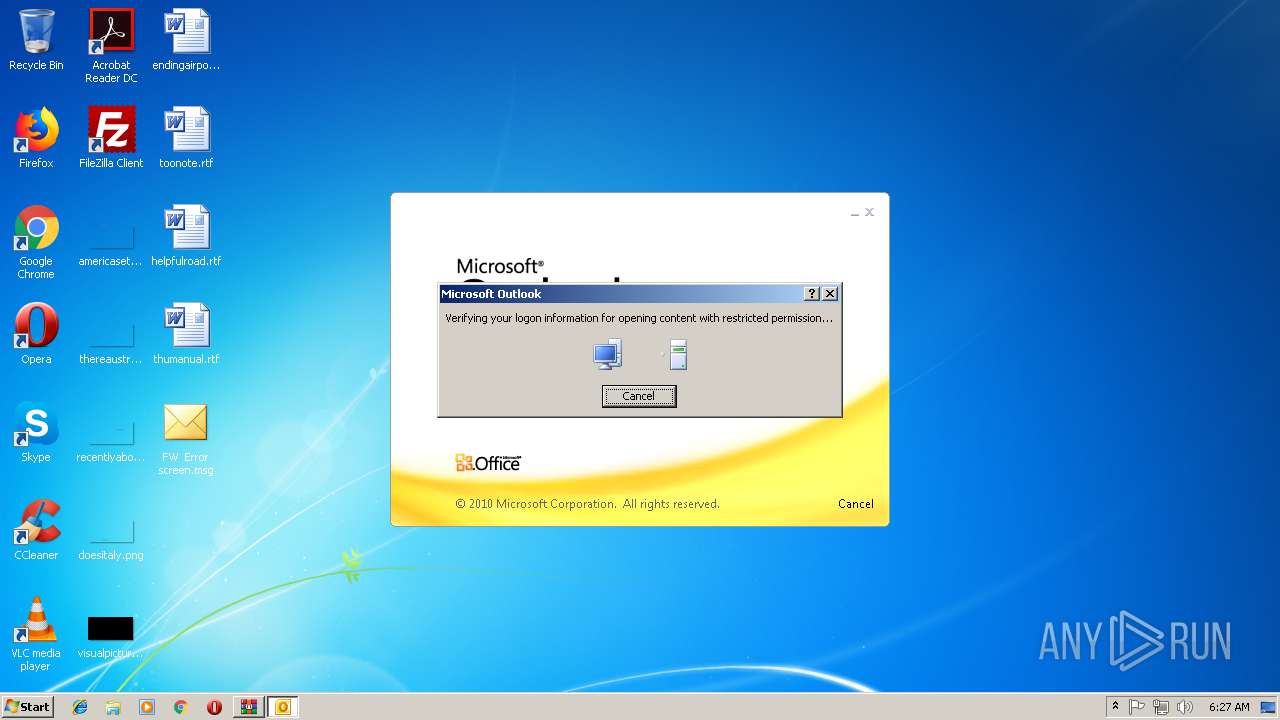
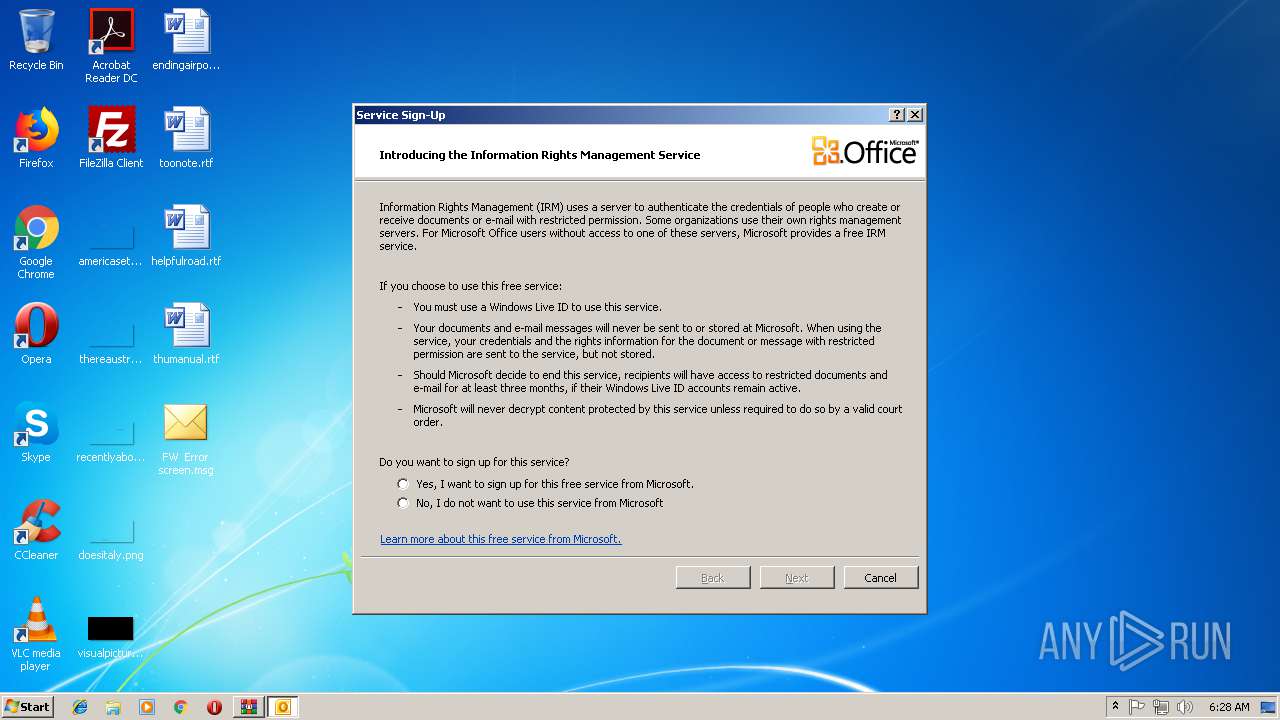
| File name: | FW Error screen.zip |
| Full analysis: | https://app.any.run/tasks/28b79608-39eb-456c-89fb-12874dd05a83 |
| Verdict: | Malicious activity |
| Analysis date: | November 15, 2018, 06:23:14 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | BC482A3ED40F8F3412F0AC1DC2599CB7 |
| SHA1: | EAF125FD984DB22D1B236B91B5C907EE830A605F |
| SHA256: | 88B7BEB41FFA35FEE315C97DDCC571D1B558B898AD5E13B06E2DB15DCD524DE7 |
| SSDEEP: | 6144:BMBS9uOHZxoUZtF270B23M7j2FxyDVsN6s0xMbd5nFCutIxbcE8u+7HzThVLy:BMBuXH/oUB270B23kq8VsNtKM38yIhZv |
MALICIOUS
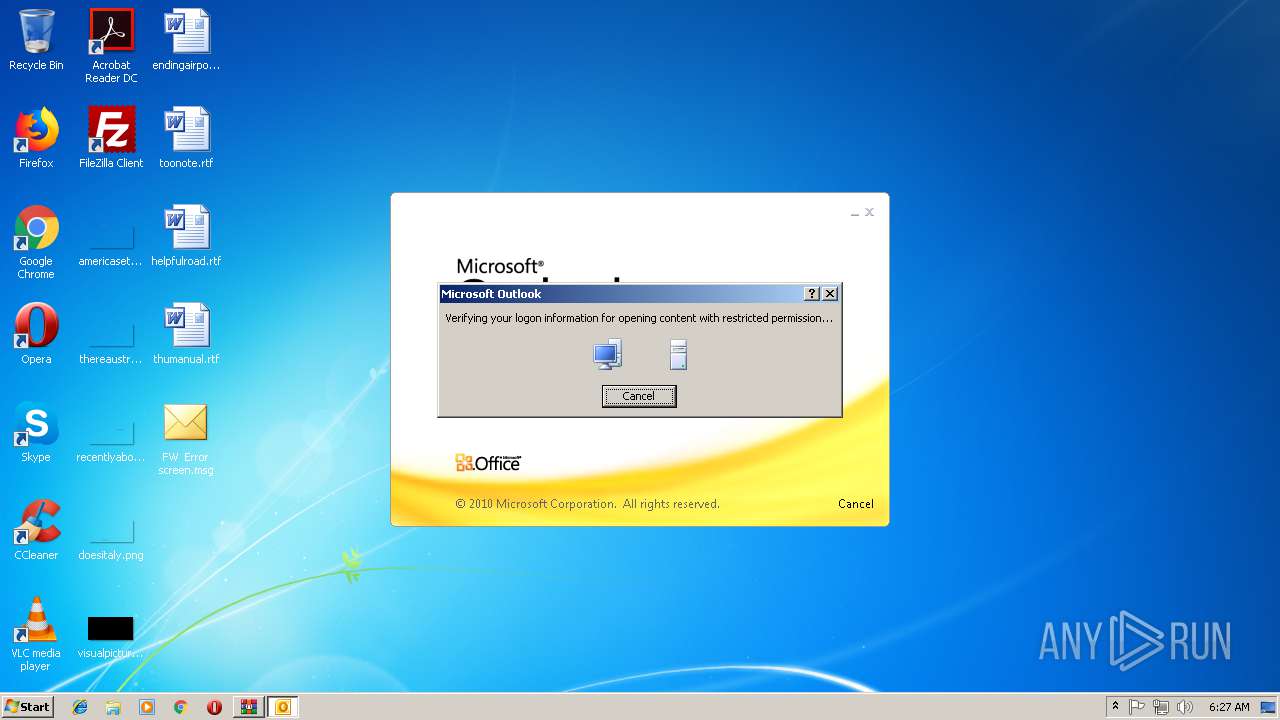
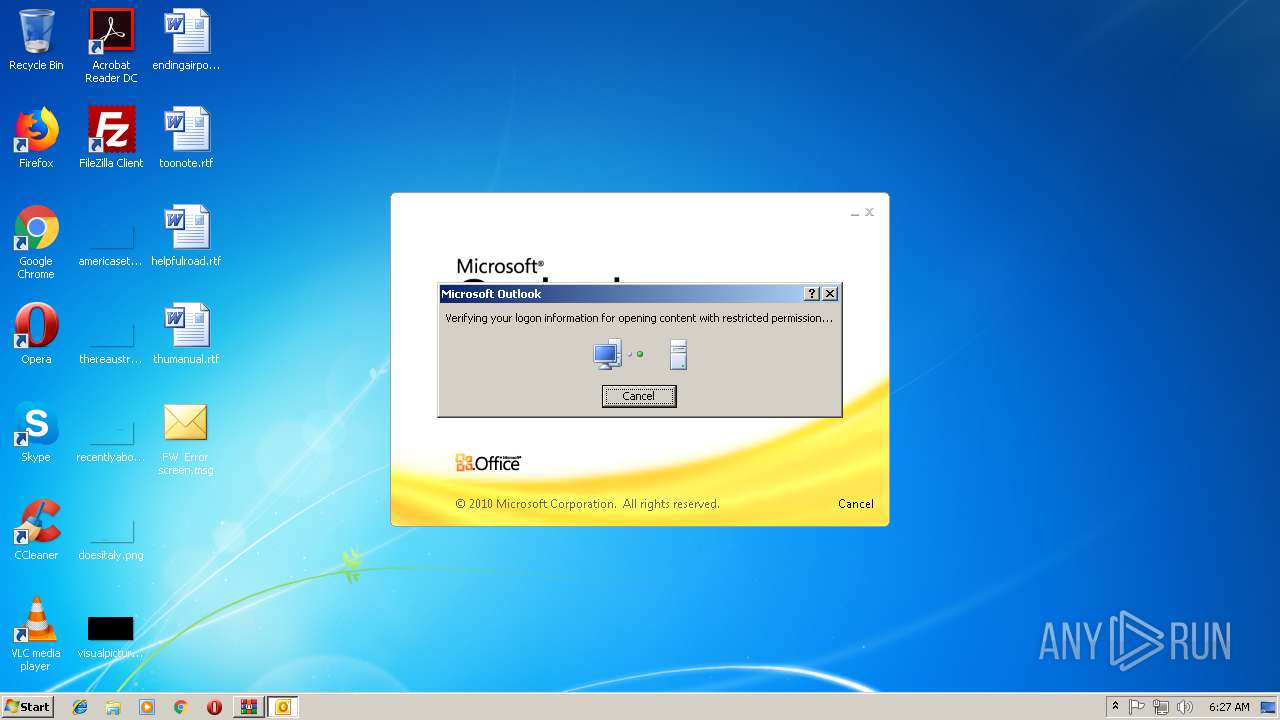
Unusual execution from Microsoft Office
- OUTLOOK.EXE (PID: 1960)
SUSPICIOUS
Reads internet explorer settings
- OUTLOOK.EXE (PID: 1960)
- OUTLOOK.EXE (PID: 3584)
Starts Microsoft Office Application
- WinRAR.exe (PID: 2936)
Reads Internet Cache Settings
- OUTLOOK.EXE (PID: 1960)
- OUTLOOK.EXE (PID: 3584)
INFO
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 1960)
- OUTLOOK.EXE (PID: 3584)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2018:11:15 11:48:11 |
| ZipCRC: | 0x91a9bc50 |
| ZipCompressedSize: | 338199 |
| ZipUncompressedSize: | 373760 |
| ZipFileName: | FW Error screen.msg |
Total processes
38
Monitored processes
4
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
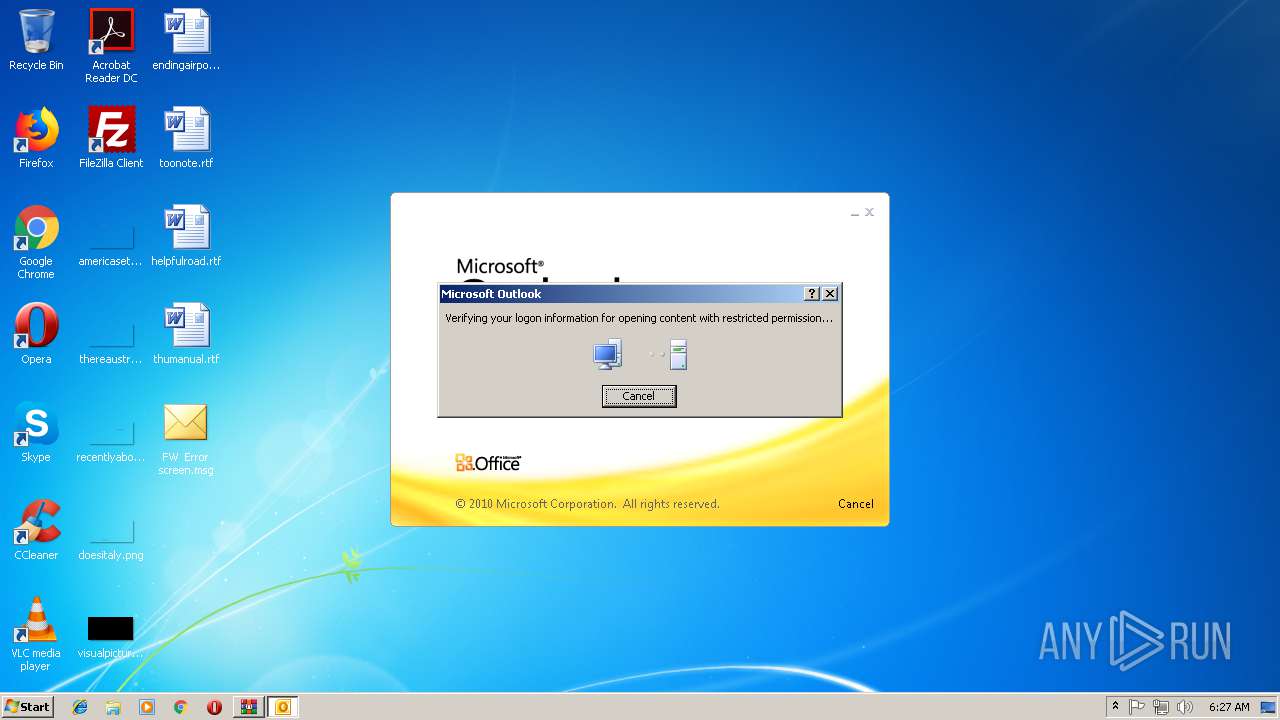
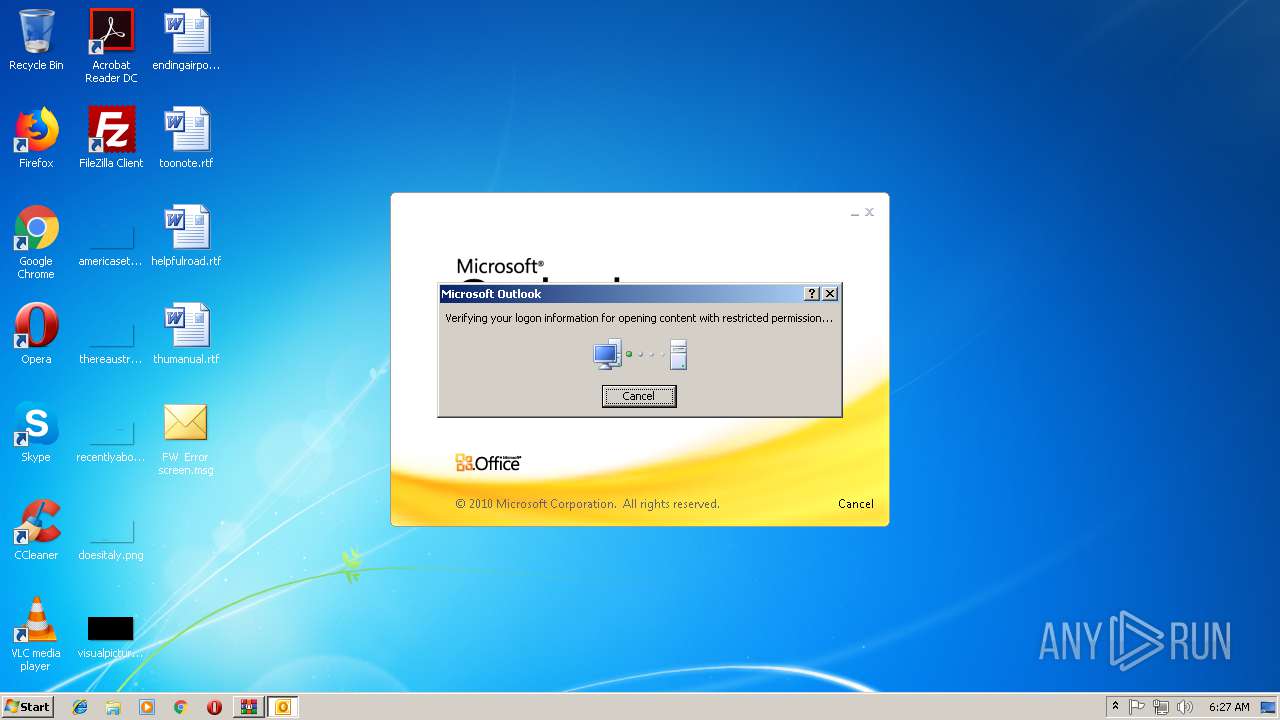
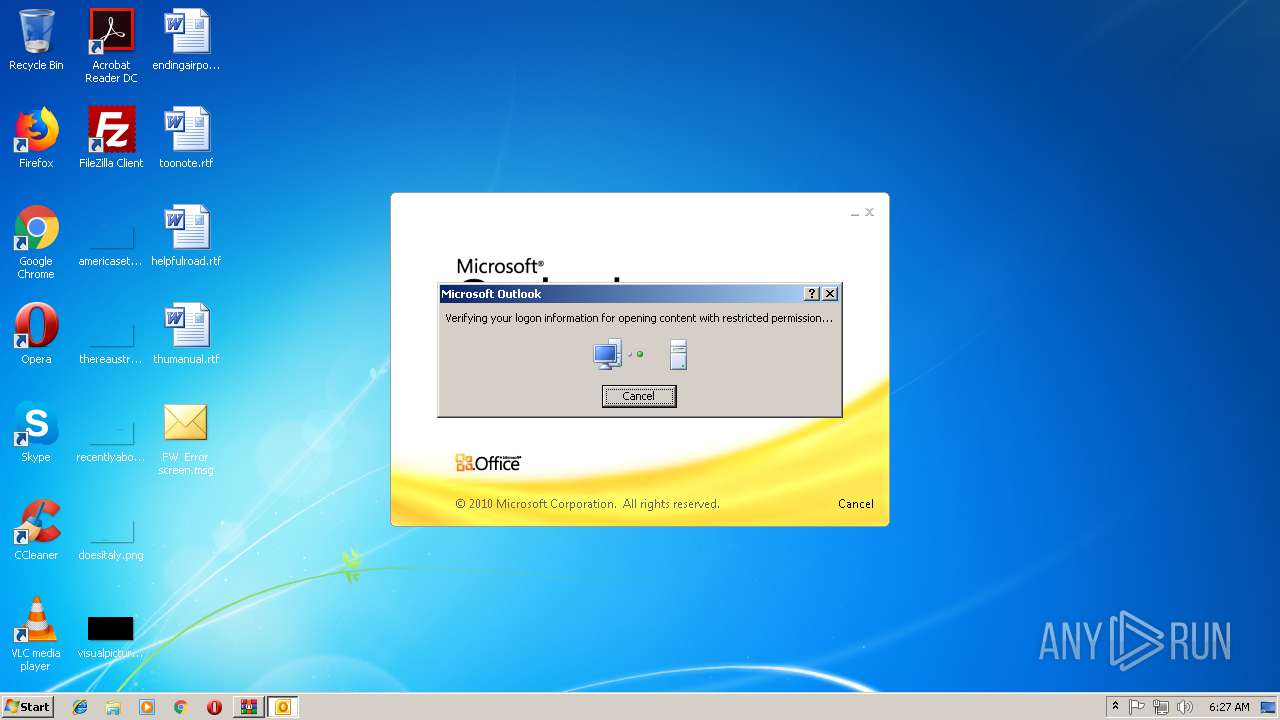
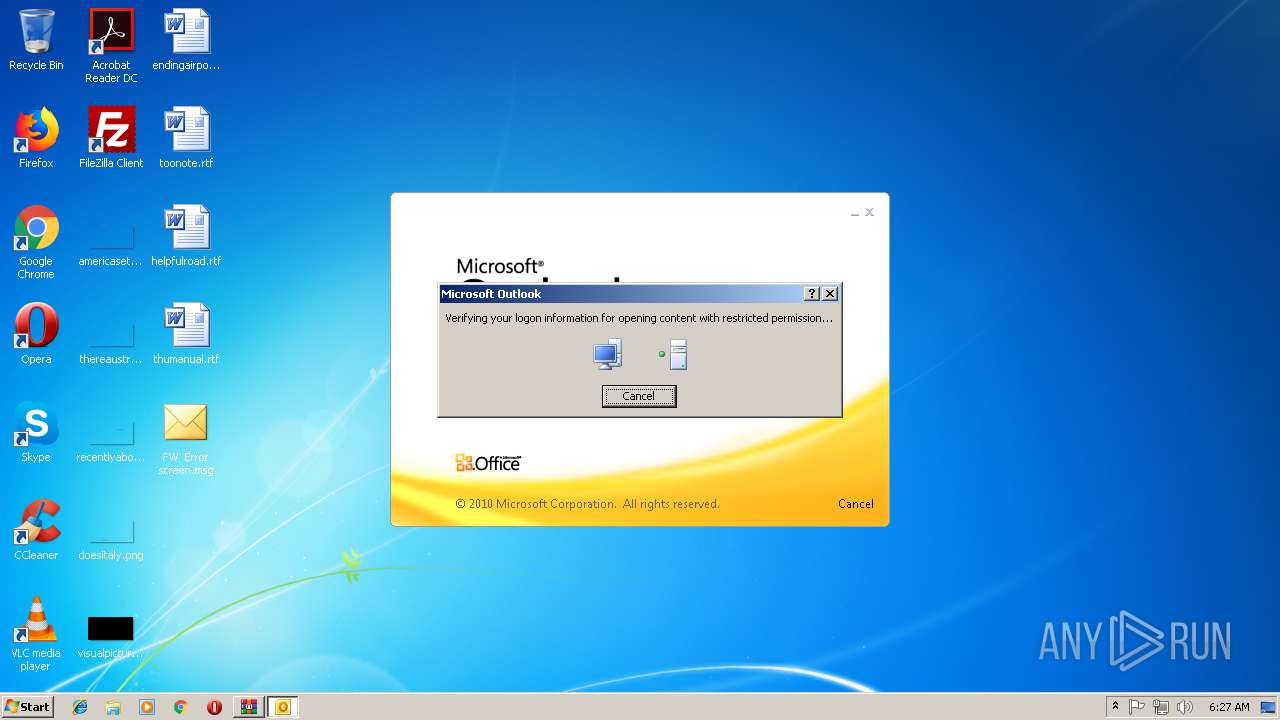
| 1960 | "C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE" /f "C:\Users\admin\AppData\Local\Temp\Rar$DIa2936.4062\FW Error screen.msg" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 2936 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\FW Error screen.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3584 | "C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE" /f "C:\Users\admin\Desktop\FW Error screen.msg" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
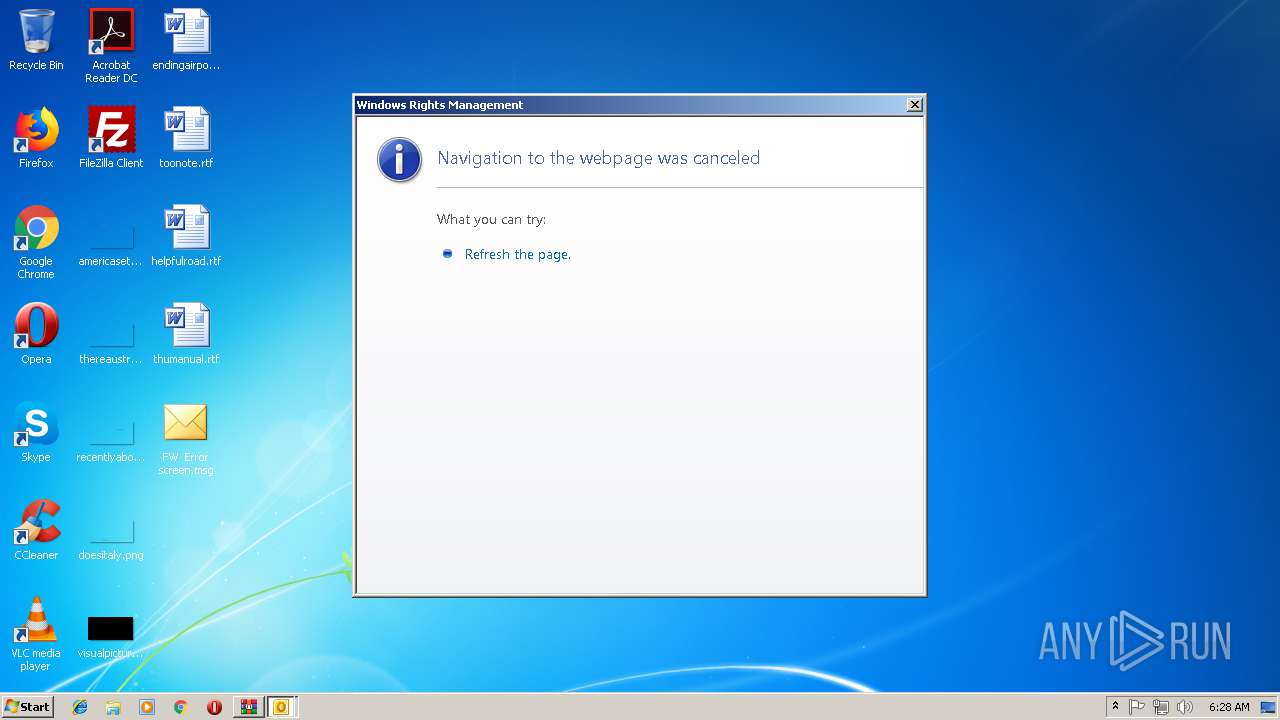
| 3636 | "C:\Windows\system32\rmactivate.exe" | C:\Windows\system32\rmactivate.exe | OUTLOOK.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Rights Management Services Activation for Desktop Security Processor Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 371
Read events
1 253
Write events
115
Delete events
3
Modification events
| (PID) Process: | (2936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2936) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\FW Error screen.zip | |||
| (PID) Process: | (2936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {0006F045-0000-0000-C000-000000000046} {000214FA-0000-0000-C000-000000000046} 0xFFFF |
Value: 010000000000000004E00DC4AB7CD401 | |||
| (PID) Process: | (2936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {0006F045-0000-0000-C000-000000000046} {000214EB-0000-0000-C000-000000000046} 0xFFFF |
Value: 0100000000000000B8A412C4AB7CD401 | |||
Executable files
0
Suspicious files
13
Text files
56
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1960 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVRE9AF.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1960 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\RB73MZ6Y\ServiceLocator[1].asmx | — | |
MD5:— | SHA256:— | |||
| 3636 | rmactivate.exe | C:\Users\admin\AppData\Local\Temp\CabF604.tmp | — | |
MD5:— | SHA256:— | |||
| 3636 | rmactivate.exe | C:\Users\admin\AppData\Local\Temp\TarF605.tmp | — | |
MD5:— | SHA256:— | |||
| 1960 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0UU90R59\ErrorPageTemplate[1] | — | |
MD5:— | SHA256:— | |||
| 1960 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\RB73MZ6Y\errorPageStrings[1] | — | |
MD5:— | SHA256:— | |||
| 1960 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\R9ZEWH8D\httpErrorPagesScripts[1] | — | |
MD5:— | SHA256:— | |||
| 2936 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa2936.4062\FW Error screen.msg | msg | |
MD5:— | SHA256:— | |||
| 1960 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\~Outlook Data File - NoMail.pst.tmp | — | |
MD5:— | SHA256:— | |||
| 1960 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\IZR9TV1Q\message.rpmsg | rpmsg | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
21
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1960 | OUTLOOK.EXE | GET | 302 | 104.111.243.236:80 | http://go.microsoft.com/fwlink/?LinkId=5998&LANGID=1033 | NL | — | — | whitelisted |
3584 | OUTLOOK.EXE | GET | 302 | 104.111.243.236:80 | http://go.microsoft.com/fwlink/?LinkId=5998&LANGID=1033 | NL | — | — | whitelisted |
3636 | rmactivate.exe | GET | 200 | 2.16.186.74:80 | http://crl.microsoft.com/pki/crl/products/MicrosoftTimeStampPCA.crl | unknown | der | 550 b | whitelisted |
3584 | OUTLOOK.EXE | GET | 200 | 2.16.186.74:80 | http://crl.microsoft.com/pki/crl/products/tspca.crl | unknown | der | 521 b | whitelisted |
3636 | rmactivate.exe | GET | 200 | 2.16.186.74:80 | http://crl.microsoft.com/pki/crl/products/microsoftrootcert.crl | unknown | der | 781 b | whitelisted |
3636 | rmactivate.exe | GET | 200 | 2.16.186.74:80 | http://crl.microsoft.com/pki/crl/products/WinPCA.crl | unknown | der | 530 b | whitelisted |
3584 | OUTLOOK.EXE | GET | 200 | 2.16.186.74:80 | http://crl.microsoft.com/pki/crl/products/CSPCA.crl | unknown | der | 506 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1960 | OUTLOOK.EXE | 13.107.6.181:443 | 6e7e26ce-8ca5-41b5-a6bd-d8192a7abe2e.rms.ap.aadrm.com | Microsoft Corporation | US | suspicious |
3636 | rmactivate.exe | 2.16.186.74:80 | crl.microsoft.com | Akamai International B.V. | — | whitelisted |
1960 | OUTLOOK.EXE | 104.111.243.236:80 | go.microsoft.com | Akamai International B.V. | NL | whitelisted |
3584 | OUTLOOK.EXE | 65.55.61.29:443 | certification.drm.microsoft.com | Microsoft Corporation | US | whitelisted |
1960 | OUTLOOK.EXE | 65.55.61.29:443 | certification.drm.microsoft.com | Microsoft Corporation | US | whitelisted |
3584 | OUTLOOK.EXE | 104.111.243.236:80 | go.microsoft.com | Akamai International B.V. | NL | whitelisted |
3584 | OUTLOOK.EXE | 13.107.6.181:443 | 6e7e26ce-8ca5-41b5-a6bd-d8192a7abe2e.rms.ap.aadrm.com | Microsoft Corporation | US | suspicious |
3584 | OUTLOOK.EXE | 2.16.186.74:80 | crl.microsoft.com | Akamai International B.V. | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
6e7e26ce-8ca5-41b5-a6bd-d8192a7abe2e.rms.ap.aadrm.com |
| suspicious |
crl.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
certification.drm.microsoft.com |
| whitelisted |