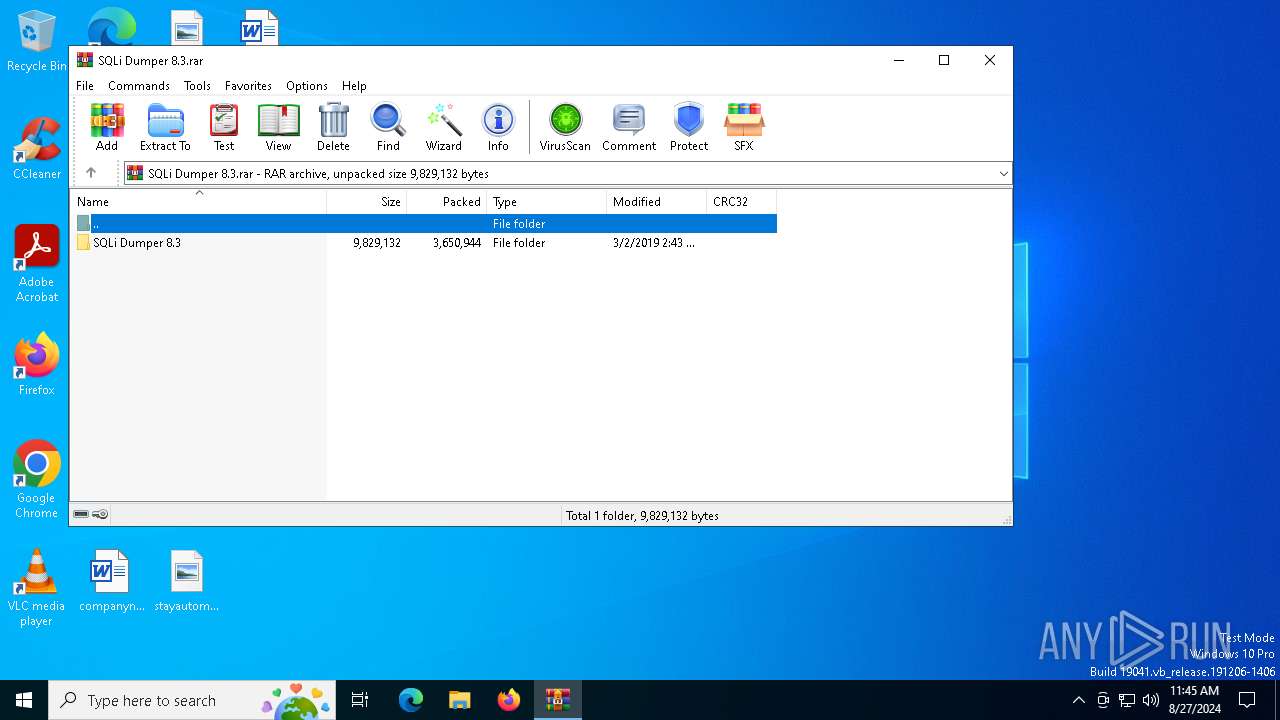
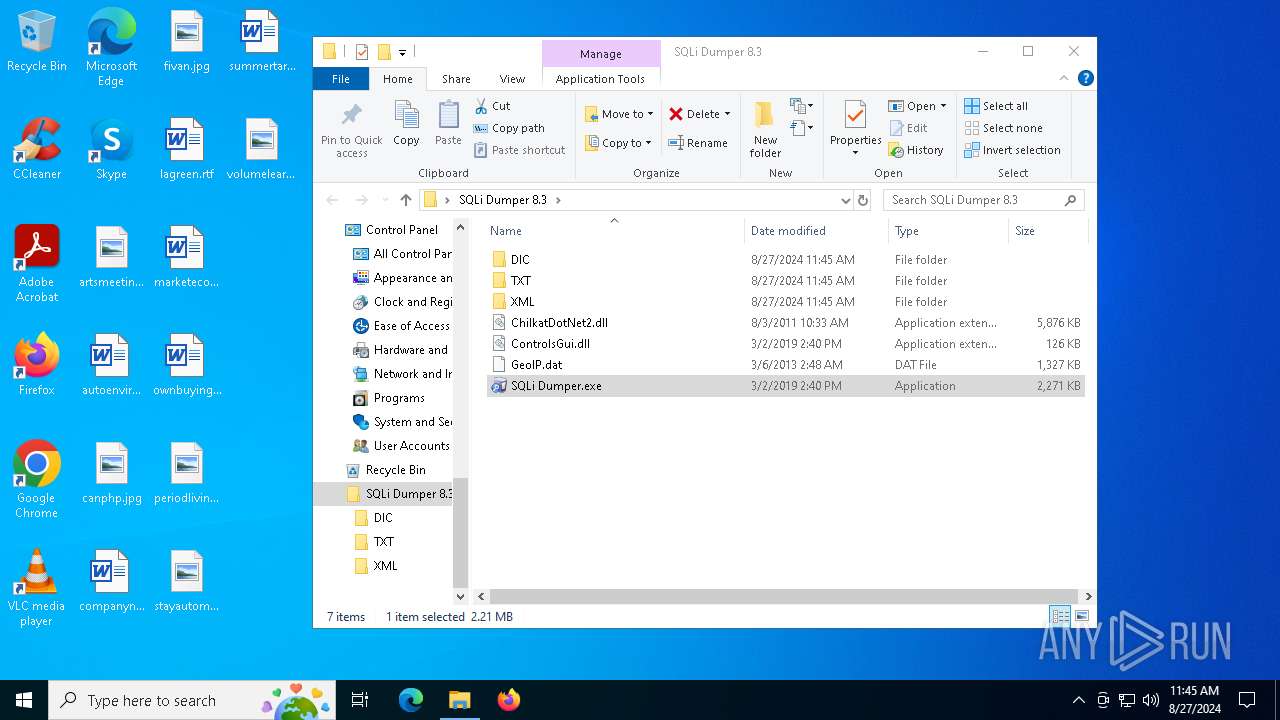
| File name: | SQLi Dumper 8.3.rar |
| Full analysis: | https://app.any.run/tasks/edcf6aa6-0300-464c-ad3f-e31b93e39904 |
| Verdict: | Malicious activity |
| Analysis date: | August 27, 2024, 11:45:00 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | CC96828D159EAF9218E09693CEB39755 |
| SHA1: | FAE99B704EA2E895FC42BE084D0B34EC72D36670 |
| SHA256: | 88B0031BC611EE20B27C96A9FD1910D610987D08962A2D1EC51EF599FA5E1633 |
| SSDEEP: | 98304:j1ztOm5JFNG8MbqtqjrHajwSaVTpEu4Khslcr0GV17T3TlMg4VqkfubOUWsiYzxb:Oal62A31VNh |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads security settings of Internet Explorer
- SQLi Dumper.exe (PID: 3352)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 5388)
Reads Microsoft Outlook installation path
- SQLi Dumper.exe (PID: 3352)
Reads Internet Explorer settings
- SQLi Dumper.exe (PID: 3352)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5388)
Manual execution by a user
- SQLi Dumper.exe (PID: 3352)
Reads the machine GUID from the registry
- SQLi Dumper.exe (PID: 3352)
Reads Environment values
- SQLi Dumper.exe (PID: 3352)
Checks supported languages
- SQLi Dumper.exe (PID: 3352)
Reads the computer name
- SQLi Dumper.exe (PID: 3352)
Process checks Internet Explorer phishing filters
- SQLi Dumper.exe (PID: 3352)
Checks proxy server information
- SQLi Dumper.exe (PID: 3352)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
129
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2068 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
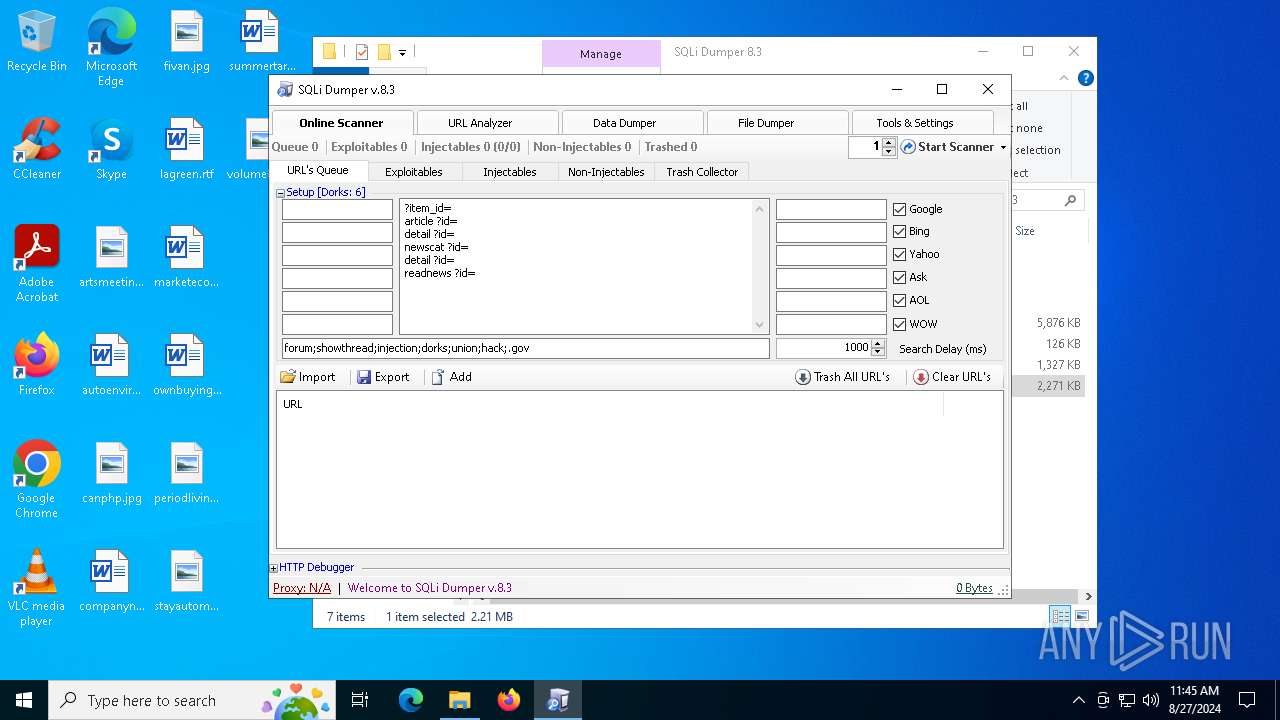
| 3352 | "C:\Users\admin\Desktop\SQLi Dumper 8.3\SQLi Dumper.exe" | C:\Users\admin\Desktop\SQLi Dumper 8.3\SQLi Dumper.exe | — | explorer.exe | |||||||||||
User: admin Company: c4rl0s@jabber.ru Integrity Level: MEDIUM Description: SQLi Dumper Version: 8.3.0.0 Modules
| |||||||||||||||
| 5388 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\SQLi Dumper 8.3.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
6 873
Read events
6 843
Write events
30
Delete events
0
Modification events
| (PID) Process: | (5388) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (5388) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (5388) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (5388) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\SQLi Dumper 8.3.rar | |||
| (PID) Process: | (5388) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5388) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5388) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5388) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5388) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (5388) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\AppData\Local\Temp | |||
Executable files
3
Suspicious files
1
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5388 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5388.42723\SQLi Dumper 8.3\GeoIP.dat | binary | |
MD5:CB9AD69965F9F4CFF8572983F60BE67C | SHA256:56C7079DC309168D9C41DD4A7A61033ACD264A120CA8D2E2182ABB5B9AE6B0A3 | |||
| 5388 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5388.42723\SQLi Dumper 8.3\SQLi Dumper.exe | executable | |
MD5:E5D3F124126A4B1FAA148FC8ECEDF433 | SHA256:3F3ED131FE2A88B0085F5F2E1C5BCDDA32D7C76BCF3F28F82065048966887706 | |||
| 3352 | SQLi Dumper.exe | C:\Users\admin\Desktop\SQLi Dumper 8.3\DIC\dic_file_dump.txt | text | |
MD5:351CACFFC2884FCD4E69BB1FB04DDEB5 | SHA256:C67BCC0B4ED5E5EF72AA1134C0838D9201A97C2BF462FDFF0AC9052A53B286A2 | |||
| 5388 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5388.42723\SQLi Dumper 8.3\ChilkatDotNet2.dll | executable | |
MD5:6990F5076EB51EE135492BA5BA619B72 | SHA256:6733F1B7DAF40076FFE88DC8A88E23181D1BA449D6E5BB36A5325B4353849460 | |||
| 3352 | SQLi Dumper.exe | C:\Users\admin\Desktop\SQLi Dumper 8.3\DIC\dic_admin.txt | text | |
MD5:A0E54634DDD435DF5B82E20EA20C7EFE | SHA256:963E3A1E46D5F4C35B85464DB61B7C346C5C44669E64A5C016192DDE078F997A | |||
| 5388 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5388.42723\SQLi Dumper 8.3\ControlsGui.dll | executable | |
MD5:F6660AE3A390595E834D1DAEBB14136B | SHA256:276FCEECF4199B6352D073D8DA7C143D47BB9CD03B6A9546154D99832F0C47F5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
21
DNS requests
13
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2032 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3672 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3672 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
736 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6192 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6192 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3260 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2032 | svchost.exe | 20.190.160.20:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2032 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |