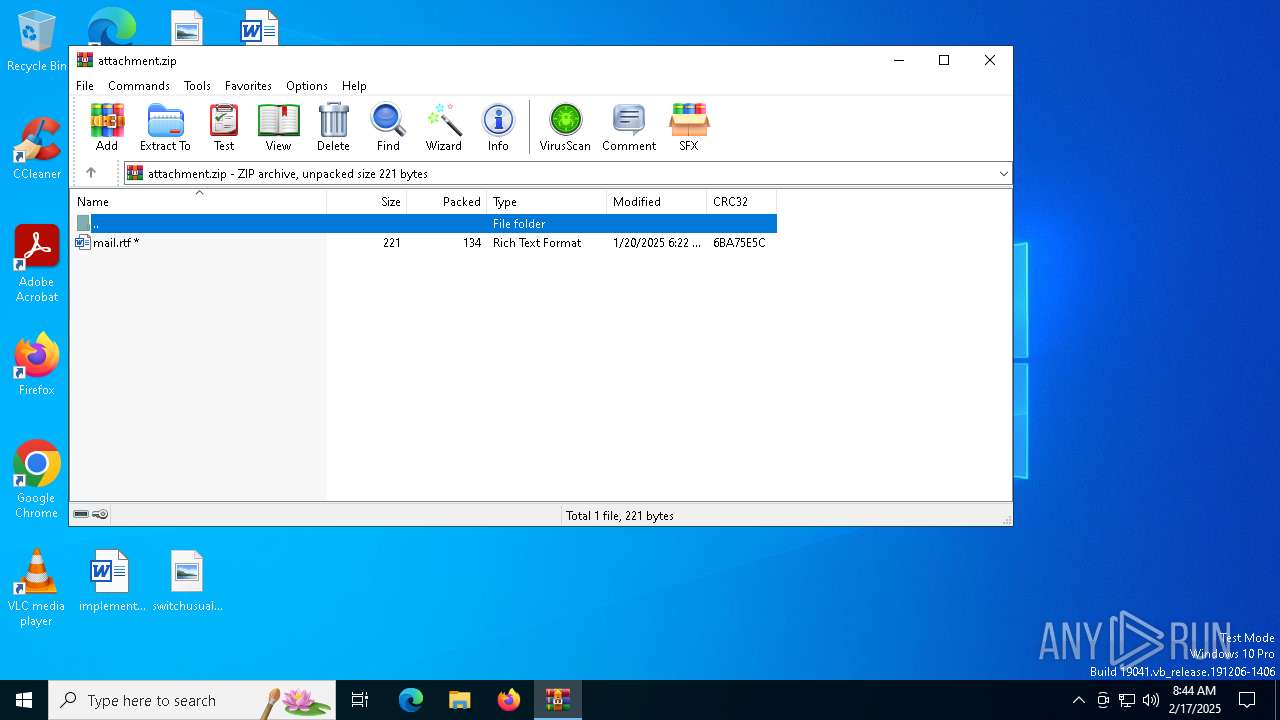
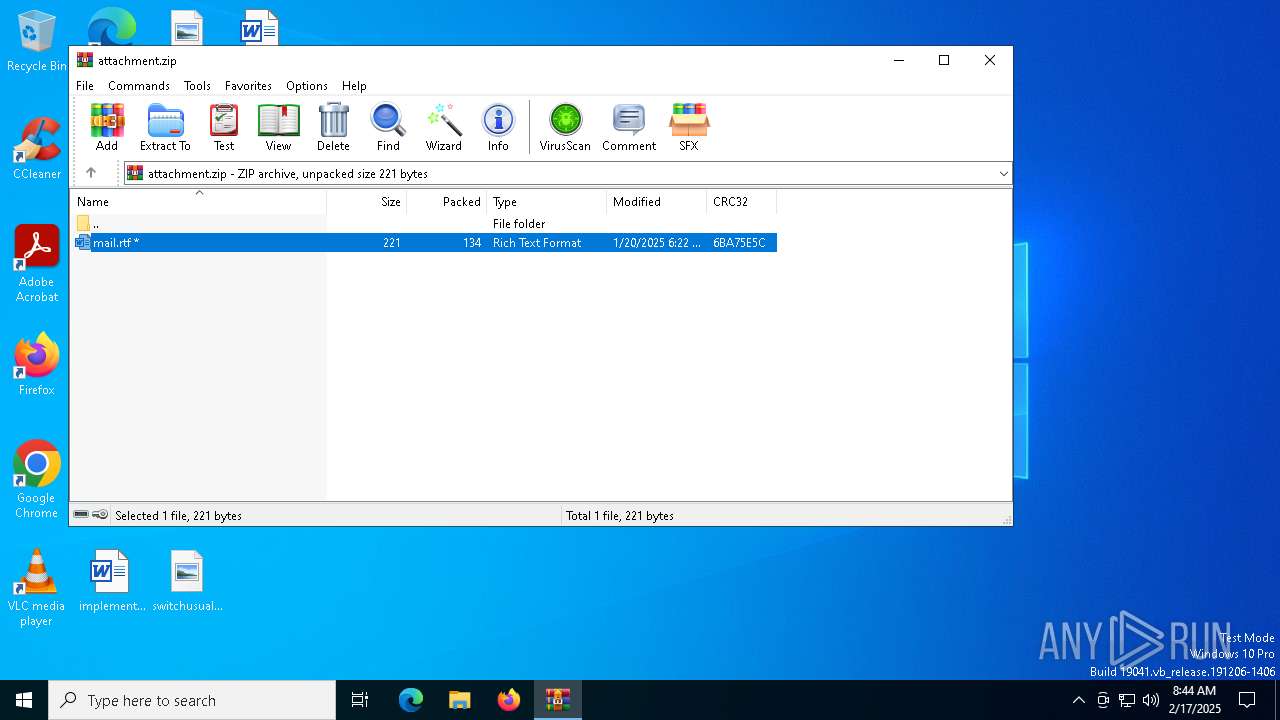
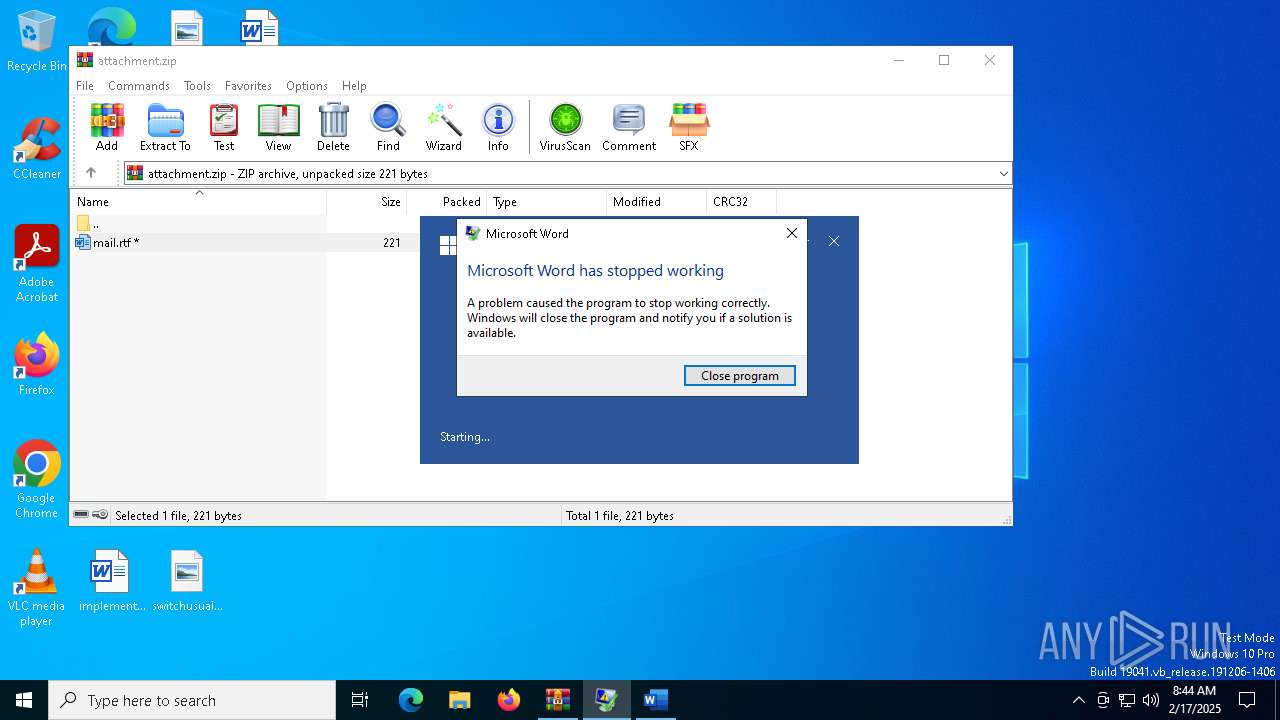
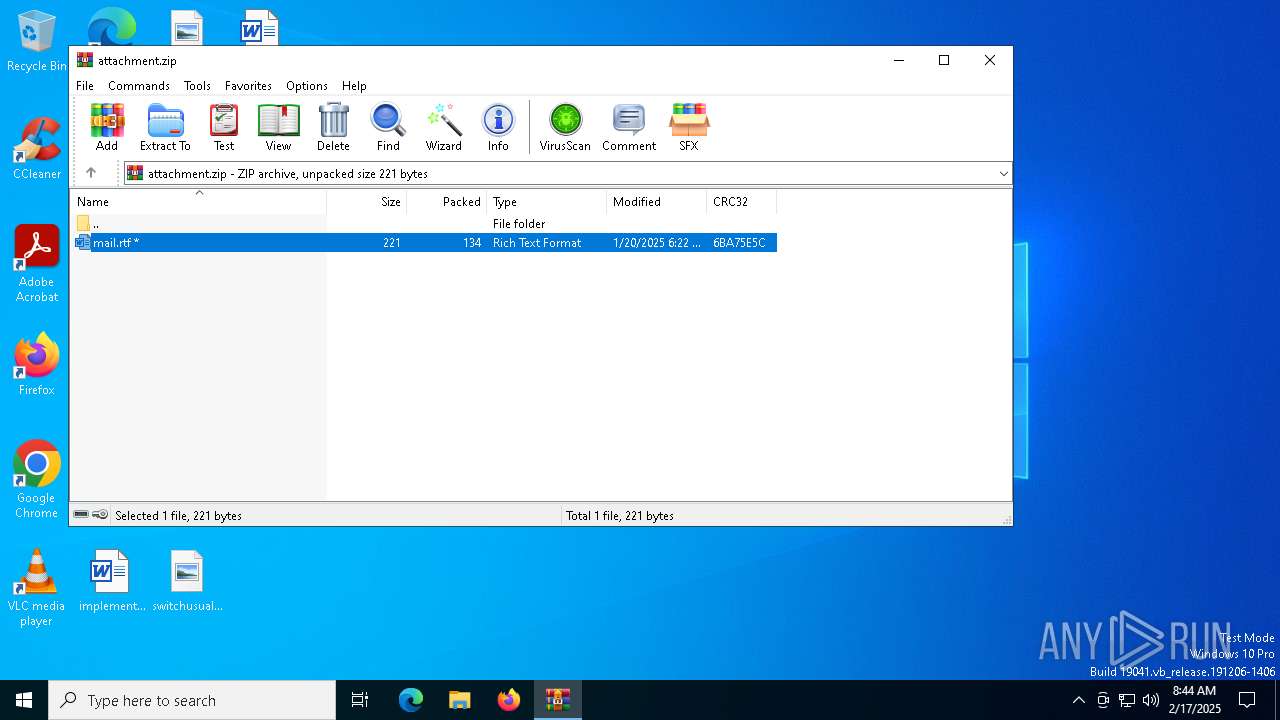
| File name: | attachment.zip |
| Full analysis: | https://app.any.run/tasks/ed4a10b7-6255-46da-b99a-14dacbdf1995 |
| Verdict: | Suspicious activity |
| Analysis date: | February 17, 2025, 08:44:25 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | E0DD5DB184384CB5A9B1762906DB0C95 |
| SHA1: | 55F99C69399134EE39C7CE9E30CD268E7536B82F |
| SHA256: | 889D79E7E004891E2A887C3A11D37DDD7E9028D53BB33622AE12685776181068 |
| SSDEEP: | 12:5jDadqyLS9zTbKLoPaTAu8IqMIadg5Htab:9vlTbavTAu8Iz2Y |
MALICIOUS
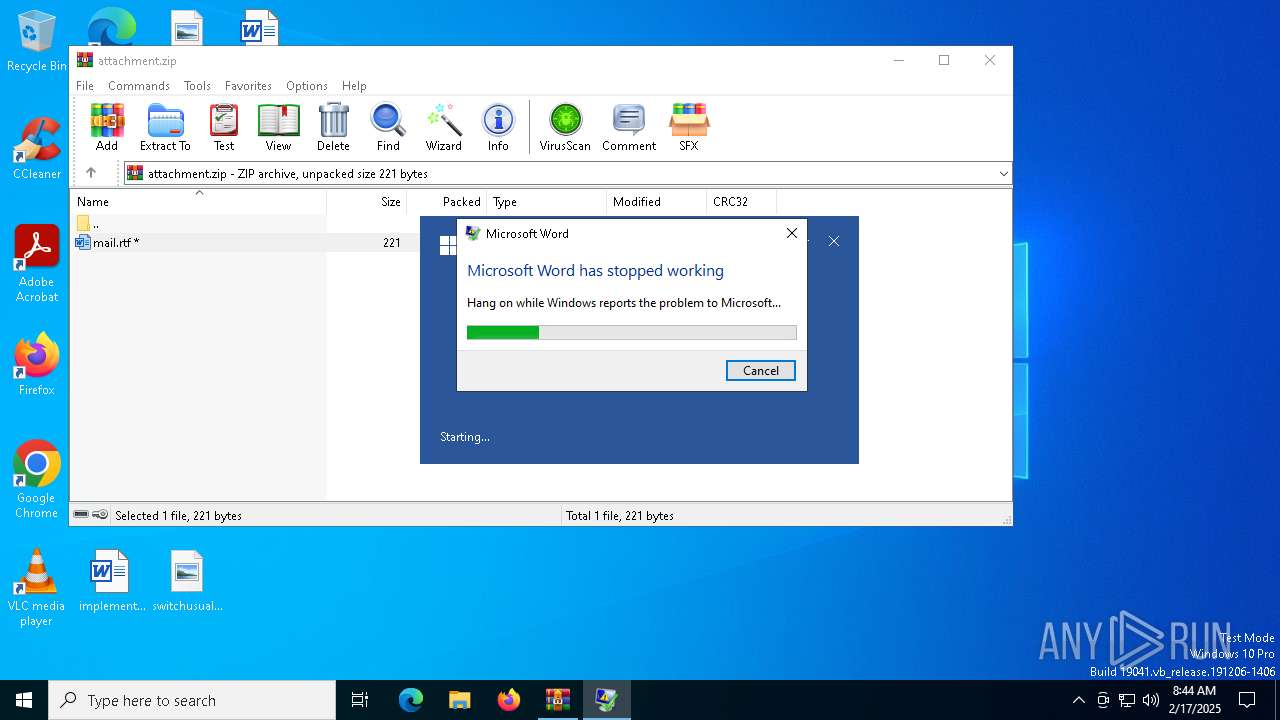
Unusual execution from MS Office
- WINWORD.EXE (PID: 6884)
SUSPICIOUS
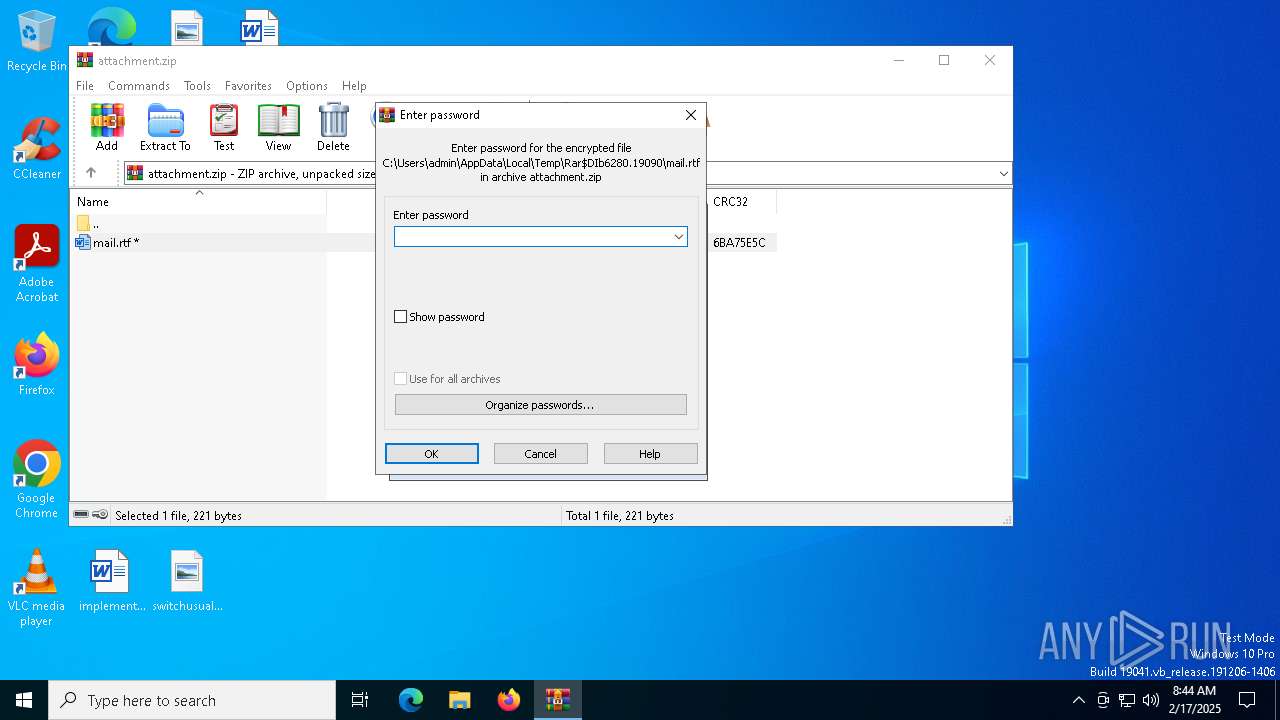
Generic archive extractor
- WinRAR.exe (PID: 6280)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6280)
INFO
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 6280)
- DWWIN.EXE (PID: 5988)
Creates files in the program directory
- DWWIN.EXE (PID: 5988)
Reads the software policy settings
- DWWIN.EXE (PID: 5988)
Checks proxy server information
- DWWIN.EXE (PID: 5988)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:01:20 21:22:02 |
| ZipCRC: | 0x6ba75e5c |
| ZipCompressedSize: | 134 |
| ZipUncompressedSize: | 221 |
| ZipFileName: | mail.rtf |
Total processes
135
Monitored processes
3
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 5988 | C:\WINDOWS\system32\dwwin.exe -x -s 3872 | C:\Windows\System32\DWWIN.EXE | WINWORD.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Error Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6280 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\attachment.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
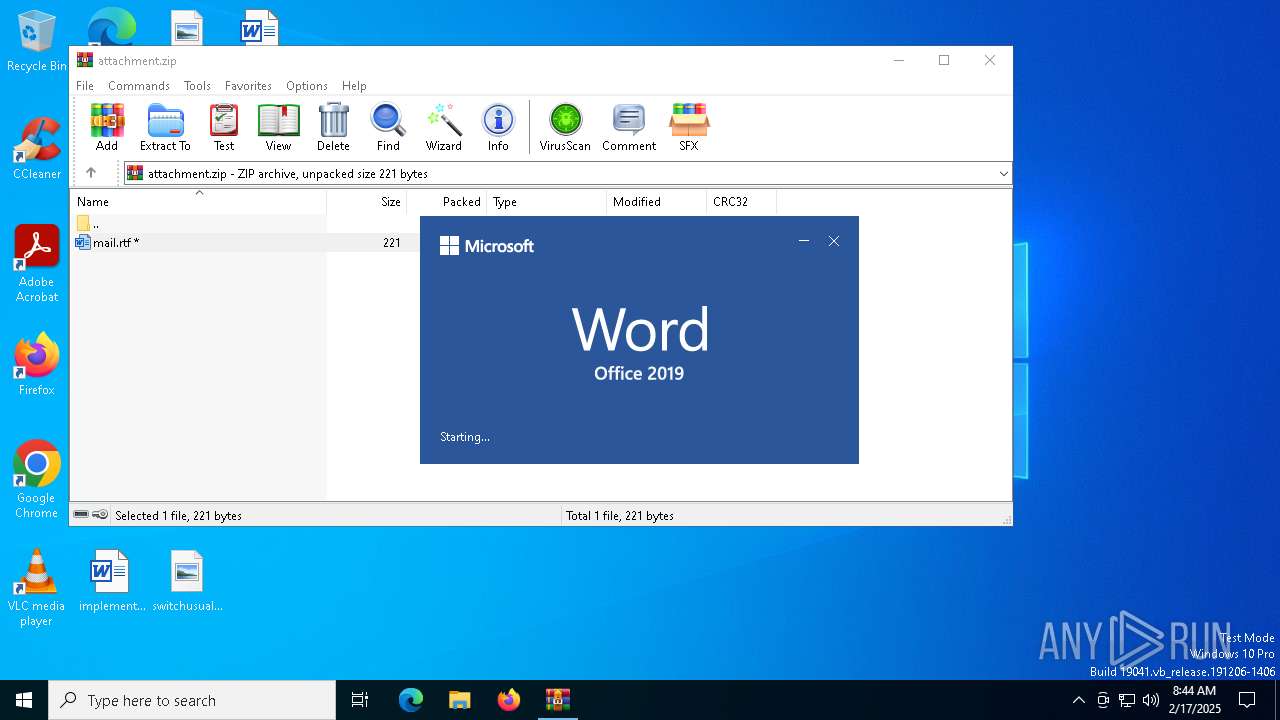
| 6884 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\Rar$DIb6280.19090\mail.rtf" /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 4 Version: 16.0.16026.20146 Modules
| |||||||||||||||
Total events
9 566
Read events
9 344
Write events
216
Delete events
6
Modification events
| (PID) Process: | (6280) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6280) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6280) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6280) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\attachment.zip | |||
| (PID) Process: | (6280) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6280) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6280) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6280) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6280) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (6280) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.rtf\OpenWithProgids |
| Operation: | write | Name: | Word.RTF.8 |
Value: | |||
Executable files
0
Suspicious files
13
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5988 | DWWIN.EXE | C:\ProgramData\Microsoft\Windows\WER\ReportArchive\AppCrash_WINWORD.EXE_32afa92cd6dc5a41387953d68edafb73db78ecf_00000000_707cbbc2-c9a0-4bb1-9ad5-1dc52453628d\Report.wer | — | |
MD5:— | SHA256:— | |||
| 6884 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | binary | |
MD5:53F7AAE068F915A02D2021CACBE8BAB0 | SHA256:26C61183FC8F94A3633048384DE13E67946BBA65692EF7E15BB2C7396624C2D1 | |||
| 6884 | WINWORD.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_363582827213C09529A76F35FB615187 | binary | |
MD5:8FD39C4AC3967909ACDEE363BDBE2130 | SHA256:DC0D556B7C2F7DF79F134CBB34CD5C200A4EF2A19BCE1FBA13BB7FA247A80C01 | |||
| 6280 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb6280.19090\mail.rtf | text | |
MD5:9D68678AEEE52684BBE3C983222B1DA3 | SHA256:93EF57B81021BE174E33B5B48C1AED525D2785C3607AEB540508BB3713690179 | |||
| 6884 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\Rar$DIb6280.19090\~$mail.rtf | binary | |
MD5:FC3035372175115873487EFC3DEB6ADD | SHA256:EB910A90F2A7219C4E81DFF3E6962652A55F2C1A69AFF1B91AD96FDA122F0481 | |||
| 6884 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:FF614A94A794D41DFFE4D07B922D1A28 | SHA256:E809FA2A9C54F07F0A65E6731DB8DADF4352037176F970082662333C8979D9AB | |||
| 6884 | WINWORD.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_363582827213C09529A76F35FB615187 | binary | |
MD5:8B420A982DD958AE60CC6F76F90C7352 | SHA256:F201F143E1344B3358FB411BEB2599ACECD63030AB61F7C364BAACBD13ECD528 | |||
| 6884 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntitiesUpdated.bin | text | |
MD5:1B604F994F5CE45EEE5E38E7FBC2DE71 | SHA256:2C609ECDC3B309EB006602B7F9E0A4F2CEA4F8C76CEB039C3E5B9DD471181800 | |||
| 6884 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntities.bin | text | |
MD5:CC90D669144261B198DEAD45AA266572 | SHA256:89C701EEFF939A44F28921FD85365ECD87041935DCD0FE0BAF04957DA12C9899 | |||
| 5988 | DWWIN.EXE | C:\ProgramData\Microsoft\Windows\WER\Temp\WER8D8E.tmp.xml | xml | |
MD5:43B94D9381E8F6CFAA9401DFC42BF1E6 | SHA256:379581E4E0001B6AB9C446991F86A535AA18AF4813667199B56CB065DAA0A5DB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
38
DNS requests
21
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5988 | DWWIN.EXE | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6480 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5988 | DWWIN.EXE | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3884 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3884 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
3508 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6884 | WINWORD.EXE | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3508 | svchost.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3416 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3508 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 40.126.32.138:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1176 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
1076 | svchost.exe | 2.19.106.8:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
3508 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3508 | svchost.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |