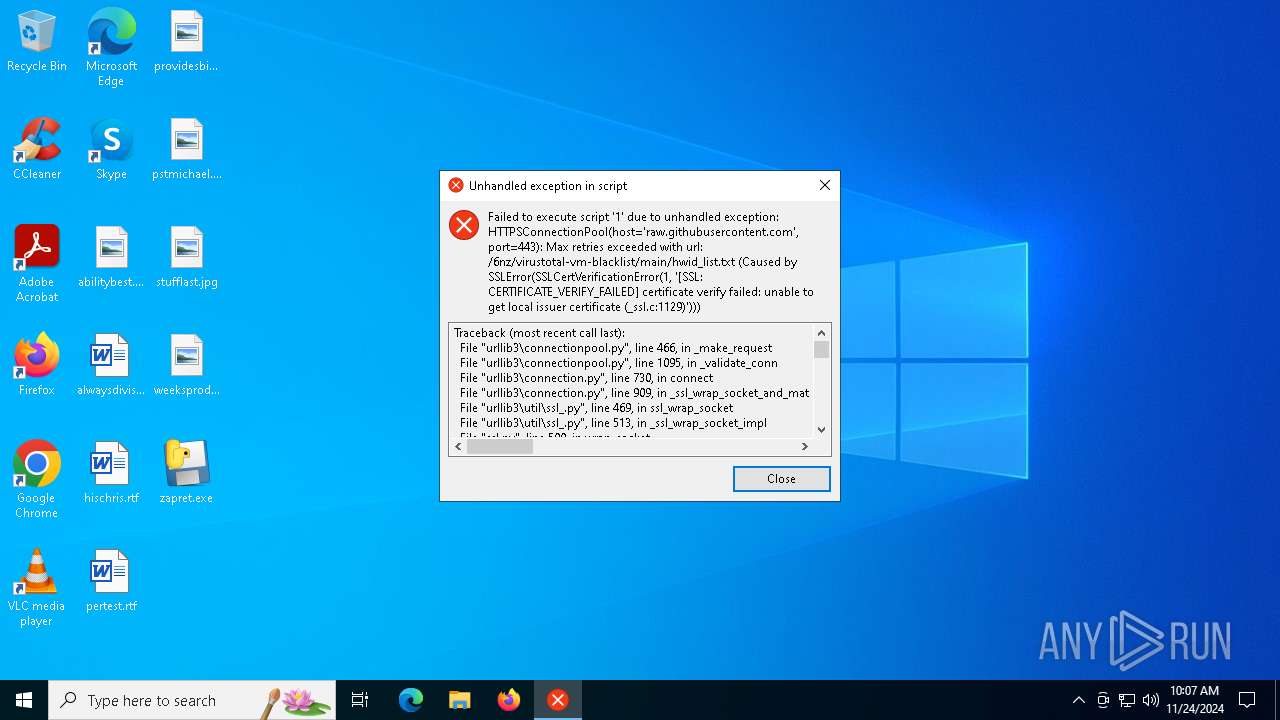
| File name: | zapret.exe |
| Full analysis: | https://app.any.run/tasks/03ca05f8-3ea8-4829-a281-dd71cfb3fe9f |
| Verdict: | Malicious activity |
| Analysis date: | November 24, 2024, 10:07:24 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64 (stripped to external PDB), for MS Windows, 12 sections |
| MD5: | B334E071601498FE209FA9553B37D7AD |
| SHA1: | D41A57E6AC317D9F7A192ED8502B3C138B16D3E6 |
| SHA256: | 889766832B793B6971C21BDE6FEF741285AF8B9ADC16A29DBDDE54AD7C450465 |
| SSDEEP: | 98304:3ah9Ip6KTKNYDDt53l5gbVSjIr7ZMKy65YXbBVlWRplU9aM4zSqNC0JyO3uHmHE4:jztwkWR0P/acEIB3hOWo8W |
MALICIOUS
No malicious indicators.SUSPICIOUS
Process drops legitimate windows executable
- zapret.exe (PID: 5472)
The process drops C-runtime libraries
- zapret.exe (PID: 5472)
Process drops python dynamic module
- zapret.exe (PID: 5472)
Executable content was dropped or overwritten
- zapret.exe (PID: 5472)
Application launched itself
- zapret.exe (PID: 5472)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 3848)
Loads Python modules
- zapret.exe (PID: 2440)
Accesses product unique identifier via WMI (SCRIPT)
- WMIC.exe (PID: 1064)
Uses WMIC.EXE to obtain data on the base board management (motherboard or system board)
- cmd.exe (PID: 1468)
- cmd.exe (PID: 3820)
Starts CMD.EXE for commands execution
- zapret.exe (PID: 2440)
Uses WMIC.EXE to obtain physical disk drive information
- cmd.exe (PID: 3144)
Checks for external IP
- zapret.exe (PID: 2440)
Uses WMIC.EXE to obtain CPU information
- cmd.exe (PID: 5992)
Uses WMIC.EXE to obtain BIOS management information
- cmd.exe (PID: 3172)
Possible usage of Discord/Telegram API has been detected (YARA)
- zapret.exe (PID: 2440)
INFO
Reads the computer name
- zapret.exe (PID: 5472)
- zapret.exe (PID: 2440)
Create files in a temporary directory
- zapret.exe (PID: 5472)
- zapret.exe (PID: 2440)
Checks supported languages
- zapret.exe (PID: 5472)
- zapret.exe (PID: 2440)
Reads the machine GUID from the registry
- zapret.exe (PID: 2440)
Checks proxy server information
- zapret.exe (PID: 2440)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 1064)
- WMIC.exe (PID: 1448)
- WMIC.exe (PID: 5628)
- WMIC.exe (PID: 3140)
- WMIC.exe (PID: 848)
- WMIC.exe (PID: 4024)
PyInstaller has been detected (YARA)
- zapret.exe (PID: 5472)
- zapret.exe (PID: 2440)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
ims-api
(PID) Process(2440) zapret.exe
Discord-Webhook-Tokens (1)1309876516099854346/NlmIv0BUlP0y3DODPLAmrEm_t2a4-__dOn_mRm2KytzcqpDVCOfCFafejFHgbPj1Dc5y
Discord-Info-Links
1309876516099854346/NlmIv0BUlP0y3DODPLAmrEm_t2a4-__dOn_mRm2KytzcqpDVCOfCFafejFHgbPj1Dc5y
Get Webhook Infohttps://discord.com/api/webhooks/1309876516099854346/NlmIv0BUlP0y3DODPLAmrEm_t2a4-__dOn_mRm2KytzcqpDVCOfCFafejFHgbPj1Dc5y
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:11:23 13:54:03+00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, Large address aware, No debug |
| PEType: | PE32+ |
| LinkerVersion: | 2.39 |
| CodeSize: | 96256 |
| InitializedDataSize: | 208384 |
| UninitializedDataSize: | 61440 |
| EntryPoint: | 0x10f6 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows GUI |
Total processes
140
Monitored processes
20
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 848 | wmic cpu get serialnumber | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1064 | wmic csproduct get uuid | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1448 | wmic baseboard get manufacturer | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1468 | C:\WINDOWS\system32\cmd.exe /c "wmic baseboard get manufacturer" | C:\Windows\System32\cmd.exe | — | zapret.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2440 | "C:\Users\admin\Desktop\zapret.exe" | C:\Users\admin\Desktop\zapret.exe | zapret.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
ims-api(PID) Process(2440) zapret.exe Discord-Webhook-Tokens (1)1309876516099854346/NlmIv0BUlP0y3DODPLAmrEm_t2a4-__dOn_mRm2KytzcqpDVCOfCFafejFHgbPj1Dc5y Discord-Info-Links 1309876516099854346/NlmIv0BUlP0y3DODPLAmrEm_t2a4-__dOn_mRm2KytzcqpDVCOfCFafejFHgbPj1Dc5y Get Webhook Infohttps://discord.com/api/webhooks/1309876516099854346/NlmIv0BUlP0y3DODPLAmrEm_t2a4-__dOn_mRm2KytzcqpDVCOfCFafejFHgbPj1Dc5y | |||||||||||||||
| 2796 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3140 | wmic diskdrive get serialnumber | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3144 | C:\WINDOWS\system32\cmd.exe /c "wmic diskdrive get serialnumber" | C:\Windows\System32\cmd.exe | — | zapret.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3172 | C:\WINDOWS\system32\cmd.exe /c "wmic bios get serialnumber" | C:\Windows\System32\cmd.exe | — | zapret.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3224 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
1 631
Read events
1 631
Write events
0
Delete events
0
Modification events
Executable files
33
Suspicious files
2
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5472 | zapret.exe | C:\Users\admin\AppData\Local\Temp\_MEI54722\_asyncio.pyd | executable | |
MD5:CCC47CD433F0ED282A5AA14C8513EFCA | SHA256:4D6AA25D76A9739C6B6DF1D36448BD8CAF9B758FDF77311B8D57600C813B0C74 | |||
| 5472 | zapret.exe | C:\Users\admin\AppData\Local\Temp\_MEI54722\_lzma.pyd | executable | |
MD5:CE4A35FC25D50497E8BE0E75FF8D61B3 | SHA256:E352C77F7810EA83617ED096626AC9C3D628726DEF47551F90741D201C1F3B3D | |||
| 5472 | zapret.exe | C:\Users\admin\AppData\Local\Temp\_MEI54722\_queue.pyd | executable | |
MD5:1B1A7CB8FD95C0D9741462DE11ABD43D | SHA256:3C907316271B15935FF400B65D24F229FEB980A5BE9CB4AD9F79F210FF0B884C | |||
| 5472 | zapret.exe | C:\Users\admin\AppData\Local\Temp\_MEI54722\_decimal.pyd | executable | |
MD5:2DABDD7B03EE2D8328FAD17BC9CF9970 | SHA256:5F8E850820050CABE5AA36838BA9ABD62A4F5D5D2AA1B337CBB795077E1D48BF | |||
| 5472 | zapret.exe | C:\Users\admin\AppData\Local\Temp\_MEI54722\_socket.pyd | executable | |
MD5:439B4D756CDE64FBA441E640DF56DD60 | SHA256:ACB377FD6967B2CE819601C7D6A102D30AF570EAEE9E312E383F34AECD5DF142 | |||
| 5472 | zapret.exe | C:\Users\admin\AppData\Local\Temp\_MEI54722\_win32sysloader.pyd | executable | |
MD5:8BC46C6802867A8D753D4481B09A2BED | SHA256:A2B7367DCC4E91A504D3077465C2C310C91241587568D901F11C3F5DFB5F37CC | |||
| 5472 | zapret.exe | C:\Users\admin\AppData\Local\Temp\_MEI54722\_ctypes.pyd | executable | |
MD5:A1B81CE092C5A2C9AFD13B5CAE872441 | SHA256:EB5EBEB25888FF124ABD0DB3E08577B84538E62610107FE4E008D7C188A78210 | |||
| 5472 | zapret.exe | C:\Users\admin\AppData\Local\Temp\_MEI54722\VCRUNTIME140.dll | executable | |
MD5:A87575E7CF8967E481241F13940EE4F7 | SHA256:DED5ADAA94341E6C62AEA03845762591666381DCA30EB7C17261DD154121B83E | |||
| 5472 | zapret.exe | C:\Users\admin\AppData\Local\Temp\_MEI54722\_ssl.pyd | executable | |
MD5:5E2EE0A0277FFE2BD854ABB898310D43 | SHA256:75AE15B70EAA1950CF259FED95ADE499D7C6DFEFFFDF4C3292C46BD24DA25902 | |||
| 5472 | zapret.exe | C:\Users\admin\AppData\Local\Temp\_MEI54722\_uuid.pyd | executable | |
MD5:C6CED76F58EB9BCC88DFEA9B4A11D974 | SHA256:E4CD5A2B7BE54E858592F451B84280397AA8D6546906BC6834170A24A3857FAE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
22
DNS requests
8
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
648 | RUXIMICS.exe | GET | 200 | 2.16.164.106:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
244 | svchost.exe | GET | 200 | 2.16.164.106:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
648 | RUXIMICS.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
244 | svchost.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.106:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
244 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
648 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2440 | zapret.exe | 104.26.13.205:443 | api.ipify.org | CLOUDFLARENET | US | shared |
244 | svchost.exe | 2.16.164.106:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.164.106:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
648 | RUXIMICS.exe | 2.16.164.106:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
244 | svchost.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
api.ipify.org |
| shared |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
raw.githubusercontent.com |
| shared |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
2440 | zapret.exe | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |