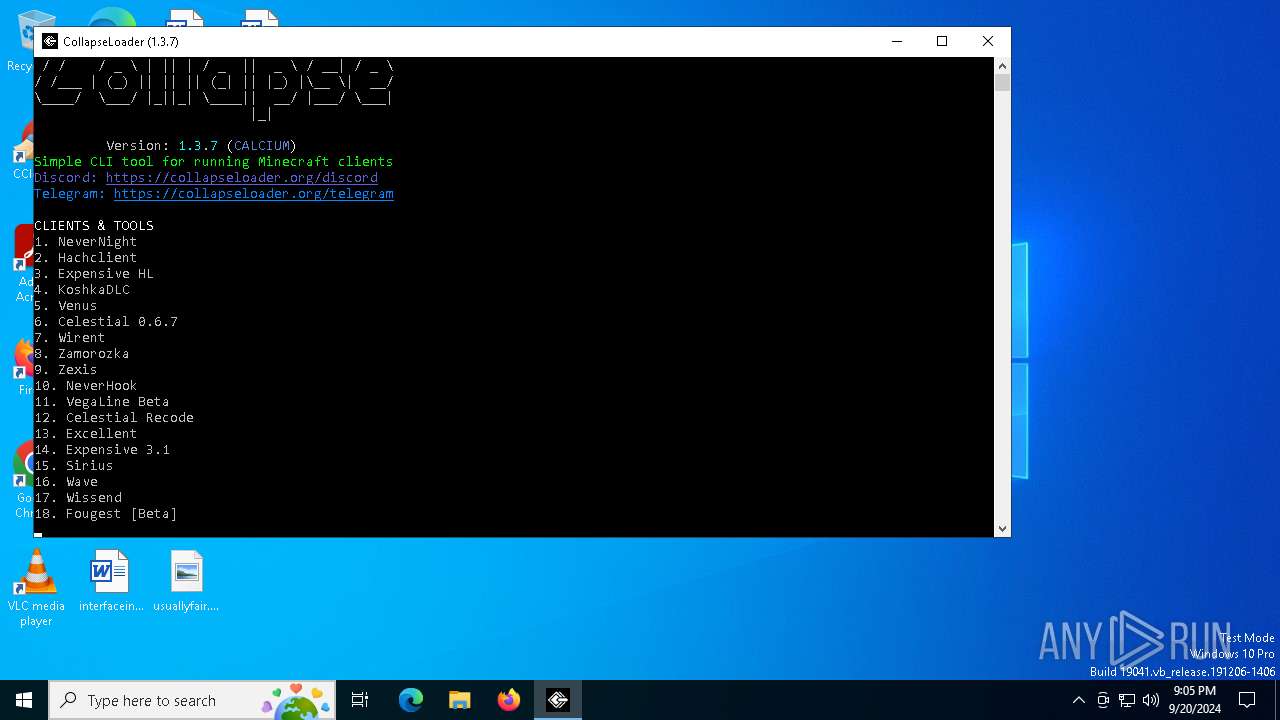
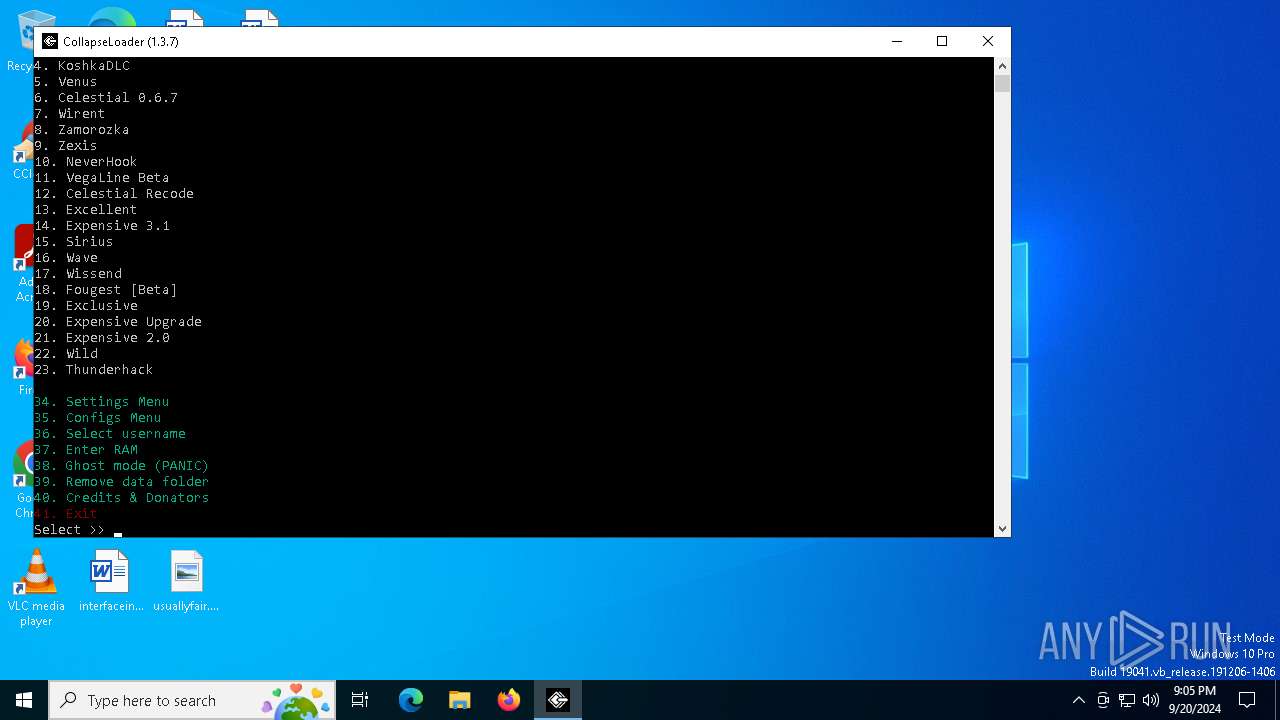
| File name: | CollapseLoader_ffa95d4.exe |
| Full analysis: | https://app.any.run/tasks/d3f163db-7b22-44dc-85b0-6cd36daed8cb |
| Verdict: | Malicious activity |
| Analysis date: | September 20, 2024, 21:05:37 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (console) x86-64, for MS Windows |
| MD5: | 389BDF6F2C11BC0B816B4626D9D5E5CE |
| SHA1: | 3781B17F7DC9C5AFECFF44C4E6D73285C735D353 |
| SHA256: | 888614CB343A3F8B2D5A5EB48D11D363C54F1D610E8A95F47FC7140F8DC94EAB |
| SSDEEP: | 98304:7VIyDdtpjNT/qrzehL7f9hsDmNxl+a52tlMEaXkx/g0I2w5jnywT006GHgBuHhiM:54ITyYbH7NddCPqVQufcEvwh6U |
MALICIOUS
No malicious indicators.SUSPICIOUS
Process drops python dynamic module
- CollapseLoader_ffa95d4.exe (PID: 7152)
Executable content was dropped or overwritten
- CollapseLoader_ffa95d4.exe (PID: 7152)
Process drops legitimate windows executable
- CollapseLoader_ffa95d4.exe (PID: 7152)
The process drops C-runtime libraries
- CollapseLoader_ffa95d4.exe (PID: 7152)
Application launched itself
- CollapseLoader_ffa95d4.exe (PID: 7152)
INFO
Checks supported languages
- CollapseLoader_ffa95d4.exe (PID: 7152)
- CollapseLoader_ffa95d4.exe (PID: 6300)
Reads the computer name
- CollapseLoader_ffa95d4.exe (PID: 7152)
Create files in a temporary directory
- CollapseLoader_ffa95d4.exe (PID: 7152)
PyInstaller has been detected (YARA)
- CollapseLoader_ffa95d4.exe (PID: 7152)
- CollapseLoader_ffa95d4.exe (PID: 6300)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:09:20 18:52:16+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.4 |
| CodeSize: | 176640 |
| InitializedDataSize: | 94720 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xc320 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
114
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 6300 | "C:\Users\admin\AppData\Local\Temp\CollapseLoader_ffa95d4.exe" | C:\Users\admin\AppData\Local\Temp\CollapseLoader_ffa95d4.exe | CollapseLoader_ffa95d4.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 6560 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | CollapseLoader_ffa95d4.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7152 | "C:\Users\admin\AppData\Local\Temp\CollapseLoader_ffa95d4.exe" | C:\Users\admin\AppData\Local\Temp\CollapseLoader_ffa95d4.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
Total events
3 379
Read events
3 379
Write events
0
Delete events
0
Modification events
Executable files
72
Suspicious files
2
Text files
142
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7152 | CollapseLoader_ffa95d4.exe | C:\Users\admin\AppData\Local\Temp\_MEI71522\_wmi.pyd | executable | |
MD5:827615EEE937880862E2F26548B91E83 | SHA256:73B7EE3156EF63D6EB7DF9900EF3D200A276DF61A70D08BD96F5906C39A3AC32 | |||
| 7152 | CollapseLoader_ffa95d4.exe | C:\Users\admin\AppData\Local\Temp\_MEI71522\_lzma.pyd | executable | |
MD5:9E94FAC072A14CA9ED3F20292169E5B2 | SHA256:A46189C5BD0302029847FED934F481835CB8D06470EA3D6B97ADA7D325218A9F | |||
| 7152 | CollapseLoader_ffa95d4.exe | C:\Users\admin\AppData\Local\Temp\_MEI71522\VCRUNTIME140_1.dll | executable | |
MD5:F8DFA78045620CF8A732E67D1B1EB53D | SHA256:A113F192195F245F17389E6ECBED8005990BCB2476DDAD33F7C4C6C86327AFE5 | |||
| 7152 | CollapseLoader_ffa95d4.exe | C:\Users\admin\AppData\Local\Temp\_MEI71522\_bz2.pyd | executable | |
MD5:30F396F8411274F15AC85B14B7B3CD3D | SHA256:CB15D6CC7268D3A0BD17D9D9CEC330A7C1768B1C911553045C73BC6920DE987F | |||
| 7152 | CollapseLoader_ffa95d4.exe | C:\Users\admin\AppData\Local\Temp\_MEI71522\aiohttp\_http_writer.cp312-win_amd64.pyd | executable | |
MD5:E37DE249124DAF6FD5164B7CFB8B7FE1 | SHA256:8A13B94B85D917D25CB8A6EA5D99CC82A39E9DD1618CB71E6A9219AADB76C5C3 | |||
| 7152 | CollapseLoader_ffa95d4.exe | C:\Users\admin\AppData\Local\Temp\_MEI71522\_ctypes.pyd | executable | |
MD5:5377AB365C86BBCDD998580A79BE28B4 | SHA256:6C5F31BEF3FDBFF31BEAC0B1A477BE880DDA61346D859CF34CA93B9291594D93 | |||
| 7152 | CollapseLoader_ffa95d4.exe | C:\Users\admin\AppData\Local\Temp\_MEI71522\VCRUNTIME140.dll | executable | |
MD5:BE8DBE2DC77EBE7F88F910C61AEC691A | SHA256:4D292623516F65C80482081E62D5DADB759DC16E851DE5DB24C3CBB57B87DB83 | |||
| 7152 | CollapseLoader_ffa95d4.exe | C:\Users\admin\AppData\Local\Temp\_MEI71522\aiohttp\_http_parser.cp312-win_amd64.pyd | executable | |
MD5:8E4CDED9429EC06C8F681EA0AFA3BB93 | SHA256:CF70C494EC7087114A84412B8BD4E9EE7F60A2716DF8D73252BF56B24A72FD9E | |||
| 7152 | CollapseLoader_ffa95d4.exe | C:\Users\admin\AppData\Local\Temp\_MEI71522\_hashlib.pyd | executable | |
MD5:A25BC2B21B555293554D7F611EAA75EA | SHA256:43ACECDC00DD5F9A19B48FF251106C63C975C732B9A2A7B91714642F76BE074D | |||
| 7152 | CollapseLoader_ffa95d4.exe | C:\Users\admin\AppData\Local\Temp\_MEI71522\_uuid.pyd | executable | |
MD5:D8C6D60EA44694015BA6123FF75BD38D | SHA256:8AE23BFA84CE64C3240C61BEDB06172BFD76BE2AD30788D4499CB24047FCE09F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
19
DNS requests
12
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1452 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1452 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6300 | CollapseLoader_ffa95d4.exe | 188.114.97.3:443 | cdn.collapseloader.org | CLOUDFLARENET | NL | unknown |
6300 | CollapseLoader_ffa95d4.exe | 188.114.96.3:443 | cdn.collapseloader.org | CLOUDFLARENET | NL | unknown |
6300 | CollapseLoader_ffa95d4.exe | 140.82.121.5:443 | api.github.com | GITHUB | US | whitelisted |
1452 | SIHClient.exe | 4.245.163.56:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1452 | SIHClient.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
cdn.collapseloader.org |
| unknown |
web.collapseloader.org |
| unknown |
api.github.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |