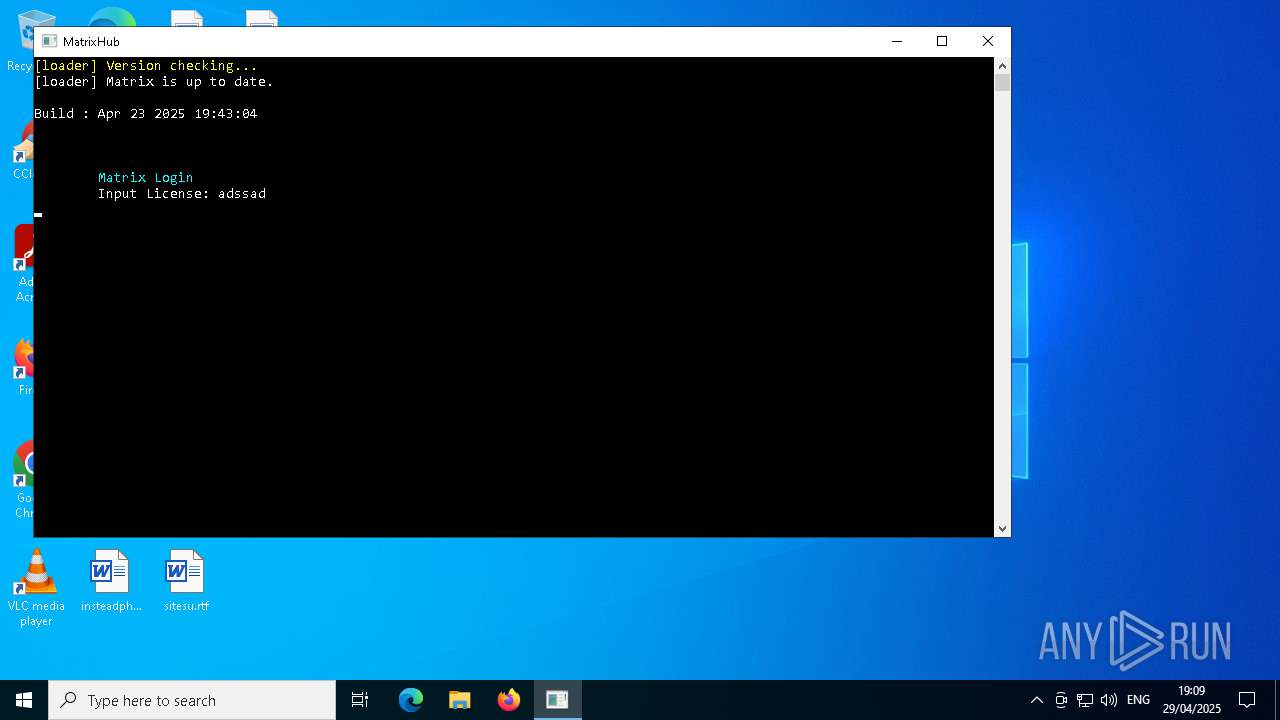
| File name: | newuimatrix.exe |
| Full analysis: | https://app.any.run/tasks/39a0289b-754a-44cc-9ba2-5dbf392416ca |
| Verdict: | Malicious activity |
| Analysis date: | April 29, 2025, 18:08:06 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 6 sections |
| MD5: | 49B79A318C7CF4BCF6C3F44D0ED260F9 |
| SHA1: | 790E8BA03760DE49F818A716CD47531242D3DEA6 |
| SHA256: | 887B773172839A3149DF2E67E8F6746A1BEAEF05C98718F525089F82D4EB15FF |
| SSDEEP: | 98304:QnYnYRTdRJVlgKI/lYKf6j1FJ7uVYXnFqWu7X1lTWA3/G5m33PNh8hsT+dh+lyQH:O |
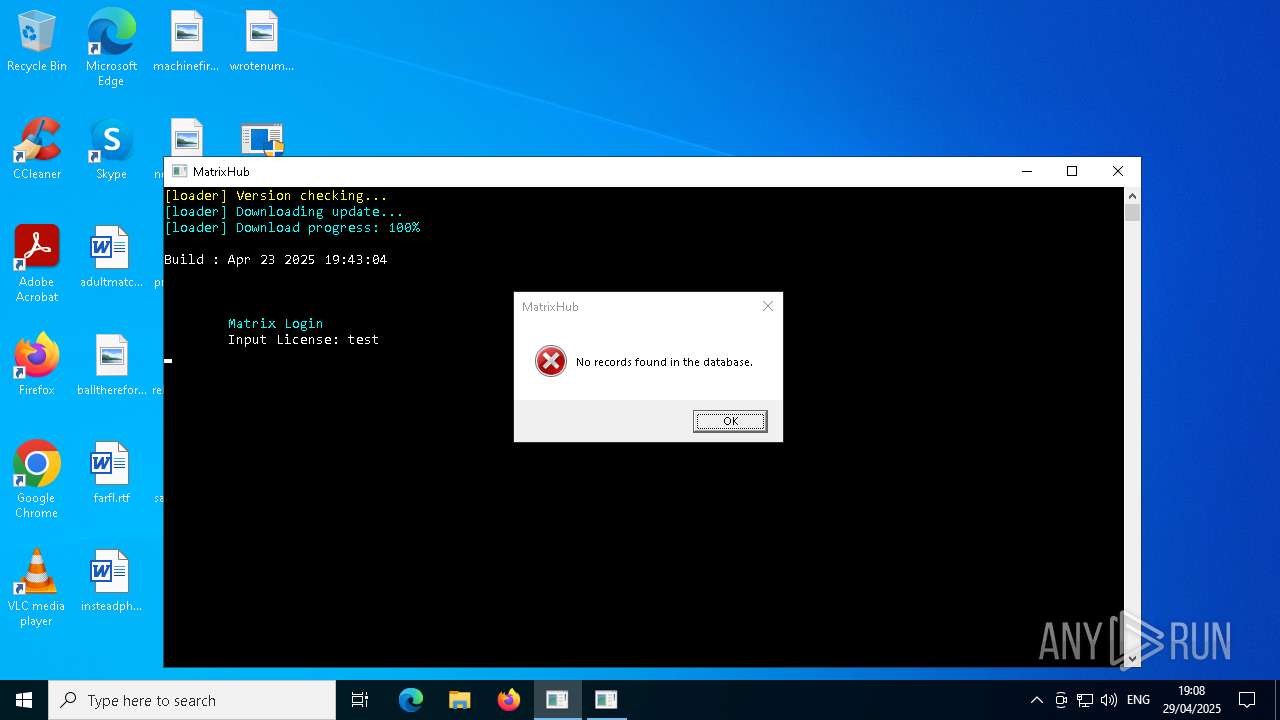
MALICIOUS
Application was injected by another process
- explorer.exe (PID: 5492)
Runs injected code in another process
- newuimatrix.exe (PID: 516)
- newuimatrix.exe (PID: 3896)
SUSPICIOUS
Reads security settings of Internet Explorer
- newuimatrix.exe (PID: 516)
Modifies hosts file to alter network resolution
- newuimatrix.exe (PID: 516)
- newuimatrix.exe (PID: 3896)
Executes application which crashes
- newuimatrix.exe (PID: 516)
- newuimatrix.exe (PID: 3896)
INFO
Reads security settings of Internet Explorer
- explorer.exe (PID: 5492)
Reads the computer name
- newuimatrix.exe (PID: 516)
- newuimatrix.exe (PID: 3896)
Checks proxy server information
- newuimatrix.exe (PID: 516)
- slui.exe (PID: 4560)
Checks supported languages
- newuimatrix.exe (PID: 516)
- newuimatrix.exe (PID: 3896)
Reads the machine GUID from the registry
- newuimatrix.exe (PID: 516)
Reads the software policy settings
- newuimatrix.exe (PID: 516)
- slui.exe (PID: 4560)
Creates files or folders in the user directory
- newuimatrix.exe (PID: 516)
- WerFault.exe (PID: 4880)
- WerFault.exe (PID: 1168)
Create files in a temporary directory
- WerFault.exe (PID: 4880)
- WerFault.exe (PID: 1168)
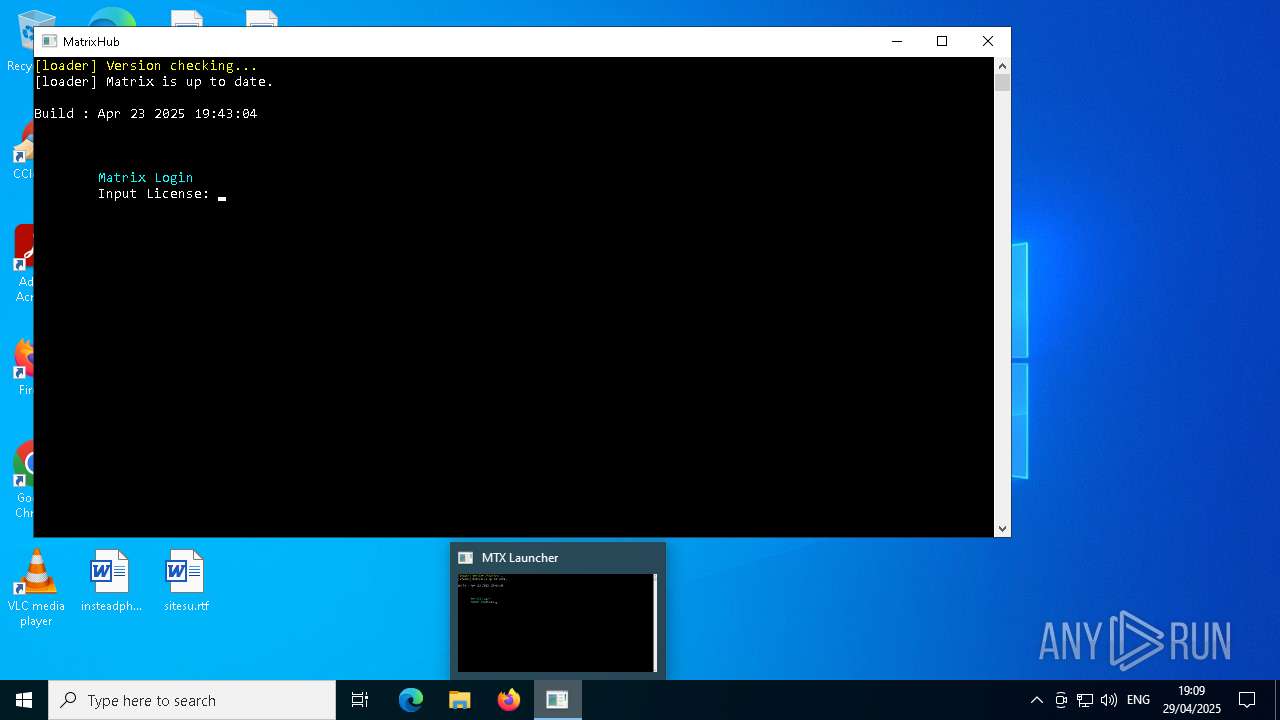
Manual execution by a user
- newuimatrix.exe (PID: 5324)
- newuimatrix.exe (PID: 3896)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:03:29 22:06:45+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.41 |
| CodeSize: | 39936 |
| InitializedDataSize: | 4216832 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x9988 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
136
Monitored processes
10
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 516 | "C:\Users\admin\Desktop\newuimatrix.exe" | C:\Users\admin\Desktop\newuimatrix.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 3221225477 Modules
| |||||||||||||||
| 1168 | C:\WINDOWS\system32\WerFault.exe -u -p 3896 -s 656 | C:\Windows\System32\WerFault.exe | — | newuimatrix.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1180 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | newuimatrix.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3896 | "C:\Users\admin\Desktop\newuimatrix.exe" | C:\Users\admin\Desktop\newuimatrix.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 3221225477 Modules
| |||||||||||||||
| 4560 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4880 | C:\WINDOWS\system32\WerFault.exe -u -p 516 -s 1088 | C:\Windows\System32\WerFault.exe | — | newuimatrix.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5324 | "C:\Users\admin\Desktop\newuimatrix.exe" | C:\Users\admin\Desktop\newuimatrix.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 5392 | "C:\Users\admin\Desktop\newuimatrix.exe" | C:\Users\admin\Desktop\newuimatrix.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 5492 | C:\WINDOWS\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6028 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | newuimatrix.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
11 412
Read events
11 380
Write events
22
Delete events
10
Modification events
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Security and Maintenance\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 23004100430042006C006F0062000000000000000000000001000000FFFFFFFFFFFF0000 | |||
| (PID) Process: | (516) newuimatrix.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (516) newuimatrix.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (516) newuimatrix.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | IconLayouts |
Value: 00000000000000000000000000000000030001000100010015000000000000002C000000000000003A003A007B00360034003500460046003000340030002D0035003000380031002D0031003000310042002D0039004600300038002D003000300041004100300030003200460039003500340045007D003E002000200000001000000000000000430043006C00650061006E00650072002E006C006E006B003E0020007C0000001500000000000000410064006F006200650020004100630072006F006200610074002E006C006E006B003E0020007C0000000F00000000000000460069007200650066006F0078002E006C006E006B003E0020007C000000150000000000000047006F006F0067006C00650020004300680072006F006D0065002E006C006E006B003E0020007C000000180000000000000056004C00430020006D006500640069006100200070006C0061007900650072002E006C006E006B003E0020007C00000016000000000000004D006900630072006F0073006F0066007400200045006400670065002E006C006E006B003E0020007C0000000D0000000000000053006B007900700065002E006C006E006B003E0020007C00000012000000000000006100640075006C0074006D0061007400630068002E007200740066003E002000200000001500000000000000620061006C006C007400680065007200650066006F00720065002E006A00700067003E002000200000000D0000000000000066006100720066006C002E007200740066003E00200020000000140000000000000069006E0073007400650061006400700068006F006E0065002E007200740066003E0020002000000014000000000000006D0061006300680069006E006500660069007200730074002E006A00700067003E0020002000000010000000000000006E0065007800740073006100760065002E006A00700067003E002000200000000E0000000000000070006D0062006F006F006B002E006A00700067003E002000200000001500000000000000720065006C0065006100730065007300610066006500740079002E0070006E0067003E00200020000000150000000000000073006100690064006F007000650072006100740069006E0067002E0070006E0067003E002000200000000E000000000000007300690074006500730075002E007200740066003E002000200000001300000000000000770072006F00740065006E0075006D006200650072002E006A00700067003E0020002000000013000000000000006E0065007700750069006D00610074007200690078002E006500780065003E002000200000000F00000000000000760065007200730069006F006E002E006400610074003E00200020000000010000000000000002000100000000000000000001000000000000000200010000000000000000001100000006000000010000001500000000000000000000000000000000000000803F0000004008000000803F0000404009000000803F000080400A000000803F0000A0400B0000000040000000000C00000000400000803F0D0000000040000000400E0000000040000040400F0000000040000080401000000000400000A040110000004040000000001200000000000000803F0100000000000000004002000000000000004040030000000000000080400400000000000000A04005000000803F0000000006000000803F0000803F0700000040400000803F130000004040000000401400 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | IconNameVersion |
Value: 1 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\5\ApplicationViewManagement\W32:00000000000A02E2 |
| Operation: | write | Name: | VirtualDesktop |
Value: 1000000030304456BFA0DB55E4278845B426357D5B5F97B3 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\5\ApplicationViewManagement\W32:000000000008014C |
| Operation: | write | Name: | VirtualDesktop |
Value: 1000000030304456BFA0DB55E4278845B426357D5B5F97B3 | |||
| (PID) Process: | (4880) WerFault.exe | Key: | \REGISTRY\A\{2014fee6-9d6e-08e0-5de4-d0a65edfbf3e}\Root\InventoryApplicationFile |
| Operation: | write | Name: | WritePermissionsCheck |
Value: 1 | |||
| (PID) Process: | (4880) WerFault.exe | Key: | \REGISTRY\A\{2014fee6-9d6e-08e0-5de4-d0a65edfbf3e}\Root\InventoryApplicationFile\PermissionsCheckTestKey |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
0
Suspicious files
5
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 516 | newuimatrix.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\attachments-00000000732474BF[1] | — | |
MD5:— | SHA256:— | |||
| 516 | newuimatrix.exe | C:\Users\admin\Desktop\version.dat | — | |
MD5:— | SHA256:— | |||
| 4880 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_bad_module_info_1eba89dbf420a62f833a4ce282376bda3656d4_85207d7d_9bd92b3d-0ea0-44be-91c0-2ba649542232\Report.wer | — | |
MD5:— | SHA256:— | |||
| 1168 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_bad_module_info_1eba89dbf420a62f833a4ce282376bda3656d4_85207d7d_d09861c2-21ea-44a3-ad31-178412891370\Report.wer | — | |
MD5:— | SHA256:— | |||
| 4880 | WerFault.exe | C:\Users\admin\AppData\Local\Temp\WERF8AB.tmp.WERDataCollectionStatus.txt | binary | |
MD5:6C2ECA55FFFFD0C95E15698F4887880C | SHA256:C79A60BD36C0EB01A01F41A71BB8A50A491A4517444979D24EEA7ABBE13E3C5B | |||
| 1168 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERCD23.tmp.WERInternalMetadata.xml | binary | |
MD5:8230D387920B41D41E253C4A044EF56A | SHA256:12A5AFC25C7E36FC3A96AD189BD02B4D51B76FB9FB7E8A2D17121FA041E2F01A | |||
| 4880 | WerFault.exe | C:\Windows\appcompat\Programs\Amcache.hve | binary | |
MD5:401E45A7636A1AC0C1BBC63927F33B1B | SHA256:9E67B4F428CA29FBF3372EDEED8C182A3CC964873D2CC8AA2C1EA9F8C81B9736 | |||
| 4880 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER89B.tmp.xml | xml | |
MD5:7013A0AE142AE631044588AA65174416 | SHA256:25CA9D034A1D5680DA8D96827C18EF76C7DCF83BEC9A60F313A99D2DEE300815 | |||
| 1168 | WerFault.exe | C:\Users\admin\AppData\Local\Temp\WERBD62.tmp.WERDataCollectionStatus.txt | binary | |
MD5:B14BA8C15977553D32AB79B4CA3CD1C3 | SHA256:9E2D11A196646492CCD46ECAA4D2BA7F37CE3C2C5399D5CA38E69F03BB06FD6D | |||
| 1168 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERCD43.tmp.xml | xml | |
MD5:7CC2CEC8C9DA2FB611CE28A457459D72 | SHA256:22602A01EAC539C984481EE5DC79F83E6A49818F210E8B4BD986287EFAB8653B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
25
TCP/UDP connections
44
DNS requests
15
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 302 | 140.82.121.4:443 | https://github.com/npdotdev/endpoint-file/raw/refs/heads/main/attachments-00000000732474BF | unknown | — | — | unknown |
— | — | GET | 304 | 20.109.210.53:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
— | — | GET | 200 | 20.109.210.53:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
— | — | GET | 200 | 20.3.187.198:443 | https://fe3cr.delivery.mp.microsoft.com/clientwebservice/ping | unknown | — | — | unknown |
6392 | SIHClient.exe | GET | 200 | 23.216.77.8:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6392 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
6392 | SIHClient.exe | GET | 200 | 23.216.77.8:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
6392 | SIHClient.exe | GET | 200 | 23.216.77.8:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
6392 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6392 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
516 | newuimatrix.exe | 109.123.234.188:9999 | — | — | — | unknown |
516 | newuimatrix.exe | 140.82.121.4:443 | github.com | GITHUB | US | whitelisted |
516 | newuimatrix.exe | 185.199.110.133:443 | raw.githubusercontent.com | FASTLY | US | whitelisted |
6392 | SIHClient.exe | 20.109.210.53:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6392 | SIHClient.exe | 23.216.77.8:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6392 | SIHClient.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
github.com |
| whitelisted |
raw.githubusercontent.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Possibly Unwanted Program Detected | ET ADWARE_PUP User-Agent (FileDownloader) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
— | — | Possibly Unwanted Program Detected | ET ADWARE_PUP User-Agent (FileDownloader) |