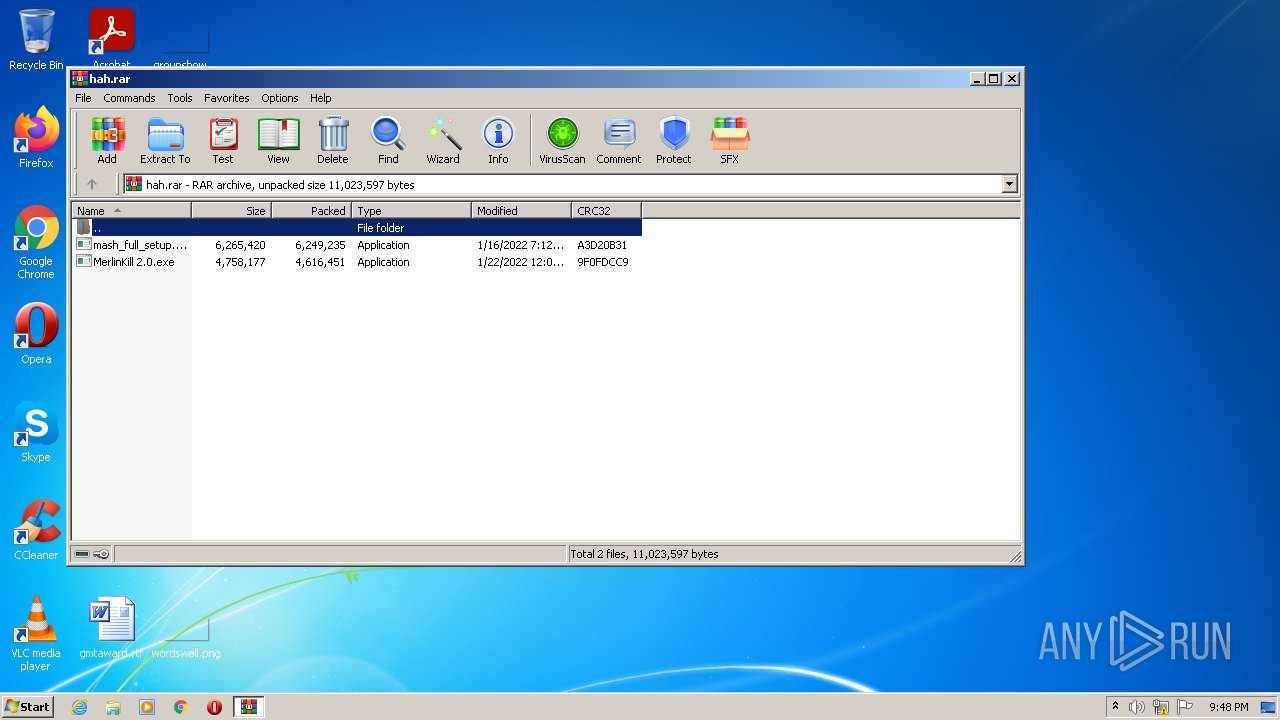
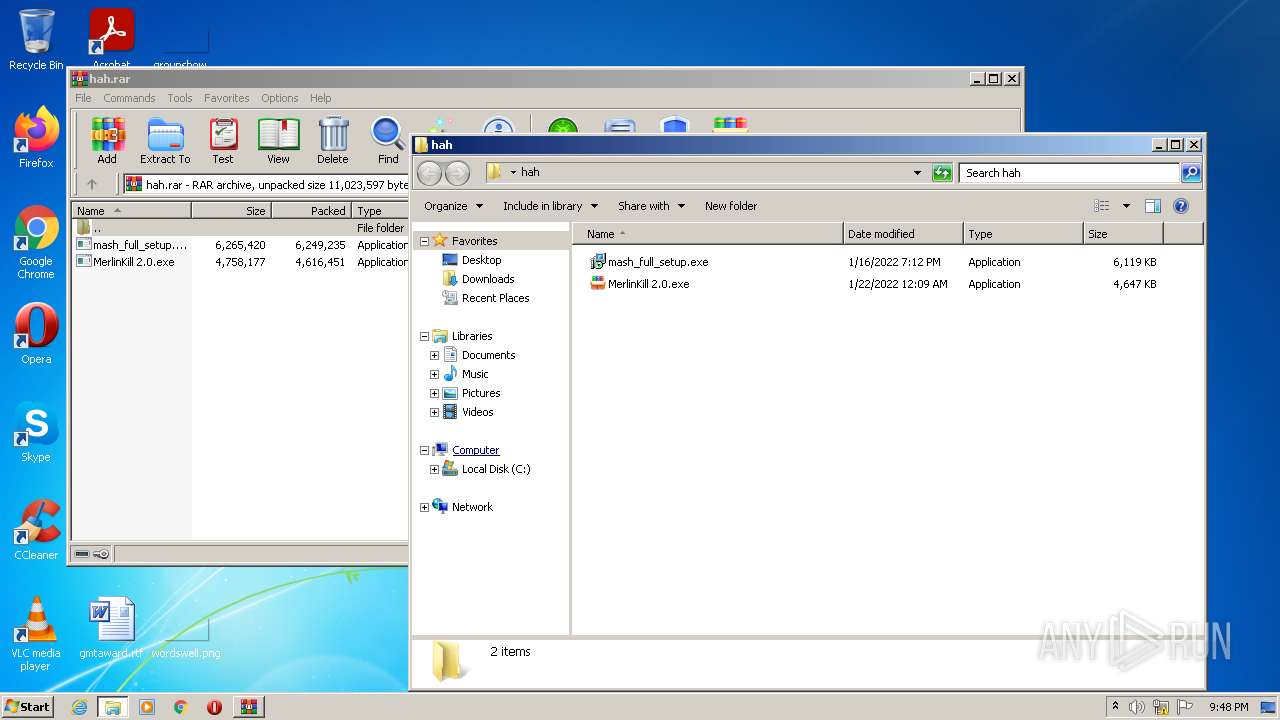
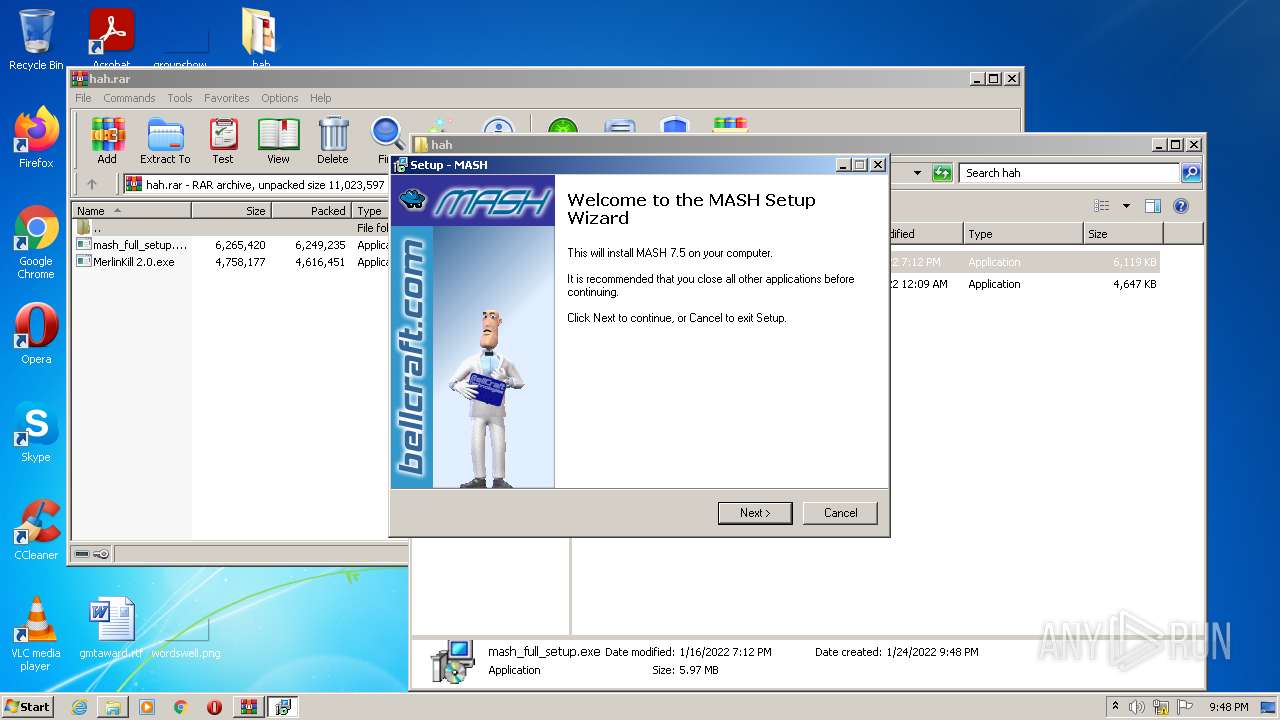
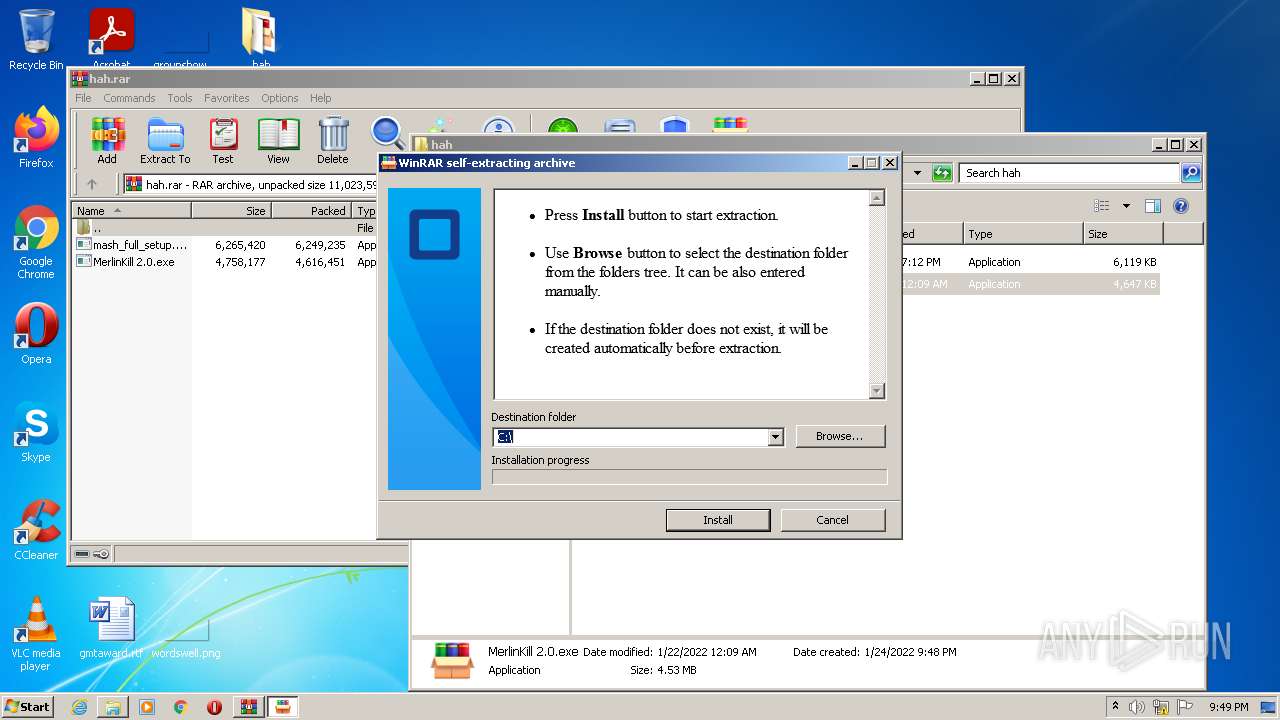
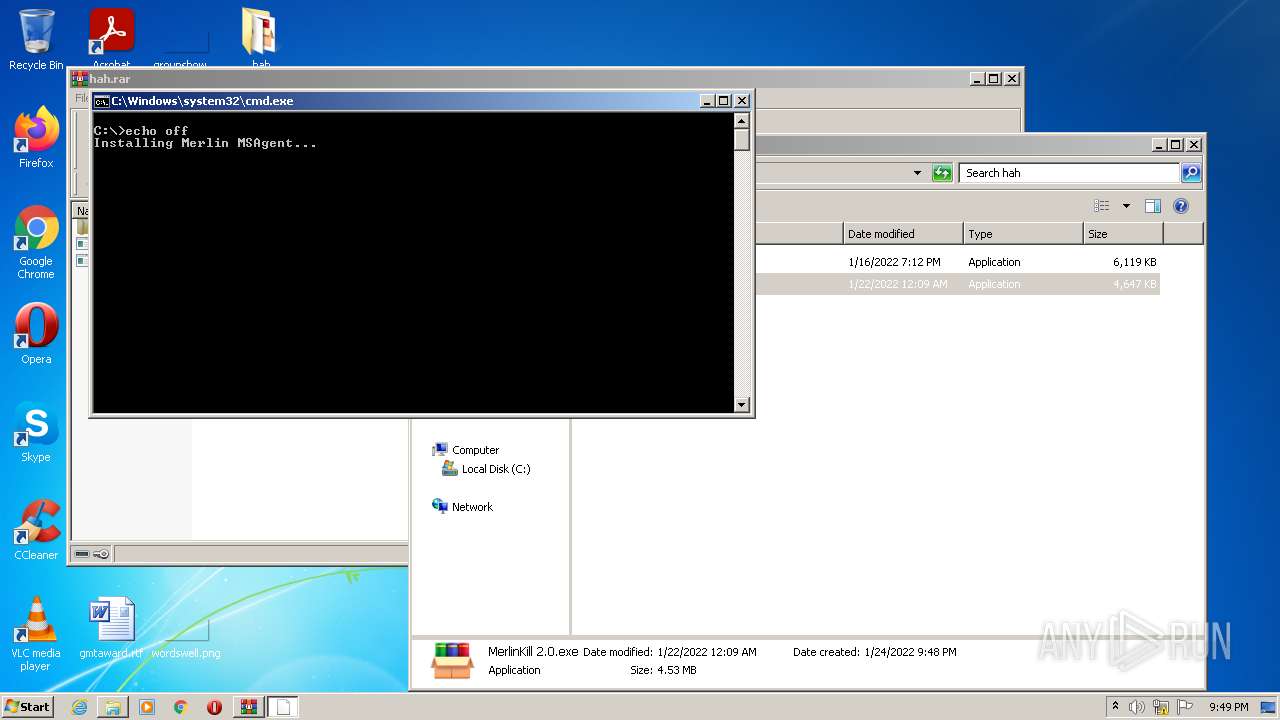
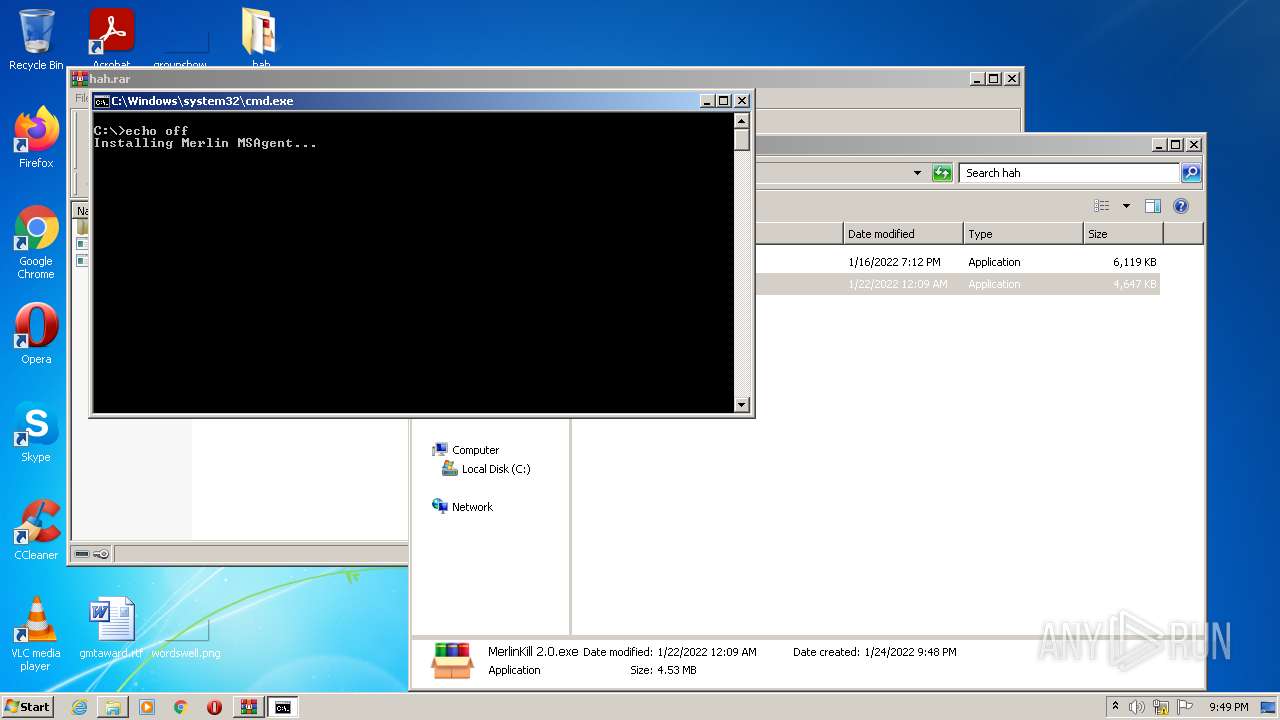
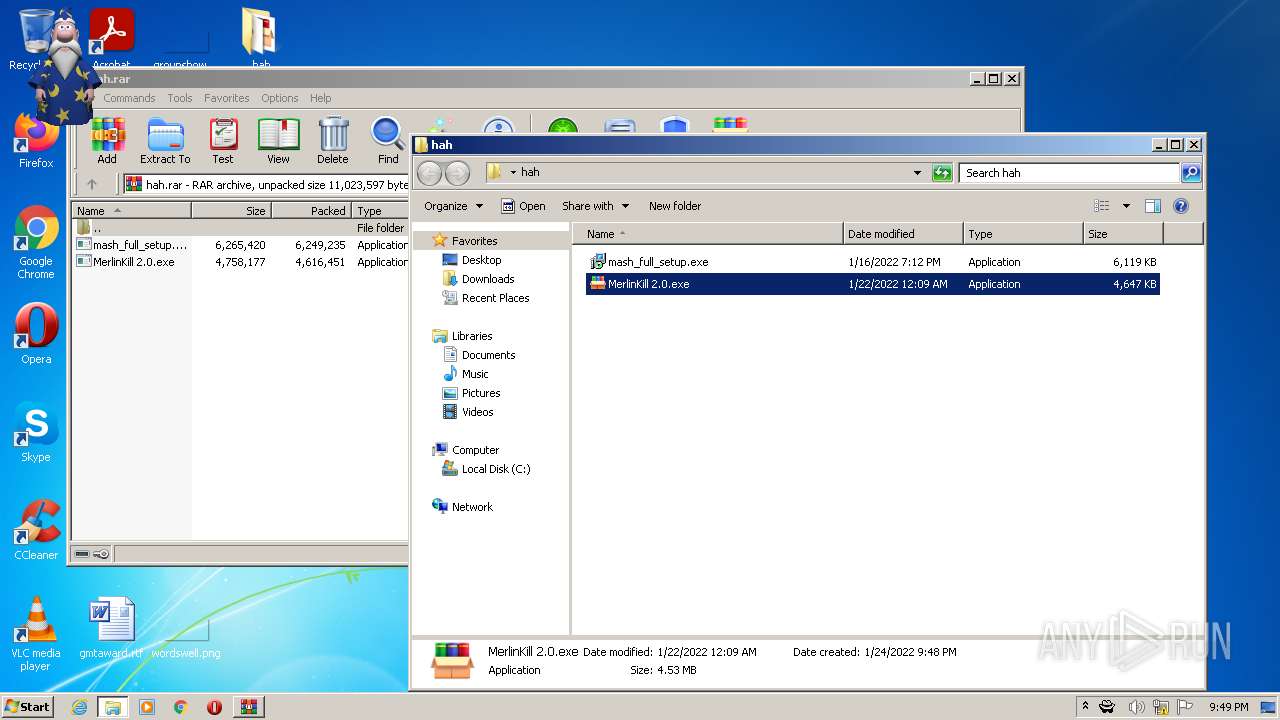
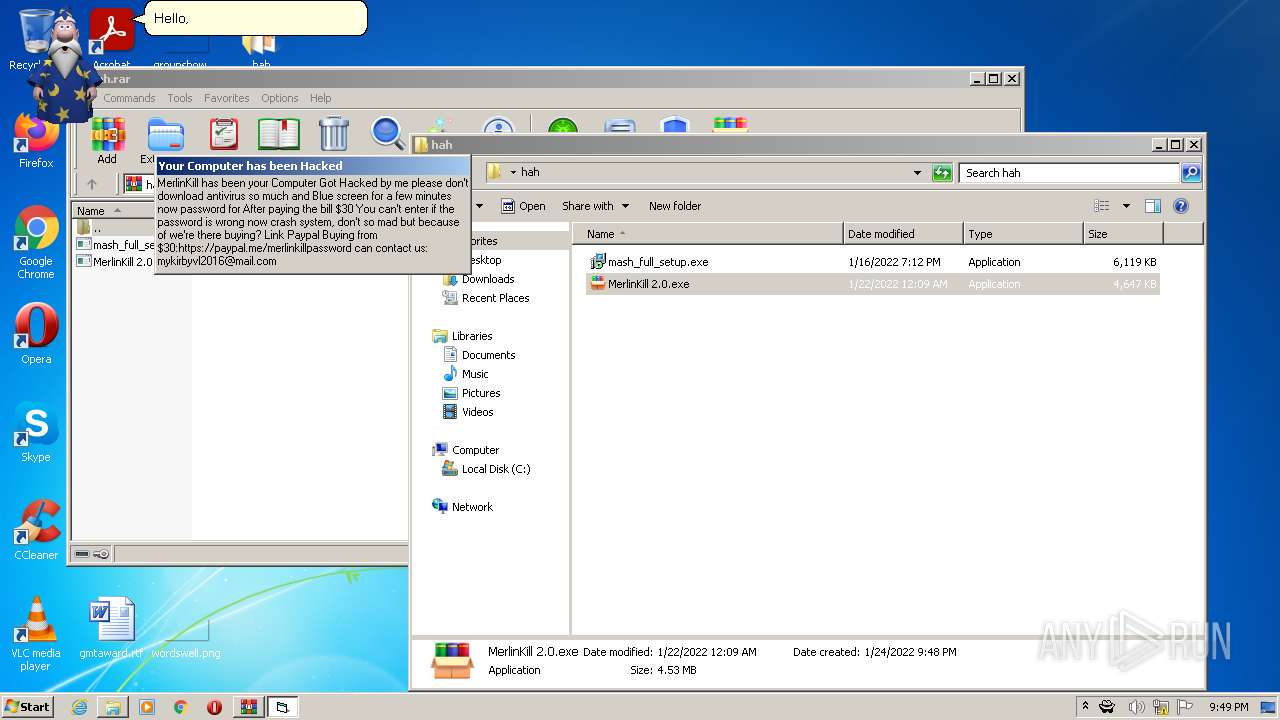
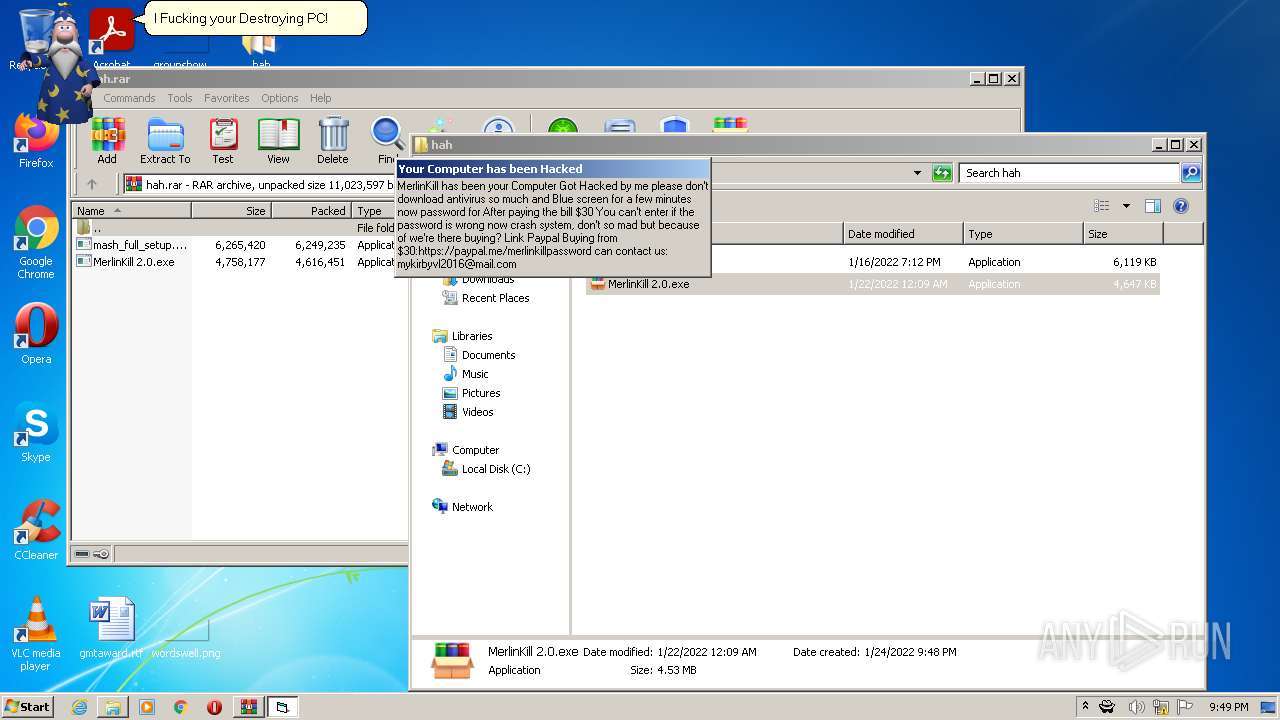
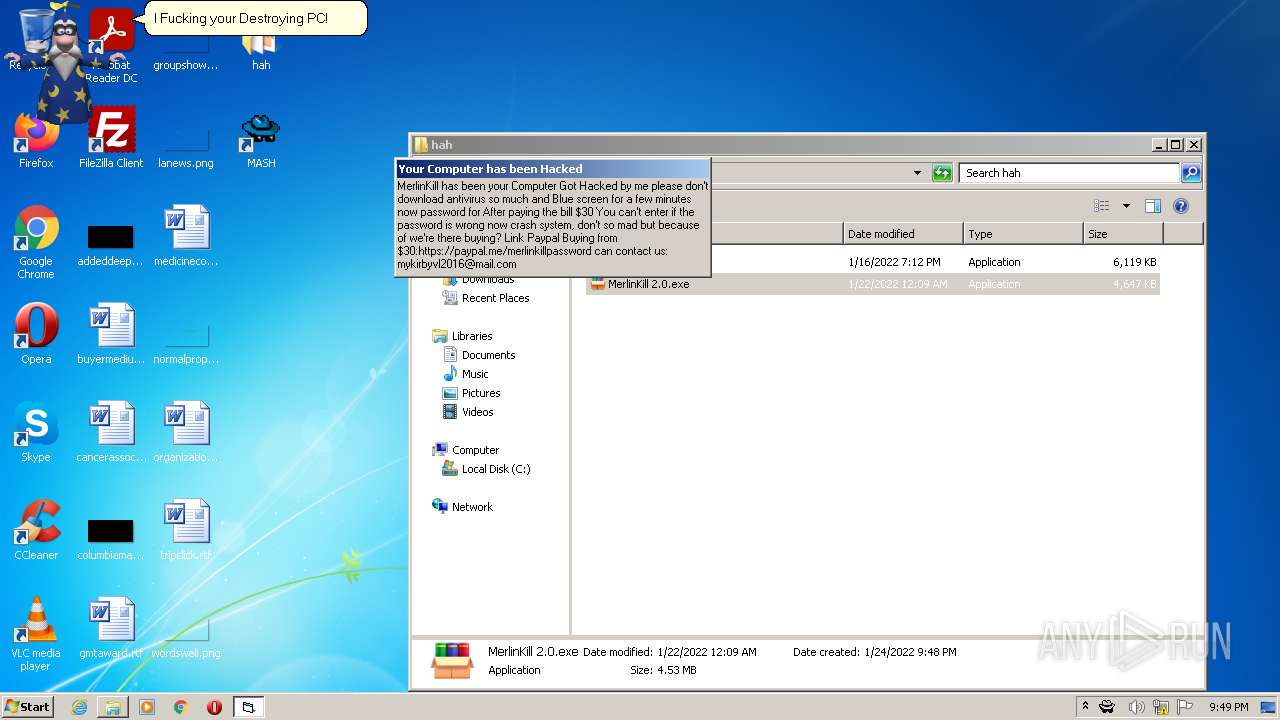
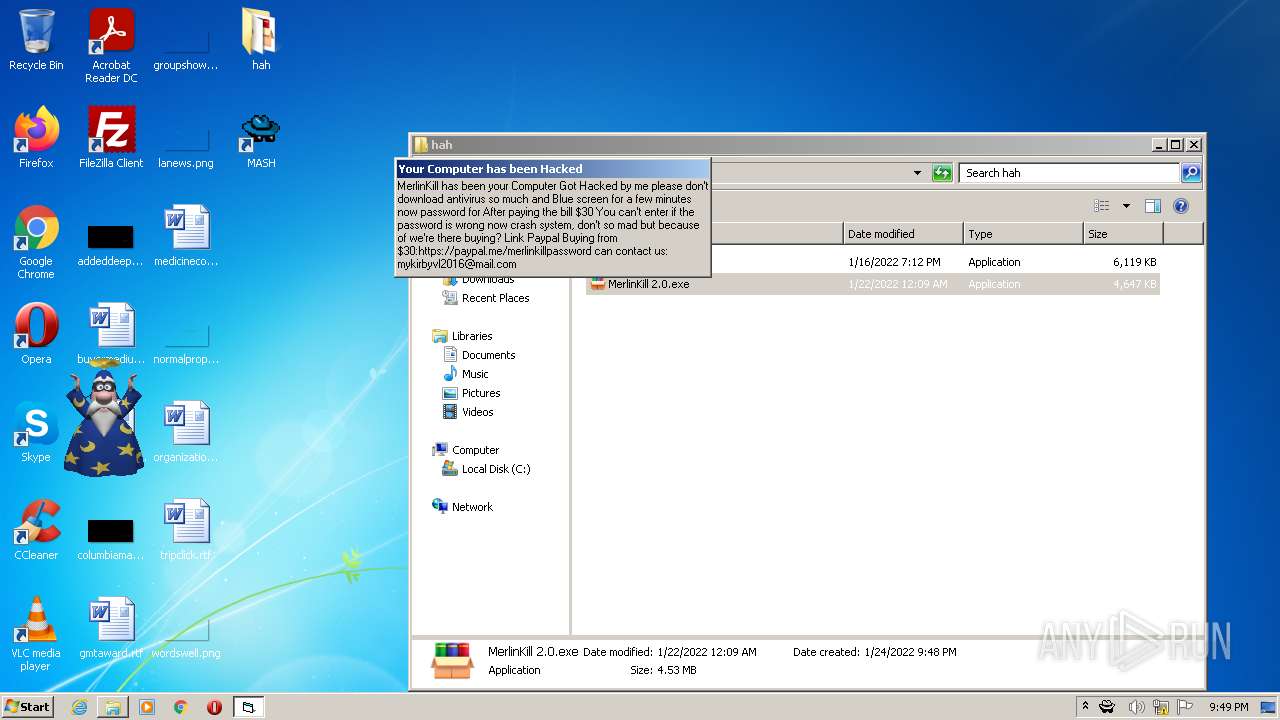
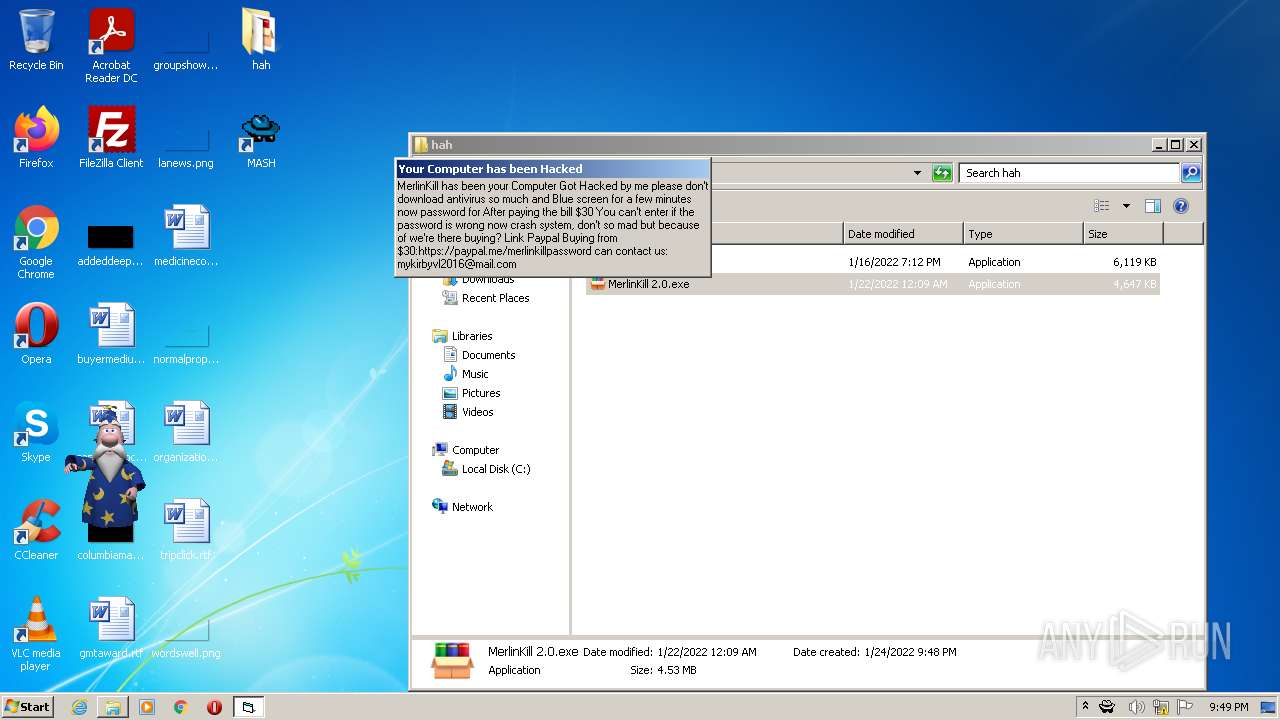
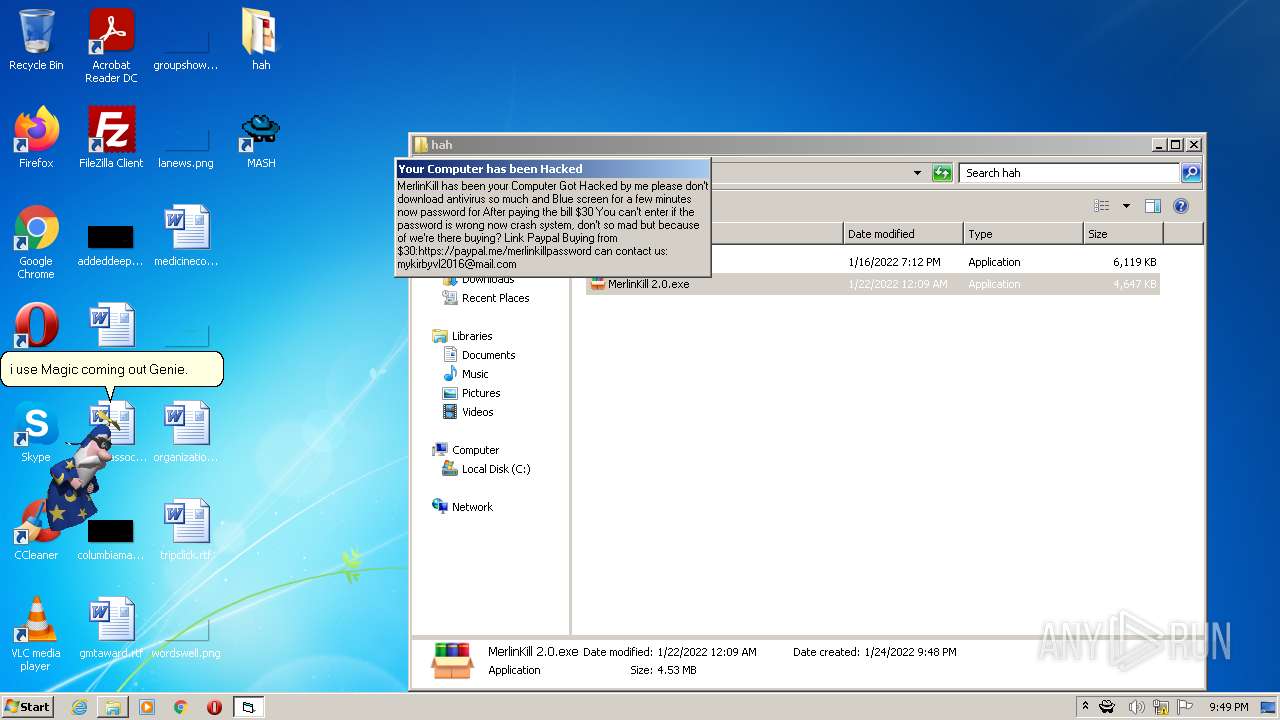
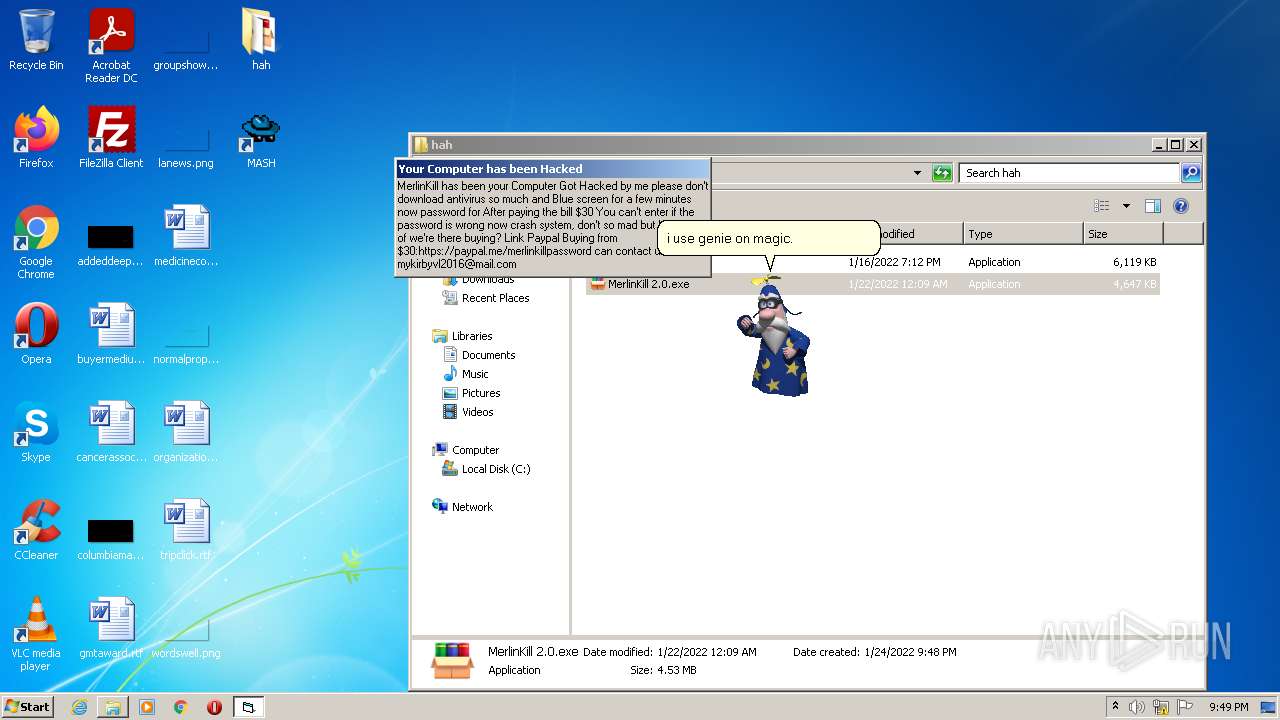
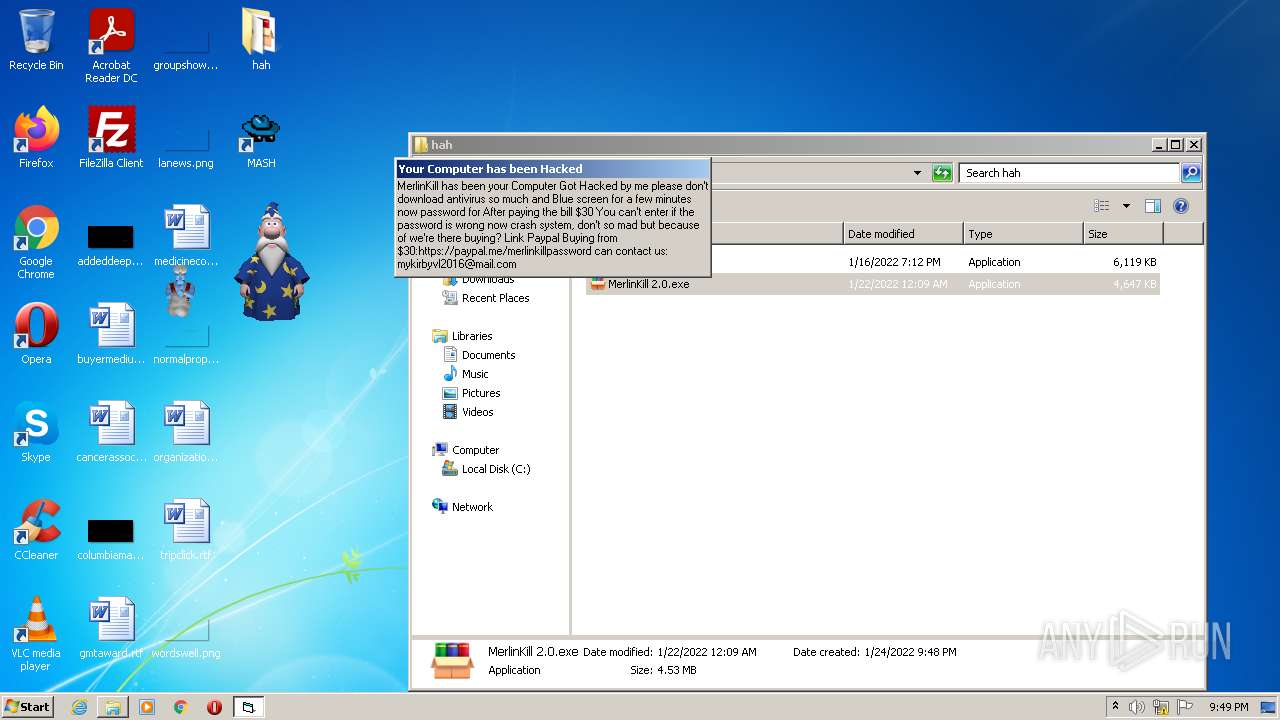
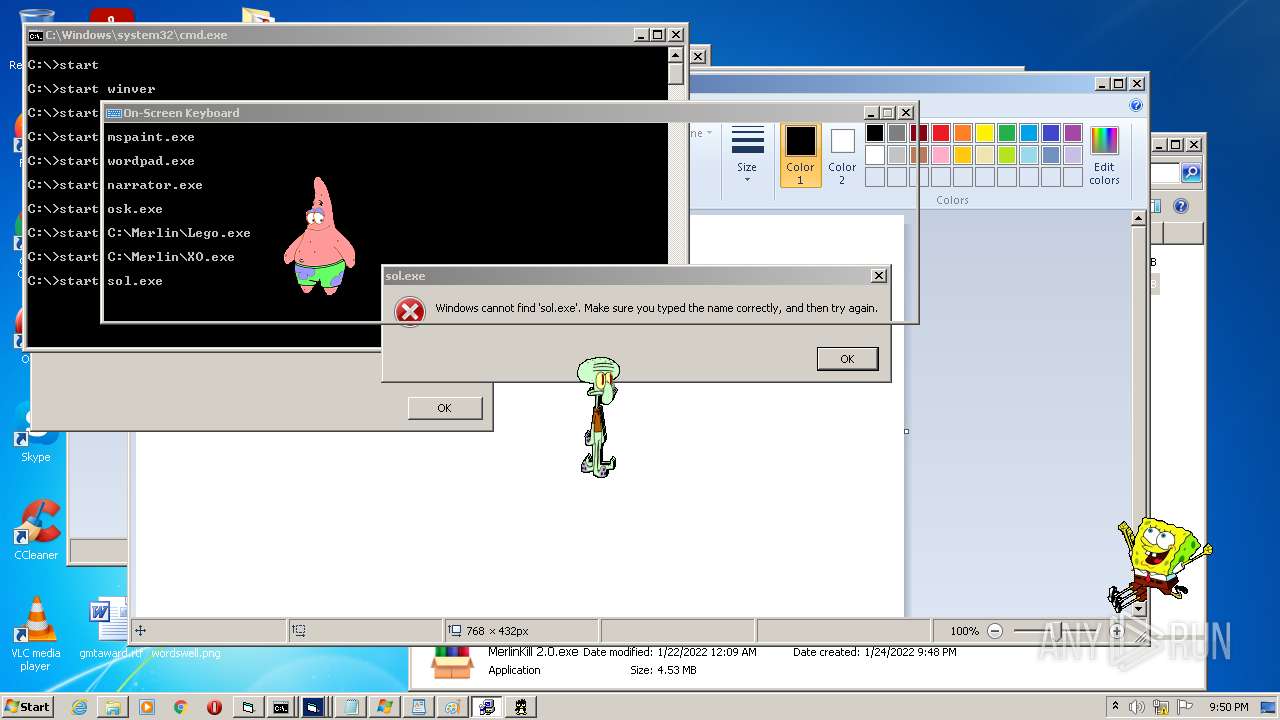
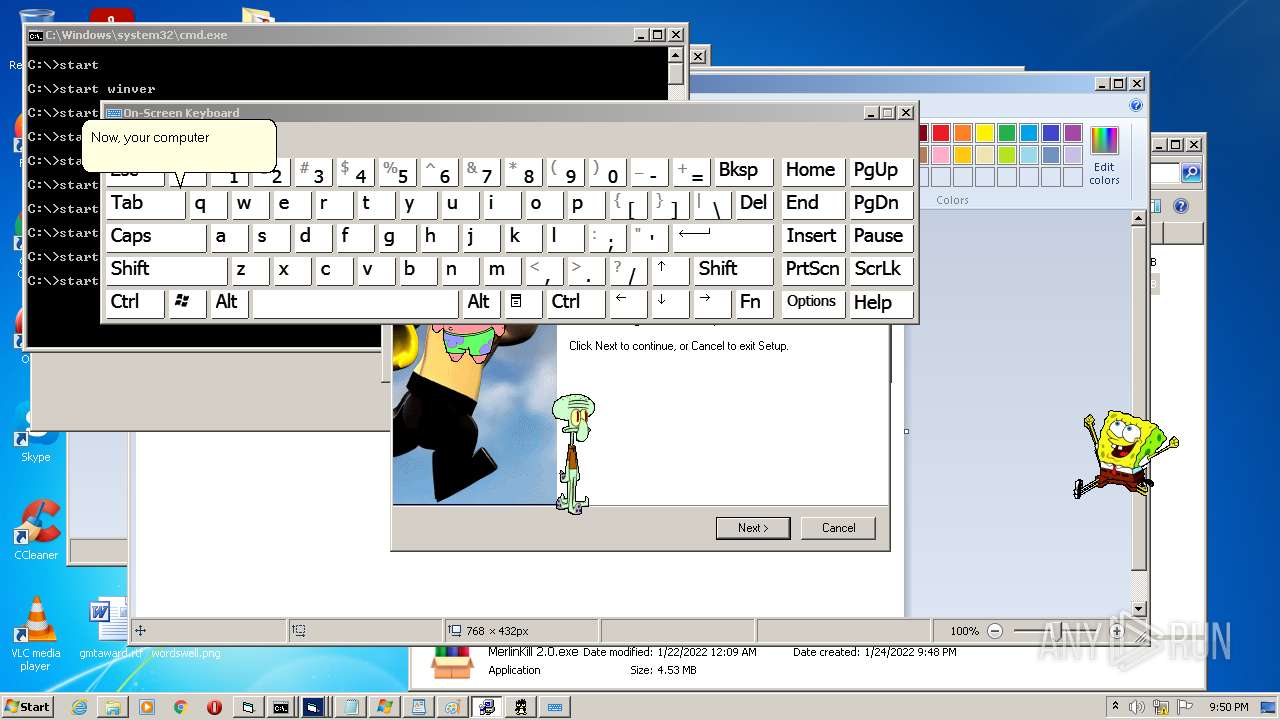
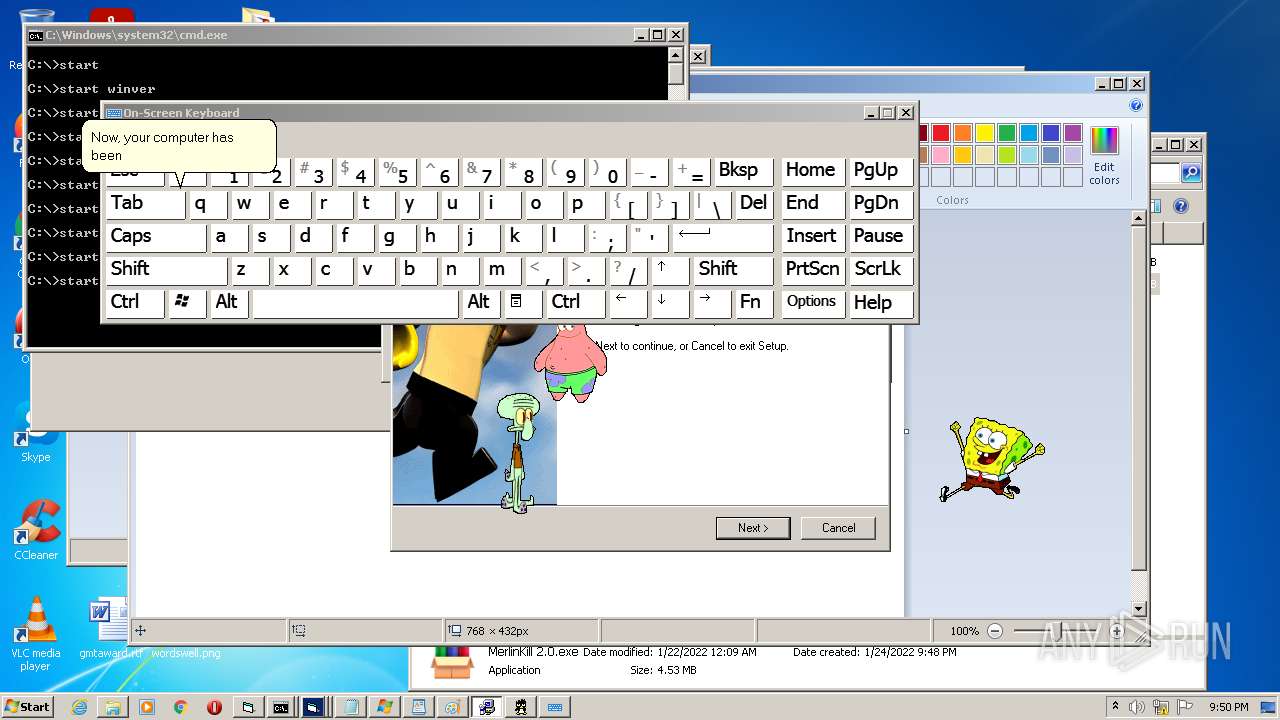
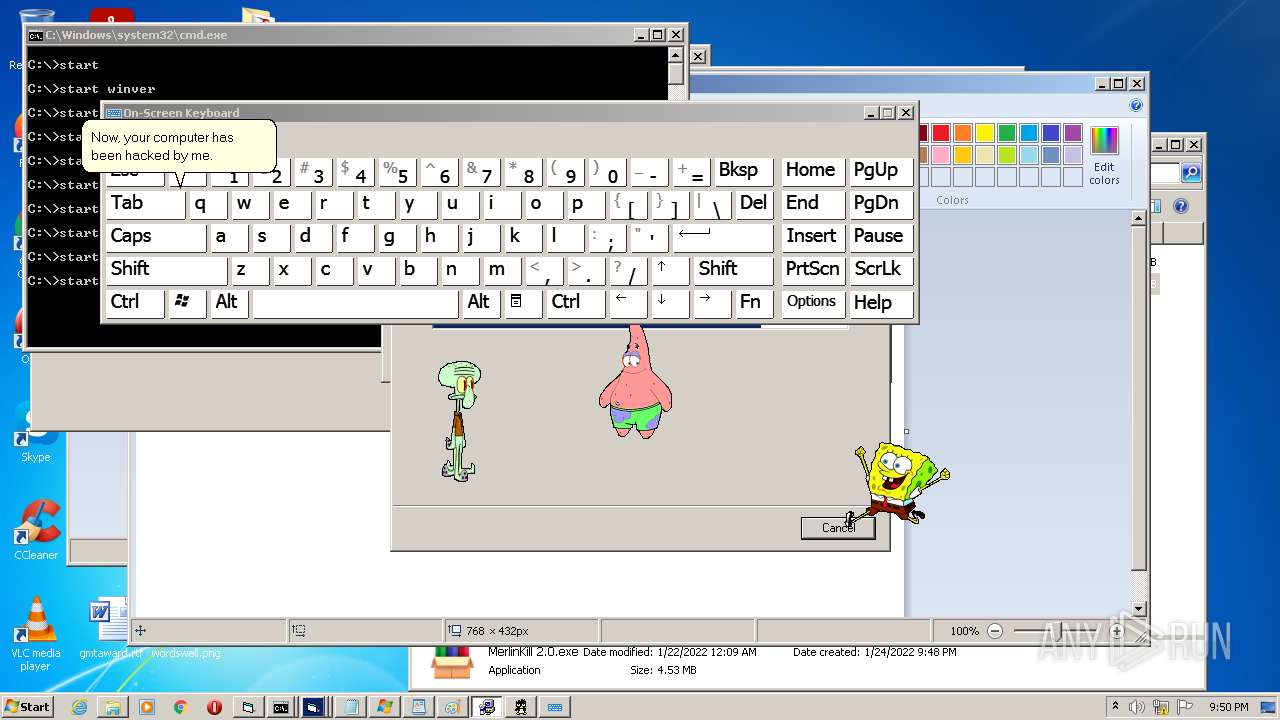
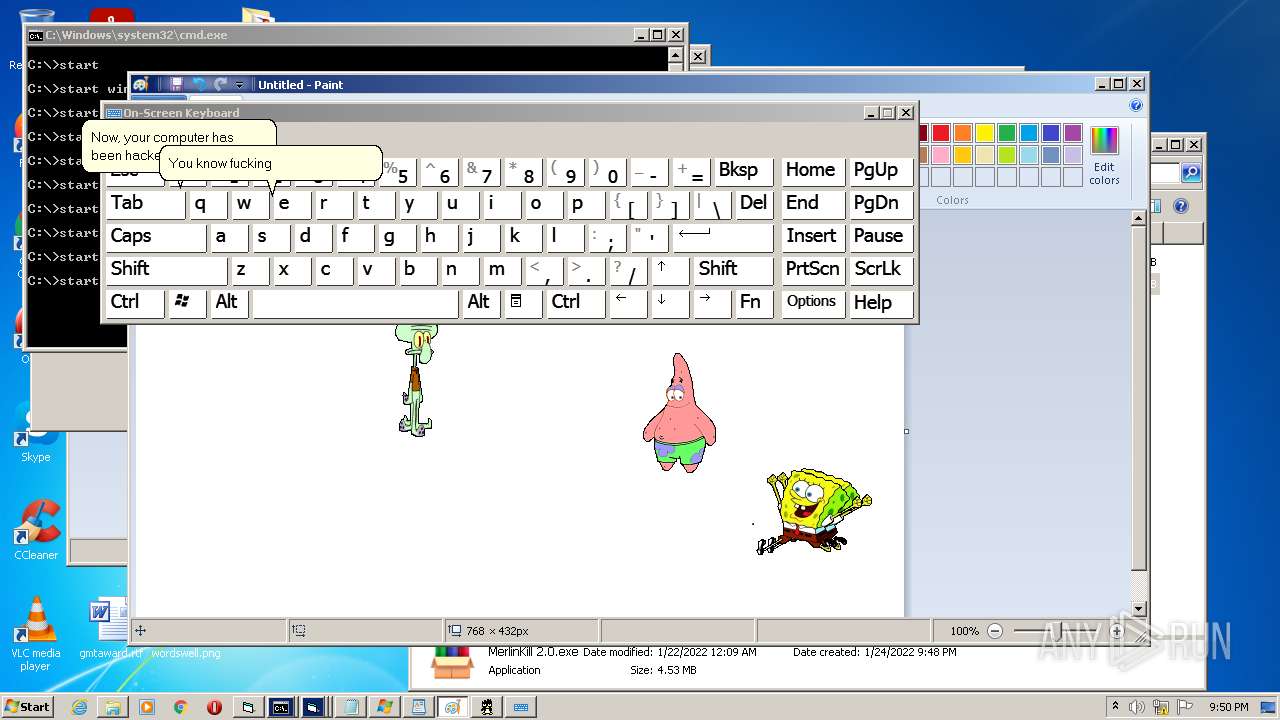
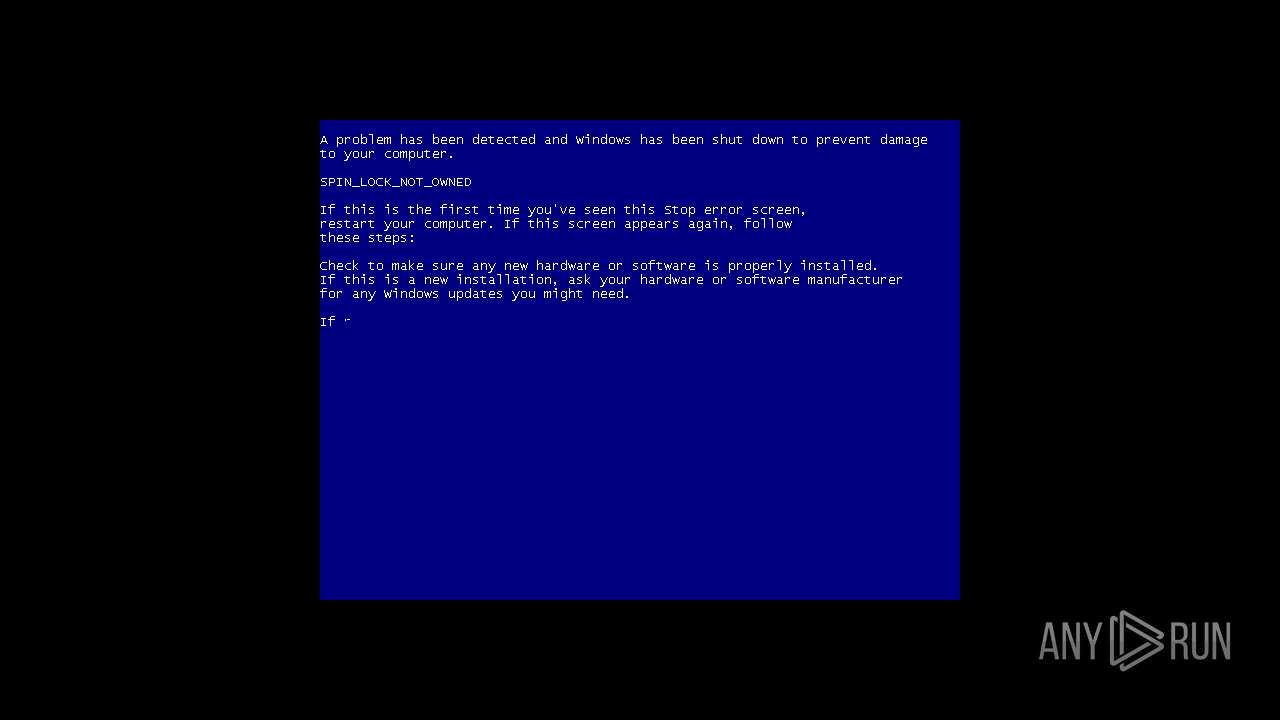
| File name: | hah.rar |
| Full analysis: | https://app.any.run/tasks/a12fe25d-cbbd-4836-aa2e-b78e3e56321d |
| Verdict: | Malicious activity |
| Threats: | Gootkit is an advanced banking trojan. It is extremely good at evading detection and has an incredibly effective persistence mechanism, making it a dangerous malware that researchers and organizations should be aware of. |
| Analysis date: | January 24, 2022, 21:48:30 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | B2A07A6A9AF4A4EE733241C1E88BF174 |
| SHA1: | FE416F9832D6AD67E38584583CB4CA532AA92EE7 |
| SHA256: | 887A7B19BDFC625F8B9B3C28A94A7090D484C296F8A8E566503EE08B63918094 |
| SSDEEP: | 196608:zge8Z+qMRHC+DJvreE/IMl3OEJD6kpepUzOgj+yJdYpIVjgwLy3z/+woO:zgei+ZRHC2hrei1OEEkIpUKgCy2Ugwul |
MALICIOUS
Application was dropped or rewritten from another process
- mash_full_setup.exe (PID: 3968)
- mash_full_setup.exe (PID: 1412)
- AgentSvr.exe (PID: 3336)
- spchapi.exe (PID: 3172)
- MerlinKill 2.0.exe (PID: 1500)
- MerlinKill 2.0.exe (PID: 3544)
- meme.exe (PID: 436)
- xp11.exe (PID: 3464)
- Project1.exe (PID: 712)
- SpongeBob_ScreenToy.exe (PID: 3460)
- AgentSvr.exe (PID: 3544)
- Lego.exe (PID: 1088)
- XO.EXE (PID: 1200)
- INS4F71.tmp (PID: 2676)
- StartBlueScreen.exe (PID: 532)
Drops executable file immediately after starts
- mash_full_setup.exe (PID: 3968)
- mash_full_setup.exe (PID: 1412)
- mash_full_setup.exe.tmp (PID: 3464)
- msagent.exe (PID: 2768)
- tv_enua.exe (PID: 2812)
- spchcpl.exe (PID: 4048)
- spchapi.exe (PID: 3172)
- MerlinKill 2.0.exe (PID: 3544)
- Lego.exe (PID: 1088)
- INS4F71.tmp (PID: 2676)
- StartBlueScreen.exe (PID: 532)
Registers / Runs the DLL via REGSVR32.EXE
- mash_full_setup.exe.tmp (PID: 3464)
- msagent.exe (PID: 2768)
- tv_enua.exe (PID: 2812)
Changes the autorun value in the registry
- tv_enua.exe (PID: 2812)
- rundll32.exe (PID: 3004)
Loads dropped or rewritten executable
- regsvr32.exe (PID: 2096)
- regsvr32.exe (PID: 2348)
- regsvr32.exe (PID: 2640)
- regsvr32.exe (PID: 3180)
- regsvr32.exe (PID: 3128)
- regsvr32.exe (PID: 600)
- regsvr32.exe (PID: 880)
- spchapi.exe (PID: 3172)
- DllHost.exe (PID: 3224)
- regsvr32.exe (PID: 2388)
- regsvr32.exe (PID: 4004)
- grpconv.exe (PID: 3360)
- consent.exe (PID: 3236)
- DllHost.exe (PID: 3412)
- DllHost.exe (PID: 3280)
- AgentSvr.exe (PID: 3336)
- WinRAR.exe (PID: 3316)
- regsvr32.exe (PID: 1368)
- mash_full_setup.exe (PID: 1412)
- mash_full_setup.exe (PID: 3968)
- regsvr32.exe (PID: 1168)
- grpconv.exe (PID: 3832)
- DllHost.exe (PID: 2812)
- regsvr32.exe (PID: 2336)
- grpconv.exe (PID: 2436)
- regsvr32.exe (PID: 1304)
- MerlinKill 2.0.exe (PID: 1500)
- grpconv.exe (PID: 2888)
- consent.exe (PID: 2228)
- DllHost.exe (PID: 3304)
- DllHost.exe (PID: 3480)
- MerlinKill 2.0.exe (PID: 3544)
- conhost.exe (PID: 3524)
- xp11.exe (PID: 3464)
- cmd.exe (PID: 3412)
- PING.EXE (PID: 3268)
- rundll32.exe (PID: 3004)
- runonce.exe (PID: 2568)
- rundll32.exe (PID: 4072)
- grpconv.exe (PID: 1480)
- meme.exe (PID: 436)
- AgentSvr.exe (PID: 3544)
- Project1.exe (PID: 712)
- SpongeBob_ScreenToy.exe (PID: 3460)
- conhost.exe (PID: 1688)
- cmd.exe (PID: 4052)
- cmd.exe (PID: 2644)
- mspaint.exe (PID: 3088)
- wordpad.exe (PID: 3764)
- conhost.exe (PID: 2764)
- winver.exe (PID: 3816)
- notepad.exe (PID: 3204)
- svchost.exe (PID: 3520)
- consent.exe (PID: 888)
- consent.exe (PID: 744)
- DllHost.exe (PID: 832)
- Narrator.exe (PID: 2076)
- osk.exe (PID: 3160)
- Lego.exe (PID: 1088)
- XO.EXE (PID: 1200)
- INS4F71.tmp (PID: 2676)
- SearchProtocolHost.exe (PID: 3256)
- SearchFilterHost.exe (PID: 2244)
- DllHost.exe (PID: 3956)
- conhost.exe (PID: 3324)
- taskkill.exe (PID: 3652)
- wmiprvse.exe (PID: 272)
- cmd.exe (PID: 2856)
- conhost.exe (PID: 2248)
- StartBlueScreen.exe (PID: 532)
- cmd.exe (PID: 2332)
GOOTKIT detected
- spchapi.exe (PID: 3172)
Runs PING.EXE for delay simulation
- cmd.exe (PID: 3412)
Runs app for hidden code execution
- cmd.exe (PID: 4052)
Tries to delete the host file
- cmd.exe (PID: 2856)
SUSPICIOUS
Checks supported languages
- WinRAR.exe (PID: 3316)
- mash_full_setup.exe (PID: 3968)
- mash_full_setup.exe.tmp (PID: 3268)
- mash_full_setup.exe.tmp (PID: 3464)
- mash_full_setup.exe (PID: 1412)
- msagent.exe (PID: 2768)
- tv_enua.exe (PID: 2812)
- AgentSvr.exe (PID: 3336)
- spchcpl.exe (PID: 4048)
- spchapi.exe (PID: 3172)
- MerlinKill 2.0.exe (PID: 3544)
- MerlinKill 2.0.exe (PID: 1500)
- cmd.exe (PID: 3412)
- xp11.exe (PID: 3464)
- conhost.exe (PID: 3524)
- meme.exe (PID: 436)
- AgentSvr.exe (PID: 3544)
- conhost.exe (PID: 1688)
- SpongeBob_ScreenToy.exe (PID: 3460)
- cmd.exe (PID: 4052)
- Project1.exe (PID: 712)
- conhost.exe (PID: 2764)
- cmd.exe (PID: 2644)
- wordpad.exe (PID: 3764)
- Lego.exe (PID: 1088)
- XO.EXE (PID: 1200)
- INS4F71.tmp (PID: 2676)
- conhost.exe (PID: 3324)
- cmd.exe (PID: 2856)
- wmiprvse.exe (PID: 272)
- conhost.exe (PID: 2248)
- StartBlueScreen.exe (PID: 532)
- cmd.exe (PID: 2332)
Reads the computer name
- WinRAR.exe (PID: 3316)
- mash_full_setup.exe.tmp (PID: 3268)
- mash_full_setup.exe.tmp (PID: 3464)
- msagent.exe (PID: 2768)
- tv_enua.exe (PID: 2812)
- spchcpl.exe (PID: 4048)
- spchapi.exe (PID: 3172)
- MerlinKill 2.0.exe (PID: 1500)
- MerlinKill 2.0.exe (PID: 3544)
- AgentSvr.exe (PID: 3544)
- meme.exe (PID: 436)
- cmd.exe (PID: 4052)
- wordpad.exe (PID: 3764)
- INS4F71.tmp (PID: 2676)
- wmiprvse.exe (PID: 272)
- StartBlueScreen.exe (PID: 532)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 3316)
- mash_full_setup.exe.tmp (PID: 3464)
- msagent.exe (PID: 2768)
- tv_enua.exe (PID: 2812)
- spchcpl.exe (PID: 4048)
- spchapi.exe (PID: 3172)
- MerlinKill 2.0.exe (PID: 3544)
- INS4F71.tmp (PID: 2676)
Drops a file with too old compile date
- WinRAR.exe (PID: 3316)
- mash_full_setup.exe (PID: 3968)
- mash_full_setup.exe (PID: 1412)
- mash_full_setup.exe.tmp (PID: 3464)
- msagent.exe (PID: 2768)
- tv_enua.exe (PID: 2812)
- spchcpl.exe (PID: 4048)
- spchapi.exe (PID: 3172)
- MerlinKill 2.0.exe (PID: 3544)
- Lego.exe (PID: 1088)
- INS4F71.tmp (PID: 2676)
- StartBlueScreen.exe (PID: 532)
Executable content was dropped or overwritten
- mash_full_setup.exe (PID: 3968)
- WinRAR.exe (PID: 3316)
- mash_full_setup.exe (PID: 1412)
- mash_full_setup.exe.tmp (PID: 3464)
- msagent.exe (PID: 2768)
- tv_enua.exe (PID: 2812)
- spchcpl.exe (PID: 4048)
- spchapi.exe (PID: 3172)
- MerlinKill 2.0.exe (PID: 3544)
- Lego.exe (PID: 1088)
- INS4F71.tmp (PID: 2676)
- StartBlueScreen.exe (PID: 532)
Reads the Windows organization settings
- mash_full_setup.exe.tmp (PID: 3464)
- winver.exe (PID: 3816)
Reads Windows owner or organization settings
- mash_full_setup.exe.tmp (PID: 3464)
- winver.exe (PID: 3816)
Creates a directory in Program Files
- mash_full_setup.exe.tmp (PID: 3464)
- INS4F71.tmp (PID: 2676)
Creates/Modifies COM task schedule object
- regsvr32.exe (PID: 1168)
- regsvr32.exe (PID: 600)
- regsvr32.exe (PID: 2336)
- regsvr32.exe (PID: 2640)
- regsvr32.exe (PID: 3128)
- regsvr32.exe (PID: 2348)
- regsvr32.exe (PID: 2096)
- regsvr32.exe (PID: 3180)
- regsvr32.exe (PID: 880)
- regsvr32.exe (PID: 2388)
- spchapi.exe (PID: 3172)
Drops a file with a compile date too recent
- msagent.exe (PID: 2768)
- tv_enua.exe (PID: 2812)
- spchcpl.exe (PID: 4048)
- spchapi.exe (PID: 3172)
Creates files in the Windows directory
- msagent.exe (PID: 2768)
- mash_full_setup.exe.tmp (PID: 3464)
- tv_enua.exe (PID: 2812)
- spchcpl.exe (PID: 4048)
- spchapi.exe (PID: 3172)
- rundll32.exe (PID: 3004)
- StartBlueScreen.exe (PID: 532)
Removes files from Windows directory
- msagent.exe (PID: 2768)
- tv_enua.exe (PID: 2812)
- spchcpl.exe (PID: 4048)
- spchapi.exe (PID: 3172)
- rundll32.exe (PID: 3004)
- cmd.exe (PID: 2856)
Changes default file association
- mash_full_setup.exe.tmp (PID: 3464)
Reads Microsoft Outlook installation path
- MerlinKill 2.0.exe (PID: 1500)
Reads internet explorer settings
- MerlinKill 2.0.exe (PID: 1500)
- Narrator.exe (PID: 2076)
Application launched itself
- MerlinKill 2.0.exe (PID: 1500)
- cmd.exe (PID: 4052)
Starts CMD.EXE for commands execution
- MerlinKill 2.0.exe (PID: 3544)
- meme.exe (PID: 436)
- cmd.exe (PID: 4052)
Uses RUNDLL32.EXE to load library
- xp11.exe (PID: 3464)
- runonce.exe (PID: 2568)
Reads the time zone
- runonce.exe (PID: 2568)
Executed via COM
- AgentSvr.exe (PID: 3544)
Starts application with an unusual extension
- Lego.exe (PID: 1088)
Creates files in the user directory
- Narrator.exe (PID: 2076)
Creates a software uninstall entry
- INS4F71.tmp (PID: 2676)
Creates files in the program directory
- INS4F71.tmp (PID: 2676)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 2856)
Creates or modifies windows services
- StartBlueScreen.exe (PID: 532)
Creates files in the driver directory
- StartBlueScreen.exe (PID: 532)
INFO
Checks supported languages
- DllHost.exe (PID: 2812)
- consent.exe (PID: 3236)
- DllHost.exe (PID: 3412)
- DllHost.exe (PID: 3224)
- regsvr32.exe (PID: 1368)
- regsvr32.exe (PID: 1168)
- regsvr32.exe (PID: 4004)
- regsvr32.exe (PID: 1304)
- regsvr32.exe (PID: 3180)
- regsvr32.exe (PID: 600)
- DllHost.exe (PID: 3280)
- regsvr32.exe (PID: 2348)
- regsvr32.exe (PID: 2336)
- regsvr32.exe (PID: 2640)
- regsvr32.exe (PID: 3128)
- grpconv.exe (PID: 3360)
- regsvr32.exe (PID: 2096)
- grpconv.exe (PID: 2888)
- regsvr32.exe (PID: 2388)
- regsvr32.exe (PID: 880)
- grpconv.exe (PID: 2436)
- grpconv.exe (PID: 3832)
- DllHost.exe (PID: 3304)
- DllHost.exe (PID: 3480)
- consent.exe (PID: 2228)
- PING.EXE (PID: 3268)
- rundll32.exe (PID: 3004)
- runonce.exe (PID: 2568)
- rundll32.exe (PID: 4072)
- grpconv.exe (PID: 1480)
- winver.exe (PID: 3816)
- notepad.exe (PID: 3204)
- mspaint.exe (PID: 3088)
- DllHost.exe (PID: 832)
- Narrator.exe (PID: 2076)
- consent.exe (PID: 744)
- svchost.exe (PID: 3520)
- consent.exe (PID: 888)
- osk.exe (PID: 3160)
- SearchProtocolHost.exe (PID: 3256)
- SearchFilterHost.exe (PID: 2244)
- DllHost.exe (PID: 3956)
- taskkill.exe (PID: 3652)
Reads the computer name
- DllHost.exe (PID: 2812)
- consent.exe (PID: 3236)
- DllHost.exe (PID: 3412)
- DllHost.exe (PID: 3224)
- regsvr32.exe (PID: 4004)
- regsvr32.exe (PID: 1368)
- regsvr32.exe (PID: 1304)
- DllHost.exe (PID: 3280)
- consent.exe (PID: 2228)
- DllHost.exe (PID: 3304)
- DllHost.exe (PID: 3480)
- PING.EXE (PID: 3268)
- rundll32.exe (PID: 3004)
- runonce.exe (PID: 2568)
- rundll32.exe (PID: 4072)
- mspaint.exe (PID: 3088)
- svchost.exe (PID: 3520)
- consent.exe (PID: 888)
- DllHost.exe (PID: 832)
- osk.exe (PID: 3160)
- consent.exe (PID: 744)
- Narrator.exe (PID: 2076)
- SearchProtocolHost.exe (PID: 3256)
- SearchFilterHost.exe (PID: 2244)
- taskkill.exe (PID: 3652)
- DllHost.exe (PID: 3956)
Manual execution by user
- mash_full_setup.exe (PID: 3968)
- MerlinKill 2.0.exe (PID: 1500)
Checks Windows Trust Settings
- consent.exe (PID: 3236)
- consent.exe (PID: 2228)
- consent.exe (PID: 888)
- consent.exe (PID: 744)
Application was dropped or rewritten from another process
- mash_full_setup.exe.tmp (PID: 3268)
- mash_full_setup.exe.tmp (PID: 3464)
- msagent.exe (PID: 2768)
- tv_enua.exe (PID: 2812)
- spchcpl.exe (PID: 4048)
Loads dropped or rewritten executable
- mash_full_setup.exe.tmp (PID: 3464)
- tv_enua.exe (PID: 2812)
- msagent.exe (PID: 2768)
- spchcpl.exe (PID: 4048)
- mash_full_setup.exe.tmp (PID: 3268)
Creates files in the program directory
- mash_full_setup.exe.tmp (PID: 3464)
Reads mouse settings
- regsvr32.exe (PID: 1368)
Creates a software uninstall entry
- mash_full_setup.exe.tmp (PID: 3464)
- tv_enua.exe (PID: 2812)
Reads CPU info
- runonce.exe (PID: 2568)
Reads settings of System Certificates
- consent.exe (PID: 888)
- consent.exe (PID: 744)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
113
Monitored processes
80
Malicious processes
22
Suspicious processes
17
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 272 | C:\Windows\system32\wbem\wmiprvse.exe -secured -Embedding | C:\Windows\system32\wbem\wmiprvse.exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: WMI Provider Host Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 436 | C:\Merlin\meme.exe | C:\Merlin\meme.exe | — | cmd.exe | |||||||||||
User: admin Company: BellCraft Technologies Integrity Level: HIGH Exit code: 3221225547 Version: 7.05 Modules
| |||||||||||||||
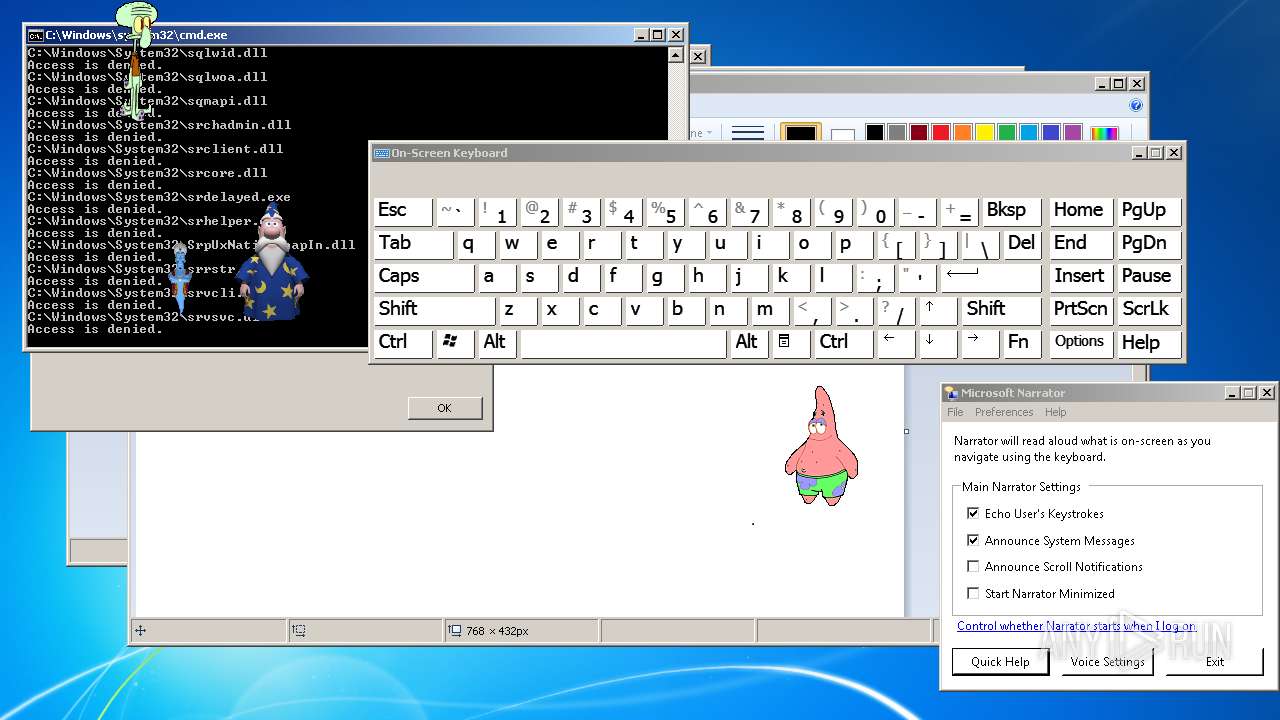
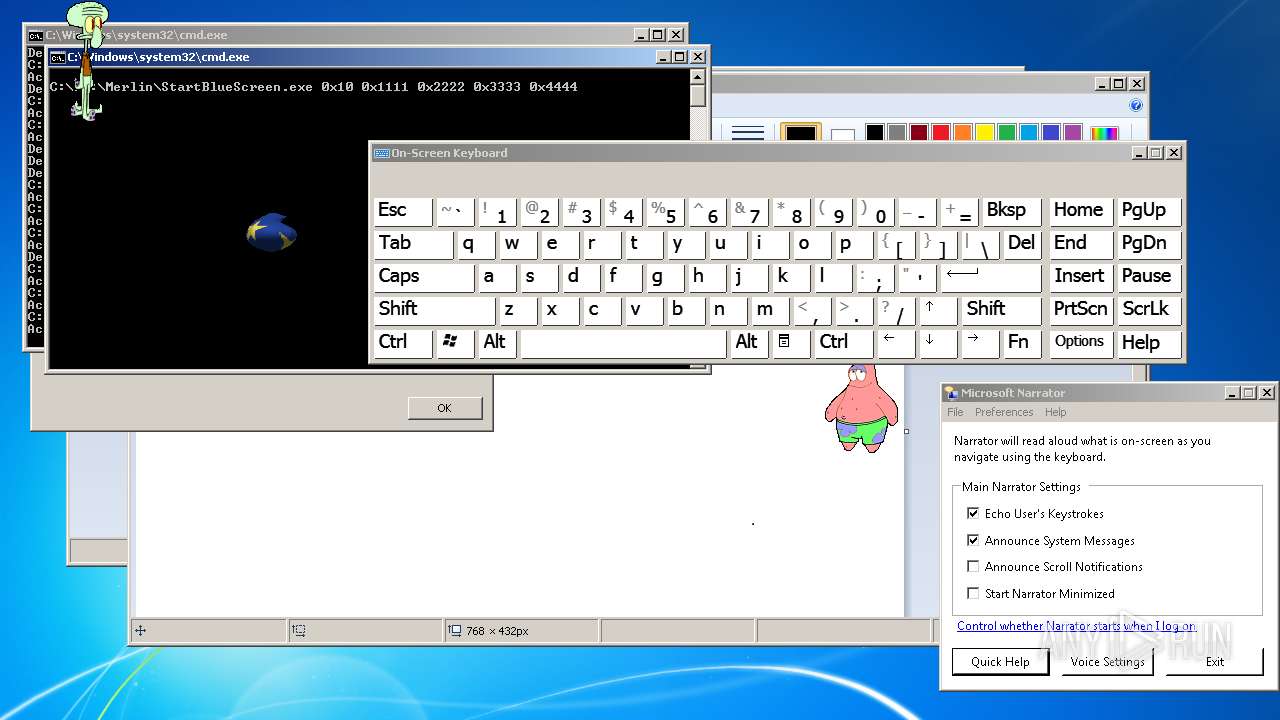
| 532 | C:\Merlin\StartBlueScreen.exe 0x10 0x1111 0x2222 0x3333 0x4444 | C:\Merlin\StartBlueScreen.exe | cmd.exe | ||||||||||||
User: admin Company: NirSoft Integrity Level: HIGH Description: StartBlueScreen Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 600 | regsvr32 /s "C:\Windows\msagent\AgentCtl.dll" | C:\Windows\system32\regsvr32.exe | — | msagent.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 684 | "C:\Windows\system32\osk.exe" | C:\Windows\system32\osk.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Accessibility On-Screen Keyboard Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 712 | C:\Merlin\Project1.exe | C:\Merlin\Project1.exe | — | meme.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 744 | consent.exe 924 240 0019F050 | C:\Windows\system32\consent.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Consent UI for administrative applications Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 832 | C:\Windows\system32\DllHost.exe /Processid:{E10F6C3A-F1AE-4ADC-AA9D-2FE65525666E} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 880 | regsvr32 /s C:\Windows\lhsp\tv\tvenuax.dll | C:\Windows\system32\regsvr32.exe | — | tv_enua.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 888 | consent.exe 924 270 02A9C018 | C:\Windows\system32\consent.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Consent UI for administrative applications Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
15 563
Read events
13 888
Write events
1 594
Delete events
81
Modification events
| (PID) Process: | (3316) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3316) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3316) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3316) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3316) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3316) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\hah.rar | |||
| (PID) Process: | (3316) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3316) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3316) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3316) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
144
Suspicious files
15
Text files
59
Unknown types
32
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3316 | WinRAR.exe | C:\Users\admin\Desktop\hah\MerlinKill 2.0.exe | executable | |
MD5:— | SHA256:— | |||
| 3464 | mash_full_setup.exe.tmp | C:\Users\admin\AppData\Local\Temp\is-68PMJ.tmp\_isetup\_shfoldr.dll | executable | |
MD5:92DC6EF532FBB4A5C3201469A5B5EB63 | SHA256:9884E9D1B4F8A873CCBD81F8AD0AE257776D2348D027D811A56475E028360D87 | |||
| 3968 | mash_full_setup.exe | C:\Users\admin\AppData\Local\Temp\is-BV4VV.tmp\mash_full_setup.exe.tmp | executable | |
MD5:35825DC6EFC3C1DDE507E2224574F711 | SHA256:2D3108E9BB7C88892F3C2247D7B9A3B62A3E5CF6DB502650655C0C912F8D25D9 | |||
| 3464 | mash_full_setup.exe.tmp | C:\Users\admin\AppData\Local\Temp\is-68PMJ.tmp\_isetup\_RegDLL.tmp | executable | |
MD5:C594B792B9C556EA62A30DE541D2FB03 | SHA256:5DCC1E0A197922907BCA2C4369F778BD07EE4B1BBBDF633E987A028A314D548E | |||
| 1412 | mash_full_setup.exe | C:\Users\admin\AppData\Local\Temp\is-70DEP.tmp\mash_full_setup.exe.tmp | executable | |
MD5:35825DC6EFC3C1DDE507E2224574F711 | SHA256:2D3108E9BB7C88892F3C2247D7B9A3B62A3E5CF6DB502650655C0C912F8D25D9 | |||
| 3464 | mash_full_setup.exe.tmp | C:\Program Files\BellCraft.com\MASH\MASH.chm | chm | |
MD5:CC7C6CF1ADAF17773589C90D65F8C173 | SHA256:7C0570592C435AC95B029762FEB25D9ACEE95FABF8BA4D3EA772DB466A5FCAE3 | |||
| 3464 | mash_full_setup.exe.tmp | C:\Program Files\BellCraft.com\MASH\is-6CHDU.tmp | ini | |
MD5:14EE168040435559B97C3F6E16A85BD8 | SHA256:3E0493BDE8EED23B62B9C10675370F6B08E4203FD27FD903822659E12B3965EB | |||
| 3464 | mash_full_setup.exe.tmp | C:\Program Files\BellCraft.com\MASH\is-RTJT3.tmp | text | |
MD5:816D59B6DA5F34FE80B8E2D1647FE63D | SHA256:88D20E6925F7BC11434A2793D6A9FA37FBB26366A0F8CE50B3C1779C594F13CA | |||
| 3464 | mash_full_setup.exe.tmp | C:\Program Files\BellCraft.com\MASH\is-4M7F3.tmp | text | |
MD5:43C8F9189162D2FD142B261AC06B90C9 | SHA256:26512915E5E2E8E1FAD2F6FFB904B0A3F22EF87B8D094D423E45FA2B672AAF9F | |||
| 3464 | mash_full_setup.exe.tmp | C:\Program Files\BellCraft.com\MASH\is-JHR4O.tmp | chm | |
MD5:CC7C6CF1ADAF17773589C90D65F8C173 | SHA256:7C0570592C435AC95B029762FEB25D9ACEE95FABF8BA4D3EA772DB466A5FCAE3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
DNS requests
Threats
Process | Message |
|---|---|
AgentSvr.exe |
++++++ ITTSCentral::Release() Called ++++++
|
AgentSvr.exe |
++++++ ITTSCentral::Release() Called ++++++
|
AgentSvr.exe | ClaimOutput
|
AgentSvr.exe | UnclaimOutput
|
AgentSvr.exe | ClaimOutput
|
AgentSvr.exe | UnclaimOutput
|
AgentSvr.exe | ClaimOutput
|
AgentSvr.exe | UnclaimOutput
|
AgentSvr.exe | ClaimOutput
|
AgentSvr.exe | UnclaimOutput
|