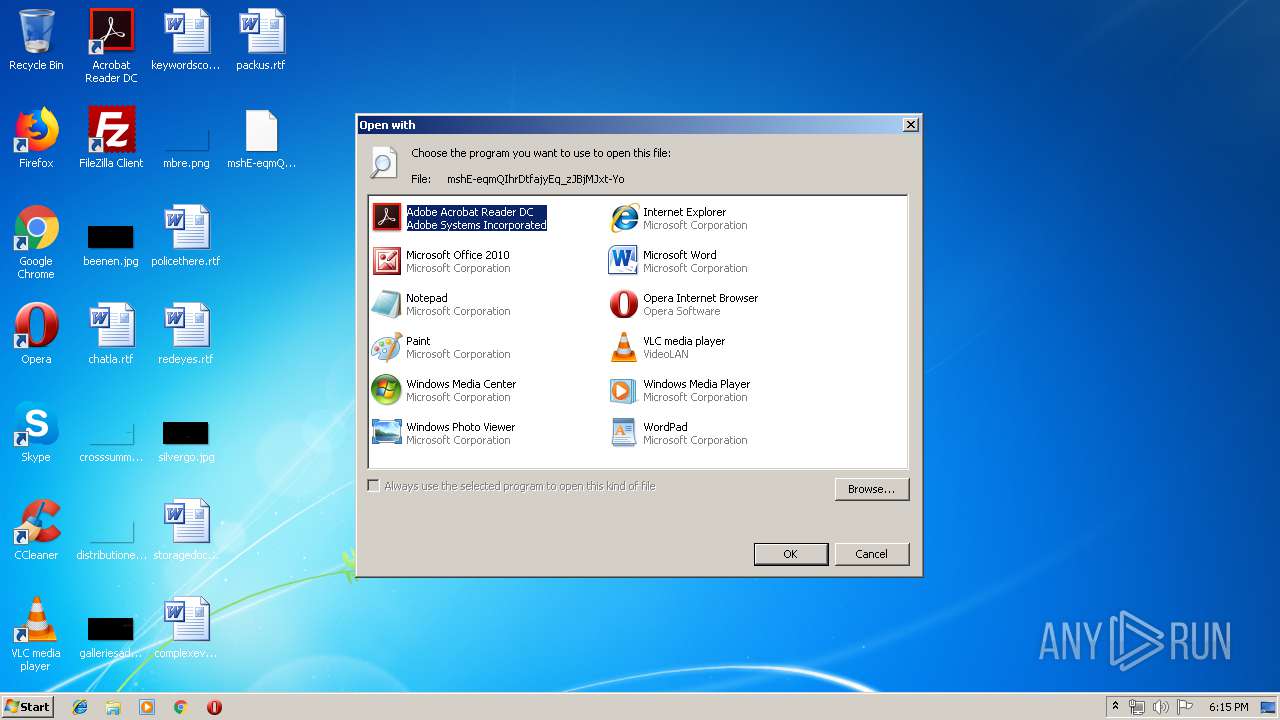
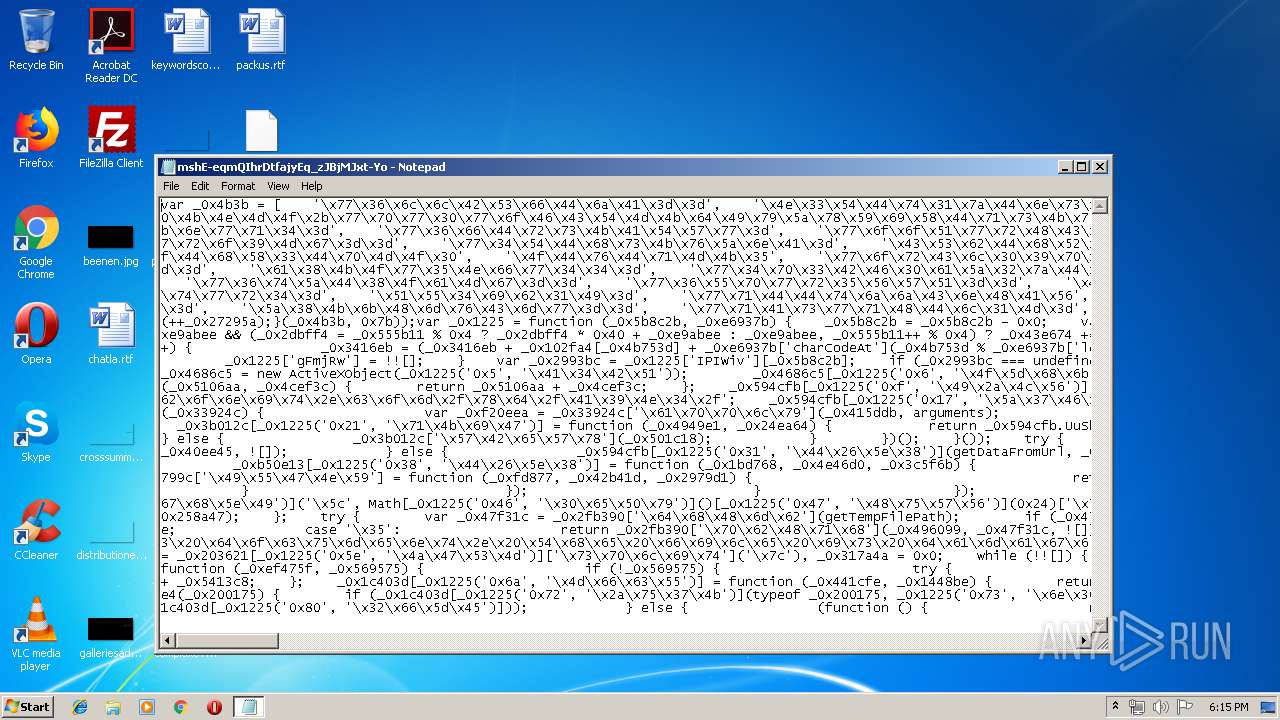
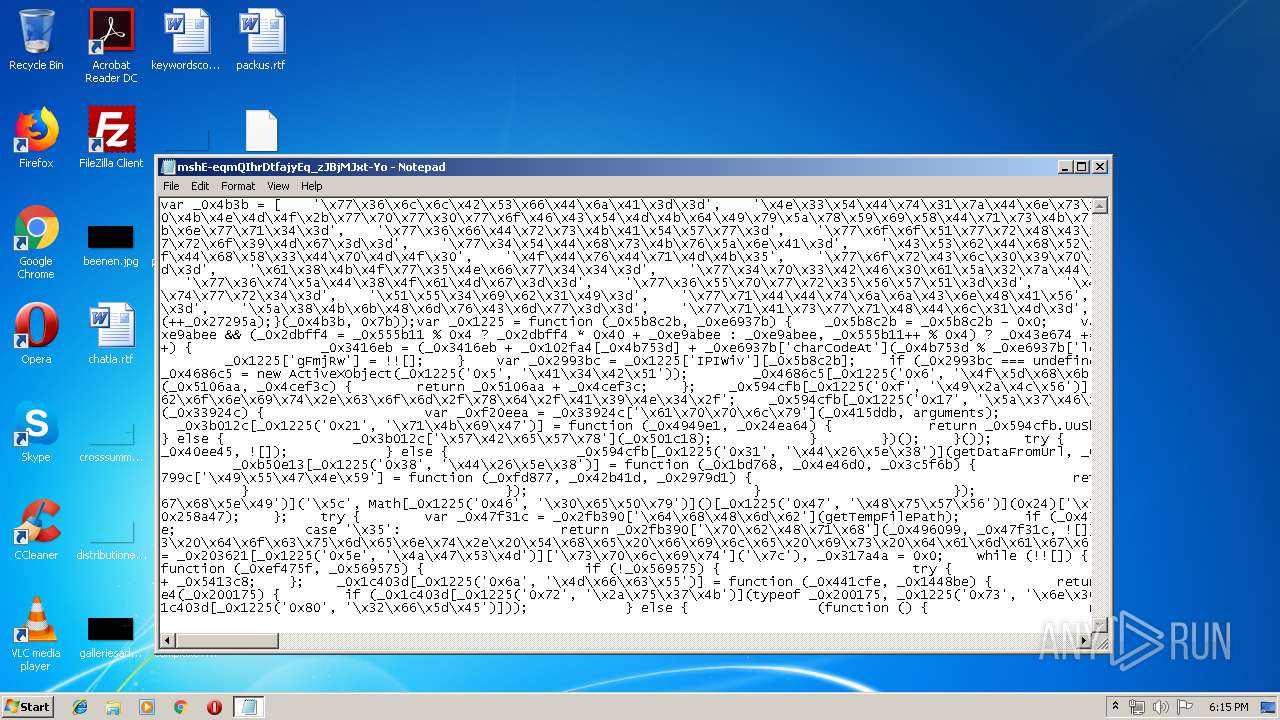
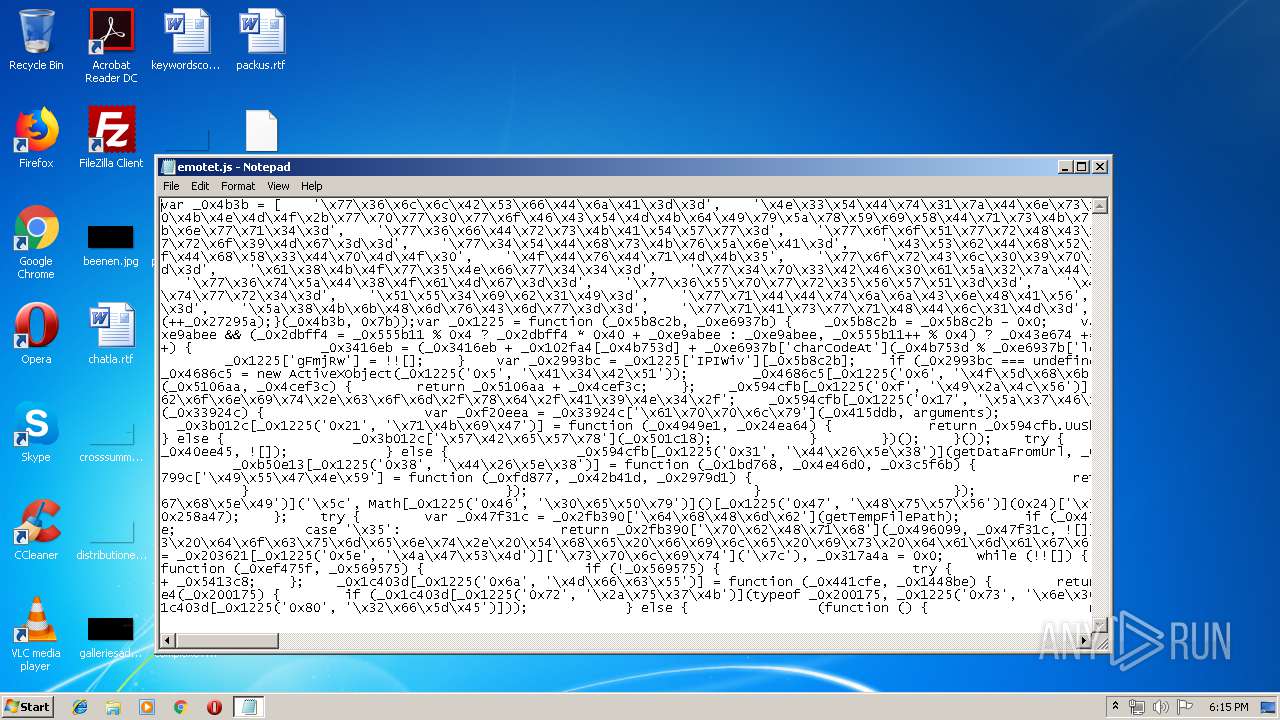
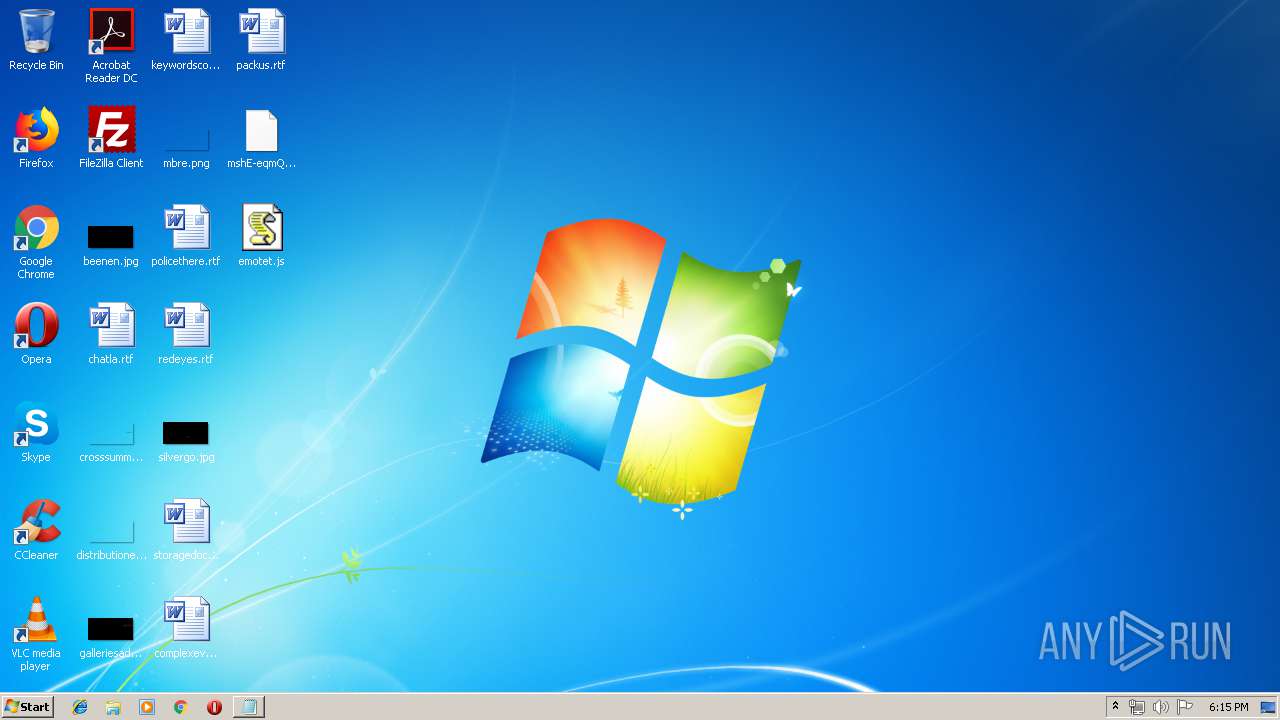
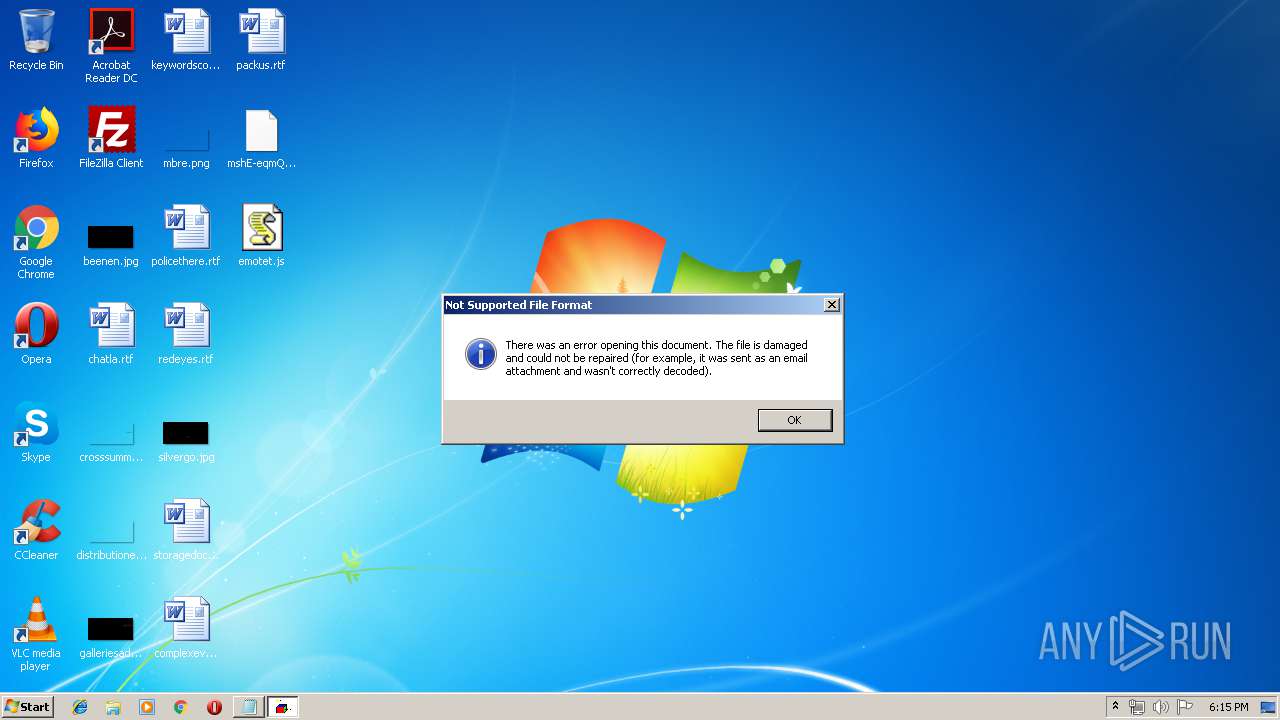
| download: | mshE-eqmQIhrDtfajyEq_zJBjMJxt-Yo |
| Full analysis: | https://app.any.run/tasks/d8419b32-7e54-4e23-b866-ed60aff09c4b |
| Verdict: | Malicious activity |
| Analysis date: | April 23, 2019, 17:15:06 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines |
| MD5: | 0048F1B910697EB8B5F1C0AC9985F102 |
| SHA1: | AEEE2E8F15AEE2C1AEAF193EAEC3666A34FD5A1F |
| SHA256: | 8870927B7FCB804322779608FABF59E1C019245DF08AAAF5F9202D131E92EFDA |
| SSDEEP: | 768:SeftiG5S0FRVA0sH6Qttk6ueJvKA2bE1SImBtYTl5sQBpt+T+TJrrVZdEDS1TEis:SeFiG5S0FPA0sH6v7oX/E |
MALICIOUS
Changes settings of System certificates
- WScript.exe (PID: 2492)
SUSPICIOUS
Adds / modifies Windows certificates
- WScript.exe (PID: 2492)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
36
Monitored processes
3
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2492 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Desktop\emotet.js" | C:\Windows\System32\WScript.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 3640 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\mshE-eqmQIhrDtfajyEq_zJBjMJxt-Yo | C:\Windows\system32\NOTEPAD.EXE | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 4004 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\Desktop\mshE-eqmQIhrDtfajyEq_zJBjMJxt-Yo | C:\Windows\system32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
753
Read events
607
Write events
143
Delete events
3
Modification events
| (PID) Process: | (4004) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | LangID |
Value: 0904 | |||
| (PID) Process: | (4004) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe |
Value: Adobe Acrobat Reader DC | |||
| (PID) Process: | (4004) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\eHome\ehshell.exe |
Value: Windows Media Center | |||
| (PID) Process: | (4004) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Internet Explorer\iexplore.exe |
Value: Internet Explorer | |||
| (PID) Process: | (4004) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\system32\mspaint.exe |
Value: Paint | |||
| (PID) Process: | (4004) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\system32\NOTEPAD.EXE |
Value: Notepad | |||
| (PID) Process: | (4004) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\PROGRA~1\MICROS~1\Office14\OIS.EXE |
Value: Microsoft Office 2010 | |||
| (PID) Process: | (4004) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Opera\Opera.exe |
Value: Opera Internet Browser | |||
| (PID) Process: | (4004) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Windows Photo Viewer\PhotoViewer.dll |
Value: Windows Photo Viewer | |||
| (PID) Process: | (4004) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\VideoLAN\VLC\vlc.exe |
Value: VLC media player | |||
Executable files
0
Suspicious files
0
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3640 | NOTEPAD.EXE | C:\Users\admin\Desktop\emotet.js | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
5
DNS requests
6
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2492 | WScript.exe | GET | 404 | 164.52.146.13:80 | http://potterspots.com/cgi-bin/8MnY/ | US | xml | 345 b | suspicious |
2492 | WScript.exe | GET | 404 | 216.177.136.16:80 | http://sandovalgraphics.com/webalizer/Xfje/ | US | xml | 345 b | suspicious |
2492 | WScript.exe | GET | 404 | 167.114.189.192:80 | http://nexusinfor.com/img/pjVK/ | CA | xml | 345 b | malicious |
2492 | WScript.exe | GET | 404 | 185.83.144.75:80 | http://recepsahin.net/assets/F2f/ | TR | xml | 345 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2492 | WScript.exe | 164.52.146.13:80 | potterspots.com | Latisys-Denver, LLC | US | suspicious |
2492 | WScript.exe | 216.177.136.16:80 | sandovalgraphics.com | Web Site Source | US | suspicious |
— | — | 192.3.2.170:443 | sundarbonit.com | ColoCrossing | US | malicious |
2492 | WScript.exe | 167.114.189.192:80 | nexusinfor.com | OVH SAS | CA | malicious |
2492 | WScript.exe | 185.83.144.75:80 | recepsahin.net | Netinternet Bilisim Teknolojileri AS | TR | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
potterspots.com |
| suspicious |
sandovalgraphics.com |
| suspicious |
sundarbonit.com |
| malicious |
nexusinfor.com |
| malicious |
recepsahin.net |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2492 | WScript.exe | Misc activity | SUSPICIOUS [PTsecurity] Cmd.Powershell.Download HTTP UserAgent (Win7) |
2492 | WScript.exe | Misc activity | SUSPICIOUS [PTsecurity] Cmd.Powershell.Download HTTP UserAgent (Win7) |
2492 | WScript.exe | Misc activity | SUSPICIOUS [PTsecurity] Cmd.Powershell.Download HTTP UserAgent (Win7) |
2492 | WScript.exe | Misc activity | SUSPICIOUS [PTsecurity] Cmd.Powershell.Download HTTP UserAgent (Win7) |