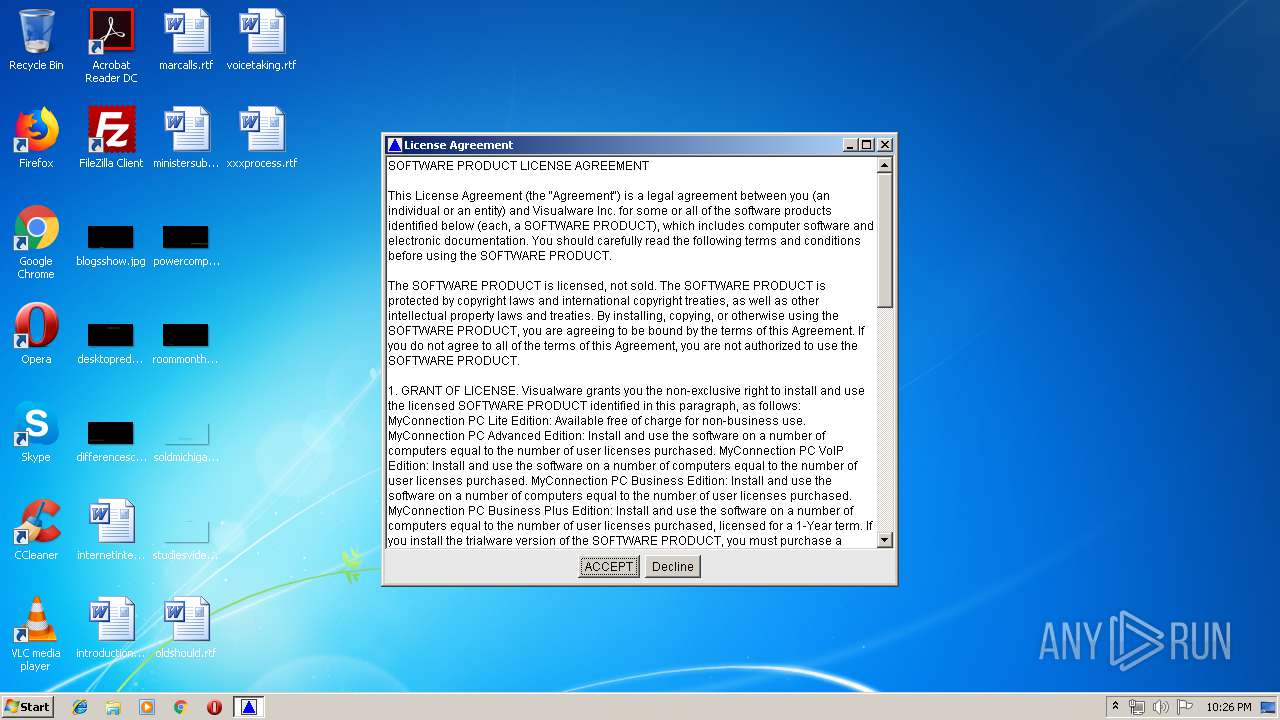
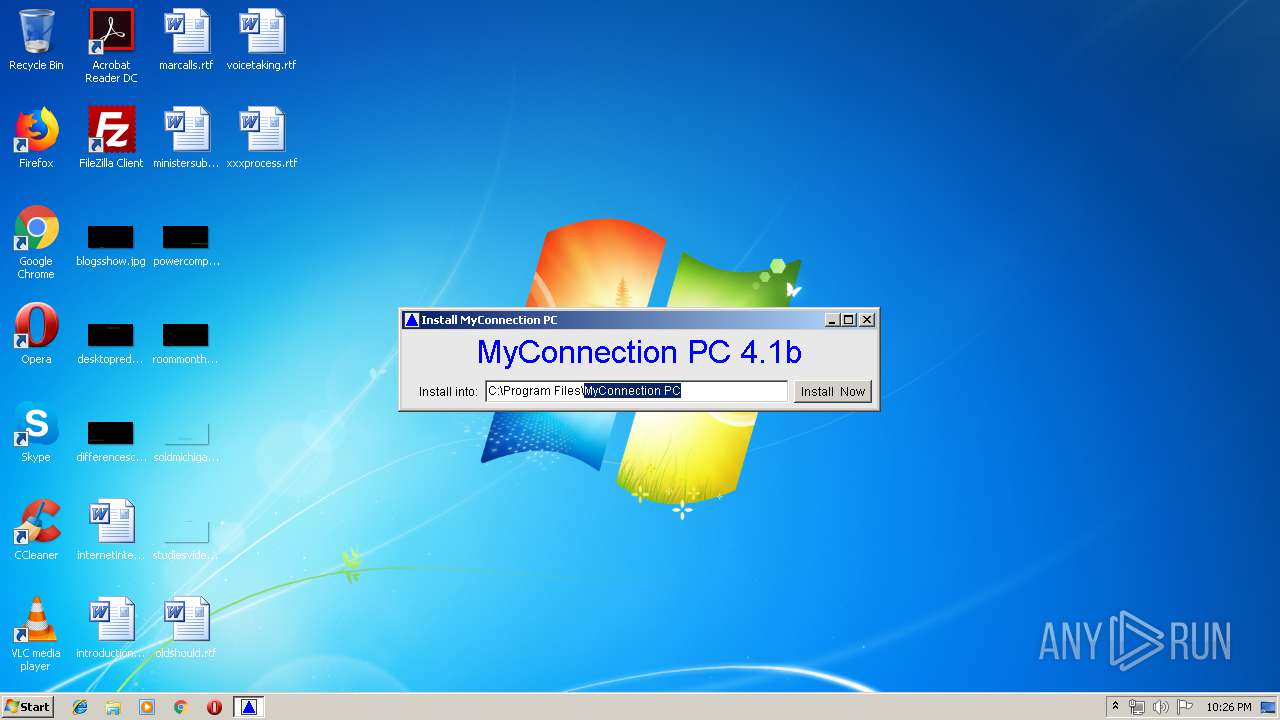
| download: | myspeedpc.exe |
| Full analysis: | https://app.any.run/tasks/d7b9121b-f42f-4957-90ff-67f474201442 |
| Verdict: | Malicious activity |
| Analysis date: | April 14, 2019, 21:25:49 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | B5F774DE19773CDF2919262B23129E28 |
| SHA1: | 0FEA73D8B31CDCD8AEDE9A3033699467CEC8F6E2 |
| SHA256: | 886CF9C517CD73B5D4B5B85564638EA5FD7931733EB676DA628F1B006C1A489F |
| SSDEEP: | 24576:hnzABXFT5Nkp28OTkjPz+ynIAtuf+zsQ5jhSMlj+5nxFjry4DATy5:5zukUZwb+ynttuf+zsASMlcxhyaB |
MALICIOUS
Loads dropped or rewritten executable
- java.exe (PID: 3632)
- java.exe (PID: 904)
- java.exe (PID: 1472)
Application was dropped or rewritten from another process
- MakeLink.exe (PID: 936)
- runfile.exe (PID: 3160)
- msclientae.exe (PID: 3212)
SUSPICIOUS
Executable content was dropped or overwritten
- java.exe (PID: 3632)
- java.exe (PID: 3860)
- java.exe (PID: 2404)
Creates files in the program directory
- java.exe (PID: 3632)
- MakeLink.exe (PID: 936)
Creates a software uninstall entry
- java.exe (PID: 3632)
Uses IPCONFIG.EXE to discover IP address
- java.exe (PID: 904)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2005:12:19 19:55:35+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 6656 |
| InitializedDataSize: | 5632 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x26c8 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 19-Dec-2005 18:55:35 |
| Detected languages: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000D8 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 4 |
| Time date stamp: | 19-Dec-2005 18:55:35 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x0000185C | 0x00001A00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 5.99769 |
.rdata | 0x00003000 | 0x0000062A | 0x00000800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.11709 |
.data | 0x00004000 | 0x000005A4 | 0x00000600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.35919 |
.rsrc | 0x00005000 | 0x00000604 | 0x00000800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.97551 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 4.81626 | 542 | Latin 1 / Western European | English - United States | RT_MANIFEST |
234 | 2.16096 | 20 | Latin 1 / Western European | English - United States | RT_GROUP_ICON |
Imports
ADVAPI32.dll |
KERNEL32.dll |
MSVCRT.dll |
SHELL32.dll |
USER32.dll |
Total processes
46
Monitored processes
11
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 904 | java -mx256m jexepackboot R "C:\Program Files\MyConnection PC\msclientae.exe" "C:\Users\admin\AppData\Local\Temp\X438C8C" | C:\ProgramData\Oracle\Java\javapath\java.exe | msclientae.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: HIGH Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.920.14 Modules
| |||||||||||||||
| 936 | "C:\Users\admin\AppData\Local\Temp\X430A50\MakeLink" C:\Users\admin\AppData\Local\Temp\X430A50\makelinks.txt | C:\Users\admin\AppData\Local\Temp\X430A50\MakeLink.exe | — | java.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1472 | java -mx256m jexepackboot R "C:\Program Files\MyConnection PC\runfile.exe" "C:\Users\admin\AppData\Local\Temp\X437C58" "/install" | C:\ProgramData\Oracle\Java\javapath\java.exe | — | runfile.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: HIGH Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.920.14 Modules
| |||||||||||||||
| 2404 | java -mx256m jexepackboot E "C:\Program Files\MyConnection PC\runfile.exe" "C:\Users\admin\AppData\Local\Temp\X437C58" "/install" | C:\ProgramData\Oracle\Java\javapath\java.exe | runfile.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: HIGH Description: Java(TM) Platform SE binary Exit code: 12345 Version: 8.0.920.14 Modules
| |||||||||||||||
| 2448 | ipconfig.exe /all | C:\Windows\system32\ipconfig.exe | — | java.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: IP Configuration Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2640 | "C:\Users\admin\AppData\Local\Temp\myspeedpc.exe" | C:\Users\admin\AppData\Local\Temp\myspeedpc.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3040 | "C:\Users\admin\AppData\Local\Temp\myspeedpc.exe" | C:\Users\admin\AppData\Local\Temp\myspeedpc.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 3160 | "C:\Program Files\MyConnection PC\runfile.exe" -Q* /install | C:\Program Files\MyConnection PC\runfile.exe | — | java.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3212 | "C:\Program Files\MyConnection PC\msclientae.exe" | C:\Program Files\MyConnection PC\msclientae.exe | — | java.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3632 | java -mx256m jexepackboot ER "C:\Users\admin\AppData\Local\Temp\myspeedpc.exe" "C:\Users\admin\AppData\Local\Temp\X430A50" | C:\ProgramData\Oracle\Java\javapath\java.exe | myspeedpc.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: HIGH Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.920.14 Modules
| |||||||||||||||
Total events
249
Read events
239
Write events
10
Delete events
0
Modification events
| (PID) Process: | (3632) java.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: java.exe | |||
| (PID) Process: | (3632) java.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\App Paths\msclientae.exe |
| Operation: | write | Name: | |
Value: C:\Program Files\MyConnection PC\msclientae.exe | |||
| (PID) Process: | (3632) java.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\App Paths\msclientae.exe |
| Operation: | write | Name: | Path |
Value: C:\Program Files\MyConnection PC | |||
| (PID) Process: | (3632) java.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\MyConnection PC |
| Operation: | write | Name: | DisplayName |
Value: MyConnection PC | |||
| (PID) Process: | (3632) java.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\MyConnection PC |
| Operation: | write | Name: | UninstallString |
Value: "C:\Program Files\MyConnection PC\Uninstall.exe" "C:\Program Files\MyConnection PC" | |||
| (PID) Process: | (1472) java.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (1472) java.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (904) java.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: java.exe | |||
Executable files
10
Suspicious files
5
Text files
109
Unknown types
11
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3632 | java.exe | C:\Users\admin\AppData\Local\Temp\X430A50\src\images\appspeed.png | image | |
MD5:— | SHA256:— | |||
| 3632 | java.exe | C:\Users\admin\AppData\Local\Temp\X430A50\install.ini | text | |
MD5:— | SHA256:— | |||
| 3632 | java.exe | C:\Users\admin\AppData\Local\Temp\X430A50\src\images\back.gif | image | |
MD5:— | SHA256:— | |||
| 3632 | java.exe | C:\Users\admin\AppData\Local\Temp\X430A50\MessageBox.class | class | |
MD5:A78FC2F749D70CA7F2EF8664DDEDA18E | SHA256:096B10F1B702895AD69681746F9F5195FBD1E41E8F0C973BCDFAA00B9CED725F | |||
| 3632 | java.exe | C:\Users\admin\AppData\Local\Temp\X430A50\InstallProgram.class | class | |
MD5:DE2285F6AB634A218F84F800745FE976 | SHA256:2551D118B491FF1B7EAD4A5B50BA9226198E188364E4CCDF38DD52112B7DE524 | |||
| 3632 | java.exe | C:\Users\admin\AppData\Local\Temp\X430A50\src\images\bar.gif | image | |
MD5:— | SHA256:— | |||
| 3632 | java.exe | C:\Users\admin\AppData\Local\Temp\X430A50\src\images\bighelp.png | image | |
MD5:— | SHA256:— | |||
| 3632 | java.exe | C:\Users\admin\AppData\Local\Temp\X430A50\packlist.txt | text | |
MD5:— | SHA256:— | |||
| 3632 | java.exe | C:\Users\admin\AppData\Local\Temp\X430A50\src\images\box.gif | image | |
MD5:— | SHA256:— | |||
| 3632 | java.exe | C:\Users\admin\AppData\Local\Temp\X430A50\Win32.class | class | |
MD5:9B299F75002E0026CBA02F210287A8DE | SHA256:6E8A613BE31EADE2EC96CFB34BF766CF79CF15D25191EFD3DCF77445BF144D23 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
28
DNS requests
6
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
904 | java.exe | GET | 400 | 38.100.141.75:80 | http://secure.visualware.com./crm/LiveUpdate?q=sUMQVzV3NqeAnt2gsW41hyAFvY2wEKcUEMh8n6WNRzp1S9MpZEXVPUdUsu613LyHwqUQtNw33eUvbgB1UlyWrt6FUGPMuYYDtk1YsD2VhSG5MK5QZYK3RJ715Oqtgict4H | US | — | — | suspicious |
904 | java.exe | GET | — | 38.100.141.110:80 | http://update.visualware.com/hotlinks/Hotlinks?p=MSC&e=5&b=3461&v=40101&i=0&o=W&t=T&j=o-1.8.0_92 | US | — | — | suspicious |
904 | java.exe | GET | 200 | 38.99.229.74:80 | http://qualitytestord.visualware.com/myspeed/MySpeedServer/mss | US | text | 1.14 Kb | unknown |
904 | java.exe | GET | 200 | 38.100.141.80:80 | http://www.myspeed.com/msservers/msclient-e5-v4.txt?t=1555277172467 | US | text | 1.88 Kb | malicious |
904 | java.exe | GET | 200 | 38.100.141.110:80 | http://update.visualware.com/hotlinks/Hotlinks?p=MSC&e=5&b=3461&v=40101&i=0&o=W&t=T&j=o-1.8.0_92 | US | html | 182 b | suspicious |
904 | java.exe | GET | 200 | 38.99.229.74:80 | http://qualitytestord.visualware.com/myspeed/MySpeedServer/ticket/ra | US | text | 10 b | unknown |
904 | java.exe | GET | 200 | 38.99.229.74:80 | http://qualitytestord.visualware.com/myspeed/MySpeedServer/mss | US | text | 1.14 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
904 | java.exe | 38.100.141.110:80 | update.visualware.com | Cogent Communications | US | suspicious |
904 | java.exe | 38.99.229.74:20001 | qualitytestord.visualware.com | Cogent Communications | US | unknown |
— | — | 38.100.141.110:80 | update.visualware.com | Cogent Communications | US | suspicious |
904 | java.exe | 38.100.141.80:80 | www.myspeed.com | Cogent Communications | US | malicious |
904 | java.exe | 38.100.141.75:80 | secure.visualware.com | Cogent Communications | US | unknown |
904 | java.exe | 38.99.229.74:20000 | qualitytestord.visualware.com | Cogent Communications | US | unknown |
904 | java.exe | 38.99.229.74:80 | qualitytestord.visualware.com | Cogent Communications | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.myspeed.com |
| malicious |
update.visualware.com |
| suspicious |
www.visualware.com |
| malicious |
secure.visualware.com |
| suspicious |
sUMQVzV3NqeAnt2gsW41hyAFvY2wEKcUEMh8n6WNRzp.1S9MpZEXVPUdUsu613LyHwqUQtNw33eUvbgB1UlyWrt.6FUGPMuYYDtk1YsD2VhSG5MK5QZYK3RJ715Oqtgict4H.LiveUpdate.crm.visualware.com |
| unknown |
qualitytestord.visualware.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
904 | java.exe | Generic Protocol Command Decode | SURICATA Applayer Protocol detection skipped |