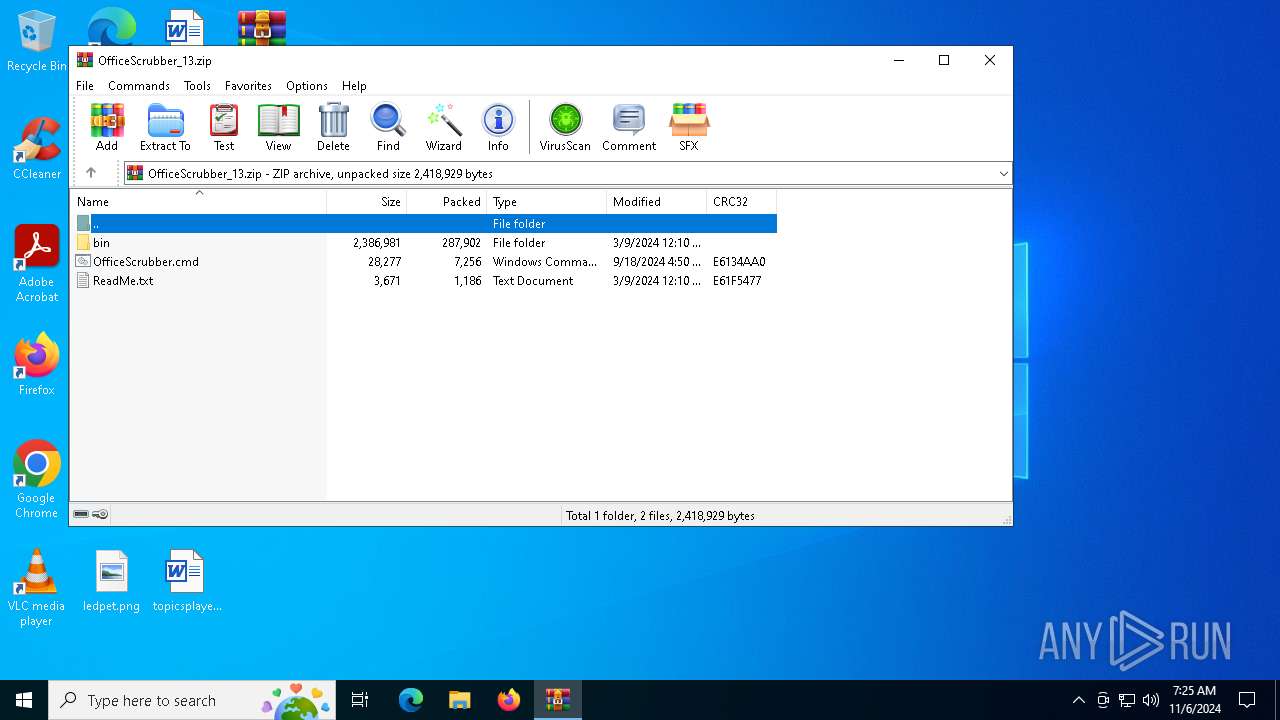
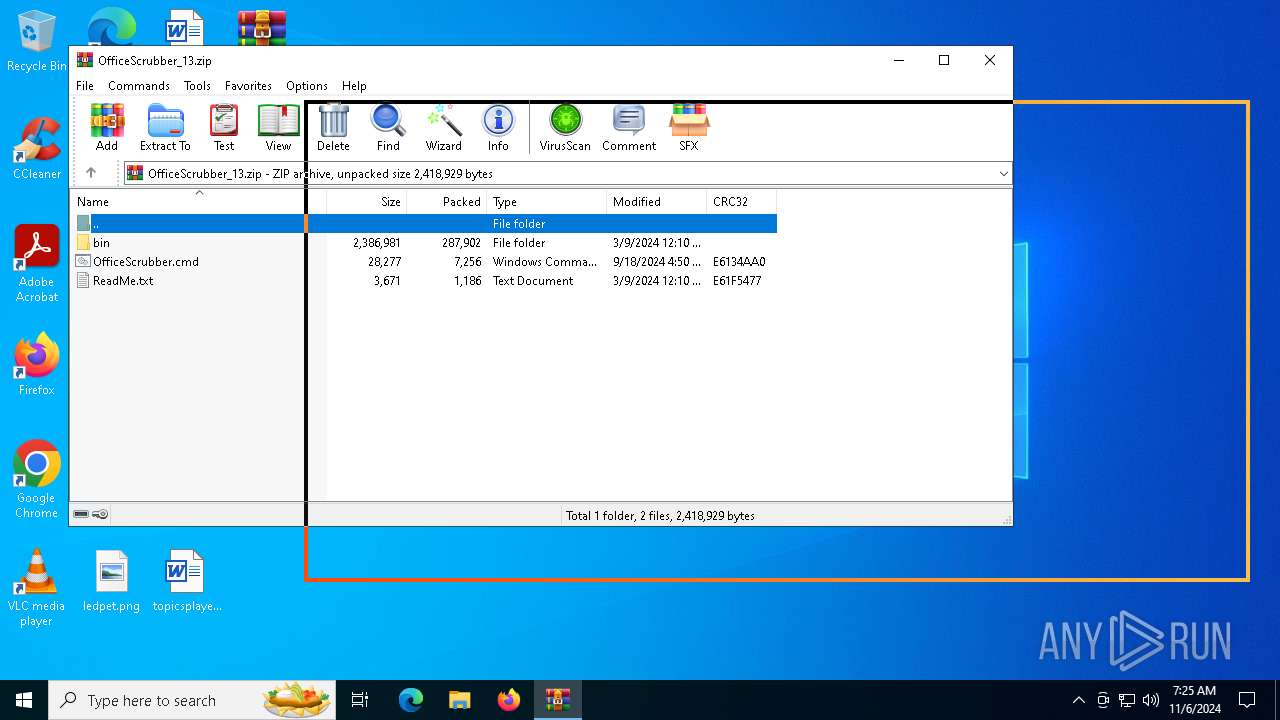
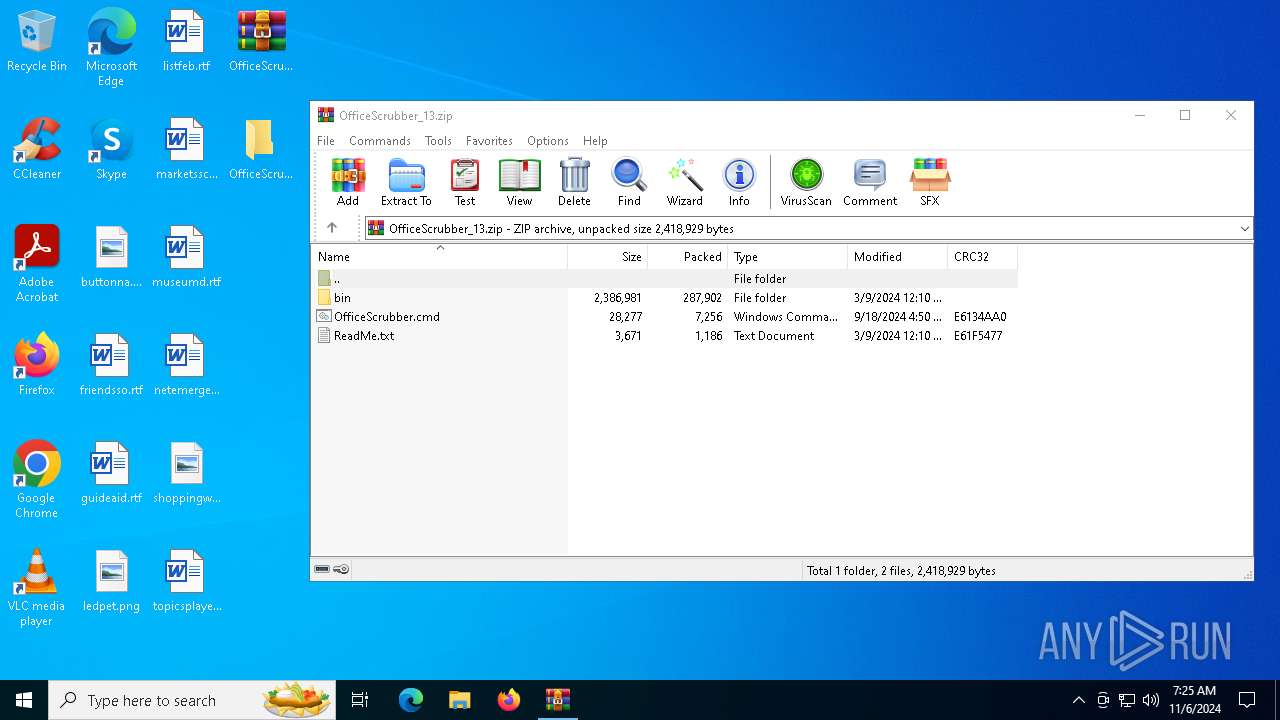
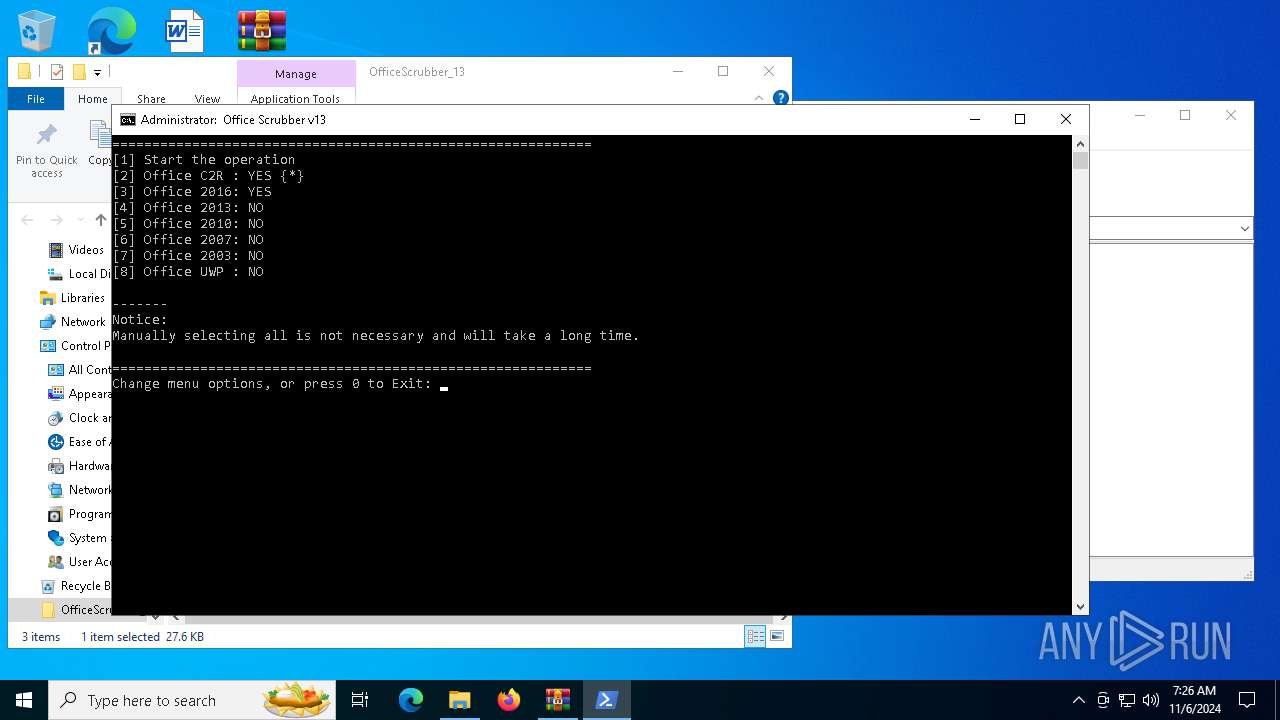
| File name: | OfficeScrubber_13.zip |
| Full analysis: | https://app.any.run/tasks/e723b2b6-2919-4542-9cda-02b4ef481ee9 |
| Verdict: | Malicious activity |
| Analysis date: | November 06, 2024, 07:25:30 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | EBC91F408FCC82C30172082E253B6008 |
| SHA1: | 9856FADEFB06E853D0138D20F804890D7A166B4C |
| SHA256: | 88597450CD5331EF6096EA01CAA7151ABE698148A74B1D660AB089D50F8F216A |
| SSDEEP: | 6144:lFzXT2byGbI9oSusHCu6WkFAgPoWNfXneg81+F3IIr9rcG1pU:l9XqeGbI9oS3O5NfXnegs+1r9AG7U |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6608)
Execute application with conhost.exe as parent process
- powershell.exe (PID: 3004)
Starts NET.EXE for service management
- net.exe (PID: 4956)
- cmd.exe (PID: 1584)
- net.exe (PID: 5168)
- net.exe (PID: 2972)
- net.exe (PID: 6276)
SUSPICIOUS
Starts CMD.EXE for commands execution
- cmd.exe (PID: 1768)
- cmd.exe (PID: 1884)
- powershell.exe (PID: 3004)
- cmd.exe (PID: 1584)
- cscript.exe (PID: 7116)
Application launched itself
- cmd.exe (PID: 1768)
- cmd.exe (PID: 1884)
- cmd.exe (PID: 1584)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 1768)
- cmd.exe (PID: 1884)
- cmd.exe (PID: 1584)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 2280)
- cmd.exe (PID: 6864)
- cmd.exe (PID: 6904)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 1768)
- cmd.exe (PID: 1884)
- conhost.exe (PID: 4816)
- cmd.exe (PID: 1584)
Uses RUNDLL32.EXE to load library
- cscript.exe (PID: 7116)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 1768)
- cmd.exe (PID: 1884)
- conhost.exe (PID: 4816)
- cmd.exe (PID: 1584)
Executes script without checking the security policy
- powershell.exe (PID: 7124)
- powershell.exe (PID: 6604)
- powershell.exe (PID: 3004)
- powershell.exe (PID: 2076)
Executing commands from ".cmd" file
- cscript.exe (PID: 7116)
- powershell.exe (PID: 3004)
Hides command output
- cmd.exe (PID: 5356)
- cmd.exe (PID: 1804)
- cmd.exe (PID: 616)
- cmd.exe (PID: 6952)
- cmd.exe (PID: 6904)
- cmd.exe (PID: 6756)
- cmd.exe (PID: 528)
- cmd.exe (PID: 5532)
- cmd.exe (PID: 4464)
- cmd.exe (PID: 6916)
- cmd.exe (PID: 7080)
- cmd.exe (PID: 4680)
- cmd.exe (PID: 6612)
- cmd.exe (PID: 1084)
- cmd.exe (PID: 2464)
- cmd.exe (PID: 7112)
Starts SC.EXE for service management
- cmd.exe (PID: 1584)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 6916)
- cmd.exe (PID: 1084)
- cmd.exe (PID: 1584)
- cmd.exe (PID: 2464)
- cmd.exe (PID: 7112)
- cmd.exe (PID: 4464)
Get information on the list of running processes
- cmd.exe (PID: 1584)
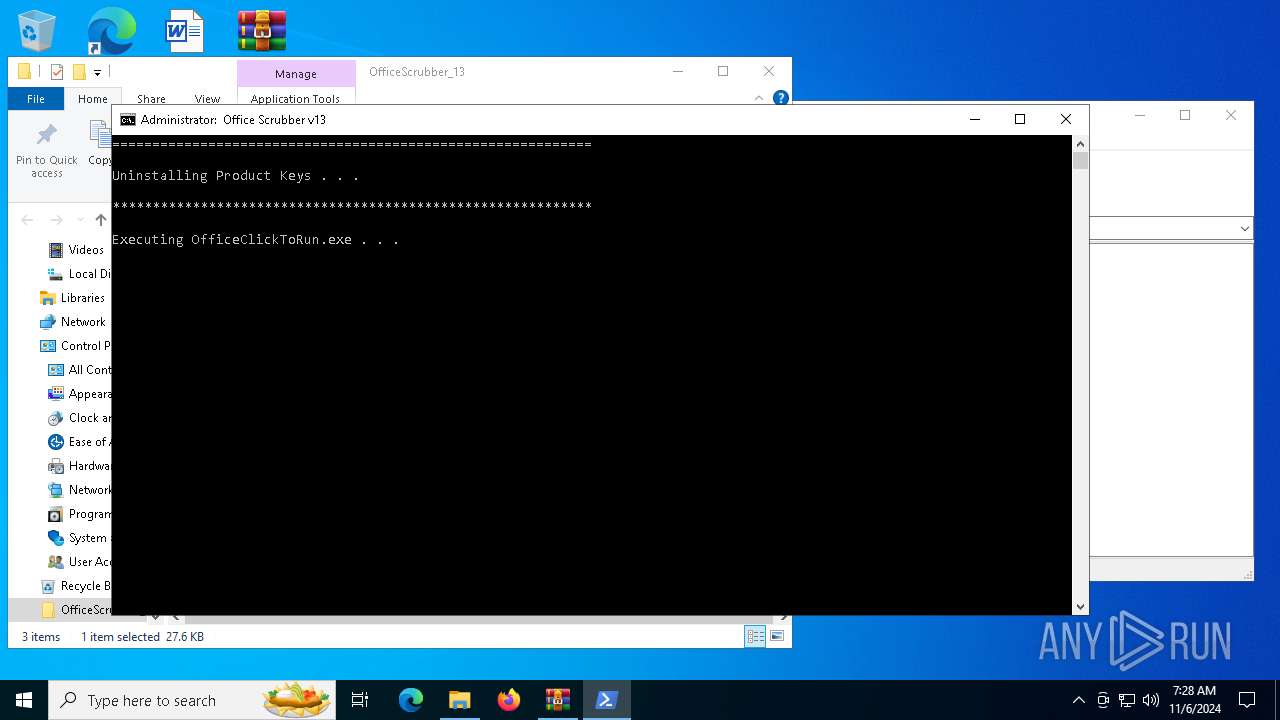
Process drops legitimate windows executable
- OfficeClickToRun.exe (PID: 6540)
The process drops C-runtime libraries
- OfficeClickToRun.exe (PID: 6540)
Executable content was dropped or overwritten
- OfficeClickToRun.exe (PID: 6540)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 1584)
INFO
Manual execution by a user
- cmd.exe (PID: 1768)
- WinRAR.exe (PID: 4448)
Checks operating system version
- cmd.exe (PID: 1768)
- cmd.exe (PID: 1884)
- cmd.exe (PID: 1584)
Executes as Windows Service
- OfficeClickToRun.exe (PID: 6540)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:03:09 15:10:32 |
| ZipCRC: | 0xe61f5477 |
| ZipCompressedSize: | 1186 |
| ZipUncompressedSize: | 3671 |
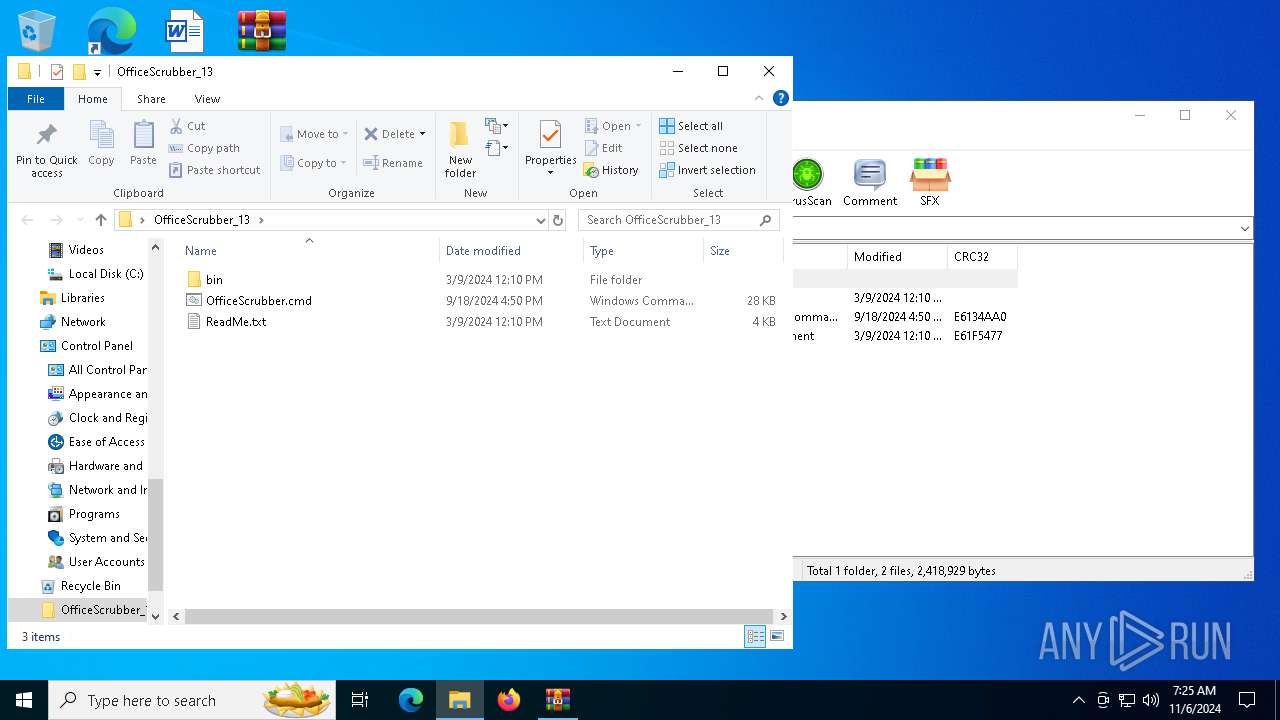
| ZipFileName: | ReadMe.txt |
Total processes
316
Monitored processes
183
Malicious processes
7
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 528 | find /i "Full" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 528 | C:\WINDOWS\system32\cmd.exe /c "reg.exe query HKLM\SOFTWARE\Microsoft\Office\16.0\Common\InstallRoot /v Path" 2>nul | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 616 | C:\WINDOWS\system32\cmd.exe /c "reg.exe query HKLM\SOFTWARE\Wow6432Node\Microsoft\Office\12.0\Common\InstallRoot /v Path" 2>nul | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 696 | C:\WINDOWS\system32\cmd.exe /S /D /c" ver" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 696 | reg.exe query "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\App Paths\msoxmled.exe" | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 696 | reg.exe delete "HKU\S-1-5-20\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SoftwareProtectionPlatform\0ff1ce15-a989-479d-af46-f275c6370663" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 696 | find /i "outlook.exe" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 700 | find /i "graph.exe" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 780 | tasklist /FI "IMAGENAME eq integrator.exe" | C:\Windows\System32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1084 | C:\WINDOWS\system32\cmd.exe /c "wmic path SoftwareLicensingProduct where (Name LIKE 'Office 19%' AND PartialProductKey is not NULL) get ID /VALUE" 2>nul | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
27 189
Read events
26 958
Write events
125
Delete events
106
Modification events
| (PID) Process: | (6608) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6608) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\OfficeScrubber_13.zip | |||
| (PID) Process: | (6608) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6608) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6608) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6608) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4448) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
35
Suspicious files
1 421
Text files
482
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4448 | WinRAR.exe | C:\Users\admin\Desktop\OfficeScrubber_13\bin\OffScrub_O16msi.vbs | text | |
MD5:5BB0D64A99276CEA45BD3E9013024636 | SHA256:A72BB334CFFF2DC236BE4160B495D8F45849D9AD061A17A2396BC6158AC8B0EF | |||
| 6604 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_mnyrrchg.gu1.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4448 | WinRAR.exe | C:\Users\admin\Desktop\OfficeScrubber_13\ReadMe.txt | text | |
MD5:06756744EF6648EF08EE6A3766D3F3F1 | SHA256:7CA226F215D9C1289ECA9217E13A239A2D97D58C527763D1E78830B64A04316D | |||
| 4448 | WinRAR.exe | C:\Users\admin\Desktop\OfficeScrubber_13\bin\OffScrub10.vbs | text | |
MD5:2D12C6C8328D2CF44F8CA3A4EB32AE78 | SHA256:C7319ACD86E6489D44D1723FA9F71F6E76899474D2473B5AB153C01E6C542BE9 | |||
| 3004 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_f5xewirr.ep1.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6540 | OfficeClickToRun.exe | C:\ProgramData\Microsoft\ClickToRun\ProductReleases\A8610DA8-C847-43EC-BFE5-F042E8786B96\x-none.16\stream.x64.x-none.man.dat | — | |
MD5:— | SHA256:— | |||
| 4448 | WinRAR.exe | C:\Users\admin\Desktop\OfficeScrubber_13\bin\OffScrubC2R.vbs | text | |
MD5:DD026195EBF162DAB0C24B25E01B96F1 | SHA256:CD94604F7636085641273CAD146266DFC997724B4FAABE1BE42C21310C040DEC | |||
| 2076 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_cibfpalq.nau.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6604 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_polu0r0h.nrz.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4448 | WinRAR.exe | C:\Users\admin\Desktop\OfficeScrubber_13\bin\OffScrub07.vbs | text | |
MD5:6B9011588E15B67509869001E4C18153 | SHA256:4F1E42CE509FD0108A2BF261C5BC6E04B749DC7431CEF083572623946DBE697B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
35
DNS requests
23
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5488 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7028 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7040 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
3860 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
7040 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6944 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5640 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5488 | MoUsoCoreWorker.exe | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
5488 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4360 | SearchApp.exe | 2.23.209.157:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4020 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |