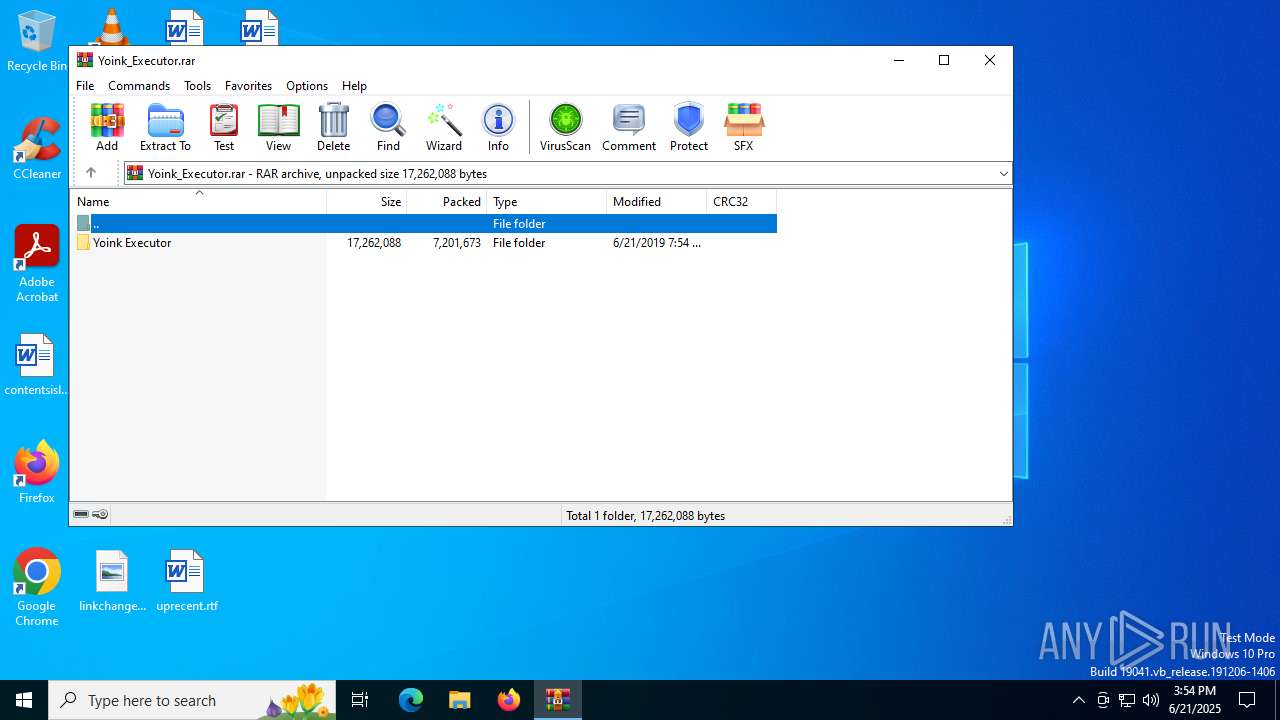
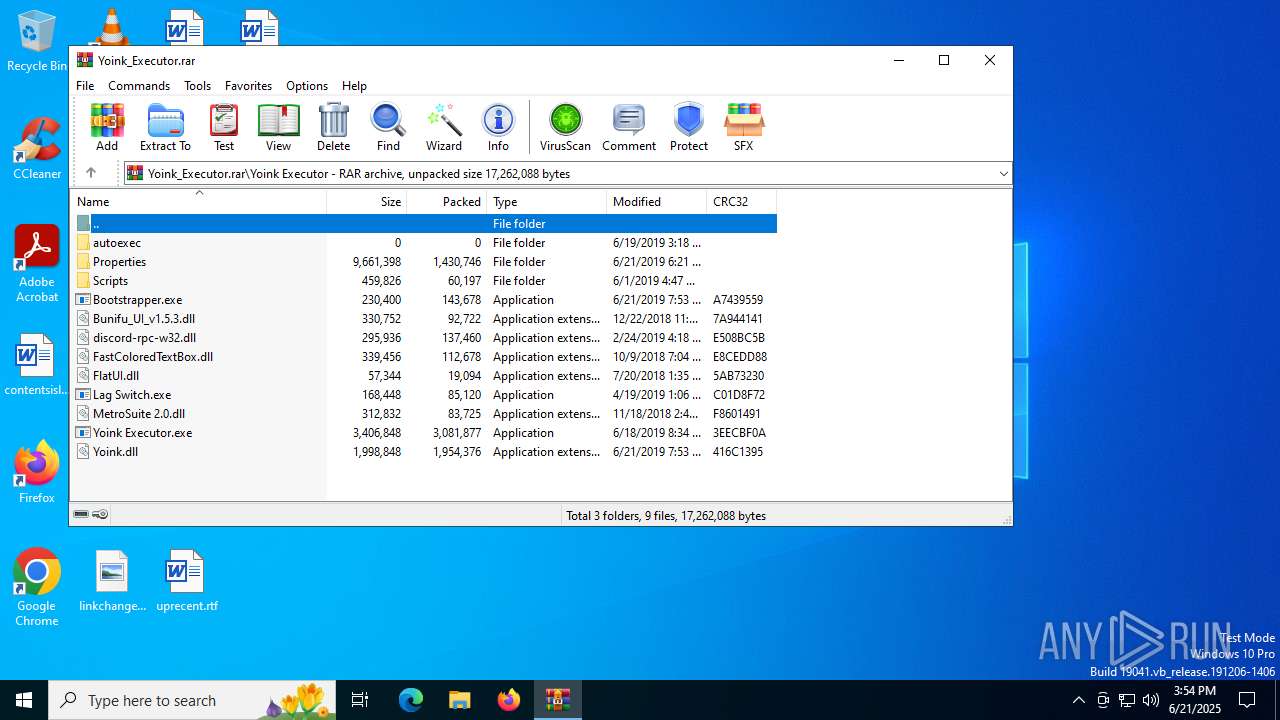
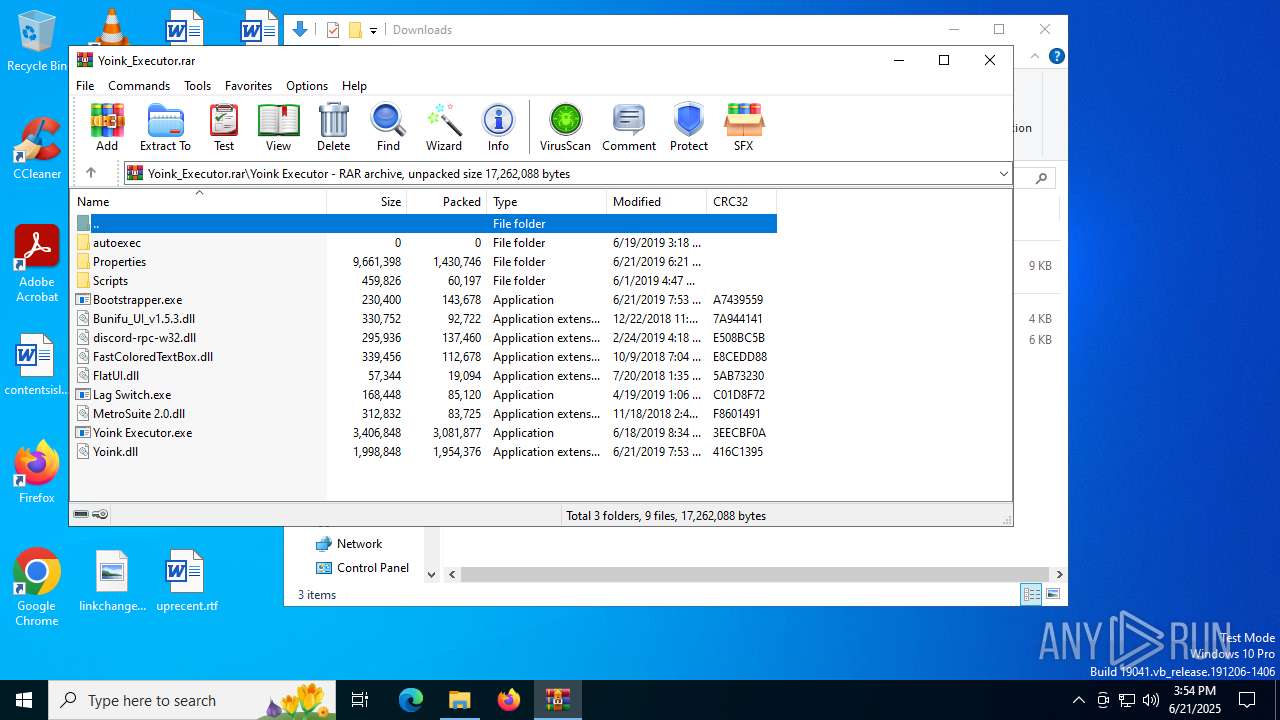
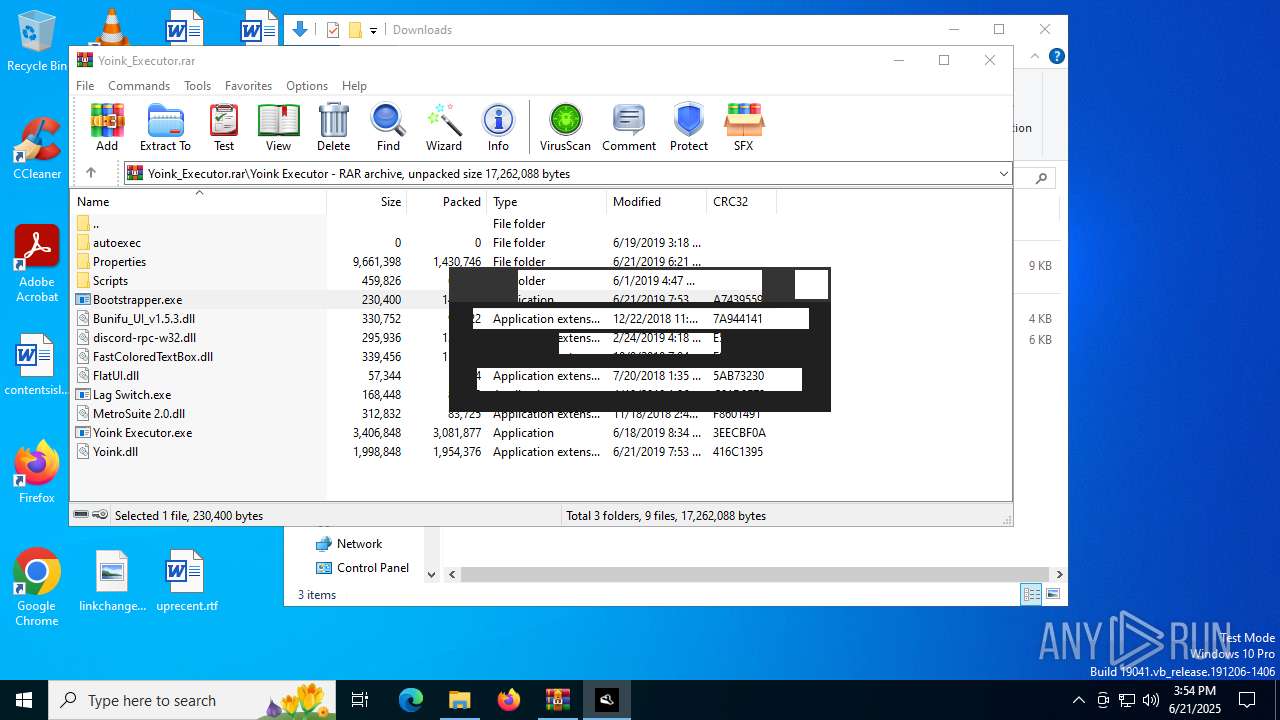
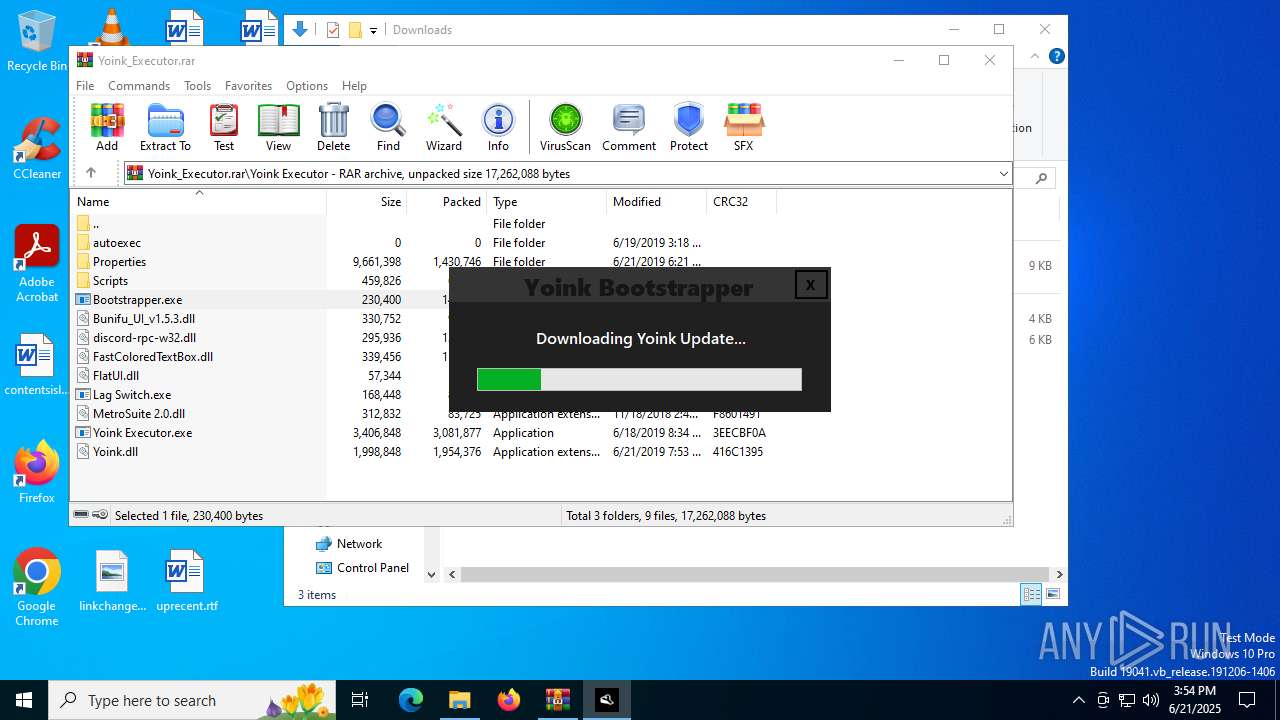
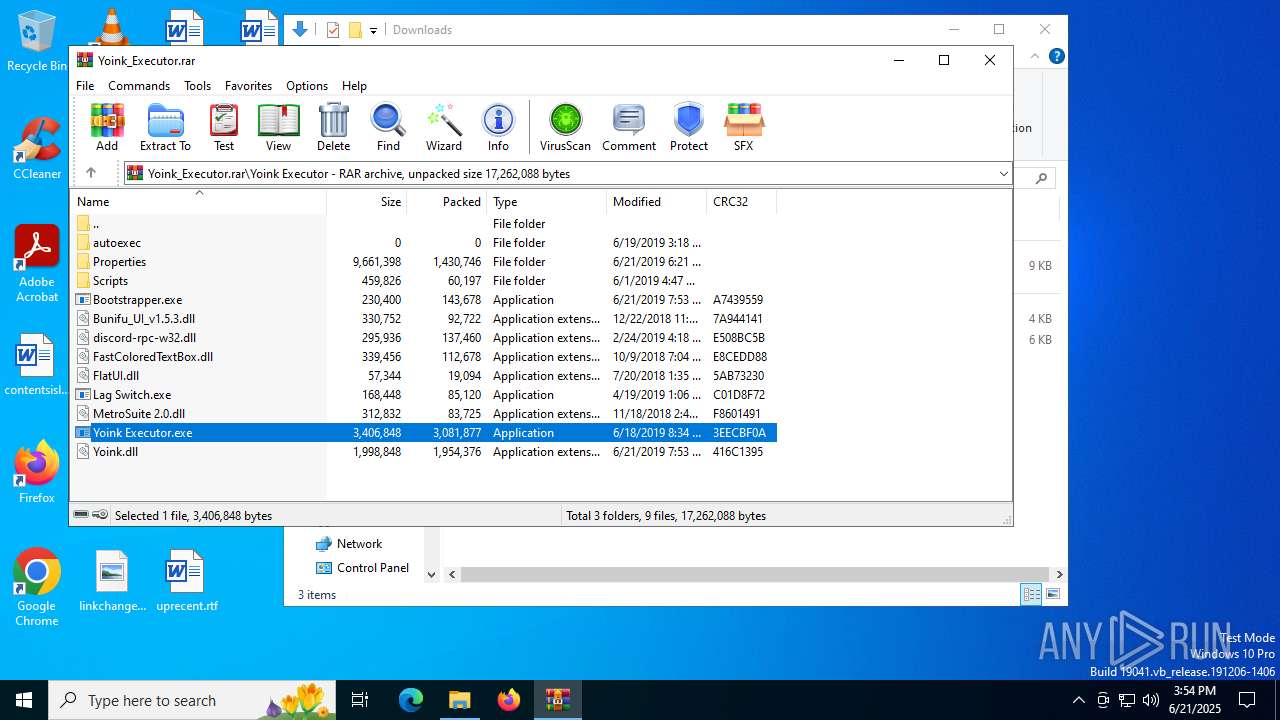
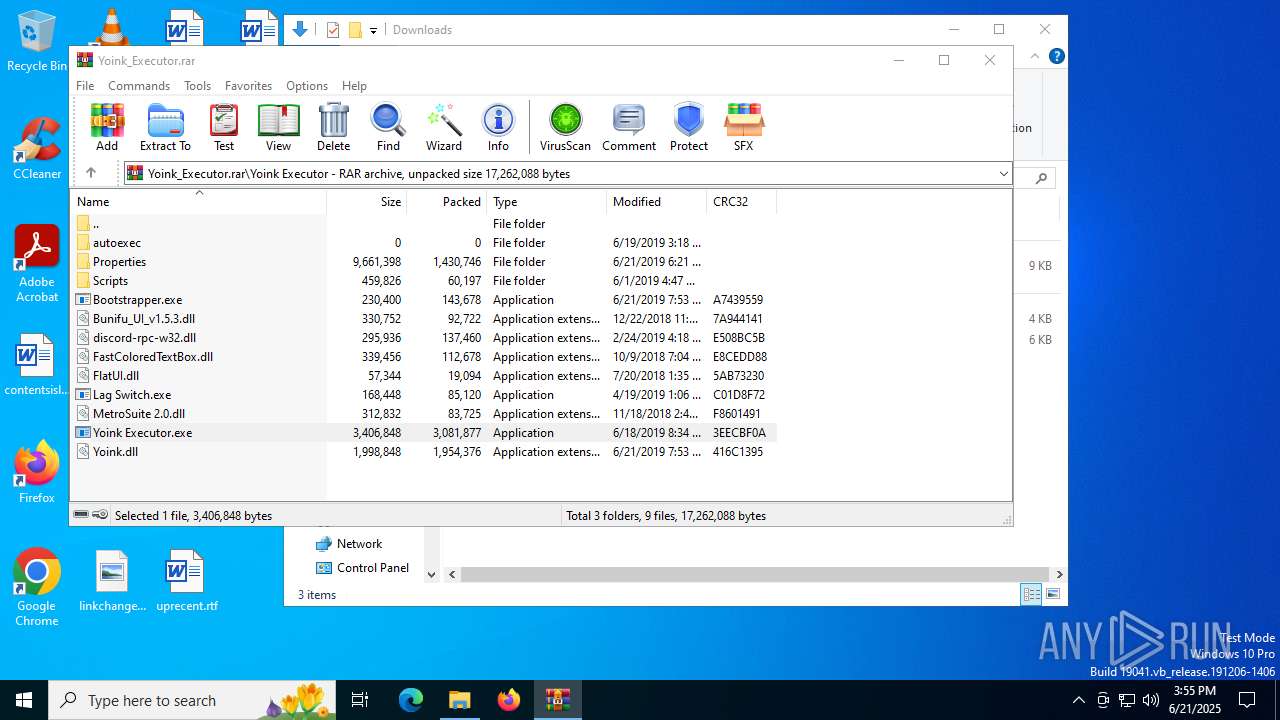
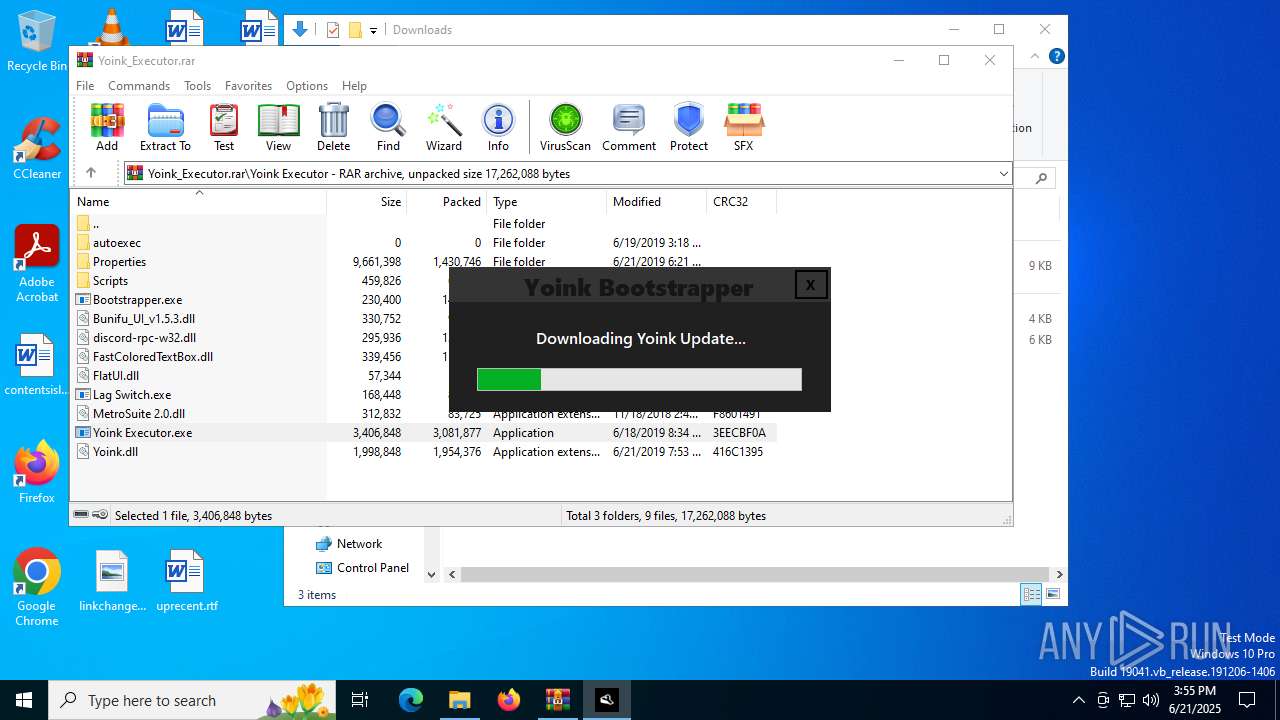
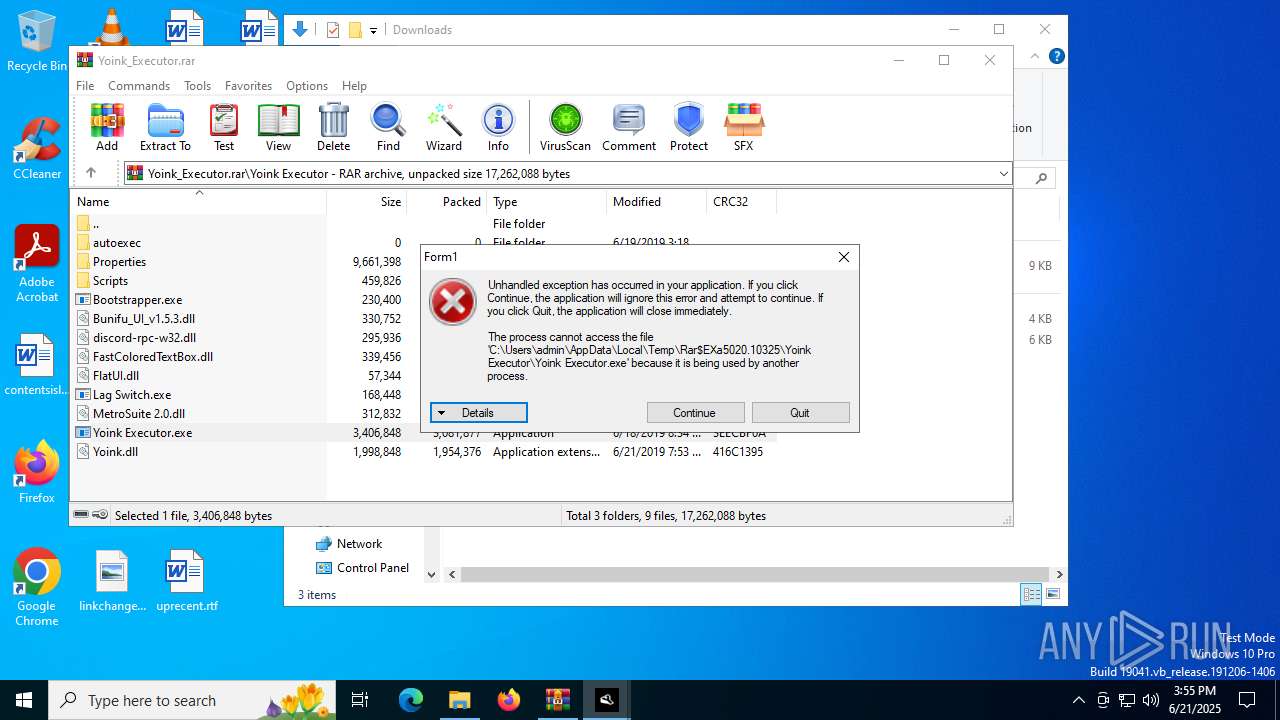
| File name: | Yoink_Executor.rar |
| Full analysis: | https://app.any.run/tasks/8798c4d0-8db8-4643-85b1-830d626591d0 |
| Verdict: | Malicious activity |
| Analysis date: | June 21, 2025, 15:54:18 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | E890C042E642CDC2206C778902598344 |
| SHA1: | 23FA111096F90FA634CD7CA37682BA5FE41F6BC7 |
| SHA256: | 88594C6DBC0B32853BC6E7317680E5CDA939B8BCFEC9604B5B01EB7DC0277778 |
| SSDEEP: | 98304:bJCC8bptfm5/xHJ8QPjV031JcvGCp1XxT/yInxofZzyr16n2AMd2nHQXiRzPfzzl:bcTOUorawd3ObR |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 5020)
SUSPICIOUS
Reads the BIOS version
- Yoink Executor.exe (PID: 6348)
The process checks if it is being run in the virtual environment
- Yoink Executor.exe (PID: 6348)
Reads security settings of Internet Explorer
- Yoink Executor.exe (PID: 6348)
- WinRAR.exe (PID: 5020)
Read disk information to detect sandboxing environments
- Yoink Executor.exe (PID: 6348)
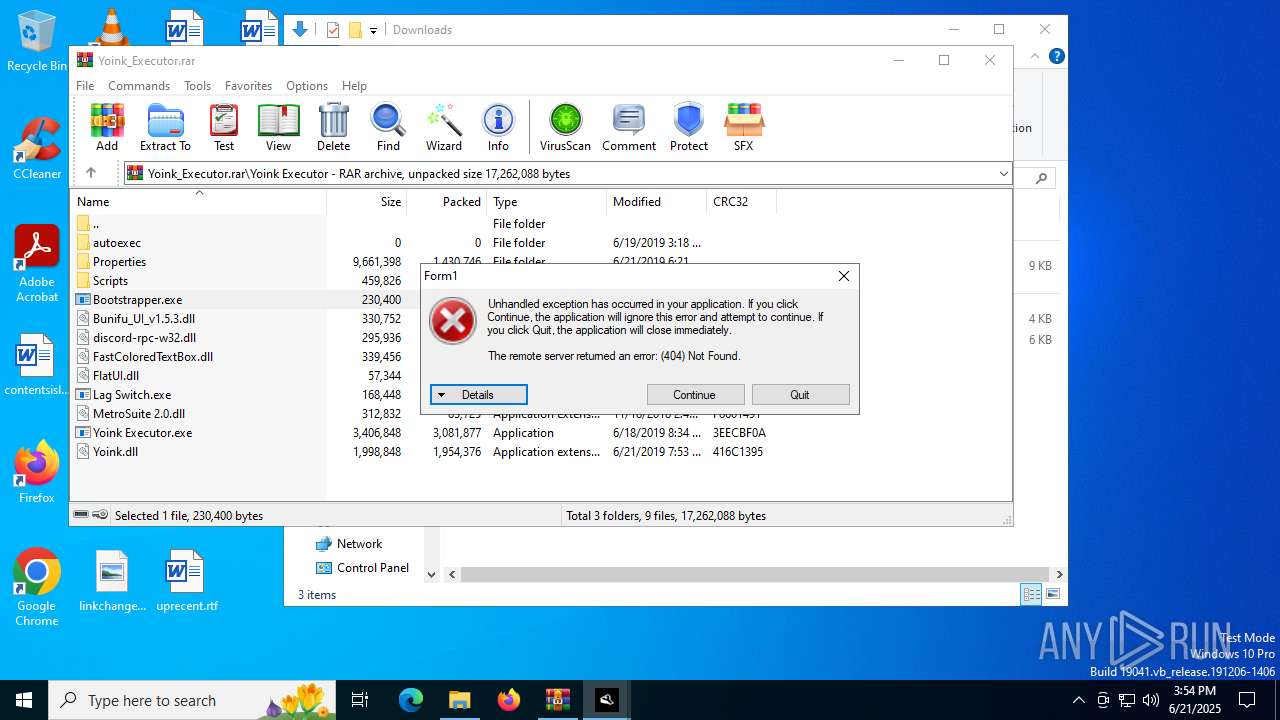
Executes application which crashes
- Yoink Executor.exe (PID: 6348)
Possible usage of Discord/Telegram API has been detected (YARA)
- Yoink Executor.exe (PID: 6348)
INFO
Disables trace logs
- Bootstrapper.exe (PID: 1480)
- Yoink Executor.exe (PID: 6348)
- Bootstrapper.exe (PID: 6840)
Reads the computer name
- Yoink Executor.exe (PID: 6348)
- Bootstrapper.exe (PID: 1480)
- Bootstrapper.exe (PID: 6840)
Checks proxy server information
- Bootstrapper.exe (PID: 1480)
- Yoink Executor.exe (PID: 6348)
- Bootstrapper.exe (PID: 6840)
- WerFault.exe (PID: 6868)
Confuser has been detected (YARA)
- Bootstrapper.exe (PID: 1480)
Reads the machine GUID from the registry
- Yoink Executor.exe (PID: 6348)
- Bootstrapper.exe (PID: 1480)
- Bootstrapper.exe (PID: 6840)
Checks supported languages
- Bootstrapper.exe (PID: 1480)
- Yoink Executor.exe (PID: 6348)
- Bootstrapper.exe (PID: 6840)
Reads the software policy settings
- Yoink Executor.exe (PID: 6348)
- Bootstrapper.exe (PID: 6840)
- WerFault.exe (PID: 6868)
- Bootstrapper.exe (PID: 1480)
Create files in a temporary directory
- Bootstrapper.exe (PID: 1480)
Process checks computer location settings
- Yoink Executor.exe (PID: 6348)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5020)
Creates files or folders in the user directory
- WerFault.exe (PID: 6868)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
ims-api
(PID) Process(6348) Yoink Executor.exe
Discord-Webhook-Tokens (1)574725018164920323/A0THmXBEzl-JiAbL_PcKBeZWKv1TDN5XdCRPRLVRQBsJyBNZYAjNEP57CqBtsabNqdad
Discord-Info-Links
574725018164920323/A0THmXBEzl-JiAbL_PcKBeZWKv1TDN5XdCRPRLVRQBsJyBNZYAjNEP57CqBtsabNqdad
Get Webhook Infohttps://discord.com/api/webhooks/574725018164920323/A0THmXBEzl-JiAbL_PcKBeZWKv1TDN5XdCRPRLVRQBsJyBNZYAjNEP57CqBtsabNqdad
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 143678 |
| UncompressedSize: | 230400 |
| OperatingSystem: | Win32 |
| ArchivedFileName: | Yoink Executor/Bootstrapper.exe |
Total processes
143
Monitored processes
7
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1480 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa5020.8988\Yoink Executor\Bootstrapper.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa5020.8988\Yoink Executor\Bootstrapper.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Yoink Updater Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3148 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3956 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5020 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Yoink_Executor.rar | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6348 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa5020.10325\Yoink Executor\Yoink Executor.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa5020.10325\Yoink Executor\Yoink Executor.exe | WinRAR.exe | ||||||||||||
User: admin Company: Immortal Donkey Integrity Level: MEDIUM Description: YoinkEXE Exit code: 3221226505 Version: 1.0.0.0 Modules
ims-api(PID) Process(6348) Yoink Executor.exe Discord-Webhook-Tokens (1)574725018164920323/A0THmXBEzl-JiAbL_PcKBeZWKv1TDN5XdCRPRLVRQBsJyBNZYAjNEP57CqBtsabNqdad Discord-Info-Links 574725018164920323/A0THmXBEzl-JiAbL_PcKBeZWKv1TDN5XdCRPRLVRQBsJyBNZYAjNEP57CqBtsabNqdad Get Webhook Infohttps://discord.com/api/webhooks/574725018164920323/A0THmXBEzl-JiAbL_PcKBeZWKv1TDN5XdCRPRLVRQBsJyBNZYAjNEP57CqBtsabNqdad | |||||||||||||||
| 6840 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa5020.10325\Yoink Executor\Bootstrapper.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa5020.10325\Yoink Executor\Bootstrapper.exe | Yoink Executor.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Yoink Updater Version: 1.0.0.0 Modules
| |||||||||||||||
| 6868 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 6348 -s 1376 | C:\Windows\SysWOW64\WerFault.exe | Yoink Executor.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
8 419
Read events
8 381
Write events
38
Delete events
0
Modification events
| (PID) Process: | (5020) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5020) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5020) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5020) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Yoink_Executor.rar | |||
| (PID) Process: | (5020) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5020) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5020) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5020) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1480) Bootstrapper.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Bootstrapper_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (1480) Bootstrapper.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Bootstrapper_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
Executable files
18
Suspicious files
124
Text files
44
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5020 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5020.8988\Yoink Executor\FastColoredTextBox.dll | executable | |
MD5:7D315038DA4CB77039DC315C64946E22 | SHA256:777C68C5C47CF91E18583A0FA50B556B1551898A07097F296A0811943A493FA6 | |||
| 5020 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5020.8988\Yoink Executor\Properties\Anti-AFK.txt | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 5020 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5020.8988\Yoink Executor\Properties\Monaco\vs\basic-languages\cpp\cpp.js | binary | |
MD5:0A16509E6CD0155FB622E785CFE976C7 | SHA256:A7C2BEA7CA3D9E203A3A286735945FE010C8F4F8D46620386EE8BEFC6A78B32B | |||
| 5020 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5020.8988\Yoink Executor\MetroSuite 2.0.dll | executable | |
MD5:0D30A398CEC0FF006B6EA2B52D11E744 | SHA256:8604BF2A1FE2E94DC1EA1FBD0CF54E77303493B93994DF48479DC683580AA654 | |||
| 5020 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5020.8988\Yoink Executor\Bootstrapper.exe | executable | |
MD5:37B795C38DB2B45B0F9F2AD4CC6B79CE | SHA256:96143EED230674C732B2DE28420D67C1EB4C22FE728E749C918FDDE3E20055DB | |||
| 5020 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5020.8988\Yoink Executor\Properties\LoadstringConvert.txt | binary | |
MD5:CFCD208495D565EF66E7DFF9F98764DA | SHA256:5FECEB66FFC86F38D952786C6D696C79C2DBC239DD4E91B46729D73A27FB57E9 | |||
| 5020 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5020.8988\Yoink Executor\Properties\Monaco\vs\basic-languages\csp\csp.js | binary | |
MD5:22ADA25D590811DCFF4E5F5D698E583B | SHA256:4B5A5D7D50986B86B00833447E097C0F01A4388CE1765B48E7E371D06E3A4789 | |||
| 5020 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5020.8988\Yoink Executor\Properties\Auto-Inject.txt | binary | |
MD5:CFCD208495D565EF66E7DFF9F98764DA | SHA256:5FECEB66FFC86F38D952786C6D696C79C2DBC239DD4E91B46729D73A27FB57E9 | |||
| 5020 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5020.8988\Yoink Executor\Lag Switch.exe | executable | |
MD5:20551D48E3FC40F396EC3B51DB9B15C5 | SHA256:F0788E17074EA4B30E75AABA15B4BB661B9E9C6D79F963F1AB13B07CC4FAD297 | |||
| 5020 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5020.8988\Yoink Executor\FlatUI.dll | executable | |
MD5:797261F587BB9C6B223B81D31D3B1507 | SHA256:EE5AA955CC297FD7ADBE641EE3A913D08FC0013C239B9710C9C87E10002DB089 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
29
DNS requests
20
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1336 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6868 | WerFault.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5716 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5716 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6868 | WerFault.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6404 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1480 | Bootstrapper.exe | 172.67.25.94:443 | pastebin.com | CLOUDFLARENET | US | whitelisted |
1480 | Bootstrapper.exe | 162.159.130.233:443 | cdn.discordapp.com | CLOUDFLARENET | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
pastebin.com |
| whitelisted |
cdn.discordapp.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Online Pastebin Text Storage |
2200 | svchost.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discordapp .com) |
1480 | Bootstrapper.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |