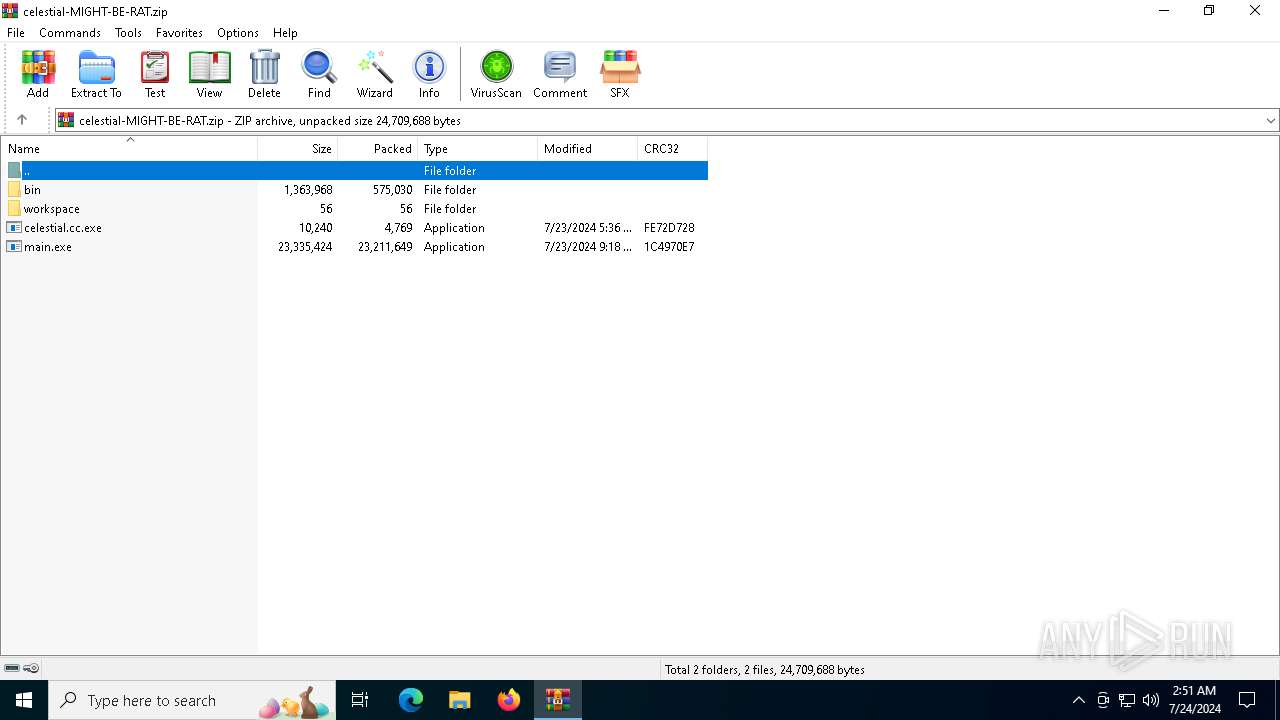
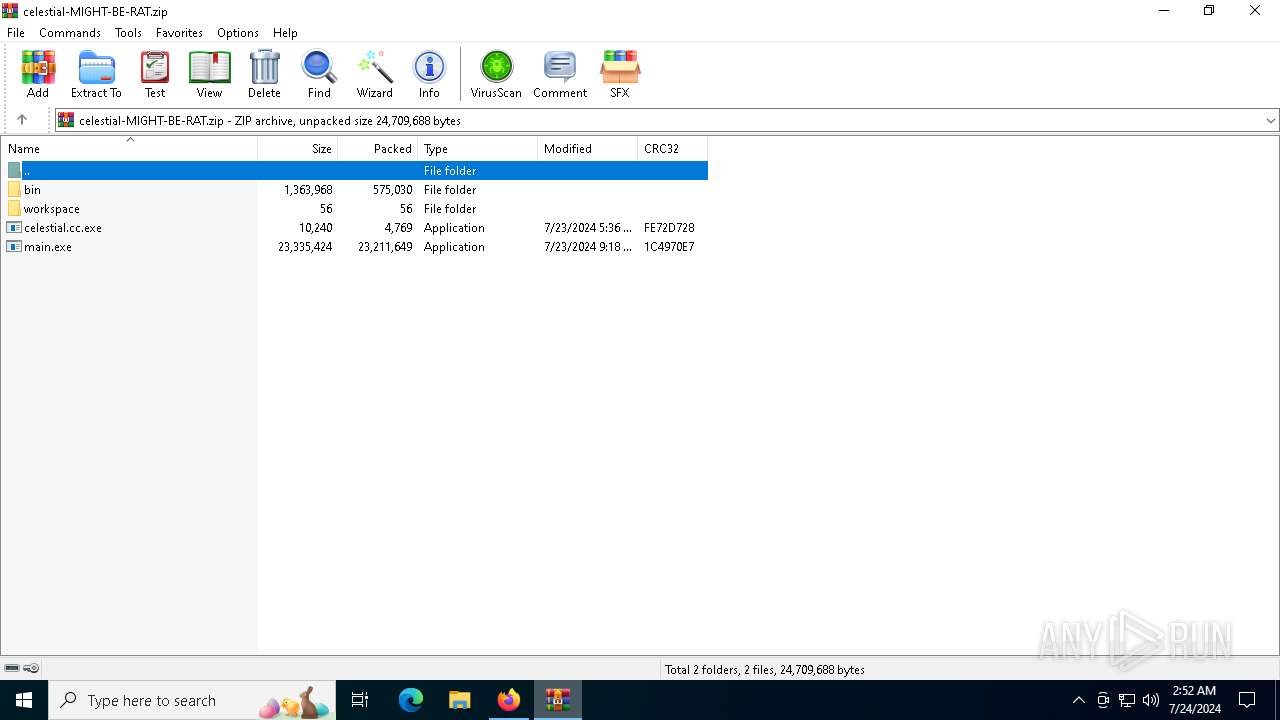
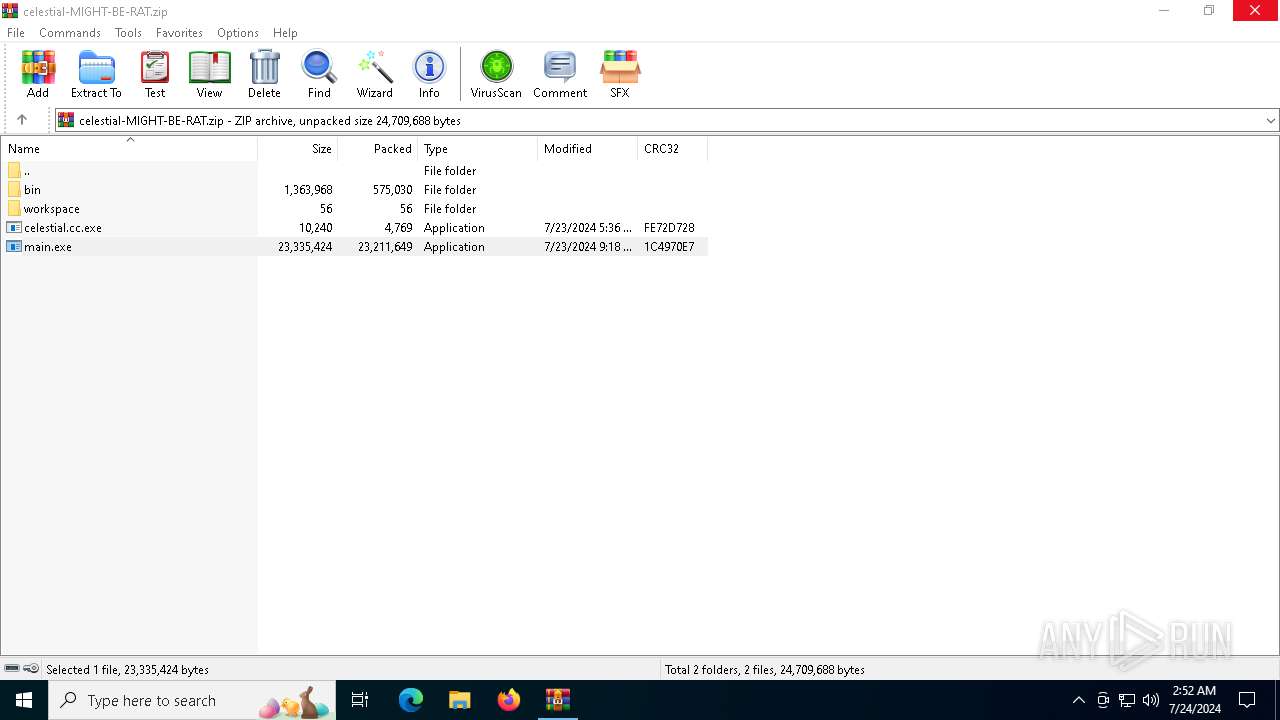
| File name: | celestial-MIGHT-BE-RAT.zip |
| Full analysis: | https://app.any.run/tasks/6a3f3734-374f-4e2f-97b9-7519462b4d0c |
| Verdict: | Malicious activity |
| Analysis date: | July 24, 2024, 02:50:50 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 3685D257BE27D3D80D9D3FEE98DE6C6C |
| SHA1: | D962CFF351DAF596279825FFA2519FBAD61F3113 |
| SHA256: | 8846D51DFD810CC9446305C5890C36662BE01BE72BE4E7FB721E4AFD45F57EF7 |
| SSDEEP: | 196608:I4f+9nncU5Gzm7373dbcFmT2gcx2S2eWnKBqoy2ZenNKk1+G4PJ:BfsncUozYDGzgcx23eWn0qbmBkD4PJ |
MALICIOUS
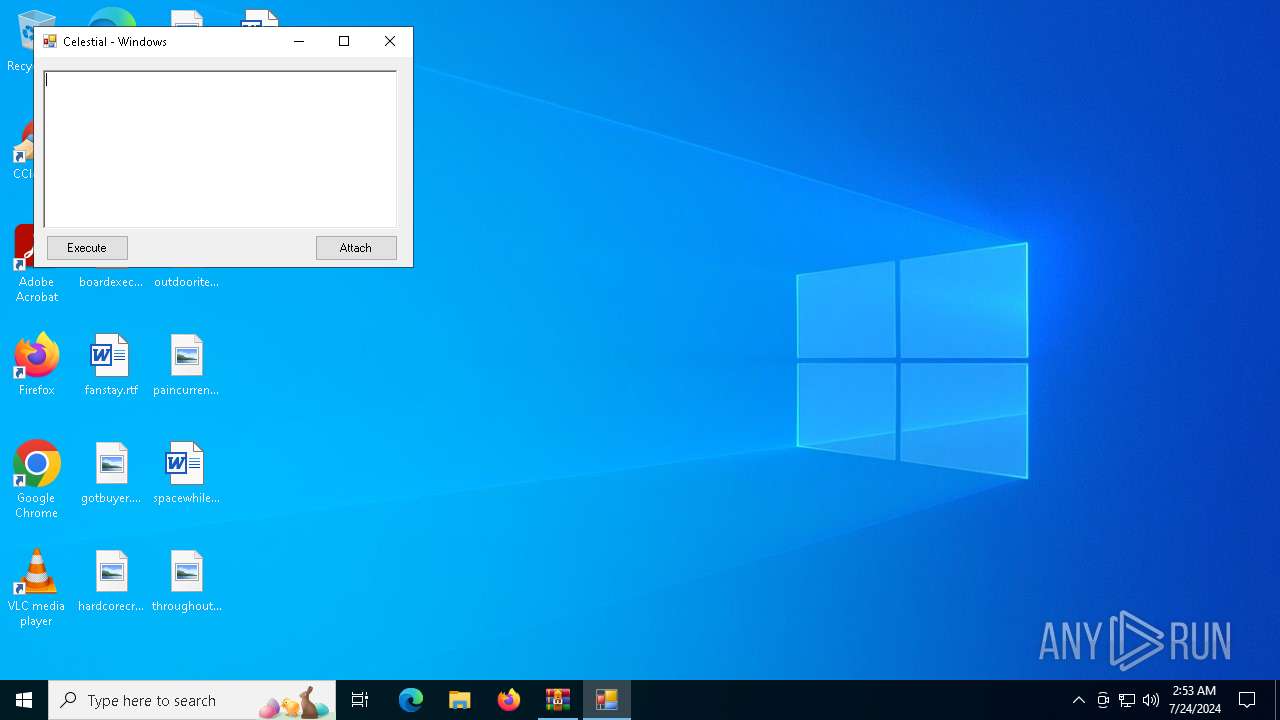
Drops the executable file immediately after the start
- WinRAR.exe (PID: 372)
- main.exe (PID: 1728)
- main.exe (PID: 1696)
DISCORDGRABBER has been detected (YARA)
- main.exe (PID: 1768)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 372)
- main.exe (PID: 1728)
- celestial.cc.exe (PID: 6328)
- main.exe (PID: 1696)
Process drops python dynamic module
- main.exe (PID: 1728)
- main.exe (PID: 1696)
Executable content was dropped or overwritten
- main.exe (PID: 1728)
- main.exe (PID: 1696)
The process drops C-runtime libraries
- main.exe (PID: 1728)
- main.exe (PID: 1696)
Process drops legitimate windows executable
- main.exe (PID: 1728)
- main.exe (PID: 1696)
Loads Python modules
- main.exe (PID: 6036)
- main.exe (PID: 1768)
Reads the date of Windows installation
- celestial.cc.exe (PID: 6328)
INFO
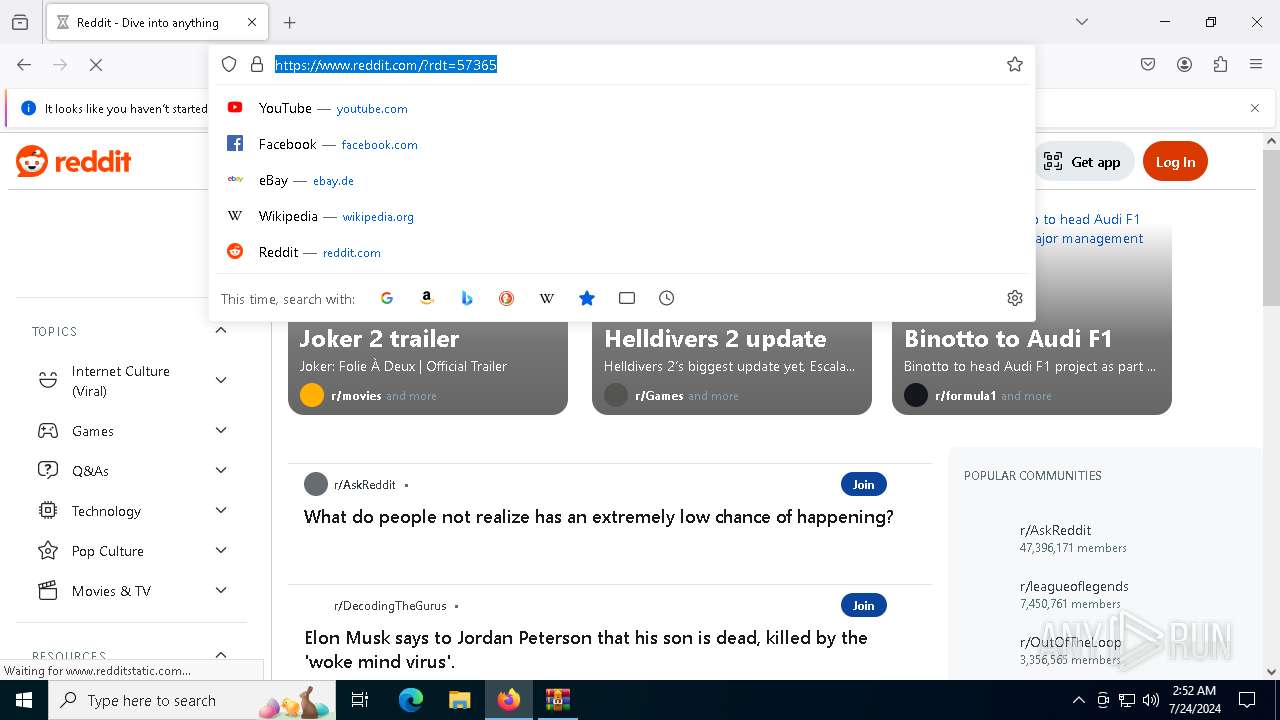
Manual execution by a user
- firefox.exe (PID: 7012)
Reads the software policy settings
- slui.exe (PID: 4688)
Checks proxy server information
- slui.exe (PID: 4688)
Application launched itself
- firefox.exe (PID: 7012)
- firefox.exe (PID: 612)
Reads Microsoft Office registry keys
- firefox.exe (PID: 612)
Reads the computer name
- TextInputHost.exe (PID: 6132)
- main.exe (PID: 6036)
- main.exe (PID: 1728)
- celestial.cc.exe (PID: 6328)
- main.exe (PID: 1696)
- main.exe (PID: 1768)
Checks supported languages
- TextInputHost.exe (PID: 6132)
- main.exe (PID: 1728)
- main.exe (PID: 6036)
- celestial.cc.exe (PID: 6328)
- main.exe (PID: 1696)
- main.exe (PID: 1768)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 372)
Create files in a temporary directory
- main.exe (PID: 1728)
- main.exe (PID: 1696)
Reads the machine GUID from the registry
- celestial.cc.exe (PID: 6328)
Process checks computer location settings
- celestial.cc.exe (PID: 6328)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:05:22 00:10:38 |
| ZipCRC: | 0xee0634e8 |
| ZipCompressedSize: | 575030 |
| ZipUncompressedSize: | 1363968 |
| ZipFileName: | bin/API.dll |
Total processes
146
Monitored processes
25
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 372 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\celestial-MIGHT-BE-RAT.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 612 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 712 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=1896 -parentBuildID 20240213221259 -prefsHandle 1832 -prefMapHandle 1812 -prefsLen 30537 -prefMapSize 244343 -appDir "C:\Program Files\Mozilla Firefox\browser" - {f7da991a-e7ef-4e92-a51b-d42636a29c11} 612 "\\.\pipe\gecko-crash-server-pipe.612" 1d7b2ee7210 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 1 Version: 123.0 Modules
| |||||||||||||||
| 1008 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | main.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1156 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2268 -parentBuildID 20240213221259 -prefsHandle 2260 -prefMapHandle 2248 -prefsLen 30537 -prefMapSize 244343 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {e9b9efad-7187-4fc8-b652-d291a52e19d5} 612 "\\.\pipe\gecko-crash-server-pipe.612" 1d7a6382110 socket | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 1468 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=6440 -childID 8 -isForBrowser -prefsHandle 6324 -prefMapHandle 6296 -prefsLen 31161 -prefMapSize 244343 -jsInitHandle 1436 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {4d238b23-8401-4074-91ac-083c6f763a2b} 612 "\\.\pipe\gecko-crash-server-pipe.612" 1d7bd21e150 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 1696 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa372.38657\main.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa372.38657\main.exe | celestial.cc.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225786 Modules
| |||||||||||||||
| 1728 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa372.36519\main.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa372.36519\main.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1768 | C:\Users\admin\AppData\Local\Temp\Rar$EXa372.38657\main.exe | C:\Users\admin\AppData\Local\Temp\onefile_1696_133662631959990767\main.exe | main.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225786 Modules
| |||||||||||||||
| 3280 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4636 -childID 2 -isForBrowser -prefsHandle 4628 -prefMapHandle 4624 -prefsLen 36263 -prefMapSize 244343 -jsInitHandle 1436 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {c1894eda-bbf2-42a0-b70a-45f9feb805be} 612 "\\.\pipe\gecko-crash-server-pipe.612" 1d7b9fcdbd0 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
Total events
39 060
Read events
39 004
Write events
55
Delete events
1
Modification events
| (PID) Process: | (372) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (372) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (372) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (372) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\celestial-MIGHT-BE-RAT.zip | |||
| (PID) Process: | (372) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (372) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (372) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (372) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7012) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Launcher |
Value: 186A17CD00000000 | |||
| (PID) Process: | (612) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Browser |
Value: 4E4618CD00000000 | |||
Executable files
116
Suspicious files
202
Text files
74
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 612 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 612 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 612 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 612 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\1657114595AmcateirvtiSty.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 612 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\9kie7cg6.default-release\startupCache\urlCache-current.bin | binary | |
MD5:297E88D7CEB26E549254EC875649F4EB | SHA256:8B75D4FB1845BAA06122888D11F6B65E6A36B140C54A72CC13DF390FD7C95702 | |||
| 612 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs.js | text | |
MD5:7A97B8DBC4F98D175F958C00F463A52A | SHA256:92074D2ED1AA1FD621287E35DB9EF1AE3DC04777EFAE5F09E7A3B4534C201548 | |||
| 612 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\datareporting\glean\db\data.safe.bin | dbf | |
MD5:D30F5B10F3D4B3992E4D666F622163F4 | SHA256:2585819A7401A308DA879FA416278E473CEA5F6D0D24C59F514C5A698C61D03A | |||
| 612 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json.tmp | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 612 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\1451318868ntouromlalnodry--epcr.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 612 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3561288849sdhlie.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
373
TCP/UDP connections
164
DNS requests
153
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 101 | 34.107.243.93:443 | https://push.services.mozilla.com/ | unknown | — | — | unknown |
612 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
612 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
— | — | GET | — | 216.58.206.36:443 | https://www.google.com/complete/search?client=firefox&q=ro&channel=fen | unknown | — | — | unknown |
— | — | GET | — | 216.58.206.36:443 | https://www.google.com/complete/search?client=firefox&q=robl&channel=fen | unknown | — | — | unknown |
— | — | GET | — | 216.58.206.36:443 | https://www.google.com/complete/search?client=firefox&q=roblo&channel=fen | unknown | — | — | unknown |
— | — | GET | — | 185.15.59.224:443 | https://www.wikipedia.org/portal/wikipedia.org/assets/js/index-24c3e2ca18.js | unknown | — | — | unknown |
— | — | GET | — | 216.58.206.36:443 | https://www.google.com/complete/search?client=firefox&q=ro&channel=fen | unknown | — | — | unknown |
— | — | GET | — | 216.58.206.36:443 | https://www.google.com/complete/search?client=firefox&q=robl&channel=fen | unknown | — | — | unknown |
— | — | POST | 401 | 4.208.221.206:443 | https://licensing.mp.microsoft.com/v7.0/licenses/content | unknown | binary | 340 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6012 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 239.255.255.250:1900 | — | — | — | whitelisted |
4424 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3648 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.23.209.140:443 | — | Akamai International B.V. | GB | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4204 | svchost.exe | 4.209.33.156:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
3648 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5668 | slui.exe | 20.83.72.98:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
spocs.getpocket.com |
| whitelisted |
prod.ads.prod.webservices.mozgcp.net |
| unknown |
content-signature-2.cdn.mozilla.net |
| whitelisted |
prod.content-signature-chains.prod.webservices.mozgcp.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Generic Protocol Command Decode | SURICATA HTTP Request unrecognized authorization method |