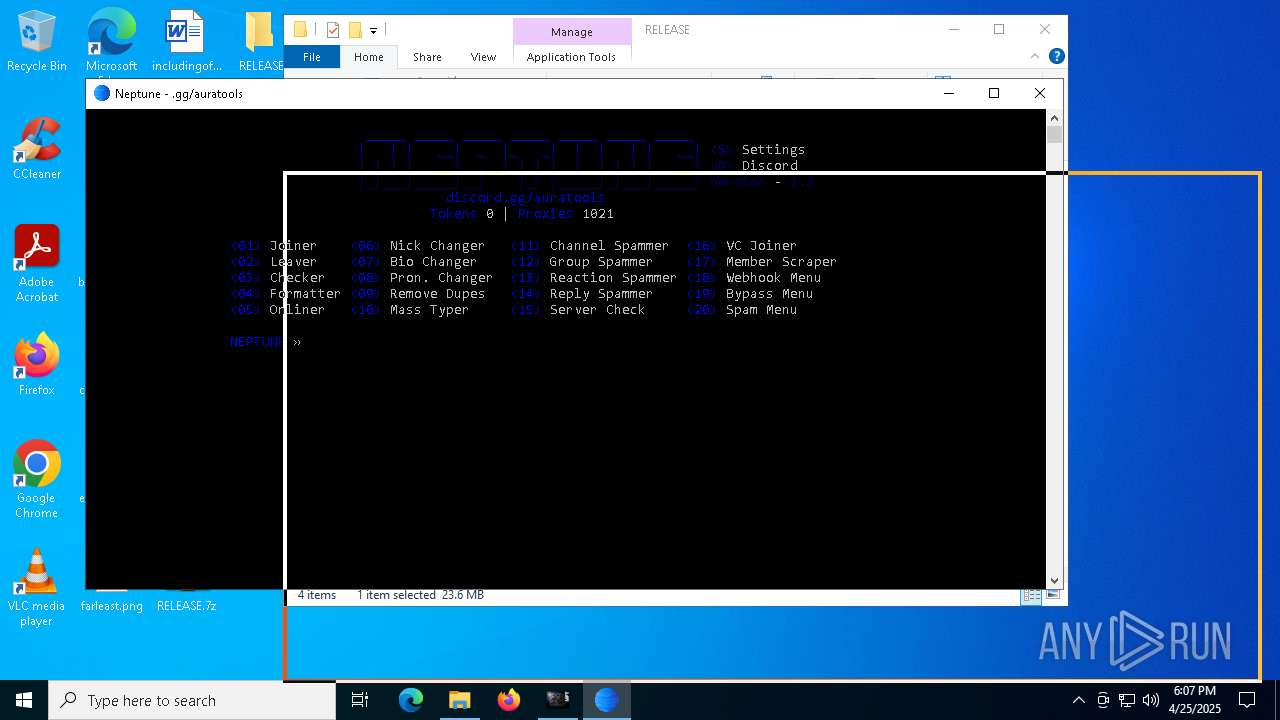
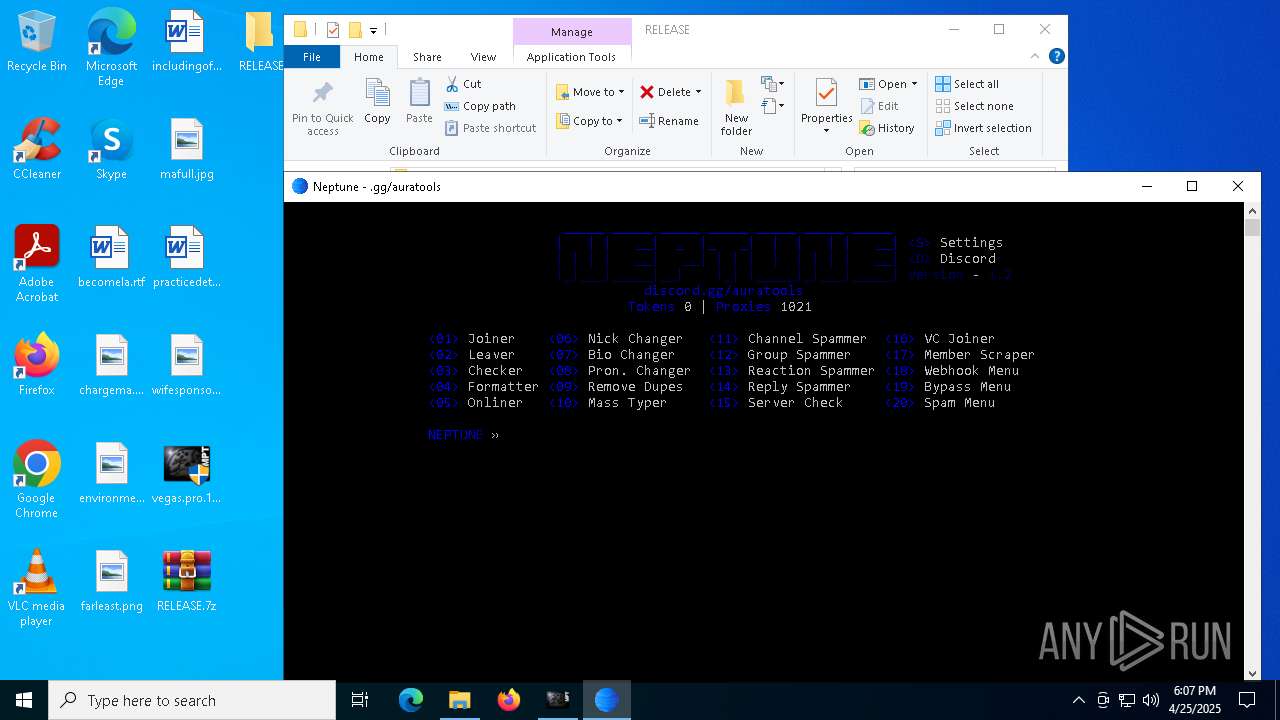
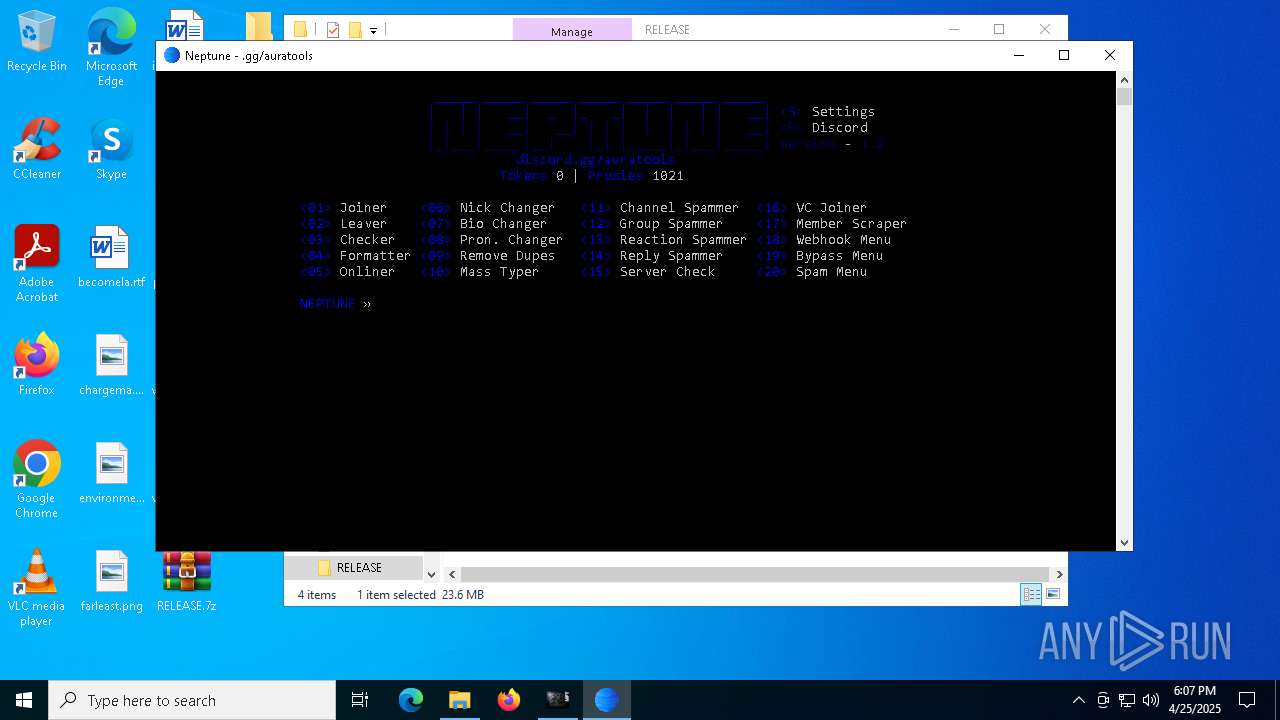
| File name: | vegas.pro.15.0.0.x.[x64]-MPT.exe |
| Full analysis: | https://app.any.run/tasks/e9125b12-9a18-4675-a762-58100c0e1031 |
| Verdict: | Malicious activity |
| Analysis date: | April 25, 2025, 18:05:12 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | 1102BFADE45BB103286FCDB4C8582AB3 |
| SHA1: | 23CBAB1C8D3A1C3D4B6F2DF176270609E2C00136 |
| SHA256: | 88178AAF93D24FAF7EFBD1CBCDA102FF69B48181870588AB2E5F3223A5840A3B |
| SSDEEP: | 6144:mK38ynuNyFaIyV8/S99R1/z2yOgSVvxAsl9QFHheDF0Ai5CLi:mK38ynvFaI2f993ayOgSVvWsl9wHc0t |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- vegas.pro.15.0.0.x.[x64]-MPT.exe (PID: 7668)
- neptune.exe (PID: 660)
There is functionality for taking screenshot (YARA)
- vegas.pro.15.0.0.x.[x64]-MPT.exe (PID: 7668)
The process drops C-runtime libraries
- neptune.exe (PID: 660)
Process drops legitimate windows executable
- neptune.exe (PID: 660)
Process drops python dynamic module
- neptune.exe (PID: 660)
Loads Python modules
- neptune.exe (PID: 1184)
Starts CMD.EXE for commands execution
- neptune.exe (PID: 1184)
Uses WMIC.EXE to obtain Windows Installer data
- neptune.exe (PID: 1184)
Accesses product unique identifier via WMI (SCRIPT)
- WMIC.exe (PID: 1760)
Reads security settings of Internet Explorer
- neptune.exe (PID: 660)
INFO
The sample compiled with english language support
- vegas.pro.15.0.0.x.[x64]-MPT.exe (PID: 7668)
- neptune.exe (PID: 660)
Create files in a temporary directory
- vegas.pro.15.0.0.x.[x64]-MPT.exe (PID: 7668)
- neptune.exe (PID: 660)
Checks supported languages
- vegas.pro.15.0.0.x.[x64]-MPT.exe (PID: 7668)
- neptune.exe (PID: 660)
- neptune.exe (PID: 1184)
Reads the computer name
- vegas.pro.15.0.0.x.[x64]-MPT.exe (PID: 7668)
- neptune.exe (PID: 660)
- neptune.exe (PID: 1184)
UPX packer has been detected
- vegas.pro.15.0.0.x.[x64]-MPT.exe (PID: 7668)
Reads the software policy settings
- slui.exe (PID: 7800)
- neptune.exe (PID: 1184)
- slui.exe (PID: 7232)
Manual execution by a user
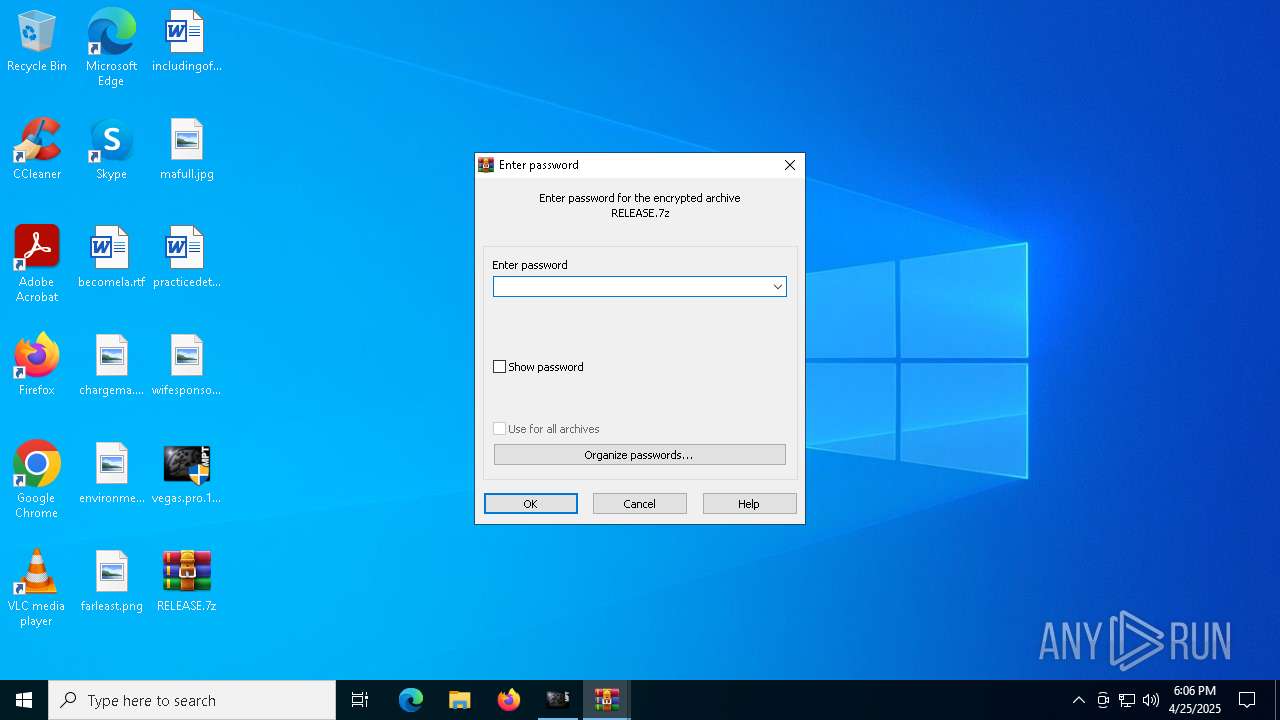
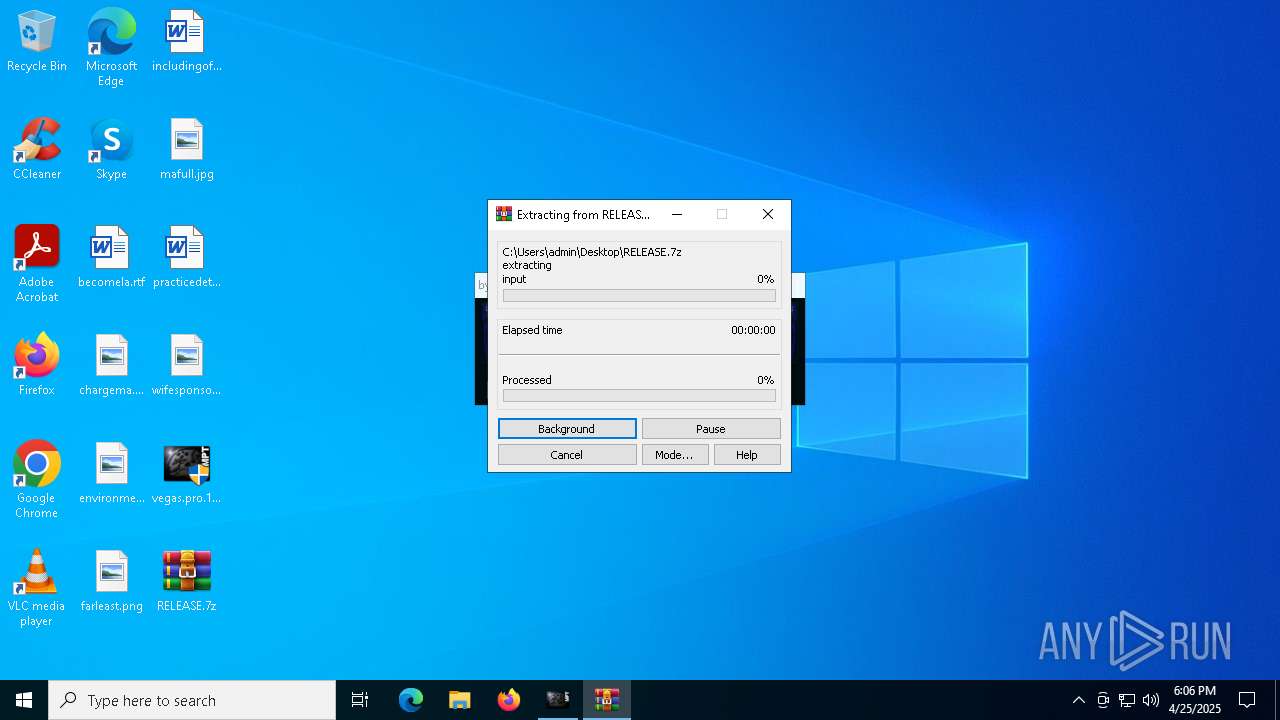
- WinRAR.exe (PID: 5364)
- neptune.exe (PID: 660)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5364)
Checks proxy server information
- neptune.exe (PID: 1184)
- slui.exe (PID: 7232)
Reads the machine GUID from the registry
- neptune.exe (PID: 1184)
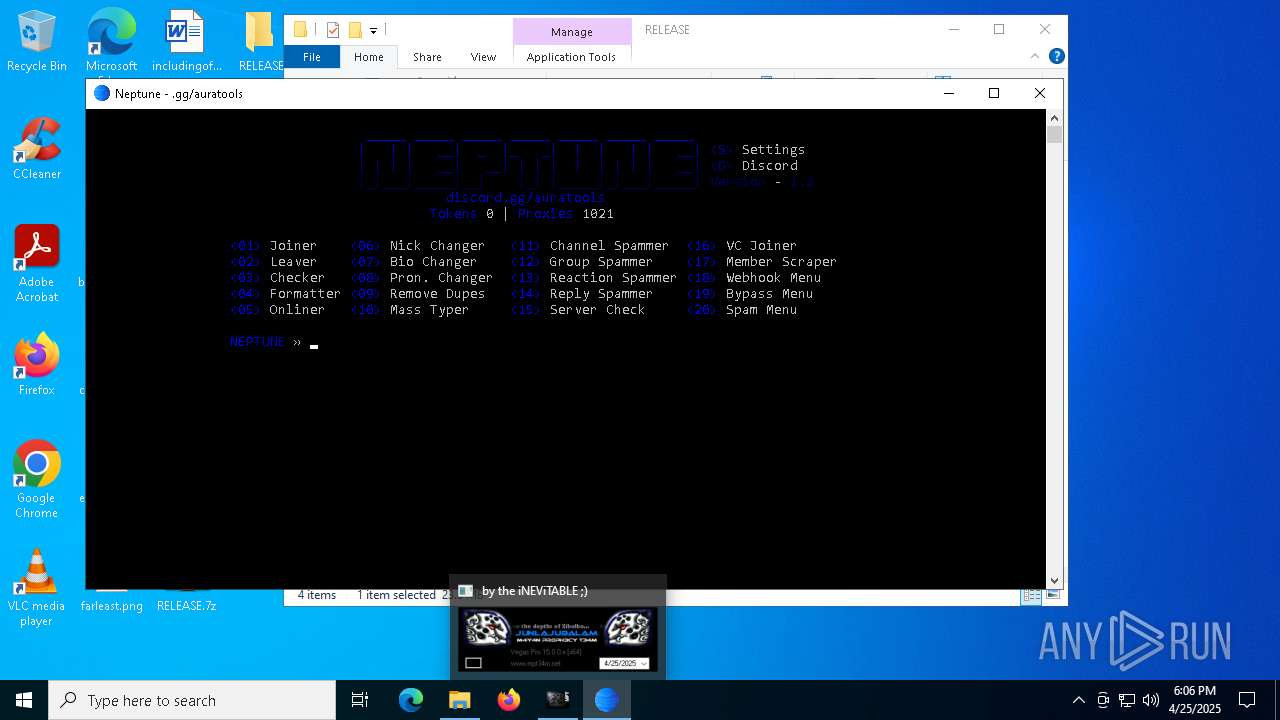
Detects GO elliptic curve encryption (YARA)
- neptune.exe (PID: 1184)
Application based on Golang
- neptune.exe (PID: 1184)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 1760)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2012:12:21 20:59:46+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 10 |
| CodeSize: | 512 |
| InitializedDataSize: | 221184 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x102b |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
Total processes
150
Monitored processes
16
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 660 | "C:\Users\admin\Desktop\RELEASE\neptune.exe" | C:\Users\admin\Desktop\RELEASE\neptune.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225786 Modules
| |||||||||||||||
| 1184 | C:\Users\admin\Desktop\RELEASE\neptune.exe | C:\Users\admin\AppData\Local\Temp\onefile_660_133900779982269658\neptune.exe | neptune.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225786 Modules
| |||||||||||||||
| 1760 | wmic csproduct get uuid | C:\Windows\System32\wbem\WMIC.exe | — | neptune.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2316 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | neptune.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3888 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | neptune.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5364 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\RELEASE.7z" C:\Users\admin\Desktop\RELEASE\ | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 6028 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | neptune.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6404 | C:\WINDOWS\system32\cmd.exe /c | C:\Windows\System32\cmd.exe | — | neptune.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7052 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7184 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | neptune.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
6 684
Read events
6 679
Write events
5
Delete events
0
Modification events
| (PID) Process: | (5364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (5364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5364) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
47
Suspicious files
599
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7668 | vegas.pro.15.0.0.x.[x64]-MPT.exe | C:\Users\admin\AppData\Local\Temp\dup2patcher.dll | executable | |
MD5:9171881DBBE121EE55826166AECAE178 | SHA256:690BD758B01B4F21723C915EF0846A3EFEE61161B8B8A2CF5137FECF099E887D | |||
| 7668 | vegas.pro.15.0.0.x.[x64]-MPT.exe | C:\Users\admin\AppData\Local\Temp\Berlin Sans FB.TTF | binary | |
MD5:FE2027C27B6A24505F548C6FD2E1076D | SHA256:0B6044C72E67AAAE9C2AE3C8B4BB06D066FDBC02779C68E3883984ACBBE24CB8 | |||
| 7668 | vegas.pro.15.0.0.x.[x64]-MPT.exe | C:\Users\admin\AppData\Local\Temp\7CEB9B2A0E395BD64E74381485A106AF.dll | executable | |
MD5:5AFB011D9DB047BB0400C5C5CA2E450B | SHA256:125FC74E03435B3E0EDE0FF523D625D9C1FBB299286E9E2DBD1442E506150DA6 | |||
| 5364 | WinRAR.exe | C:\Users\admin\Desktop\RELEASE\config.json | binary | |
MD5:976ED8151A0F5C43F6808365FFD9776F | SHA256:1AB748227A217166648411E814972BE88C2FC6C884ECD4EFF315810B891C4B70 | |||
| 5364 | WinRAR.exe | C:\Users\admin\Desktop\RELEASE\input\proxies.txt | text | |
MD5:B24BDAE9FAE4C459453DE4D5DC00B157 | SHA256:5CC540A7F0F5EF70B462E2E2194087A7EFC094303697E76ED32D30B2262CE716 | |||
| 660 | neptune.exe | C:\Users\admin\AppData\Local\Temp\onefile_660_133900779982269658\_cffi_backend.pyd | executable | |
MD5:5CBA92E7C00D09A55F5CBADC8D16CD26 | SHA256:0E3D149B91FC7DC3367AB94620A5E13AF6E419F423B31D4800C381468CB8AD85 | |||
| 660 | neptune.exe | C:\Users\admin\AppData\Local\Temp\onefile_660_133900779982269658\_queue.pyd | executable | |
MD5:955B197C38EA5BD537CE9C7CB2109802 | SHA256:73CADE82EE139459FE5841E5631274FC9CAF7F579418B613F278125435653539 | |||
| 660 | neptune.exe | C:\Users\admin\AppData\Local\Temp\onefile_660_133900779982269658\neptune.exe | executable | |
MD5:E8F868B767C0A01148454113A421344A | SHA256:7711CA897390AAF08919061DC5A920D810822423F3D3B0A302AF4ED6E102E780 | |||
| 660 | neptune.exe | C:\Users\admin\AppData\Local\Temp\onefile_660_133900779982269658\_bz2.pyd | executable | |
MD5:C17DCB7FC227601471A641EC90E6237F | SHA256:55894B2B98D01F37B9A8CF4DAF926D0161FF23C2FB31C56F9DBBAC3A61932712 | |||
| 660 | neptune.exe | C:\Users\admin\AppData\Local\Temp\onefile_660_133900779982269658\_brotli.pyd | executable | |
MD5:5ED46A7126DBDB70F3C60530E35BA035 | SHA256:67DFA82DCAED04ED3F358D84B18D1375D59126161DE92E00164D36087B179D4D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
40
DNS requests
25
Threats
11
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4008 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4008 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
736 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
736 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
— | — | 23.219.150.101:80 | www.microsoft.com | AKAMAI-AS | CL | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6544 | svchost.exe | 40.126.32.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
2112 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
1184 | neptune.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
1184 | neptune.exe | Misc activity | ET INFO Observed Discord Service Domain (discord .com) in TLS SNI |
1184 | neptune.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
2196 | svchost.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
1184 | neptune.exe | Misc activity | ET INFO Observed Discord Service Domain (discord .com) in TLS SNI |
1184 | neptune.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
2196 | svchost.exe | Misc activity | ET INFO Discord Chat Service Domain in DNS Lookup (discord .com) |
1184 | neptune.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
1184 | neptune.exe | Misc activity | ET INFO Observed Discord Service Domain (discord .com) in TLS SNI |