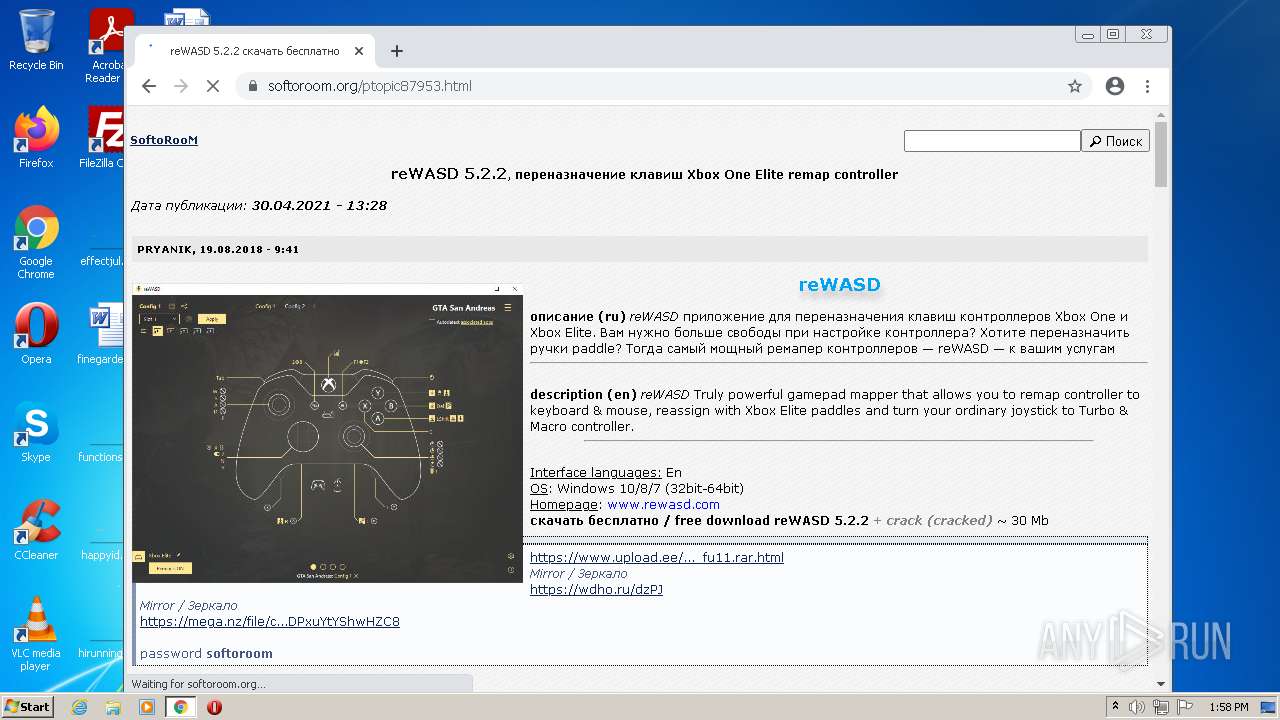
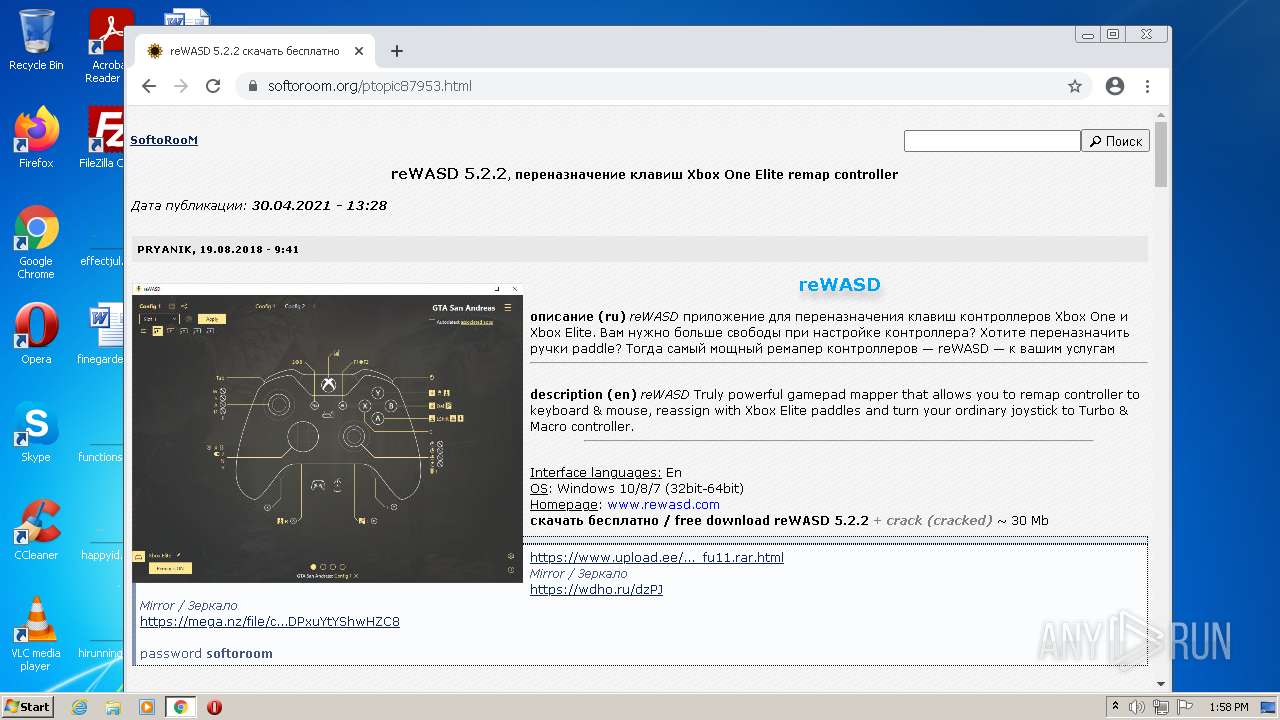
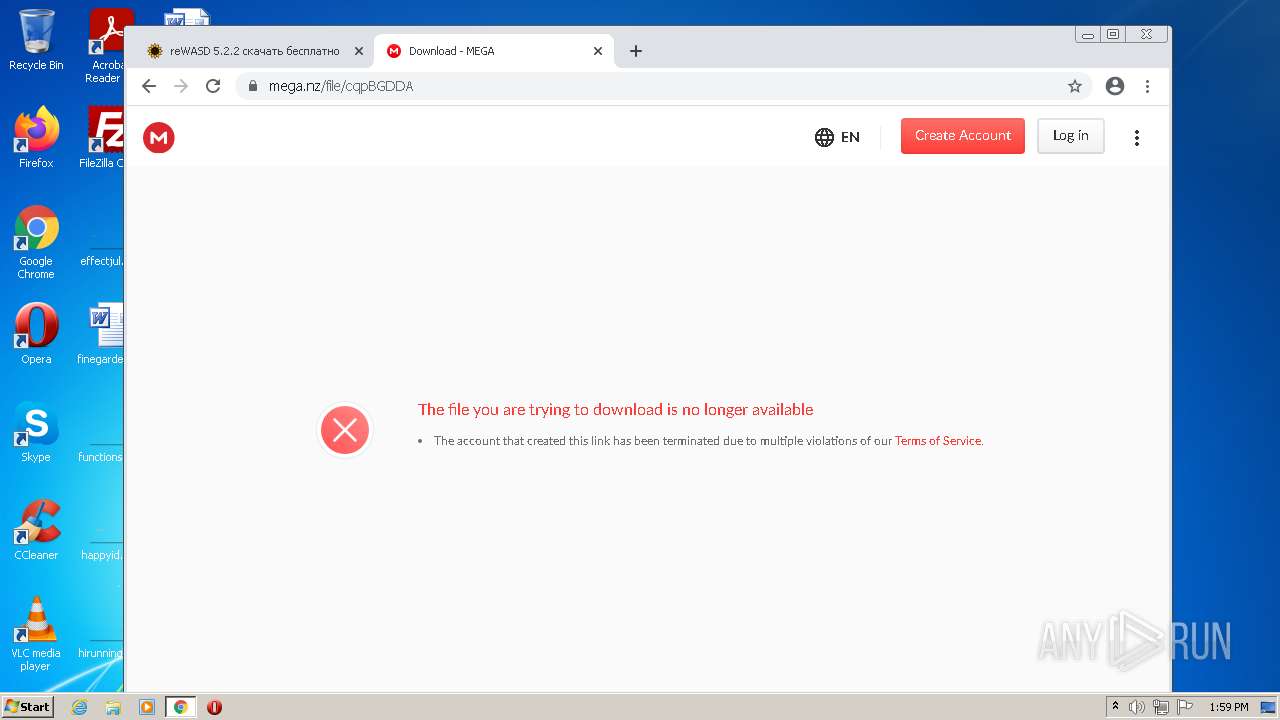
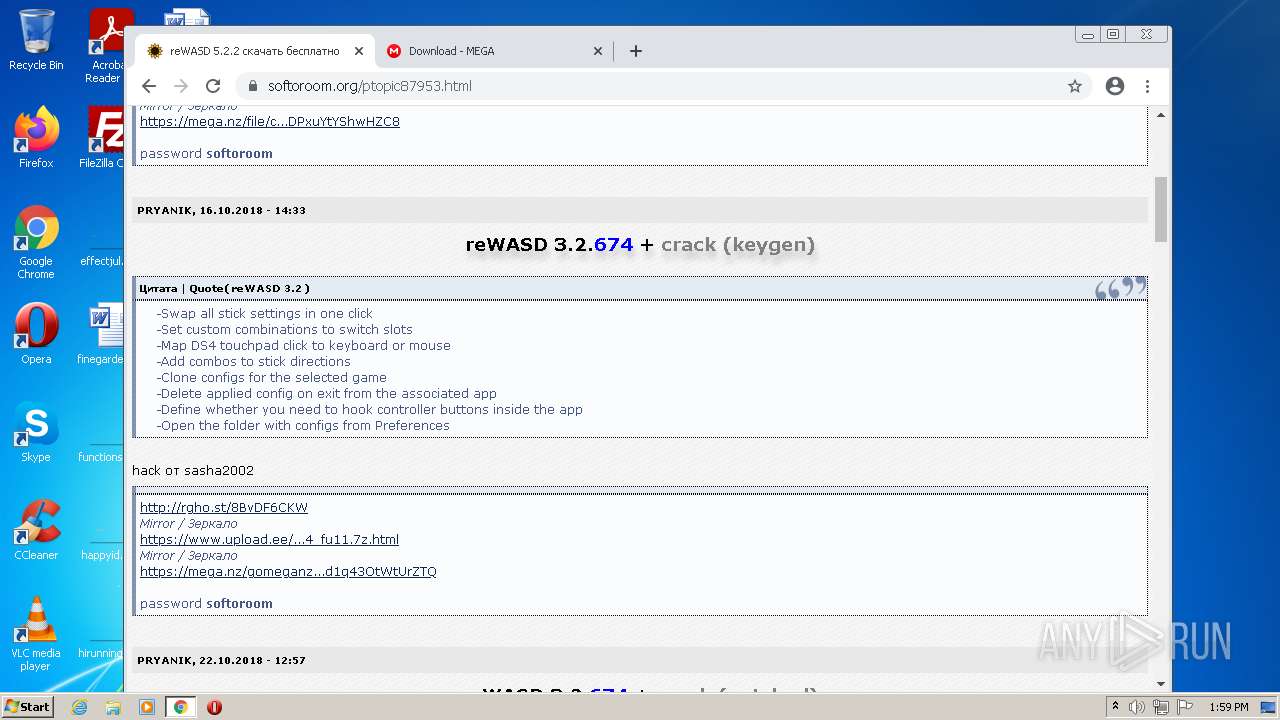
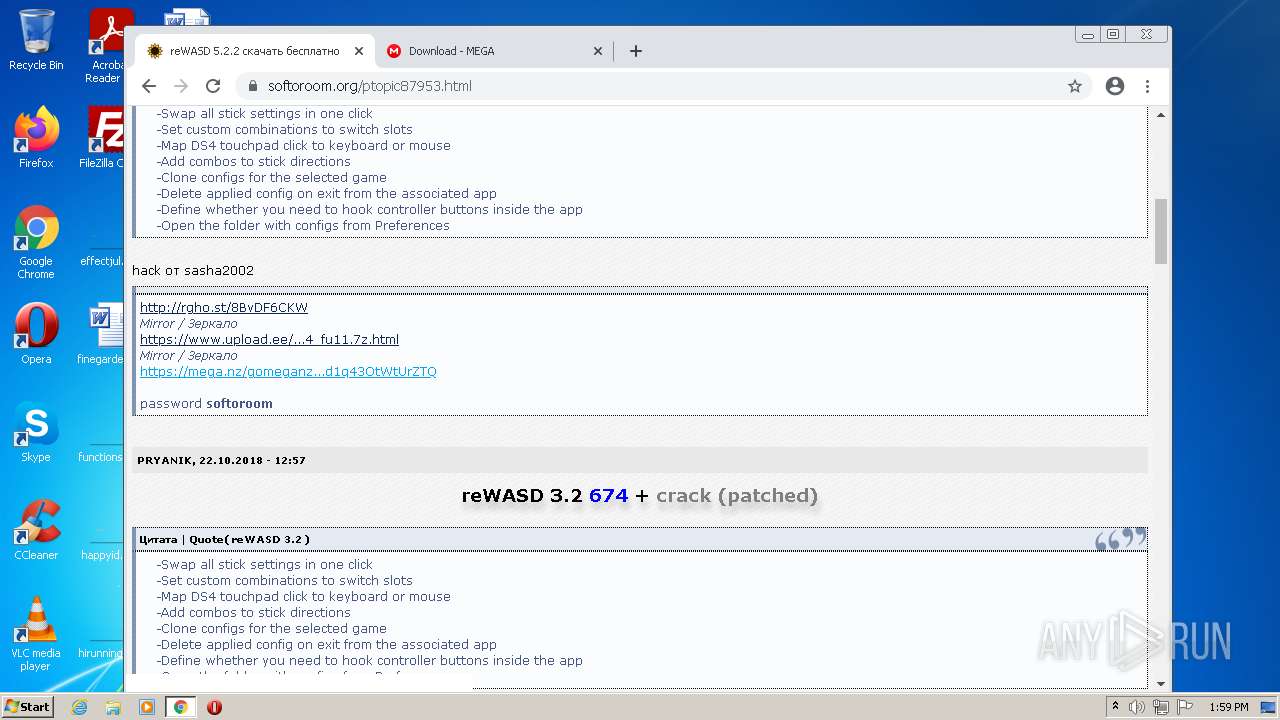
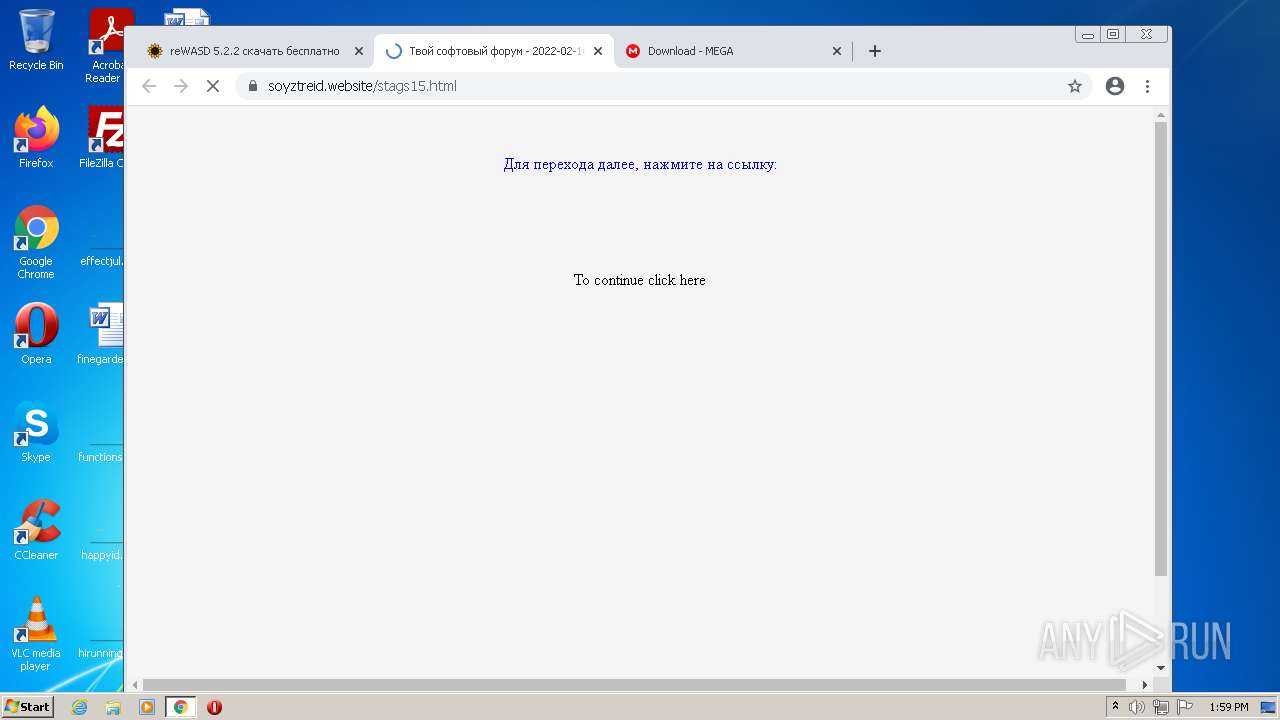
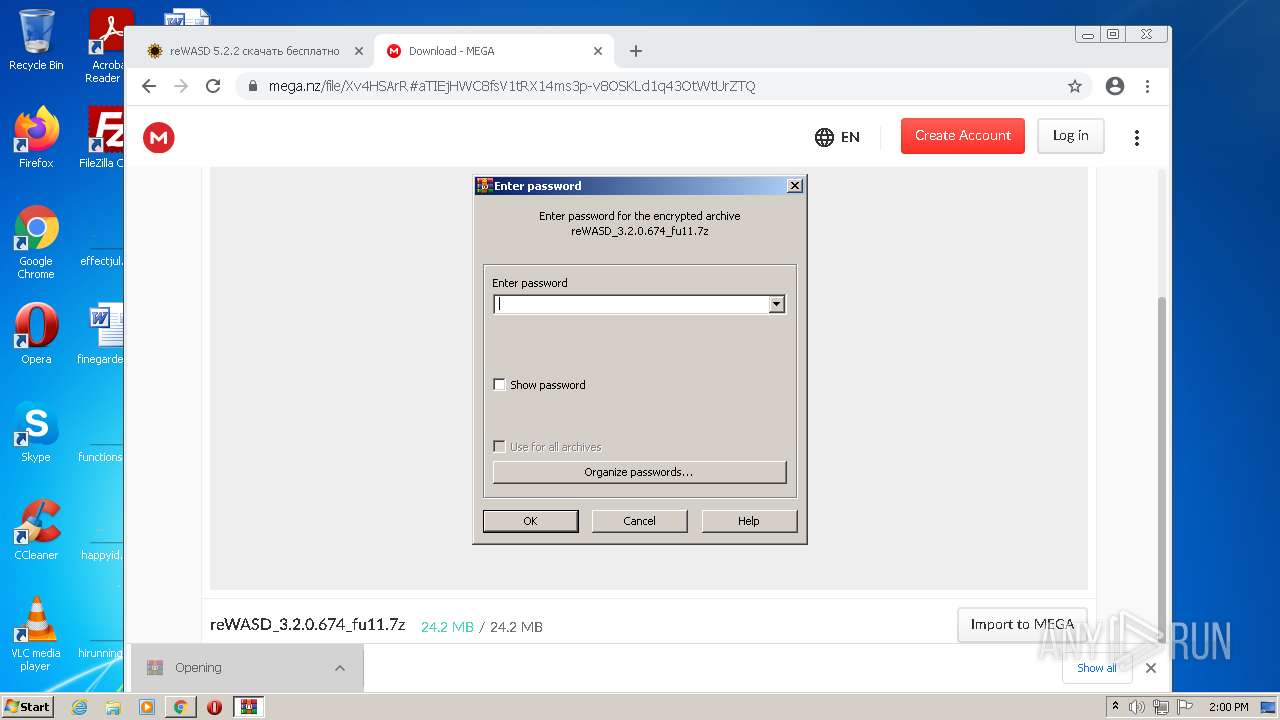
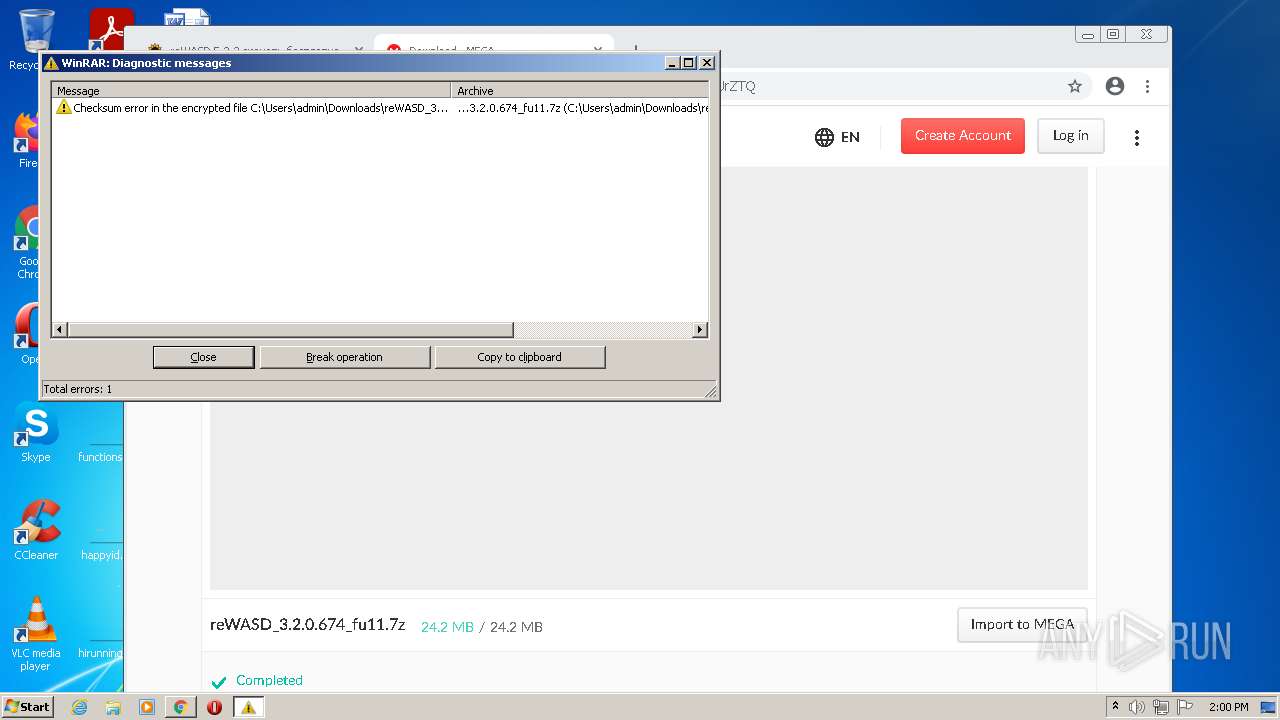
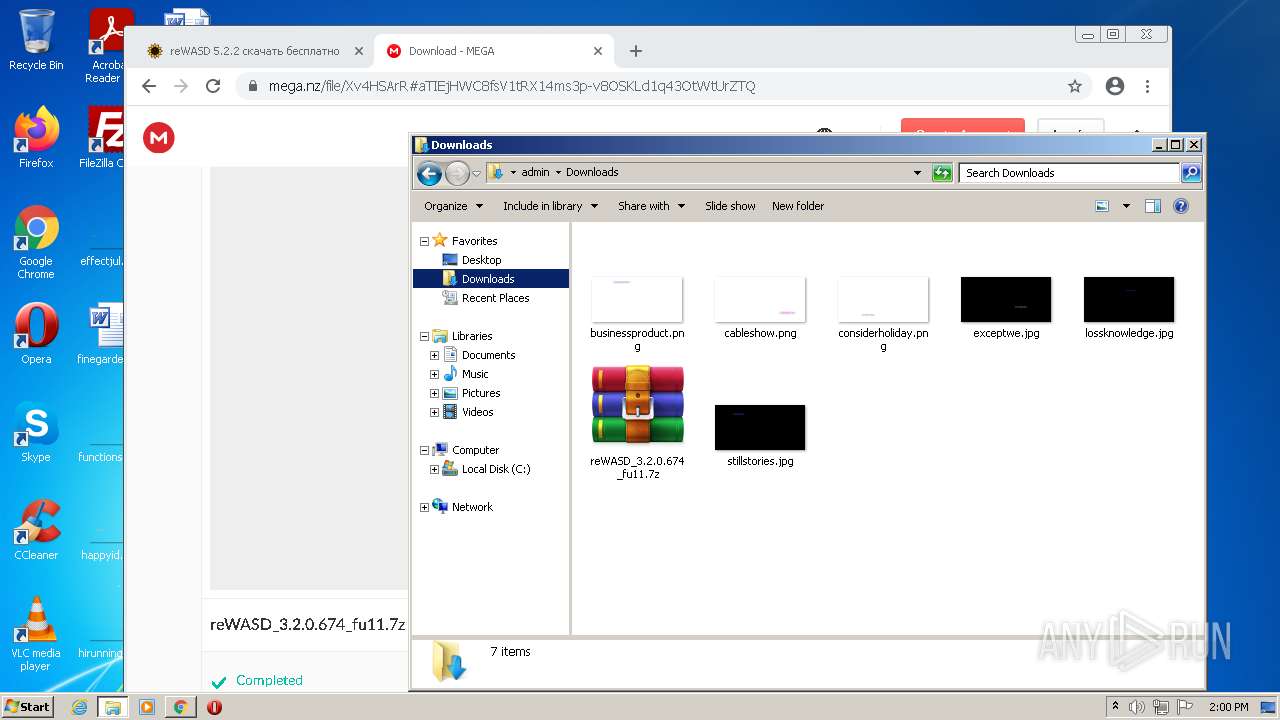
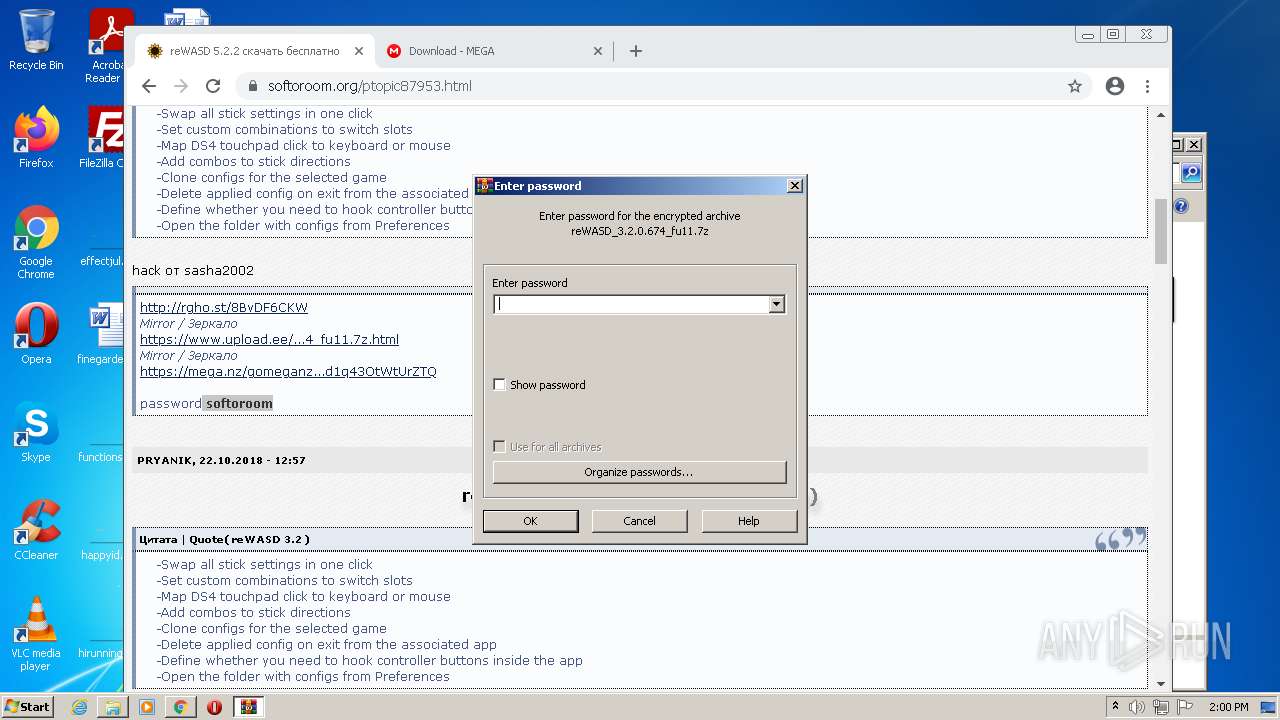
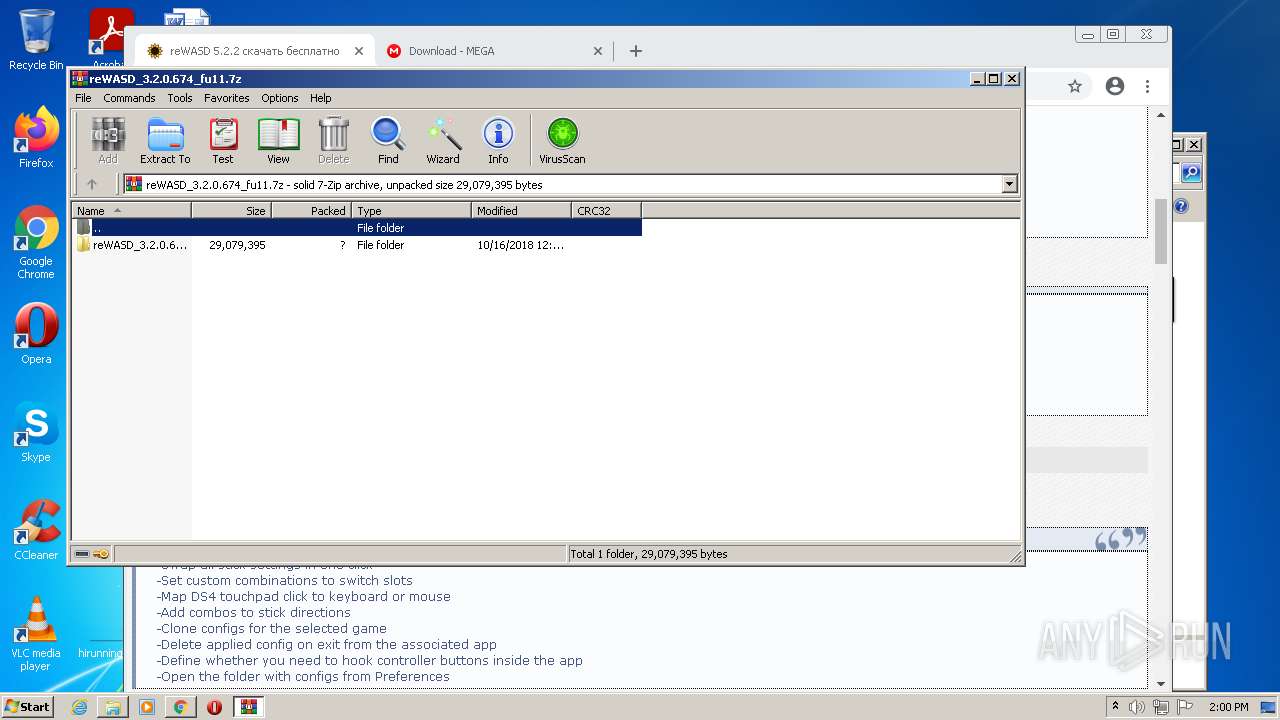
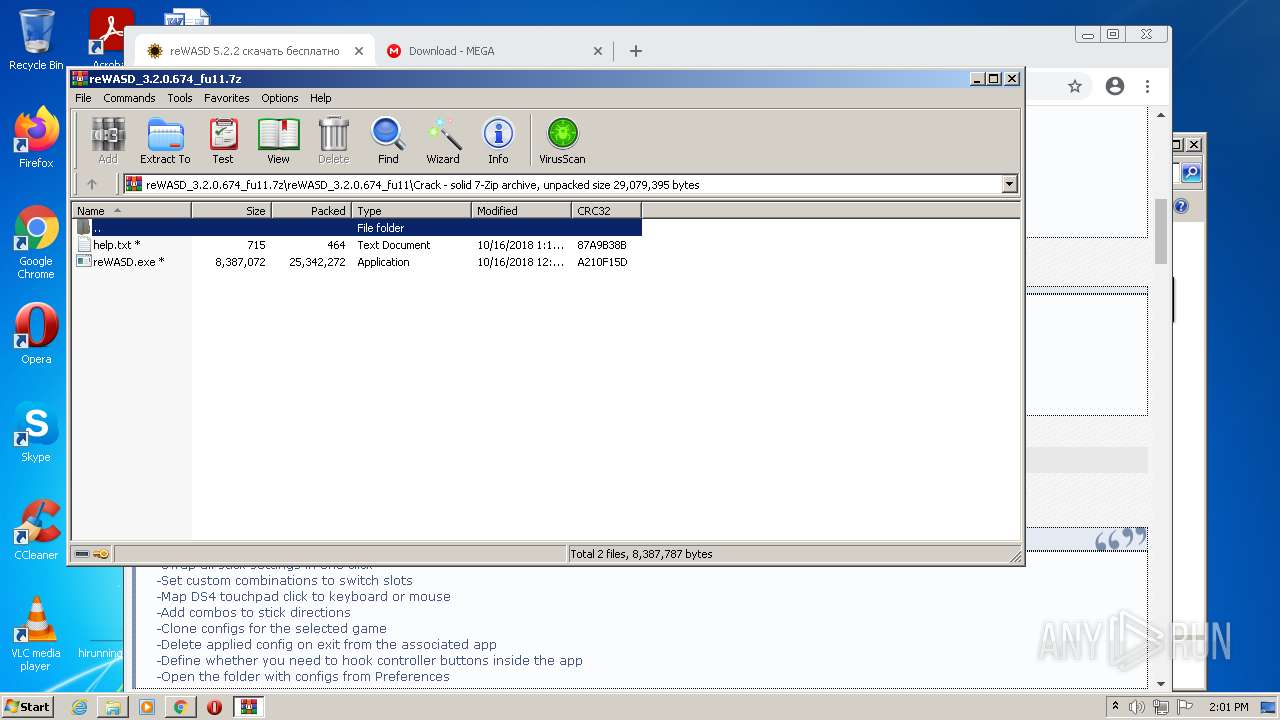
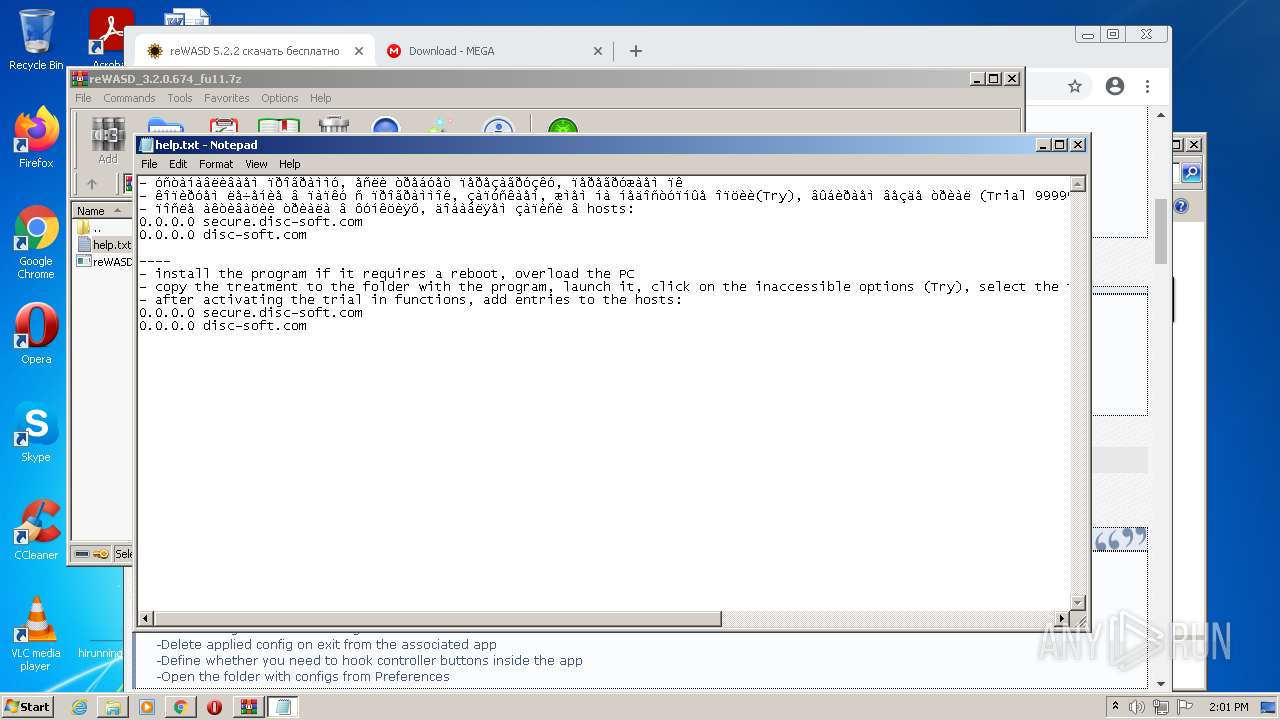
| URL: | https://mega.nz/file/Xv4HSArR#aTIEjHWC8fsV1tRX14ms3p-v8OSKLd1q43OtWtUrZTQ |
| Full analysis: | https://app.any.run/tasks/fb8b069f-f1f6-49cf-9052-745143ac8353 |
| Verdict: | Malicious activity |
| Analysis date: | February 16, 2022, 13:56:57 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 3C28D3BE0518527AEE065B0AF14CF495 |
| SHA1: | D1AF2EB9EED68B380C467ABDD96D43EF9817E230 |
| SHA256: | 87E21AA4BFAD0B2CAEA84EEBB2E54C81D9E8E0E89310AB859A481948D150A119 |
| SSDEEP: | 3:N8X/iCRtaYBtW4b3BDjyqx0:2ntDt5Biv |
MALICIOUS
Application was dropped or rewritten from another process
- reWASD320-0674.exe (PID: 1768)
- reWASD320-0674.exe (PID: 368)
- RewasdWpfInstaller.exe (PID: 1200)
- reWASDInstaller.exe (PID: 3176)
- reWASDService.exe (PID: 3928)
Drops executable file immediately after starts
- reWASD320-0674.exe (PID: 368)
- reWASDInstaller.exe (PID: 3176)
- reWASDService.exe (PID: 3928)
- DrvInst.exe (PID: 2728)
Loads dropped or rewritten executable
- reWASD320-0674.exe (PID: 368)
- reWASDInstaller.exe (PID: 3176)
Changes the autorun value in the registry
- reWASDInstaller.exe (PID: 3176)
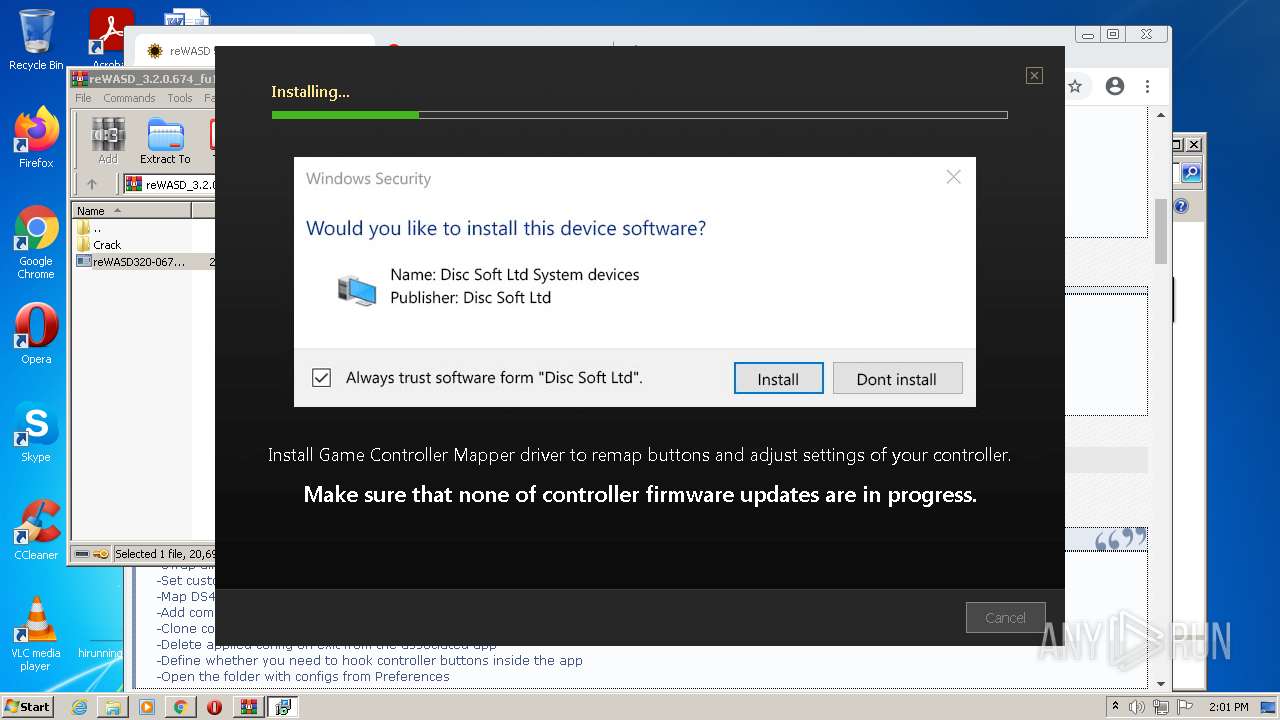
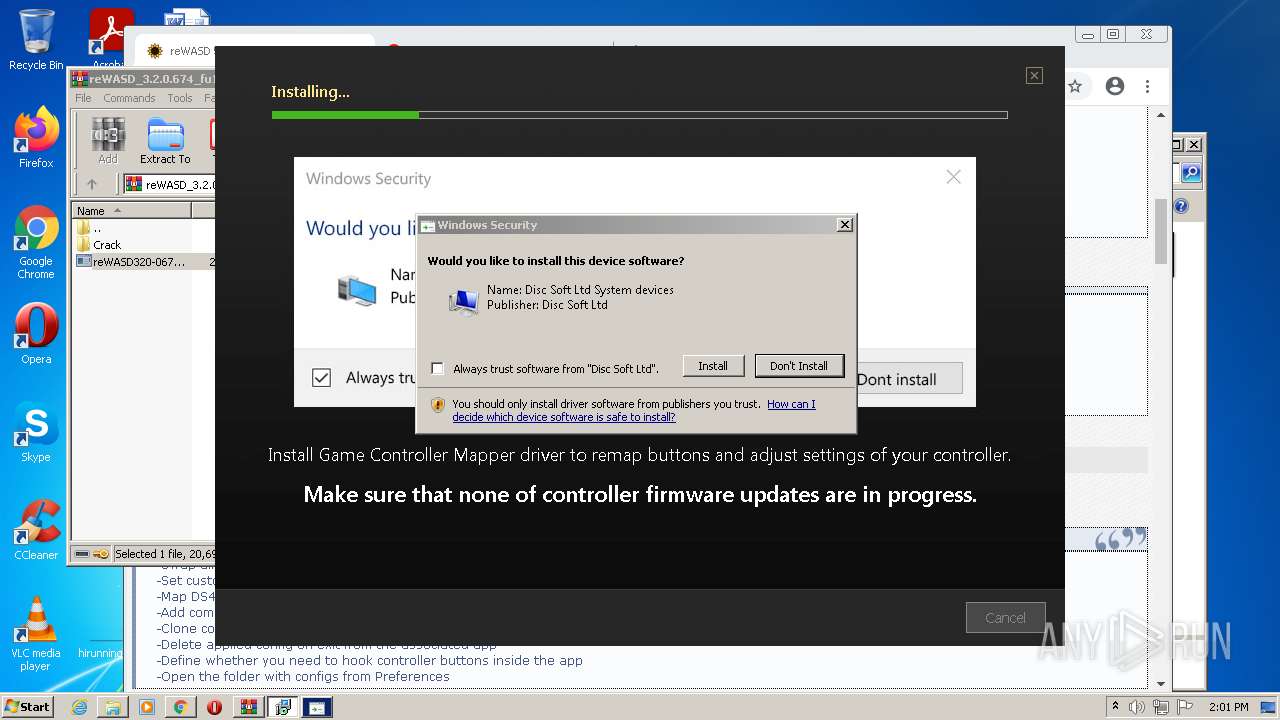
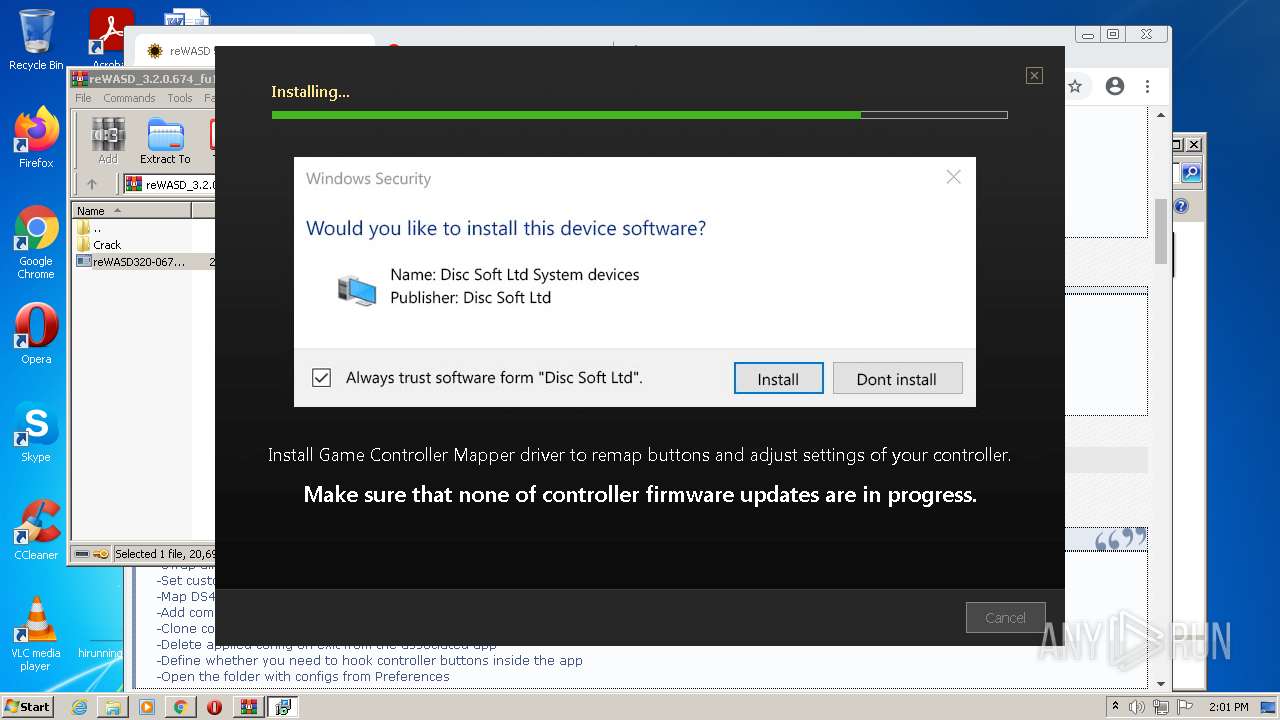
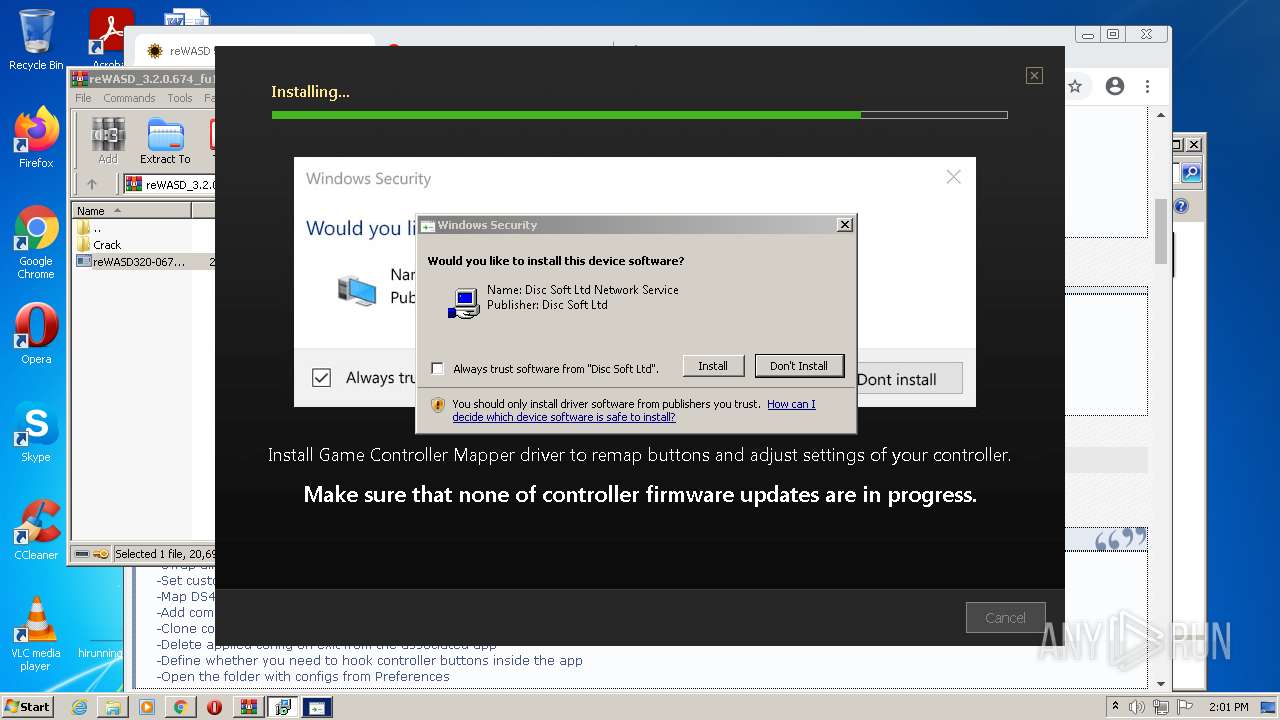
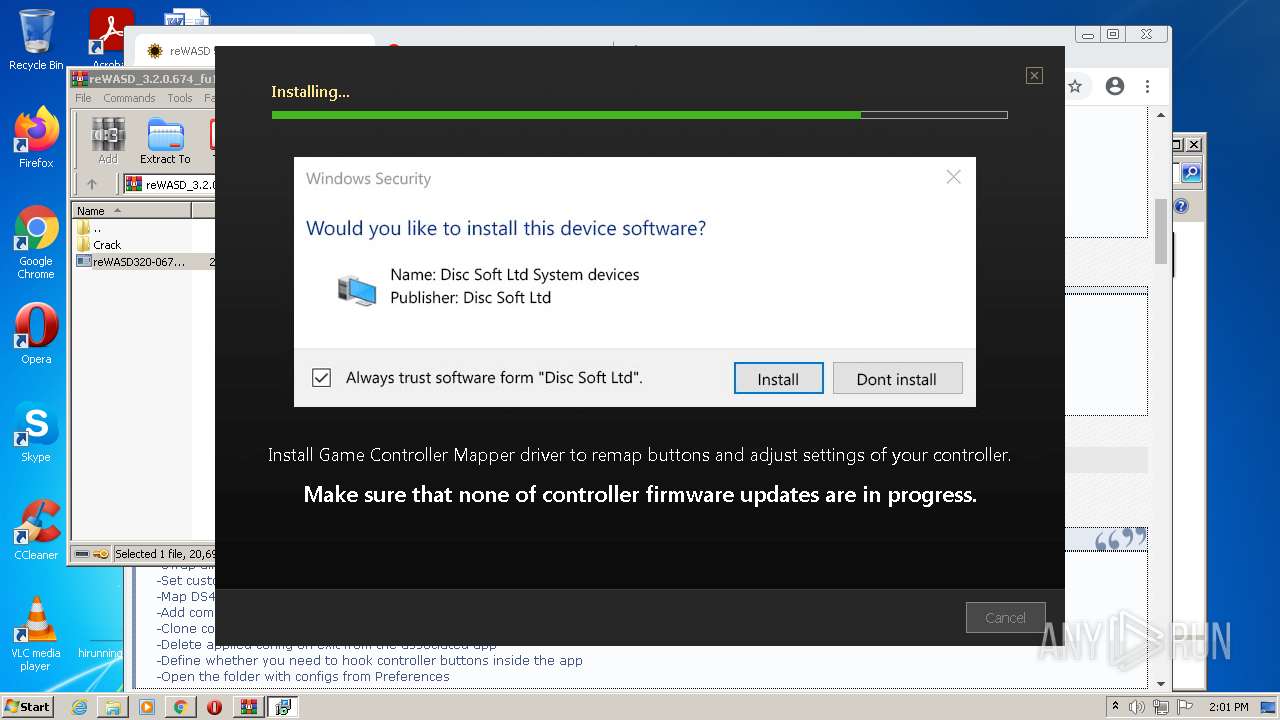
Changes settings of System certificates
- reWASDService.exe (PID: 3928)
SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 3476)
- chrome.exe (PID: 756)
Modifies files in Chrome extension folder
- chrome.exe (PID: 3052)
Reads the computer name
- WinRAR.exe (PID: 2532)
- WinRAR.exe (PID: 3056)
- reWASD320-0674.exe (PID: 368)
- RewasdWpfInstaller.exe (PID: 1200)
- reWASDInstaller.exe (PID: 3176)
- reWASDService.exe (PID: 3928)
- DrvInst.exe (PID: 2728)
Checks supported languages
- WinRAR.exe (PID: 2532)
- reWASD320-0674.exe (PID: 368)
- RewasdWpfInstaller.exe (PID: 1200)
- WinRAR.exe (PID: 3056)
- reWASDInstaller.exe (PID: 3176)
- ns26C6.tmp (PID: 1472)
- DrvInst.exe (PID: 2728)
- ns27A2.tmp (PID: 2868)
- reWASDService.exe (PID: 3928)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3056)
- reWASD320-0674.exe (PID: 368)
- RewasdWpfInstaller.exe (PID: 1200)
- reWASDInstaller.exe (PID: 3176)
- reWASDService.exe (PID: 3928)
- DrvInst.exe (PID: 2728)
Drops a file that was compiled in debug mode
- reWASD320-0674.exe (PID: 368)
- reWASDInstaller.exe (PID: 3176)
- reWASDService.exe (PID: 3928)
- DrvInst.exe (PID: 2728)
Reads Environment values
- RewasdWpfInstaller.exe (PID: 1200)
- vssvc.exe (PID: 3532)
Creates a directory in Program Files
- RewasdWpfInstaller.exe (PID: 1200)
- reWASDInstaller.exe (PID: 3176)
Creates files in the program directory
- reWASDInstaller.exe (PID: 3176)
- logman.exe (PID: 2420)
- logman.exe (PID: 3612)
- reWASDService.exe (PID: 3928)
Changes default file association
- reWASDInstaller.exe (PID: 3176)
Starts application with an unusual extension
- reWASDInstaller.exe (PID: 3176)
Adds / modifies Windows certificates
- reWASDService.exe (PID: 3928)
Executed via COM
- DrvInst.exe (PID: 2728)
- DrvInst.exe (PID: 3340)
- DrvInst.exe (PID: 3728)
Creates files in the Windows directory
- DrvInst.exe (PID: 2728)
Creates files in the driver directory
- DrvInst.exe (PID: 2728)
Uses RUNDLL32.EXE to load library
- DrvInst.exe (PID: 2728)
- DrvInst.exe (PID: 3728)
Executed as Windows Service
- vssvc.exe (PID: 3532)
Removes files from Windows directory
- DrvInst.exe (PID: 2728)
INFO
Checks supported languages
- iexplore.exe (PID: 3476)
- iexplore.exe (PID: 3020)
- control.exe (PID: 3888)
- chrome.exe (PID: 3052)
- chrome.exe (PID: 3228)
- chrome.exe (PID: 3880)
- chrome.exe (PID: 2972)
- chrome.exe (PID: 484)
- chrome.exe (PID: 2252)
- chrome.exe (PID: 3056)
- chrome.exe (PID: 1984)
- chrome.exe (PID: 2568)
- chrome.exe (PID: 3540)
- chrome.exe (PID: 2772)
- chrome.exe (PID: 3372)
- chrome.exe (PID: 3240)
- chrome.exe (PID: 2420)
- chrome.exe (PID: 2976)
- chrome.exe (PID: 3296)
- chrome.exe (PID: 3356)
- chrome.exe (PID: 3800)
- chrome.exe (PID: 344)
- chrome.exe (PID: 2928)
- chrome.exe (PID: 3204)
- chrome.exe (PID: 504)
- chrome.exe (PID: 452)
- chrome.exe (PID: 1676)
- chrome.exe (PID: 1432)
- chrome.exe (PID: 3560)
- chrome.exe (PID: 2604)
- chrome.exe (PID: 3028)
- chrome.exe (PID: 3112)
- chrome.exe (PID: 2940)
- chrome.exe (PID: 2232)
- chrome.exe (PID: 304)
- chrome.exe (PID: 764)
- chrome.exe (PID: 2516)
- chrome.exe (PID: 2160)
- chrome.exe (PID: 396)
- chrome.exe (PID: 2264)
- chrome.exe (PID: 364)
- chrome.exe (PID: 4088)
- chrome.exe (PID: 3768)
- chrome.exe (PID: 756)
- chrome.exe (PID: 2980)
- chrome.exe (PID: 3552)
- explorer.exe (PID: 2504)
- NOTEPAD.EXE (PID: 2304)
- chrome.exe (PID: 3316)
- WISPTIS.EXE (PID: 2352)
- logman.exe (PID: 2420)
- logman.exe (PID: 3612)
- rundll32.exe (PID: 2892)
- vssvc.exe (PID: 3532)
Reads the computer name
- iexplore.exe (PID: 3476)
- iexplore.exe (PID: 3020)
- chrome.exe (PID: 3052)
- control.exe (PID: 3888)
- chrome.exe (PID: 484)
- chrome.exe (PID: 3372)
- chrome.exe (PID: 3880)
- chrome.exe (PID: 2568)
- chrome.exe (PID: 3296)
- chrome.exe (PID: 344)
- chrome.exe (PID: 2604)
- chrome.exe (PID: 3768)
- chrome.exe (PID: 756)
- explorer.exe (PID: 2504)
- chrome.exe (PID: 3552)
- WISPTIS.EXE (PID: 2352)
- logman.exe (PID: 2420)
- logman.exe (PID: 3612)
- rundll32.exe (PID: 2892)
- vssvc.exe (PID: 3532)
Changes internet zones settings
- iexplore.exe (PID: 3020)
Checks Windows Trust Settings
- iexplore.exe (PID: 3476)
- iexplore.exe (PID: 3020)
- chrome.exe (PID: 3052)
- reWASDService.exe (PID: 3928)
- DrvInst.exe (PID: 2728)
- rundll32.exe (PID: 2892)
Application launched itself
- iexplore.exe (PID: 3020)
- chrome.exe (PID: 3052)
Manual execution by user
- control.exe (PID: 3888)
- chrome.exe (PID: 3052)
- explorer.exe (PID: 2504)
- WinRAR.exe (PID: 3056)
Reads settings of System Certificates
- iexplore.exe (PID: 3476)
- iexplore.exe (PID: 3020)
- chrome.exe (PID: 3880)
- reWASDService.exe (PID: 3928)
- DrvInst.exe (PID: 2728)
- rundll32.exe (PID: 2892)
Reads the date of Windows installation
- iexplore.exe (PID: 3020)
- chrome.exe (PID: 344)
Reads the hosts file
- chrome.exe (PID: 3880)
- chrome.exe (PID: 3052)
Creates files in the user directory
- chrome.exe (PID: 3052)
Changes settings of System certificates
- DrvInst.exe (PID: 2728)
Searches for installed software
- DrvInst.exe (PID: 2728)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
120
Monitored processes
68
Malicious processes
4
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 304 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1036,7065692389319509867,8240932014652691765,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=30 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1952 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 344 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1036,7065692389319509867,8240932014652691765,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=2864 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 364 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1036,7065692389319509867,8240932014652691765,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=36 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2896 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
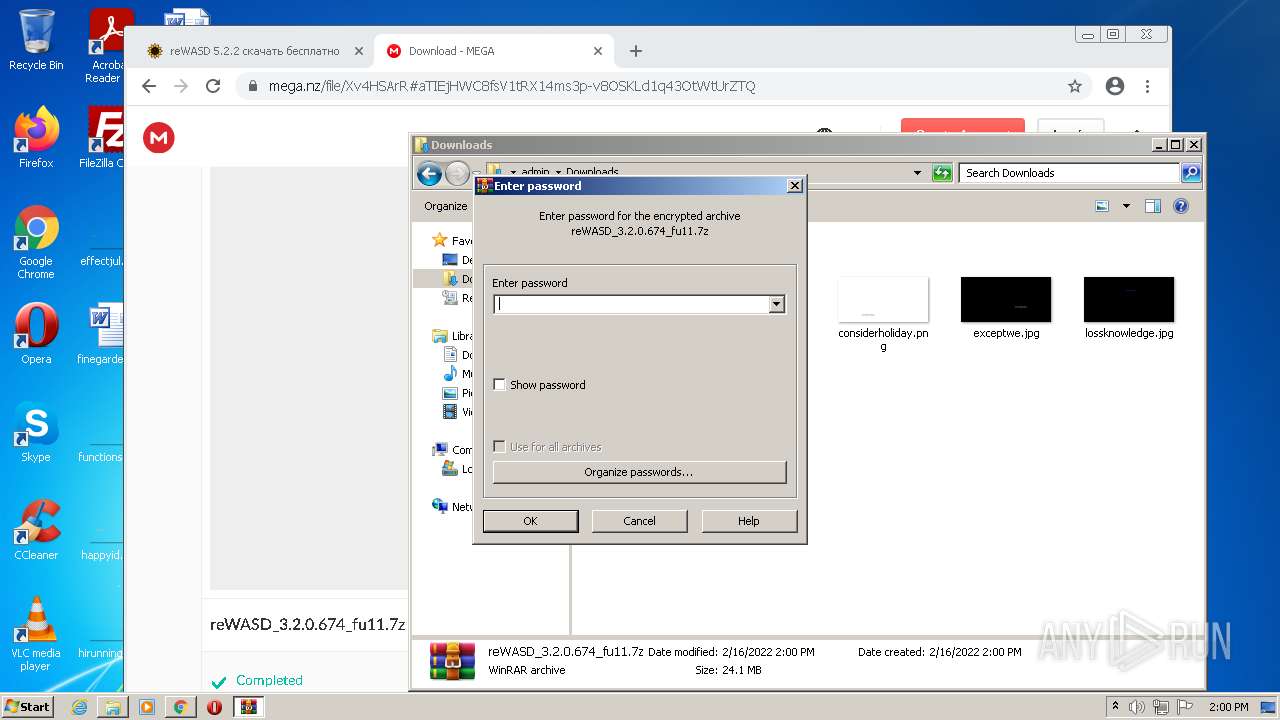
| 368 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb3056.22668\reWASD_3.2.0.674_fu11\reWASD320-0674.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb3056.22668\reWASD_3.2.0.674_fu11\reWASD320-0674.exe | WinRAR.exe | ||||||||||||
User: admin Company: Disc Soft Ltd. Integrity Level: HIGH Description: reWASD Exit code: 0 Version: 3.2.0674 Modules
| |||||||||||||||
| 396 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1036,7065692389319509867,8240932014652691765,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=37 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3612 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 452 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1036,7065692389319509867,8240932014652691765,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3592 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 484 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1036,7065692389319509867,8240932014652691765,131072 --enable-features=PasswordImport --gpu-preferences=MAAAAAAAAADgAAAwAAAAAAAAAAAAAAAAAABgAAAAAAAQAAAAAAAAAAAAAAAAAAAAKAAAAAQAAAAgAAAAAAAAACgAAAAAAAAAMAAAAAAAAAA4AAAAAAAAABAAAAAAAAAAAAAAAAUAAAAQAAAAAAAAAAAAAAAGAAAAEAAAAAAAAAABAAAABQAAABAAAAAAAAAAAQAAAAYAAAA= --mojo-platform-channel-handle=988 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 504 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1036,7065692389319509867,8240932014652691765,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=22 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2800 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 756 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --field-trial-handle=1036,7065692389319509867,8240932014652691765,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=3640 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 764 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1036,7065692389319509867,8240932014652691765,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=31 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2196 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
53 351
Read events
52 716
Write events
626
Delete events
9
Modification events
| (PID) Process: | (3020) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3020) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: 299233152 | |||
| (PID) Process: | (3020) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30942013 | |||
| (PID) Process: | (3020) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 599398933 | |||
| (PID) Process: | (3020) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30942013 | |||
| (PID) Process: | (3020) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3020) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3020) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3020) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3020) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
38
Suspicious files
246
Text files
211
Unknown types
22
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3052 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-620D02C8-BEC.pma | — | |
MD5:— | SHA256:— | |||
| 3476 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:— | SHA256:— | |||
| 3020 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | der | |
MD5:— | SHA256:— | |||
| 3020 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | binary | |
MD5:— | SHA256:— | |||
| 3476 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 3020 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF32958593BACB2A17.TMP | gmc | |
MD5:— | SHA256:— | |||
| 3020 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Last Active\RecoveryStore.{42C873D0-1D90-11EB-BA2C-12A9866C77DE}.dat | binary | |
MD5:— | SHA256:— | |||
| 3020 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF7C9D2FC79D9A7880.TMP | gmc | |
MD5:— | SHA256:— | |||
| 3020 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Last Active\{5640C71D-8F30-11EC-976C-12A9866C77DE}.dat | binary | |
MD5:— | SHA256:— | |||
| 3020 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\RecoveryStore.{4F7B7988-8F30-11EC-976C-12A9866C77DE}.dat | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
49
TCP/UDP connections
111
DNS requests
70
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
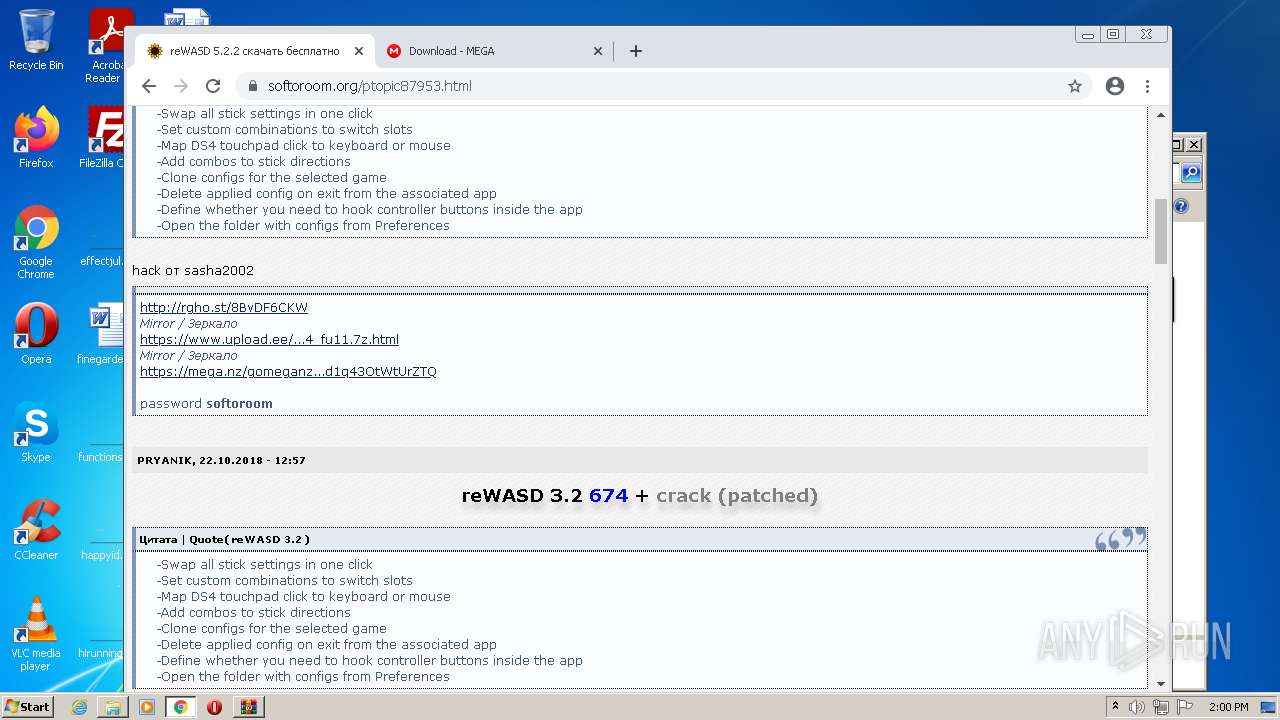
3880 | chrome.exe | GET | 301 | 172.67.220.180:80 | http://softoroom.org/ptopic87953.html | US | — | — | suspicious |
884 | svchost.exe | HEAD | 200 | 74.125.104.234:80 | http://r5---sn-ixh7yn7e.gvt1.com/edgedl/release2/chrome_component/adktovjj3t3n7jwiiegl5h6y3v5q_1.3.36.121/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.121_win_bxugoraqoudfswxg22hsatfdbi.crx3?cms_redirect=yes&mh=bj&mip=196.244.192.6&mm=28&mn=sn-ixh7yn7e&ms=nvh&mt=1645019057&mv=m&mvi=5&pl=25&rmhost=r3---sn-ixh7yn7e.gvt1.com&shardbypass=yes | US | — | — | whitelisted |
884 | svchost.exe | HEAD | 302 | 142.250.186.142:80 | http://redirector.gvt1.com/edgedl/release2/chrome_component/adktovjj3t3n7jwiiegl5h6y3v5q_1.3.36.121/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.121_win_bxugoraqoudfswxg22hsatfdbi.crx3 | US | — | — | whitelisted |
3020 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
884 | svchost.exe | GET | 302 | 142.250.186.142:80 | http://redirector.gvt1.com/edgedl/release2/chrome_component/adktovjj3t3n7jwiiegl5h6y3v5q_1.3.36.121/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.121_win_bxugoraqoudfswxg22hsatfdbi.crx3 | US | html | 575 b | whitelisted |
884 | svchost.exe | GET | 206 | 74.125.104.234:80 | http://r5---sn-ixh7yn7e.gvt1.com/edgedl/release2/chrome_component/adktovjj3t3n7jwiiegl5h6y3v5q_1.3.36.121/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.121_win_bxugoraqoudfswxg22hsatfdbi.crx3?cms_redirect=yes&mh=bj&mip=196.244.192.6&mm=28&mn=sn-ixh7yn7e&ms=nvh&mt=1645019057&mv=m&mvi=5&pl=25&rmhost=r3---sn-ixh7yn7e.gvt1.com&shardbypass=yes | US | binary | 9.50 Kb | whitelisted |
884 | svchost.exe | GET | 206 | 74.125.104.234:80 | http://r5---sn-ixh7yn7e.gvt1.com/edgedl/release2/chrome_component/adktovjj3t3n7jwiiegl5h6y3v5q_1.3.36.121/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.121_win_bxugoraqoudfswxg22hsatfdbi.crx3?cms_redirect=yes&mh=bj&mip=196.244.192.6&mm=28&mn=sn-ixh7yn7e&ms=nvh&mt=1645019057&mv=m&mvi=5&pl=25&rmhost=r3---sn-ixh7yn7e.gvt1.com&shardbypass=yes | US | binary | 12.0 Kb | whitelisted |
884 | svchost.exe | GET | 302 | 142.250.186.142:80 | http://redirector.gvt1.com/edgedl/release2/chrome_component/adktovjj3t3n7jwiiegl5h6y3v5q_1.3.36.121/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.121_win_bxugoraqoudfswxg22hsatfdbi.crx3 | US | html | 575 b | whitelisted |
884 | svchost.exe | GET | 206 | 74.125.104.234:80 | http://r5---sn-ixh7yn7e.gvt1.com/edgedl/release2/chrome_component/adktovjj3t3n7jwiiegl5h6y3v5q_1.3.36.121/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.121_win_bxugoraqoudfswxg22hsatfdbi.crx3?cms_redirect=yes&mh=bj&mip=196.244.192.6&mm=28&mn=sn-ixh7yn7e&ms=nvh&mt=1645019057&mv=m&mvi=5&pl=25&rmhost=r3---sn-ixh7yn7e.gvt1.com&shardbypass=yes | US | binary | 9.50 Kb | whitelisted |
884 | svchost.exe | GET | 302 | 142.250.186.142:80 | http://redirector.gvt1.com/edgedl/release2/chrome_component/adktovjj3t3n7jwiiegl5h6y3v5q_1.3.36.121/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.121_win_bxugoraqoudfswxg22hsatfdbi.crx3 | US | html | 575 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3476 | iexplore.exe | 31.216.145.5:443 | mega.nz | Datacenter Luxembourg S.A. | LU | malicious |
3476 | iexplore.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | Highwinds Network Group, Inc. | US | whitelisted |
3476 | iexplore.exe | 23.45.105.185:80 | x1.c.lencr.org | Akamai International B.V. | NL | unknown |
3020 | iexplore.exe | 131.253.33.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
3476 | iexplore.exe | 2.16.186.19:80 | r3.o.lencr.org | Akamai International B.V. | — | whitelisted |
3020 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3880 | chrome.exe | 142.250.186.109:443 | accounts.google.com | Google Inc. | US | whitelisted |
3880 | chrome.exe | 216.58.212.163:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
— | — | 142.250.186.174:443 | clients2.google.com | Google Inc. | US | whitelisted |
3880 | chrome.exe | 142.250.184.238:443 | encrypted-tbn0.gstatic.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.microsoft.com |
| whitelisted |
mega.nz |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
r3.o.lencr.org |
| shared |
ocsp.digicert.com |
| whitelisted |
www.google.com |
| malicious |
clientservices.googleapis.com |
| whitelisted |