| File name: | pik.zakaz.pdf |
| Full analysis: | https://app.any.run/tasks/65ee2369-eb5a-44ba-8264-2f4c57645858 |
| Verdict: | Malicious activity |
| Analysis date: | February 18, 2019, 11:21:01 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/pdf |
| File info: | PDF document, version 1.4 |
| MD5: | 9E86DA0D75DAFD0E8D1D276E64D9F869 |
| SHA1: | 9F1FB5AAE1459C5E28FA4AF8E66575799E10037C |
| SHA256: | 87A3CA431BAC8A6F733B07784A1B3630DA2568570C9EC0AFE1929990C486FCCA |
| SSDEEP: | 768:AN+houpD1ElEu+Z8uJNrRgaPpjNwzyh/yB4ILnmUvT6dC:QDkh/hKSpBBh/URLnmUr6M |
MALICIOUS
Loads the Task Scheduler COM API
- MsiExec.exe (PID: 3888)
- MsiExec.exe (PID: 708)
SUSPICIOUS
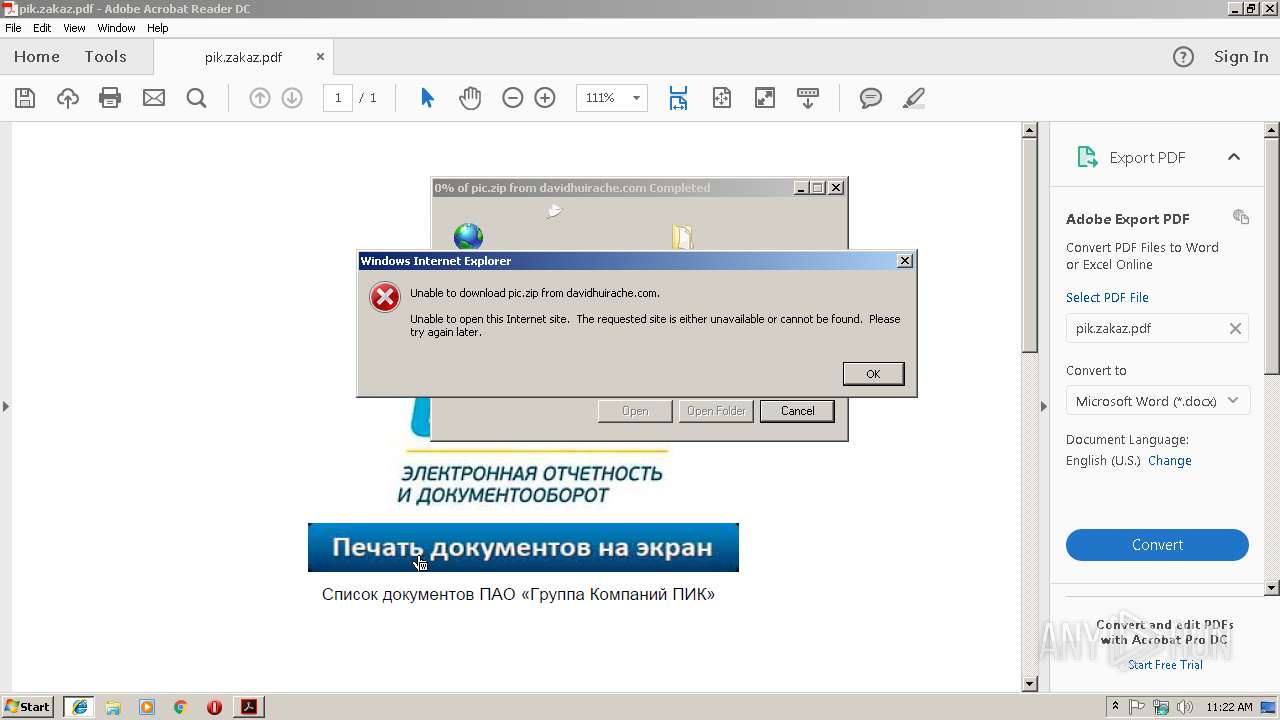
Starts Internet Explorer
- AcroRd32.exe (PID: 2852)
Creates files in the program directory
- AdobeARM.exe (PID: 3960)
Executable content was dropped or overwritten
- AdobeARM.exe (PID: 3960)
- msiexec.exe (PID: 4032)
INFO
Application launched itself
- AcroRd32.exe (PID: 2852)
- iexplore.exe (PID: 3216)
- RdrCEF.exe (PID: 2180)
- iexplore.exe (PID: 2308)
- iexplore.exe (PID: 3864)
- msiexec.exe (PID: 4032)
- firefox.exe (PID: 3840)
Changes internet zones settings
- iexplore.exe (PID: 3216)
- iexplore.exe (PID: 3864)
- iexplore.exe (PID: 2308)
Reads Internet Cache Settings
- iexplore.exe (PID: 2356)
- iexplore.exe (PID: 2496)
- iexplore.exe (PID: 4080)
Creates files in the user directory
- AcroRd32.exe (PID: 2852)
- firefox.exe (PID: 3840)
Reads settings of System Certificates
- msiexec.exe (PID: 4032)
Creates files in the program directory
- msiexec.exe (PID: 4032)
Creates a software uninstall entry
- msiexec.exe (PID: 4032)
Reads CPU info
- firefox.exe (PID: 3840)
- firefox.exe (PID: 3612)
- firefox.exe (PID: 1336)
- firefox.exe (PID: 2448)
Dropped object may contain Bitcoin addresses
- firefox.exe (PID: 3840)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| | | Adobe Portable Document Format (100) |
EXIF
| PDFVersion: | 1.4 |
|---|---|
| Linearized: | No |
Total processes
51
Monitored processes
21
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 504 | "C:\Program Files\Mozilla Firefox\pingsender.exe" https://incoming.telemetry.mozilla.org/submit/telemetry/5dada563-581b-4906-8835-6f62c85ad3d1/main/Firefox/61.0.2/release/20180807170231?v=4 C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\saved-telemetry-pings\5dada563-581b-4906-8835-6f62c85ad3d1 | C:\Program Files\Mozilla Firefox\pingsender.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Foundation Integrity Level: MEDIUM Exit code: 0 Version: 61.0.2 Modules
| |||||||||||||||
| 708 | C:\Windows\system32\MsiExec.exe -Embedding 1524B6C10E85F822DBD9D0DF1505E0FC M Global\MSI0000 | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1336 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3840.0.1300830114\538632533" -childID 1 -isForBrowser -prefsHandle 1328 -prefsLen 8309 -schedulerPrefs 0001,2 -greomni "C:\Program Files\Mozilla Firefox\omni.ja" -appomni "C:\Program Files\Mozilla Firefox\browser\omni.ja" -appdir "C:\Program Files\Mozilla Firefox\browser" - 3840 "\\.\pipe\gecko-crash-server-pipe.3840" 1472 tab | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 61.0.2 Modules
| |||||||||||||||
| 2180 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --backgroundcolor=16448250 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe RdrCEF Exit code: 3221225547 Version: 15.23.20053.211670 Modules
| |||||||||||||||
| 2188 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" --type=renderer "C:\Users\admin\AppData\Local\Temp\pik.zakaz.pdf" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Reader DC Exit code: 1 Version: 15.23.20070.215641 Modules
| |||||||||||||||
| 2308 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | AcroRd32.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2356 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3216 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2448 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3840.12.1397460427\15275894" -childID 3 -isForBrowser -prefsHandle 2992 -prefsLen 11808 -schedulerPrefs 0001,2 -greomni "C:\Program Files\Mozilla Firefox\omni.ja" -appomni "C:\Program Files\Mozilla Firefox\browser\omni.ja" -appdir "C:\Program Files\Mozilla Firefox\browser" - 3840 "\\.\pipe\gecko-crash-server-pipe.3840" 3004 tab | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 61.0.2 Modules
| |||||||||||||||
| 2496 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3864 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2852 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" "C:\Users\admin\AppData\Local\Temp\pik.zakaz.pdf" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | explorer.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat Reader DC Exit code: 1 Version: 15.23.20070.215641 Modules
| |||||||||||||||
Total events
1 991
Read events
1 685
Write events
282
Delete events
24
Modification events
| (PID) Process: | (2188) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\ExitSection |
| Operation: | write | Name: | bLastExitNormal |
Value: 0 | |||
| (PID) Process: | (2188) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\AVGeneral |
| Operation: | write | Name: | bExpandRHPInViewer |
Value: 1 | |||
| (PID) Process: | (2188) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\NoTimeOut |
| Operation: | write | Name: | smailto |
Value: 5900 | |||
| (PID) Process: | (3216) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3216) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3216) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3216) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (3216) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3216) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000069000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3216) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {5A0B88D6-336F-11E9-BAD8-5254004A04AF} |
Value: 0 | |||
Executable files
3
Suspicious files
66
Text files
61
Unknown types
54
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2188 | AcroRd32.exe | C:\Users\admin\AppData\LocalLow\Adobe\Acrobat\DC\ReaderMessages-journal | — | |
MD5:— | SHA256:— | |||
| 3216 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\RB73MZ6Y\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 3216 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3216 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFBCDB936CA41E24C3.TMP | — | |
MD5:— | SHA256:— | |||
| 2188 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\acrord32_sbx\A9R1uuqiwx_7p1gpl_1os.tmp | — | |
MD5:— | SHA256:— | |||
| 2188 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\acrord32_sbx\A9R44st15_7p1gpk_1os.tmp | — | |
MD5:— | SHA256:— | |||
| 2188 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\acrord32_sbx\A9R1eqnund_7p1gpj_1os.tmp | — | |
MD5:— | SHA256:— | |||
| 2188 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\acrord32_sbx\A9R4j0aea_7p1gpm_1os.tmp | — | |
MD5:— | SHA256:— | |||
| 2188 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\acrord32_sbx\A9R24n1bz_7p1gpn_1os.tmp | — | |
MD5:— | SHA256:— | |||
| 3216 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFA7035B4CD21398BB.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
18
TCP/UDP connections
25
DNS requests
64
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2852 | AcroRd32.exe | GET | 304 | 2.16.186.32:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/message.zip | unknown | — | — | whitelisted |
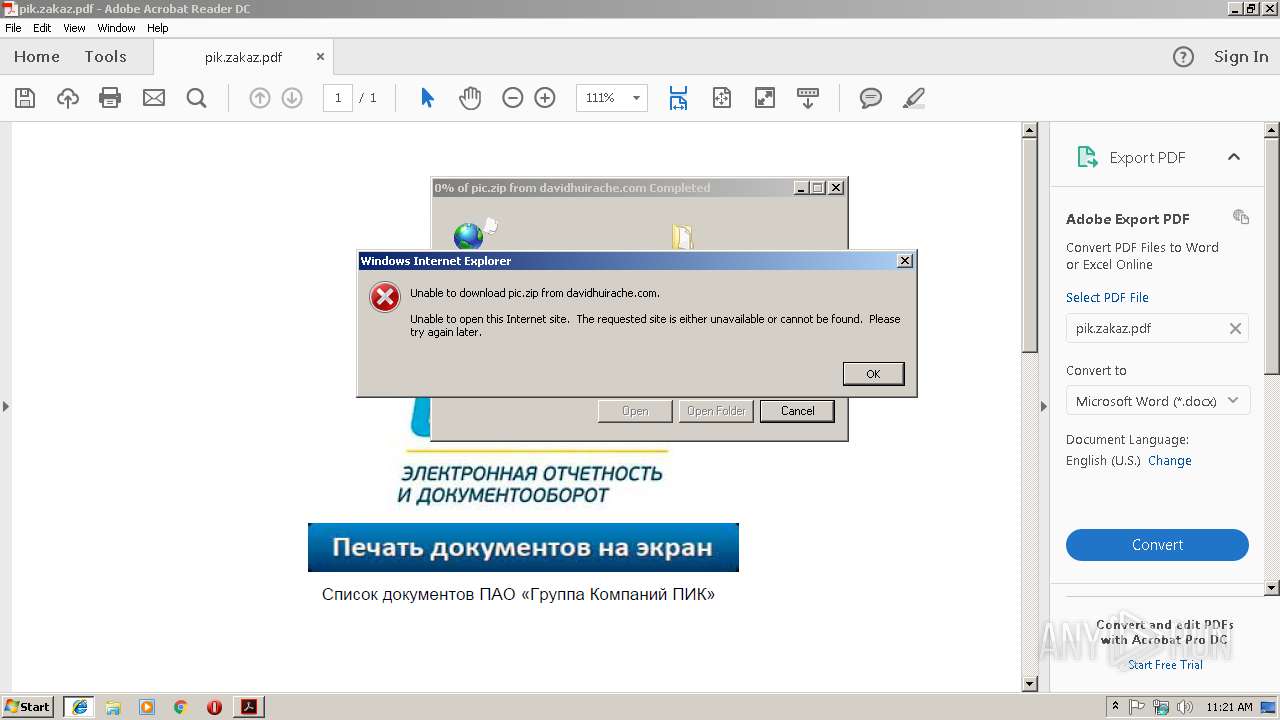
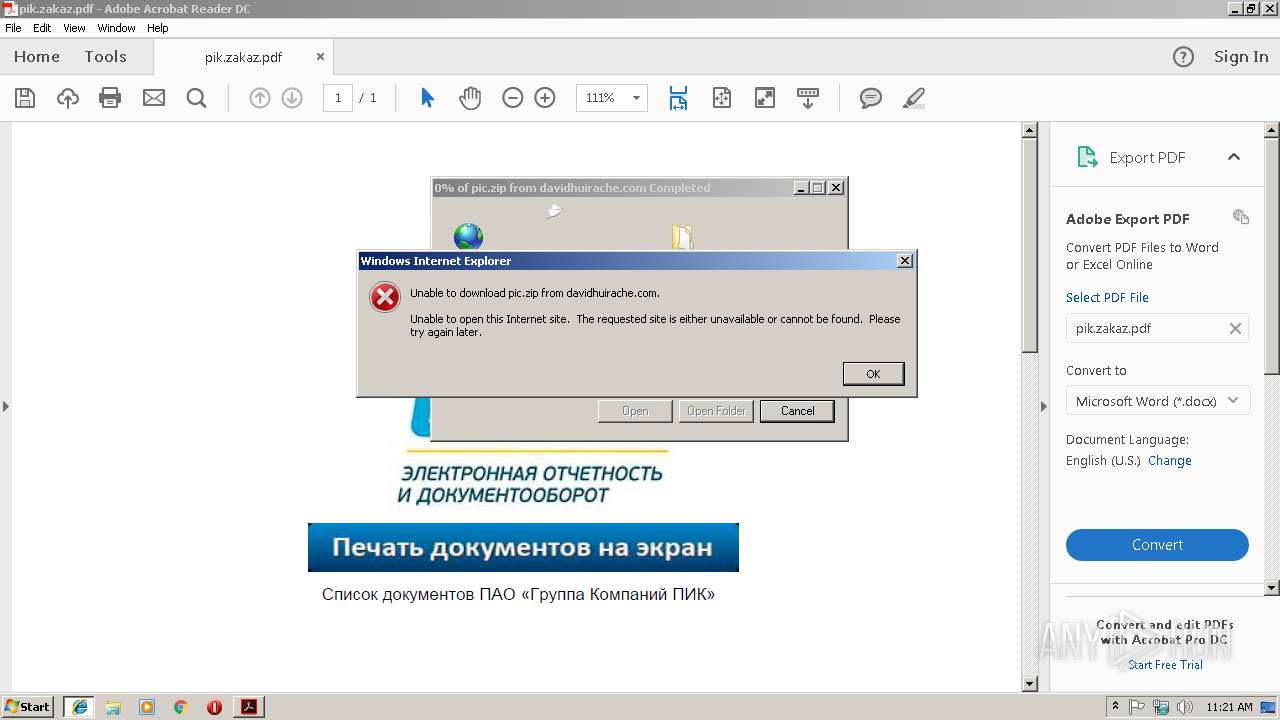
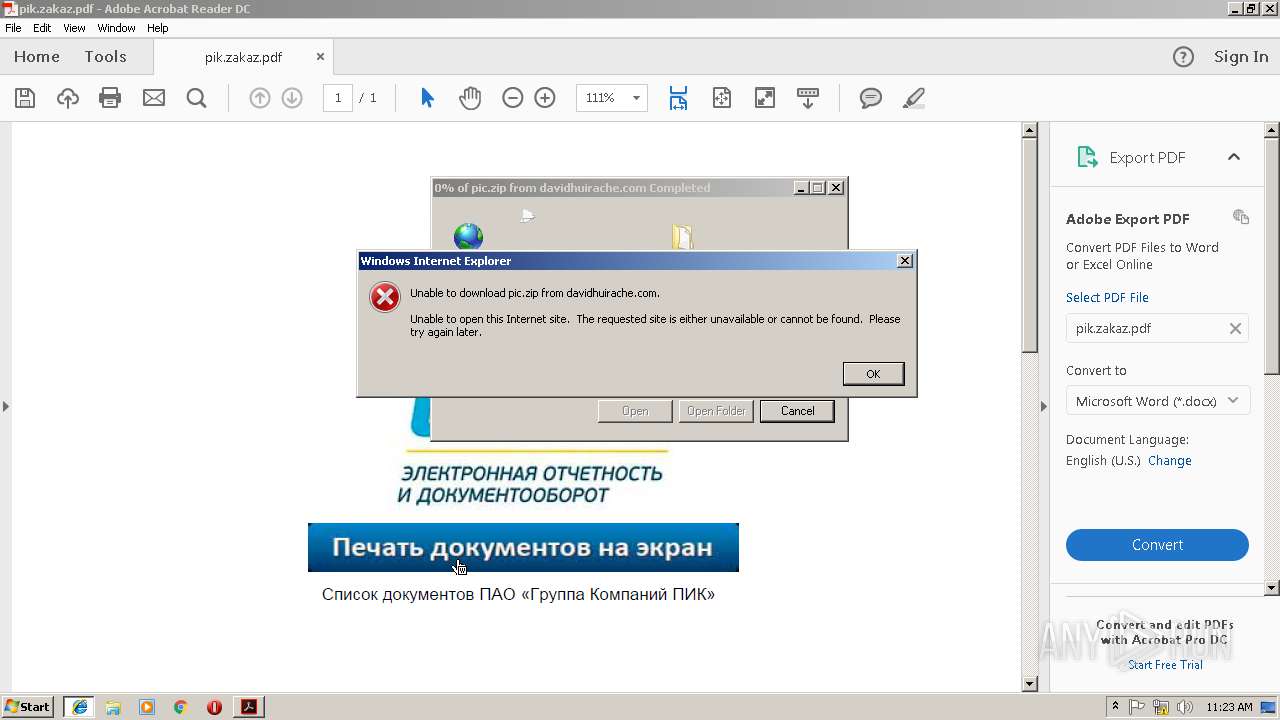
4080 | iexplore.exe | GET | 200 | 67.227.236.210:80 | http://davidhuirache.com/wp-content/themes/scholarship/template-parts/pic.zip | US | compressed | 3.35 Kb | unknown |
2496 | iexplore.exe | GET | 200 | 67.227.236.210:80 | http://davidhuirache.com/wp-content/themes/scholarship/template-parts/pic.zip | US | compressed | 3.35 Kb | unknown |
2852 | AcroRd32.exe | GET | 304 | 2.16.186.32:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/281_15_23_20070.zip | unknown | — | — | whitelisted |
2356 | iexplore.exe | GET | 200 | 67.227.236.210:80 | http://davidhuirache.com/wp-content/themes/scholarship/template-parts/pic.zip | US | compressed | 3.35 Kb | unknown |
3840 | firefox.exe | GET | 200 | 2.16.186.112:80 | http://detectportal.firefox.com/success.txt | unknown | text | 8 b | whitelisted |
3840 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
2852 | AcroRd32.exe | GET | 304 | 2.16.186.32:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/285_15_23_20070.zip | unknown | — | — | whitelisted |
3840 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
3840 | firefox.exe | POST | 200 | 216.58.206.3:80 | http://ocsp.pki.goog/GTSGIAG3 | US | der | 463 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3216 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
2356 | iexplore.exe | 67.227.236.210:80 | davidhuirache.com | Liquid Web, L.L.C | US | unknown |
2852 | AcroRd32.exe | 2.16.186.32:80 | acroipm2.adobe.com | Akamai International B.V. | — | whitelisted |
2852 | AcroRd32.exe | 2.18.233.74:443 | armmf.adobe.com | Akamai International B.V. | — | whitelisted |
— | — | 2.18.233.74:443 | armmf.adobe.com | Akamai International B.V. | — | whitelisted |
— | — | 23.210.248.251:443 | ardownload2.adobe.com | Akamai International B.V. | NL | whitelisted |
3864 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
2496 | iexplore.exe | 67.227.236.210:80 | davidhuirache.com | Liquid Web, L.L.C | US | unknown |
2308 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
4080 | iexplore.exe | 67.227.236.210:80 | davidhuirache.com | Liquid Web, L.L.C | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
davidhuirache.com |
| unknown |
armmf.adobe.com |
| whitelisted |
acroipm2.adobe.com |
| whitelisted |
ardownload2.adobe.com |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
a1089.dscd.akamai.net |
| whitelisted |
search.services.mozilla.com |
| whitelisted |
search.r53-2.services.mozilla.com |
| whitelisted |
tiles.services.mozilla.com |
| whitelisted |