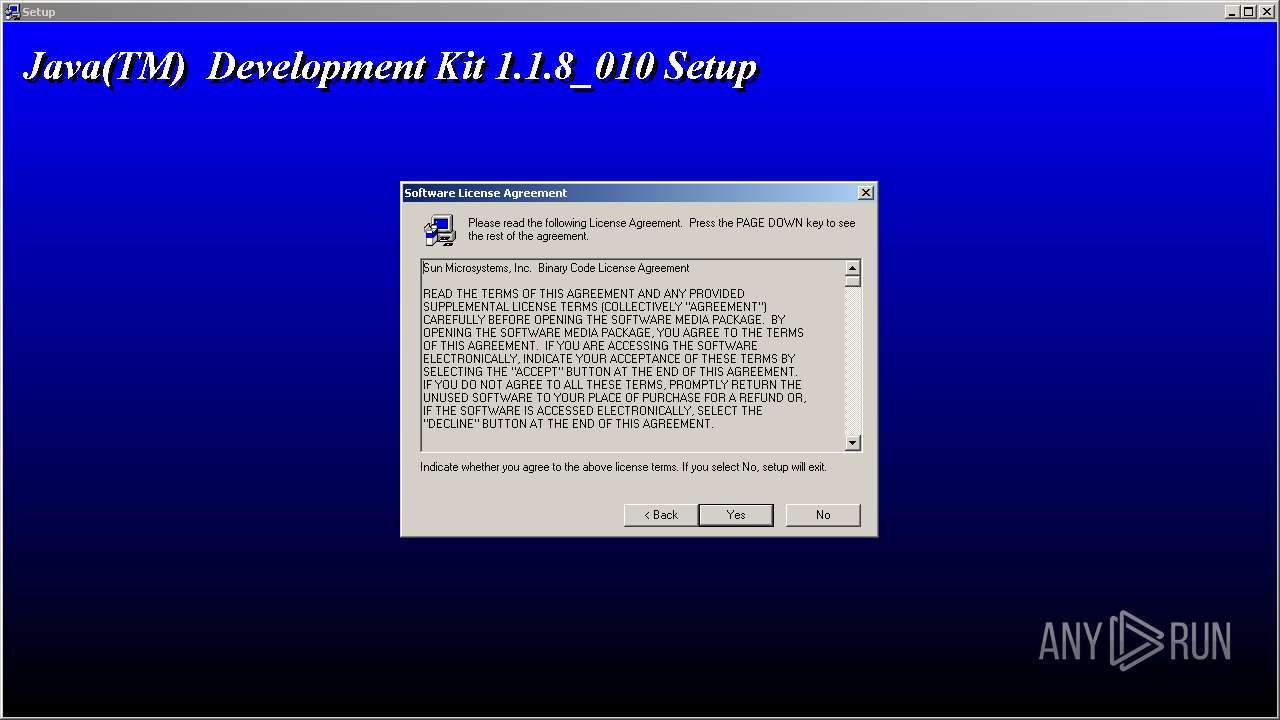
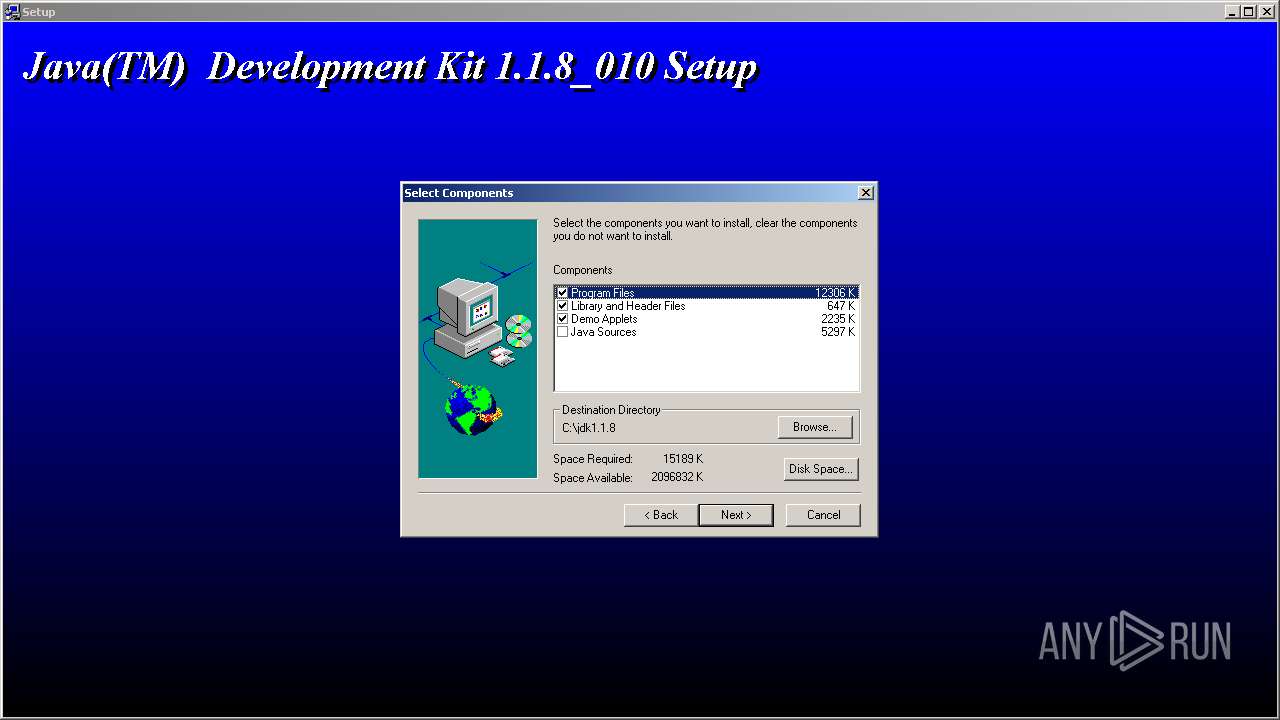
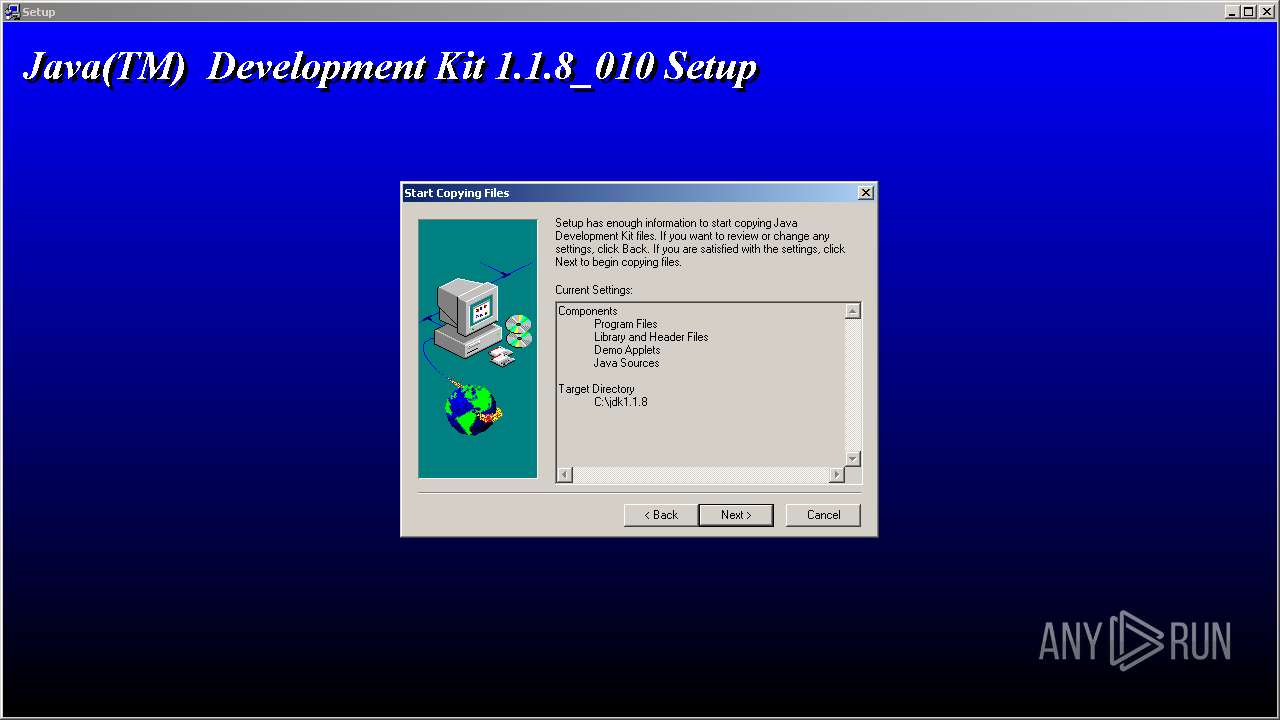
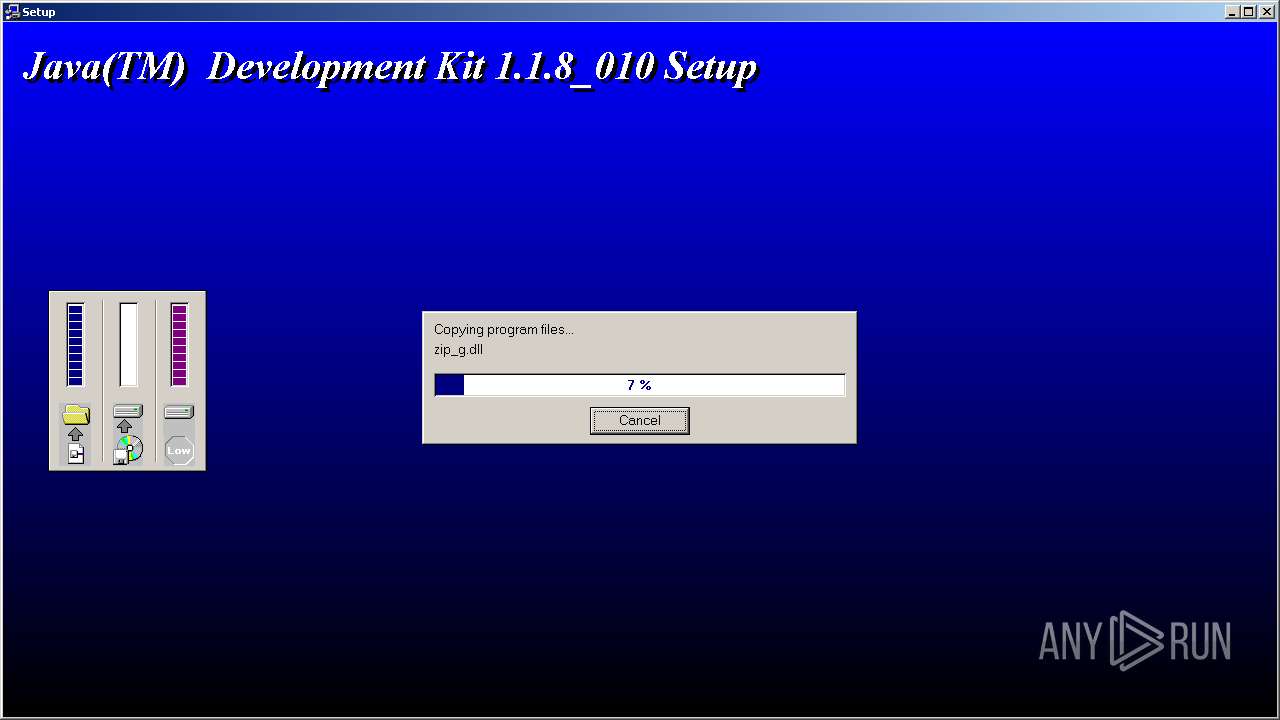
| File name: | jdk-1_1_8_010-windows-i586.exe |
| Full analysis: | https://app.any.run/tasks/0292f8f7-2325-47c0-a4e3-1889a064dd77 |
| Verdict: | Malicious activity |
| Analysis date: | June 25, 2025, 09:39:18 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 6 sections |
| MD5: | 5C78E2102F73DA5A9E11E88D3A74238D |
| SHA1: | 851114F1E396F7B2C05A2F73AA3094B80FCF0868 |
| SHA256: | 876D5BD394281B8E20E922FD3EEB56FD082EF6E7BDAC440F0F4F330777599CB7 |
| SSDEEP: | 98304:u49JsrOtuMWd6dbREAjv8KmxVe2IVvBfq5lnVCj0n0fSl5/gAClztVLjgphH6MP7:TS1AURHO5qnfj |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- jdk-1_1_8_010-windows-i586.exe (PID: 3104)
- ntvdm.exe (PID: 1116)
- _INS0432._MP (PID: 3672)
Creates file in the systems drive root
- ntvdm.exe (PID: 1116)
There is functionality for taking screenshot (YARA)
- _INS0432._MP (PID: 3672)
Starts application with an unusual extension
- ntvdm.exe (PID: 1116)
Process drops legitimate windows executable
- _INS0432._MP (PID: 3672)
Creates a software uninstall entry
- _INS0432._MP (PID: 3672)
Start notepad (likely ransomware note)
- _INS0432._MP (PID: 3672)
INFO
Create files in a temporary directory
- jdk-1_1_8_010-windows-i586.exe (PID: 3104)
- _INS0432._MP (PID: 3672)
- ntvdm.exe (PID: 1116)
Checks supported languages
- jdk-1_1_8_010-windows-i586.exe (PID: 3104)
- _INS0432._MP (PID: 3672)
Reads the computer name
- _INS0432._MP (PID: 3672)
The sample compiled with english language support
- jdk-1_1_8_010-windows-i586.exe (PID: 3104)
- ntvdm.exe (PID: 1116)
- _INS0432._MP (PID: 3672)
Manual execution by a user
- explorer.exe (PID: 2612)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ 4.x (50.4) |
|---|---|---|
| .exe | | | InstallShield setup (16.1) |
| .exe | | | Win32 Executable MS Visual C++ (generic) (11.6) |
| .exe | | | Win64 Executable (generic) (10.3) |
| .scr | | | Windows screen saver (4.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1996:12:06 20:17:50+00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 4.2 |
| CodeSize: | 75264 |
| InitializedDataSize: | 35328 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xc960 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
44
Monitored processes
6
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 328 | NOTEPAD.EXE C:\JDK11~1.8\README. | C:\Windows\System32\notepad.exe | — | _INS0432._MP | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1116 | "C:\Windows\system32\ntvdm.exe" -i1 -ws | C:\Windows\System32\ntvdm.exe | jdk-1_1_8_010-windows-i586.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: NTVDM.EXE Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2612 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3104 | "C:\Users\admin\Downloads\jdk-1_1_8_010-windows-i586.exe" | C:\Users\admin\Downloads\jdk-1_1_8_010-windows-i586.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3232 | "C:\Users\admin\Downloads\jdk-1_1_8_010-windows-i586.exe" | C:\Users\admin\Downloads\jdk-1_1_8_010-windows-i586.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 3672 | C:\Users\admin\AppData\Local\Temp\_INS0432._MP | C:\Users\admin\AppData\Local\Temp\_INS0432._MP | ntvdm.exe | ||||||||||||
User: admin Company: InstallShield Corporation, Inc. Integrity Level: HIGH Description: InstallShield Engine EXE Exit code: 0 Version: 3.00.118.0 Modules
| |||||||||||||||
Total events
459
Read events
453
Write events
6
Delete events
0
Modification events
| (PID) Process: | (3672) _INS0432._MP | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\App Paths\java.exe |
| Operation: | write | Name: | Path |
Value: C:\jdk1.1.8\bin | |||
| (PID) Process: | (3672) _INS0432._MP | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\JDK 1.1 |
| Operation: | write | Name: | UninstallString |
Value: C:\Windows\uninst.exe -fC:\jdk1.1.8\lib\DeIsL1.isu | |||
| (PID) Process: | (3672) _INS0432._MP | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\JDK 1.1 |
| Operation: | write | Name: | DisplayName |
Value: Java Development Kit 1.1 | |||
| (PID) Process: | (3672) _INS0432._MP | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\JavaSoft\Java Development Kit |
| Operation: | write | Name: | CurrentVersion |
Value: 1.1 | |||
| (PID) Process: | (3672) _INS0432._MP | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\JavaSoft\Java Development Kit\1.1 |
| Operation: | write | Name: | JavaHome |
Value: C:\jdk1.1.8 | |||
| (PID) Process: | (3672) _INS0432._MP | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\JavaSoft\Java Development Kit\1.1 |
| Operation: | write | Name: | MicroVersion |
Value: 8 | |||
Executable files
111
Suspicious files
25
Text files
959
Unknown types
182
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3104 | jdk-1_1_8_010-windows-i586.exe | C:\Users\admin\AppData\Local\Temp\~EXB0000\java.z | — | |
MD5:— | SHA256:— | |||
| 3104 | jdk-1_1_8_010-windows-i586.exe | C:\Users\admin\AppData\Local\Temp\~EXB0000\src.z | — | |
MD5:— | SHA256:— | |||
| 3104 | jdk-1_1_8_010-windows-i586.exe | C:\Users\admin\AppData\Local\Temp\~EXB0000\~IS_CMPX.~~~ | compressed | |
MD5:3CE774BBC0A6A52AE3D60725599C9EAA | SHA256:63F70C2A43A251462BDF21C19BF1134DFD7AD7D414685C851619AD44BF074E9C | |||
| 1116 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\_INZ0432._MP | executable | |
MD5:7DE04B1D19D78B46F50502F7272008CF | SHA256:4BA67538ADB2EF218EB33B0E9FBA4EC3F8D7D51D75CC3CCFD78769FDB7701CE1 | |||
| 1116 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\scs24CA.tmp | text | |
MD5:4C361DEA398F7AEEF49953BDC0AB4A9B | SHA256:06D61C23E6CA59B9DDAD1796ECCC42C032CD8F6F424AF6CFEE5D085D36FF7DFD | |||
| 3104 | jdk-1_1_8_010-windows-i586.exe | C:\Users\admin\AppData\Local\Temp\~EXB0000\_INST32I.EX_ | ??_ | |
MD5:AC76C9D10E6912D40813DC412D29A29E | SHA256:D1FA52F6DD4C3D445D725B1733AC937C7026AEF10143B83B5CD0A98F7181F26E | |||
| 1116 | ntvdm.exe | C:\Windows\_iserr31.ini | text | |
MD5:057F7E2920E8106BBB241C4F6C23B984 | SHA256:5E766188E19821E16AC154D4E28CBDE7FF1085075AC63D33FF935565F6DDFEB2 | |||
| 1116 | ntvdm.exe | C:\Users\admin\AppData\Local\Temp\_WUTL95.DLL | executable | |
MD5:5EAE709B026CDD054467640EC6EA0B44 | SHA256:24358C5E1A6AB94265FE169F9435BF1EE99B086BA283C33CAEB985F1E1F6F082 | |||
| 3104 | jdk-1_1_8_010-windows-i586.exe | C:\Users\admin\AppData\Local\Temp\~EXB0000\uninst.exe | executable | |
MD5:9CA884A033A9013EF939FF6554586200 | SHA256:F833E2754538F5B569674AE17D2F84AD7B16C362D1F949BC23B83983EF1BFF5E | |||
| 3104 | jdk-1_1_8_010-windows-i586.exe | C:\Users\admin\AppData\Local\Temp\~EXB0000\setup.pkg | binary | |
MD5:4D1BF848A28F7DF36CD24909B0B4B08D | SHA256:F73587D390D4F6F030BBC325D8DE95ADED4D9E43B564469D8DA10C2AE19744FE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
6
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |