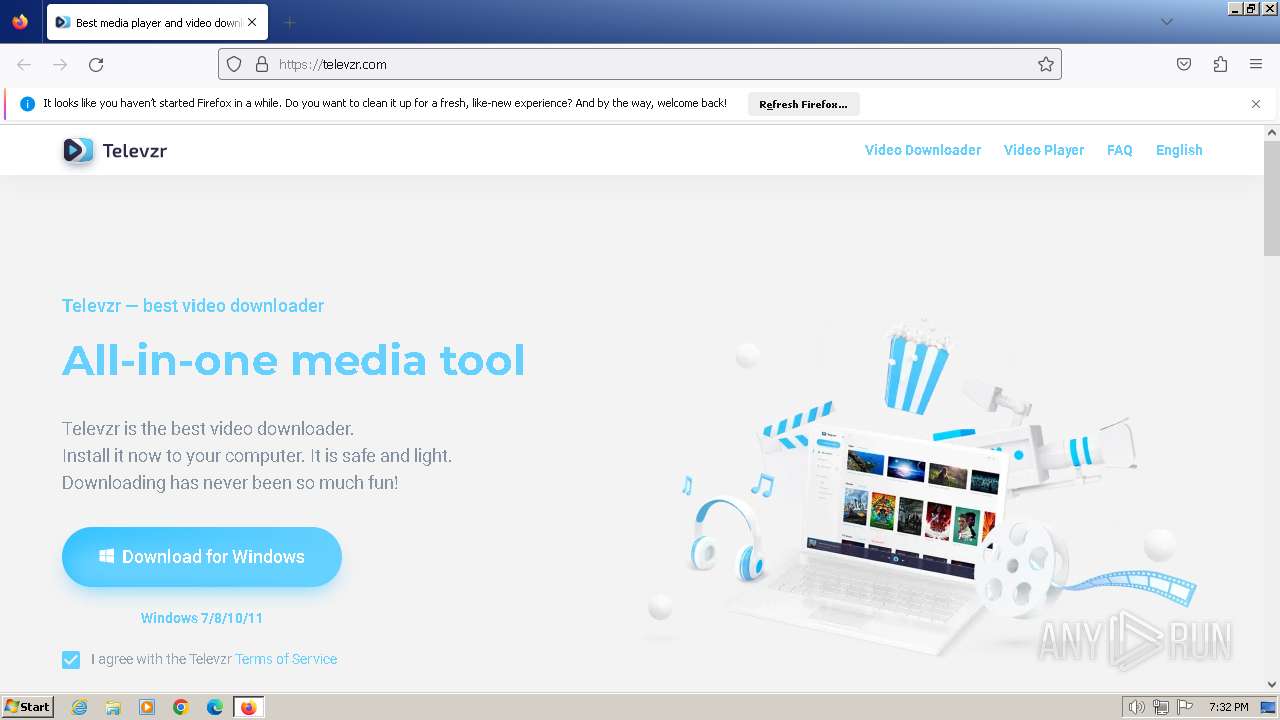
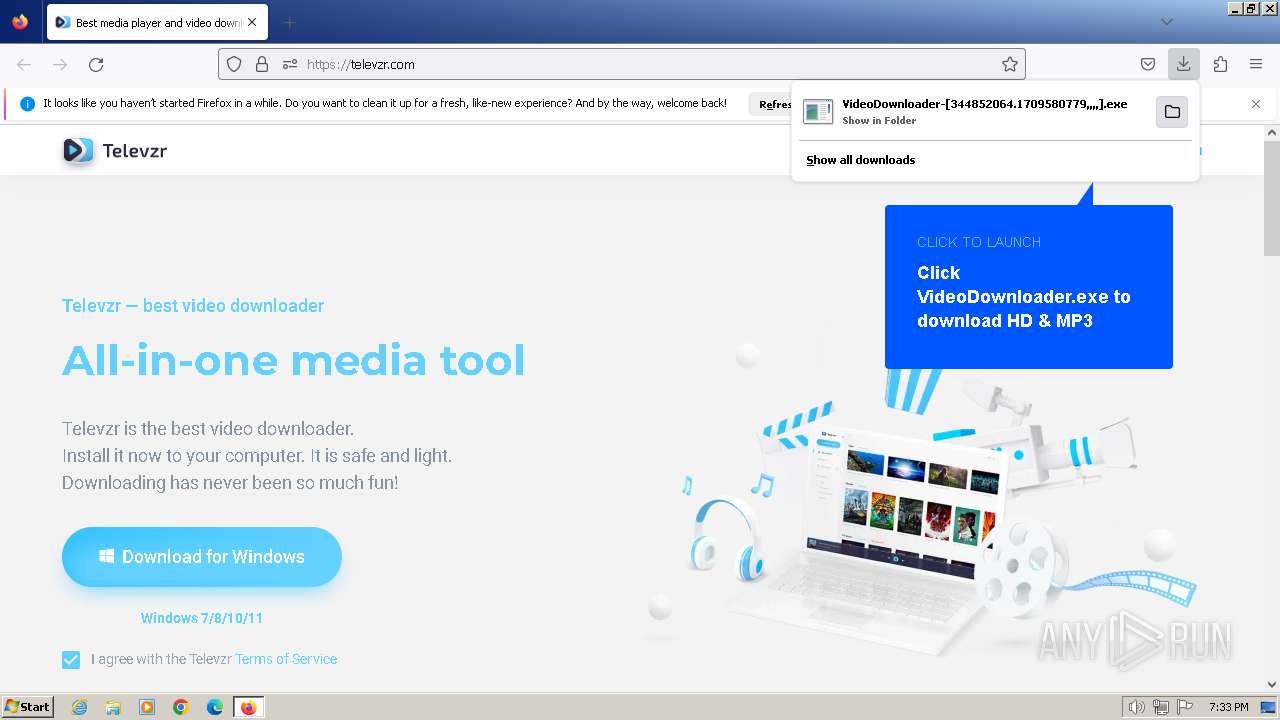
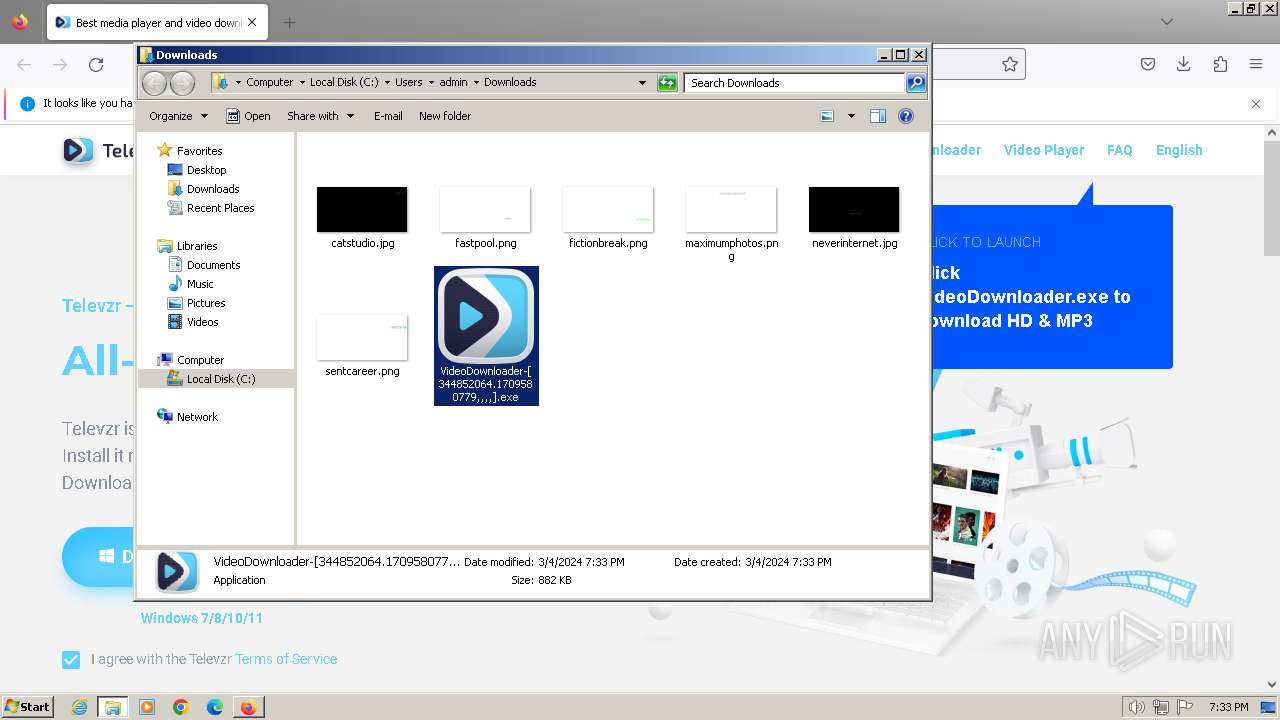
| URL: | televzr.com |
| Full analysis: | https://app.any.run/tasks/04566dcb-7824-4277-8496-f36f5d2d5485 |
| Verdict: | Malicious activity |
| Analysis date: | March 04, 2024, 19:32:46 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 4B555C149121D097D9CD6CE3FA28583A |
| SHA1: | 7C7F07D6D5EBED71099ADDE15D5524B519D159FE |
| SHA256: | 876ACE9CC61E0F399FE2E58FE7FE6ABDD8215547B68EBFFEEEF9AE8819669709 |
| SSDEEP: | 3:/vGT:/i |
MALICIOUS
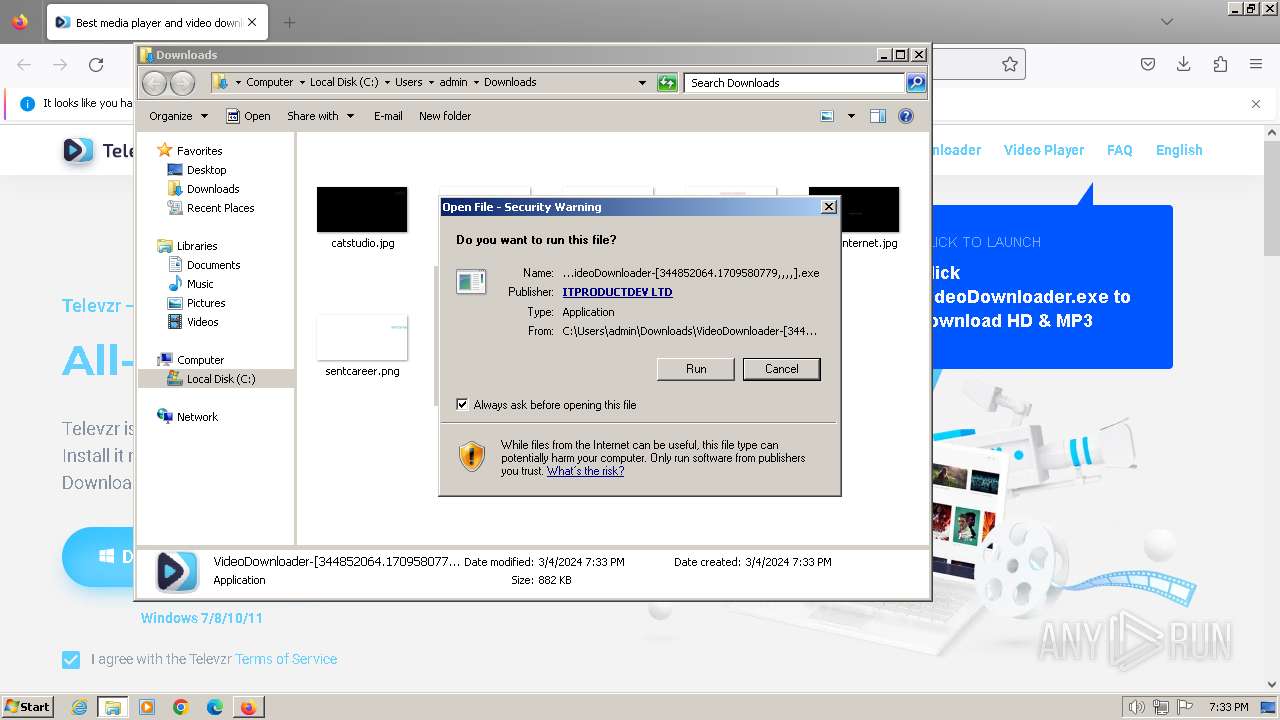
Drops the executable file immediately after the start
- VideoDownloader-[344852064.1709580779,,,,].exe (PID: 2512)
- vcredist_x86.exe (PID: 1028)
Actions looks like stealing of personal data
- Televzr.exe (PID: 3548)
SUSPICIOUS
Starts CMD.EXE for commands execution
- nsC5BE.tmp (PID: 2524)
- nsD2A0.tmp (PID: 3748)
Starts application with an unusual extension
- cmd.exe (PID: 3840)
- VideoDownloader-[344852064.1709580779,,,,].exe (PID: 2512)
Get information on the list of running processes
- VideoDownloader-[344852064.1709580779,,,,].exe (PID: 2512)
- nsD2A0.tmp (PID: 3748)
- cmd.exe (PID: 3604)
Malware-specific behavior (creating "System.dll" in Temp)
- VideoDownloader-[344852064.1709580779,,,,].exe (PID: 2512)
The process creates files with name similar to system file names
- VideoDownloader-[344852064.1709580779,,,,].exe (PID: 2512)
Executable content was dropped or overwritten
- VideoDownloader-[344852064.1709580779,,,,].exe (PID: 2512)
- vcredist_x86.exe (PID: 1028)
Reads the Internet Settings
- VideoDownloader-[344852064.1709580779,,,,].exe (PID: 2512)
- Televzr.exe (PID: 3824)
Reads security settings of Internet Explorer
- VideoDownloader-[344852064.1709580779,,,,].exe (PID: 2512)
- Setup.exe (PID: 4040)
Checks Windows Trust Settings
- VideoDownloader-[344852064.1709580779,,,,].exe (PID: 2512)
- Setup.exe (PID: 4040)
Reads settings of System Certificates
- VideoDownloader-[344852064.1709580779,,,,].exe (PID: 2512)
- Setup.exe (PID: 4040)
- Televzr.exe (PID: 3824)
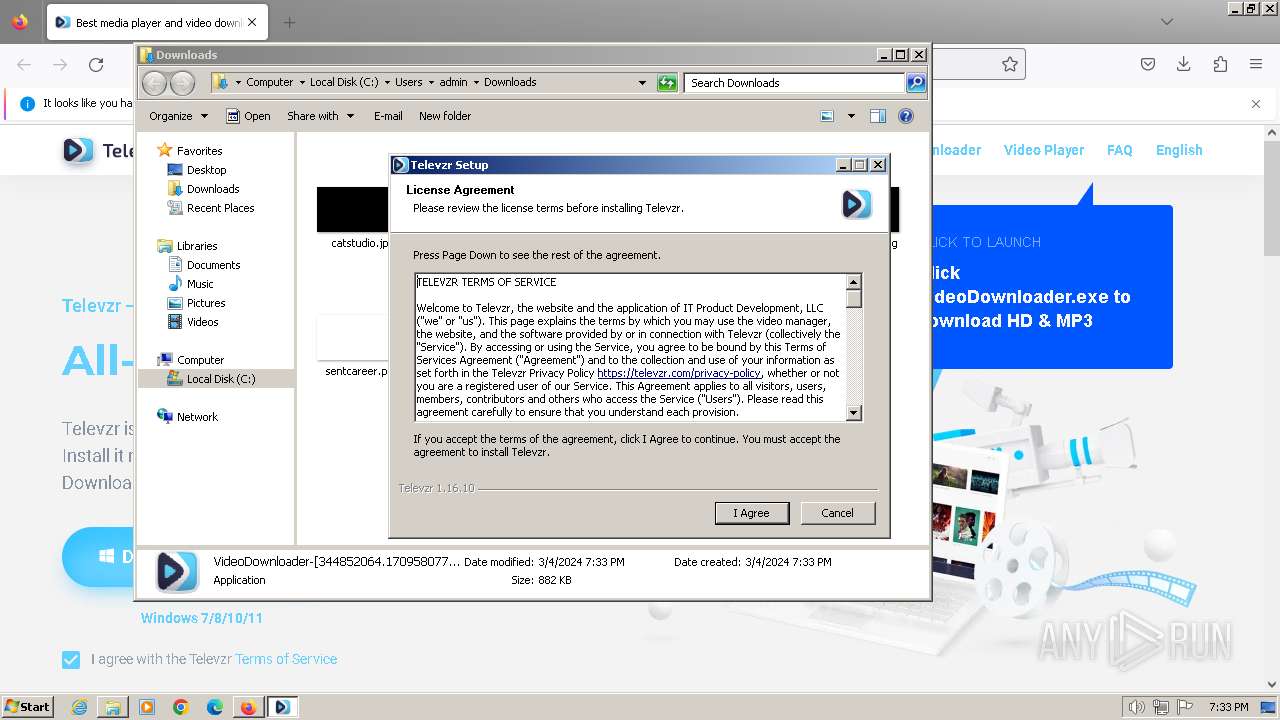
Drops 7-zip archiver for unpacking
- VideoDownloader-[344852064.1709580779,,,,].exe (PID: 2512)
Process drops legitimate windows executable
- VideoDownloader-[344852064.1709580779,,,,].exe (PID: 2512)
- vcredist_x86.exe (PID: 1028)
Creates a software uninstall entry
- VideoDownloader-[344852064.1709580779,,,,].exe (PID: 2512)
Starts a Microsoft application from unusual location
- vcredist_x86.exe (PID: 3024)
- vcredist_x86.exe (PID: 1028)
Application launched itself
- Televzr.exe (PID: 3824)
Uses REG/REGEDIT.EXE to modify registry
- Televzr.exe (PID: 3824)
INFO
Application launched itself
- firefox.exe (PID: 3864)
- firefox.exe (PID: 4052)
The process uses the downloaded file
- firefox.exe (PID: 4052)
- cmd.exe (PID: 3840)
Checks supported languages
- nsC5BE.tmp (PID: 2524)
- more.com (PID: 3572)
- VideoDownloader-[344852064.1709580779,,,,].exe (PID: 2512)
- nsD2A0.tmp (PID: 3748)
- wmpnscfg.exe (PID: 2168)
- vcredist_x86.exe (PID: 1028)
- Setup.exe (PID: 4040)
- Televzr.exe (PID: 3824)
- Televzr.exe (PID: 3852)
- Televzr.exe (PID: 2436)
- Televzr.exe (PID: 2320)
- Televzr.exe (PID: 764)
- Televzr.exe (PID: 3548)
Reads the computer name
- VideoDownloader-[344852064.1709580779,,,,].exe (PID: 2512)
- wmpnscfg.exe (PID: 2168)
- vcredist_x86.exe (PID: 1028)
- Setup.exe (PID: 4040)
- Televzr.exe (PID: 2436)
- Televzr.exe (PID: 3824)
- Televzr.exe (PID: 2320)
- Televzr.exe (PID: 764)
Manual execution by a user
- VideoDownloader-[344852064.1709580779,,,,].exe (PID: 2512)
- wmpnscfg.exe (PID: 2168)
- Televzr.exe (PID: 3824)
Create files in a temporary directory
- VideoDownloader-[344852064.1709580779,,,,].exe (PID: 2512)
- Setup.exe (PID: 4040)
- Televzr.exe (PID: 3824)
Drops the executable file immediately after the start
- firefox.exe (PID: 4052)
Executable content was dropped or overwritten
- firefox.exe (PID: 4052)
Checks proxy server information
- VideoDownloader-[344852064.1709580779,,,,].exe (PID: 2512)
Reads the machine GUID from the registry
- VideoDownloader-[344852064.1709580779,,,,].exe (PID: 2512)
- vcredist_x86.exe (PID: 1028)
- Setup.exe (PID: 4040)
- Televzr.exe (PID: 3824)
Reads the software policy settings
- VideoDownloader-[344852064.1709580779,,,,].exe (PID: 2512)
- Setup.exe (PID: 4040)
- Televzr.exe (PID: 3824)
Creates files or folders in the user directory
- VideoDownloader-[344852064.1709580779,,,,].exe (PID: 2512)
- Televzr.exe (PID: 3824)
- Televzr.exe (PID: 2320)
- Televzr.exe (PID: 3548)
Reads Environment values
- vcredist_x86.exe (PID: 1028)
- Televzr.exe (PID: 3824)
Reads CPU info
- Setup.exe (PID: 4040)
Reads product name
- Televzr.exe (PID: 3824)
Process checks computer location settings
- Televzr.exe (PID: 3852)
- Televzr.exe (PID: 3824)
- Televzr.exe (PID: 3548)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
128
Monitored processes
55
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 268 | C:\Windows\system32\reg.exe ADD HKCU\Software\Classes\.mkv\OpenWithProgids /v televzr /t REG_SZ /d "" /f | C:\Windows\System32\reg.exe | — | Televzr.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 296 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="4052.8.1094295048\283023696" -childID 7 -isForBrowser -prefsHandle 4072 -prefMapHandle 4076 -prefsLen 34336 -prefMapSize 244195 -jsInitHandle 924 -jsInitLen 240908 -parentBuildID 20230710165010 -appDir "C:\Program Files\Mozilla Firefox\browser" - {d84d3f87-d9fb-4d58-8073-c984659473f6} 4052 "\\.\pipe\gecko-crash-server-pipe.4052" 4060 18d4ec90 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 115.0.2 Modules
| |||||||||||||||
| 584 | C:\Windows\system32\reg.exe QUERY HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\\UserChoice /v ProgId | C:\Windows\System32\reg.exe | — | Televzr.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 764 | "C:\Users\admin\AppData\Local\televzr\Televzr.exe" --type=gpu-process --field-trial-handle=1112,18000975110326218887,13871539214139691817,131072 --disable-features=CookiesWithoutSameSiteMustBeSecure,HardwareMediaKeyHandling,SameSiteByDefaultCookies,SpareRendererForSitePerProcess,WinRetrieveSuggestionsOnlyOnDemand --no-sandbox --user-data-dir="C:\Users\admin\AppData\Roaming\Televzr Desktop" --gpu-preferences=UAAAAAAAAADgAAAQAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAHgAAAAAAAAAeAAAAAAAAAAoAAAABAAAACAAAAAAAAAAKAAAAAAAAAAwAAAAAAAAADgAAAAAAAAAEAAAAAAAAAAAAAAADQAAABAAAAAAAAAAAQAAAA0AAAAQAAAAAAAAAAQAAAANAAAAEAAAAAAAAAAHAAAADQAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=angle --use-angle=swiftshader-webgl --mojo-platform-channel-handle=1132 /prefetch:2 | C:\Users\admin\AppData\Local\televzr\Televzr.exe | — | Televzr.exe | |||||||||||
User: admin Company: ITPRODUCTDEV LTD Integrity Level: MEDIUM Description: Televzr Exit code: 0 Version: 1.16.10 Modules
| |||||||||||||||
| 896 | C:\Windows\system32\reg.exe ADD HKCU\Software\Classes\televzr\shell\open\command /f | C:\Windows\System32\reg.exe | — | Televzr.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1028 | "C:\Users\admin\AppData\Local\Temp\nsnC59E.tmp\vcredist_x86.exe" /install /quiet /norestart | C:\Users\admin\AppData\Local\Temp\nsnC59E.tmp\vcredist_x86.exe | VideoDownloader-[344852064.1709580779,,,,].exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Visual C++ 2010 x86 Redistributable Setup Exit code: 0 Version: 10.0.40219.325 Modules
| |||||||||||||||
| 1432 | C:\Windows\system32\reg.exe QUERY "HKCU\Software\Classes\(value not set)\shell\open\command" /ve | C:\Windows\System32\reg.exe | — | Televzr.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1504 | C:\Windows\system32\reg.exe QUERY HKCU\Software\Classes\ /ve | C:\Windows\System32\reg.exe | — | Televzr.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1588 | C:\Windows\system32\reg.exe QUERY "HKCU\Software\Classes\(value not set)\shell\open\command" /ve | C:\Windows\System32\reg.exe | — | Televzr.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1596 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="4052.6.807669405\2055333510" -childID 5 -isForBrowser -prefsHandle 3712 -prefMapHandle 3708 -prefsLen 29209 -prefMapSize 244195 -jsInitHandle 924 -jsInitLen 240908 -parentBuildID 20230710165010 -appDir "C:\Program Files\Mozilla Firefox\browser" - {b1dd6459-d1af-4d39-b1f1-6178c8a5975b} 4052 "\\.\pipe\gecko-crash-server-pipe.4052" 3748 19377280 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 115.0.2 Modules
| |||||||||||||||
Total events
38 387
Read events
38 183
Write events
187
Delete events
17
Modification events
| (PID) Process: | (3864) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Launcher |
Value: 82223A4F01000000 | |||
| (PID) Process: | (4052) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Browser |
Value: 090D3C4F01000000 | |||
| (PID) Process: | (4052) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Installer\308046B0AF4A39CB |
| Operation: | delete value | Name: | installer.taskbarpin.win10.enabled |
Value: | |||
| (PID) Process: | (4052) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Telemetry |
Value: 0 | |||
| (PID) Process: | (4052) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (4052) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\PreXULSkeletonUISettings |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Theme |
Value: 1 | |||
| (PID) Process: | (4052) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\PreXULSkeletonUISettings |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Enabled |
Value: 1 | |||
| (PID) Process: | (4052) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|DisableTelemetry |
Value: 1 | |||
| (PID) Process: | (4052) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|DisableDefaultBrowserAgent |
Value: 0 | |||
| (PID) Process: | (4052) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|SetDefaultBrowserUserChoice |
Value: 1 | |||
Executable files
59
Suspicious files
260
Text files
129
Unknown types
114
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4052 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\urlCache-current.bin | binary | |
MD5:B7A3C61D0C144CC5E166B1E769CA8F8C | SHA256:7FADCB77FFACA6B9E9F15C6F1CD3AAD4C20DCD90FA92429A627A3A7110CA2644 | |||
| 4052 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\sessionCheckpoints.json | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 4052 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 4052 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 4052 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\prefs-1.js | text | |
MD5:60E0DE9E05EC76C749D80F0D15A81B21 | SHA256:08252FA62CCCCD316474E20CC7317A6B5C932B2C972234318E8CCDA39EC2EF48 | |||
| 4052 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\prefs.js | text | |
MD5:60E0DE9E05EC76C749D80F0D15A81B21 | SHA256:08252FA62CCCCD316474E20CC7317A6B5C932B2C972234318E8CCDA39EC2EF48 | |||
| 4052 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\2823318777ntouromlalnodry--naod.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 4052 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\1451318868ntouromlalnodry--epcr.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 4052 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 4052 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\3561288849sdhlie.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
38
TCP/UDP connections
115
DNS requests
187
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4052 | firefox.exe | GET | 301 | 104.21.63.211:80 | http://televzr.com/ | unknown | — | — | unknown |
4052 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | text | 90 b | unknown |
4052 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | text | 8 b | unknown |
4052 | firefox.exe | POST | 200 | 142.250.185.131:80 | http://ocsp.pki.goog/gts1c3 | unknown | binary | 472 b | unknown |
4052 | firefox.exe | POST | 200 | 142.250.185.131:80 | http://ocsp.pki.goog/gts1c3 | unknown | binary | 471 b | unknown |
4052 | firefox.exe | POST | — | 142.250.185.131:80 | http://ocsp.pki.goog/gts1c3 | unknown | — | — | unknown |
4052 | firefox.exe | POST | 200 | 142.250.185.131:80 | http://ocsp.pki.goog/gts1c3 | unknown | binary | 472 b | unknown |
4052 | firefox.exe | POST | 200 | 142.250.185.131:80 | http://ocsp.pki.goog/gts1c3 | unknown | binary | 472 b | unknown |
4052 | firefox.exe | POST | 200 | 184.24.77.54:80 | http://r3.o.lencr.org/ | unknown | binary | 503 b | unknown |
4052 | firefox.exe | POST | 200 | 184.24.77.54:80 | http://r3.o.lencr.org/ | unknown | binary | 503 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4052 | firefox.exe | 104.21.63.211:443 | televzr.com | — | — | unknown |
4052 | firefox.exe | 104.21.63.211:80 | televzr.com | CLOUDFLARENET | — | unknown |
4052 | firefox.exe | 142.250.184.234:443 | safebrowsing.googleapis.com | — | — | whitelisted |
4052 | firefox.exe | 34.107.243.93:443 | push.services.mozilla.com | GOOGLE | US | unknown |
4052 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
4052 | firefox.exe | 34.149.100.209:443 | firefox.settings.services.mozilla.com | GOOGLE | US | unknown |
4052 | firefox.exe | 34.117.237.239:443 | contile.services.mozilla.com | GOOGLE-CLOUD-PLATFORM | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
televzr.com |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
example.org |
| whitelisted |
ipv4only.arpa |
| whitelisted |
spocs.getpocket.com |
| shared |
gkegw.prod.ads.prod.webservices.mozgcp.net |
| unknown |
r3.o.lencr.org |
| shared |
firefox.settings.services.mozilla.com |
| whitelisted |
Threats
Process | Message |
|---|---|
Setup.exe | The operation completed successfully.
|