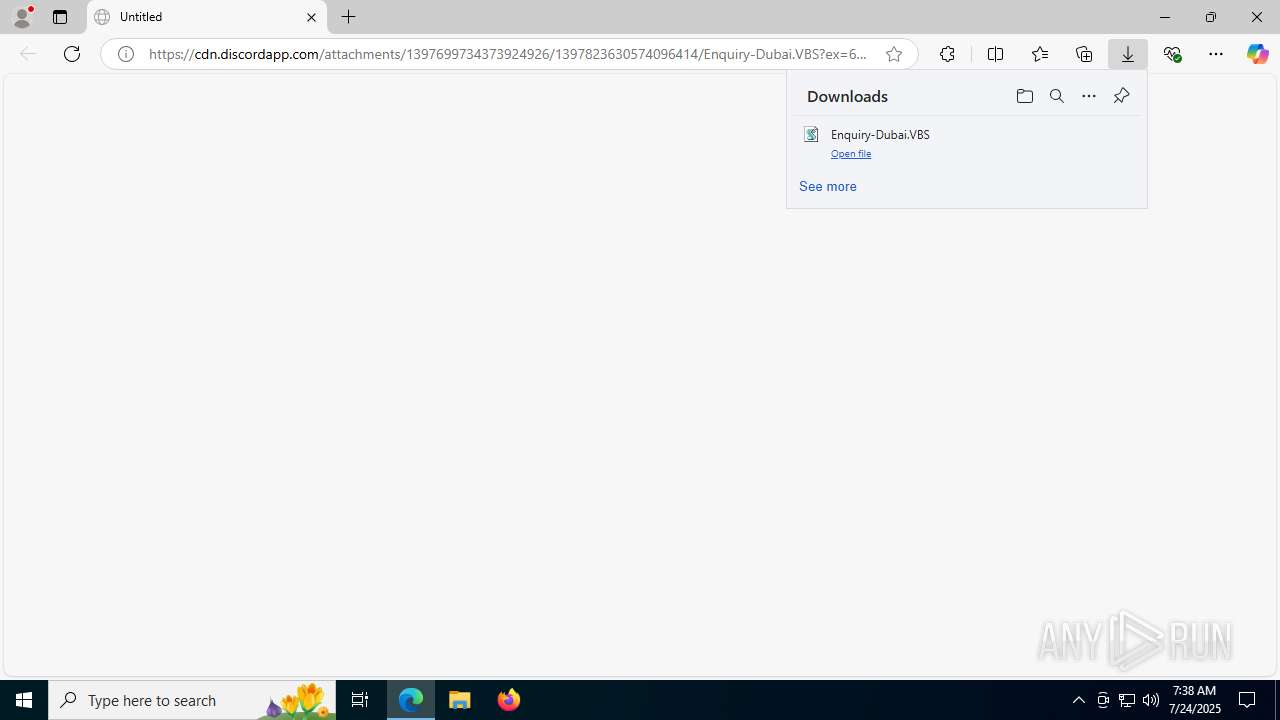
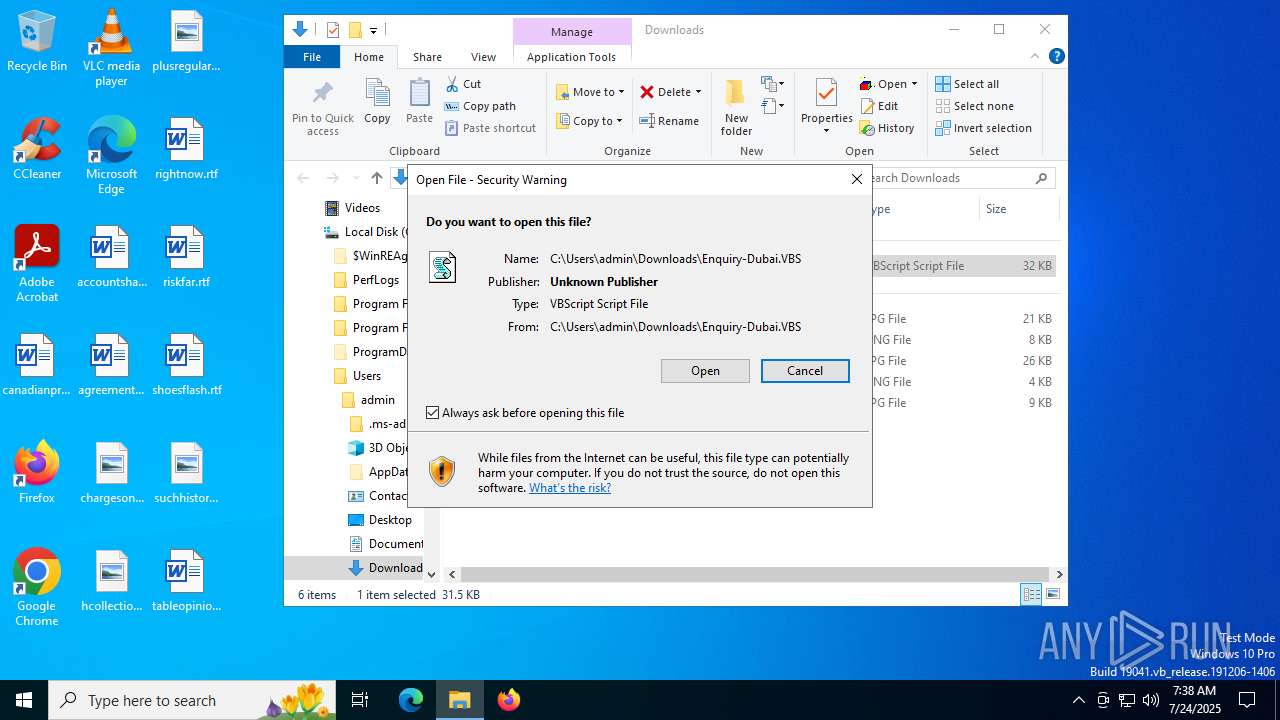
| URL: | https://cdn.discordapp.com/attachments/1397699734373924926/1397823630574096414/Enquiry-Dubai.VBS?ex=68832033&is=6881ceb3&hm=ecb9191bf36cb9ef9d61d083a844a1bd93eb0553f022ba6e98fcda6c9de16ed1& |
| Full analysis: | https://app.any.run/tasks/aad63231-2157-4efa-9793-7a8914384e97 |
| Verdict: | Malicious activity |
| Analysis date: | July 24, 2025, 07:37:57 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 3956B886C87BBE9E7C451719628D005C |
| SHA1: | 1BEA847493700F6BF9FB45B035D2281E1616276F |
| SHA256: | 8761EDAB0A5ACC90A07DE736CA871C02CD59DDF97BABF8929B7D63FB545F346C |
| SSDEEP: | 3:N8cCWdy6//PcgcqWDHSVyOJ72aVSFWuGQGFdKTGWTUjdnxcVFE9qKUF:2cry6XPcgcT7SBJBgHG2rUjdnx2FmUF |
MALICIOUS
Sends HTTP request (SCRIPT)
- wscript.exe (PID: 7640)
Creates internet connection object (SCRIPT)
- wscript.exe (PID: 7640)
Opens an HTTP connection (SCRIPT)
- wscript.exe (PID: 7640)
Changes powershell execution policy (Bypass)
- wscript.exe (PID: 7640)
Bypass execution policy to execute commands
- powershell.exe (PID: 7720)
Run PowerShell with an invisible window
- powershell.exe (PID: 7720)
SUSPICIOUS
Discord domain found in command line (probably downloading payload)
- msedge.exe (PID: 2228)
Runs shell command (SCRIPT)
- wscript.exe (PID: 7640)
Adds, changes, or deletes HTTP request header (SCRIPT)
- wscript.exe (PID: 7640)
Starts POWERSHELL.EXE for commands execution
- wscript.exe (PID: 7640)
Possibly malicious use of IEX has been detected
- wscript.exe (PID: 7640)
The process bypasses the loading of PowerShell profile settings
- wscript.exe (PID: 7640)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 7720)
INFO
Checks supported languages
- identity_helper.exe (PID: 7532)
- identity_helper.exe (PID: 6648)
Reads Environment values
- identity_helper.exe (PID: 6648)
- identity_helper.exe (PID: 7532)
Application launched itself
- msedge.exe (PID: 2228)
- msedge.exe (PID: 7308)
Reads the computer name
- identity_helper.exe (PID: 7532)
- identity_helper.exe (PID: 6648)
Manual execution by a user
- wscript.exe (PID: 7640)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 7720)
Found Base64 encoded text manipulation via PowerShell (YARA)
- powershell.exe (PID: 7720)
Found Base64 encoded spyware-related PowerShell classes (YARA)
- powershell.exe (PID: 7720)
Disables trace logs
- powershell.exe (PID: 7720)
Gets data length (POWERSHELL)
- powershell.exe (PID: 7720)
Found Base64 encoded access to BitConverter class via PowerShell (YARA)
- powershell.exe (PID: 7720)
Found Base64 encoded reflection usage via PowerShell (YARA)
- powershell.exe (PID: 7720)
Checks proxy server information
- powershell.exe (PID: 7720)
- slui.exe (PID: 6004)
Failed to connect to remote server (POWERSHELL)
- powershell.exe (PID: 7720)
Reads the software policy settings
- slui.exe (PID: 6004)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7720)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
192
Monitored processes
46
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1132 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --extension-process --renderer-sub-type=extension --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --always-read-main-dll --field-trial-handle=4272,i,8468028653023983604,16486564214162316230,262144 --variations-seed-version --mojo-platform-channel-handle=4280 /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1148 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --message-loop-type-ui --string-annotations --always-read-main-dll --field-trial-handle=1624,i,6508273114773732216,14661620087181025297,262144 --variations-seed-version --mojo-platform-channel-handle=5184 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1244 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=entity_extraction_service.mojom.Extractor --lang=en-US --service-sandbox-type=entity_extraction --disable-quic --onnx-enabled-for-ee --string-annotations --always-read-main-dll --field-trial-handle=4980,i,8468028653023983604,16486564214162316230,262144 --variations-seed-version --mojo-platform-channel-handle=5092 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1576 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=133.0.6943.142 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 --annotation=prod=Edge --annotation=ver=133.0.3065.92 --initial-client-data=0x304,0x308,0x30c,0x2fc,0x314,0x7ffc43cbf208,0x7ffc43cbf214,0x7ffc43cbf220 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2168 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=5312,i,6508273114773732216,14661620087181025297,262144 --variations-seed-version --mojo-platform-channel-handle=5636 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2200 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2228 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" "https://cdn.discordapp.com/attachments/1397699734373924926/1397823630574096414/Enquiry-Dubai.VBS?ex=68832033&is=6881ceb3&hm=ecb9191bf36cb9ef9d61d083a844a1bd93eb0553f022ba6e98fcda6c9de16ed1&" | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2528 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --extension-process --renderer-sub-type=extension --pdf-upsell-enabled --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --always-read-main-dll --field-trial-handle=3684,i,6508273114773732216,14661620087181025297,262144 --variations-seed-version --mojo-platform-channel-handle=3712 /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2612 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=5604,i,6508273114773732216,14661620087181025297,262144 --variations-seed-version --mojo-platform-channel-handle=4264 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2620 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=5640,i,6508273114773732216,14661620087181025297,262144 --variations-seed-version --mojo-platform-channel-handle=5636 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
Total events
15 219
Read events
15 199
Write events
20
Delete events
0
Modification events
| (PID) Process: | (2228) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2228) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2228) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2228) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (2228) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: A5E06A303E992F00 | |||
| (PID) Process: | (2228) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\459528 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {A724BEDC-998C-4BB3-83ED-31AAF2191ABB} | |||
| (PID) Process: | (2228) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\EdgeUpdate\Clients\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\Commands\on-logon-autolaunch |
| Operation: | write | Name: | Enabled |
Value: 0 | |||
| (PID) Process: | (2228) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 50C279303E992F00 | |||
| (PID) Process: | (2228) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | MicrosoftEdgeAutoLaunch_29EBC4579851B72EE312C449CF839B1A |
Value: "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --no-startup-window --win-session-start | |||
| (PID) Process: | (2228) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\Profiles |
| Operation: | write | Name: | EnhancedLinkOpeningDefault |
Value: Default | |||
Executable files
0
Suspicious files
275
Text files
116
Unknown types
40
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2228 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old~RF18d4fe.TMP | — | |
MD5:— | SHA256:— | |||
| 2228 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF18d50e.TMP | — | |
MD5:— | SHA256:— | |||
| 2228 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2228 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2228 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF18d51d.TMP | — | |
MD5:— | SHA256:— | |||
| 2228 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF18d51d.TMP | — | |
MD5:— | SHA256:— | |||
| 2228 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2228 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2228 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF18d51d.TMP | — | |
MD5:— | SHA256:— | |||
| 2228 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
25
TCP/UDP connections
62
DNS requests
69
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7728 | svchost.exe | GET | 200 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/03b2d981-4f59-42a6-8f9a-a2b6278a0020?P1=1753912433&P2=404&P3=2&P4=gWJanqeCQ224TMlMg%2bEsI02%2bCc2TQ57OxDB7SewsHJIrtA2%2bt5QemJql%2fJaqB8YQTjJeRBa7c118r9YJ0A5anA%3d%3d | unknown | — | — | whitelisted |
7728 | svchost.exe | GET | 200 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/6b853aed-57d0-44a7-b8d5-4cdd01a61f64?P1=1753908835&P2=404&P3=2&P4=NYf55XeRbbal8wixILhXqeL8DlYPp%2fK3rEIKdzF5M%2brLfatyZlAhxHHyax4X0Zt0%2bRPzze%2bM85Qinohk5CENsw%3d%3d | unknown | — | — | whitelisted |
7728 | svchost.exe | HEAD | 200 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/03b2d981-4f59-42a6-8f9a-a2b6278a0020?P1=1753912433&P2=404&P3=2&P4=gWJanqeCQ224TMlMg%2bEsI02%2bCc2TQ57OxDB7SewsHJIrtA2%2bt5QemJql%2fJaqB8YQTjJeRBa7c118r9YJ0A5anA%3d%3d | unknown | — | — | whitelisted |
7084 | msedge.exe | GET | 200 | 150.171.27.11:80 | http://edge.microsoft.com/browsernetworktime/time/1/current?cup2key=2:pgek7N61yG9QTGeCokqVw4zZSwMeN7TI7Y3rwFiCSYE&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
6176 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.55.110.211:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7848 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7848 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7728 | svchost.exe | HEAD | 200 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1753908830&P2=404&P3=2&P4=eMJddOkrretcxo60HhpgMUXz8QfYgaQH8oc5hxsrgLveuGY5uGXjFNAI1ElNOERaWLJyJDpzX4SKusf7A6gWIA%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
7008 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7084 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7084 | msedge.exe | 150.171.27.11:80 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7084 | msedge.exe | 162.159.134.233:443 | cdn.discordapp.com | CLOUDFLARENET | — | whitelisted |
7084 | msedge.exe | 150.171.28.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7084 | msedge.exe | 2.23.227.199:443 | copilot.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
cdn.discordapp.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
copilot.microsoft.com |
| whitelisted |
update.googleapis.com |
| whitelisted |
www.bing.com |
| whitelisted |
clients2.googleusercontent.com |
| whitelisted |
edgeassetservice.azureedge.net |
| whitelisted |
www.googleapis.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7084 | msedge.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discordapp .com) |
7084 | msedge.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discordapp .com) |