| File name: | snoser.rar |
| Full analysis: | https://app.any.run/tasks/23924752-730b-41ef-9c79-3419199306f6 |
| Verdict: | Malicious activity |
| Analysis date: | March 26, 2025, 13:50:21 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | EC2D53921CE11838BF985CFBAA275950 |
| SHA1: | DAEC83B7E1DA8F2D210D35B49E2339DA759BCC8F |
| SHA256: | 875EFAECB81B2BCBDAADBC8F2A550839FB8327438A8966638D97AE0660CF777D |
| SSDEEP: | 12288:fC2kluOnrMWIRf4+Cvdqc3rkpKn/9PGt9Ud4Gcj0:fC2kljnrDKf4+Cvdqc7kwn/RGDW4Gcj0 |
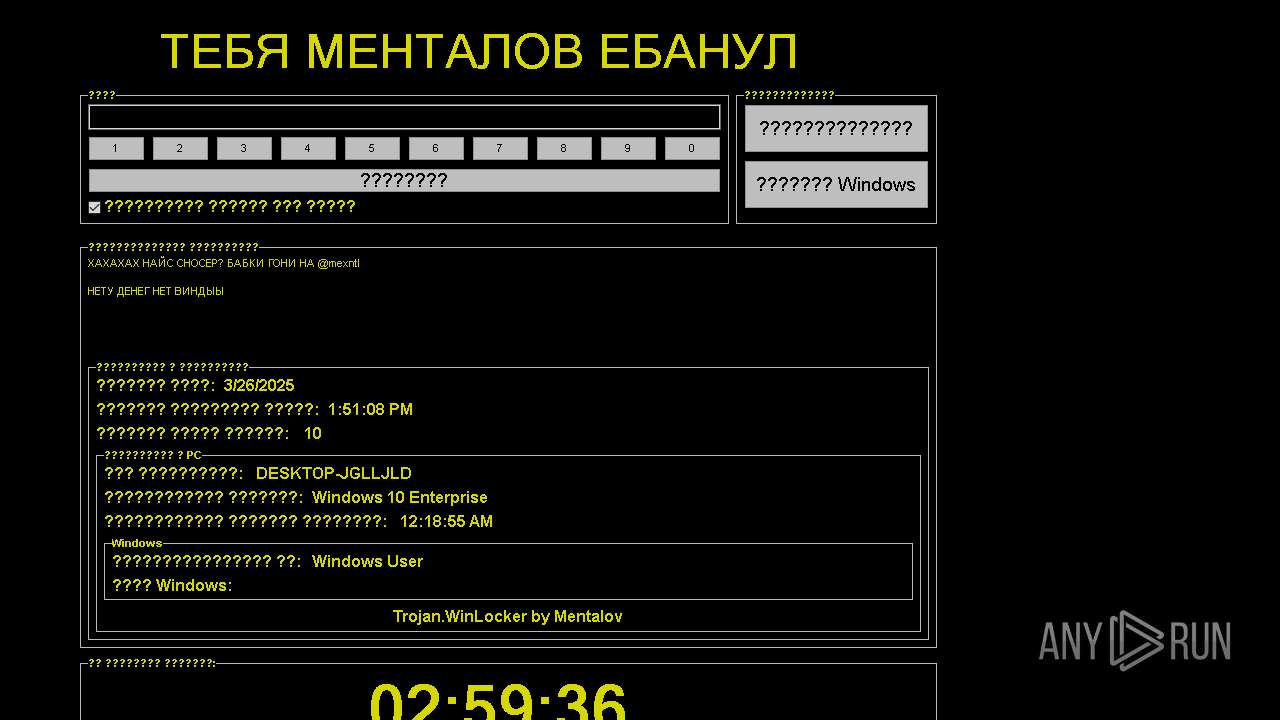
MALICIOUS
FRAGTOR mutex has been found
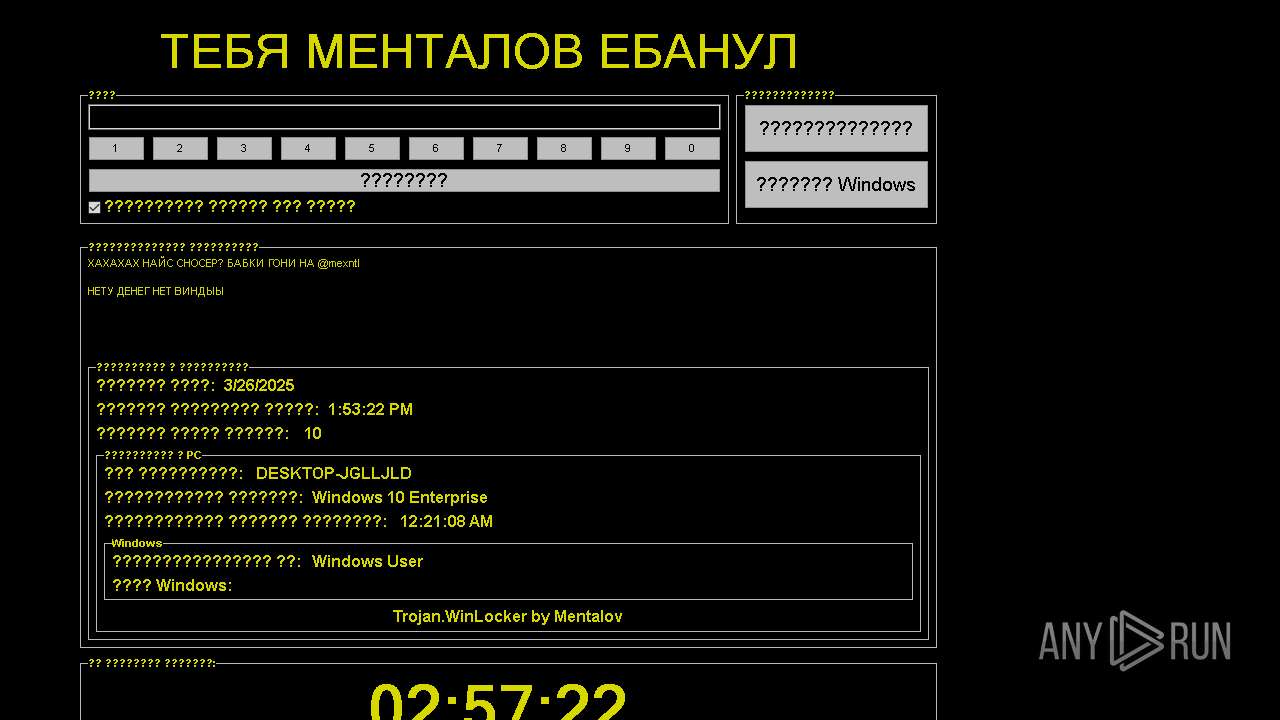
- snos by Rim Waletow.exe (PID: 7960)
Adds path to the Windows Defender exclusion list
- snos by Rim Waletow.exe (PID: 7960)
UAC/LUA settings modification
- snos by Rim Waletow.exe (PID: 7960)
Disables the Shutdown in the Start menu
- snos by Rim Waletow.exe (PID: 7960)
Disables the Run the Start menu
- snos by Rim Waletow.exe (PID: 7960)
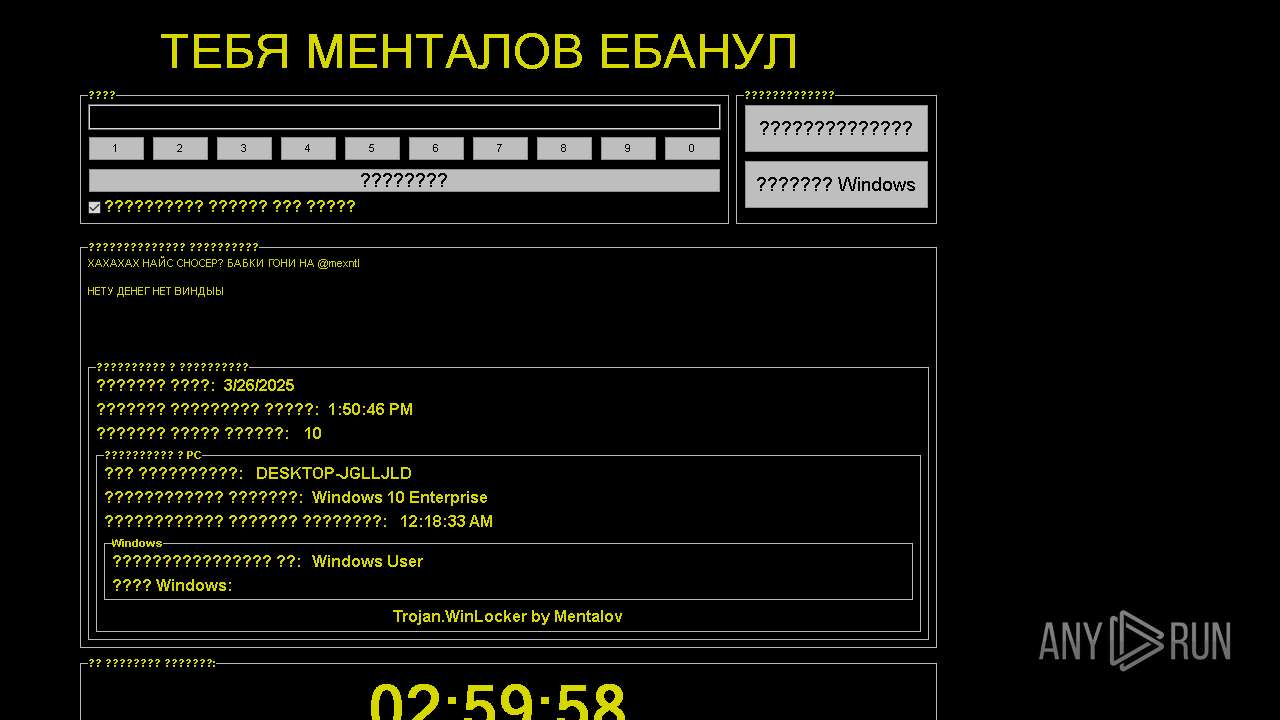
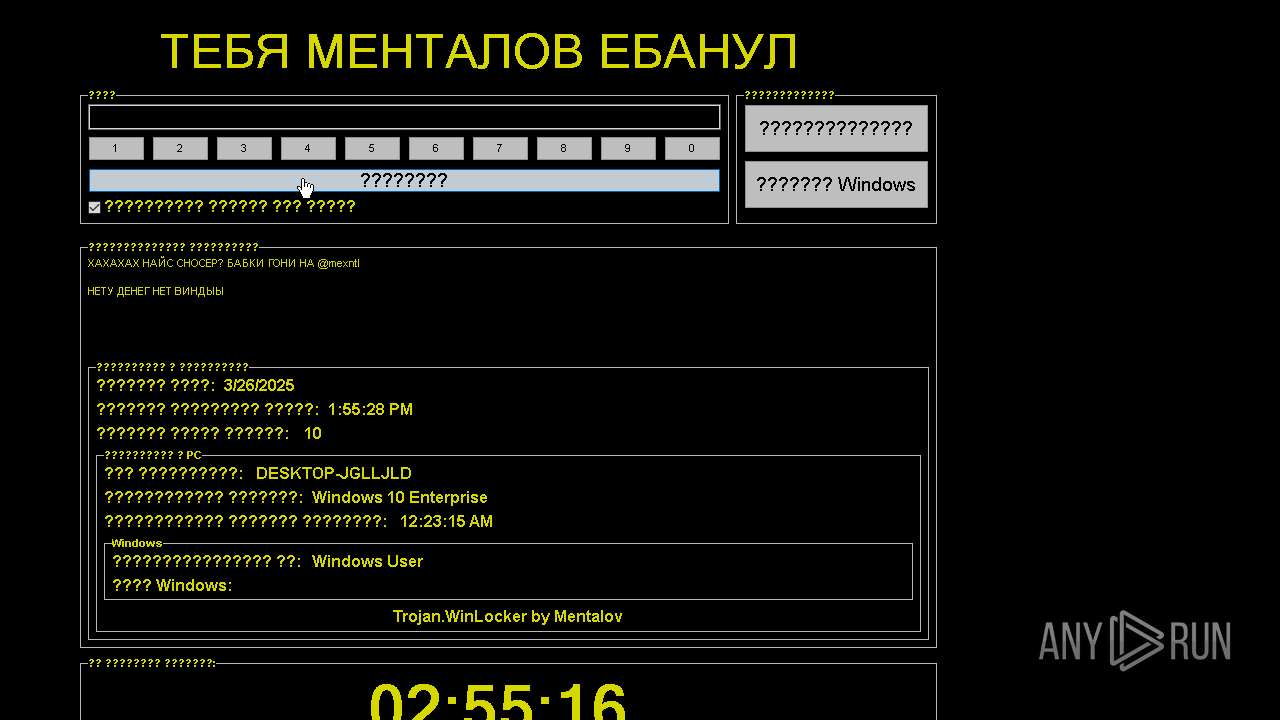
WINLOCKER has been detected (YARA)
- snos by Rim Waletow.exe (PID: 7960)
Disables Windows Defender
- snos by Rim Waletow.exe (PID: 7960)
Changes Windows Defender settings
- snos by Rim Waletow.exe (PID: 7960)
Disables the LogOff the Start menu
- snos by Rim Waletow.exe (PID: 7960)
Disables the Find the Start menu
- snos by Rim Waletow.exe (PID: 7960)
Changes image file execution options
- snos by Rim Waletow.exe (PID: 7960)
Changes the autorun value in the registry
- snos by Rim Waletow.exe (PID: 7960)
SUSPICIOUS
Reads security settings of Internet Explorer
- snos by Rim Waletow.exe (PID: 7960)
Starts POWERSHELL.EXE for commands execution
- snos by Rim Waletow.exe (PID: 7960)
Starts CMD.EXE for commands execution
- snos by Rim Waletow.exe (PID: 7960)
Script adds exclusion path to Windows Defender
- snos by Rim Waletow.exe (PID: 7960)
There is functionality for VM detection VMWare (YARA)
- snos by Rim Waletow.exe (PID: 7960)
There is functionality for VM detection VirtualBox (YARA)
- snos by Rim Waletow.exe (PID: 7960)
INFO
Manual execution by a user
- snos by Rim Waletow.exe (PID: 7912)
- snos by Rim Waletow.exe (PID: 7960)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4224)
Reads the computer name
- snos by Rim Waletow.exe (PID: 7960)
Checks supported languages
- snos by Rim Waletow.exe (PID: 7960)
Process checks computer location settings
- snos by Rim Waletow.exe (PID: 7960)
Create files in a temporary directory
- snos by Rim Waletow.exe (PID: 7960)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 8080)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 8080)
Compiled with Borland Delphi (YARA)
- snos by Rim Waletow.exe (PID: 7960)
- slui.exe (PID: 7880)
Checks proxy server information
- slui.exe (PID: 7880)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | - |
| UncompressedSize: | - |
| OperatingSystem: | Win32 |
| ArchivedFileName: | snoser/session/ss — копия (10).txt |
Total processes
153
Monitored processes
11
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 4224 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\snoser.rar | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 7216 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7268 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7844 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7880 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7912 | "C:\Users\admin\Desktop\snoser\snos by Rim Waletow.exe" | C:\Users\admin\Desktop\snoser\snos by Rim Waletow.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 7960 | "C:\Users\admin\Desktop\snoser\snos by Rim Waletow.exe" | C:\Users\admin\Desktop\snoser\snos by Rim Waletow.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 8044 | "C:\Windows\System32\cmd.exe" /c schtasks /create /tn "GoogleUpdateTaskMachineUK" /sc MINUTE /mo 1 /tr "C:\Users\admin\Desktop\snoser\snos by Rim Waletow.exe" /rl HIGHEST /f | C:\Windows\System32\cmd.exe | — | snos by Rim Waletow.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 8056 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 8080 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -Command "Add-MpPreference -ExclusionPath 'C:\Users\admin\Desktop\snoser\snos by Rim Waletow.exe'" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | snos by Rim Waletow.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
8 468
Read events
8 416
Write events
52
Delete events
0
Modification events
| (PID) Process: | (4224) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4224) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4224) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4224) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\snoser.rar | |||
| (PID) Process: | (4224) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4224) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4224) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4224) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4224) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (4224) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
Executable files
1
Suspicious files
1
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4224 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4224.34389\snoser\snos by Rim Waletow.exe | executable | |
MD5:F4442A83DAA91200FCFAD1C11AA5BD87 | SHA256:54A8855840154664A64F69E6FA1D09840ECCFAD371450F12CF7B142AE756621A | |||
| 8080 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:82D0C7D320C3FBC6564044CF023225BD | SHA256:129608DA01A14575F836A964F97E43ECE5CD77E2BABB4BB20E75A520C587F0A7 | |||
| 8080 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ccmuzuyx.lvj.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7960 | snos by Rim Waletow.exe | C:\Users\admin\AppData\Local\Temp\Time2.ini | text | |
MD5:1281E7CD37295F4793D7C2A89768C0DC | SHA256:1FA21D9E19BF83DD68505165FEC38E46263B582FF8E3D582ADD57C756210B8FA | |||
| 7960 | snos by Rim Waletow.exe | C:\Users\admin\AppData\Local\Temp\Time.ini | text | |
MD5:EB13B7EAF7F30D348E471F0907B31AAC | SHA256:94BA214735774FB4E68BE906C3E181D29C71DBBCD10540E70BA7021FCF5EA3AA | |||
| 8080 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_50vqhf1q.2sb.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
29
DNS requests
19
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.137:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7356 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7236 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7236 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.137:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3216 | svchost.exe | 20.198.162.78:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | SG | whitelisted |
6544 | svchost.exe | 20.190.160.20:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
7356 | backgroundTaskHost.exe | 20.223.35.26:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7356 | backgroundTaskHost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |