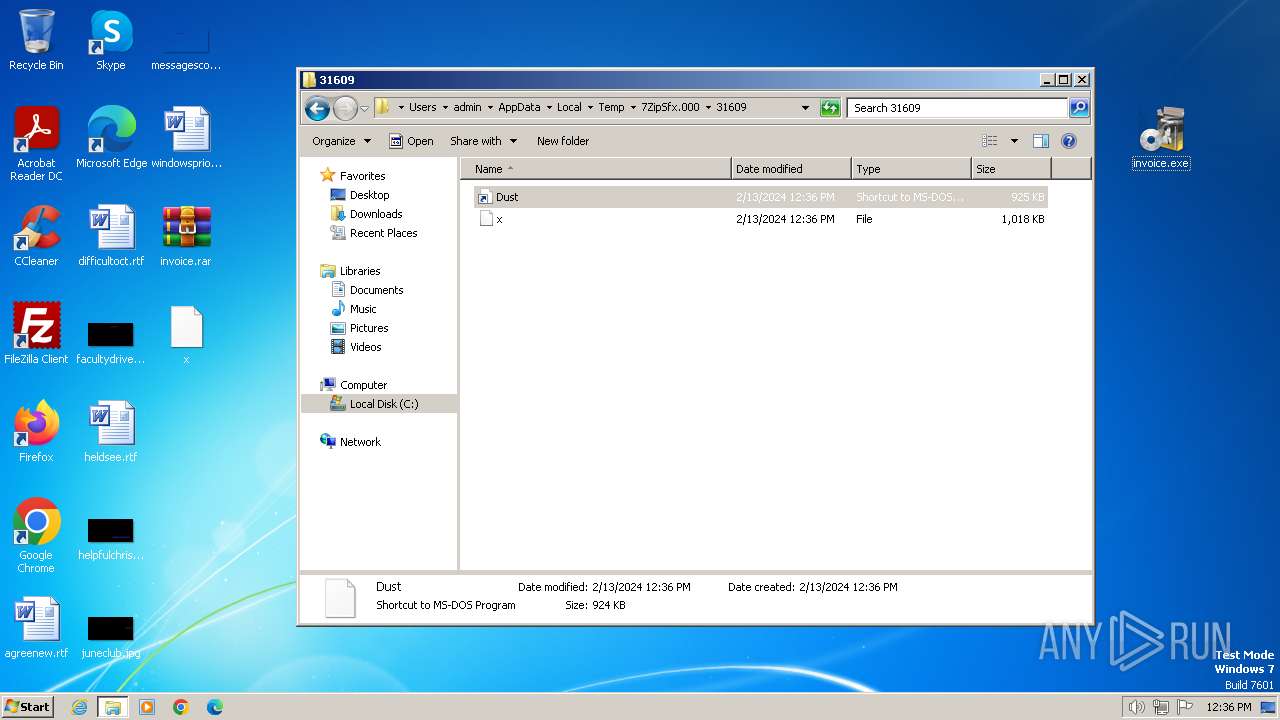
| File name: | invoice.rar |
| Full analysis: | https://app.any.run/tasks/81eb9331-490f-48cb-9e32-6d28e20c265e |
| Verdict: | Malicious activity |
| Analysis date: | February 13, 2024, 12:35:15 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | A1D01D6EFA49117A638FB783F0F81684 |
| SHA1: | C2F6D95C8D7D2974D958B43CBEEA9E2AE17E561F |
| SHA256: | 87249E1B561ED492233437AEC7293CD0D7520188A4638C4D2BB53DD9F2D5D81E |
| SSDEEP: | 49152:rcw9yLAvofVjJGlo1XIVNYxrCWYJ6NhKZaRLap2BMD64AcKW+g59hl/KbpJfRc8J:rcioV0+10NYpeQKZaRmI2nAcKW+q9P/S |
MALICIOUS
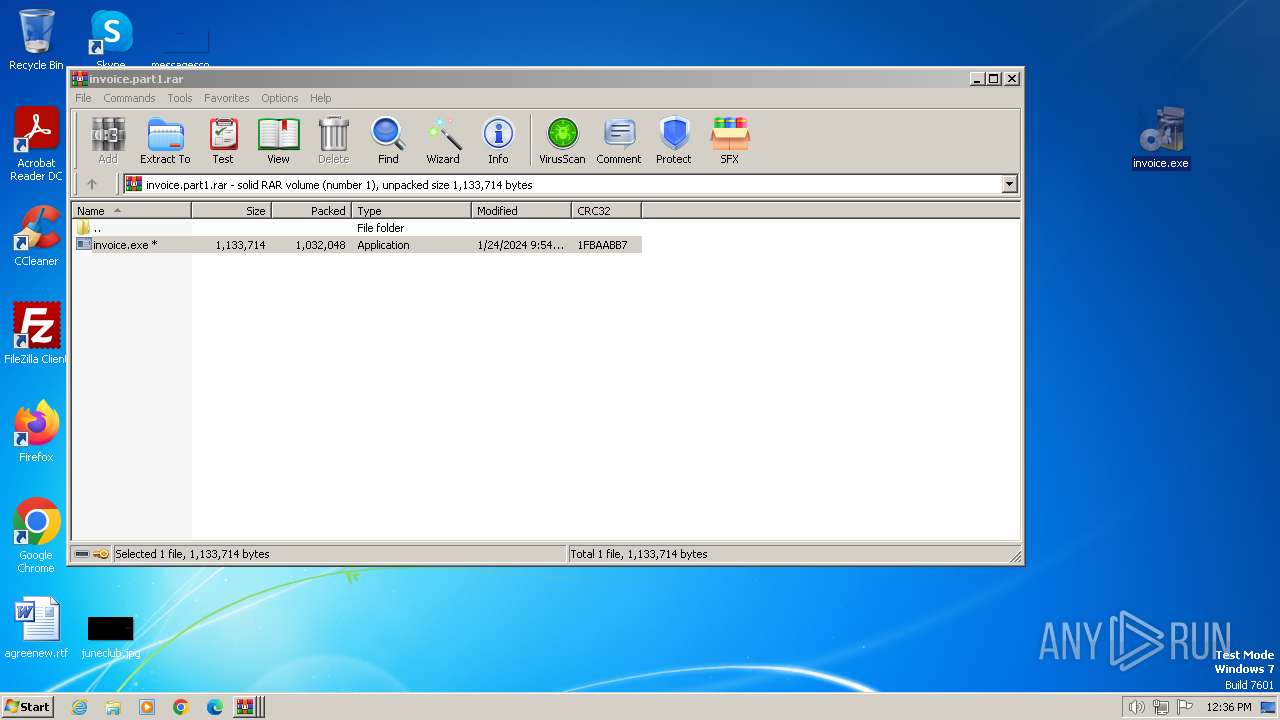
Drops the executable file immediately after the start
- invoice.exe (PID: 2672)
- cmd.exe (PID: 2900)
- invoice.exe (PID: 3932)
- cmd.exe (PID: 2596)
Antivirus name has been found in the command line (generic signature)
- findstr.exe (PID: 1740)
- findstr.exe (PID: 1860)
- findstr.exe (PID: 3848)
- findstr.exe (PID: 1644)
SUSPICIOUS
Application launched itself
- WinRAR.exe (PID: 3720)
- WinRAR.exe (PID: 3240)
- cmd.exe (PID: 3164)
- cmd.exe (PID: 3724)
- cmd.exe (PID: 2328)
- cmd.exe (PID: 2636)
Executable content was dropped or overwritten
- invoice.exe (PID: 2672)
- cmd.exe (PID: 2900)
- invoice.exe (PID: 3932)
- cmd.exe (PID: 2596)
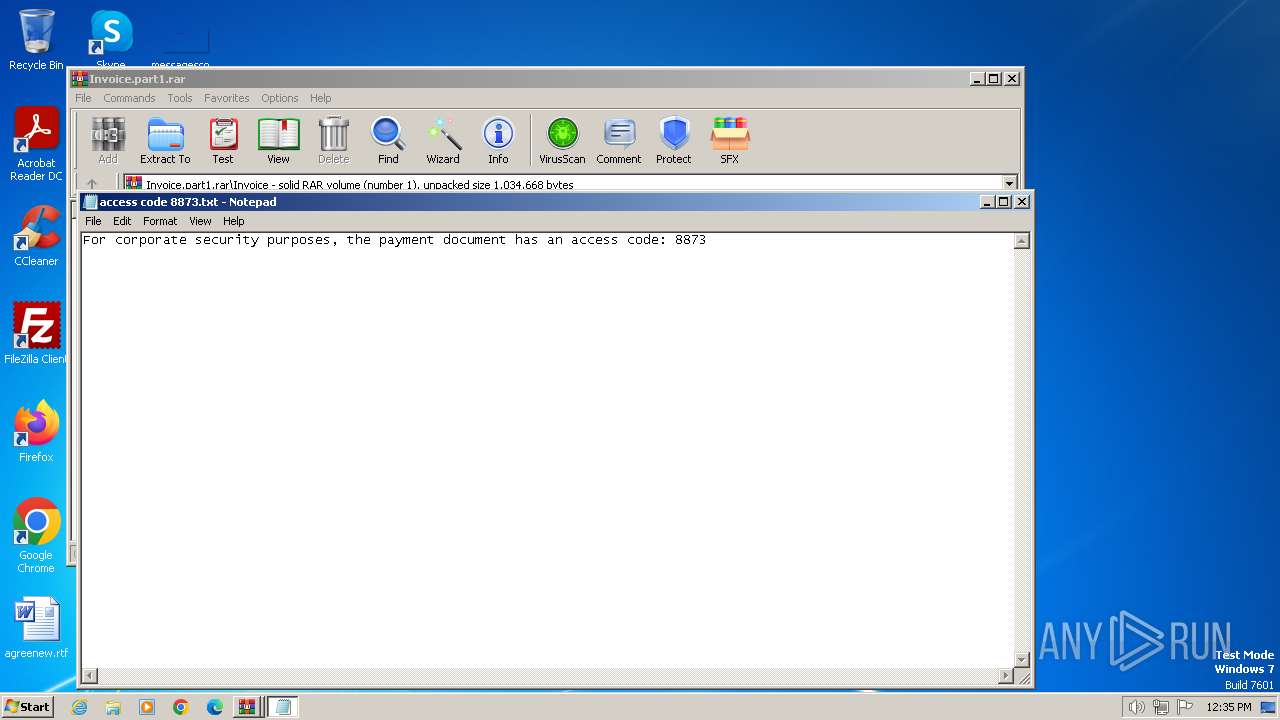
Start notepad (likely ransomware note)
- WinRAR.exe (PID: 3720)
Reads the Internet Settings
- invoice.exe (PID: 2672)
- Dust.pif (PID: 2080)
- invoice.exe (PID: 3932)
- rundll32.exe (PID: 1780)
Reads security settings of Internet Explorer
- invoice.exe (PID: 2672)
- invoice.exe (PID: 3932)
Starts CMD.EXE for commands execution
- invoice.exe (PID: 2672)
- cmd.exe (PID: 3164)
- cmd.exe (PID: 3724)
- cmd.exe (PID: 2636)
- cmd.exe (PID: 2328)
- invoice.exe (PID: 3932)
Get information on the list of running processes
- cmd.exe (PID: 3724)
- cmd.exe (PID: 2328)
The executable file from the user directory is run by the CMD process
- Dust.pif (PID: 2100)
- Dust.pif (PID: 1808)
Drops a file with a rarely used extension (PIF)
- cmd.exe (PID: 2900)
- cmd.exe (PID: 2596)
Starts application with an unusual extension
- cmd.exe (PID: 3724)
- cmd.exe (PID: 2328)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 3724)
- cmd.exe (PID: 2328)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 3724)
- cmd.exe (PID: 2328)
INFO
Checks supported languages
- wmpnscfg.exe (PID: 3932)
- invoice.exe (PID: 2672)
- Dust.pif (PID: 2100)
- invoice.exe (PID: 3932)
- Dust.pif (PID: 2080)
- Dust.pif (PID: 4036)
- Dust.pif (PID: 992)
- Dust.pif (PID: 1808)
Reads the computer name
- wmpnscfg.exe (PID: 3932)
- invoice.exe (PID: 2672)
- Dust.pif (PID: 2100)
- invoice.exe (PID: 3932)
- Dust.pif (PID: 2080)
- Dust.pif (PID: 4036)
- Dust.pif (PID: 992)
- Dust.pif (PID: 1808)
Create files in a temporary directory
- invoice.exe (PID: 2672)
- invoice.exe (PID: 3932)
Manual execution by a user
- invoice.exe (PID: 2672)
- wmpnscfg.exe (PID: 3932)
- explorer.exe (PID: 2804)
- Dust.pif (PID: 4036)
- invoice.exe (PID: 3932)
- Dust.pif (PID: 2080)
- Dust.pif (PID: 992)
- rundll32.exe (PID: 1780)
- rundll32.exe (PID: 2028)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2840)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2840)
Reads mouse settings
- Dust.pif (PID: 2100)
- Dust.pif (PID: 2080)
- Dust.pif (PID: 4036)
- Dust.pif (PID: 1808)
- Dust.pif (PID: 992)
Reads the machine GUID from the registry
- Dust.pif (PID: 2080)
- Dust.pif (PID: 4036)
- Dust.pif (PID: 992)
Reads security settings of Internet Explorer
- rundll32.exe (PID: 1780)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
99
Monitored processes
36
Malicious processes
5
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 992 | "C:\Users\admin\AppData\Local\Temp\7ZipSfx.001\31923\Dust.pif" | C:\Users\admin\AppData\Local\Temp\7ZipSfx.001\31923\Dust.pif | — | explorer.exe | |||||||||||
User: admin Company: AutoIt Team Integrity Level: MEDIUM Description: AutoIt v3 Script (Beta) Exit code: 0 Version: 3, 3, 15, 4 Modules
| |||||||||||||||
| 1236 | cmd /c mkdir 31609 | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1236 | ping -n 5 localhost | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1368 | ping -n 5 localhost | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Ping Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1572 | cmd /c mkdir 31923 | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1644 | findstr /I "wrsa.exe" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1740 | findstr /I "avastui.exe avgui.exe nswscsvc.exe sophoshealth.exe" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1780 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\Desktop\x | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1808 | 31923\Dust.pif 31923\x | C:\Users\admin\AppData\Local\Temp\7ZipSfx.001\31923\Dust.pif | cmd.exe | ||||||||||||
User: admin Company: AutoIt Team Integrity Level: HIGH Description: AutoIt v3 Script (Beta) Exit code: 3221225477 Version: 3, 3, 15, 4 Modules
| |||||||||||||||
| 1860 | findstr /I "wrsa.exe" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
35 292
Read events
34 920
Write events
359
Delete events
13
Modification events
| (PID) Process: | (3240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3240) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\invoice.rar | |||
| (PID) Process: | (3240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3240) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
5
Suspicious files
11
Text files
12
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3240 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3240.21241\invoice\Invoice.part1.rar | compressed | |
MD5:2CA26102C71A2C10571233C565881284 | SHA256:6087932CCB8B9CA6E4691501E2EE9810D41922A1E2A119D064FE36E48BCBEF22 | |||
| 3720 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3720.22531\Invoice\access code 8873.txt | text | |
MD5:FF26B8BF6827A4B705D937AB513224E3 | SHA256:A21FFBB354A6D5A5AEABD94A4AEA330ABC349D9948374D02B298298BC25CC5F6 | |||
| 3720 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa3720.21769\access code 8873.txt | text | |
MD5:FF26B8BF6827A4B705D937AB513224E3 | SHA256:A21FFBB354A6D5A5AEABD94A4AEA330ABC349D9948374D02B298298BC25CC5F6 | |||
| 3720 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3720.22531\Invoice\invoice.part4.rar | compressed | |
MD5:8DA19A95E36FB9618E0B1956CBEC2E02 | SHA256:24BE9A81ACE842FF0339D100D04D6DC9BEED47DBFEAA9CE870D30D3B628EFCCE | |||
| 3240 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3240.21241\invoice\Invoice.part2.rar | compressed | |
MD5:22C8A0F546D8A28E42265AFFBE02B74F | SHA256:90A846C2CD01D5379679E77442DFCA2D2E5DD2D0D8E6F57276A375623D3DC1B4 | |||
| 3720 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3720.22531\Invoice\invoice.part2.rar | compressed | |
MD5:8995437672BC642E5C6A912255EC6A81 | SHA256:33D9CA04EDC70DB181AF7005BF438C4BB523C70CCD483ABF7BCA4A93A096B27F | |||
| 3720 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3720.22531\Invoice\invoice.part5.rar | compressed | |
MD5:825F6C3A69F59F4AAA95DDE3B3550BD8 | SHA256:AD6BC819E086CC89EBFD518C854EE3EA6DAD0002F96C4363238B03D57E326D3A | |||
| 2672 | invoice.exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\Hour | text | |
MD5:A019BB2B7A90E9BAE3104C87B3807146 | SHA256:2C1695CD883C74A43D516A57585C3685F28C87E74D60738F5DDE2667D718555C | |||
| 2672 | invoice.exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\Dns | text | |
MD5:451C9E294CEF59C22CAE54FC123E63D9 | SHA256:41A05D5D15240D62D1F455AE70EB6A2241FC695C27193FFCDC1DEF81D657B5B7 | |||
| 2672 | invoice.exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\Injection | binary | |
MD5:AC1262C690C9FFA132B284FE8F60A529 | SHA256:EAE586960418F7D3390C98A43632D4BAF4BF17D3951A7074B5E93BCEF555BD2C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
5
DNS requests
2
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3260 | WerFault.exe | 104.208.16.93:443 | watson.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
nmkrkibbwxQ.nmkrkibbwxQ |
| unknown |
watson.microsoft.com |
| whitelisted |