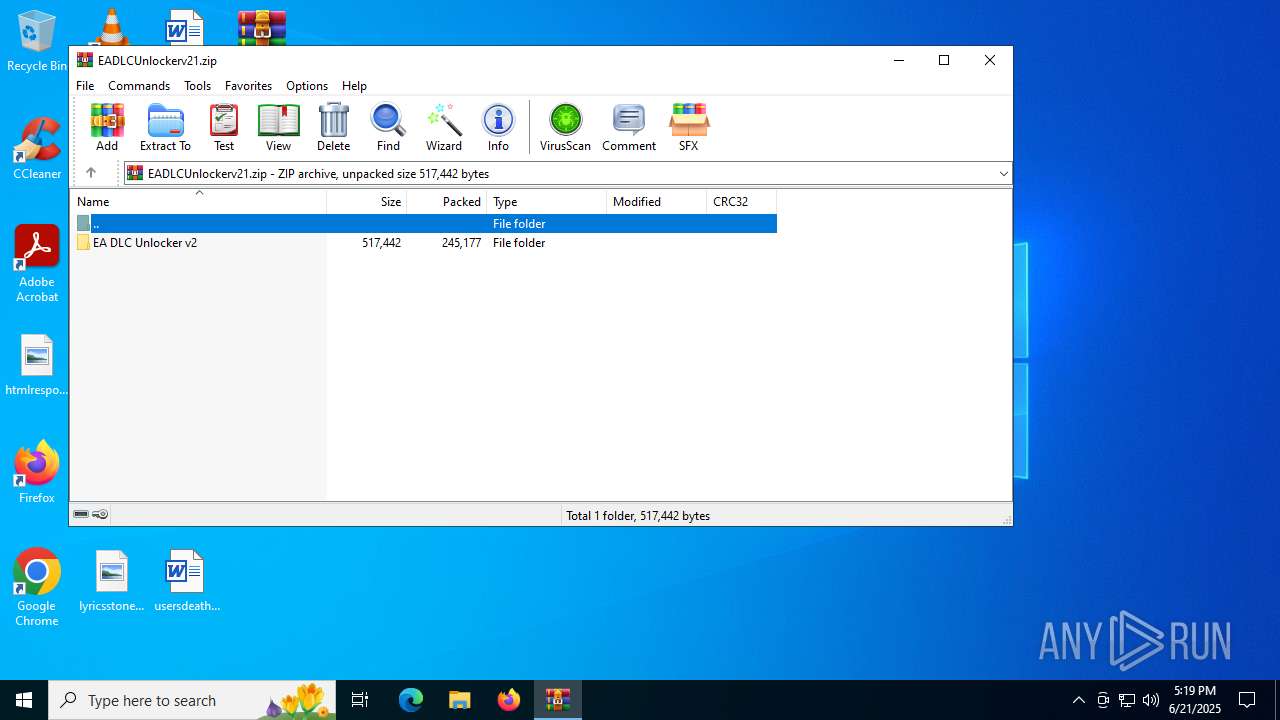
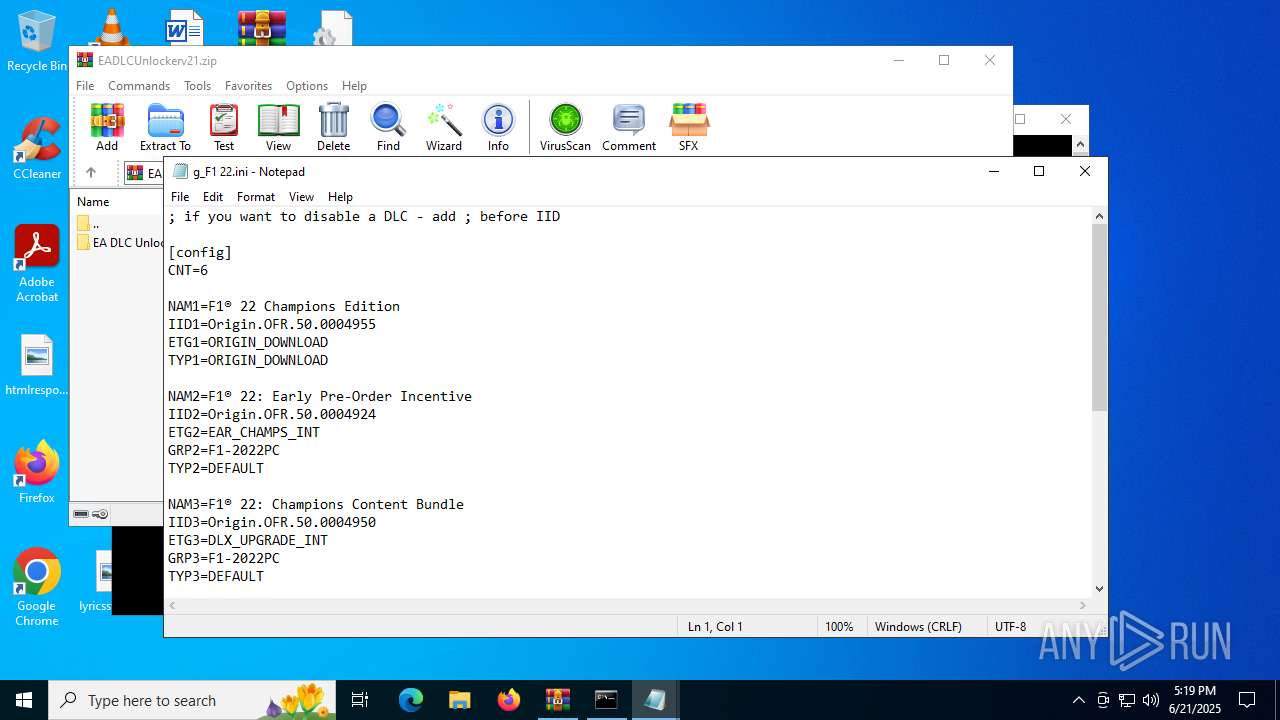
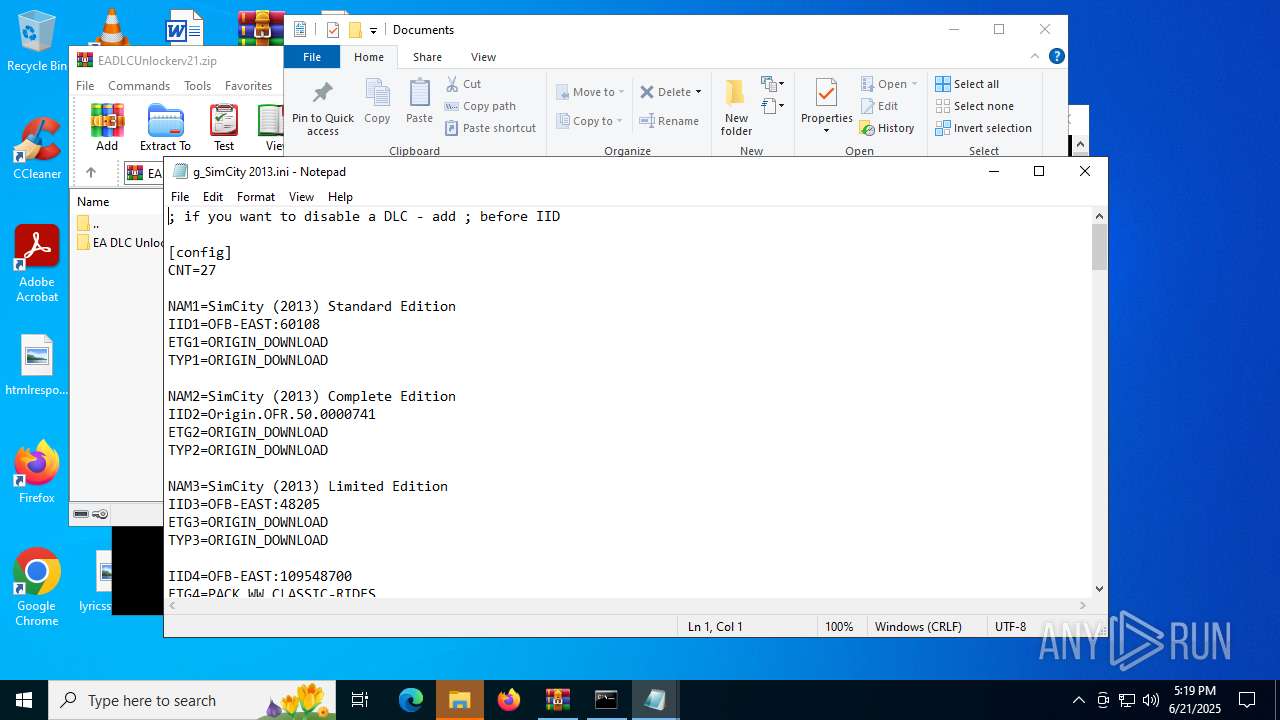
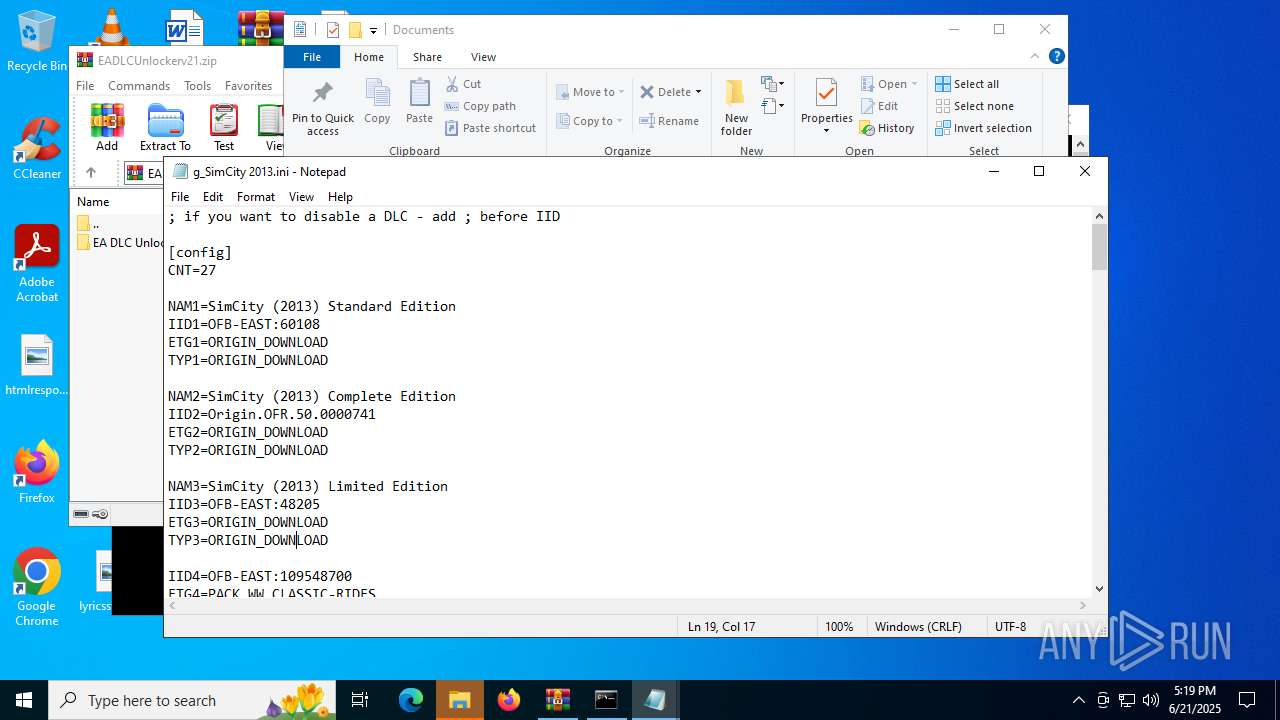
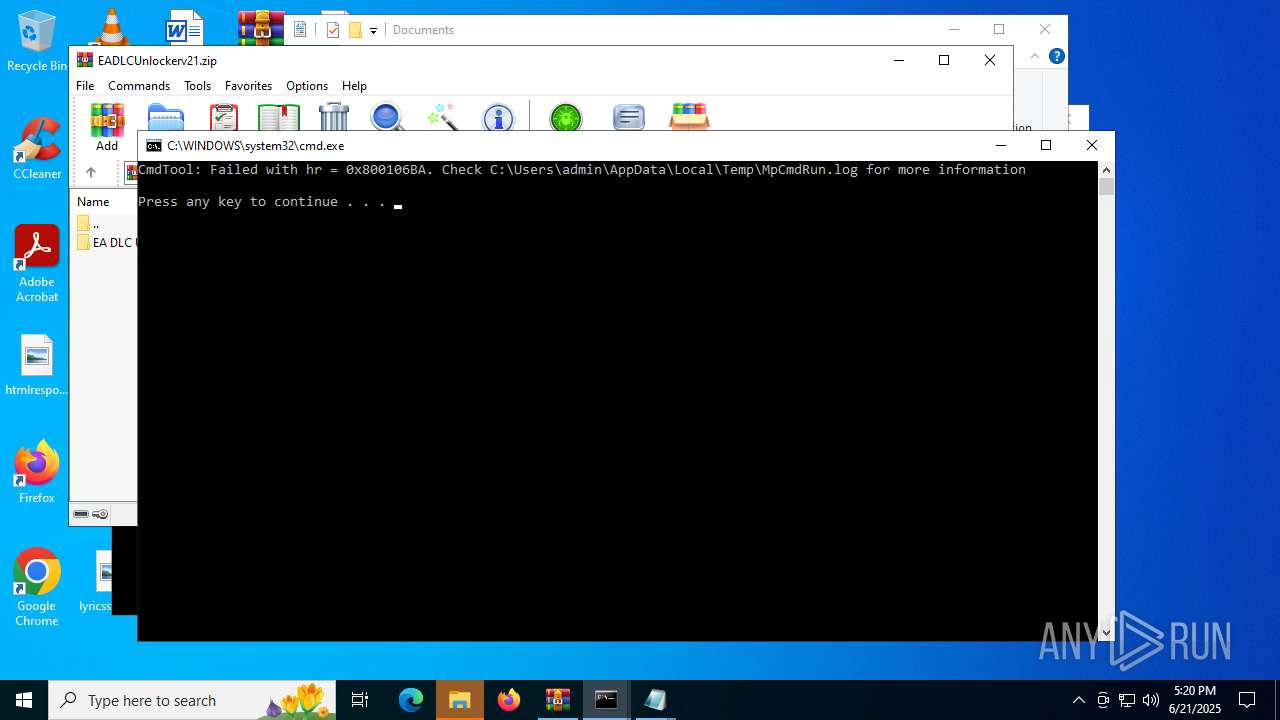
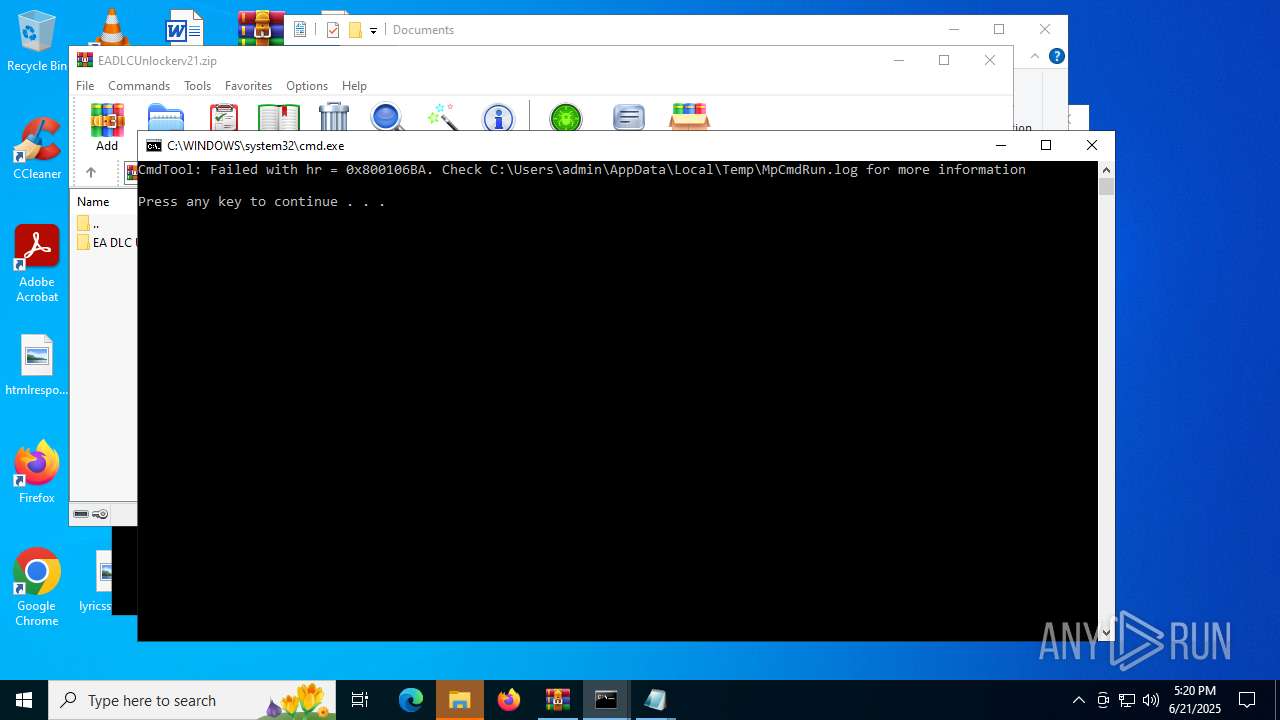
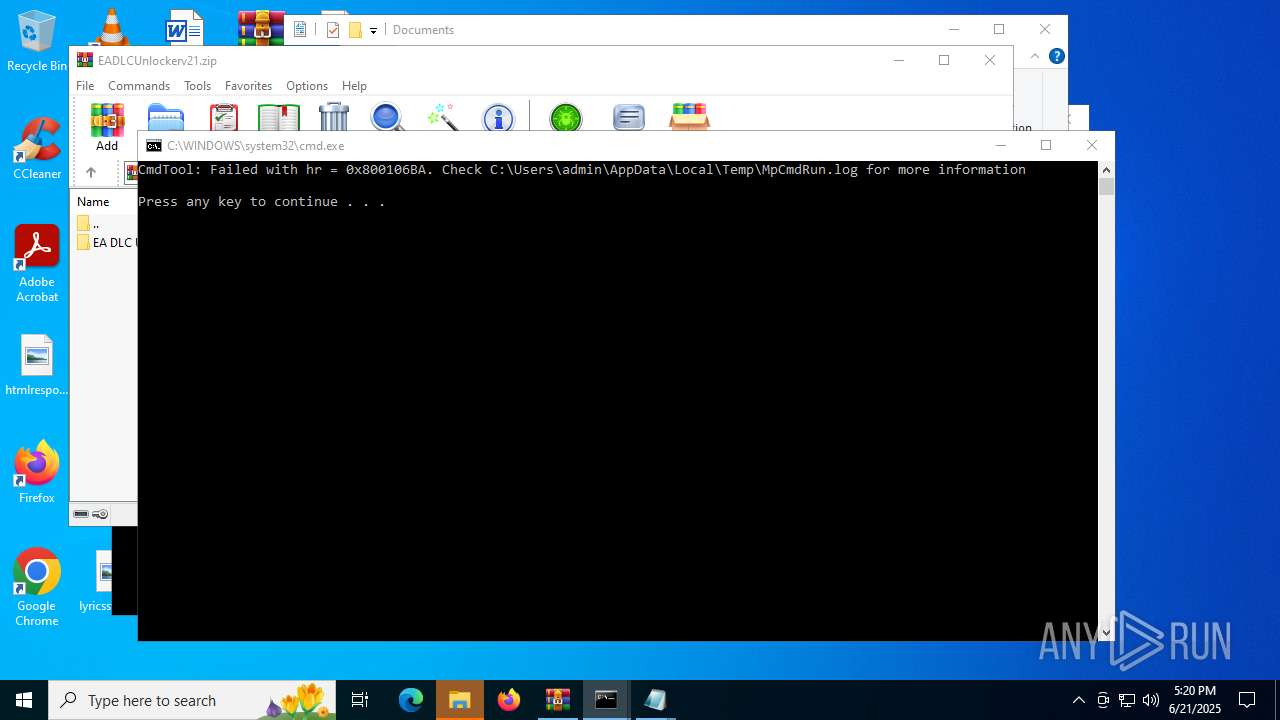
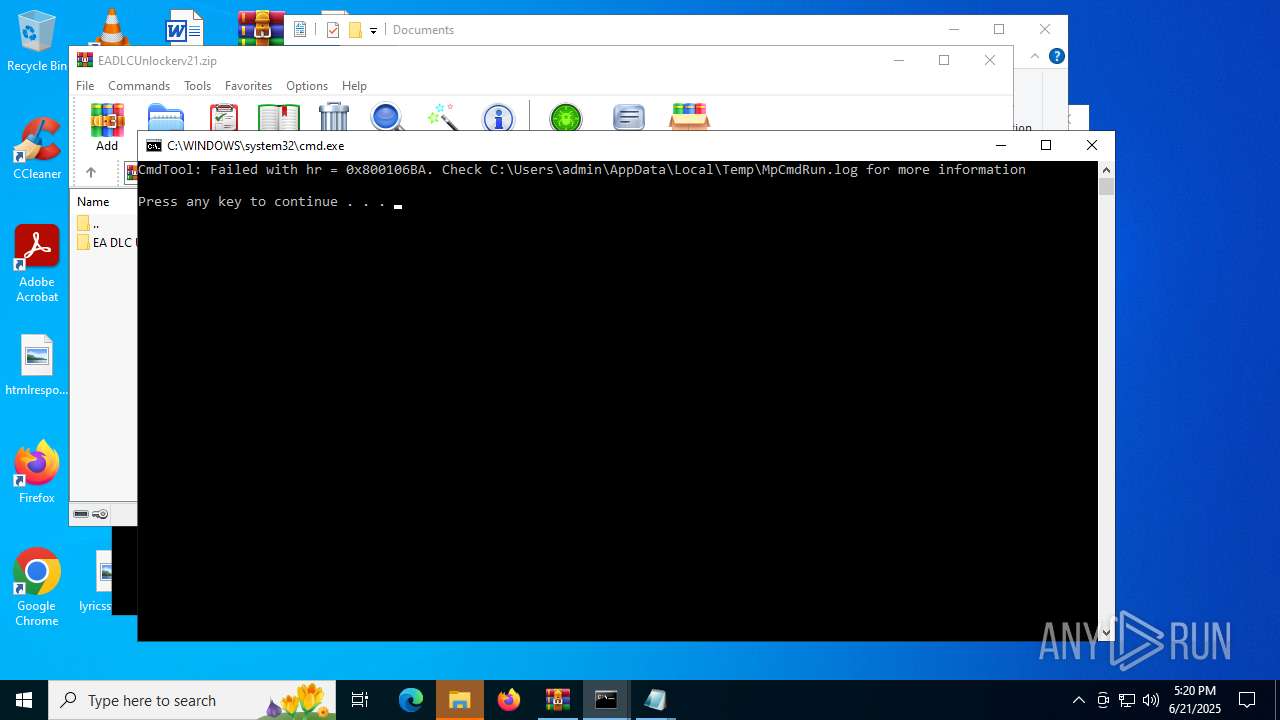
| File name: | EADLCUnlockerv21.zip |
| Full analysis: | https://app.any.run/tasks/91325985-2bbf-42fd-87ff-6b5ee6017f18 |
| Verdict: | Malicious activity |
| Analysis date: | June 21, 2025, 17:19:11 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 0812AE0CF47285B49A9A44DD85027F4F |
| SHA1: | F086EED69E7422798FBF395143B08A6B664C9916 |
| SHA256: | 871AD47FCF002F684A63B3543104A8B7CE7A121B5AB5E1BD3E4283A2279A7778 |
| SSDEEP: | 12288:FDBo3GiOUloC1vuxCodMwEQlS3HtHLEwzF/:FDBo3GlUcxCodM5HLdzF/ |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 1068)
SUSPICIOUS
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 4984)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 4984)
- WinRAR.exe (PID: 1068)
Application launched itself
- cmd.exe (PID: 4984)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 4984)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 4984)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 4984)
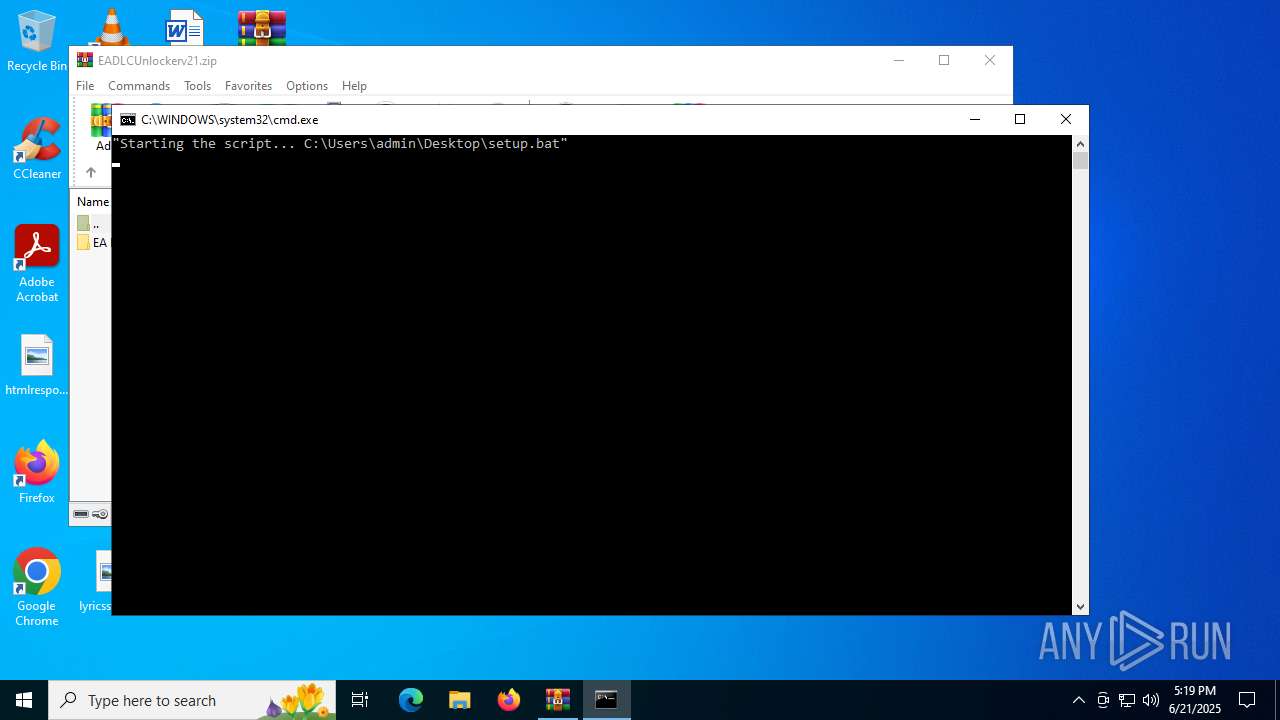
Executing commands from a ".bat" file
- WinRAR.exe (PID: 1068)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 1068)
INFO
Manual execution by a user
- cmd.exe (PID: 4984)
- notepad.exe (PID: 6360)
- notepad.exe (PID: 6292)
- notepad.exe (PID: 4520)
- notepad.exe (PID: 5600)
- notepad.exe (PID: 592)
- notepad.exe (PID: 6776)
- notepad.exe (PID: 1712)
Reads security settings of Internet Explorer
- notepad.exe (PID: 6292)
- notepad.exe (PID: 6360)
- notepad.exe (PID: 4520)
- notepad.exe (PID: 5600)
- notepad.exe (PID: 592)
- notepad.exe (PID: 6776)
- notepad.exe (PID: 1712)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1068)
The sample compiled with english language support
- WinRAR.exe (PID: 1068)
Reads the computer name
- MpCmdRun.exe (PID: 2160)
Checks supported languages
- MpCmdRun.exe (PID: 2160)
Create files in a temporary directory
- MpCmdRun.exe (PID: 2160)
Checks proxy server information
- slui.exe (PID: 304)
Reads the software policy settings
- slui.exe (PID: 304)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:01:05 21:04:48 |
| ZipCRC: | 0xee8619b1 |
| ZipCompressedSize: | 204 |
| ZipUncompressedSize: | 302 |
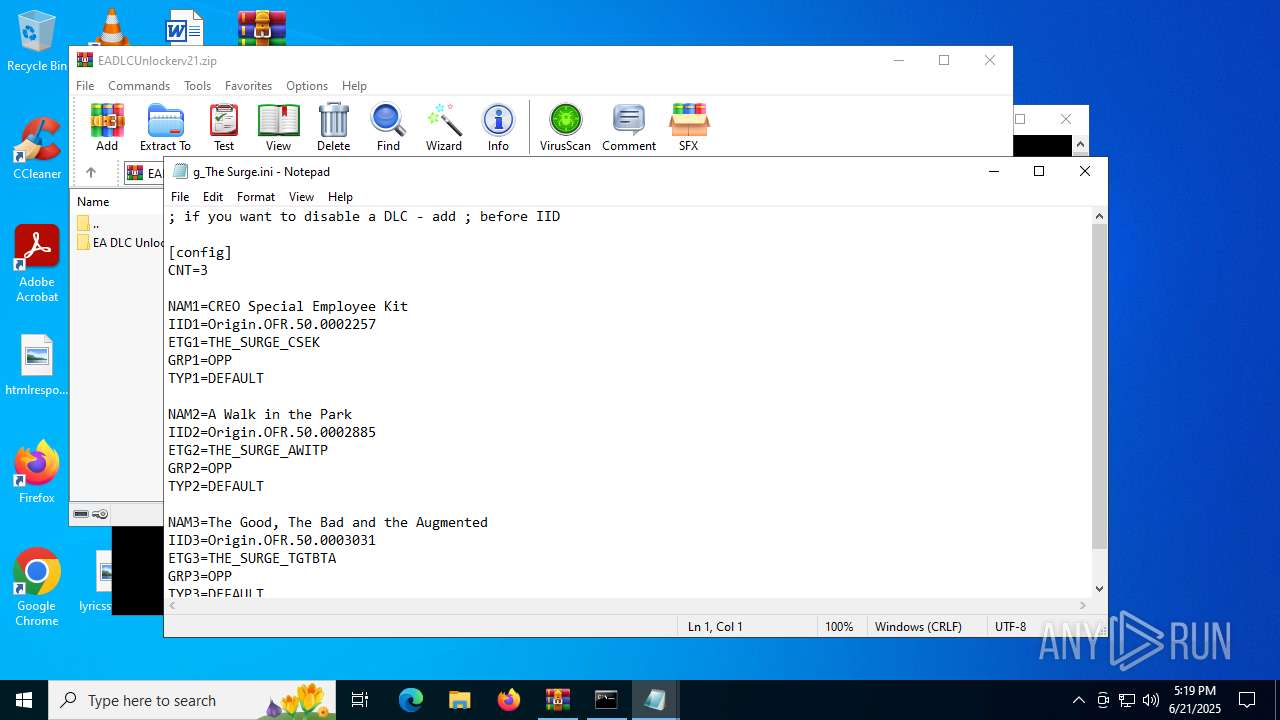
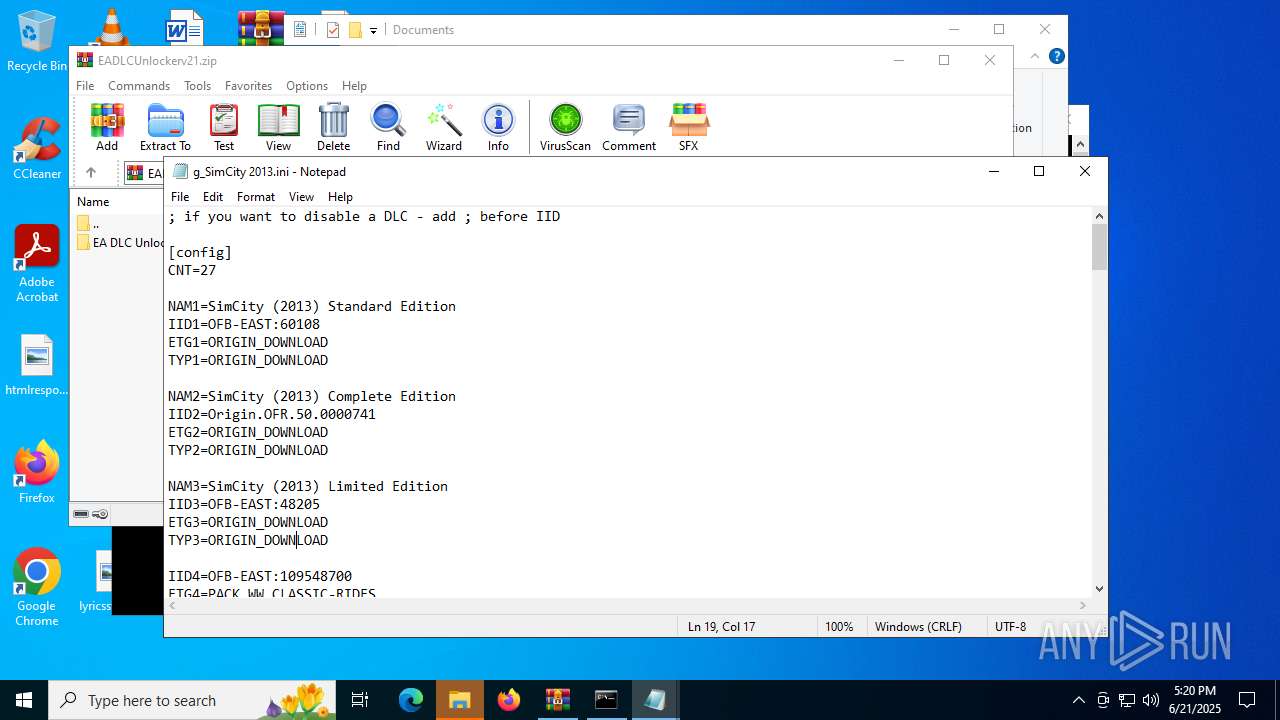
| ZipFileName: | EA DLC Unlocker v2/g_STAR WARS Jedi Survivor.ini |
Total processes
152
Monitored processes
21
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 304 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 420 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
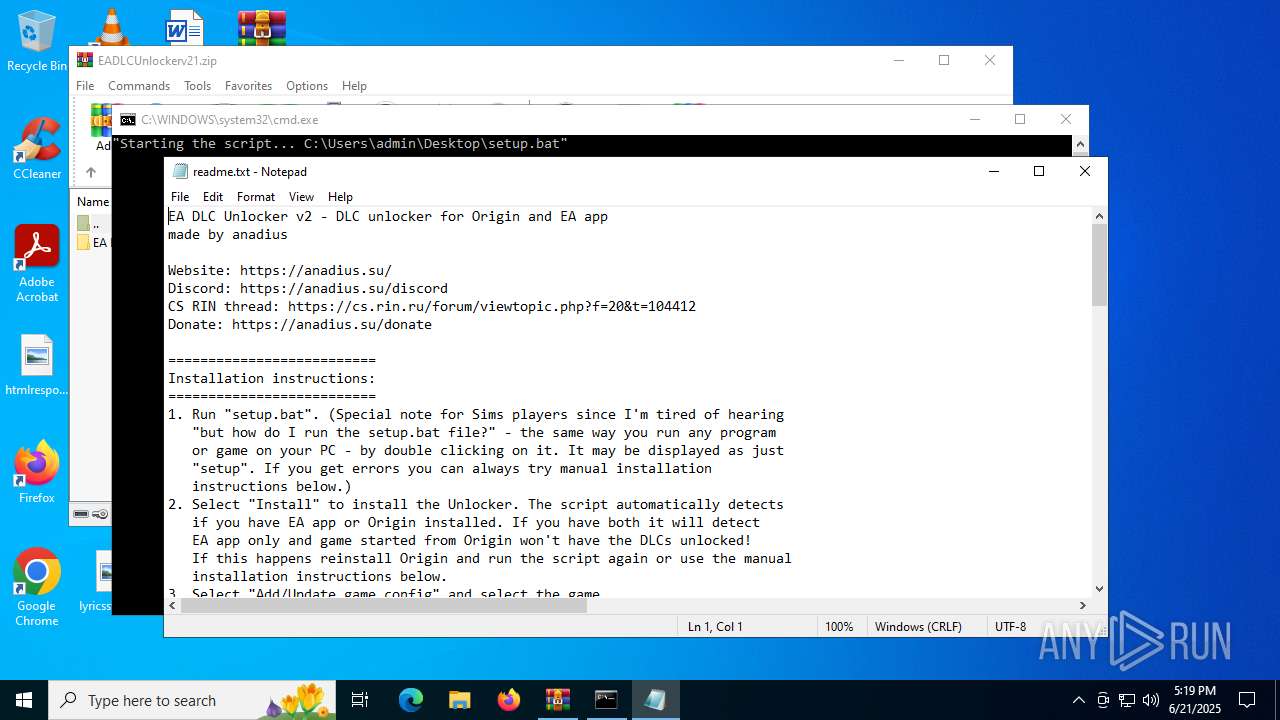
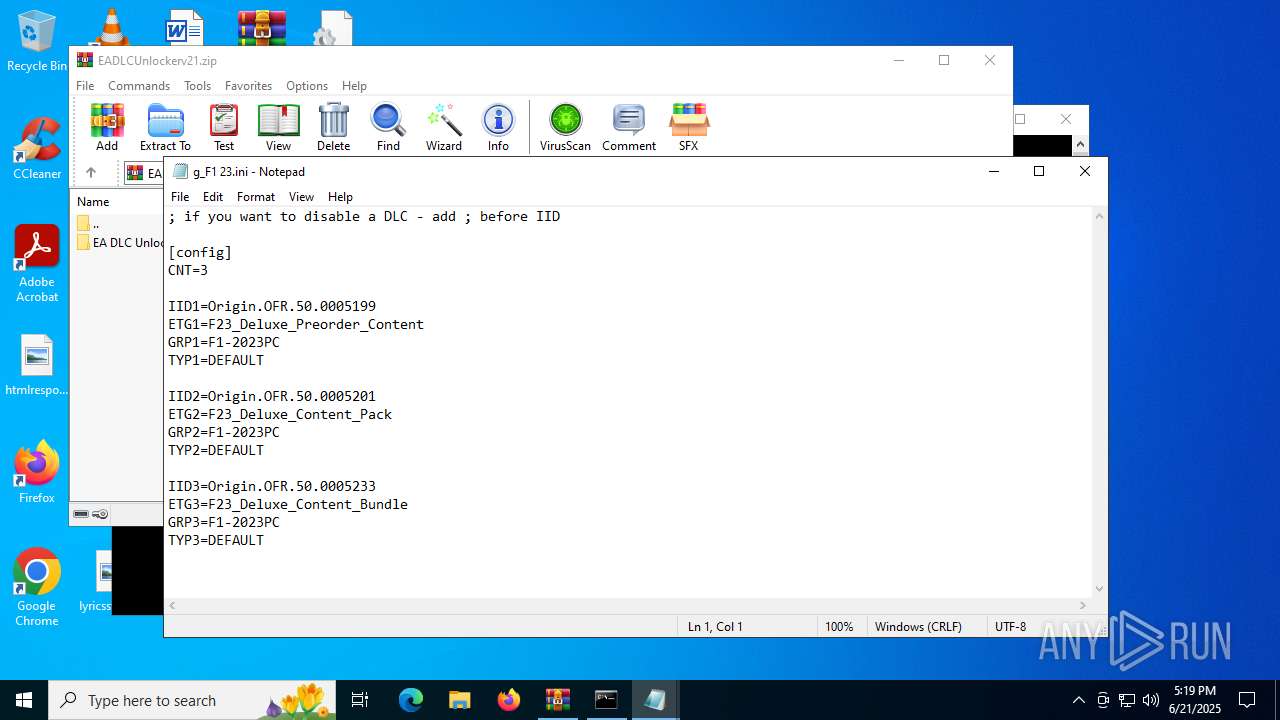
| 592 | "C:\WINDOWS\system32\NOTEPAD.EXE" "C:\Users\admin\Desktop\g_F1 23.ini" | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1068 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\EADLCUnlockerv21.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 1712 | "C:\WINDOWS\system32\NOTEPAD.EXE" "C:\Users\admin\Desktop\g_SimCity 2013.ini" | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1752 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
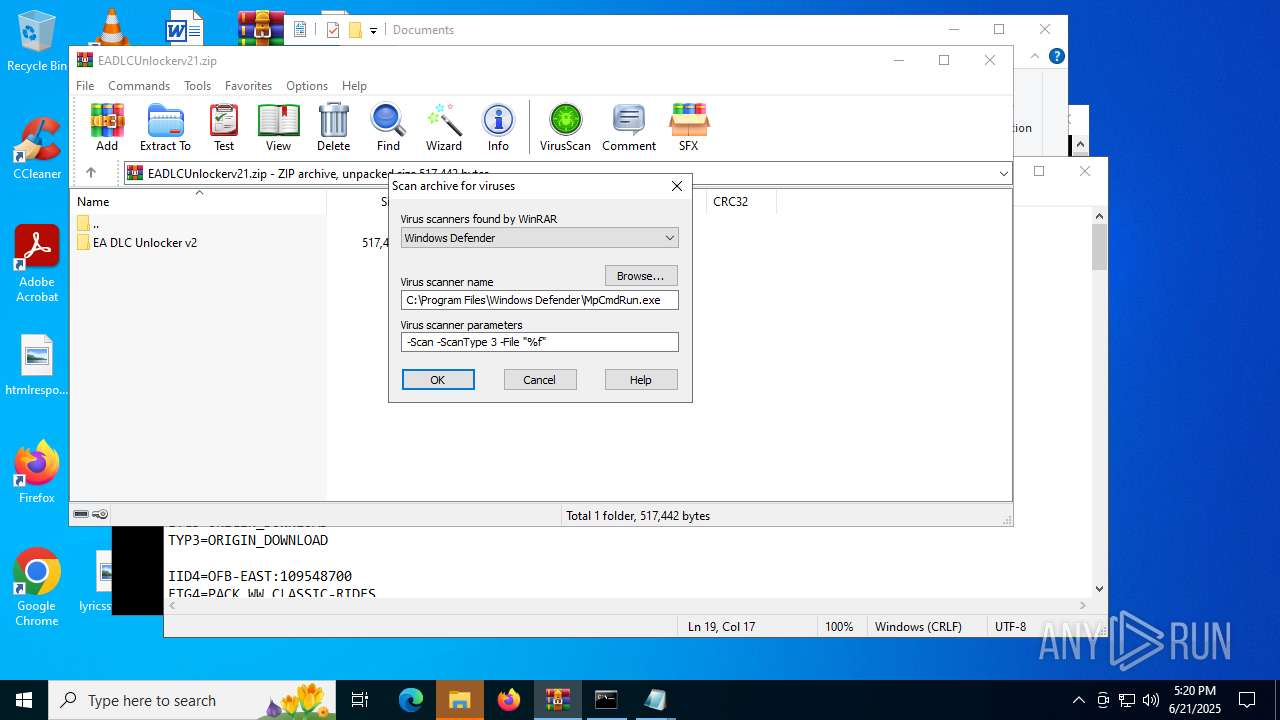
| 2160 | "C:\Program Files\Windows Defender\MpCmdRun.exe" -Scan -ScanType 3 -File "C:\Users\admin\AppData\Local\Temp\Rar$VR1068.23919" | C:\Program Files\Windows Defender\MpCmdRun.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Malware Protection Command Line Utility Exit code: 2 Version: 4.18.1909.6 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2276 | powershell -noprofile "$_PSCommandPath = [Environment]::GetEnvironmentVariable('script_path', 'Process'); iex ((Get-Content -LiteralPath $_PSCommandPath) | out-string)" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3720 | C:\WINDOWS\system32\cmd.exe /S /D /c" echo marco " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4012 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$VR1068.23919\Rar$Scan69885.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
13 133
Read events
13 117
Write events
16
Delete events
0
Modification events
| (PID) Process: | (1068) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1068) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1068) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (1068) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (1068) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (1068) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\EADLCUnlockerv21.zip | |||
| (PID) Process: | (1068) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1068) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1068) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1068) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
3
Suspicious files
1
Text files
32
Unknown types
0
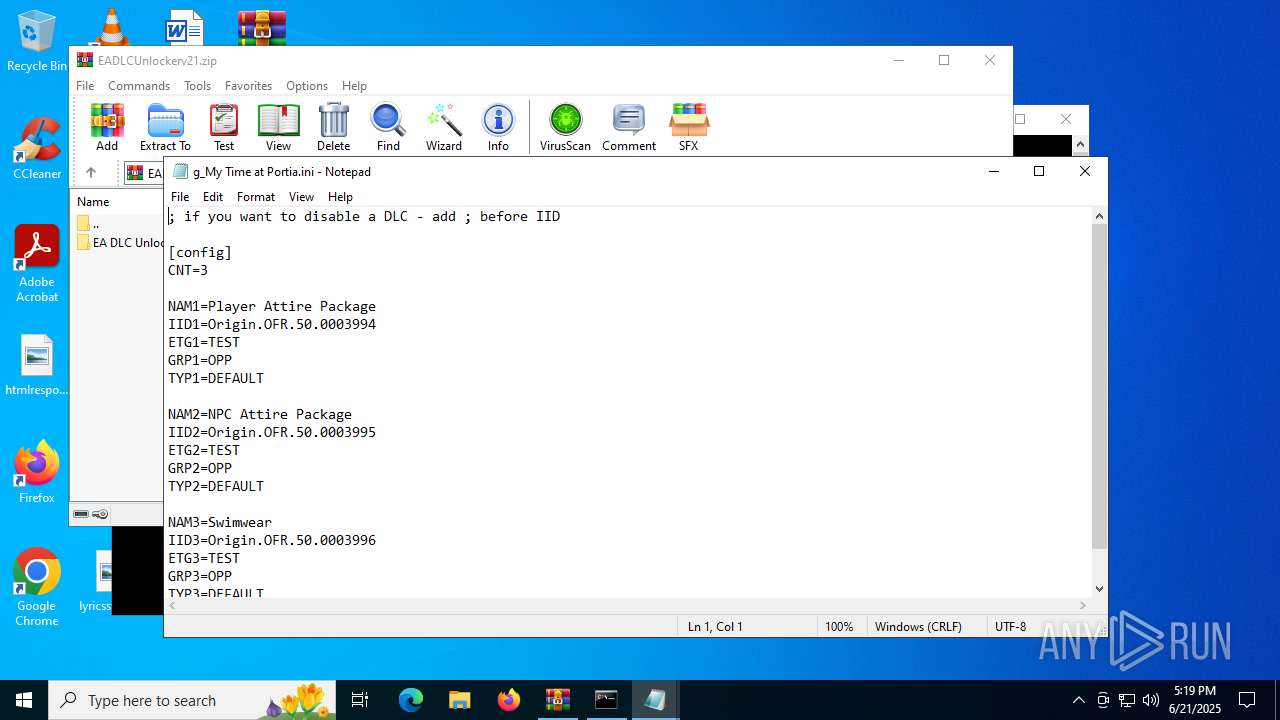
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2276 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:06577DE60FB3D286B88B704D2EFC9DAF | SHA256:DA8784873119A492D410F4660ECD0C153E2F7A270A4BBAAB2405AA2E7266C7C4 | |||
| 1068 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR1068.23919\EADLCUnlockerv21.zip\EA DLC Unlocker v2\g_STAR WARS Jedi Survivor.ini | text | |
MD5:85EC254324D2B9B8BD33FC7E1023D873 | SHA256:F66F3E8899C43A8433AF80DD9F3FD6C9C196418FBC19EB340ABE4C31513E60D6 | |||
| 2276 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_r1keyb3a.jnb.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1068 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR1068.23919\EADLCUnlockerv21.zip\EA DLC Unlocker v2\g_STAR WARS Jedi Fallen Order.ini | text | |
MD5:473C794E2D9CE2A2A68879595B0E7F04 | SHA256:06C8F383E8383C4B17362710E666D76BBC90FEAB913D0B85C96588BFB8E84C02 | |||
| 1068 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR1068.23919\EADLCUnlockerv21.zip\EA DLC Unlocker v2\g_SimCity 2013.ini | text | |
MD5:2A83A1D376BD05D4C5516AA75C9D7786 | SHA256:87DF6F4F1C246E0E5D43448929E577775983DAAFF4A016D84D2AAF89BA215052 | |||
| 1068 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR1068.23919\EADLCUnlockerv21.zip\EA DLC Unlocker v2\g_The Surge.ini | text | |
MD5:7B0CFFC89D868888402003BE8D94C0E7 | SHA256:F4930E222BBBF8815E12700B425CCC5DBC5F013573CBF9616B950D33F2C2976A | |||
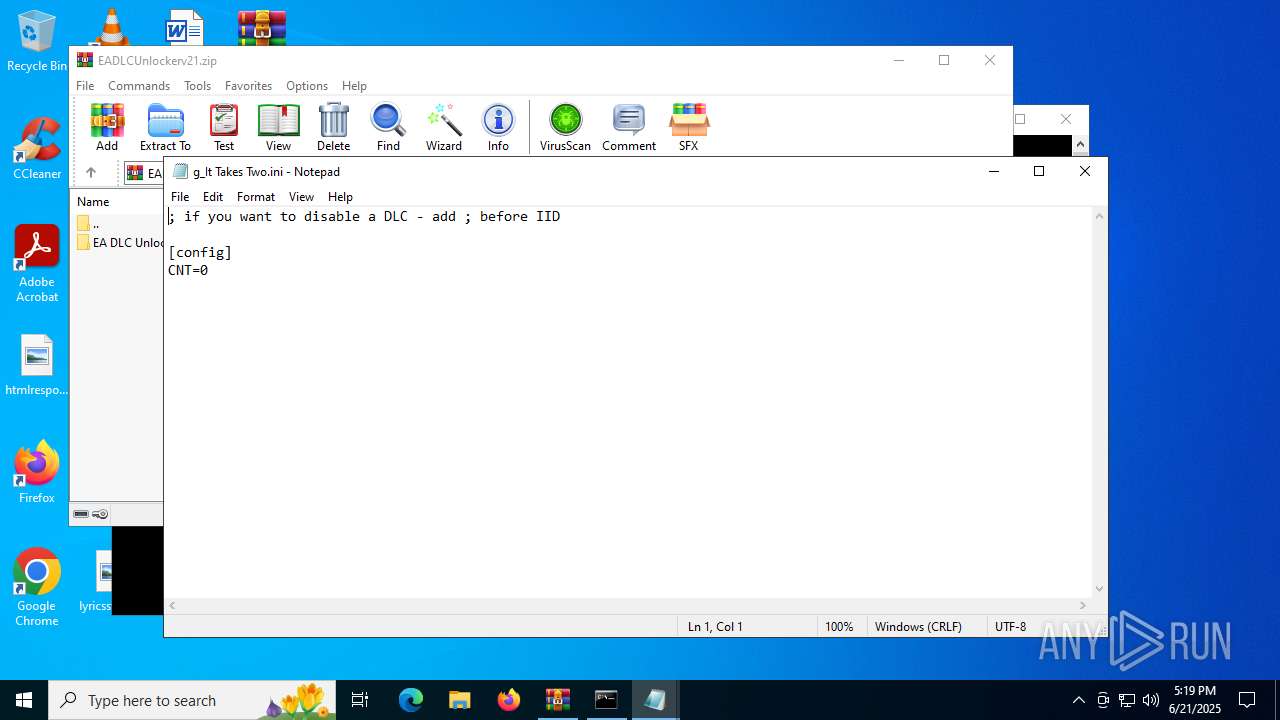
| 1068 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR1068.23919\EADLCUnlockerv21.zip\EA DLC Unlocker v2\g_It Takes Two.ini | text | |
MD5:31561ACF01F495280B2E03EC26B7812F | SHA256:3435BE593EE7214A75789417B0B6E90FB7939B26DC43A8CCA197620E72EC48AF | |||
| 1068 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR1068.23919\EADLCUnlockerv21.zip\EA DLC Unlocker v2\g_Northgard.ini | text | |
MD5:43B7F6386594BB53E06AA1B750950F47 | SHA256:FEFECE92AD8D2018072DB14B70012F812BE0AD6CAC747A1C64E73CA454D615A4 | |||
| 1068 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR1068.23919\EADLCUnlockerv21.zip\EA DLC Unlocker v2\setup_linux.sh | text | |
MD5:8C366769D0258E5B915688014508FDC8 | SHA256:B6B4797B1CE41E14B7C3E8C2A601D3487FD5D4D01477C2EF405B9C4529F1B1F6 | |||
| 1068 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR1068.23919\EADLCUnlockerv21.zip\EA DLC Unlocker v2\g_F1 23.ini | text | |
MD5:18416EFA57D527355F065064172A821D | SHA256:CFBE14FC02F08A2B941DB25DE2379A5849CEDA301E529514004948D0088945FA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
22
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5720 | RUXIMICS.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
5720 | RUXIMICS.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5720 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5720 | RUXIMICS.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 69.192.161.161:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1268 | svchost.exe | 69.192.161.161:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |