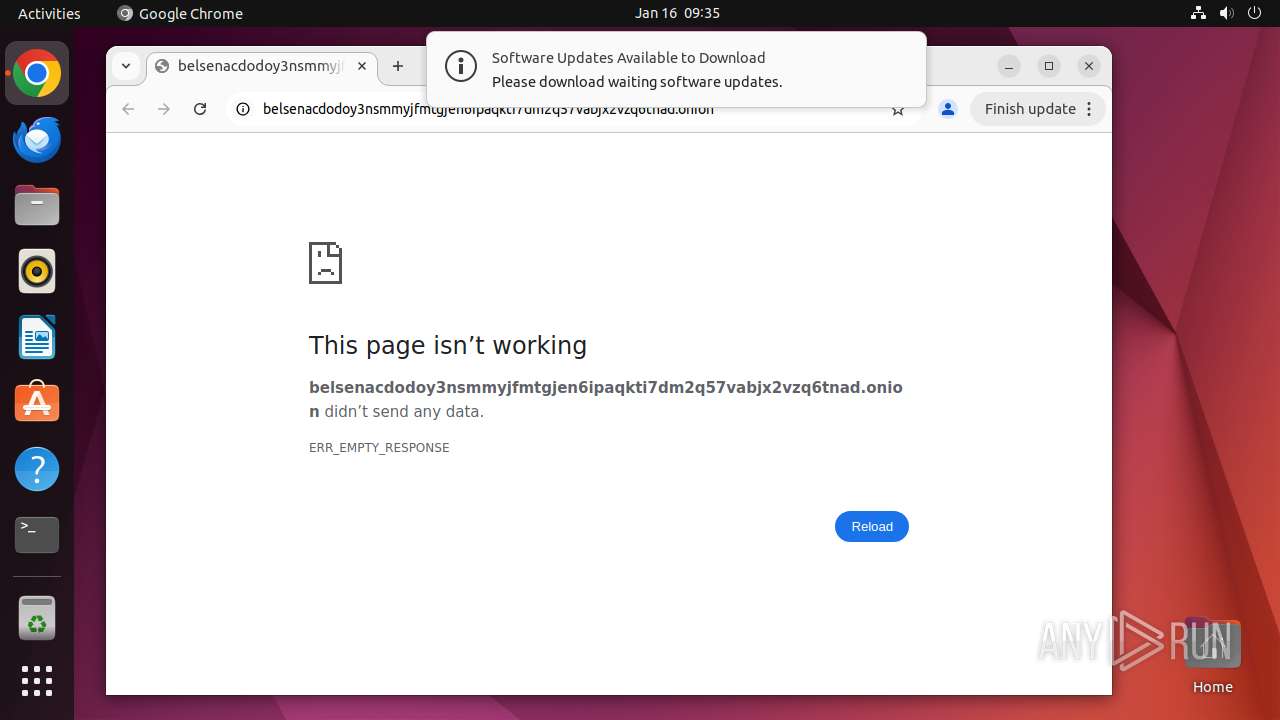
| URL: | belsenacdodoy3nsmmyjfmtgjen6ipaqkti7dm2q57vabjx2vzq6tnad.onion |
| Full analysis: | https://app.any.run/tasks/5427006e-3537-4142-99f3-2b25a594a51b |
| Verdict: | Malicious activity |
| Analysis date: | January 16, 2025, 09:35:09 |
| OS: | Ubuntu 22.04.2 LTS |
| Indicators: | |
| MD5: | 7CAB492912DF2DFEFFAF9C6FD07C7414 |
| SHA1: | 266C8B73720269A5B3D40520131073D26729C742 |
| SHA256: | 8706C4029BEC49E5CE81A41956A85C14B4A3855A791EE74B78699E7FB796C6A6 |
| SSDEEP: | 3:pE9IMAMb+TBI3FX+tELQ:plMb+aotE0 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Potential Corporate Privacy Violation
- systemd-resolved (PID: 445)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
318
Monitored processes
111
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 445 | /lib/systemd/systemd-resolved | /usr/lib/systemd/systemd-resolved | systemd | |
User: systemd-resolve Integrity Level: UNKNOWN | ||||
| 38754 | /bin/sh -c "DISPLAY=:0 sudo -iu user google-chrome belsenacdodoy3nsmmyjfmtgjen6ipaqkti7dm2q57vabjx2vzq6tnad\.onion " | /usr/bin/dash | — | any-guest-agent |
User: root Integrity Level: UNKNOWN | ||||
| 38755 | sudo -iu user google-chrome belsenacdodoy3nsmmyjfmtgjen6ipaqkti7dm2q57vabjx2vzq6tnad.onion | /usr/bin/sudo | — | dash |
User: root Integrity Level: UNKNOWN | ||||
| 38756 | /usr/bin/google-chrome belsenacdodoy3nsmmyjfmtgjen6ipaqkti7dm2q57vabjx2vzq6tnad.onion | /opt/google/chrome/chrome | — | sudo |
User: user Integrity Level: UNKNOWN | ||||
| 38757 | /usr/bin/locale-check C.UTF-8 | /usr/bin/locale-check | — | chrome |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 38758 | readlink -f /usr/bin/google-chrome | /usr/bin/readlink | — | chrome |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 38759 | dirname /opt/google/chrome/google-chrome | /usr/bin/dirname | — | chrome |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 38760 | mkdir -p /home/user/.local/share/applications | /usr/bin/mkdir | — | chrome |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 38761 | cat | /usr/bin/cat | — | chrome |
User: user Integrity Level: UNKNOWN | ||||
| 38762 | cat | /usr/bin/cat | — | chrome |
User: user Integrity Level: UNKNOWN | ||||
Executable files
0
Suspicious files
172
Text files
14
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 38756 | chrome | /home/user/.config/google-chrome/ShaderCache/data_3 | binary | |
MD5:— | SHA256:— | |||
| 38756 | chrome | /home/user/.config/google-chrome/ShaderCache/data_2 | vxd | |
MD5:— | SHA256:— | |||
| 38756 | chrome | /home/user/.config/google-chrome/ShaderCache/data_0 | binary | |
MD5:— | SHA256:— | |||
| 38756 | chrome | /home/user/.config/google-chrome/Default/GPUCache/data_3 | vxd | |
MD5:— | SHA256:— | |||
| 38756 | chrome | /home/user/.config/google-chrome/Default/GPUCache/data_2 | vxd | |
MD5:— | SHA256:— | |||
| 38756 | chrome | /home/user/.config/google-chrome/Default/GPUCache/data_0 | vxd | |
MD5:— | SHA256:— | |||
| 38756 | chrome | /home/user/.config/google-chrome/Default/History | binary | |
MD5:— | SHA256:— | |||
| 38756 | chrome | /home/user/.config/google-chrome/Default/DawnWebGPUCache/data_3 | vxd | |
MD5:— | SHA256:— | |||
| 38756 | chrome | /home/user/.config/google-chrome/Default/DawnWebGPUCache/data_2 | vxd | |
MD5:— | SHA256:— | |||
| 38756 | chrome | /home/user/.config/google-chrome/Default/DawnWebGPUCache/data_0 | vxd | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
28
TCP/UDP connections
71
DNS requests
69
Threats
11
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
38801 | chrome | GET | — | 10.235.157.191:80 | http://belsenacdodoy3nsmmyjfmtgjen6ipaqkti7dm2q57vabjx2vzq6tnad.onion/ | unknown | — | — | unknown |
— | — | GET | 204 | 185.125.190.96:80 | http://connectivity-check.ubuntu.com/ | unknown | — | — | whitelisted |
38801 | chrome | GET | — | 10.235.157.191:80 | http://belsenacdodoy3nsmmyjfmtgjen6ipaqkti7dm2q57vabjx2vzq6tnad.onion/ | unknown | — | — | unknown |
38801 | chrome | GET | — | 10.235.157.191:80 | http://belsenacdodoy3nsmmyjfmtgjen6ipaqkti7dm2q57vabjx2vzq6tnad.onion/ | unknown | — | — | unknown |
38801 | chrome | GET | — | 10.235.157.191:80 | http://belsenacdodoy3nsmmyjfmtgjen6ipaqkti7dm2q57vabjx2vzq6tnad.onion/ | unknown | — | — | unknown |
38801 | chrome | GET | — | 10.235.157.191:80 | http://belsenacdodoy3nsmmyjfmtgjen6ipaqkti7dm2q57vabjx2vzq6tnad.onion/ | unknown | — | — | unknown |
38801 | chrome | GET | — | 10.235.157.191:80 | http://belsenacdodoy3nsmmyjfmtgjen6ipaqkti7dm2q57vabjx2vzq6tnad.onion/files/FortiGate.zip | unknown | — | — | unknown |
38801 | chrome | GET | — | 10.235.157.191:80 | http://belsenacdodoy3nsmmyjfmtgjen6ipaqkti7dm2q57vabjx2vzq6tnad.onion/files/FortiGate.zip | unknown | — | — | unknown |
38801 | chrome | GET | — | 10.235.157.191:80 | http://belsenacdodoy3nsmmyjfmtgjen6ipaqkti7dm2q57vabjx2vzq6tnad.onion/files/FortiGate.zip | unknown | — | — | unknown |
38801 | chrome | GET | 403 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/diffgen-puffin/gcmjkmgdlgnkkcocmoeiminaijmmjnii/e34960f2d401eef17cbb082b4e74706241213d97e437d766de99d8bdb5fc264b | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 91.189.91.98:80 | connectivity-check.ubuntu.com | Canonical Group Limited | US | whitelisted |
— | — | 185.125.190.96:80 | — | Canonical Group Limited | GB | unknown |
484 | avahi-daemon | 224.0.0.251:5353 | — | — | — | unknown |
1178 | snap-store | 212.102.56.179:443 | odrs.gnome.org | Datacamp Limited | DE | whitelisted |
38801 | chrome | 10.235.157.191:80 | belsenacdodoy3nsmmyjfmtgjen6ipaqkti7dm2q57vabjx2vzq6tnad.onion | — | — | unknown |
38801 | chrome | 10.235.157.191:443 | belsenacdodoy3nsmmyjfmtgjen6ipaqkti7dm2q57vabjx2vzq6tnad.onion | — | — | unknown |
38801 | chrome | 142.250.185.227:443 | clientservices.googleapis.com | GOOGLE | US | whitelisted |
38801 | chrome | 142.250.184.202:443 | safebrowsingohttpgateway.googleapis.com | GOOGLE | US | whitelisted |
38801 | chrome | 108.177.127.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
38801 | chrome | 146.75.121.91:443 | google-ohttp-relay-safebrowsing.fastly-edge.com | FASTLY | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
odrs.gnome.org |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
safebrowsingohttpgateway.googleapis.com |
| whitelisted |
belsenacdodoy3nsmmyjfmtgjen6ipaqkti7dm2q57vabjx2vzq6tnad.onion |
| unknown |
accounts.google.com |
| whitelisted |
google-ohttp-relay-safebrowsing.fastly-edge.com |
| unknown |
api.snapcraft.io |
| whitelisted |
update.googleapis.com |
| whitelisted |
179.100.168.192.in-addr.arpa |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
445 | systemd-resolved | Potential Corporate Privacy Violation | ET POLICY DNS Query for TOR Hidden Domain .onion Accessible Via TOR |
445 | systemd-resolved | Potential Corporate Privacy Violation | ET POLICY DNS Query for TOR Hidden Domain .onion Accessible Via TOR |
445 | systemd-resolved | Potential Corporate Privacy Violation | ET POLICY DNS Query for TOR Hidden Domain .onion Accessible Via TOR |
445 | systemd-resolved | Potential Corporate Privacy Violation | ET POLICY DNS Query for TOR Hidden Domain .onion Accessible Via TOR |
445 | systemd-resolved | Potential Corporate Privacy Violation | ET POLICY DNS Query for TOR Hidden Domain .onion Accessible Via TOR |
445 | systemd-resolved | Potential Corporate Privacy Violation | ET POLICY DNS Query for TOR Hidden Domain .onion Accessible Via TOR |
445 | systemd-resolved | Potential Corporate Privacy Violation | ET POLICY DNS Query for TOR Hidden Domain .onion Accessible Via TOR |
445 | systemd-resolved | Potential Corporate Privacy Violation | ET POLICY DNS Query for TOR Hidden Domain .onion Accessible Via TOR |
445 | systemd-resolved | Potential Corporate Privacy Violation | ET POLICY DNS Query for TOR Hidden Domain .onion Accessible Via TOR |
445 | systemd-resolved | Potential Corporate Privacy Violation | ET POLICY DNS Query for TOR Hidden Domain .onion Accessible Via TOR |