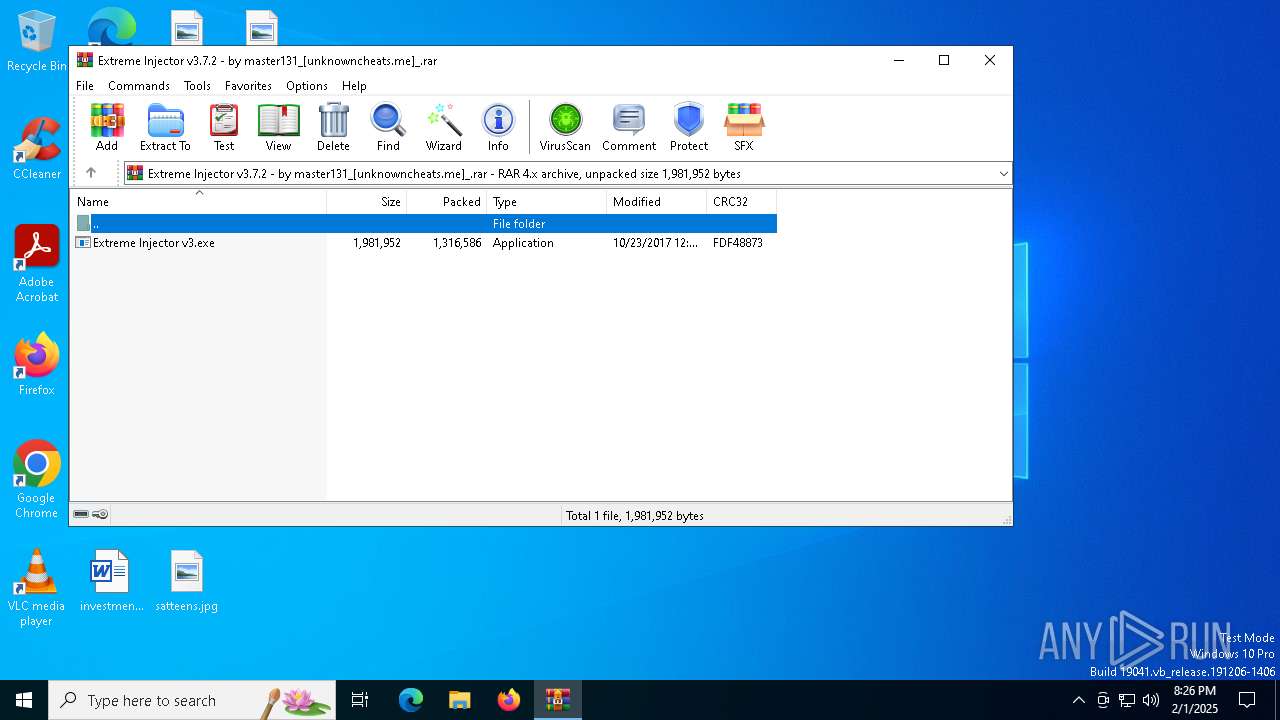
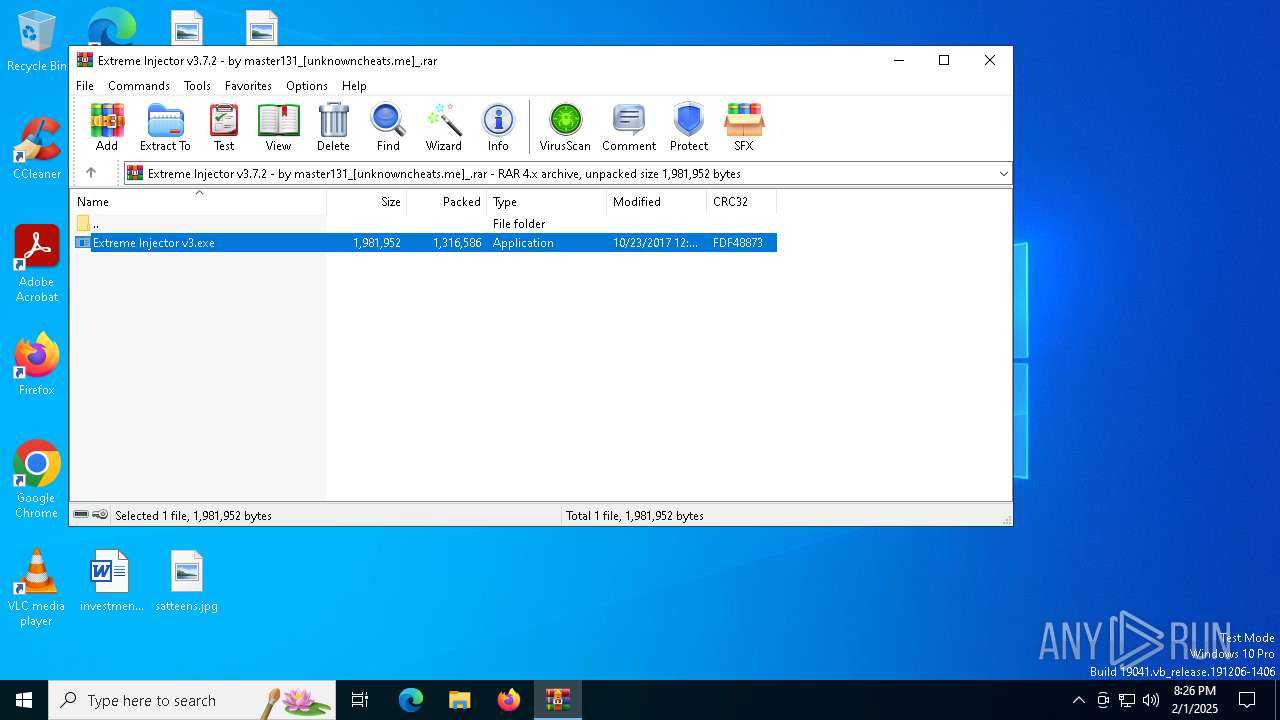
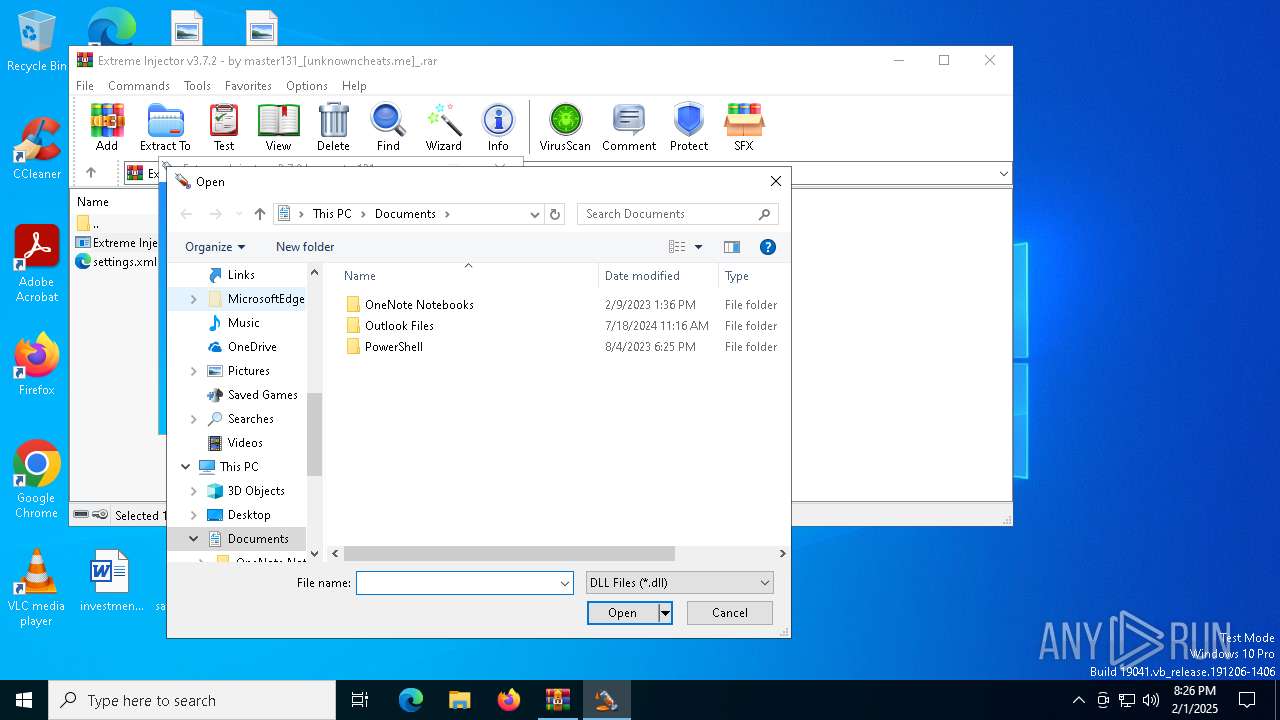
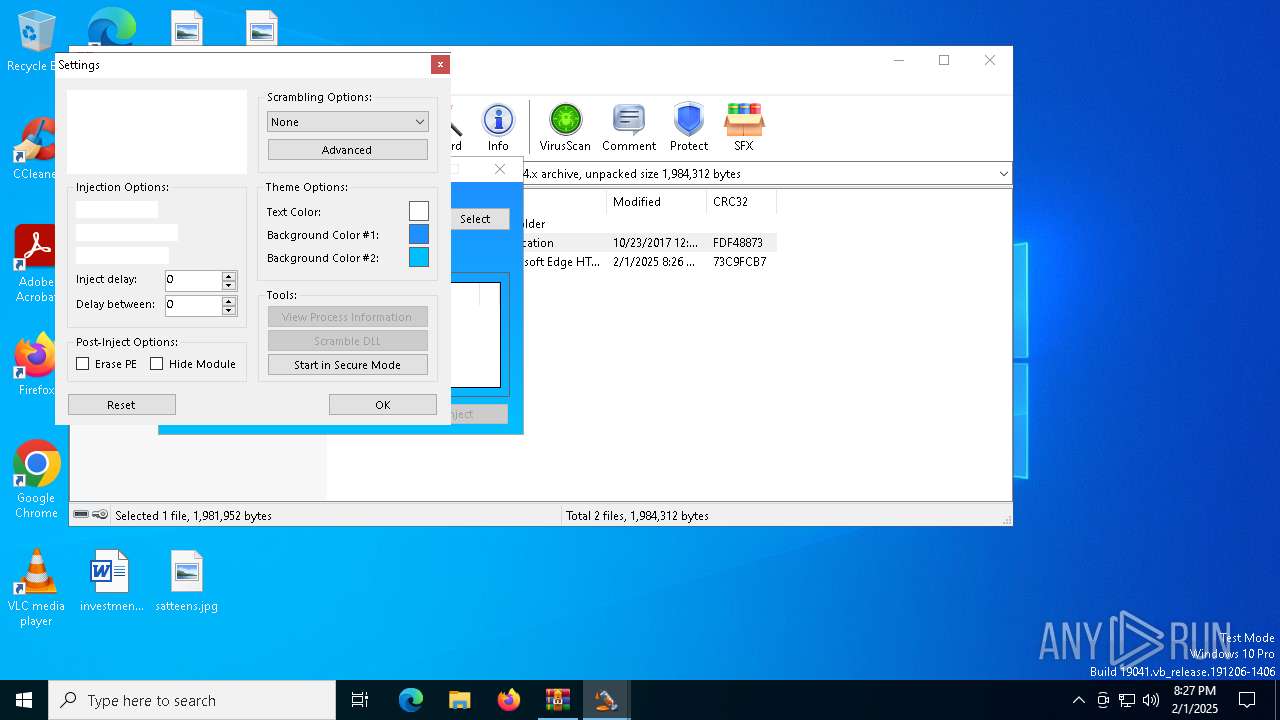
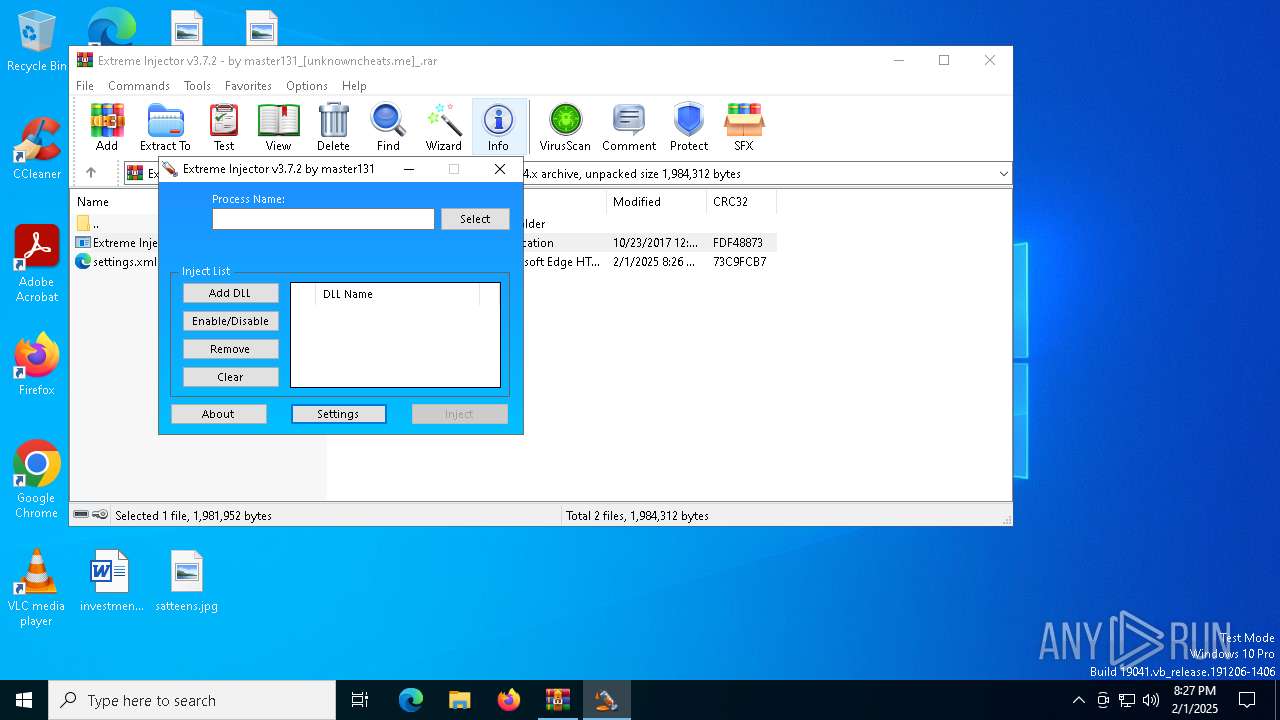
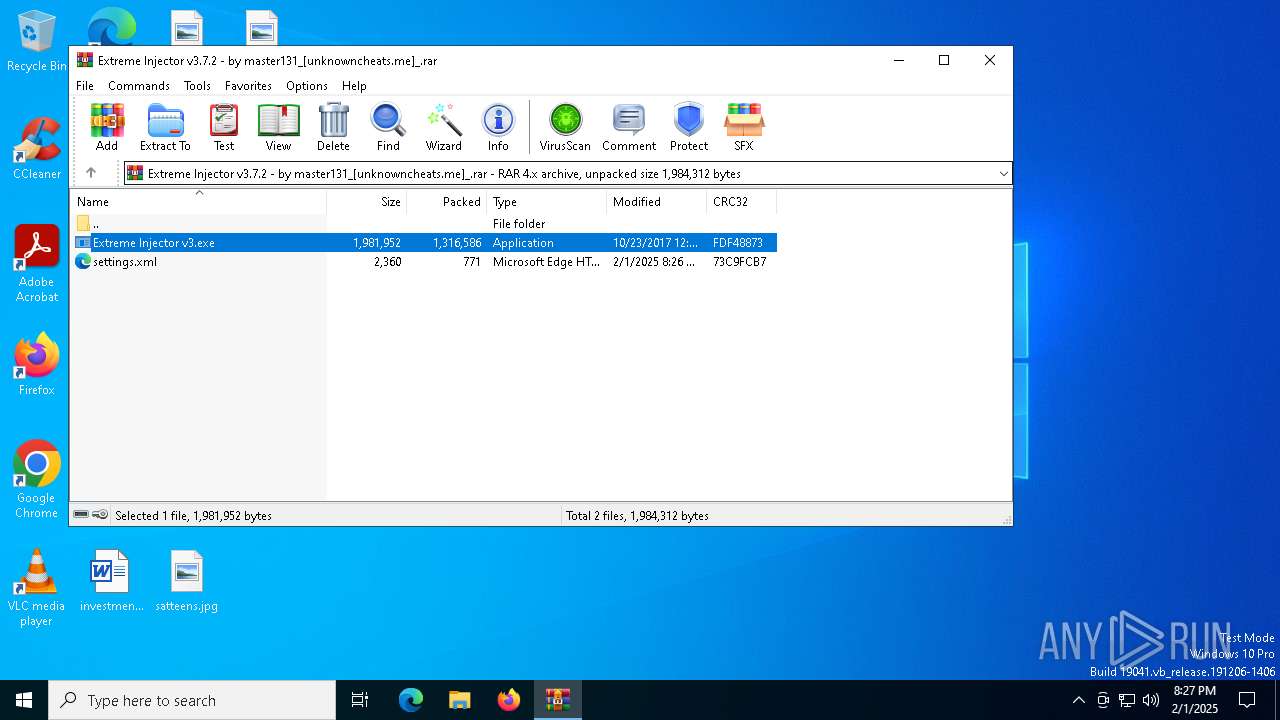
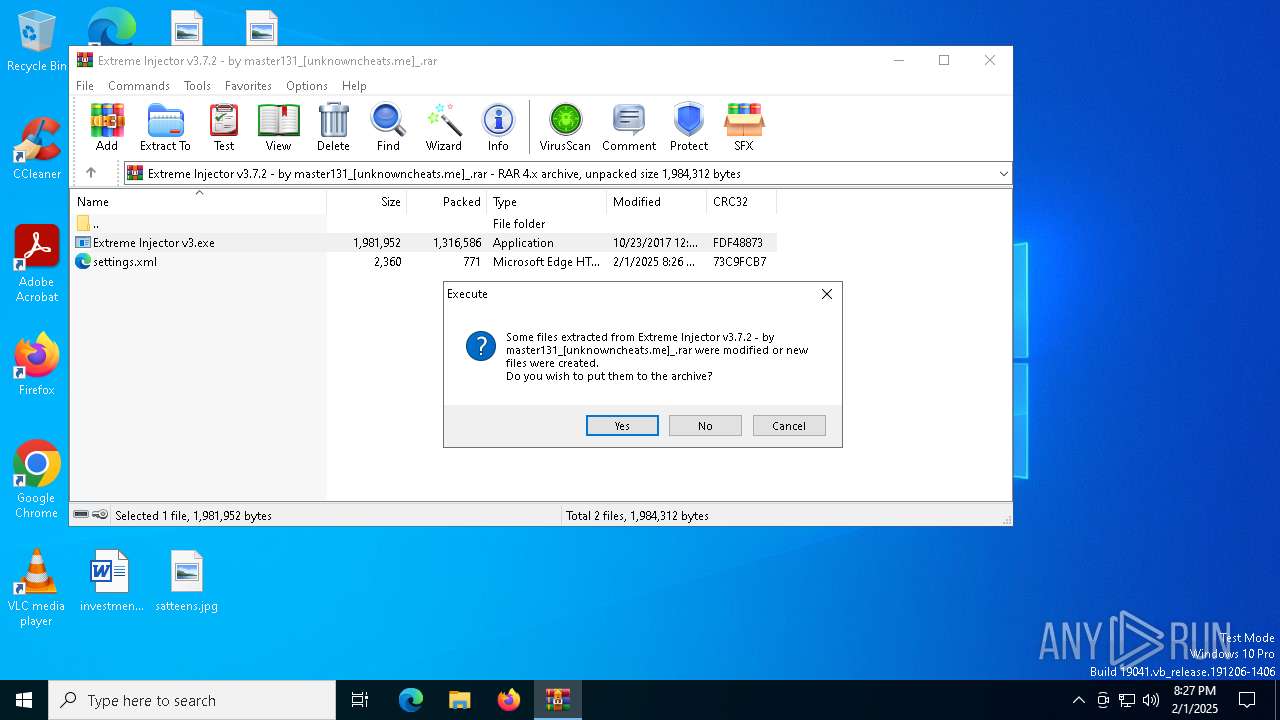
| File name: | Extreme Injector v3.7.2 - by master131_[unknowncheats.me]_.rar |
| Full analysis: | https://app.any.run/tasks/8493acea-a314-465a-82e1-0b34d17c2760 |
| Verdict: | Malicious activity |
| Analysis date: | February 01, 2025, 20:26:11 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | 7453B0B6C9CCAF7ABD220F68C03C37EA |
| SHA1: | E622F382E9680BEF59EEA35BD0A7E37488BBD755 |
| SHA256: | 86F5B99943EB87662AF3CA9EC26163AB2BFEB7B892C8CC068B8EB9589035ADBC |
| SSDEEP: | 49152:gQcRpVknF2n24sduR+7j/TpOobqsMRy7nwU/x/n6OHYFqZaSRRcKwgDjYKP9jyDh:gHaFc2MQ0ob2ywkv7HYiDclgVjK3861f |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 3540)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3540)
- Extreme Injector v3.exe (PID: 6356)
- Extreme Injector v3.exe (PID: 6576)
Reads the date of Windows installation
- Extreme Injector v3.exe (PID: 6356)
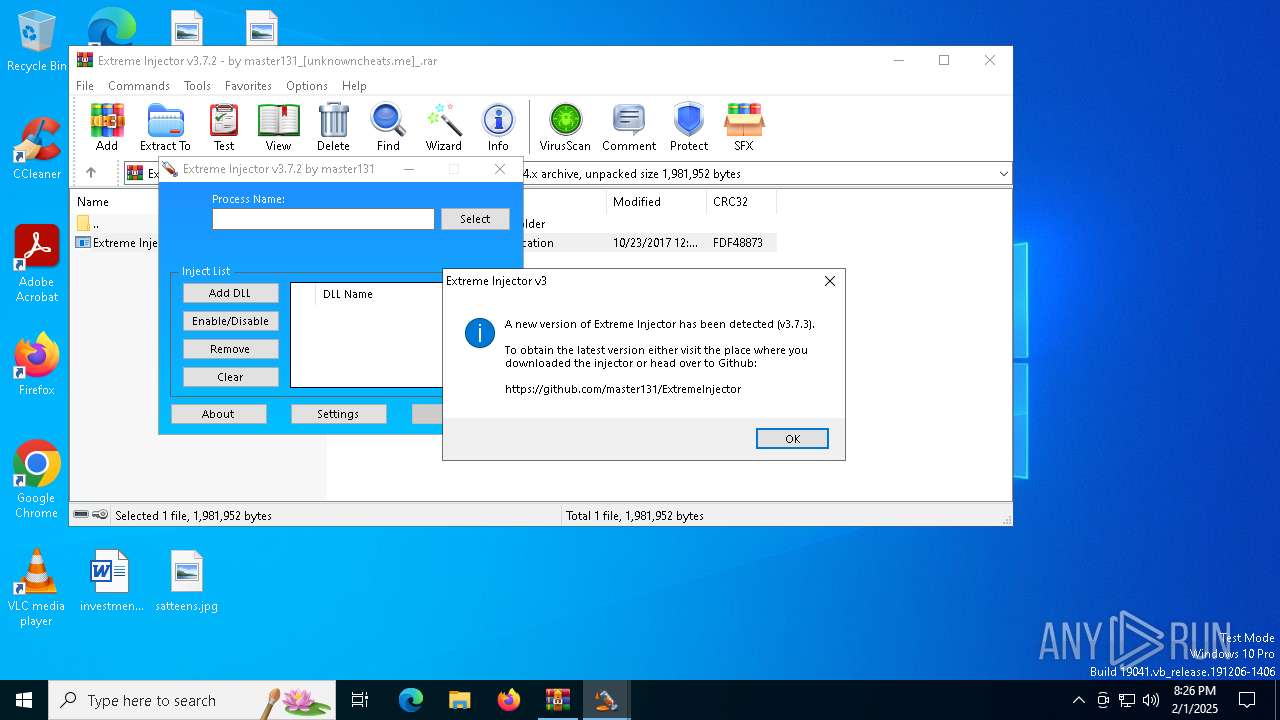
Application launched itself
- Extreme Injector v3.exe (PID: 6356)
Reads Internet Explorer settings
- Extreme Injector v3.exe (PID: 6576)
INFO
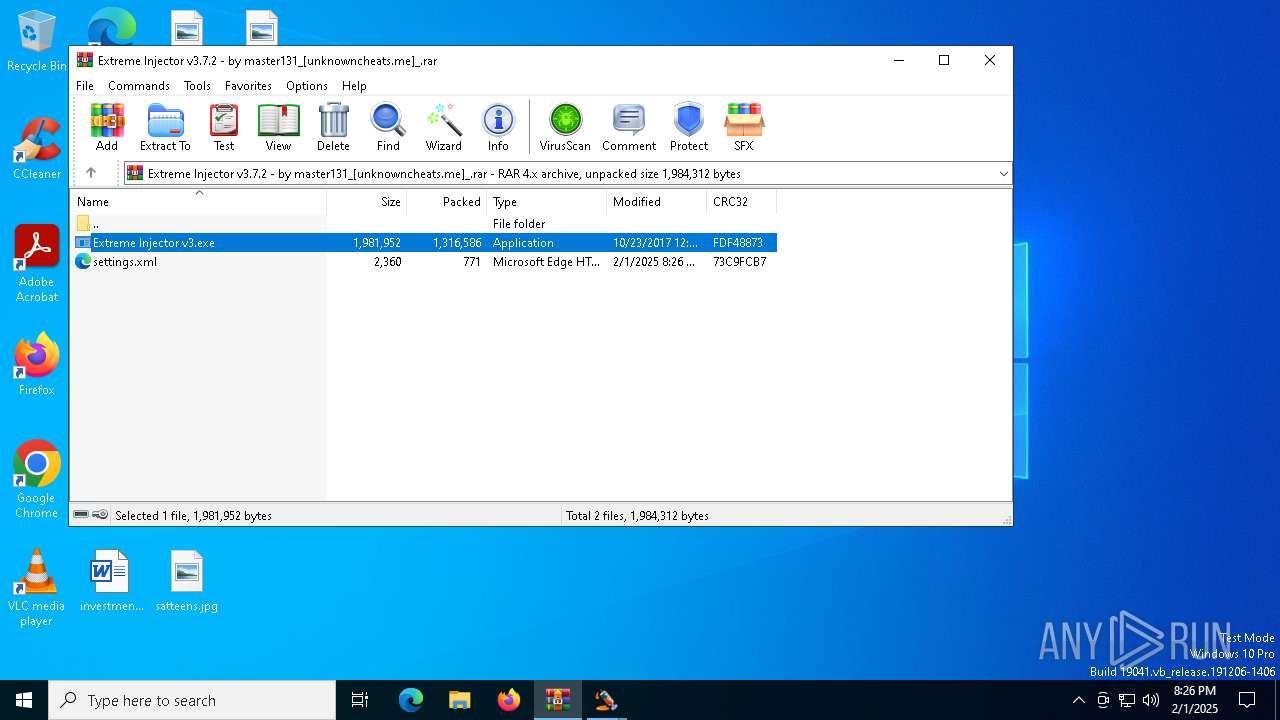
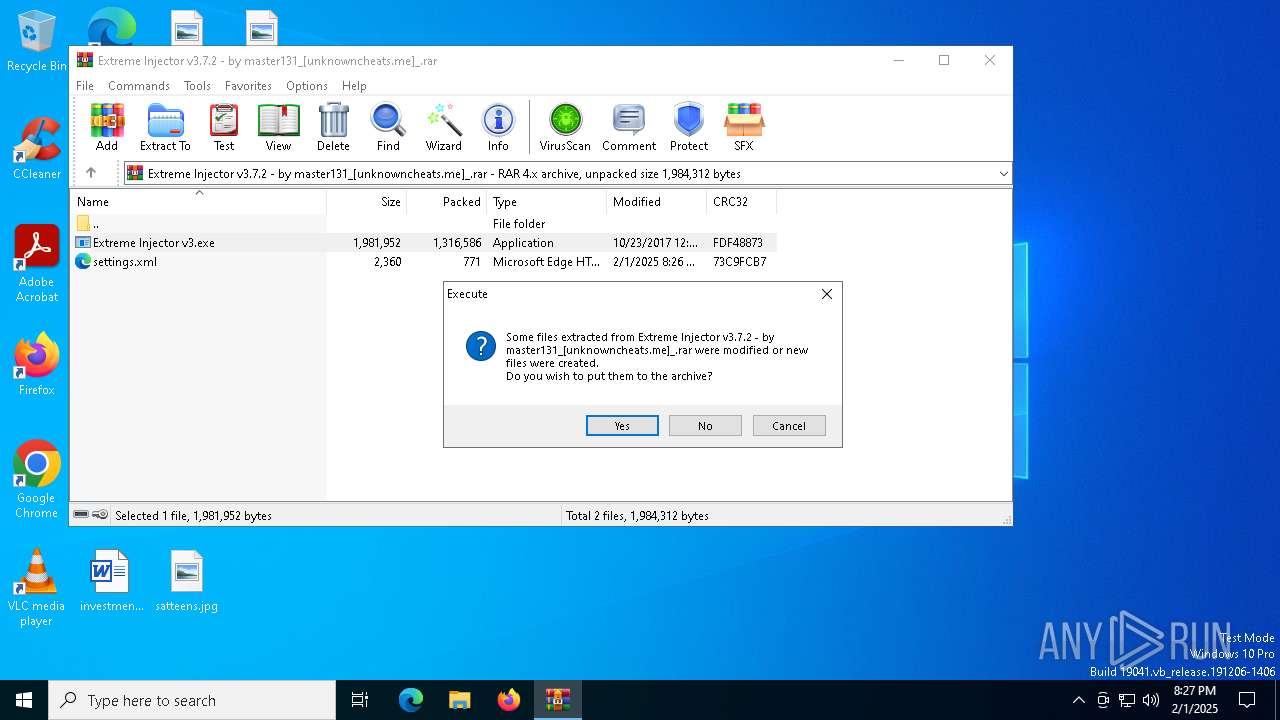
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3540)
Reads the computer name
- Extreme Injector v3.exe (PID: 6356)
- Extreme Injector v3.exe (PID: 6576)
Checks supported languages
- Extreme Injector v3.exe (PID: 6356)
- Extreme Injector v3.exe (PID: 6576)
Reads the machine GUID from the registry
- Extreme Injector v3.exe (PID: 6356)
- Extreme Injector v3.exe (PID: 6576)
Process checks computer location settings
- Extreme Injector v3.exe (PID: 6356)
Disables trace logs
- Extreme Injector v3.exe (PID: 6576)
Create files in a temporary directory
- Extreme Injector v3.exe (PID: 6576)
Reads Environment values
- Extreme Injector v3.exe (PID: 6576)
Checks proxy server information
- Extreme Injector v3.exe (PID: 6576)
Reads the software policy settings
- Extreme Injector v3.exe (PID: 6576)
Potential library load (Base64 Encoded 'LoadLibrary')
- Extreme Injector v3.exe (PID: 6576)
Potential access to remote process (Base64 Encoded 'OpenProcess')
- Extreme Injector v3.exe (PID: 6576)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| FileVersion: | RAR v4 |
|---|---|
| CompressedSize: | 1316635 |
| UncompressedSize: | 1981952 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2017:10:23 00:11:58 |
| PackingMethod: | Normal |
| ArchivedFileName: | Extreme Injector v3.exe |
Total processes
131
Monitored processes
3
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3540 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Extreme Injector v3.7.2 - by master131_[unknowncheats.me]_.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 6356 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3540.39263\Extreme Injector v3.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3540.39263\Extreme Injector v3.exe | — | WinRAR.exe | |||||||||||
User: admin Company: master131 Integrity Level: MEDIUM Description: Extreme Injector Exit code: 0 Version: 3.7.2.0 Modules
| |||||||||||||||
| 6576 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3540.39263\Extreme Injector v3.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3540.39263\Extreme Injector v3.exe | Extreme Injector v3.exe | ||||||||||||
User: admin Company: master131 Integrity Level: HIGH Description: Extreme Injector Exit code: 0 Version: 3.7.2.0 Modules
| |||||||||||||||
Total events
8 669
Read events
8 590
Write events
78
Delete events
1
Modification events
| (PID) Process: | (3540) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (3540) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (3540) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (3540) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Extreme Injector v3.7.2 - by master131_[unknowncheats.me]_.rar | |||
| (PID) Process: | (3540) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3540) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3540) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3540) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6576) Extreme Injector v3.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Extreme Injector v3_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (6576) Extreme Injector v3.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Extreme Injector v3_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
1
Suspicious files
6
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3540 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3540.39263\Extreme Injector v3.exe | executable | |
MD5:C4394FB4DAAF350CDBF5303D812E917E | SHA256:0AC3387B6E0283C972722C2A6664EE23AC5BA10640D18B827E8732F5C57E7D2C | |||
| 3540 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Extreme Injector v3.7.2 - by master131_[unknowncheats.me]_.rar | compressed | |
MD5:B2503C0D6B1BF365F112DB62D8C4D52D | SHA256:E08932A73148FB932969BE1DA19B34A34A9124443CC393E70B432BD7AC8FCCAA | |||
| 3540 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Extreme Injector v3.7.2 - by master131_[unknowncheats.me]_.bak3540.40049 | compressed | |
MD5:7453B0B6C9CCAF7ABD220F68C03C37EA | SHA256:86F5B99943EB87662AF3CA9EC26163AB2BFEB7B892C8CC068B8EB9589035ADBC | |||
| 3540 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\__rar_3540.43943 | compressed | |
MD5:4B36299ACACD56226114D130CBC16EA8 | SHA256:D0BDA615B8B54F552D514CDCDA66714AFE2AB49FDE2FD48DA0D14A215647FB97 | |||
| 3540 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Extreme Injector v3.7.2 - by master131_[unknowncheats.me]_.bak3540.43965 | compressed | |
MD5:B2503C0D6B1BF365F112DB62D8C4D52D | SHA256:E08932A73148FB932969BE1DA19B34A34A9124443CC393E70B432BD7AC8FCCAA | |||
| 6576 | Extreme Injector v3.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3540.39263\settings.xml | xml | |
MD5:E84591FE639CAD19B8FD2DC779A3A19C | SHA256:A789D349D44CD1E87395AB4E4AF27D2A6523E686CA220A76338D8B1EDC51F3E9 | |||
| 3540 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\__rar_3540.40027 | compressed | |
MD5:B2503C0D6B1BF365F112DB62D8C4D52D | SHA256:E08932A73148FB932969BE1DA19B34A34A9124443CC393E70B432BD7AC8FCCAA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
33
DNS requests
19
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6276 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6760 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6276 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5064 | SearchApp.exe | 92.123.104.44:443 | — | Akamai International B.V. | DE | unknown |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5764 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
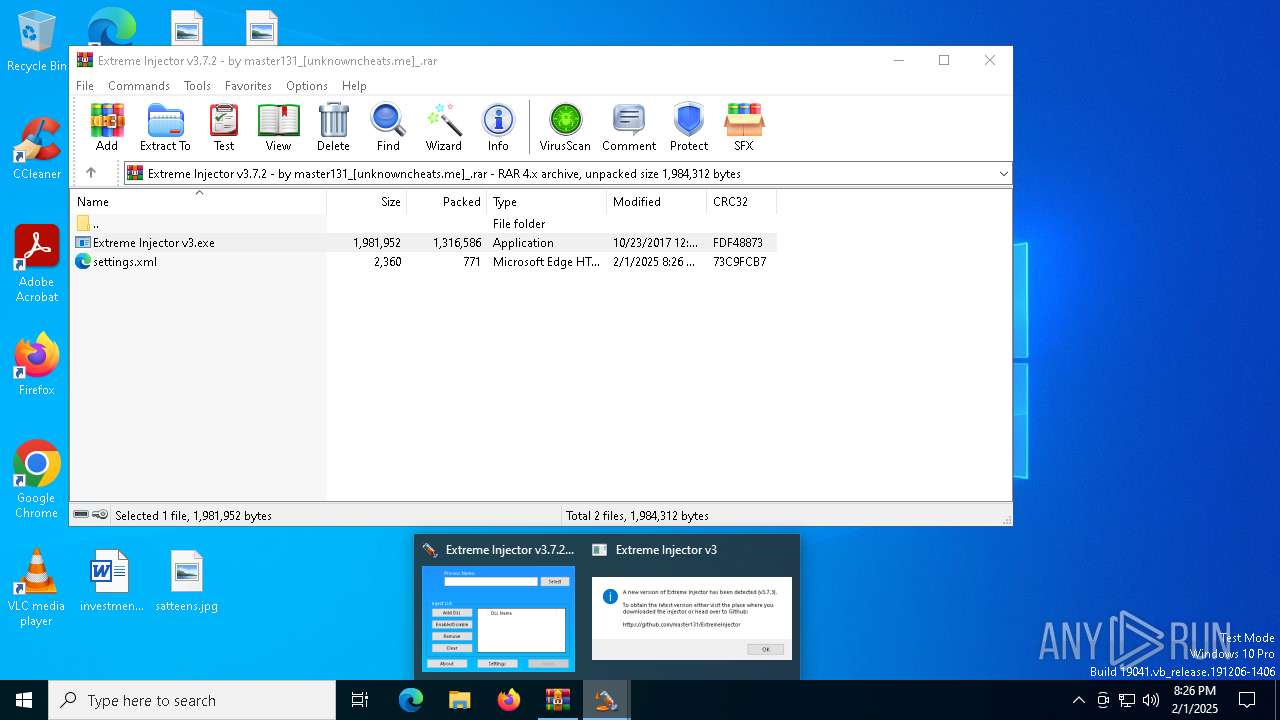
6576 | Extreme Injector v3.exe | 185.199.109.133:443 | raw.githubusercontent.com | FASTLY | US | shared |
5064 | SearchApp.exe | 92.123.104.66:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
raw.githubusercontent.com |
| shared |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |