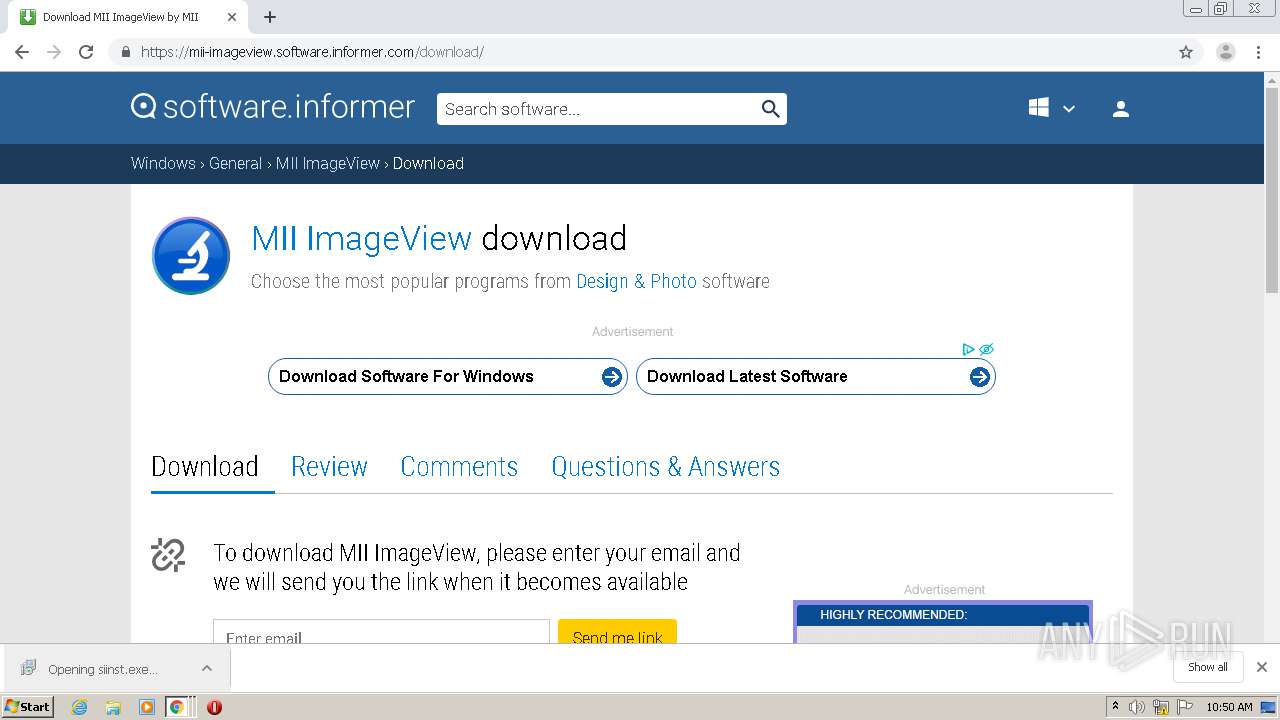
| URL: | https://mii-imageview.software.informer.com/4.1/ |
| Full analysis: | https://app.any.run/tasks/b8634ee2-613a-436f-8167-bb104ceb3ef5 |
| Verdict: | Malicious activity |
| Analysis date: | December 17, 2020, 10:48:56 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | D4BCFCF901E3CD17E40072A69B6780B6 |
| SHA1: | 322780DFB6DC39258ACB44299B05464C60DC6E76 |
| SHA256: | 86F2A7249554FD71A98DED758FAF2D4EF83DE76233D1CBEF7AF1A9295B79BB52 |
| SSDEEP: | 3:N81MIrr5hj4kK:2Pb0kK |
MALICIOUS
Application was dropped or rewritten from another process
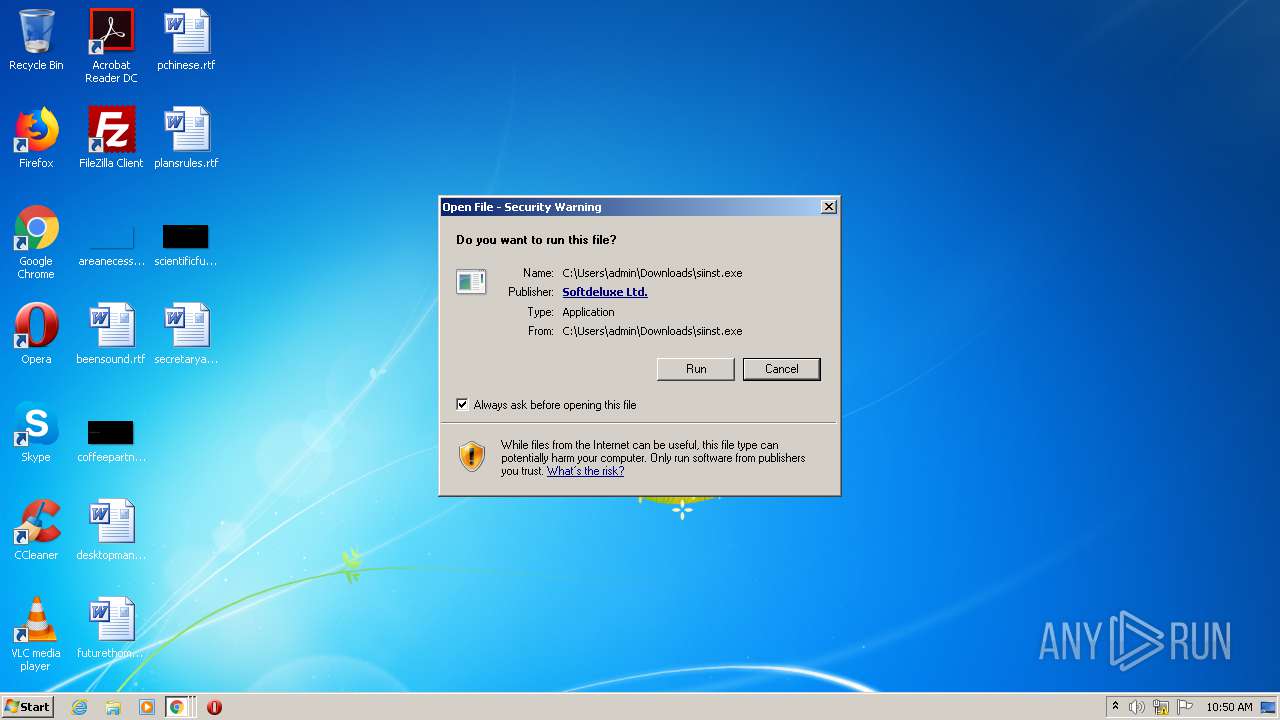
- siinst.exe (PID: 1916)
- siinst.exe (PID: 3828)
- softinfo.exe (PID: 2456)
- softinfo.exe (PID: 3552)
Drops executable file immediately after starts
- siinst.exe (PID: 3828)
- siinst.exe (PID: 1916)
- siinst.tmp (PID: 2784)
Uses Task Scheduler to autorun other applications
- siinst.tmp (PID: 2784)
Loads dropped or rewritten executable
- softinfo.exe (PID: 2456)
- softinfo.exe (PID: 3552)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 3044)
SUSPICIOUS
Executable content was dropped or overwritten
- siinst.exe (PID: 1916)
- chrome.exe (PID: 2600)
- siinst.exe (PID: 3828)
- siinst.tmp (PID: 2784)
Drops a file with too old compile date
- siinst.tmp (PID: 2784)
Reads Windows owner or organization settings
- siinst.tmp (PID: 2784)
Drops a file that was compiled in debug mode
- siinst.tmp (PID: 2784)
Reads the Windows organization settings
- siinst.tmp (PID: 2784)
Creates a directory in Program Files
- siinst.tmp (PID: 2784)
Creates files in the user directory
- siinst.tmp (PID: 2784)
- softinfo.exe (PID: 3552)
Changes IE settings (feature browser emulation)
- siinst.tmp (PID: 2784)
Searches for installed software
- softinfo.exe (PID: 3552)
Reads internet explorer settings
- softinfo.exe (PID: 3552)
Application launched itself
- taskmgr.exe (PID: 376)
INFO
Reads settings of System Certificates
- chrome.exe (PID: 2544)
- chrome.exe (PID: 2600)
- softinfo.exe (PID: 3552)
Reads the hosts file
- chrome.exe (PID: 2600)
- chrome.exe (PID: 2544)
Application was dropped or rewritten from another process
- siinst.tmp (PID: 2948)
- siinst.tmp (PID: 2784)
Application launched itself
- chrome.exe (PID: 2600)
Loads dropped or rewritten executable
- siinst.tmp (PID: 2784)
Creates files in the program directory
- siinst.tmp (PID: 2784)
Creates a software uninstall entry
- siinst.tmp (PID: 2784)
Manual execution by user
- taskmgr.exe (PID: 376)
- opera.exe (PID: 3624)
Dropped object may contain Bitcoin addresses
- softinfo.exe (PID: 3552)
Creates files in the user directory
- opera.exe (PID: 3624)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
71
Monitored processes
27
Malicious processes
7
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 376 | "C:\Windows\system32\taskmgr.exe" /4 | C:\Windows\system32\taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Task Manager Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 820 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1032,16909910458703851027,6012915723283404053,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=1870443988631885747 --renderer-client-id=9 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3636 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 824 | "C:\Windows\system32\taskmgr.exe" /1 | C:\Windows\system32\taskmgr.exe | taskmgr.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Task Manager Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1112 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1032,16909910458703851027,6012915723283404053,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAADgACAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=6947927490189175637 --mojo-platform-channel-handle=1036 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1328 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1032,16909910458703851027,6012915723283404053,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=10602435294823241758 --renderer-client-id=12 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3264 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
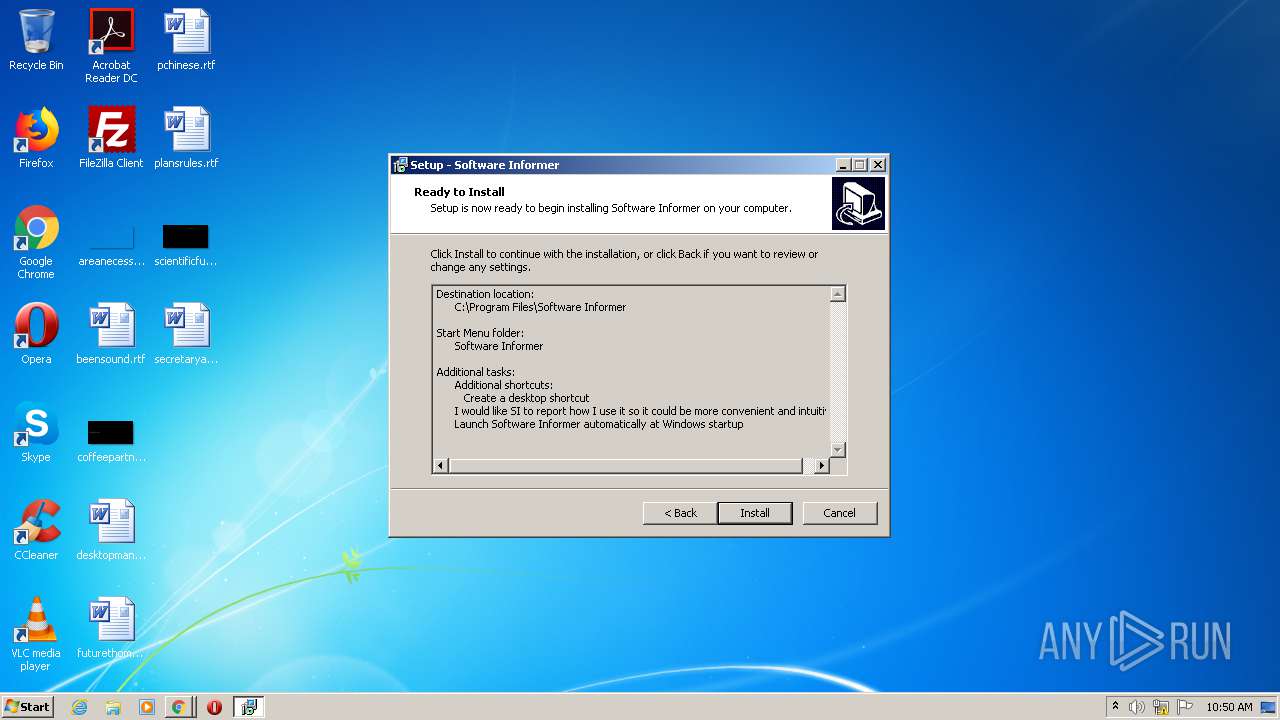
| 1916 | "C:\Users\admin\Downloads\siinst.exe" | C:\Users\admin\Downloads\siinst.exe | chrome.exe | ||||||||||||
User: admin Company: Informer Technologies, Inc. Integrity Level: MEDIUM Description: Software Informer Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 1936 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1032,16909910458703851027,6012915723283404053,131072 --enable-features=PasswordImport --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=9018901868203210115 --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2340 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2088 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1032,16909910458703851027,6012915723283404053,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=7182558958724426162 --renderer-client-id=13 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3504 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2144 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1032,16909910458703851027,6012915723283404053,131072 --enable-features=PasswordImport --disable-gpu-sandbox --use-gl=disabled --gpu-preferences=KAAAAAAAAADgACAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=9081266360383737498 --mojo-platform-channel-handle=2400 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2164 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1032,16909910458703851027,6012915723283404053,131072 --enable-features=PasswordImport --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=7781463322721777002 --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2176 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
2 914
Read events
2 714
Write events
195
Delete events
5
Modification events
| (PID) Process: | (2600) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2600) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2600) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (2600) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (2600) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2616) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 2600-13252675751867125 |
Value: 259 | |||
| (PID) Process: | (2600) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (2600) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (2600) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3252-13245750958665039 |
Value: 0 | |||
| (PID) Process: | (2600) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
Executable files
20
Suspicious files
131
Text files
274
Unknown types
17
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2600 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-5FDB37A8-A28.pma | — | |
MD5:— | SHA256:— | |||
| 2600 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\f46deec4-e3ca-46f0-9d6e-4c21a010e64d.tmp | — | |
MD5:— | SHA256:— | |||
| 2600 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000048.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2600 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Session Storage\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2600 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2600 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2600 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RF18cbf6.TMP | text | |
MD5:— | SHA256:— | |||
| 2600 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Feature Engagement Tracker\EventDB\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2600 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2600 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old~RF18ce47.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
137
DNS requests
57
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3624 | opera.exe | GET | 200 | 93.184.220.29:80 | http://crl4.digicert.com/DigiCertHighAssuranceEVRootCA.crl | US | der | 592 b | whitelisted |
3552 | softinfo.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | US | der | 471 b | whitelisted |
3552 | softinfo.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | US | der | 727 b | whitelisted |
3552 | softinfo.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRDC9IOTxN6GmyRjyTl2n4yTUczyAQUjYxexFStiuF36Zv5mwXhuAGNYeECEQC98wdfa2xiQewEDHzwctEh | US | der | 472 b | whitelisted |
3552 | softinfo.exe | GET | 200 | 74.117.179.74:80 | http://si5-s0.infcdn.net/img/win_v3/refresh_bg.png | US | image | 4.52 Kb | suspicious |
3552 | softinfo.exe | GET | 200 | 172.217.21.195:80 | http://ocsp.pki.goog/gts1o1core/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEB6CSjN0CZFqBQAAAAB%2BjGs%3D | US | der | 471 b | whitelisted |
3552 | softinfo.exe | GET | 200 | 100.25.93.238:80 | http://software.informer.com/images/online/gaotd.jpg | US | image | 71.9 Kb | whitelisted |
3552 | softinfo.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRDC9IOTxN6GmyRjyTl2n4yTUczyAQUjYxexFStiuF36Zv5mwXhuAGNYeECEDCUpvoIGi%2BlQzucdYHiLwk%3D | US | der | 471 b | whitelisted |
3552 | softinfo.exe | GET | 200 | 172.217.21.195:80 | http://ocsp.pki.goog/gsr2/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBTgXIsxbvr2lBkPpoIEVRE6gHlCnAQUm%2BIHV2ccHsBqBt5ZtJot39wZhi4CDQHjtJqhjYqpgSVpULg%3D | US | der | 468 b | whitelisted |
3552 | softinfo.exe | GET | 200 | 74.117.179.74:80 | http://si5-s0.infcdn.net/img/win_v3/background.png | US | image | 16.8 Kb | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2544 | chrome.exe | 100.25.93.238:443 | mii-imageview.software.informer.com | — | US | unknown |
2544 | chrome.exe | 208.88.224.98:443 | i.informer.com | WZ Communications Inc. | US | unknown |
2544 | chrome.exe | 204.155.159.109:443 | hits.informer.com | WZ Communications Inc. | US | unknown |
2544 | chrome.exe | 172.217.22.110:443 | www.google-analytics.com | Google Inc. | US | whitelisted |
2544 | chrome.exe | 74.117.179.70:443 | img.informer.com | WZ Communications Inc. | US | suspicious |
2544 | chrome.exe | 172.217.18.162:443 | partner.googleadservices.com | Google Inc. | US | whitelisted |
2544 | chrome.exe | 216.58.212.170:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
2544 | chrome.exe | 74.117.179.74:443 | art-u3.infcdn.net | WZ Communications Inc. | US | unknown |
2544 | chrome.exe | 216.58.207.65:443 | tpc.googlesyndication.com | Google Inc. | US | whitelisted |
2544 | chrome.exe | 172.217.23.110:443 | clients1.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
mii-imageview.software.informer.com |
| suspicious |
accounts.google.com |
| shared |
img.informer.com |
| whitelisted |
i.informer.com |
| whitelisted |
www.google-analytics.com |
| whitelisted |
hits.informer.com |
| unknown |
pagead2.googlesyndication.com |
| whitelisted |
art-u3.infcdn.net |
| suspicious |
art-u2.infcdn.net |
| suspicious |
software.informer.com |
| whitelisted |