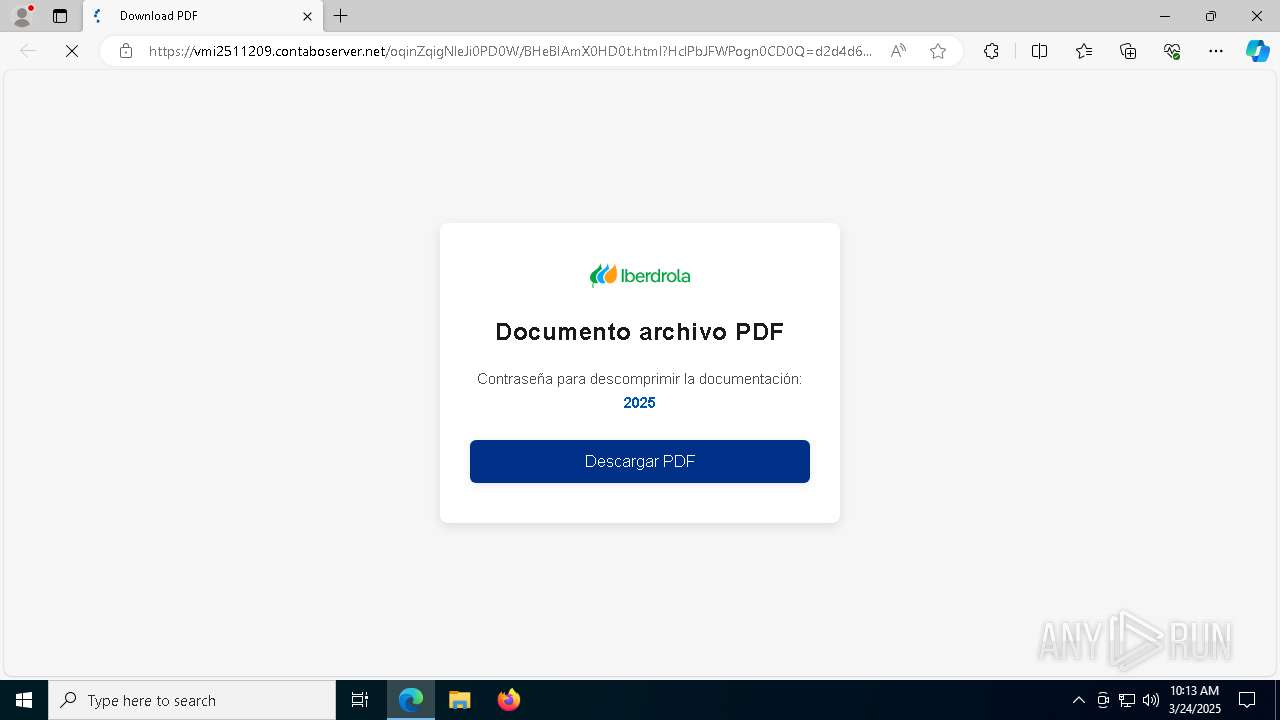
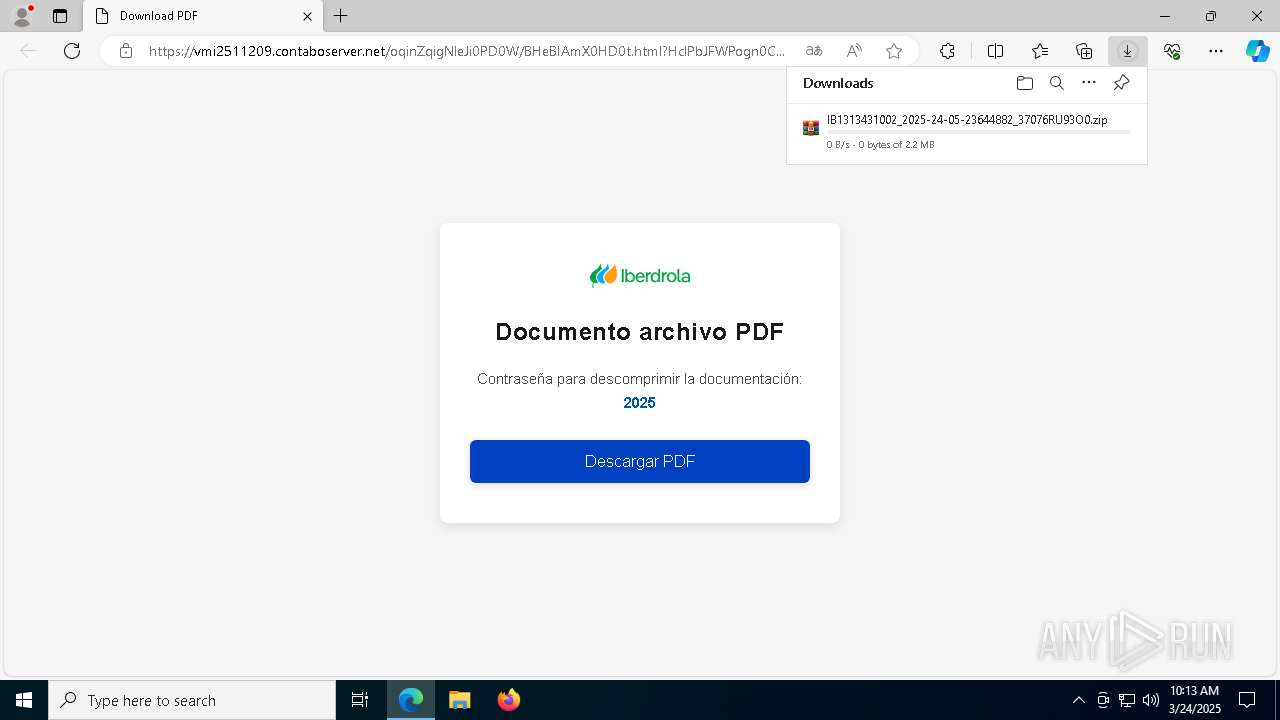
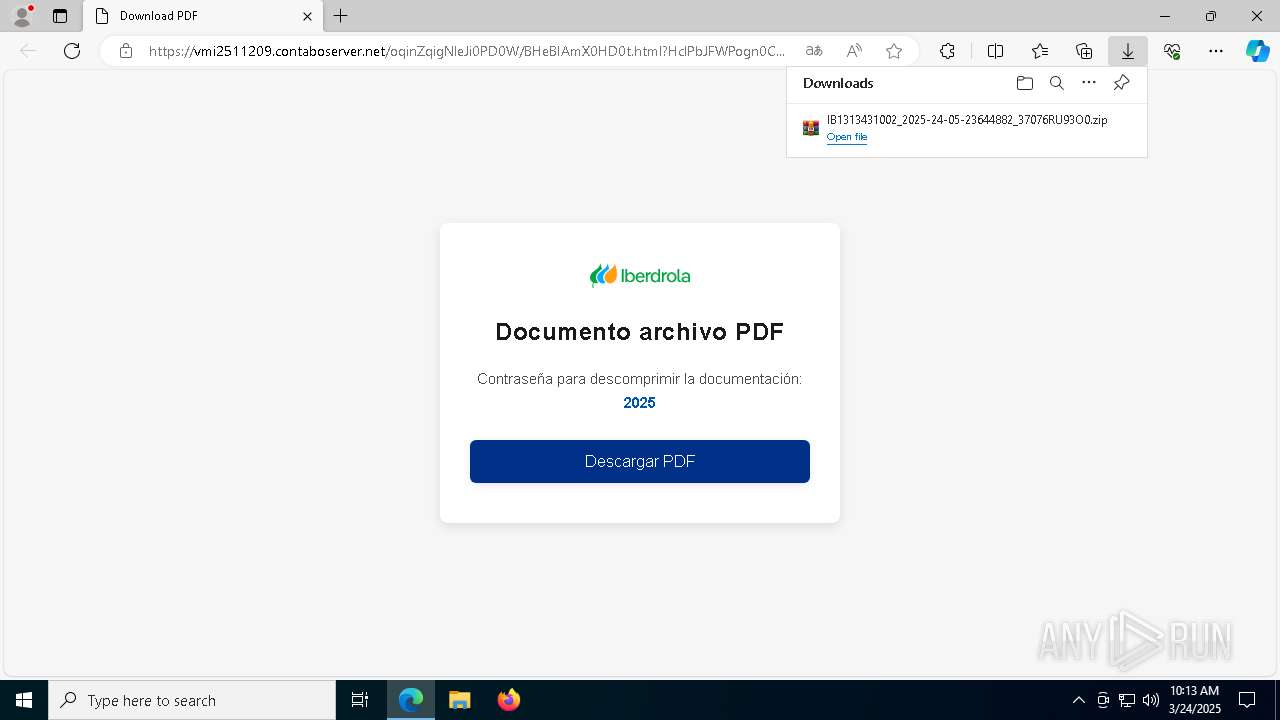
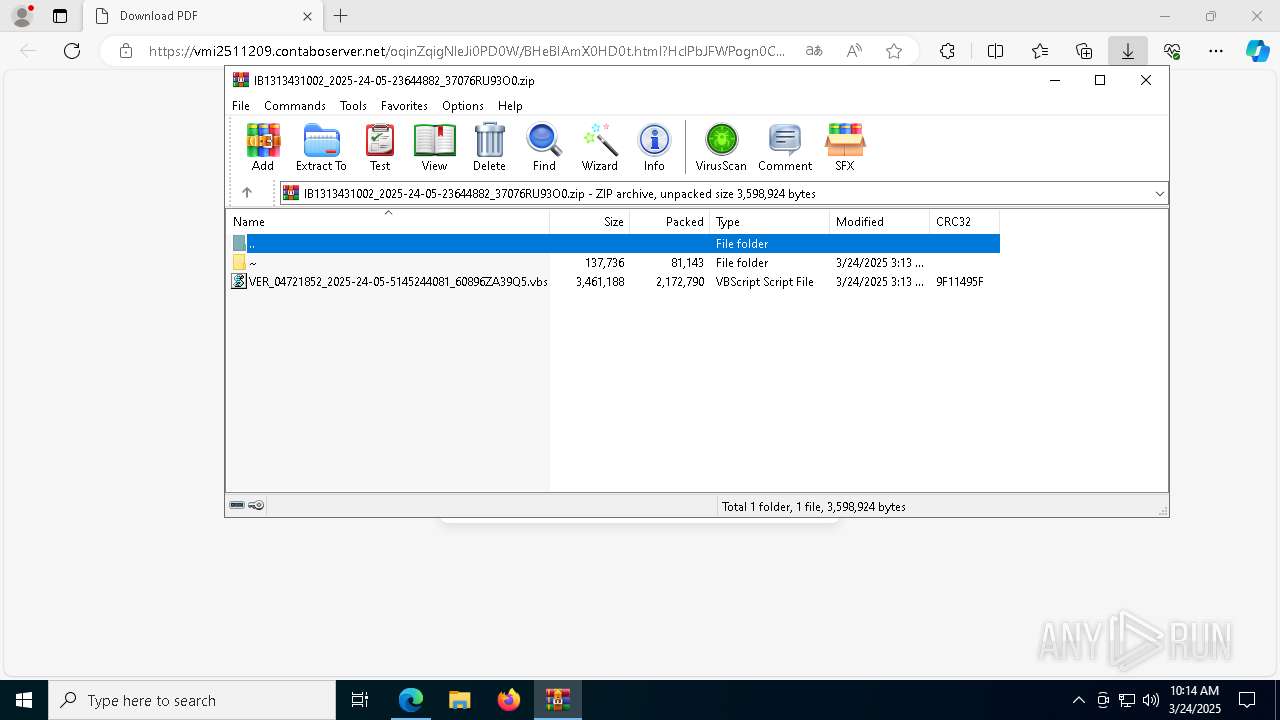
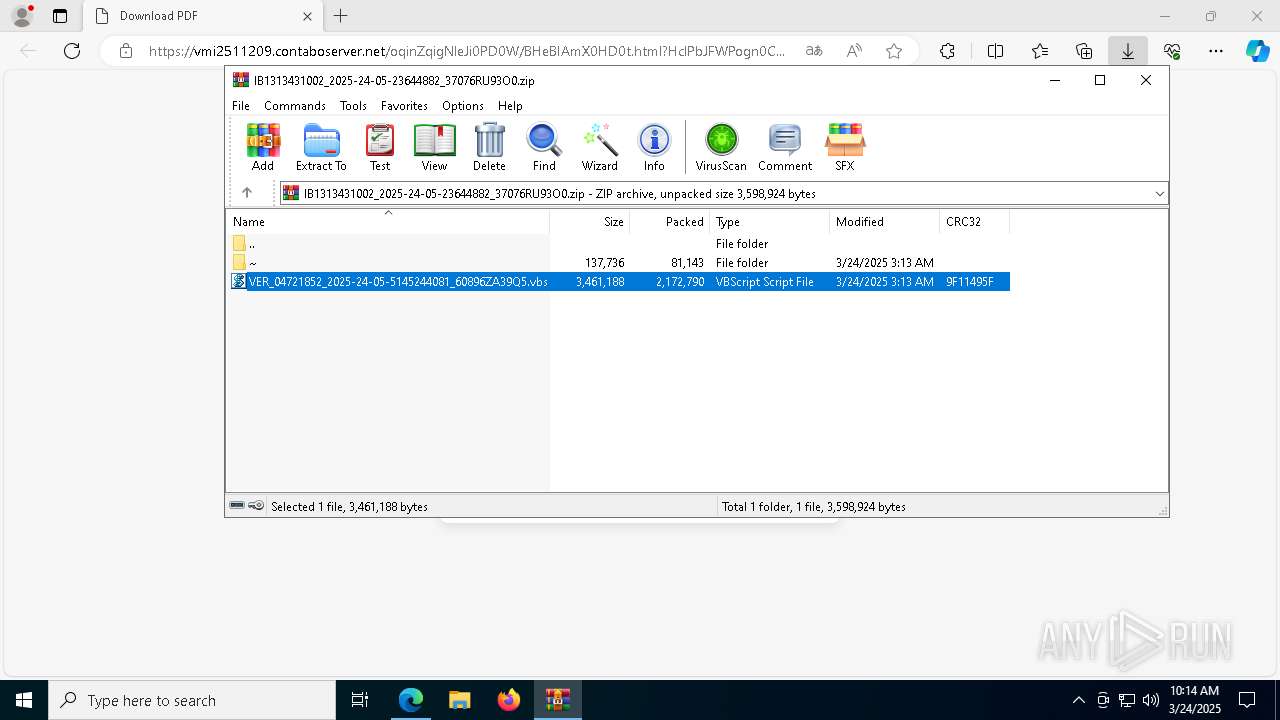
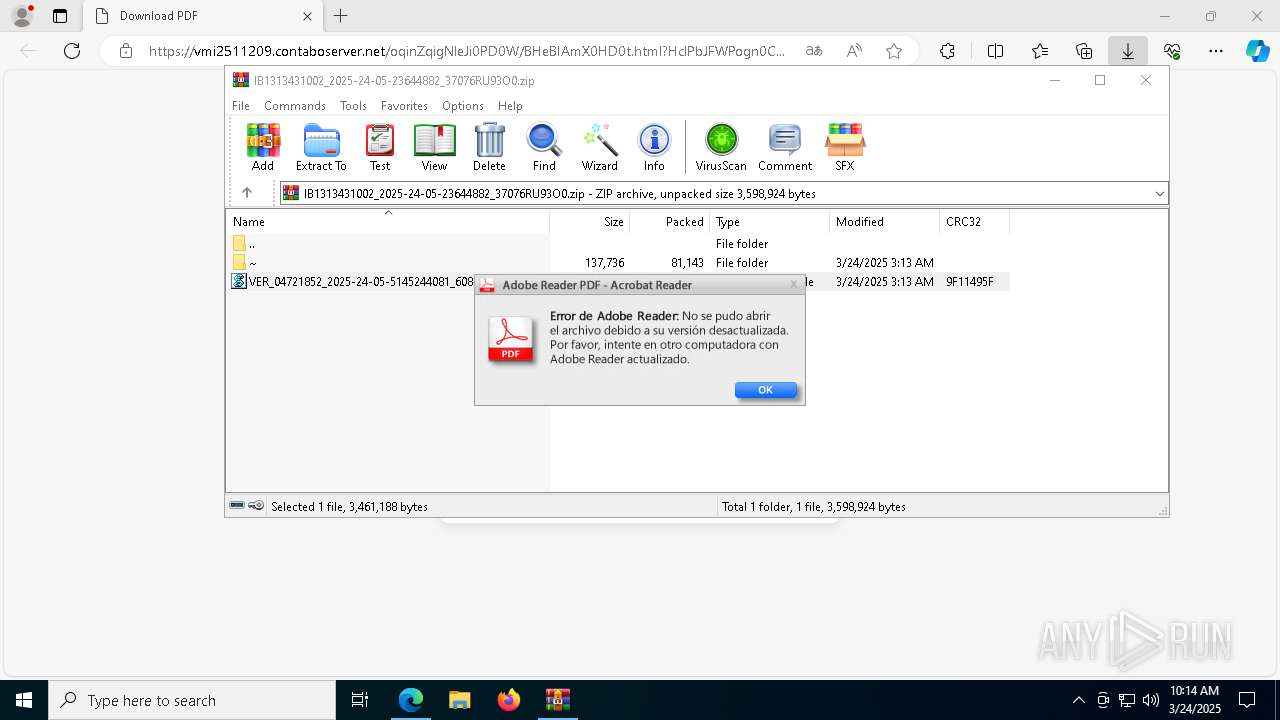
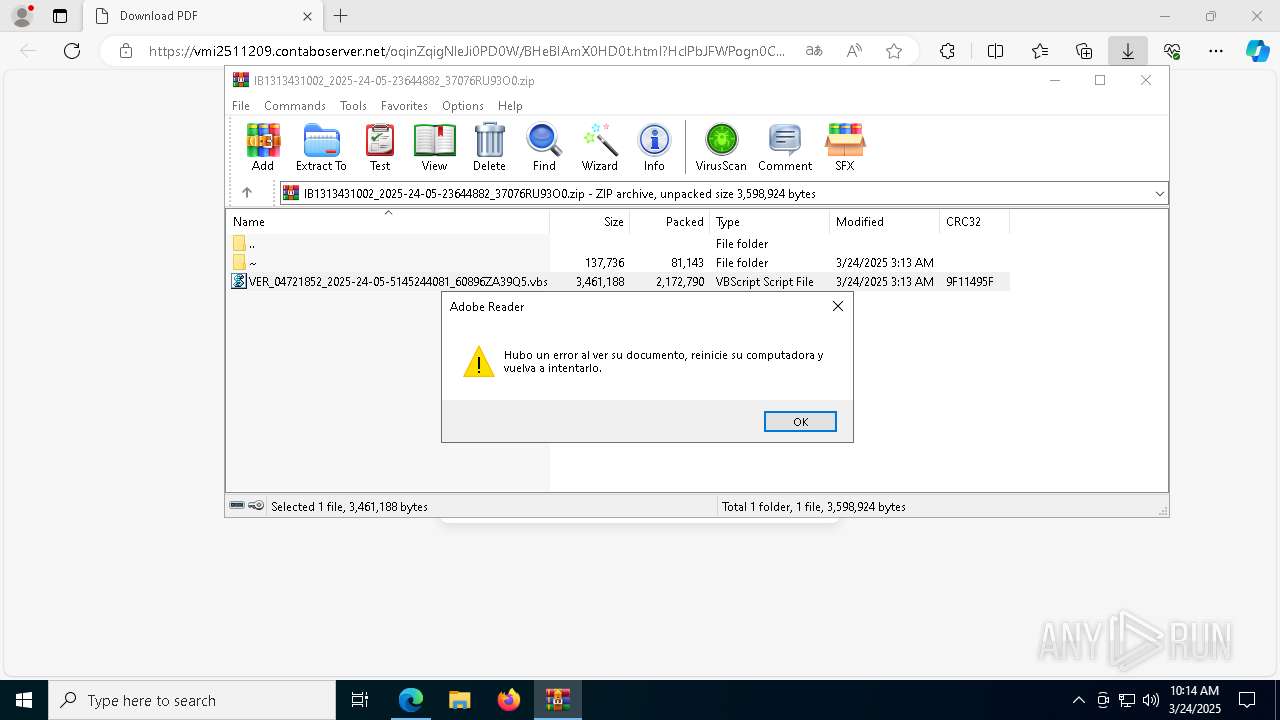
| URL: | https://vmi2511209.contaboserver.net/oqinZqigNleJi0PD0W/BHeBIAmX0HD0t.html?HclPbJFWPogn0CD0Q=d2d4d6823fab68e43a826ff20a8417eb |
| Full analysis: | https://app.any.run/tasks/721d18f6-76f2-408b-8ec9-d392ad1995bb |
| Verdict: | Malicious activity |
| Analysis date: | March 24, 2025, 10:13:34 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 35C2297F96C8EBD4C6BB22B99516FACD |
| SHA1: | 5A3DAFBC2E434C2047C5AC887D7DDA1C96668D62 |
| SHA256: | 86E4D540A737D344475F35F594F4FE85B8748DD3D28167A55F2B3E8DA555D629 |
| SSDEEP: | 3:N83XQELGA3TA8RUkVCdmaklFaZSjdGDuTCXZEYSAH:23AElTAunCdsl0ZHDhKIH |
MALICIOUS
Deletes a file (SCRIPT)
- wscript.exe (PID: 7880)
Uses base64 encoding (SCRIPT)
- wscript.exe (PID: 7880)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 2908)
- ShellExperienceHost.exe (PID: 3888)
The process executes VB scripts
- WinRAR.exe (PID: 2908)
Runs shell command (SCRIPT)
- wscript.exe (PID: 7880)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 7880)
Sets XML DOM element text (SCRIPT)
- wscript.exe (PID: 7880)
Likely accesses (executes) a file from the Public directory
- FBbOxqnUeMuyqbSqBViSd.exe (PID: 1628)
Writes binary data to a Stream object (SCRIPT)
- wscript.exe (PID: 7880)
Saves data to a binary file (SCRIPT)
- wscript.exe (PID: 7880)
Checks for external IP
- svchost.exe (PID: 2196)
- FBbOxqnUeMuyqbSqBViSd.exe (PID: 1628)
There is functionality for communication over UDP network (YARA)
- FBbOxqnUeMuyqbSqBViSd.exe (PID: 1628)
Creates a Stream, which may work with files, input/output devices, pipes, or TCP/IP sockets (SCRIPT)
- wscript.exe (PID: 7880)
There is functionality for taking screenshot (YARA)
- FBbOxqnUeMuyqbSqBViSd.exe (PID: 1628)
INFO
Checks supported languages
- identity_helper.exe (PID: 6048)
- ShellExperienceHost.exe (PID: 3888)
- FBbOxqnUeMuyqbSqBViSd.exe (PID: 1628)
Reads the computer name
- identity_helper.exe (PID: 6048)
- ShellExperienceHost.exe (PID: 3888)
- FBbOxqnUeMuyqbSqBViSd.exe (PID: 1628)
Reads Environment values
- identity_helper.exe (PID: 6048)
Autorun file from Downloads
- msedge.exe (PID: 4944)
- msedge.exe (PID: 6964)
Reads security settings of Internet Explorer
- BackgroundTransferHost.exe (PID: 4436)
- BackgroundTransferHost.exe (PID: 2552)
- BackgroundTransferHost.exe (PID: 7708)
- BackgroundTransferHost.exe (PID: 3100)
- BackgroundTransferHost.exe (PID: 6576)
Creates files or folders in the user directory
- BackgroundTransferHost.exe (PID: 2552)
Checks proxy server information
- BackgroundTransferHost.exe (PID: 2552)
- slui.exe (PID: 7676)
Reads the software policy settings
- BackgroundTransferHost.exe (PID: 2552)
- slui.exe (PID: 8108)
- slui.exe (PID: 7676)
Application launched itself
- msedge.exe (PID: 4944)
Reads Microsoft Office registry keys
- msedge.exe (PID: 4944)
- WinRAR.exe (PID: 2908)
The sample compiled with english language support
- wscript.exe (PID: 7880)
- msedge.exe (PID: 7748)
Compiled with Borland Delphi (YARA)
- FBbOxqnUeMuyqbSqBViSd.exe (PID: 1628)
Executable content was dropped or overwritten
- msedge.exe (PID: 7748)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
200
Monitored processes
60
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 444 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=2580 --field-trial-handle=1996,i,12174652862898989693,6115443014885495136,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 744 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=26 --mojo-platform-channel-handle=6488 --field-trial-handle=1996,i,12174652862898989693,6115443014885495136,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1196 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=3640 --field-trial-handle=1996,i,12174652862898989693,6115443014885495136,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1272 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=4404 --field-trial-handle=1996,i,12174652862898989693,6115443014885495136,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1628 | "C:\Users\Public\FBbOxqnUeMuyqbSqBViSd.exe" | C:\Users\Public\FBbOxqnUeMuyqbSqBViSd.exe | wscript.exe | ||||||||||||
User: admin Company: CloudBridge Solutions 437756 Inc. Integrity Level: MEDIUM Description: Advanced Data Protection Management 437756, 49590.13709.32418.30035, I821. Exit code: 0 Version: 49590.13709.32418.30035 Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2552 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2908 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\IB1313431002_2025-24-05-23644882_37076RU93O0.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | msedge.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 3100 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3268 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=6972 --field-trial-handle=1996,i,12174652862898989693,6115443014885495136,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
13 017
Read events
12 973
Write events
44
Delete events
0
Modification events
| (PID) Process: | (4944) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 879B3724AA8F2F00 | |||
| (PID) Process: | (4944) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 63654124AA8F2F00 | |||
| (PID) Process: | (4944) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\262926 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {E159E75F-99EE-4C95-9D9E-5B07970F0EA5} | |||
| (PID) Process: | (4944) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\262926 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {CF14C231-E4D1-42E7-AE50-2DFD47901BE6} | |||
| (PID) Process: | (4944) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (4944) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (4944) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (4944) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (4944) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 8B027024AA8F2F00 | |||
| (PID) Process: | (4944) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | MicrosoftEdgeAutoLaunch_29EBC4579851B72EE312C449CF839B1A |
Value: "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --no-startup-window --win-session-start | |||
Executable files
9
Suspicious files
143
Text files
50
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4944 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF10b671.TMP | — | |
MD5:— | SHA256:— | |||
| 4944 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4944 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF10b671.TMP | — | |
MD5:— | SHA256:— | |||
| 4944 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4944 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF10b680.TMP | — | |
MD5:— | SHA256:— | |||
| 4944 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4944 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF10b690.TMP | — | |
MD5:— | SHA256:— | |||
| 4944 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4944 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF10b6a0.TMP | — | |
MD5:— | SHA256:— | |||
| 4944 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
38
TCP/UDP connections
63
DNS requests
77
Threats
8
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
4400 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | unknown |
6272 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | unknown |
6272 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | unknown |
2552 | BackgroundTransferHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | unknown |
2268 | svchost.exe | HEAD | 200 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/e9f25f54-9a54-4e31-91fd-7fd2ad4f4a2f?P1=1743005688&P2=404&P3=2&P4=Iy0XPksiUj8GV%2fyALgIKJdgvmkwhlQ41ilM%2f4k74aRuHjPf5sMT80GTHQoZH2oHnc5g2ZA6yVJ%2b7NhX%2bqI3jEg%3d%3d | unknown | — | — | unknown |
1628 | FBbOxqnUeMuyqbSqBViSd.exe | GET | 200 | 208.95.112.1:80 | http://ip-api.com/json | unknown | — | — | unknown |
2268 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/e9f25f54-9a54-4e31-91fd-7fd2ad4f4a2f?P1=1743005688&P2=404&P3=2&P4=Iy0XPksiUj8GV%2fyALgIKJdgvmkwhlQ41ilM%2f4k74aRuHjPf5sMT80GTHQoZH2oHnc5g2ZA6yVJ%2b7NhX%2bqI3jEg%3d%3d | unknown | — | — | unknown |
2268 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/e9f25f54-9a54-4e31-91fd-7fd2ad4f4a2f?P1=1743005688&P2=404&P3=2&P4=Iy0XPksiUj8GV%2fyALgIKJdgvmkwhlQ41ilM%2f4k74aRuHjPf5sMT80GTHQoZH2oHnc5g2ZA6yVJ%2b7NhX%2bqI3jEg%3d%3d | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:137 | — | — | — | unknown |
— | — | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
5496 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | unknown |
4944 | msedge.exe | 239.255.255.250:1900 | — | — | — | unknown |
7336 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
7336 | msedge.exe | 150.171.27.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
7336 | msedge.exe | 13.107.246.44:443 | edge-mobile-static.azureedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
7336 | msedge.exe | 144.91.82.244:443 | vmi2511209.contaboserver.net | Contabo GmbH | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| unknown |
crl.microsoft.com |
| unknown |
google.com |
| unknown |
config.edge.skype.com |
| unknown |
vmi2511209.contaboserver.net |
| unknown |
edge.microsoft.com |
| unknown |
edge-mobile-static.azureedge.net |
| unknown |
business.bing.com |
| unknown |
bzib.nelreports.net |
| unknown |
www.bing.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7336 | msedge.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain (www .mediafire .com) in DNS Lookup |
7336 | msedge.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain (www .mediafire .com) in DNS Lookup |
7336 | msedge.exe | Potentially Bad Traffic | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (download .mediafire .com) |
7336 | msedge.exe | Potentially Bad Traffic | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (download .mediafire .com) |
2196 | svchost.exe | Device Retrieving External IP Address Detected | INFO [ANY.RUN] External IP Check (ip-api .com) |
1628 | FBbOxqnUeMuyqbSqBViSd.exe | A Network Trojan was detected | ET USER_AGENTS Suspicious User-Agent (Clever Internet Suite) |
2196 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (ip-api .com) |
1628 | FBbOxqnUeMuyqbSqBViSd.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup ip-api.com |